#computer monitoring software for parents
Explore tagged Tumblr posts
Text
Discover the top computer monitoring software for parents and businesses! Keep track of online activities and boost productivity. Read more: https://icttone.com/best-computer-monitoring-software/
#computer monitoring software#parental control app#activity monitoring#employee monitoring software#activity check
1 note
·
View note
Text
Computer Monitoring Software for Windows and MAC | Mobistealth
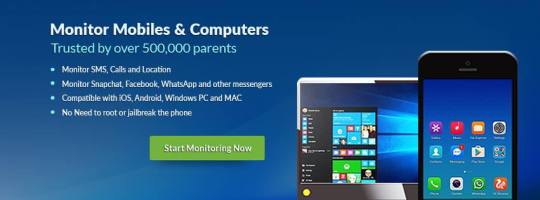
Mobistealth Software to Monitor PC provides you with a very cost effective and easy-to-use software for monitoring activities of your kid's computers. Every feature in the Mobistealth is designed to provide you with the relevant data you need to stay informed and in control. From the moment the activity monitoring software is installed on the computer you want to track, it begins recording and relaying information directly to your Mobistealth user account that you can access 24/7 from anywhere on the planet.
For More Information Visit Our Website:
https://www.mobistealth.com/pc-monitoring-software
#Parental-Control-Computer#Computer-Parental-Control#PC-Parental-Control#Parental-Control-PC#PC-Monitoring-Software#Mobistealth#Computer-Monitoring-Software-for-Windows#Computer-Monitoring-Software-for-MAC
0 notes
Note
The other two family abolitionist anons brought me back to something that's on my mind a lot: I'm eternally grateful to my parents for letting me have unrestricted internet access, not snooping on what I did online, and letting me watch/read/play whatever I felt like. I truly believe having this freedom had a positive impact on my development and think I'd have turned out much worse without it. I can't relate when people talk about how they're irreperably traumatized from doing these things as a child, and how the Internet and media designed for adults damages children.
My parents absolutely had their flaws and childhood as a whole isn't something I look back on with rose-tinted glasses, but I think they did well in terms of acknowledging that I was a whole person and respecting my desire for autonomy. I think I'd be doing worse as an adult without that, and I doubt I'd have a decent relationship with them if they had treated me as society says children should be. I've always wondered if there's anyone out there who has the same experience as me.
ive complained about this before but yea i did not have unsurveilled access to the internet until i was 17 and it was fucking miserable lol. like i am sympathetic to ppl who saw some shit they didn't want to see but wow it actually sucks so much to have zero ability to even like google something embarrassing without someone else knowing, let alone chatlogs and emails monitored and random browsing watched over ur shoulder and stuff. the whole fantasy is that if you cut off a child's connection to Online then you can control them better, often phrased as protecting them from external forces. like it's really evil not to mention dangerous in the way that anything that increases parental control & access is. i was only lucky i got the fuck out of there like a year or two before my parents figured out real-time location tracking software & sms content access thru their isp but wow i would take a hundred million billion porn jumpscares or beheading videos on the open internet over being surveilled like that. literally like core memories hunched over the corner computer in the public library lmfao
90 notes
·
View notes
Text
Why is this Canadian university scared of you seeing its Privacy Impact Assessment?

I'm coming to DEFCON! On Aug 9, I'm emceeing the EFF POKER TOURNAMENT (noon at the Horseshoe Poker Room), and appearing on the BRICKED AND ABANDONED panel (5PM, LVCC - L1 - HW1–11–01). On Aug 10, I'm giving a keynote called "DISENSHITTIFY OR DIE! How hackers can seize the means of computation and build a new, good internet that is hardened against our asshole bosses' insatiable horniness for enshittification" (noon, LVCC - L1 - HW1–11–01).

Barbra Streisand is famous for many things: her exciting performances on the big screen, the small screen, and the stage; her Grammy-winning career as a musician (she's a certified EGOT!); and for all the times she's had to correct people who've added an extra vowel to the spelling of her first name (I can relate!).
But a thousand years from now, her legacy is likely to be linguistic, rather than artistic. The "Streisand Effect" – coined by Mike Masnick – describes what happens when someone tries to suppress a piece of information, only to have that act of attempted suppression backfire by inciting vastly more interest in the subject:
https://en.wikipedia.org/wiki/Streisand_effect
The term dates to 2003, when Streisand sued the website Pictopia and its proprietors for $50m for reproducing an image from the publicly available California Coastal Records Project (which produces a timeseries of photos of the California coastline in order to track coastal erosion). The image ("Image 3850") incidentally captured the roofs of Streisand's rather amazing coastal compound, which upset Streisand.
But here's the thing: before Streisand's lawsuit, Image 3850 had only been viewed six times. After she filed the case, another 420,000 people downloaded that image. Not only did Streisand lose her suit (disastrously so – she was ordered to pay the defendants' lawyers $177,000 in fees), but she catastrophically failed in her goal of keeping this boring, obscure photo from being seen:
https://en.wikipedia.org/wiki/Streisand_effect
Streisand has since called the suit "a mistake." On the one hand, that is very obviously true, but on the other hand, it's still admirable, given how many other failed litigants went to their graves insisting that their foolish and expensive legal gambit was, in fact, very smart and we are all very stupid for failing to understand that.
Which brings me to Ian Linkletter and the Canadian Privacy Library. Linkletter is the librarian and founder of the nonprofit Canadian Privacy Library, a newish online library that collects and organizes privacy-related documents from Canadian public institutions. Linkletter kicked off the project with the goal of collecting the Privacy Impact Assessments from every public university in Canada, starting in his home province of BC.
These PIAs are a legal requirement whenever a public university procures a piece of software, and they're no joke. Ed-tech vendors are pretty goddamned cavalier when it comes to student privacy, as Linkletter knows well. Back in 2020, Linkletter was an ed-tech specialist for the University of British Columbia, where he was called upon to assess Proctorio, a "remote invigilation" tool that monitored remote students while they sat exams.
This is a nightmare category of software, a mix of high-tech phrenology (vendors claim that they can tell when students are cheating by using "AI" to analyze their faces); arrogant techno-sadism (vendors requires students – including those sharing one-room apartments with "essential worker" parents on night shifts who sleep during the day – to pan their cameras around to prove that they are alone); digital racism (products are so bad at recognizing Black faces that some students have had to sit exams with multiple task-lights shining directly onto their faces); and bullshit (vendors routinely lie about their tools' capabilities and efficacy).
Worst: remote invigilation is grounded in the pedagogically bankrupt idea that learning is best (or even plausibly) assessed through high-stakes testing. The kind of person who wants to use these tools generally has no idea how learning works and thinks of students as presumptively guilty cheats. They monitor test-taking students in realtime, and have been known to jiggle test-takers' cursors impatiently when students think too long about their answers. Remote invigilation also captures the eye-movements of test-takers, flagging people who look away from the screen while thinking for potential cheating. No wonder that many students who sit exams under these conditions find themselves so anxious that they vomit or experience diarrhea, carefully staring directly into the camera as they shit themselves or vomit down their shirts, lest they be penalized for looking away or visiting the toilet.
Linkletter quickly realized that Proctorio is a worst-in-class example of a dreadful category. The public-facing materials the company provided about its products were flatly contradicted by the materials they provided to educators, where all the really nasty stuff was buried. The company – whose business exploded during the covid lockdowns – is helmed by CEO Mike Olsen, a nasty piece of work who once doxed a child who criticized him in an online forum:
https://pluralistic.net/2020/07/01/bossware/#moral-exemplar
Proctorio's products are shrouded in secrecy. In 2020, for reasons never explained, all the (terrible, outraged) reviews of its browser plugin disappeared from the Chrome store:
https://pluralistic.net/2021/09/04/hypervigilance/#radical-transparency
Linkletter tweeted his alarming findings, publishing links to the unlisted, but publicly available Youtube videos where Proctorio explained how its products really worked. Proctorio then sued Linkletter, for copyright infringement.
Proctorio's argument is that by linking to materials that they published on Youtube with permissions that let anyone with the link see them, Linkletter infringed upon their copyright. When Linkletter discovered that these videos already had publicly available links, indexed by Google, in the documentation produced by other Proctorio customers for students and teachers, Proctorio doubled down and argued that by collecting these publicly available links to publicly available videos, Linkletter had still somehow infringed on their copyright.
Luckily for Linkletter, BC has an anti-SLAPP law that is supposed to protect whistleblowers facing legal retaliation for publishing protected speech related to matters of public interest (like whether BC's flagship university has bought a defective and harmful product that its students will be forced to use). Unluckily for Linkletter, the law is brand new, lacks jurisprudence, and the courts have decided that he can't use a SLAPP defense and his case must go to trial:
https://pluralistic.net/2023/04/20/links-arent-performances/#free-ian-linkletter
Linkletter could have let that experience frighten him away from the kind of principled advocacy that riles up deep-pocketed, thin-skinned bullies. Instead, he doubled down, founding the Canadian Privacy Library, with the goal of using Freedom of Information requests to catalog all of Canada's post-secondary institutions' privacy assessments. Given how many bodies he found buried in Proctorio's back yard, this feels like the kind of thing that should be made more visible to Canadians.
There are 25 public universities in BC, and Linkletter FOI'ed them all. Eleven provided their PIAs. Eight sent him an estimate of what it would cost them (and thus what they would charge) to assemble these docs for him. Six requested extensions.
One of them threatened to sue.
Langara College is a 19,000-student spinout of Vancouver Community College whose motto is Eruditio Libertas Est ("Knowledge is Freedom"). Linkletter got their 2019 PIA for Microsoft's Office 365 when he FOI'ed the Nicola Valley Institute of Technology (universities often recycle one another's privacy impact assessments, which is fine).
That's where the trouble started. In June, Langara sent Linkletter a letter demanding that he remove their Office 365 PIA; the letter CC'ed two partners in a law firm, and accused Linkletter of copyright infringement. But that's not how copyright – or public records – work. As Linkletter writes, the PIA is "a public record lawfully obtained through an FOI request" – it is neither exempted from disclosure, nor is it confidential:
https://www.privacylibrary.ca/legal-threat/
Langara claims that in making their mandatory Privacy Impact Assessment for Office 365 available, Linkletter has exposed them to "heightened risks of data breaches and privacy incidents," they provided no evidence to support this assertion.
I think they're full of shit, but you don't have to take my word for it. After initially removing the PIA, Linkletter restored it, and you can read it for yourself:
https://www.privacylibrary.ca/langara-college-privacy-impact-assessments/
I read it. It is pretty goddamned anodyne – about as exciting as looking at the roof of Barbra Streisand's mansion.
Sometimes, where there's smoke, there's only Streisand – a person who has foolishly decided to use the law to bully a weaker stranger out of disclosing some innocuous and publicly available fact about themselves. But sometimes, where there's smoke, there's fire. A lot of people who read my work are much more familiar with ed-tech, privacy, and pedagogy than I am. If that's you, maybe you want to peruse the Langara PIA to see if they are hiding something because they're exposing their students to privacy risks and don't want that fact to get out.
There are plenty of potential privacy risks in Office 365! The cloud version of Microsoft Office contains a "bossware" mode that allows bosses to monitor their workers' keystrokes for spelling, content, and accuracy, and produce neat charts of which employees are least "productive." The joke's on the boss, though: Office 365 also has a tool that lets you compare your department's usage of Office 365 to your competitors, which is another way of saying that Microsoft is gathering your trade secrets and handing it out to your direct competitors:
https://pluralistic.net/2021/02/24/gwb-rumsfeld-monsters/#bossware
So, yeah, there are lots of "features" in Office 365 that could give rise to privacy threats when it is used at a university. One hopes that Langara correctly assessed these risks and accounted for them in its PIA, which would mean that they are bullying Linkletter out of reflex, rather than to cover up wrongdoing. But there's only one way to find out: go through the doc that Linkletter has restored to public view.
Linkletter has excellent pro bono representation from Norton Rose Fulbright, a large and powerful law-firm that is handling his Proctorio case. Linkletter writes, "they have put this public college on notice that any proceeding is liable to be dismissed pursuant to the Protection of Public Participation Act, BC’s anti-SLAPP legislation."
Langara has now found themselves at the bottom of a hole, and if they're smart, they'll stop digging.

Support me this summer on the Clarion Write-A-Thon and help raise money for the Clarion Science Fiction and Fantasy Writers' Workshop!

If you'd like an essay-formatted version of this post to read or share, here's a link to it on pluralistic.net, my surveillance-free, ad-free, tracker-free blog:
https://pluralistic.net/2024/08/01/eruditio-libertas-est/#streisand-v-linkletter

Image: Copyright (C) 2002 Kenneth & Gabrielle Adelman, California Coastal Records Project, www.californiacoastline.org (modified) https://en.wikipedia.org/wiki/File:Streisand_Estate.jpgbr>
CC BY-SA 3.0 https://creativecommons.org/licenses/by-sa/3.0/deed.en
--
Langara College (modified) https://langara.ca/
Fair use (parody) https://scholarship.law.ufl.edu/cgi/viewcontent.cgi?article=1104
Fair dealing (parody) https://papers.ssrn.com/sol3/papers.cfm?abstract_id=1468015
#pluralistic#streisand effect#privacy impact assessment#canada#ian linkletter#Canadian Privacy Library#canpoli#foi#pia#Langara College#libraries#glam#Freedom of Information and Protection of Privacy Act#fippa#slapp#anti-slapp#langara college#bullies
227 notes
·
View notes
Text
When the claims representative, whom I’ll call Steven, sat down at his computer around 7:15 A.M. last week, he had already been awake for an hour and a half. The morning routine for him and his family is best described as “fend for yourself,” he said. That day, he waited for his older son to shower before taking his turn; neither he nor his wife had time for breakfast. He had joined the Social Security Administration two decades ago, and came to specialize in one of its more complex and lesser-known functions: providing a form of welfare called Supplemental Security Income, or S.S.I., to people who are disabled or extremely poor. But the S.S.A. is so understaffed that Steven does a bit of everything. “My job is to be kind of like an octopus,” he said. The agency’s administrative budget had not kept up with its rising workload as more people aged into retirement. Now news outlets were reporting that President Donald Trump and Elon Musk, via Musk’s DOGE outfit, planned to fire up to half of the agency’s sixty-thousand-odd employees. (The S.S.A. later said that its goal was to lose seven thousand.) DOGE had also gained access to S.S.A. databases. “We don’t know how long we’ll be here,” Steven said. “Some people are really pissed. Others are sad and emotional. Others are making plans.” A couple days earlier, Trump had delivered a long self-congratulatory speech to Congress, in which he accused the S.S.A. of “shocking levels of incompetence and probable fraud.”
Steven lives in a Midwestern town near where he was born and raised, which means that he occasionally recognizes a relative or a family friend in a case file and has to recuse himself. Three days a week, he’s at a cubicle in a regional field office, one of twelve hundred across the U.S. The other two days, he works from home, at a plastic folding table in the corner of his bedroom. He was on the early shift. His laptop was propped up on a neon-green bin, the kind typically used to store Legos or crayons. It was flanked by two large monitors, creating a triptych. All around him were piles of kids’ clothes and books. Near his left foot was a tiny metal car; he had taped yellow notecards reading “clock,” “fan,” and “shelf” to a clock, fan, and shelf for the benefit of his youngest child, who was learning to read. Steven’s wife made drop-offs at kindergarten and day care, then came home. She has her own office setup downstairs.
The day officially started when Steven logged on to a dozen software programs. One had a blocky monochrome interface that looked like it was from the late nineties. Another was labelled “Workload Action Center,” in a light-brown, slanted font of a similar vintage. Steven kept a list of his passwords, which he had to routinely update, on a scrap of paper next to his keyboard. He scanned something called a “Tickle List” that highlighted urgent cases. His primary task was to conduct nonmedical “redetermination” interviews (code: “RZ”)—part of the S.S.A.’s process for insuring that current recipients are still eligible to receive benefits. More than seven million Americans of all ages count on S.S.I., and sixty-eight million seniors receive earned retirement payments. Social Security is the largest government program in the country and most recipients’ main source of income. It was envisioned by Frances Perkins during the Great Depression. “Redeterminations are the highest priority,” Steven said. “We should have three to five people on them at every office. Sometimes there’s only one.”
He put on a wireless headset that connected to his laptop and an online phone system. The first redetermination call was with a parent who was receiving S.S.I. on behalf of a disabled child. “Hi, this is Steven, from Social Security Administration,” he said. “I’m just calling to see if you’re able to do the redetermination appointment.” His stomach growled. The bottom-right corner of his center screen flickered with notifications. He stayed with the caller. Date of birth? Marriages? Job placements? He clicked “yes” and “no” bubbles and typed in numbers. He had much of the script memorized. “Any items held for potential value?” he asked. “Promissory notes, real property or business property, or ABLE accounts?” S.S.I. is allocated based on an applicant’s income, assets, family size, and other factors. It often takes a year, and the help of a lawyer, to get a decision. (Earlier in Steven’s career, the time frame had been three to six months.) If an application is rejected, the case can be appealed to an administrative-law judge, and the wait for those hearings is around two years.
“That was the last amount verified,” Steven continued. “Has that changed?” While waiting for the program to advance to the next screen, he glanced at e-mails on his rightmost monitor. There were more from headquarters and human resources and the employees’ union than usual. Since November, three S.S.A. commissioners or acting commissioners had come and gone: Martin O’Malley, Carolyn W. Colvin, and Michelle King. The guy in charge now was Leland Dudek, whom Trump had elevated from a middle-management role for his eagerness to help DOGE access S.S.A. files, a vast library of individual medical, housing, family, and financial records. Dudek announced plans to eliminate six out of ten regional headquarters; several directors left the agency. In an all-staff e-mail, Dudek wrote:
Criticism, contempt, stonewalling, and defensiveness are the four forces that can end any relationship and weaken any institution. . . .
Elections have consequences. . . .
Now, under President Trump, we follow established precedent: we serve at the pleasure and direction of the President. Only the Courts or Congress can intervene.
The latest e-mail from headquarters stated that, “effective today,” employees were prohibited from engaging in “Internet browsing” of “general news” or “sports” on “government-furnished equipment.”
Steven was almost done with the redetermination. Hard cases, like an overpayment that needed to be clawed back, could “make the conversation longer, vulgar.” This one was easy; the payments, of around a thousand dollars per month, would continue. “You will receive a summary statement regarding the information that we discussed,” he said. He moved on to a second call. This one, too, involved a young adult whose caretaker—in this case, a nonprofit organization—was the payee. “Hello. This is Steven from Social Security. How are you?” His cellphone buzzed. Since Trump’s reëlection, he had been in a prolific, darkly humorous group chat with fellow S.S.A. workers in the Midwest. He referred to them as his sisters and brothers. The incoming message was a link to a news story about the imminent closure of S.S.A. field offices in the area. One man in the chat, who voted Republican but had grown skeptical of Trump, wrote, “Fucking unbelievable. . . . This would devastate our agency’s ability to serve the public.”
Meanwhile, the redetermination call was getting tricky. A new source of income seemed to be complicating the calculation of resources. Steven put the nonprofit on hold and logged into Equifax. He walked across the room to grab a plastic bottle of water and took a swig. “I’m trying really not to go off the deep end,” he said. If his office closed, and the neighboring offices closed, many people would have no way of getting benefits. For one thing, applications for Social Security cards and certain forms of S.S.I. had to be submitted in person.
Steven worried about his own well-being, too. His kids were on his health insurance. He and his wife had to take care of his father. S.S.A.’s human-resources division had sent an e-mail titled “Organizational Restructuring—Availability of Voluntary Reassignment, Early Out Retirement, and Separation Incentive Payments to ALL ELIGIBLE EMPLOYEES—No Component or Position Exceptions,” which seemed to pressure workers to leave. “A lot of this stuff is intentionally degrading,” Steven said. “They’re trying to do whatever they can to get people to resign.” Recently, he and other field-office staff were told that their jobs were safe because they were “mission critical.” That was reassuring, but only “a little bit.”
When the Equifax search proved inconclusive, Steven told the nonprofit, “I’ll have to put this on the back burner for a bit until I can get some info.” All three of his screens were noisy. In Microsoft Teams, a supervisor was asking for updates on specific cases. Another window showed the names of people waiting in the lobby of the field office, in real time. He stared at a name in the queue. “This one, I’ve been playing phone tag with her,” Steven said. He opened a chat to alert a colleague at the office.
The work is surprisingly personal. A Social Security file contains a lot of intimate information. From a quick glance, Steven can tell where a recipient was born, what language they speak, whether they’d been involved in the child-welfare system, if they are married, whether that marriage had ended as a result of divorce or death. He has some colleagues whose “attitudes suck to high heaven,” caused by a mix of stress and a suspicion of the poor. “I love helping people,” he said. “You’re the first contact for them.”
Next, Steven had to get “on the phones.” Fielding random calls on the S.S.A. hotline isn’t technically part of his job, but he didn’t question the assignment. For several weeks, everyone had been required to help out. “Good morning. Social Security. This is Steven,” he said. “What is your Social Security number, please? All right, starting with your name and date of birth . . .” He wrapped up his first few calls rather quickly. He sent out a missing tax document, scheduled a father for an in-person appointment to get a Social Security card for his baby, and confirmed bank information for a recipient’s direct deposit. A fourth call, involving a lost check, was more complicated. He rubbed his forehead with his thumbs and forefingers.
Steven later received two mass e-mails. The first reminded all S.S.A. employees to send their “mandatory weekly assignment”—the “What Did You Do Last Week” e-mail, with five bullet points summarizing what they had worked on—directly to the government’s Office of Personnel Management, not to anyone in their actual agency. The second one was yet another plea for workers to quit or take early retirement. It warned that some who opted to remain in “non-mission critical positions” might be reassigned to S.S.A. call centers. No definition of “non-mission critical” was offered.
“I just keep wondering, How long can I be doing this?” Steven said. Many years before Trump and DOGE, there was a period when he could not sleep. “The job would cause me to wake up in the middle of the night,” he said. “You know how your brain can’t shut stuff off, or you’re just dreading going in the next day?” He was troubled by certain cases—a girl who had been abused in foster care, only to end up with a grandmother who stole her S.S.I. checks. He was also haunted by the need to reach case quotas, never explicitly stated but often implied. “Cutting corners happens in this industry, when representatives are trying to just get something off their list,” he said. “So then it’s like, ‘I got that done.’ But did you really help the person?” His latest sources of worry were a news article in which O’Malley, the former S.S.A. commissioner, predicted “system collapse and an interruption of benefits” within “thirty to ninety days” and an affidavit by a former agency official that described DOGE’s violation of privacy protocols and the likelihood of “critical errors that could upend SSA systems.”
Steven has never been a zealot for anything except his favorite football team, but now he believes that he and his co-workers are part of an “underground movement” to prevent the destruction of Social Security. Trump and Musk, and more conventional Republicans, talk obsessively about rooting out fraud at the S.S.A. Mistakes and overpayments do occur, but the agency’s inspector general recently found that less than one per cent of benefits distributed between 2015 and 2022 were improper. Steven believes that mass layoffs will result in vulnerable Americans not getting the money they’re entitled to. “We service people at their best and worst times,” he said. “People heading into retirement, surviving spouses, widows, widowers. It used to be we’d get complaints from the public. We’d start off a call by apologizing. ‘We’re understaffed!’ ” Now, he went on, “people are apologizing to us.” ♦
33 notes
·
View notes
Text
Numbers l Chapter Four

Pairing: Spencer Reid x Disabled OC
Content Warning: Talk of disability, stalking, light cussing
Word Count: 1.6k
Summary: Brooke already feels the effects of the work she'll be surrounded by.
Taglist: @ihatethecrowdsyouknowthat @just-call-me-by-yn @slowdownpal
A/n: Sorry it took a minute to get this chapter out! Life got a little busy. Also the banner sucks because it's my first attempt at making one 😭
Story:
Coffee wafted up my nose from the cup resting on my wheelchair tray. Penelope and I had the opportunity to take a break as Spencer and the rest of the team worked with the information we gathered for them so far. That was the nice thing about just being a technical analyst, once we followed our orders, we could let them handle the rest of the horrors.
Currently, Spencer was using Penelope’s- well, I guess now it’s our office, to come up with a geographical profile. He explained once they figured out where the unsub carries out his plans, they’d be making huge strides in the case. So now, a huge map was hanging up on the one wall that didn’t have a computer monitor, or software tower. Penelope suggested she and I get a cup of coffee while he works.
“So, Newbie, tell me everything I should know about you” She requests while leaning back against the break area counter with a beaming smile “Your hopes, your dreams, cute quirks, I want to know everything.”
My eyes grow wide, a little stunned by her boldness. Although I really shouldn’t be surprised, this girl adopted me within the first five minutes of knowing each other, and I can’t help but kind of love it. I let out a small awkward laugh “Well…” My voice trails off as I think “I grew up in Florida which is where my family still is.”
Besides getting a new job, moving hours away from my parents, aka, my soul caregivers was a big deal. Honestly from an early age I thought it wasn’t in the cards. I can’t bathe myself, let alone live on my own. I applied for this job in secret, knowing my mother would have a nervous breakdown over the idea of me moving out. I figured if I didn’t get the job, she wouldn’t have to know and I could save her the anxiety.
I did get the job though, which meant having to have a very nerve-racking conversation at the dining room table. You could say my mother wasn’t exactly thrilled when she found out I went behind her back, but my dad was there to be the level-headed one. He had the habit of being the rational one mediating between my mother and I. He used to say we butt heads just because she and I are so similar. I appreciated his positive outlook on things, but from my point of view, she had the tendency to suffocate me with her protection. Deep down I know she just wants what she feels like is best. It could be worse, she could just not care at all. That thought keeps me at bay for the most part.
After the dust settled, my parents helped me find an accessible apartment and a reliable caregiving program. “If I can’t be there with you, I’m gonna make damn sure whoever takes care of you knows what they’re doing.” Is what my mother said as we scrolled through different agencies.
“Florida!” Penelope gasped then frowned, her voice full of empathy “You must miss your folks with them living so far away.”
I smile softly with a sheepish shrug. “I mean, yeah- of course, I miss them at times but I feel like I needed the independence.” Penelope probably didn’t understand how literal I meant that, I didn’t want to unpack the trapped feeling of being stuck needing help with most daily things. The poor girl wasn’t my therapist.
Penelope smiled and nodded “Well good for you girl.”
My eyes flicker down to my cup of coffee. When I asked for one, I didn’t think it through all the way. The only way I’d be able to actually sip it is if someone held up the cup for me and I didn’t exactly want to turn my new coworkers into caregivers, so I just let the beverage get cold.
Suddenly I see Spencer come speed walking down the hall towards us with the giant map in hand.
“Uh oh… I think Wonder Boy stumbled upon something.” Penelope says before following him in suit over to the desks.
I quickly followed but made sure to keep my coffee steady so we didn’t have a mess on our hands.
Spencer moves items out of the way with the help of Penelope before laying the map out “I already called Hotch, but look at this…” He starts before connecting the dots on the map with a red marker “After looking at each woman’s residential location, I discovered something….” After a few more lines and curves, Spencer stands up straight and snaps the cap back on the marker “If you connect all of them, they outline an eardrum.”
My eyebrows pinch together as I look closely at the map. He was right. It’s not like I knew exactly what an eardrum looked like, but the drawing looked like something out of a human anatomy textbook. “What the hell…?” I whisper under my breath.
Penelope looked back and forth between the map and Spencer, horrified “What on earth could that possibly mean?”
Spencer sighs while looking back down at his own drawing “It means this unsub is more calculated and smart than we thought. Also it tells us the ear is somehow important for their fantasy, or compulsion.” He rolls up the map, avoiding our gaze “It also tells us they’ve been watching these women.”
That thought made a cold shiver run down my spine. It’s terrifying to think even when you feel like you’re safe in your own home, you’re not. Definitely making sure my door is locked tonight. I was already nervous living in a new town, and this didn’t help.
“Hotch suggested we pack it up here tonight.” Spencer explained, “He said they’ll work throughout the night on their end, and I think I might as well.”
Penelope and I nodded, both looking a little bit like we just saw a ghost.
Penelope was the first one to say “Ok, um… I’m going to go get my stuff.”
That left Spencer and I sitting in silence. He was busy making sure the map was rolled up nice and tight with edges lined up. I was busy in my head thinking about the trip to the bus stop I’m gonna have to take in the dark, now with the fear of potentially being watched. Not only was I a female, but I was a female who literally couldn’t fight back. If an unsub like this one was around, I’d be a perfect target. An unsub could easily disable my wheelchair somehow and just like that, I’d be at their mercy. Cool, first day at my dream job, and I’m probably already going to have nightmares.
“Are you ok?”
I jump a little and snap out of it to see Spencer looking at me with slight concern in his eyes. In the 30 seconds of me irrationally thinking of the worst case scenario, he pulled up a chair and began looking through the case file again.
“I-” I didn’t know what to say. I didn’t want him to think I was scared to go home where I didn’t have copious amounts of security besides a chain lock. After a few blinks, I end up giving him my best fake smile and shrug him off “O-Oh yeah, I was just thinking of what I should have for dinner tonight.” Note to self, if you ever commit a crime, don’t get caught because you suck at lying.
Spencer’s eyebrows narrow “Are you sure?” His face softens “You know, speakers who usually do not stutter may experience problems with fluency when they are nervous or feel pressured. Also when they lie.”
Just like that, my pea-sized brain was shown up by the genius. I let out the breath I was apparently holding and let out a subtle nervous giggle “I guess I’m a little nervous heading home in the dark.”
He looked at me confused again, more concerned this time “You’re not walking all the way home, are you?”
That’s when I let out a genuine laugh and shook my head “Just to the bus stop. It’s cheaper than an accessible cab.”
“Oooh…” He replied with raised eyebrows and nodded slowly, almost as if he was thinking of something. He leans back in his seat before looking at me again “Penelope could walk with you until you’re safely on the bus.”
“I hear myself being summoned.” Out of nowhere, Penelope returned with her familiar smile glowing on her face like it wasn’t wiped away less than five minutes ago. Her jacket and purse were just as colorful as the rest of her attire.
“Could you walk Brooke to the bus stop?” Spencer asked before I even had the chance to open my mouth. His tone felt oddly protective, like he didn’t care what my answer would be, he was going to make sure I felt comfortable about going home.
Normally I would be pissed about having the choice being taken away from me, but it was hard not to appreciate the gesture.
Penelope didn’t hesitate to quickly nod, then looked down at me and playfully nudged my shoulder. “You could have just asked, newbie, let’s go get your stuff.” With that, she spins around and starts heading towards our office.
I giggle softly then mouth to Spencer “Thank you.”
Before I turned around to follow the click-clack of yellow heels, I caught Spencer smiling softly and mouthing back “You’re welcome.” His smile was warm, comforting even.
This job came with horrors, but maybe seeing these people every day along with saving others, will make it all worth it.
#criminal minds#spencer reid#fangirl#mgg#mathew gray gubler#spencer#reid#fiction#fanfiction#fanfic#spencer reid fanfiction#spencer reid x oc#spencer reid x disabled oc#fanfic writer#writers on tumblr#writers#writing#penelope garcia
29 notes
·
View notes
Text
Ok I've had a very random train of thoughts and now wanna compile it into post.
Some MM characters computer-related (???) headcanons lol
Riley:
Has above average knowledge of Excel/Google sheets due to studying finance, but after four years with no practise forgot most of it.
The "Sooon, I have a problem" person in their family. Actually, surprisingly good and patient at explaining computer stuff to older people.
Has a higher responsibility of doing taxes (finance, after all). Even he never fails to do them right, Ed always double checks. Sometimes they get into argument, where inevitably Riley proves he is right but his father would never admit it.
Warren, Leeza, Ooker and other teens:
Also nothing outstanding in terms of skills, except few of them have interest in IT.
They have bunch of small local Discord servers and one big main server with some very stupid name.
Few times Bev tried to bring up importance of parental control over this "new and rapidly growing young community", but thanks God no one took her concerns seriously
Leeza moderates it and her moder role called "Mayor-mini". Like father like daughter.
All teens local jokes and memes were bourn/spread though that server.
Bev:
Rumors says she sacrificed her humanity to obtain such powers with Microsoft software package.
Can build up Access database from scratch, using basic SQL commands, assemble primitive, but surprisingly sufficient interface to it and synchronize it with Excel in span of one day or less.
In her laptop there're every pupil's personal file, countless Excel tables, several automatised document accounts, Google calendar with precisely planned schedule for next several months (for school, church, island and personal matters) and probably Pentagon files.
Probably can find all Pi numbers with Excel formulas.
Never lets anyone to her laptop.
Spends her free time at different forums, mostly gardening-related.
Wade:
Made a very fucking poor decision to let Bev do all the legwork with digital document accounting.
Now has no idea how some of things even work, so just goes with a flow and does what Bev tells.
No wander she got away with embezzlement.
Knows about kid's server. Very proud of Leeza for managing it :)
Because of that, he knows one or two memes from there, but keeps them in secret.
Has hobby of fixing office equipment. Does it with Sturge in spare time due to Dupuytren's contracture not letting him operate his hand fully.
Sarah:
There's no good medical technicians on island, so when something goes wrong with equipment electronics - tries to fix it herself to best of her ability.
Always monitors electronic e-shops for spare details or equipment. Grows more and more addicted to it.
Frequently updates her selection of sites with useful medical information, because Erin asked her for help guiding teens though puberty. For that receives glances from Bev, but doesn't give a shit.
Has reputation of cool aunt among kids, so she was one and only adult invited to main Discord server. Didn't accept it (doesn't even have Discord acc), but still grateful for trust.
Plays solitaire a lot.
John:
Back when he was playing Paul, Bev asked him to do something with Excel. In conclusion, poor bastard had to learn basic computer skills and Excel in span of several days. Now he is traumatized for rest of his life.
Will do all the work manually just to not touch laptop again.
Upsets very easly when does something wrong.
Doesn't own laptop. Don't give that man laptop, he will cry.
By his own will uses it only to watch baseball. Always asks someone to help with that.
#midnight mass#midnight mass headcanons#beverly keane#idk I just felt silly and wanted to write it down#riley flynn#warren flynn#leeza scarborough#wade scarborough#sarah gunning#john pruitt#monsignor pruitt#father paul hill
23 notes
·
View notes
Note
do you have any suggustions for porygon enrichment? ive been wanting to get one since i was little, but i want to make sure theyll be happy.
(OOC: i really like the aesthetic of your blog and you seem like you could help. have you come across any quality porygon themed desktop pets? ive been trying to find one and theyre shockingly scarce.

Hello! I would be glad to help!
Porygon are quite distinct between individual. As I like to say, if you’ve met a Porygon, you’ve met one Porygon. There are no easy one size fits all approaches to Porygon enrichment as they all have particular interests. Despite all that, there are some trends and patterns you can use as a jumping off point while you get to know your Porygon.
A couple popular toys for Porygon are building blocks, puzzles, puzzle boxes, marble race tracks, abacuses and soundboards. They generally like things that engage their creativity and problem solving skills, as well as audio-visual stimulation (they generally aren’t that big on smells, textures or taste).
Another option is an electronic device, like a computer or phone. You can install different programs and widgets that serve the same purposes the physical toys would. You can also get mods for your Porygon, a lot of them love modifications, like color alterations, accessories or new models.
Finally, you could give your Porygon internet access. The internet is amazing for a porygon’s enrichment, but there are certain precautions you have to take. First of all, make sure your Porygon wants to use the internet. There are Porygon who are completely uninterested on the internet, so verifying they actually want to use it might save you some trouble.
If your Porygon does want to use your internet, you’ll have to install an antivirus for your Porygon’s health and anti-doxing software for your safety and privacy. Parental controls are also a useful feature to make sure your Porygon doesn’t end in a weird corner of the internet, but the best thing you can do is just monitor their internet use.
And those are the basics for Porygon enrichment!
Hope you find this useful!

//No, sorry, I really don’t do widgets or desktop pets (specially since my computer is currently a bit dead). Nell and I are very much not the same person, also. They are just a character with knowledge and interests that differ from mine quite a bit. But I’m glad you like the blog! Hope you can find what you’re looking for, tho!
8 notes
·
View notes
Text
Video Game Enthusiasts Lament that the Best Game of the Year Is Essentially Softcore Pornography

"I mean, fuck's sake," says Derek "CuntBlaster97" Przybelski, a "gamer" from Salt Lake City speaking to Facts! News. "So many games came out in 2024. A new Tekken, a new Dragon Age, a Final Fantasy 7 remaster... and basically the only games worth playing are two goddamned co-op shooters, something that looks like what my solitaire-addicted grandma would get peer pressured into trying in an alley, and this fucking shit," gesturing to the 8-foot-tall F-cup goat person depicted on his computer's monitor. He proceeded to "run" a "dungeon," frowning and muttering angrily while having the most fun he's had since he was a child.
"It's basically fucked," says another video-gamer who wished to remain anonymous. "Like, this is the only actual good game that's released since September," referring to Saber Interactive's Warhammer 40,000: Space Marine 2. "I can't play that one though or I'll get banned from my girlfriend's Discord server for being a chud. But, like, fuck's sake, I can't play this one either. What if my parents see this?," gesturing to his "gaming avatar", a two-foot tall, 200-pound opossum woman which nobody over the age of 30 would be able to recognize as sexualized. "I have Steam Family Share with my little brother. If he sees this in his library I'm fucked... it's probably the only thing I'm gonna play for the next month though, at least until the next Abiotic Factor update."
"Atlyss is part of a larger trend," according to Vanessa Dobbins, a researcher at the University of Waterloo's Games Institute. "In the 90s with the advent of the M-rated video game, there was mostly a clear deliniation between good games, which were wholesome, and what we in the field call 'slop,' which was edgy and sexual -- which at the time meant anorexic women in leather. World of Warcraft by Blizzard Entertainment, being a good game yet edgy and sexual, was an outlier that caused changes in the behavior of Homo stupidens, the common video game developer. Now good games tried to become sexual in imitation of Warcraft, whereas slop games rejected sexuality in an attempt to seem superior to it. With Japanese gaming falling victim to anime in the mid 2000s, however, good games mostly became the territory of Homo stupidens basementii. This subspecies generally does not begin seeking a mate until relatively later in their life cycle, resulting in a shift in sexual games from the likes of Bayonetta towards more abstract sexual imagery, like the black slime from Changed, or in this case, ass-cheeks wobbling so hard that they should rip off."
An inside source at Unity Technologies, Inc., owners of the "Unity" video-game software which was used to create Atylss, told Facts! News that they are working hard with Microsoft Corporation and Sony Group to do as much as they can to prevent further good games from being released in the future. "This one slipped through the cracks, but we are working night and day to make sure this sort of thing doesn't happen again."
3 notes
·
View notes
Text
Honestly, I think the TV/computer restrictions we had in my house were good for kids our age. The computers were desktops so you couldn’t really hide what you were doing on there, but the only bad part was that my dad would like comment on my writing when I was very obviously simply writing bad fantasy fiction. They didn’t care if I was on Neopets or playing Cake Mania or whatever. I also remember watching Glee in the middle of the computer room, where my parents could see the screen but not hear what was happening. They didn’t have to closely monitor what I was doing (like having tracking software) because they knew they could always just see it. I started having access to a more private computer around 12 or 13 ish.
What they almost never tracked was what we were reading from the library, so we would read stuff way too old for us (I remember reading Memoirs of a Geisha pretty young) but the harm that can do is in part limited on account of being vetted by a public librarian for inclusion in the library. My sister and I also both read the Elsie Dinsmore series, which is this horrible very Christian series about an antebellum plantation. Elsie is a poor little rich girl who lives on the plantation; her family owns slaves and the slaves all love Elsie because she is so virtuous and upholds Christian values. Elsie’s father is abusive and mean because he is not Christian, but she does what she’s told to anyway because she knows to honor her father. Eventually he reforms and accepts Jesus into his heart and becomes a better father. And again, my parents could see what we were reading (except Memoirs of a Geisha, I was so sneaky about that one because I knew it was about sex) but they mostly didn’t care. Parental panopticon? Maybe! But it worked pretty well.
5 notes
·
View notes
Text
How to check if your computer is being monitored
In today's digital age, the issue of privacy and security is more pressing than ever. Whether you’re a casual user or a professional, understanding if your computer is being monitored is crucial. This guide will delve into the signs of monitoring, tools to detect it, and steps to safeguard your privacy.

Understanding Computer Monitoring
Before diving into the signs and detection methods, it’s essential to understand what computer monitoring entails. Monitoring can involve tracking your online activity, keystrokes, file access, and even webcam usage. This can be done by malicious software (malware), spyware, or legitimate monitoring software used by employers or parents.
Types of Monitoring
Malware and Spyware: These are malicious programs that can be installed without your knowledge. They can track your activities and send data back to an attacker.
Keyloggers: This type of software records keystrokes, capturing sensitive information like passwords and personal messages.
Remote Access Tools (RATs): These tools allow someone to control your computer remotely, monitoring your screen, accessing files, and even using your webcam.
Legitimate Monitoring Software: Often used in corporate environments, this software tracks employee activity for productivity or compliance reasons. While legal, it can still infringe on personal privacy.
Signs That Your Computer May Be Monitored
Recognizing the signs that your computer might be monitored is the first step in protecting yourself.
1. Unusual System Behavior
Slow Performance: If your computer suddenly becomes sluggish, it might be due to monitoring software consuming resources.
Frequent Crashes or Freezes: Unexpected system crashes can indicate underlying issues, including malware.
2. Suspicious Programs
Unknown Applications: Check your installed programs for any unfamiliar applications. Many monitoring tools disguise themselves as legitimate software.
High Resource Usage: Use the Task Manager (Windows) or Activity Monitor (Mac) to look for processes consuming excessive CPU or memory.
3. Network Activity
Unexplained Network Traffic: Use network monitoring tools to check for unusual data being sent or received. High outbound traffic could indicate that data is being transmitted without your consent.
Blocked Ports: Monitoring software often uses specific ports to communicate. If you notice blocked ports that you didn’t configure, it could be a red flag.
4. Webcam and Microphone Behavior
Indicator Light Activation: If your webcam or microphone is being accessed without your knowledge, the indicator light may be on even when you're not using it.
Unexpected Recordings: Check for unusual files that could be recordings made by your microphone or webcam.
5. Browser Behavior
Unusual Browser Extensions: Check for extensions you didn’t install. Some can track your browsing activity.
Unexpected Redirects: Frequent redirects to strange sites or altered search results can indicate tracking.
6. Security Alerts
Antivirus Notifications: If your antivirus software frequently alerts you about threats, it may indicate that monitoring software is present.
Firewall Alerts: Unusual outgoing connection attempts can suggest that an unauthorized program is trying to access the internet.
Tools to Detect Monitoring Software
If you suspect that your computer is being monitored, several tools can help you investigate further.
1. Antivirus and Anti-Malware Software
Using a reliable antivirus or anti-malware program can help detect and remove malicious software. Some popular options include:
Malwarebytes: Excellent for detecting and removing malware and spyware.
Norton: Offers comprehensive protection against various types of threats.
2. Network Monitoring Tools
Tools like Wireshark can help analyze network traffic and identify suspicious activity. You can monitor data packets to see if there are any unexpected connections.
3. Task Manager / Activity Monitor
Regularly check the Task Manager (Windows) or Activity Monitor (Mac) for processes that look unfamiliar or suspicious. Research any questionable applications before taking action.
4. System Scans
Use built-in tools to perform system scans:
Windows Defender: Run a full scan for malware and spyware.
Mac’s Built-in Security Features: Use the Malware Removal Tool for additional scanning.
5. Firewall Monitoring
Make sure your firewall is active and monitor logs for any unusual activity. A firewall can block unauthorized access attempts and alert you to potential threats.
Steps to Protect Your Privacy
If you determine that your computer is being monitored or you want to prevent it from happening, follow these steps to enhance your security.
1. Update Your Software Regularly
Keeping your operating system and all software up-to-date ensures that you have the latest security patches. This reduces vulnerabilities that can be exploited by monitoring tools.
2. Use Strong Passwords
Implement strong, unique passwords for all your accounts and devices. Consider using a password manager to generate and store complex passwords securely.
3. Enable Two-Factor Authentication
Two-factor authentication (2FA) adds an extra layer of security by requiring a second form of verification, making unauthorized access much more difficult.
4. Install a Firewall
Ensure you have a firewall activated, whether it’s built-in (like Windows Firewall) or third-party. This helps control incoming and outgoing network traffic.
5. Be Cautious with Downloads
Avoid downloading software from untrusted sources, as this can introduce malware to your system. Always verify the legitimacy of software before installing it.
6. Regularly Review Permissions
Check application permissions on your device regularly. Revoke access for any apps that do not need to access your camera, microphone, or location.
7. Use a VPN
A Virtual Private Network (VPN) encrypts your internet connection, making it difficult for anyone to monitor your online activities.
8. Educate Yourself
Stay informed about the latest cybersecurity threats and best practices. Knowledge is your best defense against monitoring.
When to Seek Professional Help
If you suspect your computer is being monitored and cannot identify or remove the software yourself, consider seeking professional help. Cybersecurity experts can perform a thorough analysis of your system and provide tailored solutions.
Conclusion
Understanding if your computer is being monitored is vital for protecting your privacy. By recognizing the signs, utilizing detection tools, and implementing security measures, you can safeguard your personal information. Remember, vigilance is key in the ever-evolving landscape of digital security. Stay informed, proactive, and secure in your online presence.
#Computer Security#Online Privacy#Cybersecurity#Monitoring Software#Malware Detection#Privacy Protection#Digital Security#Keyloggers#Network Monitoring#Antivirus#VPN#Internet Safety#Personal Data Security#Remote Access Tools#Digital Awareness
2 notes
·
View notes
Text
Israel targets information technology experts as part of its genocide in Gaza
The Israeli army has systematically targeted dozens of programmers, information technology experts, and workers in computer engineering, in addition to destroying the headquarters of their companies, as part of the ongoing crime of genocide in the Gaza Strip since 7 October 2023. Since the beginning of its large-scale attack on Gaza, the Israeli army has killed hundreds of people with intellects and expertise in the blockaded enclave, especially those proficient in information technology, programming, and computer engineering, as well as other elites in the local community such as doctors, academics, and others. Euro-Med Human Rights Monitor compiled a list of technology specialists, including those with expertise in programming and artificial intelligence, who have been directly killed by the ongoing Israeli attacks. Among those is the well-known programming engineer Haitham Muhammad Al-Nabahin, who was esteemed as one of the Gaza Strip’s most accomplished computer engineering specialists. He, along with his wife, Eng. Nasma Zuhair Sadiq, was killed in an Israeli air strike on a residential home in the Bureij refugee camp in the central Gaza Strip on 14 March. A relative of Nabahin told Euro-Med that he and his family had fled to a house in Rafah in the far south of the Gaza Strip. However, Nabahin’s two children, Layan and Muhammad, were killed, and his wife was wounded in an Israeli attack that forced them to flee once more, this time to a house in the Bureij camp, where the Israeli army killed them approximately two weeks later. According to his relative, Nabahin had paid a hefty price to have his and his wife’s names included in the coordination lists for individuals seeking to leave the Gaza Strip through the Rafah Border with Egypt in order to treat his wife abroad, before they were both killed in the Israeli attack. Tariq Thabet, a graduate of the American Hubert H. Humphrey Fellowship Program, was also killed on 31 October 2023 in an Israeli air strike that also claimed the lives of his wife, children, parents, and other family members. Thabet was the director of the UCAS Technology Incubator Programs at the University College in the Gaza Strip. Baraa Abdullah al-Saqqa, the founder of DITS and a software engineer specializing in website and smartphone application programming (senior and lead developer), was also killed in a similar Israeli air strike on 21 November 2023. He held positions with numerous industry-specific businesses, such as (CTO) company. Additionally, he was active in providing programming courses and specialized workshops. In addition to being a student in a master’s program in computer engineering with a focus on artificial intelligence, Saqqa was regarded as one of the leading young programmers in Gaza. He was recognized for his efforts in training numerous new employees in the technical fields and was awarded numerous certificates and awards. Saqqa was killed in an Israeli air strike on his family home in Gaza City, along with his pregnant wife and his in-laws. The list also includes Muhammad al-Athal, who was killed on 26 October 2023, Hamza al-Shami on 2 November 2023, Obaida Khater on 20 December 2023, Anas al-Sheikh on 9 December 2023, and Abdel Rahman Hamada on 15 March, in addition to another group of young programmers, including Rami al-Sousi, Abdel Hamid Al-Fayoumi, Bilal Zaqout, Ahmed Nidal Qaddoura, engineer Muhammad Hassouna, and others.
[keep reading]
4 notes
·
View notes
Text
WHAT IF - Ubdertale AU idea - ContinueTale
What if the ‘player’ was a huge Undertale fan, but also a major in coding. They hooked their game up to a software and messed with the code so they would be able to put their own custom answers for fun. They never put in an AI for the characters or messed w/ the characters speech so it caught them by surprise when the characters responded differently. They later figured out that these characters were real, living in this loop like the lore goes. The player wanted to be able to help them. They teamed up w/ their science friend and through the character of Frisk they helped Alphys and Sans try to figure out how to actually get them out of the loop. They tried transferring the characters (conscious and sprites) to another software, nothing, they tried defying the laws of the game and inputting DT into monsters, nope, Try and fix the machine? Not even close. (To make sure Alphy wouldn’t forget the past they saved a video into the files of the game would play automatically into Alphy brain whenever they reset to try again. Years went into this and basically no progress was made; 300 resets. Then, an experiment worked, by writing new game laws the monsters would be able to withstand a small bit of DT. One day, the player’s computer crashed. They feared they had lost everything and they did. Their copy of Undertale had oddly been deleted and when they tried to re-download it the computer would just crash again. The player and the scientist wept at their loss, but eventually they would forget; Move on w/ their lives. 3 years later, the scientist and the player got married, a year after they adopted a kid. When the kid was about 15 years old (a total of 6 years have passed since the computer crash). The kid (Who we will be calling ‘player2’) found an old flash drive in the garage. They asked their parents about it and they shrugged, not knowing what it was. Player2 input it into their computer and a game called ‘Undertale’ was downloaded on it. Curious, the kid decided to play it. In the game, during those 6 years the characters never had a reset. Sans and Alphys would never forget about the humans that abandoned the experiments. Through those 6 years they had found life peaceful somewhat, Sure they couldn’t escape the underground or the game, nor age. but all self aware characters were content (By night they would work in trying to continue the experiments on their own, trying to break into the games code but a fire wall always stopped them) and any un-aware characters went on w/ their life (to an extent). Then, a reset; Everyone was suddenly back. Sans immediately went to the door, he was excited ‘did the humans decide to come back? Did they change their mind? Would they help them break the game and be able to continue their lives?’ he would ask hopefully. But fear would strike his boney heart as he saw the red eyes of the Player he had come to love (PLATONICALLY YOU FREAKS.) now possessed. He checked Frisk, ‘Player2’ it had read. No.. a new player? Where was the old player? Player2 had done research on the “ancient game”, they found most interest in the genocide route and started to play. Unaware of the text to speech input their parents had implanted into the game to speak to the monsters. They assumed the game was glitched when the sans had shown up earlier then old lets plays had shown. San’s was confused, ‘why was there a new player?’ ‘Who is the new player?’ ‘Why are they coming back now?’ ‘why did they decide to do a genocide?’ , thoughts both sans and Alphys shared. Alphys observed through the monitors.
This is the possible comic idea - do y’all like it?? idk—
1 note
·
View note
Text
the little artsy speedster
Irey West. Donna Troy. Babysitting. Sketchbooks. Polaroid Photographs. 2353 words. (ao3.)
The Troy Photography studio was located at a townhouse in the Upper West Side, up a short flight of stairs and inside a bedroom that had been converted into a work space. On one end was a backdrop and numerous light stands, and on the other was a computer desk, a couch, and several shelves cluttered with nothing but photography equipment.
Evidently, Auntie Donna had a strong preference for Fujis.
As the photographer sat at her desk and meticulously edited photographs for her client, Irey West sat on the nearby couch and made an attempt at her science homework — attempt being the operative word. Sure, learning about the anatomy of the human eye was probably the more productive thing to do, but doodling flowers in the margins of her textbook was much more fun.
Plus, after getting into trouble for spacing out in class on three separate occasions, there was probably no way that Irey could get into any more.
After decorating a page with roses of varying colors, Irey closed her book and decided she had enough “science-ing” for the day.
She got up from the couch and stretched her shoulders, her eyes catching sight of the studio window, and the view of Manhattan outside.
Curious, she stepped through the studio and arrived at her babysitter’s desk. She stood by the chair as Donna affixed her eyes to her monitor, utilizing the finest image editing software available to properly finish her project.
Irey peered over and took in the photograph on the monitor. The image depicted a grown man with a head of neatly combed brown hair, a pair of blue eyes, and a kindly smile on his face.
Auntie Donna had already explained that she was editing headshots for her various clients, most of which were working actors. The photos on the screen now looked exactly the same as the ones before, except the current guy had a chin shaped like a butt.
Noticing the young redhead, Donna turned her head to the side and smiled. “How’s that homework coming along?”
Irey looked down to her shoes. “... it’s fine.”
“Are you sure?” asked Donna, smirking. She turned in her swivel chair to face her little niece. “Because you’ve been doodling more than studying.”
Irey let out a sigh. “Doodling is all I’m good at.”
Donna tilted her head to the side just slightly, then spoke in a soft tone. “That’s not true.”
Irey was unconvinced, especially if her last report card was anything to go by. If it wasn’t the dyslexia making it difficult to put words to paper, then it was the ADHD making her space out during class and missing the lesson entirely. At least doodling on her notebook, sketchpad, and textbooks helped her feel grounded, like she was actually okay at something for once.
It helped that her art teachers seemed to tolerate her more than the others.
Sensing the distress in her young niece, Donna decided to speak up again.
“I have an idea — how about I finish up here and we get an early dinner?” she suggested. “I need a break, anyways.”
Irey couldn’t help but smile. “I’d like that.”
Donna gave a quick nod, then turned towards her computer screen once more. “Great, just give me a few minutes.”
As the photographer went on to tinker with her client’s headshots just a little more, Irey turned her head towards one part of the studio that she was particularly interested in.
That part being the shelf of trinkets near Auntie Donna’s desk. She had seen it a handful of times before and every time she was utterly intrigued by the collection of cameras put on display. The actual equipment used for photo shoots were kept in thick plastic boxes, while the shelf appeared to be a place for Auntie Donna to display her camera collection.
The contraptions Irey saw were unlike the mirrorless digital camera her parents had at home, or even the medium format workhorse Auntie Donna used for her clients. The cameras were much older, yet managed to stand the test of time. All of them used film, which meant that every shot had to matter.
There was one camera that was made of black plastic, felt like a toy, and was called a Holga. There was another that was made of metal and built like a tank — it was called a SLR, which meant single-lens reflex. According to Auntie Donna, back in a certain day and age most cameras had a mirror inside of them to reflect the image from the lens and into an eyepiece for the photographer to see.
But then there was one that Irey just couldn’t keep her eyes off of. On the bottom right shelf there was a blocky camera that was most definitely older than herself. Irey had seen Donna use it before, and everytime she did the camera would make a whirring sound as it dispensed a square-shaped photograph out the front. It would only take a few moments for the image taken to appear on the thick, plasticky material.
Curiously, Irey reached for the camera and took it gently in her hands. She had witnessed Donna being very precious with the thing and made sure to do exactly the same.
Back at the computer desk, Donna looked over her shoulder to see her young niece toying with her prized Polaroid Supercolor 635 CL. Unsurprisingly, she was quick to speak up.
“Be careful, that’s-”
Immediately, Irey’s finger put pressure on the shutter button, causing a flash of light to emit from the camera and for Irey to start stumbling backwards. By the grace of a higher power, she didn’t drop the device and have it shatter into a million little pieces.
Irey let out a grumble as she put her arm over her now overstimulated eyes.
“Aaaah! I flashed myself!”
Donna stepped out of her chair and approached Irey, reaching out to steady the girl and gently taking the camera away. As she placed the whirring device on her desk, she just had to wonder if there was a much less concerning way for Irey to phrase her thoughts.
…
…
…
Donna didn’t consider herself a great cook, but she was well-versed in the art of scrounging around one’s kitchen and making a meal out of whatever she could find.
Fortunately, there was enough groceries left in her fridge and pantries to constitute some kind of dish. Though she wondered exactly how old the frozen shrimp in her freezer was.
Nonetheless, Donna busied herself over a hot stove as Irey sat at the island in the middle of the kitchen. It was nice to occupy her mind with something that didn’t involve a camera or punching a supervillain for a change.
As Donna boiled fettuccine and fried shrimp, she would look over her shoulder just to check on the speedster at the counter.
Every time she looked over Irey was in the same spot. On the counter was a sketchbook and in her hand was a pencil, and on the paper Irey drew to her heart’s content on a surface that was actually made for it.
After slicing a few lemons on a cutting board, Donna put her knife down and walked over to the sketching speedster.
“What are you drawing, Irey?”
Irey put down her pen and slid her sketchbook.
As Donna looked towards the moleskine on the counter, she expected the usual abstract scribbles that most kids would make when doodling, or even the flowers Irey had placed in the margins of her textbook.
But to her surprise, the illustration that Irey had made could only be described as a winged eldritch abomination with two dark, beady eyes that had been drawn with so much pressure that the paper was slightly warped.
“It’s mothman!” Irey exclaimed in a cheery voice.
Had it not been for the girl’s utter enthusiasm, Donna would have been concerned. But instead she couldn’t but smile at her little niece’s rather amusing — albeit slightly unpredictable — imagination.
“Oh, how macabre,” Donna said as if a thirteen-year-old would know exactly what that meant. She flipped through the pages of the book and found a handful of similar pencil drawings depicting the same creature.
Either kids were super into urban legends nowadays, or Irey had a really strong appreciation for the cryptid of West Virginia.
Irey quickly took her sketchbook back and flipped a few pages forward. What awaited Donna on the other side was an illustration of a window, one seemingly in front of a city skyline that looked somewhat familiar.
Donna blinked for a few moments, her interest very much piqued, then realized that what Irey had drawn was a recreation of the view outside of her photography studio.
While the lines were uneven and the shading was spotty in some places, the fact that Donna could actually recognize it as her little corner of the Upper West side was impressive. Irey even managed to depict the rooftops of various brownstones and the few tree branches of Central Park.
“I also tried to draw the view outside your office,” Irey said in an almost timid tone.
“Did you do this by memory?” asked Donna, gently grazing the surface of the drawing with her fingertip.
“Yeah, so it sucks, but I tried,” Irey confirmed, shrugging. “But Mom said that trying something and sucking is the first step in trying something and not sucking.”
Amused, Donna gave the young budding artist a smile. “Your mother’s a very wise lady, Irey.”
Stepping away from the kitchen island, Donna walked towards one of the drawers in the room and pulled it open, said drawer being one of those spaces that a person would fill with whatever clutter they needed out of the way.
After rifling through the fast food napkins, numerous rubber bands, and brochures she took but never read, Donna emerged from the mess with a single fine-tipped pen in her hand.
“Here, try this,” said the Amazon as she handed it over to the little artsy speedster. “You won’t have to use as much pressure for the details.”
Irey looked apprehensive as she accepted the pen. Perhaps all her time drawing with her school supplies had led to unfamiliarity with anything else.
Nonetheless, Donna noticed Irey testing the fine-tipped pen as she turned back towards the meal on the stove.
After testing if the pasta was done, Donna drained and added it to the pan with the shrimp. She squeezed a healthy dose of lemon juice onto the food, then added a few pats of butter to ensure that all the ingredients were able to truly mingle.
For a meal that she was partially bullshitting, it turned out remarkably well.
Donna placed the shrimp scampi with fettuccine onto two plates and garnished them with celery leaves, pepper, and grated parmesan. As she brought it to the kitchen island she could see Irey putting the final touches on her masterpiece.
“How’s it looking?” asked Donna as she placed the meals on the counter.
Irey put down her pen and showed off her not new, but improved illustration. “It’s looking less sucky,” she admitted, shrugging once more.
“It was never sucky to begin with, trust me,” Donna assured as she peered towards the sketchbook. With a smile on her face she slipped into the role of art critic.
Unsurprisingly, Irey managed to enhance the details of her recreation of Donna’s studio window, adding darker lines wherever it was necessary to highlight the details outside of the Troy brownstone. She even made sure to properly detail every window of every building that she depicted.
“Excellent work, Irey,” Donna lauded with a grin. “Top marks.”
Irey looked as if she was trying not to blush. “You know a lot about drawing,” she said sheepishly, perhaps trying to deflect the complement. “But I thought you were a photographer.”
“An old friend of mine used to draw a lot,” Donna explained easily. She took a seat next to her young niece and placed the sketchbook down. “I like to think I picked up a thing or two.”
Irey let out a hum, then suddenly her attention was caught by the steaming plate of pasta in front of her. With a grin, she grabbed the nearest fork and began digging in.
“Thanks for dinner, Auntie D,” she managed to say before taking her first bite.
In the span of a few seconds Donna saw nearly every bit of Wally West in the little girl in front of her — everything from the shade of his hair to his signature speedster appetite.
“You’re welcome, Irey,” Donna said. Before she picked up a fork, she suddenly remembered something that she had brought with her from the studio upstairs.
Reaching into the pocket of her cardigan, Donna soon pulled out the polaroid photograph that had been taken during Irey’s little camera incident.
She leaned over the counter slightly and held the photo towards the little redhead.
“Oh, let’s see how this turned out.”
Irey’s mouth was half-full with pasta as she peered over. The photo immortalized on the material was nothing special, essentially an analog selfie of a curious redhead who didn’t realize that the camera she was holding was full of film.
Donna thought it was a good first shot, but Irey was thinking otherwise.
“Ugh, even my photos suck,” said Irey, crinkling her nose.
“No, it doesn’t,” Donna promised. “It’s just your first, and if you try to take more than I can assure you that they’ll get better with time.”
Irey shrugged. “Yeah, but I’m a drawer, not a photographer.”
Donna tilted her head to the side just slightly. “Some people could be both.”
For a moment, Irey blinked in shock as she took in the news, and in her little niece’s eyes Donna could see a certain revelation settling into the girl, one that clearly had not been realized before.
With a sly grin on her face, Donna dug into her pasta and wondered if this — of all things — could be a day that would change Iris West II’s life forever.
#Irey West#Donna Troy#Iris West II#Impulse#Thunderheart#Troia#Wonderfam#Flashfam#DC#things you edit at 3AM
6 notes
·
View notes
Text
How Billionaires Organize Their WorkSpace—What You can Learn From it?
Do you ever wonder what billionaires’ workspace looks like and how they manage their workspaces?
What was their workspace before they were famous or Internet celebrities?
In this post, we will explore the workspaces of Bill Gates, Elon Musk, Mark Zuckerberg, Steve Jobs, Mike Bloomberg, and Kevin Kelly with many other articles and entrepreneurs to see how they are productive and what their workspace looks like.
We will also see what we can learn from them.
Bill Gates
Bill Gates is an American technology entrepreneur, investor, and philanthropist better known for the software company Microsoft, As of Dec 2023 it's being valued at 2.76 trillion dollars.
The first person to achieve a $100 Billion net worth. He also owns Codex Leicester, a collection of scientific writing by Leonardo da Vinci.
Gates being a nerd is interesting to see what his workspace looks like.
These are some photographs of the workspace of Bill Gates when he was building Microsoft. You can clearly see the messy piles of papers with computers, keyboards, and telephones.
Gradually over the year, he becomes neat and clean as other work is delegated to others. Gates now uses a clean work setup with a water bottle, computer, keyboard, mouse, and other important things.
Throughout the images of Bill Gates, you can see a book near to him, as he likes to read a lot.
Elon Musk
Elon Musk is an interest entrepreneur and investor and the wealthiest person in the world with over $222 billion as of Dec 2023. He is the CEO of SpaceX and Tesla, owner of X, formally Twitter, and also the founder of xAI.
Mr. Musk always grabs a vacant desk whenever he needs one to work and it's interesting to see what his workspace looks like.
Elon Musk always uses an oval-shaped desk to work from the end of his work desktop and other end his places his other important documents or projects.
The desk is somewhat clean and you always find some book near to him, being an avid reader like Bill Gates. The U-shaped desk is the most interesting thing I liked the most from his workspace.
It allows him to switch places from his desktop to the front when he meets someone.
You can also see Musk always works in a place that has large windows to allow natural sun lights to come.
Mark Zuckerberg
Mark Zuckerberg is a computer programmer and entrepreneur, better known for social media Apps like Facebook, Instagram, WhatsApp, and Threads. He is the CEO of Facebook and its parent company, Meta.
Mark is also an interesting personality and it is interesting to see the workspace of Mark Zuckerberg.
From the early days of Facebook, Mark has been comfortable with a small setup with a monitor or laptop with a mouse or some paper around him. You can clearly see he only uses a laptop and it allows him to work from anywhere.
You can see the present day picture of Mark’s desk where you can see some books, a laptop with no mouse and cable connect to it, his phone and Meta Quest VR, which lunched recently.
Steve Jobs
Steve Jobs was an American businessman, inventor, and investor better known for co-founding Apple Inc. He was also the primary investor of Pixar and the founder of NeXT.
As you can see the workspace of Steve Jobs from the last days of his life. He is kind of messy and that may be the sign of geniuses. He is filled with books, electronic devices, and piles of papers.
Nothing is expected more from a person who values and makes minimalist products like iPod, iPhone, and iPad.
Mike Bloomberg
Micheal Bloomberg is an American businessman and politician, who is better known for founding Bloomberg L.P. financial data services firm, and served as mayor of New York City from 2002-2013.
The workspace of Bloomberg looks like the modern coders with multiple screens and monitors opened with chats. Because of his industry, he is always open to news and chats on his multiple monitors.
Kevin Kelly
Kevin Kelly is a founding executive editor of Wired magazine. He is also a writer and photographer. Kelly is an interesting man and with also in his workspace. His workspace looks different from other billionaires.
He also has a messy desktop with a wall of Legos and a skeleton of some kind. You can see the mess of things like books, notebooks, papers, mic, desktops, and more.
See Workspaces of Great Minds, Artists, Scientists, and Writers
Jane Austen, Novelist:
Yoshitomo Nara, Artist:
Pablo Picasso, Painter:
Mark Twain, Writer:
Virginia Wolf, Writer:
Roald Dahl, Children's Writer:
Thomas Edison, Inventor:
Stephen Hawkings, Theoretical Physicist:
Nicholas Tesla, Inventor:
Martin Luther King, Political Leader:
Warren Buffet, Investor:
NASA Scientists:
Bob Dylan, Singer:
Winston Churchill, Former PM of the US and political Leader:
Neil Gaiman, Writer:
PS: You can see my workspace here.
What You can learn from their workspaces?
Looking at different kinds of workspaces from modern-day entrepreneurs to billionaires and artists to scientists, here are some of the things that we can learn from their workspaces.
Everybody is different in their own way, we can't say a clean background led to success or a messy own. They are the clear examples of this.
You can often find books in their workspace that allow them to read whenever they want to.
Some use a simple workspace and other messy or complex workspaces like Bloomberg with multiple monitors.
They seem to love their own workspace with their own choice of design.
2 notes
·
View notes
Text
What is Bitdefender Central & How Do I Use It?
Bitdefender provides one of the most popular antivirus software that protects your computers and mobile phones. The company product helps you by protecting your devices and data as it comes with lots of features. Also, it is a cloud-based engine that will protect devices when browsing or using the internet. It goes light on the system and doesn't take up much space. This blog will discuss what is Bitdefender Central & how do I use it. And explore more on it.
What is Bitdefender Central?
The company created Bitdefender Central, an online platform to manage all the company's products and subscriptions. First, You need to create your account. And then only you will be able to log in to Central's web portal. There you will find the main dashboard, which provides you with details about all your Bitdefender devices. Also, which devices are under protection, and have any new threats been detected?
Further, you can manage any of the active subscriptions. If you are facing any issues, you can browse from the library of help features. So it acts as a hub for all your devices using Bitdefender software. Moreover, the Central hub also facilitates access to premium security services.
How to Use the Bitdefender Central?
Now, we will look at how you can use this platform and manage your devices. Remember, the online portal has many features that simplify managing the devices. Further, it acts as a remote access portal across your devices. Let us see the functions you can access via Cental's portal.
Subscriptions
From the Central managing account, you can access all your subscribed devices. Also, make payments and details of the same. Further, you can even activate a new subscription service and manage your devices.
Remote Management
With the Central portal account, you will be able to view details of any device connected with the Bitdefender product. Also, you can manage certain things directly from the hub, which includes triggering a malware scan. Plus, you can boost the functioning of a device.
Anti-Theft
If ever you lose your mobile or someone steals your laptop, then the Central management hub will enable you to track the lost device. Further, you can even send a message; in the worst cases, you can lock your device or completely delete its files.
Parental Control
If you have subscribed to the Internet or Total Security feature, you will get a parental control feature. So, from this hub, you will be able to monitor your child's online activity, their live location, set screen time, and much more.
Further, it can display the time spent, applications, websites, and even contacts saved on the device. The feature is really helpful in protecting your child from age-inappropriate sites and content.
Digital Identity Protection
In this age, where anyone can be found on the internet, protecting one's identity on the internet becomes important. So, the company assures you by protecting your digital identity. You use the functions in this to see how much of your data is made public or leaked.
Further, you can always be aware of sensitive information about your identity on the Dark Web or public data. Moreover, you will be alerted if there is any attempt on your identity, such as data breaches, account info leaking, and hacking.
Support Portal
If you ever need help, there is a list of options that the company offers that you can use to resolve your issue. The help features include video tutorials, FAQs, a knowledge base, and more. These resources are helpful and come in handy for users who are new to using a Central account.
Conclusion
Bitdefender is a great software that ensures all-around protection of your devices against all threats. You will get many features and functions that create multiple layers of protection. In this blog, we discussed what is Bitdefender Central & how do I use it. Now, this online platform lets you access all your devices, protect your files against device theft, and many more features.
FAQs
How to reset your Central Account password?
If you ever forget your password and are unable to access your account, open the account and Sign in. Later, type your associated email with the account, and then select Next. Now, select the Forgot Password option, and you will receive an email with instructions and reset your password. Further, you have to enter the security code, create a new password, and press save. Finally, you will be able to sign in again with your new password.
How to remove a device from a Central account?
To remove a particular device, first sign in to your account. Later, go to the My Devices section, which is present on the sidebar. Now, you will be able to see all the devices and select view details. After that, you will see the remove option and confirm it. Finally, the device is removed from the subscription list.
How can you delete a Central account?
Bitdefender's Central account is an online hub that helps manage all your subscriptions and devices. To delete the account, you need to sign in to your account. After that, select the account icon, and choose your account. Once, then go to Data & Privacy, and finally select the Delete account option. After this, you will lose all the services and products the company provides.
Visit: bitdefender central login
central.bitdefender.com
Source: https://centralbitdefenderdotcom.wordpress.com/2023/12/14/what-is-bitdefender-central-how-do-i-use-it/
#central.bitdefender.com#bitdefender sign in#bitdefender login#bitdefender central login#www.central.bitdefender.com#bitdefender.com/activate#bitdefender central#bitdefender#bitdefender antivirus#bitdefender log in
2 notes
·
View notes