#cyber-attacks
Explore tagged Tumblr posts
Text
OCR Proposed Tighter Security Rules for HIPAA Regulated Entities, including Business Associates and Group Health Plans
As the healthcare sector continues to be a top target for cyber criminals, the Office for Civil Rights (OCR) issued proposed updates to the HIPAA Security Rule (scheduled to be published in the Federal Register January 6). It looks like substantial changes are in store for covered entities and business associates alike, including healthcare providers, health plans, and their business…
#covered entities#cyber criminals#cyber-attacks#ePHI#hacking#health care#Health Insurance Portability and Accountability Act#HIPAA#HIPAA Security Rule#OCR#Office for Civil Rights#public health#Ransomware
0 notes
Text
All About Advanced Persistent Threat (APT): Definition, Types And Examples

Have you ever seen the Netflix series Black Mirror? It’s an anthology that delves into the darker side of human nature, often intertwined with technological advancements. The first episode, titled "The National Anthem," presents a shocking scenario where a Prime Minister is forced into a harrowing situation after a member of the royal family, Princess Susannah, is kidnapped. The episode highlights how a leader's vulnerability can have severe consequences on a national level.
Just as the episode explores a national crisis, there are numerous security threats in the digital space. One of the most severe types is Advanced Persistent Threats (APTs), sophisticated cyber-attacks typically supported by organized criminal groups. These attacks aim to infiltrate a network and maintain a long-term presence, causing significant risks for both organizations and governments.
While discussing such topics can be unsettling, it's vital to raise awareness about APTs and their potential impact on our security and privacy. Understanding these threats allows us to better prepare and safeguard ourselves against them.
In this article, we will delve into the concept of Advanced Persistent Threats, exploring their definition, various types, and real-world examples.
What Is an Advanced Persistent Threat?
An Advanced Persistent Threat (APT) is a highly sophisticated cyber-attack conducted by skilled hackers, typically targeting high-profile organizations. Unlike typical cyber-attacks, APTs are not designed to cause immediate damage. Instead, they infiltrate a network and remain undetected for extended periods—sometimes months or even years.
The primary objective of an APT attack is to gain unauthorized access to a network and maintain this access over time, allowing the attackers to extract valuable data or disrupt critical systems. These attacks pose significant risks, including financial losses, reputational damage, and the theft of sensitive information.
Now that we have an overview of what Advanced Persistent Threats are, let's explore the different types of APTs.
Types of Advanced Persistent Threats
Advanced Persistent Threats can manifest in various forms, each posing unique challenges and risks. Here are some common types of APTs:
Account Takeover: This attack involves cybercriminals gaining unauthorized access to an individual's or organization's account, such as email, social media, or banking accounts. Once they gain access, they can steal sensitive data, initiate fraudulent transactions, or spread malware.
Ransomware: A form of malware that encrypts the victim's data, making it inaccessible until a ransom is paid. Ransomware attacks can cripple an organization's operations, leading to significant financial losses.
Data Breach: APTs may infiltrate a network with the intent to steal sensitive data, such as customer information, trade secrets, or intellectual property. Data breaches can result in regulatory fines, legal liabilities, and loss of customer trust.
Social Engineering: In this type of attack, cybercriminals manipulate or deceive individuals into revealing sensitive information or performing actions that compromise security. Tactics like phishing emails, pretexting, or baiting are often used by APTs to gain a foothold within an organization.
Business Email Compromise: In this scam, attackers impersonate executives or trusted entities to trick employees into transferring funds or revealing sensitive information. This can lead to substantial financial losses and damage to an organization's reputation.
Understanding these types of APTs is crucial in defending against them. By implementing robust cybersecurity measures, educating employees, and maintaining vigilance, organizations can reduce their risk of falling victim to these threats.
Next, let's look at some real-world examples of Advanced Persistent Threats to better understand their impact.
Examples of Advanced Persistent Threats
Here are a few real-world examples that demonstrate the complexity and impact of APTs:
Hafnium: This Chinese state-sponsored APT group, discovered by Microsoft, exploited vulnerabilities in Microsoft Exchange Server to access email accounts and steal sensitive data. Hafnium has targeted various industries, including defense, healthcare, and education.
Stuxnet: A highly sophisticated worm designed to disrupt Iran's nuclear program, Stuxnet was delivered via an infected USB device and targeted the industrial control systems used for uranium enrichment, causing significant damage to centrifuges.
GhostNet: Originating in China, this APT used spear-phishing emails containing malware to compromise computers in over 100 countries. The attackers focused on gaining access to government ministries and embassy networks, turning compromised machines into surveillance tools.
These examples highlight the global reach and potentially devastating consequences of APTs. They serve as a reminder of the importance of robust cybersecurity measures and the need for constant vigilance against these sophisticated threats.
Final Thoughts
The episode "The National Anthem" from Black Mirror is a stark reminder of the far-reaching consequences of an APT attack. When critical systems and individuals are compromised, the impact can be devastating. To mitigate these risks, organizations must remain vigilant, implement multi-layered security measures, and foster a culture of cybersecurity awareness.
As Robert Mueller wisely said, "There are only two types of companies: those that have been hacked and those that will be."
Hopefully, this exploration of Advanced Persistent Threats will help you better understand and defend against such cyber threats.
0 notes
Text
Threats of Artificial Intelligence for Cybersecurity
Sfetcu, Nicolae (2024), Threats of Artificial Intelligence for Cybersecurity, IT & C, 3:3, ppp, Abstract Artificial intelligence enables automated decision-making and facilitates many aspects of daily life, bringing with it improvements in operations and numerous other benefits. However, AI systems face numerous cybersecurity threats, and AI itself needs to be secured, as cases of malicious…
#algorithmic biases#artificial intelligence#black boxes#cyber security#cyber-attacks#Cybersecurity#threat actors#threat modeling#threat taxonomy#threats
0 notes
Text
Guard Against Financial Frauds as Data Leakage Becomes Rampant: Insights from RBI Officials
In an era where digital transactions and online banking have become the norm, safeguarding financial information has never been more critical. The Reserve Bank of India (RBI) officials recently highlighted the increasing threats of financial fraud due to rampant data leakage. This blog post delves into the nuances of this pressing issue and offers strategies to protect your financial data. The…

View On WordPress
#Cyber-attacks#Cybersecurity#Data leakage#Digital transactions#Encryption methods#Financial data protection#Financial fraud#financial institutions#Identity theft#Incident response plan#Phishing scams#RBI officials#Security audits#Two-factor authentication#Vulnerability assessments
0 notes
Text
Wargaming Expertise Shared with International Delegates

UK and Finland Unite in Wargaming
In an era where the battlefield is as much digital as it is physical, the UK's Defence Experimentation and Wargaming Hub has taken a significant step forward. Recently, it played host to a team from the Hybrid Centre of Excellence (HCoE) in Finland, marking a pivotal moment in defence collaboration and strategic innovation. This gathering was more than a meeting of minds; it was a fusion of cutting-edge methodologies designed to prepare for the future of warfare.
Key Insights from the Visit
The visit emphasized the importance of combining traditional defence strategies with modern, hybrid approaches. As adversaries become more sophisticated, employing a mix of conventional and unconventional tactics, the need for comprehensive preparedness is undeniable. Moreover, the collaboration between the UK's Strategic Command and Finland's HCoE serves as a testament to the global effort required to stay ahead of emerging threats. The Role of the Defence Experimentation and Wargaming Hub Located at Southwick Park, Hampshire, the Hub is at the forefront of developing tactical responses to hybrid threats. This encompasses everything from cyber-attacks and disinformation campaigns to economic coercion. Moreover, it's a space where technology meets strategy, and where the UK's defence capabilities are honed for the complexities of modern conflict. Hybrid Centre of Excellence: A Global Network Established in 2017, the HCoE serves as a beacon of expertise and training for EU and NATO countries. Its involvement with the Wargaming Hub not only brings a wealth of knowledge but also reinforces the importance of international cooperation in defence strategy.
Future Collaborations and Their Impact
The HCoE is expected to visit the Defence Experimentation and Wargaming Hub, paving the way for ongoing partnerships. Such collaborations are crucial for enhancing the collective capacity to address hybrid threats, ensuring that allied nations possess the knowledge and skills to protect global security. The Benefits of Wargaming Wargaming is not just about simulating conflict scenarios; rather, it's about anticipation, strategy, and decision-making. The Defence Experimentation and Wargaming Hub offer a state-of-the-art facility where defence personnel can test hypotheses and strategies. Consequently, this leads to faster, evidence-based decisions.
A Unified Front Against Hybrid Threats
As the world navigates the complexities of 21st-century conflict, the collaboration between the UK's Defence Experimentation and Wargaming Hub and Finland's Hybrid Centre of Excellence stands as a beacon of strategic innovation. Through sharing expertise and resources, these institutions are setting the stage for a more secure future. This demonstrates that in the face of evolving threats, unity and preparedness are our greatest assets. Sources: THX News & Strategic Command. Read the full article
#cyber-attacks#defencecollaboration#DefenceExperimentationandWargamingHub#evidence-baseddecisions#Globalsecurity#HybridCentreofExcellence#hybridthreats#Internationalcooperation#strategicinnovation#tacticalresponses
0 notes
Text
Susceptible to cyber-attacks, and Accountants must now consider cyber security as part of their day-to-day work.
“Accountants are well placed to advise on the steps a business should take to protect itself – cyber security isn’t just about technology and computers: it involves people, information, systems, processes and culture too”
John Berriman – PwC
Almost every week, another high-profile cyber security breach affecting firms all around the world is reported. And the number of events is rising: according to a recent global survey performed by PwC, the number of assaults reported by midsize businesses – those with revenues of between £64.5 million ($100 million) and £645.6 million ($1 billion) – increased by 64 percent in 2014 compared to 2013.
These attacks cost a lot of money. According to PwC, a single data breach costs US businesses more than $500,000 on average. According to John Berriman, chairman of PwC’s cyber security practice, “the average cost of the most severe cyber security breach for a big organization now starts at £1.46 million, although that figure doesn’t take into account the impact a breach has on an organization’s reputation and relationship with its stakeholders.”
According to PwC research for the UK’s Department for Business, Innovation and Skills, smaller businesses are just as likely to be harmed, with the cost of a serious breach ranging from £65,000 to £115,000 in the UK.
Cyber criminals are particularly interested in accountants and other financial institutions. Financial institutions, according to PwC, are almost 30% more likely to be targeted than other businesses.
‘It’s because they deal with high-value business data and sensitive financial information on a regular basis,’ Frank Morey, CEO of security company Virtues Risk Management, explains. ‘There have been a series of targeted attacks against the industry, the most recent of which was the Morgan Stanley breach, which exposed the personal information of 900 of its high-net-worth clients online.’
Kaspersky Lab, a Russian security firm, reported the largest organized cyber-attack on financial institutions to date earlier this year. A global gang of cyber hackers entered more than 100 banks and other financial institutions in 30 countries, stealing £645.6 million ($1 billion) in total from the banks rather than their clients.
Accountants, both in practice and in industry, must be able to recognize and respond to cyber security threats, rather than ignoring the matter in the mistaken notion that cyber security is the realm of their IT departments or that their company’s software would protect them from intrusions.
‘While products like SAP and Oracle have built-in cyber security features that can reduce the risk of data breaches, it’s still critical that you remain vigilant in your daily job,’ says Phil Sheridan, managing director of Robert Half UK.
Cyber Attacks
‘Hacking and phishing assaults are frequently launched by an employee clicking on a link in an email,’ explains Matt White, senior manager in KPMG’s cyber security division.
Another typical way for malware to enter an organization is through opening suspicious email attachments. ‘Word, Excel, and PDF documents all make it simple to embed harmful code that can subsequently be abused,’ explains Greg Sim, CEO of security technology firm Glass wall Solutions.
In fact, while cyber-attacks are becoming more sophisticated, lax security knowledge among personnel is the leading cause of security breaches. One example is bad password behavior. According to Medium, a password management company, 90 percent of employee passwords are so predictable that they can be broken in six hours. Furthermore, 18% of employees disclose their passwords with coworkers.
Many employees have their work emails redirected to their personal email accounts. However, because personal email services do not have the same security protections as corporate email services, hackers frequently hunt for corporate data through personal email, which is easily available to them.
Cyber security
While no company is immune to cyber-attacks, there is a lot that can be done to prevent them.
‘Anything linked to the storage or transfer of data – how it is safeguarded and accessible, or how it is prevented from being accessed,’ explains White. ‘Different nations have different policies and laws about how information and data is used, with many “internet-related services” crossing several borders, so it’s not that clear,’ he adds.
Accountants can assist their clients in this area.
‘Accountants are ideally placed to advise on the steps a firm should take to defend itself – cyber security is about people, information, systems, procedures, and culture as well,’ adds Berriman.
PwC is attempting to raise awareness and prepare businesses.
‘For example, our Breach Aid event response service assists organizations in preparing for and responding to large incidents, as well as the legal and regulatory consequences of a breach,’ Berriman notes. ‘We can also monitor, analyses, and respond to threats on our clients’ networks and systems thanks to our London-based cyber security labs.’
Accountants can also take steps to protect themselves and their firms.
‘To be prepared for a wide range of risks, accountants must understand their firm’s IT security policies, including policies and processes for ensuring safe online practices, as well as procedures for reporting and dealing with breaches,’ Brown writes.
‘Accountants may also require additional cyber awareness training. As with most things, prevention is far preferable to cure.’ For information visit https://hmaa.ae/businesses-are-increasingly-susceptible-to-cyber-attacks/
You Can Count On Us!
#cyber-attacks#Accountants#cyber security#and Accountants#Susceptible to cyber-attacks#and Accountants must now consider cyber security
0 notes
Text
Cyber-Attacks: Understanding the Threat Landscape and Defending Your Digital World

Cyber-attacks have become an ever-present threat in our increasingly digital world. This comprehensive guide delves into the complex and evolving landscape of cyber threats, providing essential insights into the tactics, techniques, and motivations behind these attacks. Learn how to protect your digital assets and personal information through a deeper understanding of the cybersecurity measures, strategies, and best practices required to safeguard your online presence.
Link:- https://www.akgvg.com/blog/countering-cyber-attacks-with-seqrite-endpoint-security/
Visit our social media platform:- Linkedin:- https://www.linkedin.com/in/akgvg-and-associates-8a2680176/
0 notes
Text
What if the cyber attack on X was just a prelude of things to come? 🤔
#pay attention#educate yourselves#educate yourself#reeducate yourselves#knowledge is power#reeducate yourself#think about it#think for yourselves#think for yourself#do your homework#do your research#do your own research#do some research#ask yourself questions#question everything#government secrets#government lies#government corruption#evil lives here#lies exposed#truth be told#wef#wake up#be ready#be prepared#cyber attack#power grid#power outage#news#candace owens
161 notes
·
View notes
Text

"Eric Noonan, CEO of cybersecurity provider CyberSheath, told CNN it’s likely too early to tell if an attack caused the issues.
“One of the things that should always be taken with a grain of salt is any statements made in the short period of time, immediately after, or even in this case during an attack,” Noonan said.
Musk has a history of attributing technical snafus to cyberattacks. When his conversation with Donald Trump on X started 42 minutes late in August 2024, he said there was a “probability” of an attack."
CNN
Sky News
POLITICO
#destiel meme news#destiel meme#news#united states#us news#world news#elon musk#fuck elon#elongated muskrat#x twitter#twitter#x#cyber attack#cyberattack#cyber security#tech industry#computer technology#computer security#i hope it's just the gutted hollowed out shell of twitter's code finally giving out
191 notes
·
View notes
Text

#tesla#tesler#cyber truck#electric vehicles#law enforcement#maga#car#attack#tesla dealership#america#americans#us news#politics#political#us politics#news#donald trump#elon#musk#elon musk#president trump#american politics#jd vance#law#nps#alt national park service#national parks service#trump administration#republicans#republican
131 notes
·
View notes
Text
man i wish i could buy each volunteer at ao3 a bottle of the most expensive liquor of their choice because oh my GOD they are tireless today. they are heroes. they are the real ones
2K notes
·
View notes
Text
Top 5 Email Encryption Software Of 2024

Welcome to TechDogs! No, it’s not a mistake, but rather an encrypted message using the Caesar cipher with a shift of one letter. Wondering what that means?
Each letter in the original text is shifted one position forward in the alphabet—so A turns into B, B into C, C into D, and so forth.
Would you like us to encrypt your message now?
Many of us have likely tried this in our childhood to send secret notes to friends. However, with modern technology, several tools can easily decode such simple encryptions. The Caesar cipher is straightforward to break—you managed it, didn’t you?
In today’s digital era, businesses face similar challenges when sending secure messages. With countless sensitive documents and confidential information shared via emails daily, businesses must ensure that these communications are protected, especially given the rising number of cyber-attacks.
Introducing Email Encryption Software—a robust solution that provides end-to-end security for business communications, ensuring sensitive data remains safe during transmission and storage. This software helps organizations comply with regulations and mitigate cyber risks.
If you’re in search of Email Encryption Software for your business, keep reading as we list the top 5 options for 2024!
As businesses face increasing cyber threats in today’s digital age, email encryption becomes essential for protecting sensitive communications. In this guide, we’ll explore the top 5 Email Encryption Software solutions of 2024, offering robust security, compliance support, and peace of mind in an ever-evolving cyber landscape.
Top 5 Email Encryption Software Of 2024
To stay ahead of cyber threats, businesses must prioritize strong cybersecurity measures. Email Encryption Software is a key line of defense, safeguarding sensitive communications and protecting against data breaches. Here are the top 5 Email Encryption Software solutions for 2024.
Tool 1: Proton Mail Founded in 2013 and headquartered in Geneva, Switzerland, Proton is a leading provider of secure email services with over 400 employees. Clients include organizations such as the United Nations and Amnesty International. Proton Mail, making its first appearance on our list, offers end-to-end encrypted email with zero-access encryption. Not even Proton Mail can access user data. It features Swiss privacy protection and integrates with other Proton services like Proton Calendar and VPN.
Tool 2: Proofpoint Email Security And Protection Based in Sunnyvale, California, and founded in 2002, Proofpoint is a leader in email security with over 4,000 employees. The company serves clients like Perrigo and Pacific Life. Proofpoint’s email encryption solution provides advanced threat protection, combining machine learning and sandboxing to block threats in real-time. Its Targeted Attack Protection and Email Authentication tools ensure secure communications.
Tool 3: Avanan Cloud Email Security Avanan, based in New York and founded in 2014, is a rising star in cloud email security. With over 4,000 customers, Avanan offers advanced protection for cloud email services like Office 365. It uses AI/ML to continuously update its detection capabilities and provides unique features like File Sanitization to prevent malware.
Tool 4: Virtru Virtru, founded in 2012 and based in Washington D.C., provides end-to-end encryption for emails and files, serving industries like healthcare and finance. Virtru integrates seamlessly with email clients like Gmail and Outlook, offering features like granular access controls and persistent file protection, ensuring secure communications across platforms.
Tool 5: RMail By RPost Founded in 2000 and headquartered in Chattanooga, RMail provides email encryption, e-signature, and secure file transfer services. RMail’s technology ensures secure email exchanges with robust encryption standards. Its comprehensive tracking and compliance features make it a trusted choice for secure communications.
Conclusion Investing in Email Encryption Software is crucial for businesses to secure their communications and protect against cyber threats. With these top 5 Email Encryption Software solutions, you can ensure your sensitive information remains protected in an increasingly digital world.
0 notes
Text

CYBRR-ATTCKK
#2000s internet#2000s aesthetic#surrealcore#baidexweb#xspiritualism#web art#net art#not weirdcore#not wc#art#artwork#my art#digital art#curseweb#cyber#photo collage#collage#cars#cyber attack#xpiritualism
193 notes
·
View notes
Text
started aot last week and i’m already on season four, so now i’m day dreaming about levi 🥴
imagine lovesick levi who doesn’t know how to express himself so he just does shit like randomly pull you into enclosed spaces and kisses/fucks you stupid. he’s so cold in public, but when you’re alone, he’s hanging on your every word, silently gazing at you trying to look bored, but he can’t help the flicker of a smirk that appears in his face when you get excited about something you love.
ARGHHHH I NEED HIM SO FUCKING BAD SOMEBODY SEDATE ME 😩
#levi ackerman#cyber talks#cybersmind#aot#attack on titan#levi aot#levi attack on titan#captain levi#aot x black y/n#aot smut#aot drabbles
53 notes
·
View notes
Text
Cyberstalking/Harrassment 🤍🐇
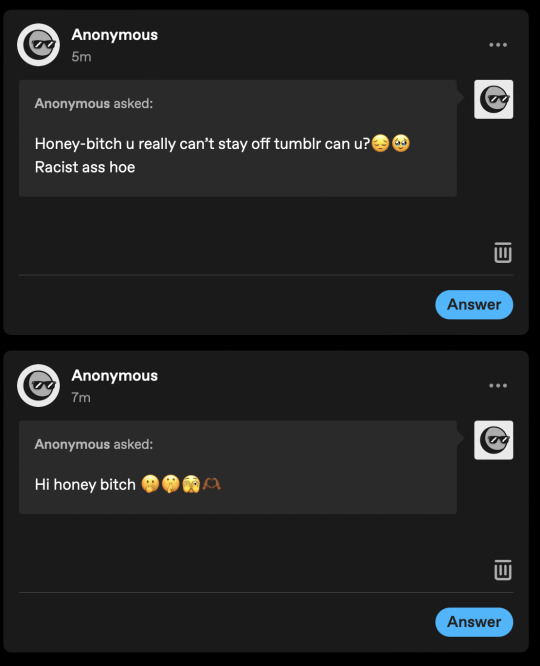
I find it quite depressing, by the fact that it's been less than a week and I'm already getting hate messages. Is anyone else experiencing cyberharrassment and stalking in their inbox? Is this a normal thing in the astro/tarot community?
I'm making this post to claify my stance on cyberbullying and this sort of behaviour. Don't accuse me of being someone I'm not, nor call me a r*cist.
To clarify: I don't know who 'honey-bitch' is and I'm not them.
This page is purly for postivity and kindness and if you send unkind and mean comments like this you will blocked. I don't care about any tea or drama page and all will be blocked.
I hope this person finds peace in their life and for them to take a second to reflect on what they're doing.
#astr#astro notes#astro community#astro observations#astrology#asteroid#asteroids#tarot#tarot community#tarot deck#tarot spread#tarot cards#cyber bullying#cyber attack#who's this#...
36 notes
·
View notes
Note
Get a life, saying Taika Waititi ruined Thor, the real question is who ruined you to threat a FICTIONAL character like a real human being and trying to ruin the very real life and career of a person, besides you think Marvel it's otherworldly good? Those movies are pathetic, every single one follows the same template and Martin Scorsese was right, that's not real cinema. Yes, it's cool the idea of superheroe movies but a very different one it's losing the sense of reality for horrible that it can be, check yourself and contemplate the harm you are causing to someone because you are bullying them online, probably what someone did to you at one point, most geeks have that in common, be better. Honestly doubt you are so perfect and for you answer, he lost himself for a bit, that's why things weren't perfect, he was going through things while he developed that movie, he said so himself, that he lost his love for the art for a bit and in part it's because of things like this, people hating for the sake of it, no other reason, excuse him for being himan. Just leave him alone and move on, write some fanfiction fixing what you didn't like and move on, leave the guy alone, he's not doing anything to you by existing and he's not attached to the movies anymore. Whatever happened or not inside Marvel between TW and KF to make decisions over TLAT we will never know but there's a reason why senior executives have quit since then.
This ask was sent to me a few days ago when this news came:

Like I've said, I'm so glad Marvel has kicked him out so hard and wants to categorically veer from his version of Thor. And everyone hates him now. He deserved this and more. ☺️
Here is my masterpost for everyone detailing how this terrible director ruined Thor like he had a vendetta against him. And here is the tag on my blog to view all the criticisms against him from me and others. Have fun.
#answers#cowards hiding behind anon#and saying i'm the one cyber bullying#the hypocrisy escapes your pea sized brain i'm sure#you must be that btch's lackey who tried to attack me a few months ago#given your same intelligent arguments#thor#thor odinson#marvel#thor 5#chris hemsworth#sam hargrave#would be excellent
33 notes
·
View notes