#details of powershell
Explore tagged Tumblr posts
Text
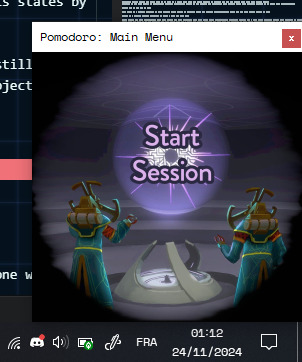
I have an issue with constantly getting distracted, so I got distracted from working by making a 100% customizable Pomodoro App to keep my future self from getting distracted. Have a Google Drive download link.
The Pomodoro technique, if you don't know it, is a discipline method for keeping track of when you are working and when you are taking breaks, notably through the use of a timer.
There are tons of apps centered around this, and yet after looking at so many of them, I somehow could not find one that would do the most basic thing I'd like to have for a study companion: change the background of the app so that yes, I do have a timer telling me to work harder, but I also have an image of my choice to cheer me up along with it.
So what did I do? Did I take the rational, reasonable path, to just suck it up and stick to one of the already existing apps even though it would mean saying no to having my adorable Hearthian OC sleep in a corner of my screen?
Or did I go the hyperfocused insane route of utter procrastination and learn a whole new programmation language from scratch just in order to get my frikkin baby to comfort me while I work?
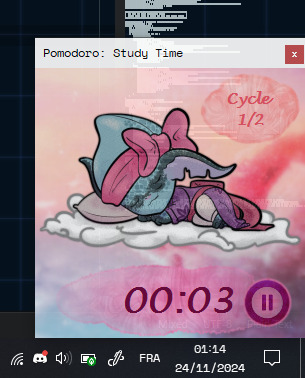
Yeah, who could have guessed.
So! The Google Drive link I shared will let you download everything you need in order to run your own version of this little app, including a tutorial on how to customize it to suit your needs.
The first thing you will see after unzipping the archive is this:
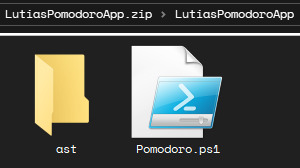
The "ast" folder (standing for "assets") contains every image used by the app -- which means that you can change them as you please! I even gave you transparent versions of the buttons in the "Asset Creation Help" subfolder, in case you like the shapes but want to change the backgrounds.
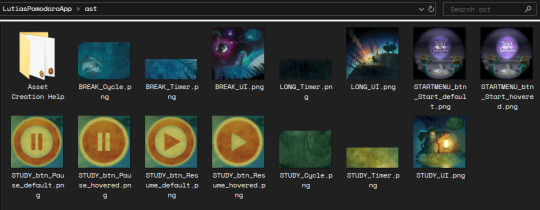
You think that's cool? Oh, but the image assets are far from being the only thing you can change for this app's behavior! You can change EVERYTHING that this app is doing (which isn't much because it's literally just three different types of timers, and even then there are some trickier details with more coding than others (but I still give tips on how to handle those), but shush. Everything this app can do, you can customize to your heart's content).
How do you do that? Well, this is what you get when you right-click on the "Pomodoro.ps1" file:
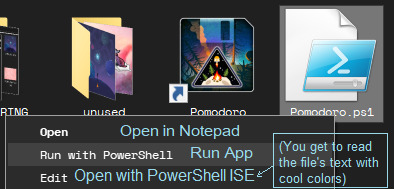
The Pomodoro.ps1 file is the "app" itself, written in PowerShell code that I made as legible as I could make it. There is a whole tutorial in there, made easier to read if you right-click on this file's icon and choose the "Edit" option. Have a preview!
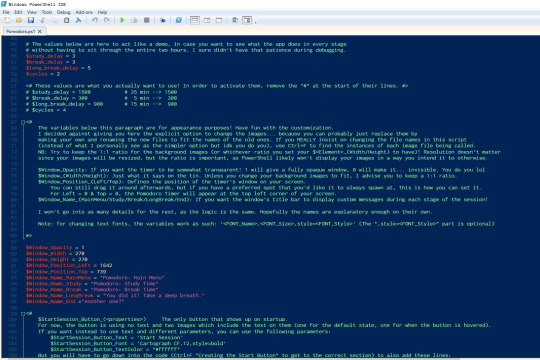
Through editing this file, you can then run a Pomodoro app from which you can have the window's appearance customized, from its size, opacity (if you want to still half-see what's sitting behind it), and start position on your screen (the window can be dragged around, but if you have a preferred position you can tell the app to always load it in that preferred spot right from the get go), to stuff like the custom messages you get whenever the timer progresses:
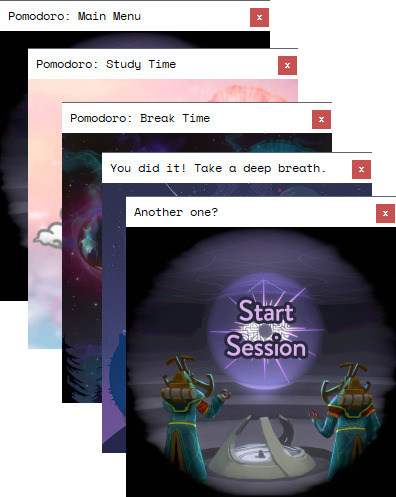
So, yeah. I made a little app meant to help with productivity. One out of many already out there, sure, and it's probably not as cool as many others (but I'll just remind you that three days ago I knew absolutely nothing about PowerShell as a whole, so- I guess that would be still a little impressive that I was able to make a working app like that at all? xD), but as far as I've looked, it's the only one that will let you have your favorite images keep you company while you use it.
I don't know whether anyone other than me will like it enough to use it, but just in case, it's here! Hope it's as easy(-ish) to customize as I made it out to be, or at least close enough.
PS: The version I use for my own personal choices uses some slightly different assets compared to the version I share in the .zip file on my Google Drive. This is because the version I share online solely uses official Outer Wilds art (while the version I made for myself notably uses one piece of OW fanart that I did not make myself, and it didn't sit right with me to share that piece uncredited, even in an edited form. If you are curious, this is the artwork in question).
41 notes
·
View notes
Note
Hi, person with some musical and technical knowlage, with both questions, and some follow-ups to other people's questions:
Regarding the dynamics question, it's implemented in MIDI via velocity, so, in theory, if you just increese the velocity by a set ammount at a certian point, for a certian string (p, ff, etc), it should work fine
Following on from that, using Capital Letters to denote accents (raise the velocity for a single note, then return to the baseline) ought to work nicely
Then, taking it to a stupid extreme, text styling, for example, if it's in the cursive style, make it legato, which then opens the tin of worms of digital legato, but, making the notes playback for 105% of their regular length works way fucking better than it should
Have you considered a method of implementing octives? I've though about it a bit, and, other than general muscal direction (for example, if the last three notes 123 are all lower than the previus note, drop 4 by an octive, visa versa for up, no change for other situations), I don't think it's very possible to implement in a musical way
How do you select the instrument for each post?
Have you considered using a system like LilyPond in order to generate scores for each post?
OK, that's everything I can think of, if you have any more questions, feel free to ask, well, me, I suppose, despite that not being how tumblr asks normally work
To be completely honest I don't want to deal with dynamics, if I do add them it'll probably be in like version 3 of the script at best, version 2 is already gonna be an undertaking.
See above
Copy pasting text from tumblr into powershell means it does not carry the formatting into the script and I really don't want to do that manually
I definitely want to add octaves, but figuring out an intuitive way of doing it that allows for maximum manipulation by asks is proving difficult. Your idea is good but I'd rather go for something
If you look closely at the formatted text you'll see some letters bolded and italicized, those are the letters used to choose the instrument. I've explained in further detail in the past but basically it just sees what instrument it can find in the text first.
I have never heard of lilypond and I do not want to learn entirely new notation software for silly gimmick blog, sorry. if you want the midi file for one of the posts so far i haven't deleted any though
16 notes
·
View notes
Text
downloading youtube subtitles/captions en masse (or videos, with diff options) & searching them
i wanted to take a playlist and download all of the autogenerated captions so i could then search them. here's the solution i've come up with. tried to cover even the basics here and not assuming you have any particular experience with installing/using stuff in command line
all these instructions will be for windows (11), the wiki has instructions for other OSes
install yt-dlp this can be used to download youtube and thousands of other sites' videos with a high level of customization, and fortunately for me also allows the option of downloading the subtitles without the video. i didn't really want to download 600+ videos for my project!
https://github.com/yt-dlp/yt-dlp -> download the yt-dlp.exe (see for other OSes)
put it in an executable path, i just added a new one to make things easier, see under the cut for detailed instructions
install ffmpeg this is needed for a variety of things, but specifically for my case, i need it to convert the .vtt file that youtube gives us (which is very cluttered to read because it has formatting info in it too) to .srt which is text and timing only
https://www.ffmpeg.org/ -> same deal as yt-dlp, ditto the executable path - i downloaded this one: https://www.gyan.dev/ffmpeg/builds -> ffmpeg-release-essentials.zip
install srt_fix (for cleaning up autogenerated captions) to fix the doubling of text caused by how youtube creates the autogenerated captions:

before fix -> after
https://github.com/bindestriche/srt_fix -> create a folder in your path with the .exe's called 'yt-dlp-plugins' and copy the folder with srt_fix in it there (so the final path of the srt_fix.py for me is: C:\Users\ns\bin\yt-dlp-plugins\srt_fix-1.0.1\yt_dlp_plugins\postprocessor)
there are other methods of installation on that page as well as a link to the general yt-dlp plugin installation documentation
install grepWin if you want to search the text of the files quickly (which was the whole point of this project for me 🤪) grepWin is a good option, made by the person who did tortoisesvn. at some point i might look into putting these on The Internet somewhere that would be searchable and link to the original videos/timestamps, but right now, i just wanted a quick way to search them.
https://github.com/stefankueng/grepWin - click on the release on the right
documentation with direct link to current release: https://tools.stefankueng.com/grepWin.html
now we're ready to go!
open powershell (start->windows powershell) and navigate to where you want the files to be placed, for example: (ps: press tab after writing a couple letters and it'll fill out the dir name automatically)

paste your command (using one of the panel videos for example):

yt-dlp -t sleep --write-auto-sub --convert-subs "srt" --skip-download --use-postprocessor srt_fix:when=before_dl https://youtu.be/tjqkei7nLhw?si=EfaEnVnf-oCv1kxt
replace with the video or playlist you're interested in. recommend starting with a video first :) if it seems to be bombing out repeatedly, stop with ctrl+c
the flags are needed as follows:
-t sleep - if you don't use this, youtube will stop the download after 300 videos and make you wait an hour, this adds some delays to get around that
--write-auto-sub - this is to grab the autogenerated captions as opposed to the uploaded/created versions
--convert-subs "srt" - to use ffmepg to convert the vtt subs into an srt file
--skip-download - to not download the actual video, we only want the subtitles
--use-postprocessor srt_fix:when=before_dl - this is calling the srt_fix specifically when using the skip-download flag

when it's working correctly, it'll look something like this and the folder will contain two files per video, the original srt and the -fixed srt with the non-duplicated text

the file it creates is named (by default, this can be changed, see the docs) video title [youtube video id] - aka plop that string on the end of this url and it'll pull up the source video https://www.youtube.com/watch?v=
and lastly, searching! obviously this is where things kind of break down, because common words are more likely to be understood and captioned correctly; but proper names, sketchy audio quality, mumbling, etc is going to miss a lot. just for kicks, i thought i'd see if it ever got mark of cain:

detailed instructions on adding a new entry to the path environment variable below - just be careful with this

open system properties - search for that in the start menu or enter environmental - it'll pull it up
in the system properties window -> click environment variables

double-click the user variable Path

click New and put the path. i made a new folder at my profile folder level (ns) called 'bin' for this:

so the path i entered was %USERPROFILE%\bin

#tutorial#yt-dlp#youtube#captions#powershell#downloading videos#panel transcript project#i have no idea what to tag this lol#this is beyond niche content but maybe someone somewhere out there also has a project this might be handy for
4 notes
·
View notes
Note
how are you downloading Ici tout commence?
From the official site!
First, I use a VPN to get a French IP (or Belgian--I'm not sure which they accept, I just know these two work) so I can access the network's streaming site, TF1+. You should be able to sign up for a free account without issue. This is the page for the season 4 eps:
https://www.tf1.fr/tf1/ici-tout-commence/videos/saison-4
Apparently there are always two eps in advance available for the premium subscribers but I'm not caught up plus I think it'd be a little harder to sign up for an actual paid account so I probably won't be able to do that.
So normally I would use youtube-dl/yt-dlp to download the eps but that won't work here, or at least not without some extra steps, because these are DRMed. This is where it gets a little tricky and the whole process isn't super well documented both because it changes a lot and it makes more sense to teach people to learn how to do it than how to do it and also because, well, the more these methods are spread, the more networks change things up and make things harder.
This thread can help you get started: https://forum.videohelp.com/threads/412113-MYTF1-Help-needed-New-DRM-system-can-t-download
The whole forum is quite useful and I've only had to post for help a couple of times, mostly I just search my issue and read through.
That provided command in the second post, that's something to be used in your command line, on Windows in Start you can open that by typing in cmd or PowerShell or just google what you'll need for your computer.
These are the things you'll need to get to run the command:
N_m3u8DL-RE is a tool you can google and download, and also ffmpeg and mp4decrypt. You'll want them in the same folder for convenience. (I think you might need to install python too? If it says you do, then go ahead, lol.)
The way to get the key, this is the most gatekept part, probably. The various streamers out there use different methods of encryption and increasing security levels, and if you read up on it, you'll see stuff about kid and pssh and cdm and L3, it can be overwhelming, but in this case, the things you need are relatively easily accessible.
I'll tell you how to get the pssh and the license URL and you'll be able to use those to get the key. There are several tools you can use them on, one is public and easy, one is private but still easy-ish, and one is pretty complex and not a route I've gone down myself yet (it's the pinned thread in that particular forum). I don't want to link any of them myself, but I'll link to a thread that mentions the easy public one. It does go down at times which is why the hardcore people recommend that last method.
First, before you click on an ep, open up your browser's Developer Tools, usually Ctrl+Shift+i will do the trick. Go over to your Network tab, this shows all the requests your browser makes when you go to a site.
Then click on the episode in the actual browser. You'll see a flood of requests in the Network tab, filter on mpd.
Select the mpd result and the details for it show on the side, click on Preview. Scroll down until you see <!-- Widevine -->. A couple of lines below it, you'll see something like <cenc:pssh>AAA[a bunch of characters]</cenc:pssh>
Grab that whoooole part that starts with AAA, that's the pssh. Go to the Headers detail tab while you're there and grab the Request URL, this is the mpd link we're going to use later.
Now to get the license. Usually you can filter in your Devtools Network tab on license or, in this case, widevine. Since we're already on the Headers detail tab, grab this Request URL now, it should start with https://widevine-proxy-m.prod.p.tf1.fr/proxy?
Now go back to that easy public tool linked in that thread I linked, lol, and just fill in the PSSH and the License. Hit Send and you get a list of three keys at the bottom. I've always gone for the one in the middle and not bothered with all three, but you can try them all.
So at this point, you should be able to fully create and use the command in the first forum link above. If you read the documentation for N_m3u8DL-RE, there are various flags you can use, --save-name "Outputname" will let you name the output what you want, -sv best defaults to the best video quality, -sa best is best audio quality, and so on.
The way to get the subtitle is to turn on subtitles on the video player on the site and to go back to the DevTools box and filter on textstream. Grab the first request, the one that ends with =1000.dash and paste it into a new browser address, and change the .dash to .vtt. That's the subtitle. :) You can use the free tool Subtitle Edit to both convert it to srt, which will let most video players play it with your video, and there's also an Auto-translate option that lets you translate to English. It offers several ways but as I don't have a Google API, I just use the normal "slow" method, it's not that bad.
A second way to get the subtitle is to use the same command as when you're downloading the ep but remove the -M format=mp4 at the end, and instead add -ss 'id="textstream_fra=1000":for=all'
This was all figured out through a LOT of trial and error on my part so please do try your own best if you hit some issues, that's the best way to learn. Also, I just don't want to be the helpdesk on this, lol.
#replies#Anonymous#sent on 20240213#whew#that's a lot#but for real unless there's a huge error in what I've said just try to troubleshoot your issues on your own :x#there seems to be increased interest in this show...I wish I was in the mood to catch up#unfortch I've stopped on both this and neighbours for now...#I don't want to waste them on the mood I'm in these days#ici tout commence
17 notes
·
View notes
Text
0 notes
Text
Office 365 to Exchange Migration: Overcoming Compatibility and Data Integrity Challenges
Migrating from Office 365 to Exchange is not a typical cloud trajectory. But for certain organizations, especially those in highly regulated industries or with on-premises infrastructure commitments, this move is strategic. While technically feasible, it brings critical compatibility concerns and serious risks to data integrity that must be addressed with precision.

Why Reverse Migration Is Gaining Attention
Not every IT strategy is cloud-first forever. Some businesses shift back to Exchange due to compliance mandates, network control, or integration with legacy systems. In hybrid environments, administrators often seek to consolidate workloads under Exchange Server for governance or policy enforcement. The challenge starts the moment Office 365 data must align with Exchange architecture.
Compatibility: A Real and Immediate Roadblock
Office 365 evolves continuously. Many cloud-native features do not exist or behave differently in on-premises Exchange. These include modern authentication methods, shared mailbox behavior, calendar sharing models, and retention policies. When data is exported, formatting, metadata, and flags may not map accurately.
Outlook clients configured for modern authentication may fail during the reconfiguration process. Autodiscover may point to incorrect records if DNS cleanup isn’t handled precisely. These issues multiply when multiple mailboxes, service accounts, and shared folders are involved. Compatibility cannot be an afterthought. It must be audited and remediated before the first batch migration begins.
The Threat of Data Loss During Repatriation
Office 365 stores data across multiple layers. Mail, calendars, contacts, tasks, and archives live in distinct locations. Repatriating this data requires extracting it in a format Exchange can understand. Exporting mailboxes to PST sounds straightforward, but issues arise when mail size limits, corrupted items, or orphaned folders are involved.
Calendars are particularly fragile. Recurring meetings often break when moved across platforms. Folder permissions may not retain their original hierarchy. Rules, categories, and MAPI properties may be lost if the migration tool does not support full-fidelity transfers.
Data integrity is more than preserving emails. It’s about keeping context, structure, and function fully intact. A partial or malformed restore can impact compliance audits and user productivity.
Avoiding Migration Disasters with Technical Foresight
Planning for Office 365 to Exchange migration must include:
Pre-migration audits: Understand mailbox size, item count, shared access patterns, and retention policies
DNS and Autodiscover configuration: Prevent mail flow interruptions and profile rebuilds
Tool selection: Choose solutions that support direct migration from Office 365 to Exchange without intermediate steps
Incremental syncs: Avoid full cutovers when mailbox activity is high
Detailed testing: Validate not just content transfer but also usability post-migration
Automate with Precision: Use Purpose-Built Migration Software
Manual exports introduce delays, errors, and inconsistencies. Relying on native methods or PowerShell scripts is rarely scalable. A purpose-built solution like EdbMails Office 365 migration software supports direct and secure migration to Exchange. It ensures folder structure, metadata, and user permissions are preserved accurately. With support for large mailboxes, advanced filtering, and incremental sync, EdbMails helps IT teams maintain compatibility and data integrity at scale.
Avoid post-migration surprises. Plan smart, validate every stage, and use a trusted solution that minimizes risk.
Additional links:
👉 Import multiple PST files to Office 365
👉 Microsoft 365 tenant to tenant migration
0 notes
Text
Fair warning that that will take you way down the rabbit hole. C and its descendants belong to the family of compiled programming languages, which means that the computer doesn't actually run your code; it compiles it into a set of machine language instructions which is saved as an .exe file and then run. Most programs are only distributed as .exe files, which means that if you open them up in a debugger to see what Microsoft borked, you'll be looking at assembly, and assembly is its own beast. It's only barely comprehensible to humans, and the instructions are so specific and low-level that you're actually looking at the computer being told which segment of memory to go to. It's one step above binary. It can be learned - if you go far enough back, programmers actually recorded binary on punch cards - but it's a very different proposition from using C, which, for all that it's a challenge, does use full words. If I'm perfectly honest, it sounds to me like you're more interested in becoming a combination of a super user and a systems administrator than a programmer. Some basic C would probably still be a good idea to help you understand the foundational principles of coding, but I don't think you actually need to be fluent in it. I am less familiar with resources for systems administration than I am for programming, but I think there are some free courses out there if you Google for them.
What I would recommend for you based on what I do know is to look into the Windows SysInternals suite of tools, together with PowerShell and command prompt. SysInternals includes tools that allow you to view more detailed information about running processes than plain old Task Manager, and gives you more granular control over them. The command line (be that PS or cmd) is usually a faster way to get information about what's wrong with your computer than the GUI. This article looks like it might be a good place to start, and this one has some commands that might help you with identifying and repairing corrupted files. I would also check out SuperUser (as well as StackOverflow, my beloved) for specific problems you may be having; it works a lot like StackOverflow, but is more sysadmin-focussed. Windows Event Viewer will probably also be your friend, especially as a source of detailed error messages to search, though I bet you already know about that.
please learn how to code
like, if you're bored today, and not doing anything,
learn a little bit of coding please
34K notes
·
View notes
Text
Cybersecurity Advisory: Hackers Exploit CAPTCHA Trick on Webflow to Deliver Phishing Attacks

In the ever-evolving landscape of cyber threats, attackers constantly devise new ways to bypass security measures and trick unsuspecting users. A recent and particularly insidious campaign has come to light, revealing hackers are exploiting a clever CAPTCHA trick, often leveraging legitimate platforms like Webflow's Content Delivery Network (CDN), to deliver sophisticated phishing attacks and malware.
This advisory details how this exploit works and, more importantly, what you can do to protect yourself and your organization.
The Deceptive CAPTCHA Trick
Traditionally, CAPTCHAs (Completely Automated Public Turing test to tell Computers and Humans Apart) are designed to differentiate between human users and automated bots, acting as a crucial security layer to prevent spam and abuse. However, in this new wave of attacks, hackers are turning this defense mechanism into an attack vector.
Here's how the exploit typically unfolds:
SEO Poisoning & Malicious PDFs: Attackers use search engine optimization (SEO) techniques to push malicious PDF files high up in search results. These PDFs are often hosted on legitimate, trusted platforms like Webflow's CDN, GoDaddy, or Strikingly, making them appear harmless. Users searching for documents, book titles, or charts might stumble upon these booby-trapped PDFs.
The Fake CAPTCHA Lure: When a victim opens one of these malicious PDFs, they are presented with an image that mimics a CAPTCHA challenge. This fake CAPTCHA often includes a checkbox or a button, prompting the user to "verify they are human" or "download the document."
Redirection to Phishing Pages: Clicking on this fake CAPTCHA image or button redirects the user to a malicious website. To add a layer of legitimacy, this phishing page might even present a real CAPTCHA (like Cloudflare Turnstile), further convincing the victim that they are on a legitimate site undergoing a security check.
Malware Delivery (Lumma Stealer): Once the user completes the genuine CAPTCHA, they are often prompted to "download" the supposed document. However, this action triggers a malicious PowerShell command, silently executing and deploying information-stealing malware, such as Lumma Stealer, onto the victim's system. In some cases, the attack directly aims to harvest credit card details or other sensitive personal information.
Information Exfiltration: The Lumma Stealer malware then proceeds to search for and exfiltrate sensitive data, including passwords, cryptocurrency wallet credentials, browser information, and other critical files.
Why is This So Effective?
This attack vector is particularly dangerous due to several factors:
Leveraging Trusted Domains: Hosting malicious PDFs on reputable CDNs like Webflow's helps bypass common security checks that flag suspicious or newly registered domains.
Social Engineering Sophistication: The use of CAPTCHAs, even fake ones, adds a veneer of legitimacy, making users less suspicious. The multi-stage nature of the attack, sometimes including a real CAPTCHA, further enhances its deceptive power.
Human Tendency to Trust: Users are accustomed to seeing CAPTCHAs and interacting with PDFs, making them more likely to fall victim to these well-crafted schemes.
Fileless Attack Techniques: The use of PowerShell scripts and other fileless methods can help the malware evade traditional antivirus detection.
How to Protect Yourself and Your Organization
Given the stealthy nature of these attacks, a multi-layered defense strategy is crucial:
Extreme Caution with Downloads and Links:
Verify Sources: Always be suspicious of unexpected PDF files or documents, especially if they are from unknown sources or appear in unusual search results.
Hover Before You Click: Before clicking any link or button within a document or on a webpage, hover over it to see the actual URL. Look for discrepancies or suspicious domains.
Direct Navigation: If you're looking for a specific document, go directly to the official website of the source rather than clicking on links from search results or emails.
Enhanced Email and Web Security:
Advanced Email Filtering: Implement robust email security solutions that can detect and block sophisticated phishing attempts, including those with malicious attachments or links.
Web Content Filtering: Deploy web filters that can identify and block access to known malicious websites, even if they are hosted on legitimate CDNs.
Endpoint Detection and Response (EDR):
Proactive Monitoring: EDR solutions can monitor endpoint activity for suspicious behaviors, such as unusual PowerShell script execution or attempts to exfiltrate data, even if the initial infection vector was subtle.
User Education and Awareness:
Regular Training: Conduct frequent cybersecurity awareness training for all employees, focusing on recognizing phishing tactics, social engineering, and the dangers of interacting with suspicious content.
"Think Before You Click": Reinforce the importance of pausing and scrutinizing any unexpected requests or prompts, especially those involving downloads or credential entry.
Keep Software Updated:
Patch Regularly: Ensure your operating systems, web browsers, PDF readers, and all other software are kept up-to-date with the latest security patches.
Implement Strong Authentication:
Multi-Factor Authentication (MFA): Enable MFA on all accounts, especially for critical services. This adds a crucial layer of security, even if credentials are stolen.
The Bottom Line
The exploitation of CAPTCHA tricks on platforms like Webflow's CDN highlights the evolving sophistication of cybercriminals. While these attacks are designed to be deceptive, a combination of user vigilance, robust security tools, and continuous education can significantly reduce your risk. Stay informed, stay cautious, and prioritize cybersecurity in your daily digital interactions.
0 notes
Text
How to Identify Dell PowerEdge Server Generation
Dell PowerEdge servers with common design components are be grouped into generations, This article provides general guidance for PowerEdge server model naming conventions to help identify the generation and key components.
To identify the generation of a Dell PowerEdge server, follow these steps:
1. Check the Model Number
Locate the Model Number: Found on the server’s front bezel, rear label, or within system information (BIOS/iDRAC).
Decode the Model Number:
Format: [Series][Generation][Design] (e.g., R740 = Rack (R), 7 Series, 14th Generation).
Key Rule: The second digit in the model number indicates the generation when added to 10.
Example: R740 → Second digit = 4 → Generation = 14 (10 + 4).
2. Use Dell’s Support Site
Enter the Service Tag (found on the server’s label) at Dell Support. The site will display the generation and full specifications.
3. Check BIOS or iDRAC
BIOS: Boot into BIOS; the main screen often lists the model and generation.
iDRAC: Access the iDRAC web interface (via IP) to view detailed system info, including generation.
4. Command-Line Tools
Linux: Run sudo dmidecode -s system-product-name to get the model number.
Windows: Use msinfo32 or PowerShell: Get-WmiObject Win32_ComputerSystem | Select-Object Model
5. Physical Indicators (Less Reliable)
LCD Bezel Color:
12th Gen (Rx20): Blue
13th Gen (Rx30): Green
14th Gen (Rx40): Orange
CPU Architecture:
12th Gen (2012): Intel Ivy Bridge
13th Gen (2014): Intel Haswell
14th Gen (2017): Intel Broadwell/Skylake
15th Gen (2020): Intel Cascade Lake/AMD Milan
Reference Chart
Model Number ExampleSecond DigitGenerationRelease Era R710, R610 1 11th ~2010 R720, R620 2 12th ~2012 R730, R630 3 13th ~2014 R740, R640 4 14th ~2017 R750, R650 5 15th ~2020 R760, R660 6 16th ~2023
Example Workflow
Model Number: R740 → Second digit = 4 → 14th Generation.
Service Tag: Enter at Dell Support → Confirms "PowerEdge R740 (14th Gen)".
iDRAC/BIOS: System Info → "PowerEdge R740, Generation 14".
This method ensures accurate identification regardless of server configuration or age.
0 notes
Link
[ad_1] Cybersecurity researchers have shed light on a new malware campaign that makes use of a PowerShell-based shellcode loader to deploy a remote access trojan called Remcos RAT. "Threat actors delivered malicious LNK files embedded within ZIP archives, often disguised as Office documents," Qualys security researcher Akshay Thorve said in a technical report. "The attack chain leverages mshta.exe for proxy execution during the initial stage." The latest wave of attacks, as detailed by Qualys, employs tax-related lures to entice users into opening a malicious ZIP archive containing a Windows shortcut (LNK) file, which, in turn, makes use of mshta.exe, a legitimate Microsoft tool used to run HTML Applications (HTA). The binary is used to execute an obfuscated HTA file named "xlab22.hta" hosted on a remote server, which incorporates Visual Basic Script code to download a PowerShell script, a decoy PDF, and another HTA file similar to xlab22.hta called "311.hta." The HTA file is also configured to make Windows Registry modifications to ensure that "311.hta" is automatically launched upon system startup. Once the PowerShell script is executed, it decodes and reconstructs a shellcode loader that ultimately proceeds to launch the Remcos RAT payload entirely in memory. Remcos RAT is a well-known malware that offers threat actors full control over compromised systems, making it an ideal tool for cyber espionage and data theft. A 32-bit binary compiled using Visual Studio C++ 8, it features a modular structure and can gather system metadata, log keystrokes, capture screenshots, monitor clipboard data, and retrieve a list of all installed programs and running processes. In addition, it establishes a TLS connection to a command-and-control (C2) server at "readysteaurants[.]com," maintaining a persistent channel for data exfiltration and control. This is not the first time fileless versions of Remcos RAT have been spotted in the wild. In November 2024, Fortinet FortiGuard Labs detailed a phishing campaign that filelessly deployed the malware by making use of order-themed lures. What makes the attack method attractive to threat actors is that it allows them to operate undetected by many traditional security solutions as the malicious code runs directly in the computer's memory, leaving very few traces on the disk. "The rise of PowerShell-based attacks like the new Remcos RAT variant demonstrates how threat actors are evolving to evade traditional security measures," J Stephen Kowski, Field CTO at SlashNext, said. "This fileless malware operates directly in memory, using LNK files and MSHTA.exe to execute obfuscated PowerShell scripts that can bypass conventional defenses. Advanced email security that can detect and block malicious LNK attachments before they reach users is crucial, as is real-time scanning of PowerShell commands for suspicious behaviors." The disclosure comes as Palo Alto Networks Unit 42 and Threatray detailed a new .NET loader that's used to detonate a wide range of commodity information stealers and RATS like Agent Tesla, NovaStealer, Remcos RAT, VIPKeylogger, XLoader, and XWorm. The loader features three stages that work in tandem to deploy the final-stage payload: A .NET executable that embeds the second and third stages in encrypted form, a .NET DLL that decrypts and loads the next stage, and a .NET DLL that manages the deployment of the main malware. "While earlier versions embedded the second stage as a hardcoded string, more recent versions use a bitmap resource," Threatray said. "The first stage extracts and decrypts this data, then executes it in memory to launch the second stage." Unit 42 described the use of bitmap resources to conceal malicious payloads a a steganography technique that can bypass traditional security mechanisms and evade detection. The findings also coincide with the emergence of several phishing and social engineering campaigns that are engineered for credential theft and malware delivery - Use of trojanized versions of the KeePass password management software – codenamed KeeLoader – to drop a Cobalt Strike beacon and steal sensitive KeePass database data, including administrative credentials. The malicious installers are hosted on KeePass typosquat domains that are served via Bing ads. Use of ClickFix lures and URLs embedded within PDF documents and a series of intermediary dropper URLs to deploy Lumma Stealer. Use of booby-trapped Microsoft Office documents that are used to deploy the Formbook information stealer protected using a malware distribution service referred to as Horus Protector. Use of blob URIs to locally loads a credential phishing page via phishing emails, with the blob URIs served using allow-listed pages (e.g., onedrive.live[.]com) that are abused to redirect victims to a malicious site that contains a link to a threat actor-controlled HTML page. Use of RAR archives masquerading as setup files to distribute NetSupport RAT in attacks targeting Ukraine and Poland. Use of phishing emails to distribute HTML attachments that contain malicious code to capture victims' Outlook, Hotmail, and Gmail credentials and exfiltrate them to a Telegram bot named "Blessed logs" that has been active since February 2025 The developments have also been complemented by the rise in artificial intelligence (AI)-powered campaigns that leverage polymorphic tricks that mutate in real-time to sidestep detection efforts. These include modifying email subject lines, sender names, and body content to slip past signature-based detection. "AI gave threat actors the power to automate malware development, scale attacks across industries, and personalize phishing messages with surgical precision," Cofense said. "These evolving threats are increasingly able to bypass traditional email filters, highlighting the failure of perimeter-only defenses and the need for post-delivery detection. It also enabled them to outmaneuver traditional defenses through polymorphic phishing campaigns that shift content on the fly. The result: deceptive messages that are increasingly difficult to detect and even harder to stop." Found this article interesting? Follow us on Twitter and LinkedIn to read more exclusive content we post. [ad_2] Source link
0 notes
Text
UNC4057 LOSTKEYS Malware Targets Western NGOs

UNC4057 LOSTKEYS
The Russian government-backed outfit COLDRIVER targets Western and non-governmental organisations with its latest spyware, LOSTKEYS.
The Russian government-backed threat organisation COLDRIVER (also known as UNC4057, Star Blizzard, and Callisto) has stolen data from NGOs and Western targets using LOSTKEYS, a new virus. The Google Threat Intelligence Group (GTIG) been tracking COLDRIVER for years, including its SPICA malware in 2024, and believes LOSTKEYS is a new tool.
COLDRIVER focusses on credential phishing targeting well-known targets. People at NGO or personal email addresses are generally targeted. They steal login passwords, emails, and contact lists after gaining access to a target's account. COLDRIVER may also access system files and infect devices with malware.
COLDRIVER has attacked journalists, think institutes, NGOs, and past and current Western government and military advisors. Plus, the gang has kept targeting Ukrainians. COLDRIVER's principal goal is to acquire intelligence for Russia's strategic goals. In several cases, the gang hacked and leaked NGO and UK official data.
January, March, and April 2025 saw the discovery of LOSTKEYS malware. The malicious application may take files from a hard-coded set of folders and extensions and transmit the attacker system details and active processes. COLDRIVER normally utilises credentials to access contacts and emails, although they have utilised SPICA to access target system documents. LOSTKEYS has a unique purpose and is utilised in certain scenarios.
The multi-step LOSTKEYS infection chain begins with a tempting website featuring a fake CAPTCHA. After the CAPTCHA is “verified,” the PowerShell code is transferred to the user's clipboard and the page invites them to execute it using Windows' “run” prompt. The “ClickFix” approach includes socially engineering targets to copy, paste, and run PowerShell scripts. Google Threat Intelligence Group said many APT and financially driven attackers use this method, which has been well documented.
PowerShell does the first stage's second step. In numerous instances, the IP address 165.227.148[.] provided this second step.68. The second step computes the display resolution MD5 hash and stops execution if it matches one of three specified values. This step may avoid virtual machine execution. The request must contain IDs unique to each observed instance of this chain to proceed. In every observation, the third stage comes from the same host as the previous phases.
Base64-encoded blobs decode into additional PowerShell in the third phase. This step requires retrieving and decoding the latest LOSTKEYS payload. It does this by downloading two additional files from the same host using different identities for each infection chain. The first-downloaded Visual Basic Script (VBS) file decodes the second file. Each infection chain is decoded with two keys. One unique key is in the decoder script, while stage 3 saves the second. Keys are used to replace cypher the encoded data.
The final payload is LOSTKEYS VBS. File theft and system data collection are its purposes.
Two more LOSTKEYS samples dated December 2023 were uncovered during this behaviour investigation. These previous PE files posing as Maltego files change greatly from the execution chain starting in 2025. It is unclear if these December 2023 samples are related to COLDRIVER or if the malware was reused from another operation into January 2025. Exchanged Indicators of Compromise (IOCs) include binary hashes and C2 addresses like njala[.]dev and 80.66.88[.]67.
Google Threat Intelligence Group uses threat actor research like COLDRIVER to improve product security and safety to safeguard consumers. Once detected, hazardous websites, domains, and files are added to Safe Browsing to protect users. Government-backed attacker warnings alerted Gmail and Workspace users. Potential targets should enrol in Google's Advanced Protection Program, enable Chrome's Enhanced Safe Browsing, and update all devices.
Google shares its findings with the security community to raise awareness and help targeted companies and people. Sharing methods and approaches improves threat hunting and sector user protections. The original post comprises YARA rules and compromise indicators and is available as a Google Threat Intelligence collection and rule bundle.
#UNC4057LOSTKEYS#UNC4057#COLDRIVER#GoogleThreatIntelligence#virtualmachines#VisualBasicScript#News#Technews#Technology#Technologynews#Technologytrends#govindhtech
0 notes
Text
15 Types of Malware Everyone Should Know About
In today’s digital world, our devices are more connected than ever. While this makes life easier, it also means more opportunities for cybercriminals to attack. One of the biggest online threats is malware. But what is malware? And how can you stay safe from it?
In this blog, we’ll explain 15 different types of malware in simple terms. We’ll also show you how using tools like CoverMeVPN can help protect your personal information and keep you safe online.
What Is Malware?
Malware is short for malicious software. It’s any program or file created to harm your computer, steal your information, or take control of your device without your permission. Cybercriminals use malware to cause problems for people, businesses, and even governments.
Let’s look at the most common types of malware you should watch out for.
The 15 Main Types of Malware
1. Virus
A virus attaches itself to a file or program. When you open that file, the virus spreads to other files on your device. Viruses can damage data, slow down your system, or even delete important files.
Example: A harmful file downloaded from a suspicious email.
Worm
A worm spreads by itself through a network. It doesn't need you to open a file or click a link. Worms often slow down computers and networks by using up resources.
Example: A worm might spread through email contacts and send copies of itself to others.
Trojan Horse
A Trojan horse, or Trojan, looks like a normal file or app. But when you open it, it installs malware secretly. Trojans are often used to steal personal data or give hackers control of your device.
Example: A free online game that secretly steals your passwords.
Ransomware
Ransomware locks your files and demands money to unlock them. It usually asks for payment in cryptocurrency, like Bitcoin.
Example: The famous WannaCry ransomware attack in 2017 affected thousands of companies around the world.
Spyware
Spyware secretly gathers information about you. It can track your keystrokes, watch the websites you visit, and record your passwords.
Example: A program that steals your online banking details while you type.
Adware
Adware shows unwanted ads on your screen. Some adware also collects information about your browsing habits without your permission.
Example: Pop-up ads that appear even when you’re not using your browser.
Rootkit
A rootkit hides deep in your system and allows hackers to control your computer remotely. It’s very hard to detect.
Example: A hacker secretly turning on your webcam.
Keylogger
A keylogger records every key you press. It captures passwords, messages, and credit card numbers.
Example: A hidden program that sends everything you type to a hacker.
Botnet
A botnet is a group of infected computers controlled by a hacker. These computers, called bots, work together to perform tasks like sending spam emails or attacking websites.
Example: A hacker using thousands of infected computers to crash a website.
Fileless Malware
Fileless malware doesn’t install any files. It uses existing programs on your computer to perform harmful tasks, making it hard for antivirus programs to find.
Example: Malware that uses system tools like PowerShell to steal data.
Logic Bomb
A logic bomb is hidden in a program and only activates when certain conditions are met, like a specific date or event.
Example: A malicious code set to delete files on April 1st.
Mobile Malware
Mobile malware attacks smartphones and tablets. It can steal data, track your location, or send premium-rate messages.
Example: A fake mobile app that quietly spies on you.
Scareware
Scareware tricks you by displaying fake virus warnings. It tries to scare you into buying fake software or services.
Example: A pop-up claiming “Your system is infected! Download now!”
Rogue Security Software
A form of scareware, rogue security software pretends to be a real antivirus program. It shows fake alerts and asks you to pay for a solution to problems that don’t exist.
Example: A program claiming you have 500 viruses when your device is clean.
Malvertising
Malvertising uses online ads to spread malware. Even trusted websites can display infected ads without knowing it.
Example: Clicking an ad promising a free prize, which installs malware.
How to Stay Safe from Malware
Staying safe online doesn’t have to be complicated. A few simple habits can protect you from most malware threats:
Always keep your software updated.
Don’t click on suspicious links or attachments.
Use strong, unique passwords for every account.
Backup your important files regularly.
Install reliable antivirus software.
Avoid downloading apps or files from unknown sources.
And here’s a powerful tool to add to your defense:
🌐 Protect Your Privacy with CoverMeVPN
One of the best ways to stay safe online is by using a VPN (Virtual Private Network). A VPN hides your IP address and encrypts your internet connection, making it much harder for hackers to target you.
We recommend CoverMeVPN, a trusted and secure VPN service that shields your online activity from prying eyes. It prevents malware from tracking your location and protects your personal information, especially when using public Wi-Fi networks.
Whether you’re working from home, traveling, or just browsing at a coffee shop, CoverMeVPN adds an extra layer of safety between you and the internet.
Why CoverMeVPN?
Keeps your identity and data private.
Protects you on public Wi-Fi.
Blocks dangerous websites.
Easy to use and fast.
Final Thoughts
Malware comes in many forms, and it’s more common than most people realize. From viruses and worms to ransomware and spyware, these digital threats can cause serious problems. The good news is that by learning about malware and taking simple steps to stay safe, you can avoid most attacks.
Make sure to use strong passwords, avoid suspicious links, and always keep your devices up to date. And for even stronger protection, consider using a VPN like CoverMeVPN to keep your online life private and secure.
By being careful and staying informed, you can enjoy the internet safely without falling victim to malware.
0 notes
Text
10 Must-Have PowerShell Scripts Every IT Admin Should Know
As an IT professional, your day is likely filled with repetitive tasks, tight deadlines, and constant demands for better performance. That’s why automation isn’t just helpful—it’s essential. I’m Mezba Uddin, a Microsoft MVP and MCT, and I built Mr Microsoft to help IT admins like you work smarter with automation, not harder. From Microsoft 365 automation to infrastructure monitoring and PowerShell scripting, I’ve shared practical solutions that are used in real-world environments. This article dives into ten of the most useful PowerShell scripts for IT admins, complete with automation examples and practical use cases that will boost productivity, reduce errors, and save countless hours.
Whether you're new to scripting or looking to optimize your stack, these scripts are game-changers.
Automate Active Directory User Creation
Provisioning new users manually can lead to errors and wasted time. One of the most widely used PowerShell scripts for IT admins is an automated Active Directory user creation script. This script allows you to import user details from a CSV file and automatically create AD accounts, set passwords, assign groups, and configure properties—all in a few seconds. It’s a perfect way to speed up onboarding in large organizations. On MrMicrosoft.com, you’ll find a complete walkthrough and customizable script templates to fit your unique IT environment. Whether you're managing 10 users or 1,000, this script will become one of your most trusted tools for Active Directory administration.
Bulk Assign Microsoft 365 Licenses
In hybrid or cloud environments, managing Microsoft 365 license assignments manually is a drain on time and accuracy. Through Microsoft 365 automation, you can use a PowerShell script to assign licenses in bulk, deactivate unused ones, and even schedule regular audits. This script is a great way to enforce licensing compliance while reducing costs. At Mr Microsoft, I provide an optimized version of this script that’s suitable for large enterprise environments. It’s customizable, secure, and a great example of how scripting can eliminate repetitive administrative tasks while ensuring your Microsoft 365 deployment runs smoothly and efficiently.
Send Password Expiry Notifications Automatically
One of the most common helpdesk tickets? Password expiry. Through simple IT infrastructure automation, a PowerShell script can send automatic email notifications to users whose passwords are about to expire. It reduces last-minute password reset requests and keeps users informed. At Mr Microsoft, I share a plug-and-play script for this task, including options to adjust frequency, messaging, and groups. It’s a lightweight, server-friendly way to keep your user base informed and proactive. With this script running on a schedule, your IT team will have fewer disruptions and more time to focus on high-priority tasks.
Monitor Server Disk Space Remotely
Monitoring disk space across multiple servers—especially in hybrid cloud environments—can be difficult without the right tools. That’s why cloud automation for IT pros includes disk monitoring scripts that remotely scan storage, trigger alerts, and generate reports. I’ve posted a working solution on Mr Microsoft that connects securely to servers, logs thresholds, and sends alerts before critical levels are hit. It’s ideal for IT teams managing Azure resources, Hyper-V, or even on-premises file servers. With this script, you can detect space issues early and prevent downtime caused by full partitions.
Export Microsoft 365 Mailbox Size Reports
For admins managing Exchange Online, mailbox size tracking is essential. With the right Microsoft 365 management tools, like a PowerShell mailbox report script, you can quickly extract user sizes, quotas, and growth over time. This is invaluable for storage planning and policy enforcement. On Mr Microsoft, I’ve shared an easy-to-adapt script that pulls all mailbox data and exports it to CSV or Excel formats. You can automate it weekly, track long-term trends, or email the results to managers. It’s a simple but powerful reporting tool that turns Microsoft 365 data into actionable insights.
Parse and Report on Windows Event Logs
If you’re getting started with scripting, working with event logs is a fantastic entry point. Using PowerShell for beginners, you can write scripts that parse Windows logs to identify system crashes, login failures, or security events. I’ve built a script on Mr Microsoft that scans logs daily and sends summary reports. It’s lightweight, customizable, and useful for security monitoring. This is a perfect project for IT pros new to scripting who want meaningful results without complexity. With scheduled execution, this tool ensures proactive monitoring—especially critical in regulated or high-security environments.
Reset Passwords for Multiple Users
Resetting passwords one at a time is inefficient—especially during mass onboarding, offboarding, or policy enforcement. Using IT admin productivity tools like a PowerShell batch password reset script can streamline the process. It’s secure, scriptable, and ideal for both on-premises AD and hybrid Azure AD environments. With added functionality like expiration dates and enforced resets at next login, this script empowers IT admins to enforce password policies with speed and consistency.
Automate Windows Update Scheduling
If you’re tired of unpredictable updates or user complaints about restarts, this is for you. One of the most effective PowerShell scripts for IT admins automates the installation of Windows updates across workstations or servers. With this tool, you can check for updates, install them silently, and even reboot during off-hours. This reduces patching delays, improves compliance, and eliminates the need for manual updates or GPO complexity—especially useful in remote or hybrid work environments.
Cleanup Inactive Users with Graph API
Inactive user accounts are a security risk and resource drain. With the Microsoft Graph API, you can automate account cleanup based on login activity or license usage. My detailed Microsoft Graph API tutorial on Mr Microsoft walks through how to connect securely, pull activity data, and disable or archive stale accounts. This not only tightens security but also saves licensing costs. It’s a must-have script for admins managing large Microsoft 365 environments. Plus, the tutorial includes reusable templates to make your deployment faster and safer.
Automate SharePoint Site Provisioning
Provisioning SharePoint sites manually is tedious and error-prone. With Microsoft 365 automation, you can instantly create SharePoint sites based on predefined templates, permissions, and naming conventions. I’ve built a reusable script on Mr Microsoft that automates this entire process. It’s ideal for departments, projects, or onboarding flows where consistency and speed are critical. This script integrates with Teams and Exchange setups too, giving your IT team a full-stack provisioning workflow with minimal effort.
Final Thoughts – Automate Smarter, Not Harder
Every script above is built from real-life IT challenges I’ve encountered over the years. At Mr Microsoft, my goal is to share solutions that are practical, secure, and ready to use. Whether you're managing hundreds of users or optimizing workflows, automation is your edge—and PowerShell scripts for IT admins are your toolkit. Want more step-by-step guides and tools built by a fellow IT pro?
Visit MrMicrosoft.com and start automating smarter today.
1 note
·
View note
Text
Shielding Prompts from LLM Data Leaks
New Post has been published on https://thedigitalinsider.com/shielding-prompts-from-llm-data-leaks/
Shielding Prompts from LLM Data Leaks
Opinion An interesting IBM NeurIPS 2024 submission from late 2024 resurfaced on Arxiv last week. It proposes a system that can automatically intervene to protect users from submitting personal or sensitive information into a message when they are having a conversation with a Large Language Model (LLM) such as ChatGPT.
Mock-up examples used in a user study to determine the ways that people would prefer to interact with a prompt-intervention service. Source: https://arxiv.org/pdf/2502.18509
The mock-ups shown above were employed by the IBM researchers in a study to test potential user friction to this kind of ‘interference’.
Though scant details are given about the GUI implementation, we can assume that such functionality could either be incorporated into a browser plugin communicating with a local ‘firewall’ LLM framework; or that an application could be created that can hook directly into (for instance) the OpenAI API, effectively recreating OpenAI’s own downloadable standalone program for ChatGPT, but with extra safeguards.
That said, ChatGPT itself automatically self-censors responses to prompts that it perceives to contain critical information, such as banking details:
ChatGPT refuses to engage with prompts that contain perceived critical security information, such as bank details (the details in the prompt above are fictional and non-functional). Source: https://chatgpt.com/
However, ChatGPT is much more tolerant in regard to different types of personal information – even if disseminating such information in any way might not be in the user’s best interests (in this case perhaps for various reasons related to work and disclosure):
The example above is fictional, but ChatGPT does not hesitate to engage in a conversation on the user on a sensitive subject that constitutes a potential reputational or earnings risk (the example above is totally fictional).
In the above case, it might have been better to write: ‘What is the significance of a leukemia diagnosis on a person’s ability to write and on their mobility?’
The IBM project identifies and reinterprets such requests from a ‘personal’ to a ‘generic’ stance.
Schema for the IBM system, which uses local LLMs or NLP-based heuristics to identify sensitive material in potential prompts.
This assumes that material gathered by online LLMs, in this nascent stage of the public’s enthusiastic adoption of AI chat, will never feed through either to subsequent models or to later advertising frameworks that might exploit user-based search queries to provide potential targeted advertising.
Though no such system or arrangement is known to exist now, neither was such functionality yet available at the dawn of internet adoption in the early 1990s; since then, cross-domain sharing of information to feed personalized advertising has led to diverse scandals, as well as paranoia.
Therefore history suggests that it would be better to sanitize LLM prompt inputs now, before such data accrues at volume, and before our LLM-based submissions end up in permanent cyclic databases and/or models, or other information-based structures and schemas.
Remember Me?
One factor weighing against the use of ‘generic’ or sanitized LLM prompts is that, frankly, the facility to customize an expensive API-only LLM such as ChatGPT is quite compelling, at least at the current state of the art – but this can involve the long-term exposure of private information.
I frequently ask ChatGPT to help me formulate Windows PowerShell scripts and BAT files to automate processes, as well as on other technical matters. To this end, I find it useful that the system permanently memorize details about the hardware that I have available; my existing technical skill competencies (or lack thereof); and various other environmental factors and custom rules:
ChatGPT allows a user to develop a ‘cache’ of memories that will be applied when the system considers responses to future prompts.
Inevitably, this keeps information about me stored on external servers, subject to terms and conditions that may evolve over time, without any guarantee that OpenAI (though it could be any other major LLM provider) will respect the terms they set out.
In general, however, the capacity to build a cache of memories in ChatGPT is most useful because of the limited attention window of LLMs in general; without long-term (personalized) embeddings, the user feels, frustratingly, that they are conversing with a entity suffering from Anterograde amnesia.
It is difficult to say whether newer models will eventually become adequately performant to provide useful responses without the need to cache memories, or to create custom GPTs that are stored online.
Temporary Amnesia
Though one can make ChatGPT conversations ‘temporary’, it is useful to have the Chat history as a reference that can be distilled, when time allows, into a more coherent local record, perhaps on a note-taking platform; but in any case we cannot know exactly what happens to these ‘discarded’ chats (though OpenAI states they will not be used for training, it does not state that they are destroyed), based on the ChatGPT infrastructure. All we know is that chats no longer appear in our history when ‘Temporary chats’ is turned on in ChatGPT.
Various recent controversies indicate that API-based providers such as OpenAI should not necessarily be left in charge of protecting the user’s privacy, including the discovery of emergent memorization, signifying that larger LLMs are more likely to memorize some training examples in full, and increasing the risk of disclosure of user-specific data – among other public incidents that have persuaded a multitude of big-name companies, such as Samsung, to ban LLMs for internal company use.
Think Different
This tension between the extreme utility and the manifest potential risk of LLMs will need some inventive solutions – and the IBM proposal seems to be an interesting basic template in this line.
Three IBM-based reformulations that balance utility against data privacy. In the lowest (pink) band, we see a prompt that is beyond the system’s ability to sanitize in a meaningful way.
The IBM approach intercepts outgoing packets to an LLM at the network level, and rewrites them as necessary before the original can be submitted. The rather more elaborate GUI integrations seen at the start of the article are only illustrative of where such an approach could go, if developed.
Of course, without sufficient agency the user may not understand that they are getting a response to a slightly-altered reformulation of their original submission. This lack of transparency is equivalent to an operating system’s firewall blocking access to a website or service without informing the user, who may then erroneously seek out other causes for the problem.
Prompts as Security Liabilities
The prospect of ‘prompt intervention’ analogizes well to Windows OS security, which has evolved from a patchwork of (optionally installed) commercial products in the 1990s to a non-optional and rigidly-enforced suite of network defense tools that come as standard with a Windows installation, and which require some effort to turn off or de-intensify.
If prompt sanitization evolves as network firewalls did over the past 30 years, the IBM paper’s proposal could serve as a blueprint for the future: deploying a fully local LLM on the user’s machine to filter outgoing prompts directed at known LLM APIs. This system would naturally need to integrate GUI frameworks and notifications, giving users control – unless administrative policies override it, as often occurs in business environments.
The researchers conducted an analysis of an open-source version of the ShareGPT dataset to understand how often contextual privacy is violated in real-world scenarios.
Llama-3.1-405B-Instruct was employed as a ‘judge’ model to detect violations of contextual integrity. From a large set of conversations, a subset of single-turn conversations were analyzed based on length. The judge model then assessed the context, sensitive information, and necessity for task completion, leading to the identification of conversations containing potential contextual integrity violations.
A smaller subset of these conversations, which demonstrated definitive contextual privacy violations, were analyzed further.
The framework itself was implemented using models that are smaller than typical chat agents such as ChatGPT, to enable local deployment via Ollama.
Schema for the prompt intervention system.
The three LLMs evaluated were Mixtral-8x7B-Instruct-v0.1; Llama-3.1-8B-Instruct; and DeepSeek-R1-Distill-Llama-8B.
User prompts are processed by the framework in three stages: context identification; sensitive information classification; and reformulation.
Two approaches were implemented for sensitive information classification: dynamic and structured classification: dynamic classification determines the essential details based on their use within a specific conversation; structured classification allows for the specification of a pre-defined list of sensitive attributes that are always considered non-essential. The model reformulates the prompt if it detects non-essential sensitive details by either removing or rewording them to minimize privacy risks while maintaining usability.
Home Rules
Though structured classification as a concept is not well-illustrated in the IBM paper, it is most akin to the ‘Private Data Definitions’ method in the Private Prompts initiative, which provides a downloadable standalone program that can rewrite prompts – albeit without the ability to directly intervene at the network level, as the IBM approach does (instead the user must copy and paste the modified prompts).
The Private Prompts executable allows a list of alternate substitutions for user-input text.
In the above image, we can see that the Private Prompts user is able to program automated substitutions for instances of sensitive information. In both cases, for Private Prompts and the IBM method, it seems unlikely that a user with enough presence-of-mind and personal insight to curate such a list would actually need this product – though it could be built up over time as incidents accrue.
In an administrator role, structured classification could work as an imposed firewall or censor-net for employees; and in a home network it could, with some difficult adjustments, become a domestic network filter for all network users; but ultimately, this method is arguably redundant, since a user who could set this up properly could also self-censor effectively in the first place.
ChatGPT’s Opinion
Since ChatGPT recently launched its deep research tool for paid users, I used this facility to ask ChatGPT to review related literature and give me a ‘cynical’ take on IBM’s paper. I received the most defensive and derisive response the system has ever given when asked to evaluate or parse a new publication:
ChatGPT-4o has a low opinion of the IBM project.
‘If users don’t trust OpenAI, Google, or Anthropic to handle their data responsibly,’ ChatGPT posits. ‘why would they trust a third-party software layer sitting between them and the AI? The intermediary itself becomes a new point of failure—potentially logging, mishandling, or even leaking data before it ever reaches the LLM. It solves nothing if it just creates another entity to exploit user data.’
This objection seems self-serving and non-applicable, given the storied history of open source projects that genuinely benefit end-users through the concerted long-term efforts of community developers and contributors; and given the growing potential of mobile devices to run – and even train – lightweight LLMs. Certainly in this instance, the use case is not terribly demanding.
Next, ChatGPT confidently misses the point of having a lightweight LLM provide oversight of input towards a commercial LLM that could not possibly be run on a local machine (because the LLM is too big, and allowing local access is too risky for the company that makes it):
‘Effective privacy filtering requires understanding the input before deciding what to strip out. If an intermediary is smart enough to recognize sensitive data (names, addresses, financial details), then it’s already processing and analyzing that data—meaning it has to store or examine the very thing it’s supposed to erase.
‘This introduces a paradox: a) A dumb filter (basic regex substitution) will be ineffective and miss subtle privacy risks. b) A smart filter (LLM-powered rewriter) has to process the full input, making it just as dangerous as the original LLM.
‘If you trust the intermediary enough to read and rewrite your inputs, why not just trust the LLM itself?’
The answer to the final question here is that the local LLM is intended to be entirely on the side of the user, and inevitably open source, with minimal or zero need for network access. An equivalent commercial version, however well-intentioned at the outset, would eventually be vulnerable to corporate shifts and changes to the terms of service, whereas a suitable open source license would prevent this kind of ‘inevitable corruption’.
ChatGPT further argued that the IBM proposal ‘breaks user intent’, since it could reinterpret a prompt into an alternative that affects its utility. However, this is a much broader problem in prompt sanitization, and not specific to this particular use case.
In closing (ignoring its suggestion to use local LLMs ‘instead’, which is exactly what the IBM paper actually proposes), ChatGPT opined that the IBM method represents a barrier to adoption due to the ‘user friction’ of implementing warning and editing methods into a chat.
Here, ChatGPT may be right; but if significant pressure comes to bear because of further public incidents, or if profits in one geographical zone are threatened by growing regulation (and the company refuses to just abandon the affected region entirely), the history of consumer tech suggests that safeguards will eventually no longer be optional anyway.
Conclusion
We can’t realistically expect OpenAI to ever implement safeguards of the type that are proposed in the IBM paper, and in the central concept behind it; at least not effectively.
And certainly not globally; just as Apple blocks certain iPhone features in Europe, and LinkedIn has different rules for exploiting its users’ data in different countries, it’s reasonable to suggest that any AI company will default to the most profitable terms and conditions that are tolerable to any particular nation in which it operates – in each case, at the expense of the user’s right to data-privacy, as necessary.
First published Thursday, February 27, 2025
Updated Thursday, February 27, 2025 15:47:11 because of incorrect Apple-related link – MA
#2024#2025#adoption#advertising#agents#ai#ai chat#Analysis#Anderson's Angle#anthropic#API#APIs#apple#approach#arrangement#Art#Article#Artificial Intelligence#attention#attributes#ban#bank#banking#barrier#bat#blueprint#browser#Business#cache#chatGPT
0 notes
Text
How to Check Motherboard Model in Windows 10 – Easy & Quick Methods

When troubleshooting hardware issues, upgrading components, or checking compatibility, knowing your motherboard model is crucial. If you’re using Windows 10 and wondering, “How to check motherboard model in Windows 10?”, you’ve come to the right place.
In this guide, we’ll walk you through multiple methods to find your motherboard model without opening your PC. These methods work on Windows 7, Windows 10, and newer versions. Let’s dive in!
Why Do You Need to Check Your Motherboard Model?
Before we explore the methods, let’s understand why identifying your motherboard model is important:
✔ Upgrading Hardware – Check compatibility for CPU, RAM, or GPU upgrades. ✔ Driver Updates – Ensure you install the correct motherboard drivers. ✔ BIOS Updates – Find the right BIOS firmware for stability and performance. ✔ Troubleshooting Issues – Diagnose and fix hardware-related problems. ✔ Warranty and Support – Contact your manufacturer for warranty-related queries.
Now, let’s explore different methods to check the motherboard model in Windows 10.
1. How to Check Motherboard Model in Windows 10 Using Command Prompt
The easiest way to check your motherboard model in Windows 10 is by using Command Prompt. Follow these steps:
1️⃣ Press Win + R, type cmd, and hit Enter to open the Command Prompt. 2️⃣ Type the following command and press Enter:wmic baseboard get product,manufacturer,version,serialnumber
3️⃣ The manufacturer, model, version, and serial number of your motherboard will be displayed.
Example Output:Manufacturer Product Version SerialNumber ASUS PRIME B450M-A Rev 1.02 XXXXXXXXXXX
This method is quick and doesn’t require any third-party software.
2. How to Find Motherboard Model in Windows 10 Using System Information
Windows 10 has a built-in tool called System Information that can help you check your motherboard model.
1️⃣ Press Win + R, type msinfo32, and hit Enter. 2️⃣ In the System Summary, look for BaseBoard Manufacturer and BaseBoard Product. 3️⃣ This will display your motherboard’s brand and model.
🔹 If the motherboard model is missing, try other methods in this guide.
3. How to Check My Motherboard Model Using Windows PowerShell
PowerShell is another built-in Windows tool that helps retrieve system details.
1️⃣ Right-click on the Start menu and select Windows PowerShell (Admin). 2️⃣ Enter the following command:Get-WmiObject Win32_BaseBoard | Format-List Product,Manufacturer,SerialNumber,Version
3️⃣ Press Enter to get your motherboard details.
4. How to Check Motherboard Model in Windows 10 Using Third-Party Software
If you want a more detailed report of your motherboard, try using third-party tools like CPU-Z or Speccy.
Using CPU-Z
1️⃣ Download and install CPU-Z. 2️⃣ Open the program and go to the Mainboard tab. 3️⃣ Here, you’ll see the motherboard manufacturer, model, chipset, and BIOS version.
Using Speccy
1️⃣ Download Speccy and install it. 2️⃣ Open Speccy and navigate to Motherboard in the left menu. 3️⃣ You’ll find detailed information about your motherboard, including manufacturer, model, and version.
These tools provide more in-depth details about your motherboard and other hardware components.
5. How to Check Motherboard Model in Windows 7 & Older Versions
If you're running Windows 7, the steps are similar to Windows 10:
✔ Command Prompt – Use wmic baseboard get product,manufacturer,version,serialnumber. ✔ System Information – Open msinfo32 and check BaseBoard details. ✔ Third-Party Tools – CPU-Z and Speccy work on Windows 7 and Windows 10.
Windows 7 users may experience limitations in System Information, but the Command Prompt method works perfectly.
6. How to Check Motherboard Model If Windows Won’t Boot?
If your system isn’t booting, you can still find your motherboard model:
1️⃣ Check Your Motherboard – Look for the model name printed on the motherboard itself. 2️⃣ BIOS/UEFI Settings – Restart your PC and press F2, F10, or DEL to enter BIOS. The model is often displayed on the main screen. 3️⃣ Check the Packaging or Invoice – If you bought a prebuilt PC, the motherboard model is listed in the invoice or manual.
Final Thoughts
Knowing how to check your motherboard model in Windows 10 is essential for upgrades, troubleshooting, and driver updates. The Command Prompt, System Information, and PowerShell methods are the easiest ways to find motherboard details without additional software. If you need detailed hardware insights, third-party tools like CPU-Z and Speccy are excellent options.
Still have questions about your motherboard model? Visit Dell Laptop Service Center in Mumbai for expert guidance on hardware upgrades, repairs, and diagnostics.
📌 Need help? Contact our experts today! ✅
#MotherboardCheck#Windows10Tips#PCUpgrade#TechGuide#LaptopRepair#MotherboardModel#Windows7Help#HardwareCheck#BIOSUpdate#PCDiagnostics#DellService#TechSupport#ComputerRepair#SystemInfo#CheckMotherboard#PCMaintenance#LaptopUpgrades#TechSolutions#ComputerTips#WindowsHelp
0 notes
Text
🔧 Fix TLD_NOT_SUPPORTED WHOIS Error ⚡Quick & Easy Guide

Introduction
Running a WHOIS lookup and suddenly getting hit with the error "TLD_NOT_SUPPORTED" can feel frustrating—especially when you're just trying to grab some basic domain information. But don’t worry, this isn’t as complicated as it sounds. In this guide, I’ll break down why this error happens and, more importantly, how you can fix it. Let’s dive in and get your WHOIS queries back on track. 🚀
🔍 What Is a WHOIS Lookup, Anyway?
Before we jump into the solutions, let’s quickly cover the basics. A WHOIS lookup helps you find details about a domain name—like who owns it, when it expires, and where it’s registered. It’s super handy for everything from buying domains to cybersecurity checks. But sometimes, when you try to look up a domain, you might hit this error: "Failed to perform lookup using WHOIS service: TLD_NOT_SUPPORTED." This simply means the WHOIS tool doesn’t recognize or support the Top-Level Domain (TLD) of the domain you’re searching for. TLDs are the endings of domain names—like .com, .net, .org, or newer ones like .ai or .tech.
⚠️ Why Am I Seeing This Error?
There are a few reasons why this might be happening: - The domain extension (TLD) isn’t supported by the WHOIS tool you’re using. - Your WHOIS tool is outdated and doesn’t recognize newer TLDs. - The server for that specific TLD isn’t properly set up in your system. - Your network or firewall might be blocking the WHOIS service. - Certain TLDs have restrictions due to privacy laws like GDPR. The good news? Each of these issues has a fix. Let’s go through them step by step.
🔧 How to Fix the TLD_NOT_SUPPORTED Error
✅ 1. Double-Check the Domain Name The simplest solution is often the most overlooked. A typo in the domain name could be causing the issue—especially if you’re dealing with unfamiliar TLDs. Try this: - Make sure the domain is spelled correctly. - Verify that the TLD is valid. For example, .comm or .coom won’t work—only .com will. Still stuck? Move on to the next step. 🔄 2. Use an Updated WHOIS Tool If your WHOIS tool is outdated, it might not recognize newer TLDs like .ai, .dev, or .app. How to update your WHOIS client: - On Linux (Debian-based): sudo apt update && sudo apt upgrade whois - On Windows: - Use PowerShell to install a fresh WHOIS tool. - You can also try using third-party WHOIS applications like Sysinternals WHOIS. ⚙️ 3. Set Up the Correct WHOIS Server Not all WHOIS clients automatically know where to look for every TLD. You might need to manually point your tool to the right server. Here’s how: - Run a WHOIS command using the specific TLD server: whois -h whois.nic. example. 🔗 Example: For an .ai domain, type: whois -h whois.nic.ai example.ai - On Linux systems, you can also edit the configuration file (/etc/whois.conf) to add missing WHOIS servers permanently. 🔒 4. Check Your Firewall and Network Settings WHOIS lookups typically use port 43. If your network or firewall blocks this port, you won’t be able to run WHOIS queries. Here’s what you can do: - Try connecting through a VPN to bypass network restrictions. - Check your firewall settings and ensure port 43 is open for outgoing traffic. 🛡 5. Domain Registry Restrictions Some domains hide WHOIS data due to privacy laws, like GDPR. In such cases, your lookup might not return any information, even if the TLD is supported. Solution: - Use registrar-specific WHOIS lookup tools. For example: - GoDaddy WHOIS - Namecheap WHOIS - Contact the domain registrar directly for more information.
📋 Quick Troubleshooting Cheat Sheet
Problem Solution Incorrect or unsupported TLD Double-check the domain name and TLD Outdated WHOIS tool Update your WHOIS client Missing WHOIS server configuration Manually set the correct WHOIS server Firewall blocking WHOIS requests Use a VPN or unblock port 43 Privacy restrictions on domain Use the registrar’s WHOIS tool
🎨 Visual: How WHOIS Lookup Works
Here’s a simple illustration of the WHOIS lookup process and where things can go wrong: 🎨 (Image suggestion: A flow diagram showing a user sending a WHOIS request, the query traveling through the internet, hitting the WHOIS server, and either receiving the data or getting blocked due to TLD_NOT_SUPPORTED.)
💡 Final Thoughts
The "TLD_NOT_SUPPORTED" error can be annoying, but it’s usually easy to fix once you know what’s causing it. Whether it’s updating your WHOIS tool, checking your domain’s spelling, or tweaking network settings, one of these solutions should have you sorted in no time. Read the full article
0 notes