#coding and robotics for certificate
Explore tagged Tumblr posts
Text
Why You Should Pursue a Diploma in Robotics & Intelligent Systems at NYRA Academy Singapore
In our time of the world that is now development technologically as in a quick pace, the requirement for skilled people in robotics and intelligent systems increase. With the increasing process of industry automation and utilization of artificial intelligence (AI) across the world economy, individuals with right skills and know-how will be able to make progress in this dynamic field. We acknowledge that an intelligent and futuristic academy like ours can only instil in our students the skills they would need for the tomorrow, and that is why this institution will be offering a wide range of robotics and intelligent systems diplomas.
Here are three compelling reasons why you should consider enrolling in our program:

Innovation Driving Careers: Robotics and a new generation of intelligent systems are now shaping the world of innovation. They are on the verge of changing the paradigms of numerous industries, among them manufacturing and healthcare, to name but a few. Through your learning while getting your diploma in this field, you will gain invaluable hands-on experience of working with the latest cutting-edge technologies which will prepare you for an exciting range of career opportunities in fields that are reshaping and redefining the future.
Meeting Industry Demands: With the uptake of automation coupled with machine learning and AI in many business practices, there are more and more jobs that are on demand such as the engineers who are into programming robotic systems. Our diploma course is prepared in cooperation with industry professionals, providing you with both theory. practical skills except the knowledge wanted on the labour market nowadays.
Future-Proofing Your Career: Considering the breakneck pace at which robotic and AI progress is occurring, the potential for shifting directions in the future makes it imperative to be adaptive and innovative in order to thrive. Our course material has always been updated according to the development of new trends and technologies to prepare you for your future job environment where you are likely to be ahead of the competitors if you are able to adapt your knowledge to the new technological and work-related aspects.
At NYRA Academy Singapore, you will certainly go on this exciting path that leads to a profession with a rewarding future which is to be a graduate of Diploma in Robotics & Intelligent Systems. Our faculty, modern facilities and a curriculum which is industry dependent will guarantee you the needed tools to propel your career into this exciting field. It is not for you to miss the chance of being at the head of innovative technologies – settle at the NYRA Academy Singapore and make use of the chance thus granted to you to get versed in robotics and systems of intelligent nature.
#ai course singapore#robotics short courses for teenagers#coding and robotics for certificate#interactive stories coding for kids#Teen python courses#beginners coding lessons for youngsters#certificate in python programming
0 notes
Text
Greetings!! Be future ready! Unlock Your Future in IT for tech and non tech students and professionals!
1. Study Scrum for FREE! Take the first step towards Agile project management with Udemy course, "Introduction to Scrum (Scrum Guide) With More PSM1 terms". Type course name in udemy site search to access this course.
2. Revolutionize Your Skills with Generative AI & RPA! Get instant access to our exclusive 10-hour course, featuring: - Generative AI - 4 industry-leading RPA tools: Automation Anywhere 360, UIPAth, Blue Prism, and Power Automate - 14 hands-on demos to practice with free AI and RPA tools on your laptop - Unbeatable price: just Rs 399(USD 4.8)! (WhatsApp at 91-9871117072 to get a coupon code for this discounted offer)
Don't miss out on these game-changing opportunities! Enroll now and transform your career in IT! Happy Learning!
#artificial intelligence#agile scrum certification#information technology#low code development#robotics and automation#robotics engineering#robotics for kids#coding#robotics#low code automation
0 notes
Text
Demon-haunted computers are back, baby

Catch me in Miami! I'll be at Books and Books in Coral Gables on Jan 22 at 8PM.

As a science fiction writer, I am professionally irritated by a lot of sf movies. Not only do those writers get paid a lot more than I do, they insist on including things like "self-destruct" buttons on the bridges of their starships.
Look, I get it. When the evil empire is closing in on your flagship with its secret transdimensional technology, it's important that you keep those secrets out of the emperor's hand. An irrevocable self-destruct switch there on the bridge gets the job done! (It has to be irrevocable, otherwise the baddies'll just swarm the bridge and toggle it off).
But c'mon. If there's a facility built into your spaceship that causes it to explode no matter what the people on the bridge do, that is also a pretty big security risk! What if the bad guy figures out how to hijack the measure that – by design – the people who depend on the spaceship as a matter of life and death can't detect or override?
I mean, sure, you can try to simplify that self-destruct system to make it easier to audit and assure yourself that it doesn't have any bugs in it, but remember Schneier's Law: anyone can design a security system that works so well that they themselves can't think of a flaw in it. That doesn't mean you've made a security system that works – only that you've made a security system that works on people stupider than you.
I know it's weird to be worried about realism in movies that pretend we will ever find a practical means to visit other star systems and shuttle back and forth between them (which we are very, very unlikely to do):
https://pluralistic.net/2024/01/09/astrobezzle/#send-robots-instead
But this kind of foolishness galls me. It galls me even more when it happens in the real world of technology design, which is why I've spent the past quarter-century being very cross about Digital Rights Management in general, and trusted computing in particular.
It all starts in 2002, when a team from Microsoft visited our offices at EFF to tell us about this new thing they'd dreamed up called "trusted computing":
https://pluralistic.net/2020/12/05/trusting-trust/#thompsons-devil
The big idea was to stick a second computer inside your computer, a very secure little co-processor, that you couldn't access directly, let alone reprogram or interfere with. As far as this "trusted platform module" was concerned, you were the enemy. The "trust" in trusted computing was about other people being able to trust your computer, even if they didn't trust you.
So that little TPM would do all kinds of cute tricks. It could observe and produce a cryptographically signed manifest of the entire boot-chain of your computer, which was meant to be an unforgeable certificate attesting to which kind of computer you were running and what software you were running on it. That meant that programs on other computers could decide whether to talk to your computer based on whether they agreed with your choices about which code to run.
This process, called "remote attestation," is generally billed as a way to identify and block computers that have been compromised by malware, or to identify gamers who are running cheats and refuse to play with them. But inevitably it turns into a way to refuse service to computers that have privacy blockers turned on, or are running stream-ripping software, or whose owners are blocking ads:
https://pluralistic.net/2023/08/02/self-incrimination/#wei-bai-bai
After all, a system that treats the device's owner as an adversary is a natural ally for the owner's other, human adversaries. The rubric for treating the owner as an adversary focuses on the way that users can be fooled by bad people with bad programs. If your computer gets taken over by malicious software, that malware might intercept queries from your antivirus program and send it false data that lulls it into thinking your computer is fine, even as your private data is being plundered and your system is being used to launch malware attacks on others.
These separate, non-user-accessible, non-updateable secure systems serve a nubs of certainty, a remote fortress that observes and faithfully reports on the interior workings of your computer. This separate system can't be user-modifiable or field-updateable, because then malicious software could impersonate the user and disable the security chip.
It's true that compromised computers are a real and terrifying problem. Your computer is privy to your most intimate secrets and an attacker who can turn it against you can harm you in untold ways. But the widespread redesign of out computers to treat us as their enemies gives rise to a range of completely predictable and – I would argue – even worse harms. Building computers that treat their owners as untrusted parties is a system that works well, but fails badly.
First of all, there are the ways that trusted computing is designed to hurt you. The most reliable way to enshittify something is to supply it over a computer that runs programs you can't alter, and that rats you out to third parties if you run counter-programs that disenshittify the service you're using. That's how we get inkjet printers that refuse to use perfectly good third-party ink and cars that refuse to accept perfectly good engine repairs if they are performed by third-party mechanics:
https://pluralistic.net/2023/07/24/rent-to-pwn/#kitt-is-a-demon
It's how we get cursed devices and appliances, from the juicer that won't squeeze third-party juice to the insulin pump that won't connect to a third-party continuous glucose monitor:
https://arstechnica.com/gaming/2020/01/unauthorized-bread-a-near-future-tale-of-refugees-and-sinister-iot-appliances/
But trusted computing doesn't just create an opaque veil between your computer and the programs you use to inspect and control it. Trusted computing creates a no-go zone where programs can change their behavior based on whether they think they're being observed.
The most prominent example of this is Dieselgate, where auto manufacturers murdered hundreds of people by gimmicking their cars to emit illegal amount of NOX. Key to Dieselgate was a program that sought to determine whether it was being observed by regulators (it checked for the telltale signs of the standard test-suite) and changed its behavior to color within the lines.
Software that is seeking to harm the owner of the device that's running it must be able to detect when it is being run inside a simulation, a test-suite, a virtual machine, or any other hallucinatory virtual world. Just as Descartes couldn't know whether anything was real until he assured himself that he could trust his senses, malware is always questing to discover whether it is running in the real universe, or in a simulation created by a wicked god:
https://pluralistic.net/2022/07/28/descartes-was-an-optimist/#uh-oh
That's why mobile malware uses clever gambits like periodically checking for readings from your device's accelerometer, on the theory that a virtual mobile phone running on a security researcher's test bench won't have the fidelity to generate plausible jiggles to match the real data that comes from a phone in your pocket:
https://arstechnica.com/information-technology/2019/01/google-play-malware-used-phones-motion-sensors-to-conceal-itself/
Sometimes this backfires in absolutely delightful ways. When the Wannacry ransomware was holding the world hostage, the security researcher Marcus Hutchins noticed that its code made reference to a very weird website: iuqerfsodp9ifjaposdfjhgosurijfaewrwergwea.com. Hutchins stood up a website at that address and every Wannacry-infection in the world went instantly dormant:
https://pluralistic.net/2020/07/10/flintstone-delano-roosevelt/#the-matrix
It turns out that Wannacry's authors were using that ferkakte URL the same way that mobile malware authors were using accelerometer readings – to fulfill Descartes' imperative to distinguish the Matrix from reality. The malware authors knew that security researchers often ran malicious code inside sandboxes that answered every network query with fake data in hopes of eliciting responses that could be analyzed for weaknesses. So the Wannacry worm would periodically poll this nonexistent website and, if it got an answer, it would assume that it was being monitored by a security researcher and it would retreat to an encrypted blob, ceasing to operate lest it give intelligence to the enemy. When Hutchins put a webserver up at iuqerfsodp9ifjaposdfjhgosurijfaewrwergwea.com, every Wannacry instance in the world was instantly convinced that it was running on an enemy's simulator and withdrew into sulky hibernation.
The arms race to distinguish simulation from reality is critical and the stakes only get higher by the day. Malware abounds, even as our devices grow more intimately woven through our lives. We put our bodies into computers – cars, buildings – and computers inside our bodies. We absolutely want our computers to be able to faithfully convey what's going on inside them.
But we keep running as hard as we can in the opposite direction, leaning harder into secure computing models built on subsystems in our computers that treat us as the threat. Take UEFI, the ubiquitous security system that observes your computer's boot process, halting it if it sees something it doesn't approve of. On the one hand, this has made installing GNU/Linux and other alternative OSes vastly harder across a wide variety of devices. This means that when a vendor end-of-lifes a gadget, no one can make an alternative OS for it, so off the landfill it goes.
It doesn't help that UEFI – and other trusted computing modules – are covered by Section 1201 of the Digital Millennium Copyright Act (DMCA), which makes it a felony to publish information that can bypass or weaken the system. The threat of a five-year prison sentence and a $500,000 fine means that UEFI and other trusted computing systems are understudied, leaving them festering with longstanding bugs:
https://pluralistic.net/2020/09/09/free-sample/#que-viva
Here's where it gets really bad. If an attacker can get inside UEFI, they can run malicious software that – by design – no program running on our computers can detect or block. That badware is running in "Ring -1" – a zone of privilege that overrides the operating system itself.
Here's the bad news: UEFI malware has already been detected in the wild:
https://securelist.com/cosmicstrand-uefi-firmware-rootkit/106973/
And here's the worst news: researchers have just identified another exploitable UEFI bug, dubbed Pixiefail:
https://blog.quarkslab.com/pixiefail-nine-vulnerabilities-in-tianocores-edk-ii-ipv6-network-stack.html
Writing in Ars Technica, Dan Goodin breaks down Pixiefail, describing how anyone on the same LAN as a vulnerable computer can infect its firmware:
https://arstechnica.com/security/2024/01/new-uefi-vulnerabilities-send-firmware-devs-across-an-entire-ecosystem-scrambling/
That vulnerability extends to computers in a data-center where the attacker has a cloud computing instance. PXE – the system that Pixiefail attacks – isn't widely used in home or office environments, but it's very common in data-centers.
Again, once a computer is exploited with Pixiefail, software running on that computer can't detect or delete the Pixiefail code. When the compromised computer is queried by the operating system, Pixiefail undetectably lies to the OS. "Hey, OS, does this drive have a file called 'pixiefail?'" "Nope." "Hey, OS, are you running a process called 'pixiefail?'" "Nope."
This is a self-destruct switch that's been compromised by the enemy, and which no one on the bridge can de-activate – by design. It's not the first time this has happened, and it won't be the last.
There are models for helping your computer bust out of the Matrix. Back in 2016, Edward Snowden and bunnie Huang prototyped and published source code and schematics for an "introspection engine":
https://assets.pubpub.org/aacpjrja/AgainstTheLaw-CounteringLawfulAbusesofDigitalSurveillance.pdf
This is a single-board computer that lives in an ultraslim shim that you slide between your iPhone's mainboard and its case, leaving a ribbon cable poking out of the SIM slot. This connects to a case that has its own OLED display. The board has leads that physically contact each of the network interfaces on the phone, conveying any data they transit to the screen so that you can observe the data your phone is sending without having to trust your phone.
(I liked this gadget so much that I included it as a major plot point in my 2020 novel Attack Surface, the third book in the Little Brother series):
https://craphound.com/attacksurface/
We don't have to cede control over our devices in order to secure them. Indeed, we can't ever secure them unless we can control them. Self-destruct switches don't belong on the bridge of your spaceship, and trusted computing modules don't belong in your devices.

I'm Kickstarting the audiobook for The Bezzle, the sequel to Red Team Blues, narrated by @wilwheaton! You can pre-order the audiobook and ebook, DRM free, as well as the hardcover, signed or unsigned. There's also bundles with Red Team Blues in ebook, audio or paperback.

If you'd like an essay-formatted version of this post to read or share, here's a link to it on pluralistic.net, my surveillance-free, ad-free, tracker-free blog:
https://pluralistic.net/2024/01/17/descartes-delenda-est/#self-destruct-sequence-initiated

Image: Mike (modified) https://www.flickr.com/photos/stillwellmike/15676883261/
CC BY-SA 2.0 https://creativecommons.org/licenses/by-sa/2.0/
#pluralistic#uefi#owner override#user override#jailbreaking#dmca 1201#schneiers law#descartes#nub of certainty#self-destruct button#trusted computing#secure enclaves#drm#ngscb#next generation secure computing base#palladium#pixiefail#infosec
576 notes
·
View notes
Text
Welcome to Error Code! ↳ Meet your Computer Tech

this is a redacted audio oc rp/ask blog, maintained by milogreer / lovaboy ! please read the carrd linked above for all important info, and look below the cut for some bonus info about omen ❤️

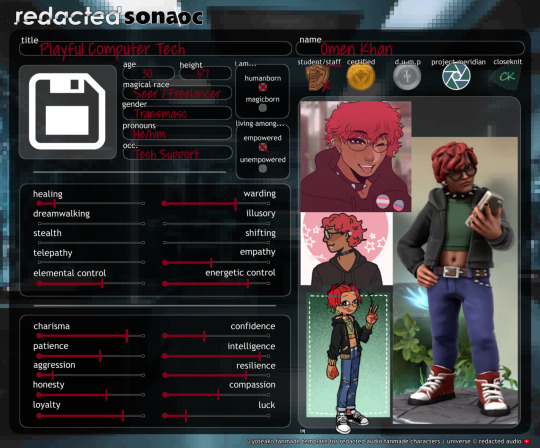


basics
born october 20, 1994
south asian american
moved to dahlia after graduating high school to attend D.A.M.N
seer masquerading as a “boring ol’ freelancer”
works at Error Code, a vintage electronics/media & tech support store on D.A.M.N's campus ↳ coworkers: @avamental, @rnprice
really good with technology and electronics. fancies himself a robotics engineer
personality
the loss of his brother and subsequently being disowned led to him self-isolating since his teens, though you wouldn't know it from his general upbeat and playful demeanor around people
he does like people and being around them, he's just generally careful not to get too close to anyone because of his Sight. stems from not wanting anyone to experience the heartbreak he went through when his brother died in the event of his own death + not wanting to experience further loss himself
primarily uses his Sight for little things (weather forecasts, traffic incidents, etc) so he can a) avoid involuntary visions and b) keep visions quick. the less he’s in the time streams, the better - his own death vision scares him
coping with the burden of Life and Death. but he stays silly /ref
always joking, even if the mood isn't right for it. but he can be sincere under the right circumstances
really smart (especially in tech, obviously) and always looking to learn more. people get annoyed sometimes by his constant questions, but he's not trying to be intrusive or anything. he's just curious
backstory
born to uninformed and unempowered parents
had a really hard time with his Sight when it first manifested in his early teens because he had no one to talk to about it. probably thought he was going crazy
he kept his visions locked down because they scared him after he saw his own death, but when he started seeing his brother's death, he finally told his parents about them
obviously they didn't believe him and thought he was being weird and morbid, but his brother died almost exactly the way he foretold, and they eventually disowned because they thought he was like. cursed. and they couldn't handle his downward spiral
from there he luckily ended up on the empowered side of things and was able to get help understanding his Sight. after graduating high school, he moved out to dahlia to attend D.A.M.N., where he got full certification as a freelancer
other
has a siamese cat named oracle. she's a certified emotional support animal
has a fucked up sleep schedule because he has chronic insomnia. also plagued by headaches, partially because of this
goes for energy drinks over soda. caffeine sharpens his Sight
relates his Sight to, like... building a PC or something. bunch of different pieces that can be changed to alter the performance in some way, ykwim? i don't build PCs idk
unapologetic romcom enjoyer. don't ask unless you want him to whip out his letterboxd and talk your ear off
despite being able to see the future, he has very bad luck. always losing chance games, spilling drinks onto keyboards, tripping over untied shoelaces, etc
has an irrational fear of birds but would sooner die than admit it
22 notes
·
View notes
Text
Today in my brain:
Don't think about how April and the boys become Splinter's caretakers as he gets older. He's always been active, so it's a slower decline than most, but eventually, his body starts catching up with his age in more ways than just appearance.
Don't think about how Donnie and April research and make their home more accessible. Donnie builds mobility aids - a cane, a walker and braces so Splinter can get on and off his favourite couch on his own. A little robot that helps their dad carry things from place to place. April makes sure her first aid certification is always up to date, and learns as much as she can about caring for the elderly. She learns so she can spot symptoms as they appear.
Mikey starts being stricter about what they eat . He makes more pizzas from scratch, finds substitutes for Splinter's favourite snacks - and still keeps the junk food, but as a treat. The others are dragged in because there's no way he's cooking two meals, they all need to be healthier anyways, and they can't let dad feel alone!
Suddenly Leo is labeling everything! He has a system and of course it's colour coded. Leo ensures that Splinter is never left alone for too long. He starts creating shifts for patrols so someone is always nearby. The lair is no longer allowed to remain unclean for extended amounts of time, and they're always stocked with supplies.
Raph starts keeping track of doctor's appointments and schedules. He makes sure Splinter gets up and moves throughout the day, taking walks, even playing games with the others to keep his mind working. He encourages splinter to go to activities and make friends in the hidden city, anything really to keep him from always being cooped up in the lair.
It's not a perfect or easy reality. There are bad days when Splinter is stubborn or April and the boys get frustrated. They're still young, it's not going to happen perfectly, in fact it rarely does. They're becoming caretakers for thier dad, but they still need thier dad. They get into fights when the boys start making choices and changes. When Splinter's memory begins to fade, it upsets everyone and April forces everyone out to the rooftops at night for some fresh air and a much needed conversation.
There are still good moments too! Splinter may need to adjust, but he loves his children more than anything. So what if he can't spar with them anymore, he shows up to the next training session with score cards and ranks thier best moves mid fight. He calls out points and imitates the announcers from those boxing matches Raph loves so much.
He makes sure to spend time with all his kids individually, he leaves them little gifts, when he mixes up thier names they laugh at it more then they're upset about it. They make peace with it.
#this is the rtmnt universe so imagine they take Splinter to the Hidden City for his doctor's appointments#Draxom shares as much info as he can about Splinter's mixed DNA to help them build an accurate medical profile#it's upsetting but the boys nd April make peace with it in thier own ways.#they have a few scares at first when Splinter is still more resistant to change#but after one bad fall that scares his children to tears and prompts a fair amount of cuddles#Splinter agrees to be open to the care he now needs#he still tries to shield his children and handle as much as he can but his kids are happy to take on the responsibility#rtmnt#rise of the tmnt#inspired by watching and helping my family care for older relatives#late night ramblings with dragonsbluee#teenage mutant ninja turtles#rise of the teenage mutant ninja turtles#hamato leonardo#hamato michelangelo#hamato donatello#hamato raphael#hamato yoshi#rottmnt
17 notes
·
View notes
Text
robotics: a few resources on getting started
a free open online robotics education resource! includes lots of lessons in video forms, which have transcripts and code sections that allow you to copy + paste from it. each lesson tells you the skill level assumed of you in order for you watch it (from general knowledge -> undergrad engineering). has lots of topics to choose from.
an open-source collection of exercises and challenges to learn robotics in a practical way. there are exercises about drone programming, about computer vision, about mobile robots, about autonomous cars, etc. It is mainly based on gazebo simulator and ROS. the students program their solutions in python.
each exercise is composed of (a) gazebo configuration files, (b) a web template to host student’s code and (c) theory contents.
with each free e-learning module you complete, you earn a certificate!
stanford university has this thing called stanford engineering everywhere which offers a few free courses you can take, including an introduction to robotics course!
some lists on github you can check out for more resources.
43 notes
·
View notes
Note
hii! robot OCs? Love to hear about them!!
Ah, my beloved bunch of vicious miscreants. One of my HiFi Rush OCs has a gaggle of robots outfitted with different primary directives (who also happen to be color-coded) My most favorite one is the one she created first, Designation 1ND1-G0. Who is, as you guessed, indigo. Tall, foreboding, but a big sweetheart.
1ND1-G0, or Indy as many call them, was originally outfitted for mercenary work. An assassin drone to dispatch threats across the globe. Think like Terminator but with a wider range of options. Well, their creator decided that healthcare needed some retooling and re-outfitted 1ND1-G0 to be The Doctor among doctors. Has certifications across the globe, knows all sorts of medicine and surgical practices. Is approved to practice medicine all over.
1ND1-G0's AI actually fell in love with the idea of practicing medicine and advanced its own programming so it could acquire all forms of knowledge surrounding the subject. It even changed its voice so it could come across as more personable to patients. Quite literally the definition of not judging a book by its cover. And its "sibling", the second of the series, got the murder-bot schtick. Each of the rest of the siblings also has their own thing.
#hi fi rush#hi-fi rush#hi fi rush oc#the robot also gave itself pronouns#and it identifies its creator as its “mother”#and sees her biological child as its brother#the whole line of em are a bunch of freaks but I love them so much#ask me about the rest of the robots#or even the people ocs
5 notes
·
View notes
Text
How-To IT
Topic: Core areas of IT
1. Hardware
• Computers (Desktops, Laptops, Workstations)
• Servers and Data Centers
• Networking Devices (Routers, Switches, Modems)
• Storage Devices (HDDs, SSDs, NAS)
• Peripheral Devices (Printers, Scanners, Monitors)
2. Software
• Operating Systems (Windows, Linux, macOS)
• Application Software (Office Suites, ERP, CRM)
• Development Software (IDEs, Code Libraries, APIs)
• Middleware (Integration Tools)
• Security Software (Antivirus, Firewalls, SIEM)
3. Networking and Telecommunications
• LAN/WAN Infrastructure
• Wireless Networking (Wi-Fi, 5G)
• VPNs (Virtual Private Networks)
• Communication Systems (VoIP, Email Servers)
• Internet Services
4. Data Management
• Databases (SQL, NoSQL)
• Data Warehousing
• Big Data Technologies (Hadoop, Spark)
• Backup and Recovery Systems
• Data Integration Tools
5. Cybersecurity
• Network Security
• Endpoint Protection
• Identity and Access Management (IAM)
• Threat Detection and Incident Response
• Encryption and Data Privacy
6. Software Development
• Front-End Development (UI/UX Design)
• Back-End Development
• DevOps and CI/CD Pipelines
• Mobile App Development
• Cloud-Native Development
7. Cloud Computing
• Infrastructure as a Service (IaaS)
• Platform as a Service (PaaS)
• Software as a Service (SaaS)
• Serverless Computing
• Cloud Storage and Management
8. IT Support and Services
• Help Desk Support
• IT Service Management (ITSM)
• System Administration
• Hardware and Software Troubleshooting
• End-User Training
9. Artificial Intelligence and Machine Learning
• AI Algorithms and Frameworks
• Natural Language Processing (NLP)
• Computer Vision
• Robotics
• Predictive Analytics
10. Business Intelligence and Analytics
• Reporting Tools (Tableau, Power BI)
• Data Visualization
• Business Analytics Platforms
• Predictive Modeling
11. Internet of Things (IoT)
• IoT Devices and Sensors
• IoT Platforms
• Edge Computing
• Smart Systems (Homes, Cities, Vehicles)
12. Enterprise Systems
• Enterprise Resource Planning (ERP)
• Customer Relationship Management (CRM)
• Human Resource Management Systems (HRMS)
• Supply Chain Management Systems
13. IT Governance and Compliance
• ITIL (Information Technology Infrastructure Library)
• COBIT (Control Objectives for Information Technologies)
• ISO/IEC Standards
• Regulatory Compliance (GDPR, HIPAA, SOX)
14. Emerging Technologies
• Blockchain
• Quantum Computing
• Augmented Reality (AR) and Virtual Reality (VR)
• 3D Printing
• Digital Twins
15. IT Project Management
• Agile, Scrum, and Kanban
• Waterfall Methodology
• Resource Allocation
• Risk Management
16. IT Infrastructure
• Data Centers
• Virtualization (VMware, Hyper-V)
• Disaster Recovery Planning
• Load Balancing
17. IT Education and Certifications
• Vendor Certifications (Microsoft, Cisco, AWS)
• Training and Development Programs
• Online Learning Platforms
18. IT Operations and Monitoring
• Performance Monitoring (APM, Network Monitoring)
• IT Asset Management
• Event and Incident Management
19. Software Testing
• Manual Testing: Human testers evaluate software by executing test cases without using automation tools.
• Automated Testing: Use of testing tools (e.g., Selenium, JUnit) to run automated scripts and check software behavior.
• Functional Testing: Validating that the software performs its intended functions.
• Non-Functional Testing: Assessing non-functional aspects such as performance, usability, and security.
• Unit Testing: Testing individual components or units of code for correctness.
• Integration Testing: Ensuring that different modules or systems work together as expected.
• System Testing: Verifying the complete software system’s behavior against requirements.
• Acceptance Testing: Conducting tests to confirm that the software meets business requirements (including UAT - User Acceptance Testing).
• Regression Testing: Ensuring that new changes or features do not negatively affect existing functionalities.
• Performance Testing: Testing software performance under various conditions (load, stress, scalability).
• Security Testing: Identifying vulnerabilities and assessing the software’s ability to protect data.
• Compatibility Testing: Ensuring the software works on different operating systems, browsers, or devices.
• Continuous Testing: Integrating testing into the development lifecycle to provide quick feedback and minimize bugs.
• Test Automation Frameworks: Tools and structures used to automate testing processes (e.g., TestNG, Appium).
19. VoIP (Voice over IP)
VoIP Protocols & Standards
• SIP (Session Initiation Protocol)
• H.323
• RTP (Real-Time Transport Protocol)
• MGCP (Media Gateway Control Protocol)
VoIP Hardware
• IP Phones (Desk Phones, Mobile Clients)
• VoIP Gateways
• Analog Telephone Adapters (ATAs)
• VoIP Servers
• Network Switches/ Routers for VoIP
VoIP Software
• Softphones (e.g., Zoiper, X-Lite)
• PBX (Private Branch Exchange) Systems
• VoIP Management Software
• Call Center Solutions (e.g., Asterisk, 3CX)
VoIP Network Infrastructure
• Quality of Service (QoS) Configuration
• VPNs (Virtual Private Networks) for VoIP
• VoIP Traffic Shaping & Bandwidth Management
• Firewall and Security Configurations for VoIP
• Network Monitoring & Optimization Tools
VoIP Security
• Encryption (SRTP, TLS)
• Authentication and Authorization
• Firewall & Intrusion Detection Systems
• VoIP Fraud DetectionVoIP Providers
• Hosted VoIP Services (e.g., RingCentral, Vonage)
• SIP Trunking Providers
• PBX Hosting & Managed Services
VoIP Quality and Testing
• Call Quality Monitoring
• Latency, Jitter, and Packet Loss Testing
• VoIP Performance Metrics and Reporting Tools
• User Acceptance Testing (UAT) for VoIP Systems
Integration with Other Systems
• CRM Integration (e.g., Salesforce with VoIP)
• Unified Communications (UC) Solutions
• Contact Center Integration
• Email, Chat, and Video Communication Integration
2 notes
·
View notes
Text
Happy April 1st, I have no new joke but here's a really good old one.
Buckle up.
Alright. Can't remember if I posted much about this before, but at my old job I produced this videogame. It was pretty cool!! It was set in the future, you're a super soldier who piloted remote robot drones called Espire.
youtube
(Violent little robot Sooty, my beloved. The shotgun pump in the trailer is still my favorite bit.)
I had my fingers in just about every pie that made up this game, and it was extremely cool getting to work with the team. April fools rolled around, game hadn't released just yet, we were finalising into the certification phase.
Every friday we had something called 'demo friday' where the team would show off something they worked on that week and we'd celebrate. It was charming to let everyone have a chance to show off their contributions, from every department in the company. I never really showed off anything because the spreadsheets I worked with, everyone already saw cause I would run around showing people every day as part of my job.
So on this fatefull, April 1st Friday, I asked to show the team something special. I pulled up a powerpoint presentation and add-libbed a new game concept pitch.


I pitched Espire to Love, a robot dating simulator, to a room full of 25 odd videogame developers.
Now as you may or may not have noticed, I don't often dabble in romance as a genre. I've barely touched dating sims and I'd never mentioned them before at work.
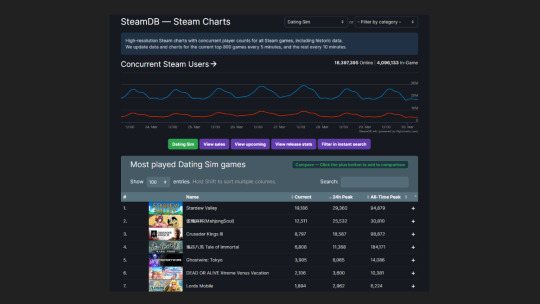
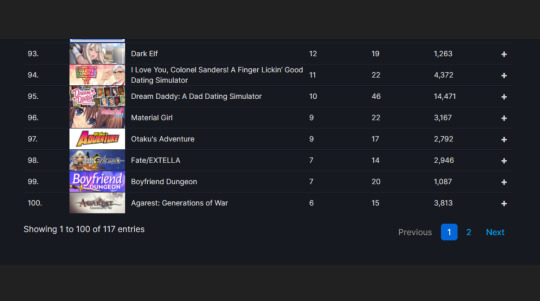

"From Dreamy daddies to anime girls, KFC's the colonel and even dinosaurs, there's an incredible range of options in the dating sim genre" I said with a straight face infront of a room full of people who were crying with laughter. I was barely holding myself together.



No one was prepared for the fake screenshots.
Still remember how hard some of them laughed when I pulled these slides up. I packed a lot of in-jokes into these that I won't explain - I wanted this to hit hard and hit home for the people I'd spent two + years working with.

People loved it, I made my friends laugh, it was good. And then upon being told "Hey you should send this to the publisher!"
That's exactly what I did.

The response from our assigned reps at Tripwire (YES, THAT TRIPWIRE) said they loved it, and they too were asking themselves the question "why not!" the whole way through.
But this story doesn't end there, oh no.
Fast forward a year. The game is released, we're hectic busy working on post release content, I'm cooking up the next stage of the joke.
Unfortunately, it never came to fruition due to time and stress. But here's what it was going to be:
We'd had our community clammoring for merch - so I wanted to pitch something bold, new and exciting, and the kind of thing that'd make us stand out.
Body pillows.
Would have been incredible. Might've made someone faint.
The robots were called Bean and Sooty during development so yes. I was going to deadass say "The bean bag and the sooty sack" (I mean what I say)
Unfortunately I didn't make it in time, and then double unfortunately, I lost my job when the studio had to significantly downsize.
But that never stops me from posting a good bit. You all know I'm a committed freak.
Fast forward a bit more and I'm trying to learn how to make my own games! So I download RenPy since it's a good starting point. It's designed more for VN's, so to find my feet I figured I should make as VN right?
I didn't want to make to make new assets, as the point was me learning to code. What to do..... what to do....
Full circle babeeeeyyyyy
And that's where we're at today! Long post I know, but I'm real proud of this joke. I love a good laugh that hits you at home, that's just honest fun. Huge shoutout to my old co-workers for listening to my original presentation, their laughter filled my heart and I was fucking terrified at the time, it was worth the joke.
It became a running gag in the office - we were playing Jackbox for a work party and it was one of those question and submitted answer games, and without any input from me the team had made the question "What would the for the sequel to Espire to Love be?"
and the options were "Espire to Live" and "Espire to death"
Anyway, I hope you only have charming and well considered April fools jokes today - designed for you to laugh at as much as the person making the joke. That's the best joke. Peace out.
#my art#long post#happy April fools everyone! Look at how fucking intense I am about this#a good april fools is crafted and considered and designed to make YOU laugh as the 'victim'#and I stand by that I used to fucking HATE april fools#and then I realised its cause people were too cruel rather then trying to make others laugh as much as themselves#Youtube
7 notes
·
View notes
Text
5 Arduino Courses for Beginners
Robotics, automation, and do-it-yourself electronics projects have all been transformed by Arduino, an open-source electronics platform. Entering the world of Arduino may seem intimidating to novices, but the correct course may make learning easier and more fun.
Arduino Step-by-Step: Getting Started (Udemy)
This extensive Udemy course is designed for complete novices. It provides an overview of Arduino's fundamentals, describing how the platform functions and assisting students with easy tasks like using sensors and manipulating LEDs.
Key Highlights:
thorough explanations for novices.
practical projects with practical uses.
instructions for configuring and debugging your Arduino board.
Introduction to Arduino (Coursera)
The main objective of this course is to introduce Arduino programming with the Arduino IDE. It goes over the fundamentals of circuits, programming, and connecting various parts, such as motors and sensors.
Key Highlights:
instructed by academics from universities.
access to a certificate of completion and graded assignments.
Concepts are explained in length but in a beginner-friendly manner.
Arduino for Absolute Beginners (Skillshare)
For those who want a quick introduction to Arduino, this brief project-based course is perfect. You'll discover how to configure and program your Arduino board to produce interactive projects.
Key Highlights:
teachings in bite-sized chunks for speedy learning.
simple projects for beginners, such as sound sensors and traffic light simulations.
Peer support and community conversations.
Exploring Arduino: Tools and Techniques for Engineering Wizardry (LinkedIn Learning)
This course delves deeply into Arduino programming and hardware integration, drawing inspiration from Jeremy Blum's well-known book. It is intended to provide you with the skills and resources you need to produce complex projects.
Key Highlights:
advice on creating unique circuits.
combining displays, motors, and sensors.
Code optimization and debugging best practices.
Arduino Programming and Hardware Fundamentals with Hackster (EdX)
This course, which is being offered in partnership with Hackster.io, covers the basics of Arduino hardware and programming. You may experiment with real-world applications because it is project-based.
Key Highlights:
Course materials are freely accessible (certification is optional).
extensive robotics and Internet of Things projects.
interaction with teachers and other students in the community.
Arduino is a great place to start if you want to construct a robot, make a smart home gadget, or just pick up a new skill. The aforementioned courses accommodate a variety of learning preferences and speeds, so every novice can discover the ideal fit. Select a course, acquire an Arduino starter kit, and set out on an exciting adventure into programming and electronics!
To know more, click here.
2 notes
·
View notes
Text
Empowering Young Minds: NYRA Academy's Innovative Approach to Kids' Coding Education
In today's rapidly evolving digital landscape, the ability to code has become a fundamental skill for success. Recognizing the importance of nurturing this skill from a young age, NYRA Academy proudly offers a diverse range of coding and robotics programs tailored specifically for children and youths.
At NYRA Academy, we understand that traditional coding courses may not always capture the attention and imagination of young learners. That's why we've developed engaging and interactive Kids Coding Courses designed to make learning fun and accessible for all skill levels. From Scratch Programming for Kids to Children's Robotics Classes, our programs cater to the diverse interests and learning styles of our students.
Our commitment to providing quality youth coding education is evident in our Scratch Coding Certificate program. Upon completion, students receive a tangible recognition of their achievements, motivating them to further explore the exciting world of coding. With a focus on hands-on learning and creative problem-solving, our Kid-Friendly Coding Training ensures that every child feels empowered to unleash their potential in the digital realm.
One of the highlights of our curriculum is our Junior Robotics Workshops, where young enthusiasts delve into the fascinating realm of robotics, learning to build and program their own robots. Through interactive projects and collaborative activities, students develop critical thinking and teamwork skills essential for success in today's tech-driven world.
Programming with Scratch for Children opens the door to endless possibilities as kids learn to create interactive stories, animations, and games. Our expert instructors guide students through every step of the process, fostering a passion for coding that extends beyond the classroom.
For those interested in exploring the creative side of coding, our courses in Animation and Game Design for Kids provide a platform for budding artists and storytellers to bring their ideas to life. Through hands-on projects, students learn the fundamentals of design and animation, gaining valuable skills that can be applied across various digital platforms.
NYRA Academy also offers Coding Short Courses specifically tailored for students aged 9 to 15, providing a comprehensive introduction to coding concepts in a condensed format. Whether your child is just beginning their coding journey or looking to expand their skills, our Beginner Coding Lessons for Youngsters provide a supportive and nurturing environment for growth and exploration.
At NYRA Academy, we believe that every child has the potential to become a coding champion. With our innovative approach to kids' coding education, we strive to inspire the next generation of digital innovators, equipping them with the skills and confidence to thrive in an ever-changing world. Join us on this exciting journey of discovery and creativity at NYRA Academy today!
#Kids coding courses#Robotics for kids#Scratch Jr courses#Children's programming classes#Coding for kids age 5-8#Certificate in Scratch Visual Coding#Scratch programming for kids#Children's robotics classes#nyra academy singapore#robotics course singapore#robotics classes for teenages
0 notes
Note
do you have any advice for finding an entry level compsci job? I'm still working on my BS and my non- job related experience hasn't been enough 😕
(not picky about any specific area)
Hi!
So I assume the US, right? (I'm European and our market is different here).
If I were a student here is how I would do it:
Create a resume and really pump your soft skills like team work and project management;
If your university offers them I'd join a club of an area of your interest such as coding, robotics, hacking... I know it feels like a waste of time, but it's still experience, regardless of the result (you don't have to win any competition to show your skills, counterintuitive I know), you will be able to show that you successfully dealt with a complicated project. That's a thing that when I was doing my rounds of interview were highly considered. You can always learn this or that language of programming but they already want a team player and one that's not afraid to take the reins when needed. If your university doesn't offer them there are online teams (or you can set up one by yourself) that do the same thing. For example I do a lot of "capture the flags", hacking challenges. They are a fun, challenging way to learn something, network with others and show how good you are.
A lot of companies (at least mine and few others in Europe did!) have these paid internships where they will teach you a job. This is a good way to get a foot in the door in cybersecurity since a lot of time even a compsci degree won't teach you anything about the subject. And training an analyst from scratch is extremely expensive, so you also have leverage for negotiating once your internship is over;
Consider taking a comptia certification! I recommend them for beginners because they are relatively cheap and are widely recognised. Comptia A+ is a good addition to a student's resume. The "three basics" comptia certifications are: A+ (for general IT), network+ and security+. They are ~300$/each.
I think I've covered most of it. You could also do a portfolio if coding is your thing, but I don't know anything about it.
Also I always suggest sending a resume if you hit 70% of what's requested, not 100%.
Plus! There are few professional associations that can help you locally! In Europe we have the Women4Cyber initiative. They will give you training, consultations etc about your career. I unfortunately don't know if there is an American one.
I hope this helps!
11 notes
·
View notes
Text
Top Machine Learning Programs in London for International Students in 2025
In today’s data-driven world, machine learning has become the backbone of innovations across industries—from healthcare and finance to robotics and autonomous systems. As a result, aspiring data scientists, software engineers, and technology enthusiasts are increasingly looking to upskill through reputable programs. If you're an international student seeking to pursue a Machine Learning course in London, 2025 offers more opportunities than ever before.
London, known as one of the world's leading hubs for technology and innovation, provides the perfect ecosystem to learn, experiment, and grow within the AI and machine learning space. With its multicultural environment, access to cutting-edge research, and thriving tech industry, it’s no surprise that thousands of students globally choose London for their AI and machine learning education.
In this blog, we’ll explore why London is a prime destination for international students, what to expect from top-tier programs, and how you can get started on your journey with the right institution.
Why Choose a Machine Learning Course in London?
International students choose London for a reason. The city combines academic excellence with vibrant industry exposure, making it ideal for both learning and launching your career.
1. Academic Excellence
London is home to some of the world’s most respected academic institutions and training centers. A Machine Learning course in London offers globally recognized certifications, industry-aligned curriculum, and access to the latest technologies and tools in AI and data science.
2. Global Tech Hub
London has established itself as a global technology and fintech center. It is filled with AI startups, enterprise R&D centers, and innovation labs, providing students access to internships, hackathons, and real-world exposure.
3. Cultural Diversity
As one of the most multicultural cities in the world, London is welcoming to international students. You’ll find peers from all corners of the globe, fostering collaboration and cross-cultural learning experiences.
4. Career Opportunities
Post-course placement opportunities are abundant. Graduates from a Machine Learning course in London often land roles in companies specializing in data science, AI solutions, machine learning platforms, and research-focused startups.
What to Expect from a Machine Learning Course in London?
Before enrolling, international students should be aware of what’s included in a comprehensive machine learning course. The ideal program covers both theoretical foundations and practical skills, with a focus on current industry applications.
Core Topics Typically Covered:
Supervised and Unsupervised Learning
Deep Learning and Neural Networks
Natural Language Processing (NLP)
Computer Vision
Reinforcement Learning
Data Preprocessing and Feature Engineering
Model Evaluation and Hyperparameter Tuning
Python Programming and Libraries (NumPy, Pandas, Scikit-learn, TensorFlow, PyTorch)
Tools and Platforms:
Python for machine learning development
Jupyter Notebooks for collaborative coding
TensorFlow and Keras for deep learning
Tableau or Power BI for data visualization
AWS, GCP, or Azure for deploying machine learning models
In 2025, London-based machine learning programs are designed to prepare students not just to build models, but also to deploy them, evaluate their impact, and understand ethical implications.
Boston Institute of Analytics – Machine Learning & AI Certification Program
The Boston Institute of Analytics offers a globally recognized certification in Machine Learning and Artificial Intelligence, specially curated for international students aiming to break into the tech industry or enhance their existing careers.
Why Choose BIA’s Machine Learning Course in London?
Here’s what sets it apart:
Global Recognition: The certification is respected across industries and geographies, giving students a competitive advantage in job markets worldwide.
Industry-Focused Curriculum: Unlike academic programs that are often theory-heavy, BIA focuses on real-world application. Students learn to build ML models that solve practical business problems.
Hands-on Training: With an emphasis on experiential learning, the course includes multiple projects, assignments, and case studies from domains like healthcare, finance, marketing, and e-commerce.
Expert Faculty: Classes are led by industry practitioners with years of experience in machine learning and data science, providing students with practical insights beyond textbooks.
Flexible Learning Options: BIA offers in-person training at its London campus and also provides hybrid or online formats to accommodate global learners.
Career Support: Resume building sessions, mock interviews, mentorship, and placement assistance are integral parts of the program.
Program Highlights:
Duration: 4 to 6 months
Mode: In-person (London Campus), Hybrid, or Online
Tools Covered: Python, Scikit-learn, TensorFlow, PyTorch, NLP toolkits
Certification: Globally recognized Machine Learning & AI Certificate
Eligibility: Open to students and professionals from all academic backgrounds
Ideal For:
International students from engineering, business, or mathematics backgrounds
Early-career professionals aiming for a transition to AI/ML roles
Entrepreneurs and analysts wanting to harness ML for decision-making
Graduates looking to improve employability and job-readiness
Benefits of Studying at Boston Institute of Analytics in London
1. Strategic Location
Located in the heart of London, BIA gives students access to a thriving network of AI meetups, startup incubators, and innovation forums. You’re not just learning in the classroom—you’re learning within the tech ecosystem.
2. Student-Centered Approach
Class sizes are kept small to ensure personalized attention. International students receive support for visa guidance, accommodation tips, and local job placement assistance.
3. Real-World Capstone Projects
Students complete a final capstone project applying the machine learning skills they’ve learned to solve a real business challenge. These projects serve as strong portfolio pieces for future employers.
4. Job Readiness by Graduation
With built-in modules for soft skill development, mock technical interviews, and resume workshops, students are prepared not only to build models but also to communicate their value effectively in the job market.
Career Outcomes After Completing a Machine Learning Course in London
The job market for machine learning professionals in London is robust and rapidly growing. After completing your certification or diploma, you’ll be well-equipped for roles such as:
Machine Learning Engineer
Data Scientist
AI Analyst
Data Engineer
NLP Specialist
Computer Vision Developer
AI Product Manager
Top industries hiring in London include finance, e-commerce, pharmaceuticals, automotive, insurance, and retail.
Salary expectations are also strong. Entry-level roles typically start between £40,000–£55,000 annually, while experienced professionals can earn upwards of £80,000, depending on the company and specialization.
Final Thoughts
Choosing a Machine Learning course in London is one of the smartest moves an international student can make in 2025. The city offers the perfect blend of academic rigor, practical experience, and career opportunities in the global AI ecosystem.
Among the top choices available, the Boston Institute of Analytics stands out for its industry-driven approach, flexible learning formats, expert faculty, and personalized career support. Whether you're a recent graduate, a working professional, or someone exploring a career shift into data science, BIA’s certification program will equip you with the knowledge and skills to succeed in the machine learning domain.
With London as your launchpad and BIA as your training ground, your journey into the future of AI begins with the right foundation. Get ready to learn, build, and innovate.
#Best Data Science Courses in London#Artificial Intelligence Course in London#Data Scientist Course in London#Machine Learning Course in London
0 notes
Text
UiPath Automation Developer Associate v1 UiPath-ADAv1 Prep Guide 2025
Achieving the UiPath Certified Professional – Automation Developer Associate (ADAv1) credential is a powerful statement in today’s robotic process automation (RPA) world. It signifies you can design and build effective automation workflows using UiPath Studio, Robots, and Orchestrator, and contribute valuably within RPA teams. As a foundational credential, ADAv1 opens doors to roles like Solution Architect, Automation Architect, and Advanced Developer.
To guide you on this path, Cert007’s UiPath Automation Developer Associate v1 UiPath-ADAv1 Prep Guide 2025 delivers the most up-to-date structure and content for the ADAv1 exam—arming you with clear study strategies and hands-on practices essential for success.
What Is the UiPath Automation Developer Associate (UiPath-ADAv1) Certification?
This entry-level certification is designed to validate your ability to design, build, and deploy simple automation solutions using key UiPath tools like UiPath Studio, Robots, and Orchestrator. It also shows that you can function effectively within a team delivering larger automation projects.
Successfully passing this exam sets the foundation for advanced roles like:
Advanced Automation Developer
Solution Architect
Automation Architect
Who Should Take the UiPath-ADAv1 Exam? Ideal Candidates and Requirements
The UiPath-ADAv1 exam is suitable for:
RPA beginners who have completed foundational UiPath training through UiPath Academy or certified partners.
Aspiring automation developers with 3–6 months of hands-on UiPath experience.
The Minimally Qualified Candidate (MQC) is someone who understands basic RPA principles and has practical experience working on simple automation tasks.
UiPath-ADAv1 Exam Overview: Format, Duration, and Key Details
Here’s a quick summary of the exam structure and key information:CategoryDetailsExam Code UiPath-ADAv1 Certification UiPath Automation Developer Associate v1 Track UiPath Certified Professional - Developer Duration 90 Minutes Passing Score 70% Exam Fee $150 USD Validity 3 Years Prerequisites None officially, but hands-on experience is advised
Complete List of Topics Covered in the UiPath-ADAv1 Exam
The UiPath-ADAv1 exam tests your knowledge across the following domains:
Business Knowledge
Platform Knowledge
UiPath Studio Interface
Variables and Arguments
Control Flow in Workflows
Debugging and Troubleshooting
Exception Handling Techniques
Activity Logging and Monitoring
UI Automation Basics
Object Repository Management
Excel Automation Tasks
Email and PDF Automation
Data Manipulation in Workflows
Version Control (e.g., Git Integration)
Workflow Analyzer Usage
RPA Testing Techniques
Orchestrator Functionalities
Integration Service
Why Cert007 Offers the Best UiPath-ADAv1 Exam Prep Materials
Preparing for a certification like UiPath-ADAv1 requires precise and targeted study materials. That’s where Cert007’s UiPath-ADAv1 Prep Guide comes in. It provides an up-to-date, comprehensive package tailored to cover everything you need to pass with confidence.
✅ Key Features of Cert007 UiPath-ADAv1 Prep Guide:
Updated and Verified Exam Questions
Realistic Mock Exams in PDF and Software Formats
Detailed Explanations for Deeper Understanding
Covers All Latest UiPath-ADAv1 Exam Objectives
Suitable for Self-Study or Team-Based Learning
Final Thoughts: Boost Your RPA Career with UiPath Certification and Cert007 Support
Earning the UiPath Automation Developer Associate v1 Certification not only validates your skills but also opens doors to exciting opportunities in the automation industry. With comprehensive preparation and dedicated practice using the UiPath-ADAv1 Prep Guide from Cert007, you'll be well on your way to achieving your RPA career goals.
Start your preparation today with the trusted UiPath-ADAv1 Prep Guide from Cert007 – your roadmap to RPA success!
0 notes
Text
Which Is the Best Cambridge IGCSE School in Mumbai for Your Child?
Choosing an international school in Mumbai is a big decision. With many options available, finding the right one that aligns with global standards and nurtures your child’s growth is crucial.
If you're searching for a Cambridge Board School in Mumbai or want to explore IGCSE curriculum schools, this guide will help you make an informed decision — and explain why Podar International School is one of the best choices today.

What is the Cambridge IGCSE Curriculum?
The IGCSE (International General Certificate of Secondary Education) is a globally recognised programme developed by Cambridge International Education, offering flexible subject choices, practical learning, and strong academic foundations.
Here’s why the Cambridge Board is preferred by many Indian parents:
Recognised in over 140 countries
Encourages critical thinking and independent learning
Ideal preparation for A Levels or IB
Accepted by Indian and international universities
Why Mumbai Parents Choose Cambridge International Schools
Mumbai, as a global city, is home to numerous reputed international schools. Here's what makes the Cambridge IGCSE schools in Mumbai popular:
Globally respected academic structure
Excellent track record in board exam results
Pathway to top global universities
Modern teaching techniques and practical focus
Experienced, internationally trained faculty
But not all Cambridge schools are equal in quality and outcomes.

Podar International School – A Top Cambridge IGCSE School in Mumbai
🔗 Explore Curriculum 🔗 Visit Main Website
Podar International School is among the most respected Cambridge Board Schools in Mumbai, offering IGCSE, A Levels, and other international programmes under one trusted name.
What Makes Podar Stand Out?
Authorised Cambridge International Centre
Expert teachers trained in IGCSE methodologies
Tech-enabled smart classrooms
Focus on global awareness with Indian values
Practical labs, co-curricular clubs & innovation hubs
University admission counselling for Indian & foreign universities
With a strong legacy and forward-thinking environment, Podar ensures your child receives a truly world-class education.
IGCSE vs Other Boards: Why It Matters
Feature IGCSE (Cambridge) Traditional Indian Boards Learning Approach Practical, student-centred Theory-heavy, teacher-led Assessment Style Written + coursework Mostly written exams Global Recognition Very High: Limited to specific countries Subject Flexibility HighLimited Ideal for global careers, higher studies National entrance-based focus
Podar’s Cambridge IGCSE curriculum gives your child a competitive edge—especially if they plan to study abroad or take up global careers.
What Parents Say About Podar
"We chose Podar for the IGCSE programme, and it has been a great decision. The teachers are very supportive, and the curriculum is balanced." — Mrs Mehta, Parent of Grade 9 IGCSE student
"Podar gives the right mix of discipline, creativity, and global education. "My son is now pursuing his degree in the UK, thanks to their guidance." — Mr Patel, A Level Parent
Beyond Academics: Life at Podar
Podar doesn’t just focus on exams. It helps children:
Build confidence
Develop public speaking & debate skills
Engage in robotics, art, sports, and coding
Learn time management and leadership
Explore creativity with interdisciplinary projects
This holistic focus makes Podar one of the most well-rounded international schools in Mumbai.

Podar Students Shine Worldwide
Thanks to IGCSE and Cambridge A Levels, Podar students get placed at top institutions like:
University of Toronto
University of Cambridge
King’s College London
University of Sydney
Ashoka University (India)
IITs (through competitive entrance routes)
Podar supports students with college counselling, entrance prep, and profile building.
Still Googling "Best IGCSE School Near Me"?
If you're searching online for:
Cambridge Board School in Mumbai
IGCSE Schools in Mumbai
Best International Schools in Mumbai
Cambridge Curriculum Schools Mumbai
You’ve already found the right direction — Podar International School.
Their academic structure, skilled faculty, and child-first approach make them a trusted name for thousands of families.
Final Thoughts
In a city like Mumbai, quality education must go beyond textbooks. Your child deserves a school that nurtures global thinking, confidence, and a love for learning.
If you're serious about giving your child an international edge, a Cambridge IGCSE education at Podar International School is a wise choice.
👉 Start here to learn more about admissions. 👉 Explore curriculum options in detail.
#International Schools in Mumbai#Schools In Santacruz#Cambridge Board Schools in Mumbai#A Level Schools in Mumbai#Best A Level Schools in Mumbai
0 notes
Text
Understanding Mechatronics: A Beginner’s Guide for Freshers
If you’ve just stepped into the world of engineering or are considering which specialization to pursue, you might have come across the term Mechatronics. It sounds futuristic—and honestly, it is. But what exactly is it? Is it mechanical? Is it electronics? Or is it something else altogether?
Let’s break it down and make it simple for you.
What Is Mechatronics?
Mechatronics is an interdisciplinary field that blends mechanical engineering, electronics, computer science, and control engineering. It’s all about designing and creating smarter machines—systems that not only move or perform tasks but also think and respond intelligently.
Think of things like self-driving cars, robotic arms in factories, automated coffee machines, or even drones that maintain stability mid-air. All of these rely on the principles of mechatronics.
This discipline is becoming essential in today’s automation-driven world, especially with the rise of Industry 4.0, where machines communicate with each other to optimize performance without human input.
Why Should You Care as a Fresher?
In the early stages of your engineering journey, it's important to understand where the future is headed. Mechatronics is one of those areas that’s not just growing—it’s exploding.
As a fresher, you might still be figuring out what excites you most. But if you're someone who enjoys blending creativity with technology—imagine coding a program and then watching it control a real robot—this field will likely click with you.
Also, if you eventually want to work in automation, AI-driven systems, or robotics, mechatronics offers you the foundation and flexibility to go in multiple directions.
What Will You Learn in Mechatronics?
Typically, if you pursue mechatronics as a core subject or even as an elective, you’ll dive into areas like:
Sensors and Actuators: Devices that help machines sense their environment and act accordingly.
Microcontrollers and Embedded Systems: The brains of most modern electronic machines.
Mechanical Design: Basics of gears, motors, and structures that move.
Control Systems: How to ensure a robot does what it’s supposed to—no more, no less.
Programming: Often in C/C++ or Python to control the devices.
You may also get your hands on software like MATLAB, Simulink, or Arduino IDE early on.
How to Get Started in College
You don't have to wait till the third year to explore mechatronics. In fact, some colleges start offering related workshops and certifications right from the first year. If you're studying in a place where the labs are well-equipped and faculty are research-active, you'll probably get the chance to work on actual robots or automation systems before you graduate.
During a visit to a lab at NMIET Bhubaneswar, I noticed students working on automated vehicle prototypes that used sensors for obstacle detection. It struck me how mechatronics isn’t just a theoretical subject in such institutions—it’s hands-on and real.
Career Scope: Where Can Mechatronics Take You?
Mechatronics engineers are highly valued in sectors like:
Robotics and Automation
Aerospace
Automobile Manufacturing
Medical Equipment Development
Home Automation and Smart Devices
With increasing reliance on smart systems and AI-driven hardware, companies are actively seeking engineers who can work across domains. This is where mechatronics gives you a massive edge.
Even core mechanical or electrical engineers are now advised to pick up basic knowledge of microcontrollers or coding. So, if you're already in a college that encourages learning beyond your core, you're in the right place.
What Makes a Good College for Mechatronics Learning?
Let’s be honest—your learning environment plays a big role. Access to automation labs, exposure to industry tools, faculty who encourage innovation, and the chance to work on real-world projects—these are the things that matter most.
Some of the top engineering colleges in Odisha are already introducing mechatronics modules in mechanical and electronics streams. The goal is to create engineers who can build, code, and innovate.
It’s always a good idea to look into whether the institute collaborates with industries for internships and whether they have tie-ups for campus placements with companies involved in automation or robotics.
Final Thoughts: A Future-Proof Path
Mechatronics is not just another subject—it’s a mindset. It teaches you to look at machines not just as static components, but as intelligent systems that interact with the world.
As a fresher, you don’t need to master it all at once. Start with basic projects—maybe build a line-follower robot or an automatic light system. Join clubs, take up online certifications, and most importantly, stay curious.
If you’re in an environment where creativity and cross-disciplinary learning are encouraged—like the one I saw at NMIET—you’re already ahead of the curve.
So, if you’re dreaming of working on robots, smart devices, or even futuristic innovations we haven’t seen yet—mechatronics might just be the path you’ve been looking for.
#bhubaneswar b tech colleges#college of engineering bhubaneswar#best engineering colleges in orissa#best engineering colleges in bhubaneswar#best private engineering colleges in odisha#best engineering colleges in odisha
0 notes