#getObject
Explore tagged Tumblr posts
Text
Integrating ROSA Applications with AWS Services (CS221)
As cloud-native architectures become the backbone of modern application deployments, combining the power of Red Hat OpenShift Service on AWS (ROSA) with native AWS services unlocks immense value for developers and DevOps teams alike. In this blog post, we explore how to integrate ROSA-hosted applications with AWS services to build scalable, secure, and cloud-optimized solutions — a key skill set emphasized in the CS221 course.
🚀 What is ROSA?
Red Hat OpenShift Service on AWS (ROSA) is a managed OpenShift platform that runs natively on AWS. It allows organizations to deploy Kubernetes-based applications while leveraging the scalability and global reach of AWS, without managing the underlying infrastructure.
With ROSA, you get:
Fully managed OpenShift clusters
Integrated with AWS IAM and billing
Access to AWS services like RDS, S3, DynamoDB, Lambda, etc.
Native CI/CD, container orchestration, and operator support
🧩 Why Integrate ROSA with AWS Services?
ROSA applications often need to interact with services like:
Amazon S3 for object storage
Amazon RDS or DynamoDB for database integration
Amazon SNS/SQS for messaging and queuing
AWS Secrets Manager or SSM Parameter Store for secrets management
Amazon CloudWatch for monitoring and logging
Integration enhances your application’s:
Scalability — Offload data, caching, messaging to AWS-native services
Security — Use IAM roles and policies for fine-grained access control
Resilience — Rely on AWS SLAs for critical components
Observability — Monitor and trace hybrid workloads via CloudWatch and X-Ray
🔐 IAM and Permissions: Secure Integration First
A crucial part of ROSA-AWS integration is managing IAM roles and policies securely.
Steps:
Create IAM Roles for Service Accounts (IRSA):
ROSA supports IAM Roles for Service Accounts, allowing pods to securely access AWS services without hardcoding credentials.
Attach IAM Policy to the Role:
Example: An application that uploads files to S3 will need the following permissions:{ "Effect": "Allow", "Action": ["s3:PutObject", "s3:GetObject"], "Resource": "arn:aws:s3:::my-bucket-name/*" }
Annotate OpenShift Service Account:
Use oc annotate to associate your OpenShift service account with the IAM role.
📦 Common Integration Use Cases
1. Storing App Logs in S3
Use a Fluentd or Loki pipeline to export logs from OpenShift to Amazon S3.
2. Connecting ROSA Apps to RDS
Applications can use standard drivers (PostgreSQL, MySQL) to connect to RDS endpoints — make sure to configure VPC and security groups appropriately.
3. Triggering AWS Lambda from ROSA
Set up an API Gateway or SNS topic to allow OpenShift applications to invoke serverless functions in AWS for batch processing or asynchronous tasks.
4. Using AWS Secrets Manager
Mount secrets securely in pods using CSI drivers or inject them using operators.
🛠 Hands-On Example: Accessing S3 from ROSA Pod
Here’s a quick walkthrough:
Create an IAM Role with S3 permissions.
Associate the role with a Kubernetes service account.
Deploy your pod using that service account.
Use AWS SDK (e.g., boto3 for Python) inside your app to access S3.
oc create sa s3-access oc annotate sa s3-access eks.amazonaws.com/role-arn=arn:aws:iam::<account-id>:role/S3AccessRole
Then reference s3-access in your pod’s YAML.
📚 ROSA CS221 Course Highlights
The CS221 course from Red Hat focuses on:
Configuring service accounts and roles
Setting up secure access to AWS services
Using OpenShift tools and operators to manage external integrations
Best practices for hybrid cloud observability and logging
It’s a great choice for developers, cloud engineers, and architects aiming to harness the full potential of ROSA + AWS.
✅ Final Thoughts
Integrating ROSA with AWS services enables teams to build robust, cloud-native applications using best-in-class tools from both Red Hat and AWS. Whether it's persistent storage, messaging, serverless computing, or monitoring — AWS services complement ROSA perfectly.
Mastering these integrations through real-world use cases or formal training (like CS221) can significantly uplift your DevOps capabilities in hybrid cloud environments.
Looking to Learn or Deploy ROSA with AWS?
HawkStack Technologies offers hands-on training, consulting, and ROSA deployment support. For more details www.hawkstack.com
0 notes
Text
AWS × Sumologic連携ガイド - セットアップから運用のベストプラクティスまで
AWS環境でのSumologicコレクター導入手順 Sumologicは、AWSのログを一元管理する優れたソリューションです。 AWS環境へのSumologicコレクターの導入は、IAMロールの作成から開始します。 AWS Management Consoleにログインし、IAMロールを作成します。 { "Version": "2012-10-17", "Statement": [ { "Effect": "Allow", "Action": [ "s3:GetObject", "s3:ListBucket" ], "Resource":…
0 notes
Text
i ported creep to javascript
const before = Date.now() - 1; if(Date.now() = before && isHere(this.you)){ this.you.lookInEye = !could; } this.you.type = "angel"; if((you.skin)){ cry() } if(world.beauty > 1){ const feather = 0.5; this.you.gravity.scale = feather; } this.wishes.push("special"); this.you.special = 10000; this.creep = true; this.weirdo = true; if(doingHere(this)); if(this.belong == herePostion){ this.belong = [0,0]; } this.cares = this.cares.filter(item => item !== "hurt"); this.wishes.push("control", "perfect body", "perfect soul"); if(getDistance(this.position, you.position) > 1200){ you.notice(this); } this.you.special = 10000; this.wishes.push("special"); this.creep = true; this.weirdo = true; if(doingHere(this)); if(this.belong == herePostion){ this.belong = [0,0]; } let she = this.you; she.runData.position = getObject("door"); for(let i = 0; i < 6; i++){ she.run(); } console.log(this.you.happyTriggers); console.log(this.you.wishes); this.you.special = 10000; this.wishes.push("special"); this.creep = true; this.weirdo = true; if(doingHere(this)); if(this.belong == herePostion){ this.belong = [0,0]; } if(this.belong == herePostion){ this.belong = [0,0]; }
1 note
·
View note
Text
SSE-KMS Support Available For Amazon S3 Express One Zone

Amazon Key Management Service (KMS) keys can now be used for server-side encryption with Amazon S3 Express One Zone, a high-performance, single-Availability Zone (AZ) S3 storage class (SSE-KMS). All items kept in S3 directory buckets are already encrypted by default by S3 Express One Zone using Amazon S3 management keys (SSE-S3). As of right now, data at rest can be encrypted using AWS KMS customer managed keys without affecting speed. With the help of this new encryption feature, you may use S3 Express One Zone which is intended to provide reliable single-digit millisecond data access for your most frequently accessed data and latency-sensitive applications to further satisfy compliance and regulatory standards.
For SSE-KMS encryption, S3 directory buckets let you define a single customer controlled key per bucket. You cannot change it to use a different key once the customer managed key has been inserted. Conversely, S3 general purpose buckets allow you to use several KMS keys during S3 PUT requests or by modifying the bucket’s default encryption configuration. S3 Bucket Keys are always enabled when utilizing SSE-KMS with S3 Express One Zone. Free S3 bucket keys can minimize AWS KMS queries by up to 99%, improving efficiency and lowering expenses.
Utilizing Amazon S3 Express One Zone with SSE-KMS
First construct an S3 directory bucket in the Amazon S3 console by following the instructions, and you can use apne1-az4 as the Availability Zone, to demonstrate this new functionality to you. To construct the final name, you automatically add the Availability Zone ID to the suffix you enter in the Base name, which is s3express-kms. Then confirm that Data is stored in a single Availability Zone by checking the corresponding checkbox.
Select Server-side encryption using AWS Key Management Service keys (SSE-KMS) under the Default encryption option. You have three options under AWS KMS Key: Create a KMS key, Enter AWS KMS key ARN, or Select from your AWS KMS keys. In this case, you choose to Create bucket after choosing from a list of previously established AWS KMS keys.
You can now automatically encrypt any new object you upload to this S3 directory bucket using my Amazon KMS key.
SSE-KMS in operation with Amazon S3 Express One Zone
You require an AWS Identity and Access Management (IAM) user or role with the following policy in order to use SSE-KMS with S3 Express One Zone using the AWS Command Line Interface (AWS CLI). In order to successfully upload and receive encrypted data to and from your S3 directory bucket, this policy permits the CreateSession API function.
Using the HeadObject command to examine the object’s properties, you can see that it is encrypted using SSE-KMS and my previously generated key:
You can use GetObject to download the encrypted object:
The object downloads and decrypts itself because your session has the required rights.
Use a separate IAM user with a policy who isn’t allowed the required KMS key rights to download the item for this second test. The SSE-KMS encryption is operating as planned, as seen by the AccessDenied error that occurs during this attempt.
Important information
Beginning the process The AWS SDKs, AWS CLI, or the Amazon S3 console can all be used to enable SSE-KMS for S3 Express One Zone. Assign your AWS KMS key and change the S3 directory bucket’s default encryption option to SSE-KMS. Recall that over the lifespan of an S3 directory bucket, only one customer controlled key may be used.
Regions: Every AWS Region where S3 Express One Zone is presently offered offers support for SSE-KMS utilizing customer-managed keys.
Performance: Request latency is unaffected by using SSE-KMS with S3 Express One Zone. The same single-digit millisecond data access will be available to you.
Pricing: To generate and recover data keys used for encryption and decryption, you must pay AWS KMS fees. For additional information, see the pricing page for AWS KMS. Furthermore, S3 Bucket Keys are enabled by default for all data plane operations aside from CopyObject and UploadPartCopy when utilizing SSE-KMS with S3 Express One Zone, and they cannot be removed. By doing this, AWS KMS request volume is lowered by up to 99%, improving both performance and cost-effectiveness.
Read more on Govindhtech.com
#SSEKMS#AmazonS3#AmazonS3ExpressOneZone#Amazon#S3Bucket#KeyManagementService#AmazonS3console#News#Technews#technology#technologynews#technologytrends#govindhtech
0 notes
Text
Updating Active Directory Computer Description Using SCCM and MDT

Updating Active Directory Computer Description Using SCCM and MDT | https://tinyurl.com/24m5azav | #Guide #MDT #OSD #SCCM You may have seen our previous post on how to set the local computer description during SCCM OSD (Operating System Deployment). Now, with the help of a script and Microsoft Deployment Toolkit (MDT), we can take that local computer description and use it as the Active Directory (AD) computer description. Required Script To achieve this, you’ll need the following script: strModel = GetModelInfostrLocalDescription = GetLocalDescriptionstrDescription = strLocalDescription & ” – ” & strModelUpdateAD Function GetModelInfostrComputer = “.”Set objWMIService = GetObject(“winmgmts:impersonationLevel=impersonate!” & strComputer & “\root\cimv2”)Set colItems = objWMIService.ExecQuery(“Select * from Win32_ComputerSystem”)For Each objItem in colItemsGetModelInfo = objItem.ModelNextEnd Function Function GetLocalDescriptionstrComputer = […] Read more... https://tinyurl.com/24m5azav
0 notes
Text
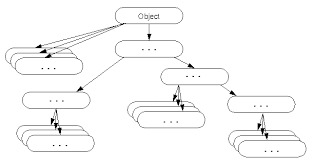
Object class in Java
The Object class is the parent class of all the classes in java by default. In other words, it is the topmost class of java.
The Object class is beneficial if you want to refer any object whose type you don't know. Notice that parent class reference variable can refer the child class object, know as upcasting.
Let's take an example, there is getObject() method that returns an object but it can be of any type like Employee,Student etc, we can use Object class reference to refer that object. For example:
0 notes
Text
Create a shortcut with script
Create a shortcut with script
I create a shortcut with a script, but why? Some applications do not know the cause, do not create a shortcut during installation or after installation. The following Script allows you to create shortcuts with the variables entered.

The shortcut name, shortcut path, file name of the target application, shortcut icon, and system architecture are automatically selected.

‘Script Started
‘Option…
View On WordPress
#architecture#chrome#cimv2#colItems#create#CreateObject#ExecQuery#GetObject#google#key#microsoft#name#objDesktop#objItem#objLink#objShell#objWMIService#path#registry#registrykey#root#script#Shell#shortcut#strAppPath#strComputer#strDesc#strWorkDir#SystemType#vbs
1 note
·
View note
Text
I'm making slow but consistent progress in attempting to decipher this mess of unused and redundant code
Me: y'know what? fuck it, I'll start working on my old game again
Me, moments after looking at my old code: Oh God
Me: y'know what? fuck it, I'm rebuilding my game (effectively) from the ground up
10 notes
·
View notes
Photo




#CorpMedia #Idiocracy #Oligarchs #MegaBanks vs #Union #Occupy #NoDAPL #BLM #SDF #DACA #MeToo #Humanity #DemExit #FeelTheBern
Nobody familiar with Michigan's Emergency Manager Law, should be at all surprised by what happened on 6 January 2021 - It's not just a few bad apples
Overview: https://www.aclumich.org/en/cases/emergency-manager-law
Full text: http://www.legislature.mi.gov/(S(40axn4mhule2iqmyhfxim0ms))/mileg.aspx?page=getObject&objectName=mcl-141-1549
2 notes
·
View notes
Text
Jonathan Vanderhagen is a father. One who did nothing more than criticize a judge, and now he's imprisoned facing a trial presided over by a judge who was complicit in violation the rights he has guaranteed by the Constition of the United States of America. Following the death of Mr. Jonathan Vanderhagen's son, Killian Vanderhagen (2 Years Old), Mr. Vanderhagen began to criticize the court which issued the ruling refusing to grant him physical custody of his son. Mr. Vanderhagen believes the court responsible, at least in part, for his son's death. Whether Mr. Vanderhagen is correct in his assertion or not, it is despicable his being jailed over his criticisms of the 16th Circuit and, more narrowly, Judge Rachel Rancilio. The details as reported are as follows; "Following the death of Killian Vanderhagen, his father, Jonathan Vanderhagen, was incensed that the child was placed in the custody of his ex-wife, who he felt was unfit, and when his child died, he began posting his criticisms of the system, and Judge Rancilo, who he felt was responsible for his child’s death, and promising, “I’m gonna dig up all the skeletons in this court’s closet.”
(An investigation did not indicate that the mother caused the death) The judge claimed to feel threatened, and referred the matter to police, who found no threat, but for "some reason" he was charged with “malicious use of telecommunications services,” and released on $2000 bond. When he continued his criticisms, his bond was revoked, and now he is sitting in jail on $500,000 bond."
Below is a link to the Michigan code covering the alleged crime that Mr. Vanderhagen has been imprisoned for: http://www.legislature.mi.gov/(S(sbjoqm0dgdoydkfbbfencgbg))/mileg.aspx?page=getobject&objectname=mcl-750-540e A $500,000 bond for a misdemeanor with a maximum fine of $1000 points to judicial impropriety, and retaliation- not justice. This bond was set by Judge Sebastian Lucido- another elected Judge. We assert that this too is a violation of Mr. Vanderhagen's constitutional rights. The U.S. Supreme court's opinion in Weems V. United States (1910) dissented from the lower court based on the principle of proportionality in defense of the 8th Ammendment.
While Judge Lucido contended in court that Mr. Vanderhagen violated the terms of his bond, his initial arrest had no merit in the first place and his confinement was, in essence, an authoritarian attempt by local officials to suppress Mr. Vanderhagen's freedom of expression. This stands in violation of the first amendment of the constitution of the United States, which calls into question the legality of the terms of the bond he allegedly violated. Finally, if it is Judge Rancilio's opinion that her interpretation of the law being used to jail Mr. Vanderhagen as well as the way that she is using her power to influence its enforcement is true and just, she lacks the common sense and decency to sit the bench. Help him fight this abuse and injustice by contributing to his legal defense team. He deserves our support, and we demand justice.
44 notes
·
View notes
Text
Spring : afterPropertiesSet , getObject
afterPropertiesSet : getObject 의해 실행되거나 getObject 가 실행되기 전에 할 일들을 처리한다.
getObject 는 @Bean 에 의해 실행된다. 대신 반환 객체가 있기 때문에 반환하지 않아되 된다면 afterPropertiesSet 이용하여 처리한다.
0 notes
Text
Okay, with a little digging i found the bills that are being approved with each statement.
TL:DR
these aren’t laws just yet, but there is an extremely good chance these all pass. Repeal of the “right-to-work” law: House Bill 4004 http://www.legislature.mi.gov/(S(difphv34nnbd2rfwadzddyzt))/mileg.aspx?page=GetObject&objectname=2023-HB-4004 it passed our house and senate, so it’s off to the governess’ office where she will most likely sign off on the bill making it a law. Repeal of the 1931 abortion law: Senate Bill 0039 http://www.legislature.mi.gov/(S(0ycy2h04zulp5h0wcanppvg1))/mileg.aspx?page=GetObject&objectname=2023-SB-0039 we had a vote to repeal the 1931 abortion law and put in our constitution that the right to an abortion is a right, this passed 56-43 and has passed our senate but oddly not yet our house. however with the democrats in control of the house, senate, and governess it most likely will pass into law. Universal background checks on gun/firearm sales: House Bill 4138 https://www.legislature.mi.gov/(S(ignsxrlkyp41g2qchss0zobj))/mileg.aspx?page=GetObject&objectname=2023-HB-4138 it has passed our house and is onto our senate. as i said before the democrats control all three branches of the state government so it too will most likely pass into law. LGBTQ anti-discrimination law: Senate Bill 0004 http://www.legislature.mi.gov/(S(ogvxcsppzbimxtyvdyzbzyj4))/mileg.aspx?page=GetObject&objectname=2023-SB-0004 this bill has passed both the house and senate. it now has gotten to Michigan’s governess to sign it into law today at 11:19am.
Michigan Democrats have had a truly incredible afternoon: they've ended the state's anti-union "right to work" law, repealed an abortion ban from 1931, enacted universal background checks on gun sales, and passed an LGBTQ anti-discrimination law. All in the last 24 hours
#Michigan#politics#labor laws#abortion#gun control#queer rights#not going to lie it is a great time to be from michigan right now
63K notes
·
View notes
Text
Quinn’s Code - The Esteemsters Code - Part 8
Thursday, September 23. 2005
Daria and Jennifer entered Jane's room with takeaway breakfast. Jane was watching a tabloid show on the TV.
“This is just astounding! Here you are, blind, deaf, and barely able to walk, yet you conducted simultaneous affairs with three members of the Royal Family! The question on all of America's mind is: how did you do it?”
“What?”
“You don't get it. It's the Royal Family. You'd have to be blind,” Jane said as commentary.
“Hi Jane, is that Sick Sad World? I was wondering when it was on here,” Daria said.
“Hey Amigos,” Jane said. “Yeah, its on in the morning, although I have heard that they are going to change it to the afternoon,” Jane said.
“Quite an interesting show,” Jennifer said.
“Definitely,” Daria said. She and Jennifer sat down next to Jane. The scene on the TV had changed to a UFO convention that was being held close to Lawndale.
“Hi! I'm Artie.”
“Artie, hello. Tell me, what brought you here, Artie.”
“It was a cone-shaped craft about 15 feet long, with an air speed of, oh, I'd estimate mach 12. They kidnapped and stripped me, examined me briefly, returned my clothes, and dropped me here.”
“I see.”
“They pressed my pants. Did a nice job.”
Daria turned down the TV. “You both know all the answers to the questions on the release test, right?”
“I've got them in my notebook,” Jane said.
“I do too,” Jennifer said.
“Well, why don't we just take the test this afternoon and get out of the class once and for all?” Daria asked.
“How would I spend my afternoons?” Jane asked. 'I would have more time to paint, that is for sure!' she thought.
“UFO conventions,” Daria said. 'I can think of many activities. Not the least of which is exploring what this town has to offer that I would like,' she thought.
“Now you're talking,” Jane said.
“Yes!” Jennifer said.
“And so, for tomorrow, I want you to make a list of ten ways the world would be a sadder place if you weren't in it,” Mr. O'Niell said as conclusion for that day's session of the Esteem-a-Teen class.
“Oh, Mr. O'Neill, Mr. O'Neill?!” 'The Head' asked, waving his hands, trying to get the teacher's attention.
“Yes, um... you.”
“Is that if we'd never been born, or if we died suddenly and unexpectedly?”
“'Oh no!' Mr. O'Neill thought. 'I didn't expect that!' he thought for a moment, trying to salvage the situation. “Never been born,” he said.
The class started filing out, except for Daria, Jane and Jennifer.
“Yes?” Mr. O'Neill asked.
“We want to take the test,” Daria said.
“We all want to take the graduation test,” Jane said.
Jennifer gave a small smile.
“Well! I'm glad your self-image meter is on the uptick! But there's still three more weeks of class left,” Mr O'Neill said. 'They need to stay in the class for the whole time to get everything out of it,' he thought.
“This first week has been a real eye-opener. It must be the way you teach,” Daria said.
Mr. O'Neill was flattered. “Oh, well... thank you very much,” he said. “You look familiar somehow,” he said to Jane and Jennifer.
“So can we take the test?” Jennifer asked.
Mr. O'Neill gave in and gave them the test.
“I don't think we have to go any farther. I am really pleased! I think the whole school needs to hear about this at assembly!” Mr. O'Neill said a few minutes later.
The three teens looked at each other. Their expressions said the same thing. 'Uh, oh!'
Andrea looked at the VBScript code on the screen.
Option Explicit
Set oWMI = GetObject("winmgmts:" & _
"\\.\root\cimv2")
Set myObj = oWMI.ExecQuery _
("select IPAddress from" & _
"Win32_NetworkAdapterConfiguration" & _
" where IPEnabled=True")
…
“That is rather good, Quinn,” she said. It looked exactly as the flowchart and the pseudocode had laid out. “You can run it now,” she said. 'I am certain that there are no errors. I think she corrected them all in that proofreading,' she thought.
Quinn minimised the IDE screen and double clicked the .vbs file. The script ran without error and a drive letter on Quinn's XP system was mapped to one of Andrea's network shares.
“Cool!” Quinn said.
Andrea smiled. 'If she is this good at VBScript...'
“So I delete it now?” Quinn asked, about the connection to the network share.
“No, keep it. All the members of the Programming Club have the connection. Its a common file repository. As long as you are on my network. It's accessable,” Andrea said.
“So, if I use a VPN to connect to it, the share is available?” Quinn asked, wondering why Andrea had a share that all of the Programming Club members could access...
“Yes,” Andrea said.
'She is up to something. It may be worth joining the Anime Club, afterall,' Quinn thought, as she started closing the programs on the laptop.
Friday, September 24, 2005
Quinn entered homeroom carrying the information sheet on the Anime Club. As she had expected the person whom had invited her to join was the President. 'Jenna Schwartz, she's a sophomore. I'll talk to her at recess.'
Jenna Schwartz was surprised when Quinn Morgendorffer walked up to her in the corridor.
“Hi, Jenna. I would like to take up your offer to join the Anime Club,” Quinn said.
“That would be cool, Quinn. But why did it take so long to decide?�� Jenna asked.
“I wasn't sure if I wanted to be in a third club, but I do like Anime so the Anime Club is a good choice. Also, that Andrea is so weird,” Quinn said.
Jenna chuckled. “She definitely is. Come with me and I will give you a form. Once its filled out, you're in,” she said.
“Cool,” she said.
Unknown to Quinn and Jenna, Stacy Rowe had overheard them from her locker. 'The Anime Club. If Sandi wasn't such a hardcase about things, I would have joined a few weeks ago,' she thought. She closed her locker and headed to the bathroom where Sandi and Tiffany were waiting for her.
The end of week school assembly was in progress.
“And once again, the bake sale was a tremendous success. We raised more than $400, which was subsequently stolen from the office, but I am confident we will get that money back. In a related note, the school nurse will be visiting homerooms on Monday to collect DNA samples. Now, Mr. O'Neill has exciting news about our after-school self-esteem class,” Principal Angela Li said.
Mr. O'Neill stood and approached the podium.
“This is really going to help me gradually ease into student life,” Daria said, sarcastically.
“Usually when I have this dream I'm wearing pink taffeta,” Jane commented.
“I always wanted to be on assembly. Not!” Jennifer said.
“Thank you. You know, self-esteem is a little like your car's brake fluid. You may not even know you're low on it until, one day, you go to shift gears and nothing happens,” Mr. O'Neill said.
“That's transmission fluid!” One of the students in the audience yelled.
“That's... what I said,” Mr. O'Neill said, trying to cover his mistake. “Anyway, I'd like you to meet three students who have completed our self-esteem course faster than anyone ever before! Please join me in congratulations as I present these certificates of self-esteem to... Daria Morgendorffer, Jane Lane and Jennifer Burns.”
There was some applause from the audience, but not much.
“Oh, what the hell,” Jane muttered as she stepped up to the podium. “I just want to say how proud I am today. Knowing that I have self-esteem gives me even more self-esteem.” She paused, looked at Daria and Jennifer and smirked. “On the other hand, having all of you know that I had low self-esteem makes me feel... kind of bad... like a big failure or something...” she said histronically.
Most of the audience began to laugh at Jane's behaviour.
“I, uh, I want to go home!” Jane said, as she let out an exaggerated sob and ran off the stage.
“Jennifer, wait!” Mr. O'Neill called out as he ran after Jane.
'That's Ms. Lane, not Ms. Burns!' Ms. Li thought, she knew that Jane was faking it even if her head Language Arts teacher didn't!
Jennifer stepped up to the podium with trepidation. There was a reason why Jodie always read the reports for the Computer Club at assemblies.
“Thank you. I am happy to have high self-esteem rather than low self-esteem. I feel I can better contribute. Thanks again,” she said. She walked away from the podium and breathed a sigh of relief. She glanced at the audience.
She could see Jodie, Mack, Quinn, Kristen, Cindy, a few other friends, members of the Computer Club and a few others clapping. She smiled as she went back to her seat.
Daria stepped up to the podium. “No one can battle a terrible problem like low self-esteem on their own. It takes good coaching... “
In the audience, Sandi was sitting boredly between two boys. 'This is stupid!' she thought.
“Who cares about these losers?” one of them said.
“Hey, beats algebra, though, doesn't it?” the other, Corey Bateman said. He then high-fived his friend over the top of Sandi's head.
“Hey!” she snapped.
“Oops,” the other said.
“Did you hear what I said, Sandi? I said, like, who cares how bad this is - it's still better than algebra!” Corey said.
“I, like, heard you the first time, Corey. I't's not funny!” Sandi said forcefully. 'Of course its better than algebra!' she thought.
“Ok,” Corey said, leaning slightly away from Sandi.
#andrea hecuba#angela li#daria#daria morgendorffer#esteemsters#fanfic#jane lane#quinn morgendorffer#sandi griffin#stacy rowe#timothy o'neill
1 note
·
View note
Text
AWS CloudTrail Monitors S3 Express One Zone Data Events

AWS CloudTrail
AWS CloudTrail is used to keep track of data events that occur in the Amazon S3 Express One Zone.
AWS introduced you to Amazon S3 Express One Zone, a single-Availability Zone (AZ) storage class designed to provide constant single-digit millisecond data access for your most frequently accessed data and latency-sensitive applications. It is intended to provide up to ten times higher performance than S3 Standard and is ideally suited for demanding applications. S3 directory buckets are used by S3 Express One Zone to store items in a single AZ.
In addition to bucket-level activities like CreateBucket and DeleteBucket that were previously supported, S3 Express One Zone now supports AWS CloudTrail data event logging, enabling you to monitor all object-level operations like PutObject, GetObject, and DeleteObject. In addition to allowing you to benefit from S3 Express One Zone’s 50% cheaper request costs than the S3 Standard storage class, this also enables auditing for governance and compliance.
This new feature allows you to easily identify the source of the API calls and immediately ascertain which S3 Express One Zone items were created, read, updated, or removed. You can immediately take steps to block access if you find evidence of unauthorised S3 Express One Zone object access. Moreover, rule-based processes that are activated by data events can be created using the CloudTrail connection with Amazon EventBridge.
S3 Express One Zone data events logging with CloudTrail
You open the Amazon S3 console first. You will make an S3 bucket by following the instructions for creating a directory bucket, selecting Directory as the bucket type and apne1-az4 as the availability zone. You can type s3express-one-zone-cloudtrail in the Base Name field, and the Availability Zone ID of the Availability Zone is automatically appended as a suffix to produce the final name. Lastly, you click Create bucket and tick the box indicating that data is kept in a single availability zone.
Now you open the CloudTrail console and enable data event tracking for S3 Express One Zone. You put in the name and start the CloudTrail trail that monitors my S3 directory bucket’s activities.
You can choose Data events with Advanced event pickers enabled under Step 2: Choose log events.
S3 Express is the data event type you have selected. To manage data events for every S3 directory bucket, you can select Log all events as my log selector template.
But you just want events for my S3 directory bucket, s3express-one-zone-cloudtrail–apne1-az4–x-s3, to be logged by the event data store. Here, you specify the ARN of my directory bucket and pick Custom as the log selection template.
Complete Step 3 by reviewing and creating. You currently have CloudTrail configured for logging.
S3 Express One Zone data event tracking with CloudTrail in action
You retrieve and upload files to my S3 directory bucket using the S3 interface
Log files are published by CloudTrail to an S3 bucket in a gzip archive, where they are arranged in a hierarchical structure according to the bucket name, account ID, region, and date. You list the bucket connected to my Trail and get the log files for the test date using the AWS CLI.
Let’s look over these files for the PutObject event. You can see the PutObject event type when you open the first file. As you remember, you only uploaded twice: once through the CLI and once through the S3 console in a web browser. This event relates to my upload using the S3 console because the userAgent property, which indicates the type of source that made the API call, points to a browser.
Upon examining the third file pertaining to the event that corresponds to the PutObject command issued through the AWS CLI, I have noticed a slight variation in the userAgent attribute. It alludes to the AWS CLI in this instance.
Let’s now examine the GetObject event found in file number two. This event appears to be related to my download via the S3 console, as you can see that the event type is GetObject and the userAgent relates to a browser.
Let me now demonstrate the event in the fourth file, including specifics about the GetObject command you issued using the AWS CLI. The eventName and userAgent appear to be as intended.
Important information
Starting out The CloudTrail console, CLI, or SDKs can be used to setup CloudTrail data event tracking for S3 Express One Zone.
Regions: All AWS Regions with current availability for S3 Express One Zone can use CloudTrail data event logging.
Activity tracking: You may record object-level actions like Put, Get, and Delete objects as well as bucket-level actions like CreateBucket and DeleteBucket using CloudTrail data event logging for S3 Express One Zone.
CloudTrail pricing
Cost: Just like other S3 storage classes, the amount you pay for S3 Express One Zone data event logging in CloudTrail is determined by how many events you log and how long you keep the logs. Visit the AWS CloudTrail Pricing page to learn more.
For S3 Express One Zone, you may activate CloudTrail data event logging to streamline governance and compliance for your high-performance storage.
Read more on Govindhtech.com
#dataevents#awscloudtrail#AmazonS3#availabilityzone#createbucket#deletebucket#API#AWSCLI#NEWS#technology#technologynews#technologytrends#govindhtech
0 notes
Text
たった1行でPower Automate for desktop(PAD)から自由自在にExcelを操作できるスクリプトの紹介
[たった1行でPower Automate for desktop(PAD)から自由自在にExcelを操作できるスクリプトの紹介]
※ 本記事は「RPA(ロボティック・プロセス・オートメーション) Advent Calendar 2022」23日目(カレンダー2)の記事となります。 12月23日、RPACommunity主催で「【自動化やIT活用ネタ】ライトニングトーク大会 X’masスペシャル!」が開催されました。 GetObject(, "Excel.Application").CommandBars.ExecuteMso "ClearAll"[/vb] 上記スクリプトでは、 起動中のExcelを取得(GetObject(,…

View On WordPress
0 notes
Text
Stretchblt copyimage

#STRETCHBLT COPYIMAGE WINDOWS#
Merges the colors of the source rectangle with the brush currently selected in hdcDest, by using the Boolean AND operator. Note that this generally cannot be used for printing device contexts. By default, the image only contains your window.
#STRETCHBLT COPYIMAGE WINDOWS#
Includes any windows that are layered on top of your window in the resulting image. (This color is black for the default physical palette.) Valueįills the destination rectangle using the color associated with index 0 in the physical palette. The following list shows some common raster operation codes. These codes define how the color data for the source rectangle is to be combined with the color data for the destination rectangle to achieve the final color. The y-coordinate, in logical units, of the upper-left corner of the source rectangle.Ī raster-operation code. The x-coordinate, in logical units, of the upper-left corner of the source rectangle. The height, in logical units, of the source and the destination rectangles. The width, in logical units, of the source and destination rectangles. The y-coordinate, in logical units, of the upper-left corner of the destination rectangle. The x-coordinate, in logical units, of the upper-left corner of the destination rectangle. Syntax BOOL BitBlt(Ī handle to the destination device context. When you load the icon or cursor, the application asks for the size that the GetSystemMetrics() suggests the system then picks the closest image and scales if necessary.The BitBlt function performs a bit-block transfer of the color data corresponding to a rectangle of pixels from the specified source device context into a destination device context. cur formats are capable of storing multiple images in a single file. (GDI+ offers additional stretching options see the GDI+ section.) Use SetStretchBltMode() to change between stretching modes:Īn alternative to scaling is using multiple images, each designed for a different DPI. HALFTONE stretching is slower, but provides much higher quality. The default stretching mode, COLORONCOLOR, is fast but loses a lot of details. This is most noticeable when scaling from a small DPI to a large one, but scaling down also has problems the details the scaling algorithm chooses to keep are not necessarily the details you would choose. Scaling does degrade the quality of the image. HdcBitmap, 0, 0, info.bmWidth, info.bmHeight, SRCCOPY) DeleteDC(hdcBitmap) SCALEX(info.bmWidth), SCALEY(info.bmHeight), HDC hdcBitmap = CreateCompatibleDC(target) GetObject(bitmap, sizeof(info), (PTSTR) &info) This example takes a bitmap designed for 96 DPI, and draws it scaled: StretchBlt can be used to do this, as well. It’s often easier for the application to scale the image when it is loaded, rather than scaling when the image is drawn. You can scale a bitmap by calling StretchBlt() instead of BitBlt(). If the display’s DPI is not the same as the DPI for which the image was designed, the image needs to be scaled in order to appear the correct physical size. Images are more difficult to deal with than fonts, since images consist of discrete pixels. “Images” covers all raster-based image files (such as BMP, JPEG, and GIF), icons, and cursors.

0 notes