#google oauth
Explore tagged Tumblr posts
Text
WOM: Restaurant Discovery app for iOS: Google OAuth Consent Screen: Incorrect App Name of wom.auth.us-east-1.amazoncognito.com
iOS 18.3.1
WOM: Restaurant Discovery app for iOS (version 2.4.0)
03/03/2025
Description:
The WOM: Restaurant Discovery app for iOS has a problem. The WOM: Restaurant Discovery app has a Google OAuth screen.
Unfortunately, on this Google OAuth consent screen, the app name is incorrect. Instead of displaying an app name appropriate to the app, an app name of: "wom.auth.us-east-1.amazoncognito.com" appears.
Here's a screenshot of how it currently appears:

Steps to Reproduce:
1. Download and launch the WOM: Restaurant Discovery app for iOS
2. Select the app icon in the upper right of the screen
3. Select "Sign Up"
4. From the "Sign Up" pop-up menu, select "Google"
5. On the Google Sign in screen, note the app name of: "wom.auth.us-east-1.amazoncognito.com"
Result: The Google OAuth consent screen displayed by the WOM: Restaurant Discovery app displays an app name of: "wom.auth.us-east-1.amazoncognito.com"Expected: An app name of "wom.auth.us-east-1.amazoncognito.com" isn't user friendly and doesn't provide relevant information to the end user

After launching the iOS app, select "Sign Up"

Select the "Google" option...
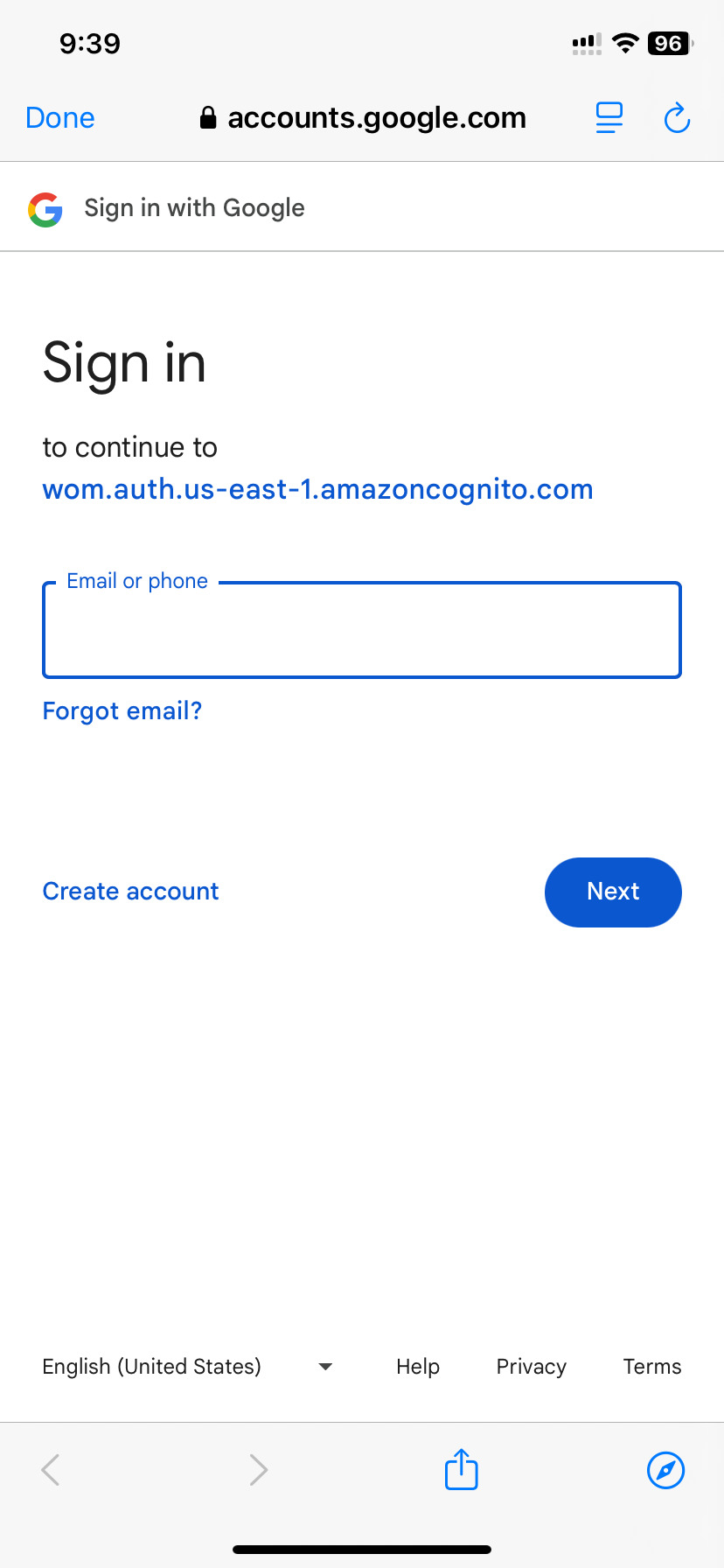
Note the app name of: "wom.auth.us-east-1.amazoncognito.com"
0 notes
Text
Implementing OAuth 2.0 in Django: A Step-by-Step Guide
Implementing OAuth 2.0 in Django: Secure Your Application with Third-Party Authentication
Introduction:OAuth 2.0 is an industry-standard protocol for authorization that allows applications to access user data without exposing their credentials. Implementing OAuth 2.0 in Django is crucial for developers looking to integrate third-party authentication services like Google, Facebook, or GitHub into their web applications. This guide will walk you through the process of setting up OAuth…
0 notes
Text
Google developers OAuth 2.0 playground And OpenID Connect

Google Auth Platform usability and security updates
Millions of developers authenticate users and access hundreds of APIs using Google's identity platform. One of the largest implementations of the Google developers OAuth 2.0 playground protocol and OpenID Connect standard in the world provides developers with a reliable, secure, and easy method to interact. Google is pleased to announce significant platform usability and security improvements.
Google engineers' OAuth 2.0 playground
Simple OAuth setting in Google Cloud Console
Developers that use Google Sign-in for authentication or user consent to use Google APIs must register their applications and websites to generate client credentials. Developers utilising Google Cloud Console previously found OAuth setup pages under APIs & Services. Separate navigation for Google Auth Platform is added to these sites.
This version speeds up app configuration updates, simplifies project registration, and improves developer advice. Upcoming improvements include an improved onboarding wizard, simpler OAuth scope management, and faster, more transparent app verification.
Developers using other consoles for OAuth have the same Firebase or Apps Script experience.
OAuth client secret presentation change
Some OAuth clients require a “secret” for authorisation and authentication. Since the client secret operates like a website or application password, protecting these strings is crucial to user account and data security.
Developers could previously download client secrets from Google Cloud Console, Firebase Console, and other Google developer tools. OAuth secrets will be hidden in Google Cloud Console client administrative pages in June. Developer consoles will show the last few characters to help identify them.
OAuth client secrets must be downloaded and handled securely by developers. For this, most developers utilise Google Cloud Platform's Secret Manager. The client secret won't appear when the creation screen closes.
Never reveal OAuth client secrets that provide access to user data or other production systems online or in version control systems. If secrets leak, change them immediately and cycle them often.
Automatic deactivation of unused OAuth clients
Starting in June, OAuth clients inactive for six months will be automatically terminated to prevent credential theft and misuse. When token exchanges end, the six-month period begins.
When inactive clients are erased, developers will be notified and can recover them for 30 days.
A great experience for you and your customers
These upgrades and more planned for later this year make your experience smoother and safer, giving you more time to build great applications and websites for your consumers.
Accessing Google APIs with OAuth 2.0
Simple acts
Every Google API-accessing app utilising OAuth 2.0 follows a pattern. You take five stages typically:
The Google API Console gives OAuth 2.0 credentials.
Get an access token from Google Authorisation Server.
Review user-granted access scopes.
Give an API the access token.
Update the access token if needed.
Google APIs authorise and authenticate using OAuth 2.0. Google supports OAuth 2.0 applications for web servers, client-side, installation, and limited-input devices.
Get OAuth 2.0 client credentials from Google API Console to begin. After that, your client app requests an access token from the Google Authorisation Server, extracts it, and sends it to the Google API you want to use. Check out the OAuth 2.0 Playground for an interactive Google OAuth 2.0 demonstration using your own client credentials.
#technology#technews#govindhtech#news#technologynews#Google developers OAuth 2.0 playground#Google developers OAuth#OAuth 2.0#OAuth clients#OAuth 2.0 playground#OAuth
0 notes
Text
Cybercriminals are abusing Google’s infrastructure, creating emails that appear to come from Google in order to persuade people into handing over their Google account credentials. This attack, first flagged by Nick Johnson, the lead developer of the Ethereum Name Service (ENS), a blockchain equivalent of the popular internet naming convention known as the Domain Name System (DNS). Nick received a very official looking security alert about a subpoena allegedly issued to Google by law enforcement to information contained in Nick’s Google account. A URL in the email pointed Nick to a sites.google.com page that looked like an exact copy of the official Google support portal.
As a computer savvy person, Nick spotted that the official site should have been hosted on accounts.google.com and not sites.google.com. The difference is that anyone with a Google account can create a website on sites.google.com. And that is exactly what the cybercriminals did. Attackers increasingly use Google Sites to host phishing pages because the domain appears trustworthy to most users and can bypass many security filters. One of those filters is DKIM (DomainKeys Identified Mail), an email authentication protocol that allows the sending server to attach a digital signature to an email. If the target clicked either “Upload additional documents” or “View case”, they were redirected to an exact copy of the Google sign-in page designed to steal their login credentials. Your Google credentials are coveted prey, because they give access to core Google services like Gmail, Google Drive, Google Photos, Google Calendar, Google Contacts, Google Maps, Google Play, and YouTube, but also any third-party apps and services you have chosen to log in with your Google account. The signs to recognize this scam are the pages hosted at sites.google.com which should have been support.google.com and accounts.google.com and the sender address in the email header. Although it was signed by accounts.google.com, it was emailed by another address. If a person had all these accounts compromised in one go, this could easily lead to identity theft.
How to avoid scams like this
Don’t follow links in unsolicited emails or on unexpected websites.
Carefully look at the email headers when you receive an unexpected mail.
Verify the legitimacy of such emails through another, independent method.
Don’t use your Google account (or Facebook for that matter) to log in at other sites and services. Instead create an account on the service itself.
Technical details Analyzing the URL used in the attack on Nick, (https://sites.google.com[/]u/17918456/d/1W4M_jFajsC8YKeRJn6tt_b1Ja9Puh6_v/edit) where /u/17918456/ is a user or account identifier and /d/1W4M_jFajsC8YKeRJn6tt_b1Ja9Puh6_v/ identifies the exact page, the /edit part stands out like a sore thumb. DKIM-signed messages keep the signature during replays as long as the body remains unchanged. So if a malicious actor gets access to a previously legitimate DKIM-signed email, they can resend that exact message at any time, and it will still pass authentication. So, what the cybercriminals did was: Set up a Gmail account starting with me@ so the visible email would look as if it was addressed to “me.” Register an OAuth app and set the app name to match the phishing link Grant the OAuth app access to their Google account which triggers a legitimate security warning from [email protected] This alert has a valid DKIM signature, with the content of the phishing email embedded in the body as the app name. Forward the message untouched which keeps the DKIM signature valid. Creating the application containing the entire text of the phishing message for its name, and preparing the landing page and fake login site may seem a lot of work. But once the criminals have completed the initial work, the procedure is easy enough to repeat once a page gets reported, which is not easy on sites.google.com. Nick submitted a bug report to Google about this. Google originally closed the report as ‘Working as Intended,’ but later Google got back to him and said it had reconsidered the matter and it will fix the OAuth bug.
11K notes
·
View notes
Text
Securing Your Digital Identity: Get Your Google API and OAuth Credentials Now

As of today, it is so easy to get the Google API and Client credentials with a few clicks via Google Developer Console. Before that, it is essential to know what API and Client credentials are. In this blog, we discuss the API and client credentials and when to use them. Are you searching for the Step by Step instructions to get the API key and OAuth Credentials? Then keep on reading….
Both API keys and OAuth are the different types of authentication handled by Cloud Endpoints.
These two differ most in the following ways:
The application or website performing the API call is identified by the API key.
An app or website’s user, or the person using it, is identified by an authentication token.
API keys provide project authorization
To decide which scheme is most appropriate, it’s important to understand what API keys and authentication can provide.
API keys provide
Project identification — Identify the application or the project that’s making a call to this API
Project authorization — Check whether the calling application has been granted access to call the API and has enabled the API in their project
API keys aren’t as secure as authentication tokens, but they identify the application or project that’s calling an API. They are generated on the project making the call, and you can restrict their use to an environment such as an IP address range, or an Android or iOS app.
By identifying the calling project, you can use API keys to associate usage information with that project. API keys allow the Extensible Service Proxy (ESP) to reject calls from projects that haven’t been granted access or enabled in the API.
Contrarily, authentication strategies often have two objectives:
Verify the identity of the calling user securely using user authentication.
Check the user's authorization to see if they have the right to submit this request.
A safe method of identifying the user who is calling is provided by authentication mechanisms.
In order to confirm that it has permission to call an API, endpoints also examine the authentication token.
The decision to authorize a request is made by the API server based on that authentication.
The calling project is identified by the API key, but the calling user is not.
An API key, for example, can identify the application that is making an API call if you have developed an application that is doing so.
Protection of API keys
In general, API keys is not seen to be safe because clients frequently have access to them. This will make it simple for someone to steal an API key. Unless the project owner revokes or regenerates the key, it can be used indefinitely once it has been stolen because it has no expiration date. There are better methods for authorization, even though the limitations you can place on an API key minimize this.
API Keys: When to Use?
An API may require API keys for part or all of its methods.
This makes sense to do if:
You should prevent traffic from anonymous sources.
In the event that the application developer wants to collaborate with the API producer to troubleshoot a problem or demonstrate the usage of their application, API keys identify an application's traffic for the API producer.
You wish to limit the number of API calls that are made.
You want to analyze API traffic to find usage trends.
APIs and services allow you to view application consumption.
You want to use the API key to filter logs.
API keys: When not to use?
Individual user identification – API keys are used to identify projects, not people
On secured authorization
Finding the authors of the project
Step-by-step instructions on how to get Google API and OAuth credentials using the Google developer console.
Step 1
Browse Google developer console

Step 2
Select your project or create a new project by clicking on the New project button

Step 3
Provide your project name, organization, and location, and click on create.
And That’s it. You have created a New Project.

Step 4
Navigate to the Enabled API and services at the Left sidebar and click on Credentials
Step 5
Move on to create Credentials

Here to get your API key click on the API key. Instantly you will get your API key for your Project.

To get your OAuth Credentials
Navigate to the OAuth Client ID on the Create Credentials drop-down menu.
Step 6
Here you need to create an application. A client ID is used to identify a single app to Google’s OAuth servers. If your app runs on multiple platforms, each will need its own client ID.
Step 7
Select the appropriate application type from the drop-down
The name of the client will be auto-generated. This is only to recognize the client console and does not show to the end users.
Step 8
Enter your URL for the Authorized JavaScript origins by clicking on Add URL
Provide your Authorized redirect URLs
Finally click on Create

Step 9
You will get an OAuth Client Id and Client Secret instantly.

Epilogue
Getting Google API and OAuth credentials is an important step in developing applications that interact with Google services. It allows developers to access data from Google APIs and services in a secure and reliable way. With the correct setup, developers can create powerful applications that can be used by millions of users. In summary, getting Google API and OAuth credentials is essential for any developer wishing to build web applications that interact with Google services.
#google drive#google cloud#google#blog post#Google api#oauth#oauth tutorial#oauthsecurity#google security#web developers#software development#developers
0 notes
Text
So with the pandora's box of AI being released into the world, cybersecurity has become kind of insane for the average user in a way that's difficult to describe for those who aren't following along. Coding in unfamiliar languages is easier to do now, for better and worse. Purchasable hacking "kits" are a thing on the dark web that basically streamline the process of deploying ransomware. And generative AI is making it much easier for more and more people to obscure their intentions and identities, regardless of their tech proficiency.
The impacts of this have been Really Bad in the last year or two in particular. For example:
(I'm about to link to sources, and you better be hovering and checking those links before clicking on them as a habit)
Ransomware attacks have become increasingly lucrative for private and state-sponsored hacking groups, with at least one hack recently reported to have resulted in a $75 MILLION payout from the victim. This in combination with the aforementioned factors has made it a bigger and bigger risk for companies and organizations holding your most sensitive data.
In the US, the Salt Typhoon hack over the past year or so has compromised virtually all major phone networks--meaning text and phone calls are no longer secure means of communication. While this won't affect most people in day-to-day, it does make basically all the information you share over traditional phone comms very vulnerable. You should avoid sharing sensitive information over the phone when you can.
CISA updated their security recommendations late last year in response to this compromise. One of the recommendations is to use a separate comms app with end-to-end encryption. I personally prefer Signal, since it's open source and not owned by Meta, but the challenge can be getting people you know on the same service. So... have fun with that.
2FA is no longer as secure as it was--because SMS itself is no longer secure, yeah, but even app-based 2FA has been rendered useless in certain circumstances. One reason for this is because...
A modern version of the early-2000's trick of gaining access to people's accounts via hijacked cookies has come back around for Chromium browsers, and hackers are gaining access to people's Google accounts via OAuth session hijacking. Meaning they can get into your already-logged-in accounts without passwords or 2FA even being needed to begin with. This has been achieved both through hackers compromising chrome browser extensions, and via a reinvigorated push to send out compromising links via email.
Thanks to AI, discerning compromised email is harder now. Cybercriminals are getting better at replicating legitimate email forms and website login screens etc., and coming up with ways to time the emails around times when you might legitimately expect them. (Some go so far as to hack into a person's phone to watch for when a text confirmation might indicate a recent purchase has been made via texted shipping alerts, for example)
If you go to a website that asks you to double-click a link or button--that is a major red flag. A potential method of clickjacking sessions is done via a script that has to be run with the end user's approval. Basically, to get around people who know enough to not authenticate scripts they don't recognize, hackers are concealing the related pop ups behind a "double-click" prompt instruction that places the "consent" prompt's button under the user's mouse in disguised UI, so that on the second click, the user will unwittingly elevate the script without realizing they are doing it.
Attachments are also a fresh concern, as hackers have figured out how to intentionally corrupt key areas of a file in a way that bypasses built-in virus check--for the email service's virus checker as well as many major anti-virus installed on endpoint systems
Hackers are also increasingly infiltrating trusted channels, like creating fake IT accounts in companies' Office 365 environment, allowing them to Teams employees instead of simply email them. Meaning when IT sends you a new PM in tools like Zoom, Slack, or Teams, you need to double-check what email address they are using before assuming it's the real IT person in question.
Spearphishing's growing sophistication has accelerated the theft of large, sensitive databases like the United/Change Healthcare hacks, the NHS hack & the recent Powerschool hack. Cybercriminals are not only gaining access to emails and accounts, but also using generative AI tools to clone the voices (written and spoken) of key individuals close to them, in order to more thoroughly fool targets into giving away sensitive data that compromises access to bigger accounts and databases.
This is mostly being used to target big-ticket targets, like company CSO's and other executives or security/IT personnel. But it also showcases the way scammers are likely to start trying to manipulate the average person more thoroughly as well. The amount of sensitive information--like the health databases being stolen and sold on the darkweb--means people's most personal details are up for sale and exploitation. So we're not too far off from grandparents being fooled by weaponized AI trained off a grandchild's scraped tiktok videos or other public-facing social media, for example. And who is vulnerable to believing these scams will expand, as scammers can potentially answer sensitive questions figured out from stolen databases, to be even more convincing.
And finally, Big Tech's interest in replacing their employees with AI to net higher profits has resulted in cybersecurity teams who are overworked, even more understaffed they already were before, and increasingly lacking the long-term industry experience useful to leading effective teams and finding good solutions. We're effectively in an arms race that is burning IT pros out faster and harder than before, resulting in the circumvention of crucial QA steps, and mistakes like the faulty release that created the Crowdstrike outage earlier last year.
Most of this won't impact the average person all at once or to the same degree big name targets with potential for big ransoms. But they are little things that have combined into major risks for people in ways that aren't entirely in our control. Password security has become virtually obsolete at this point. And 2FA's effectiveness is tenuous at best, assuming you can maintain vigilance.
The new and currently best advice to keeping your individual accounts secure is to switch to using Passkeys and FIDO keys like Yubikeys. However, the effectiveness of passkeys are held back somewhat as users are slow to adopt them, and therefore websites and services are required to continue to support passwords on people's accounts anyway--keeping password vulnerabilities there as a back door.
TLDR; it's pretty ugly out there right now, and I think it's going to get worse before it gets better. Because even with more sophisticated EDR and anti-virus tools, social engineering itself is getting more complex, which renders certain defensive technologies as somewhat obsolete.
Try to use a passkey when you can, as well as a password locker to create strong passwords you don't have to memorize and non-SMS 2FA as much as possible. FIDO keys are ideal if you can get one you won't lose.
Change your passwords for your most sensitive accounts often.
Don't give websites more personal info about yourself than is absolutely necessary.
Don't double-click links or buttons on websites/captchas.
Be careful what you click and download on piracy sources.
Try to treat your emails and PMs with a healthy dose of skepticism--double-check who is sending them etc for stealthily disguised typos or clever names. It's not going to be as obvious as it used to be that someone is phishing you.
It doesn't hurt to come up with an offline pass phrase to verify people you know IRL. Really.
And basically brace for more big hacks to happen that you cannot control to begin with. The employees at your insurance companies, your hospital, your telecomms company etc. are all likely targets for a breach.
36 notes
·
View notes
Text
Google’s “Sign in with Google” Flaw Exposes Millions of Users’ Details
Source: https://gbhackers.com/googles-sign-in-with-google-flaw/
More info: https://trufflesecurity.com/blog/millions-at-risk-due-to-google-s-oauth-flaw
3 notes
·
View notes
Text
This Week in Rust 534
Hello and welcome to another issue of This Week in Rust! Rust is a programming language empowering everyone to build reliable and efficient software. This is a weekly summary of its progress and community. Want something mentioned? Tag us at @ThisWeekInRust on Twitter or @ThisWeekinRust on mastodon.social, or send us a pull request. Want to get involved? We love contributions.
This Week in Rust is openly developed on GitHub and archives can be viewed at this-week-in-rust.org. If you find any errors in this week's issue, please submit a PR.
Updates from Rust Community
Official
Announcing Rust 1.76.0
This Development-cycle in Cargo: 1.77
Project/Tooling Updates
zbus 4.0 released. zbus is a pure Rust D-Bus crate. The new version brings a more ergonomic and safer API. Release: zbus4
This Month in Rust OSDev: January 2024
Rerun 0.13 - real-time kHz time series in a multimodal visualizer
egui 0.26 - Text selection in labels
Hello, Selium! Yet another streaming platform, but easier
Observations/Thoughts
Which red is your function?
Porting libyaml to Safe Rust: Some Thoughts
Design safe collection API with compile-time reference stability in Rust
Cross compiling Rust to win32
Modular: Mojo vs. Rust: is Mojo 🔥 faster than Rust 🦀 ?
Extending Rust's Effect System
Allocation-free decoding with traits and high-ranked trait bounds
Cross-Compiling Your Project in Rust
Kind: Our Rust library that provides zero-cost, type-safe identifiers
Performance Roulette: The Luck of Code Alignment
Too dangerous for C++
Building an Uptime Monitor in Rust
Box Plots at the Olympics
Rust in Production: Interview with FOSSA
Performance Pitfalls of Async Function Pointers (and Why It Might Not Matter)
Error management in Rust, and libs that support it
Finishing Turborepo's migration from Go to Rust
Rust: Reading a file line by line while being mindful of RAM usage
Why Rust? It's the safe choice
[video] Rust 1.76.0: 73 highlights in 24 minutes!
Rust Walkthroughs
Rust/C++ Interop Part 1 - Just the Basics
Rust/C++ Interop Part 2 - CMake
Speeding up data analysis with Rayon and Rust
Calling Rust FFI libraries from Go
Write a simple TCP chat server in Rust
[video] Google Oauth with GraphQL API written in Rust - part 1. Registration mutation.
Miscellaneous
The book "Asynchronous Programming in Rust" is released
January 2024 Rust Jobs Report
Chasing a bug in a SAT solver
Rust for hardware vendors
[audio] How To Secure Your Audio Code Using Rust With Chase Kanipe
[audio] Tweede Golf - Rust in Production Podcast
[video] RustConf 2023
[video] Decrusting the tracing crate
Crate of the Week
This week's crate is microflow, a robust and efficient TinyML inference engine for embedded systems.
Thanks to matteocarnelos for the self-suggestion!
Please submit your suggestions and votes for next week!
Call for Participation; projects and speakers
CFP - Projects
Always wanted to contribute to open-source projects but did not know where to start? Every week we highlight some tasks from the Rust community for you to pick and get started!
Some of these tasks may also have mentors available, visit the task page for more information.
* Hyperswitch - [FEATURE]: Setup code coverage for local tests & CI * Hyperswitch - [FEATURE]: Have get_required_value to use ValidationError in OptionExt
If you are a Rust project owner and are looking for contributors, please submit tasks here.
CFP - Speakers
Are you a new or experienced speaker looking for a place to share something cool? This section highlights events that are being planned and are accepting submissions to join their event as a speaker.
Devoxx PL 2024 | CFP closes 2024-03-01 | Krakow, Poland | Event date: 2024-06-19 - 2024-06-21
RustFest Zürich 2024 CFP closes 2024-03-31 | Zürich, Switzerland | Event date: 2024-06-19 - 2024-06-24
If you are an event organizer hoping to expand the reach of your event, please submit a link to the submission website through a PR to TWiR.
Updates from the Rust Project
466 pull requests were merged in the last week
add armv8r-none-eabihf target for the Cortex-R52
add lahfsahf and prfchw target feature
check_consts: fix duplicate errors, make importance consistent
interpret/write_discriminant: when encoding niched variant, ensure the stored value matches
large_assignments: Allow moves into functions
pattern_analysis: gather up place-relevant info
pattern_analysis: track usefulness without interior mutability
account for non-overlapping unmet trait bounds in suggestion
account for unbounded type param receiver in suggestions
add support for custom JSON targets when using build-std
add unstable -Z direct-access-external-data cmdline flag for rustc
allow restricted trait impls under #[allow_internal_unstable(min_specialization)]
always check the result of pthread_mutex_lock
avoid ICE in drop recursion check in case of invalid drop impls
avoid a collection and iteration on empty passes
avoid accessing the HIR in the happy path of coherent_trait
bail out of drop elaboration when encountering error types
build DebugInfo for async closures
check that the ABI of the instance we are inlining is correct
clean inlined type alias with correct param-env
continue to borrowck even if there were previous errors
coverage: split out counter increment sites from BCB node/edge counters
create try_new function for ThinBox
deduplicate tcx.instance_mir(instance) calls in try_instance_mir
don't expect early-bound region to be local when reporting errors in RPITIT well-formedness
don't skip coercions for types with errors
emit a diagnostic for invalid target options
emit more specific diagnostics when enums fail to cast with as
encode coroutine_for_closure for foreign crates
exhaustiveness: prefer "0..MAX not covered" to "_ not covered"
fix ICE for deref coercions with type errors
fix ErrorGuaranteed unsoundness with stash/steal
fix cycle error when a static and a promoted are mutually recursive
fix more ty::Error ICEs in MIR passes
for E0223, suggest associated functions that are similar to the path
for a rigid projection, recursively look at the self type's item bounds to fix the associated_type_bounds feature
gracefully handle non-WF alias in assemble_alias_bound_candidates_recur
harmonize AsyncFn implementations, make async closures conditionally impl Fn* traits
hide impls if trait bound is proven from env
hir: make sure all HirIds have corresponding HIR Nodes
improve 'generic param from outer item' error for Self and inside static/const items
improve normalization of Pointee::Metadata
improve pretty printing for associated items in trait objects
introduce enter_forall to supercede instantiate_binder_with_placeholders
lowering unnamed fields and anonymous adt
make min_exhaustive_patterns match exhaustive_patterns better
make it so that async-fn-in-trait is compatible with a concrete future in implementation
make privacy visitor use types more (instead of HIR)
make traits / trait methods detected by the dead code lint
mark "unused binding" suggestion as maybe incorrect
match lowering: consistently lower bindings deepest-first
merge impl_polarity and impl_trait_ref queries
more internal emit diagnostics cleanups
move path implementations into sys
normalize type outlives obligations in NLL for new solver
print image input file and checksum in CI only
print kind of coroutine closure
properly handle async block and async fn in if exprs without else
provide more suggestions on invalid equality where bounds
record coroutine kind in coroutine generics
remove some unchecked_claim_error_was_emitted calls
resolve: unload speculatively resolved crates before freezing cstore
rework support for async closures; allow them to return futures that borrow from the closure's captures
static mut: allow mutable reference to arbitrary types, not just slices and arrays
stop bailing out from compilation just because there were incoherent traits
suggest [tail @ ..] on [..tail] and [...tail] where tail is unresolved
suggest less bug-prone construction of Duration in docs
suggest name value cfg when only value is used for check-cfg
suggest pattern tests when modifying exhaustiveness
suggest turning if let into irrefutable let if appropriate
suppress suggestions in derive macro
take empty where bounds into account when suggesting predicates
toggle assert_unsafe_precondition in codegen instead of expansion
turn the "no saved object file in work product" ICE into a translatable fatal error
warn on references casting to bigger memory layout
unstably allow constants to refer to statics and read from immutable statics
use the same mir-opt bless targets on all platforms
enable MIR JumpThreading by default
fix mir pass ICE in the presence of other errors
miri: fix ICE with symbolic alignment check on extern static
miri: implement the mmap64 foreign item
prevent running some code if it is already in the map
A trait's local impls are trivially coherent if there are no impls
use ensure when the result of the query is not needed beyond its Resultness
implement SystemTime for UEFI
implement sys/thread for UEFI
core/time: avoid divisions in Duration::new
core: add Duration constructors
make NonZero constructors generic
reconstify Add
replace pthread RwLock with custom implementation
simd intrinsics: add simd_shuffle_generic and other missing intrinsics
cargo: test-support: remove special case for $message_type
cargo: don't add the new package to workspace.members if there is no existing workspace in Cargo.toml
cargo: enable edition migration for 2024
cargo: feat: add hint for adding members to workspace
cargo: fix confusing error messages for sparse index replaced source
cargo: fix: don't duplicate comments when editing TOML
cargo: relax a test to permit warnings to be emitted, too
rustdoc: Correctly generate path for non-local items in source code pages
bindgen: add target mappings for riscv64imac and riscv32imafc
bindgen: feat: add headers option
clippy: mem_replace_with_default No longer triggers on unused expression
clippy: similar_names: don't raise if the first character is different
clippy: to_string_trait_impl: avoid linting if the impl is a specialization
clippy: unconditional_recursion: compare by Tys instead of DefIds
clippy: don't allow derive macros to silence disallowed_macros
clippy: don't lint incompatible_msrv in test code
clippy: extend NONMINIMAL_BOOL lint
clippy: fix broken URL in Lint Configuration
clippy: fix false positive in redundant_type_annotations lint
clippy: add autofixes for unnecessary_fallible_conversions
clippy: fix: ICE when array index exceeds usize
clippy: refactor implied_bounds_in_impls lint
clippy: return Some from walk_to_expr_usage more
clippy: stop linting blocks_in_conditions on match with weird attr macro case
rust-analyzer: abstract more over ItemTreeLoc-like structs
rust-analyzer: better error message for when proc-macros have not yet been built
rust-analyzer: add "unnecessary else" diagnostic and fix
rust-analyzer: add break and return postfix keyword completions
rust-analyzer: add diagnostic with fix to replace trailing return <val>; with <val>
rust-analyzer: add incorrect case diagnostics for traits and their associated items
rust-analyzer: allow cargo check to run on only the current package
rust-analyzer: completion list suggests constructor like & builder methods first
rust-analyzer: improve support for ignored proc macros
rust-analyzer: introduce term search to rust-analyzer
rust-analyzer: create UnindexedProject notification to be sent to the client
rust-analyzer: substitute $saved_file in custom check commands
rust-analyzer: fix incorrect inlining of functions that come from MBE macros
rust-analyzer: waker_getters tracking issue from 87021 for 96992
rust-analyzer: fix macro transcriber emitting incorrect lifetime tokens
rust-analyzer: fix target layout fetching
rust-analyzer: fix tuple structs not rendering visibility in their fields
rust-analyzer: highlight rustdoc
rust-analyzer: preserve where clause when builtin derive
rust-analyzer: recover from missing argument in call expressions
rust-analyzer: remove unnecessary .as_ref() in generate getter assist
rust-analyzer: validate literals in proc-macro-srv FreeFunctions::literal_from_str
rust-analyzer: implement literal_from_str for proc macro server
rust-analyzer: implement convert to guarded return assist for let statement with type that implements std::ops::Try
Rust Compiler Performance Triage
Relatively balanced results this week, with more improvements than regressions. Some of the larger regressions are not relevant, however there was a real large regression on doc builds, that was caused by a correctness fix (rustdoc was doing the wrong thing before).
Triage done by @kobzol. Revision range: 0984becf..74c3f5a1
Summary:
(instructions:u) mean range count Regressions ❌ (primary) 2.1% [0.2%, 12.0%] 44 Regressions ❌ (secondary) 5.2% [0.2%, 20.1%] 76 Improvements ✅ (primary) -0.7% [-2.4%, -0.2%] 139 Improvements ✅ (secondary) -1.3% [-3.3%, -0.3%] 86 All ❌✅ (primary) -0.1% [-2.4%, 12.0%] 183
6 Regressions, 5 Improvements, 8 Mixed; 5 of them in rollups 53 artifact comparisons made in total
Full report here
Approved RFCs
Changes to Rust follow the Rust RFC (request for comments) process. These are the RFCs that were approved for implementation this week:
eRFC: Iterate on and stabilize libtest's programmatic output
Final Comment Period
Every week, the team announces the 'final comment period' for RFCs and key PRs which are reaching a decision. Express your opinions now.
RFCs
RFC: Rust Has Provenance
Tracking Issues & PRs
Rust
[disposition: close] Implement Future for Option<F>
[disposition: merge] Tracking Issue for min_exhaustive_patterns
[disposition: merge] Make unsafe_op_in_unsafe_fn warn-by-default starting in 2024 edition
Cargo
[disposition: merge] feat: respect rust-version when generating lockfile
New and Updated RFCs
No New or Updated RFCs were created this week.
Call for Testing
An important step for RFC implementation is for people to experiment with the implementation and give feedback, especially before stabilization. The following RFCs would benefit from user testing before moving forward:
RFC: Checking conditional compilation at compile time
Testing steps
If you are a feature implementer and would like your RFC to appear on the above list, add the new call-for-testing label to your RFC along with a comment providing testing instructions and/or guidance on which aspect(s) of the feature need testing.
Upcoming Events
Rusty Events between 2024-02-14 - 2024-03-13 💕 🦀 💕
Virtual
2024-02-15 | Virtual (Berlin, DE) | OpenTechSchool Berlin + Rust Berlin
Rust Hack and Learn | Mirror: Rust Hack n Learn
2024-02-15 | Virtual + In person (Praha, CZ) | Rust Czech Republic
Introduction and Rust in production
2024-02-19 | Virtual (Melbourne, VIC, AU)| Rust Melbourne
(Hybrid - in person & online) February 2024 Rust Melbourne Meetup - Day 1
2024-02-20 | Virtual (Melbourne, VIC, AU) | Rust Melbourne
(Hybrid - in person & online) February 2024 Rust Melbourne Meetup - Day 2
2024-02-20 | Virtual (Washington, DC, US) | Rust DC
Mid-month Rustful
2024-02-20 | Virtual | Rust for Lunch
Lunch
2024-02-21 | Virtual (Cardiff, UK) | Rust and C++ Cardiff
Rust for Rustaceans Book Club: Chapter 2 - Types
2024-02-21 | Virtual (Vancouver, BC, CA) | Vancouver Rust
Rust Study/Hack/Hang-out
2024-02-22 | Virtual (Charlottesville, NC, US) | Charlottesville Rust Meetup
Crafting Interpreters in Rust Collaboratively
2024-02-27 | Virtual (Dallas, TX, US) | Dallas Rust
Last Tuesday
2024-02-29 | Virtual (Berlin, DE) | OpenTechSchool Berlin + Rust Berlin
Rust Hack and Learn | Mirror: Rust Hack n Learn Meetup | Mirror: Berline.rs page
2024-02-29 | Virtual (Charlottesville, NC, US) | Charlottesville Rust Meetup
Surfing the Rusty Wireless Waves with the ESP32-C3 Board
2024-03-06 | Virtual (Indianapolis, IN, US) | Indy Rust
Indy.rs - with Social Distancing
2024-03-07 | Virtual (Charlottesville, NC, US) | Charlottesville Rust Meetup
Crafting Interpreters in Rust Collaboratively
2024-03-12 | Virtual (Dallas, TX, US) | Dallas Rust
Second Tuesday
2024-03-12 | Hybrid (Virtual + In-person) Munich, DE | Rust Munich
Rust Munich 2024 / 1 - hybrid
Asia
2024-02-17 | New Delhi, IN | Rust Delhi
Meetup #5
Europe
2024-02-15 | Copenhagen, DK | Copenhagen Rust Community
Rust Hacknight #2: Compilers
2024-02-15 | Praha, CZ - Virtual + In-person | Rust Czech Republic
Introduction and Rust in production
2024-02-21 | Lyon, FR | Rust Lyon
Rust Lyon Meetup #8
2024-02-22 | Aarhus, DK | Rust Aarhus
Rust and Talk at Partisia
2024-02-29 | Berlin, DE | Rust Berlin
Rust and Tell - Season start 2024
2024-03-12 | Munich, DE + Virtual | Rust Munich
Rust Munich 2024 / 1 - hybrid
North America
2024-02-15 | Boston, MA, US | Boston Rust Meetup
Back Bay Rust Lunch, Feb 15
2024-02-15 | Seattle, WA, US | Seattle Rust User Group
Seattle Rust User Group Meetup
2024-02-20 | New York, NY, US | Rust NYC
Rust NYC Monthly Mixer (Moved to Feb 20th)
2024-02-20 | San Francisco, CA, US | San Francisco Rust Study Group
Rust Hacking in Person
2024-02-21 | Boston, MA, US | Boston Rust Meetup
Evening Boston Rust Meetup at Microsoft, February 21
2024-02-22 | Mountain View, CA, US | Mountain View Rust Meetup
Rust Meetup at Hacker Dojo
2024-02-28 | Austin, TX, US | Rust ATX
Rust Lunch - Fareground
2024-03-07 | Mountain View, CA, US | Mountain View Rust Meetup
Rust Meetup at Hacker Dojo
Oceania
2024-02-19 | Melbourne, VIC, AU + Virtual | Rust Melbourne
(Hybrid - in person & online) February 2024 Rust Melbourne Meetup - Day 1
2024-02-20 | Melbourne, VIC, AU + Virtual | Rust Melbourne
(Hybrid - in person & online) February 2024 Rust Melbourne Meetup - Day 2
2024-02-27 | Canberra, ACT, AU | Canberra Rust User Group
February Meetup
2024-02-27 | Sydney, NSW, AU | Rust Sydney
🦀 spire ⚡ & Quick
2024-03-05 | Auckland, NZ | Rust AKL
Rust AKL: Introduction to Embedded Rust + The State of Rust UI
If you are running a Rust event please add it to the calendar to get it mentioned here. Please remember to add a link to the event too. Email the Rust Community Team for access.
Jobs
Please see the latest Who's Hiring thread on r/rust
Quote of the Week
For some weird reason the Elixir Discord community has a distinct lack of programmer-socks-wearing queer furries, at least compared to Rust, or even most other tech-y Discord servers I’ve seen. It caused some weird cognitive dissonance. Why do I feel vaguely strange hanging out online with all these kind, knowledgeable, friendly and compassionate techbro’s? Then I see a name I recognized from elsewhere and my hindbrain goes “oh thank gods, I know for a fact she’s actually a snow leopard in her free time”. Okay, this nitpick is firmly tongue-in-cheek, but the Rust user-base continues to be a fascinating case study in how many weirdos you can get together in one place when you very explicitly say it’s ok to be a weirdo.
– SimonHeath on the alopex Wiki's ElixirNitpicks page
Thanks to Brian Kung for the suggestion!
Please submit quotes and vote for next week!
This Week in Rust is edited by: nellshamrell, llogiq, cdmistman, ericseppanen, extrawurst, andrewpollack, U007D, kolharsam, joelmarcey, mariannegoldin, bennyvasquez.
Email list hosting is sponsored by The Rust Foundation
Discuss on r/rust
3 notes
·
View notes
Text
[Update] Support iOS 17 and More
We have a long list of improvements and bug fixes in this update(version 7.8.0).
Support iOS 17.
Fix the 'Liked Posts' bug that some posts were missing during pagination.
Fix the crash when selecting 'Open the Post Reblogged' menu.
Fix the emoji text formatting bug.
Video Posting is supported(at long last).
Post Notes: separated by Comment/Reblog/Like. The comment section includes reply and reblog with text.(BTW, the notes view is not exactly the same with the official Tumblr app. Not enough Tumblr API support yet. And sometimes, the comment section may include reblog/like if no comment exists.)
The feed menu button of the current tab is re-designed.
'Tag Search in this Blog' menu supports multiple tags delimited by Comma. It will search posts containing all the tags.
The list popup supports the 'Swipe Down' gesture on the navigation bar. When swiped down, it will be pinned to the bottom left or closed. For example, following blogs or post notes support this gesture.
Restore home screen quick action features.(It was accidently removed).
The default action for Hold Gesture on Post in Grid Mode is changed to Menu (from Like). You change this option at the Settings->Gestures.
The OAuth 2.0 is supported. But there are bugs when signing with Google/Apple in OAuth2.0 Tumblr API. So, the default method is still 1.0a. You can change this option at the 'Manage Accounts'.
iOS 12 or later is supported from this version.
PS. There was a minor bug fixing update(version 7.8.1) at 2023-10-18.
PS. Another minor update with some animation refinements on iOS 17 and scroll performance tweaks (version 7.8.2 at 2023-11-05).
6 notes
·
View notes
Quote
パスワードを変更しても攻撃者による Google サービスへのアクセスを可能にするエクスプロイトが10月に公開されたが、このエクスプロイトを組み込んだ情報窃取型マルウェアが急速に広がっているそうだ (CloudSEK のブログ記事、 The Register の記事)。 エクスプロイトの仕組みは、トークンを改ざんして永続的な Google の cookie を生成することでパスワードを変更しても引き続きアクセスが可能になるというもの。エクスプロイトの利用が判明しているマルウェアファミリーとしては Lumma や Rhadamanthys、Stealc、Meduza、RisePro、WhiteSnake が挙げられている。 CloudSEK の調査によれば、エクスプロイトは非公開の「MultiLogin」と呼ばれる Google の OAuth エンドポイントを利用しているという。MultiLogin は Google の複数のサービスにわたって Google アカウントを同期する内部メカニズムであり、Chromium のソースコードで用途が説明されている。 根本的な解決には Google による修正を待つしかないが、CloudSEK では暫定的な緩和策を紹介している。アカウントが侵害されている可能性がある場合、または用心のために緩和策を適用するには、すべてのブラウザープロファイルからサインアウトして現在のセッショントークンを無効化し、パスワードをリセットしてから再びサインインして新しいトークンを作成すればいい。特にトークンと GAIA ID が盗まれたと考えられる場合にはこの操作が重要とのことだ。
パスワード変更後も継続してGoogleアカウントを侵害できるエクスプロイト、実装するマルウェアが増加 | スラド セキュリティ
2 notes
·
View notes
Text
New heights of nerdom
I have a metric boatload of direct messages that I want to save and, surprisingly, tumblr doesn't have a way to let you do that. Copying and pasting is beyond painful. So now what?
Google and hope that some other nerd* wrote a browser extension or app or something to help.
Someone did!
https://git.jeckyll.net/published/personal/tumblr-chat-messages-downloader
It's a PHP file that uses curl and oauth to grab the messages you ask for and write them out at the command line. (If you're a programmer, this makes sense.) Then you can copy and paste the whole thing and save it to a text file.
The output looks like this except for the bolded text. That's some sort of tumblr weirdness.
06/01/2024, 15:34:28 bluemoonperegrine: EXACTLY 06/01/2024, 15:34:55 tumblr-user: lol
I found a bug: if there's an exclamation point in your password, which you have to enter locally to make it work, it goofs things up. Escaping that character doesn't help. I changed my password to get around it. * I can say that because I am one.
5 notes
·
View notes
Text
Bōzt: Restaurants & Local Food app for iOS: Google OAuth Consent Screen: Privacy Policy and Terms of Service Links Take User to Inactive Bozt.bozt Page
OS 18.3
Bozt: Restaurants & Local Food app for iOS (version 4.2.4)
02/01/2025
Description:
The Bozt: Restaurants & Local Food app for iOS has a problem with the OAuth consent screen.
The "Privacy Policy" and "Terms of Service" links on this OAuth consent screen that is displayed by the Bozt app are bad - they lead the user on a dead link.
Steps to Reproduce:
1. Download and launch the Bozt: Restaurants & Local Food app
2. From the Sign-in screen, select "Sign in with Google"
3. Select "Continue" to the pop-up prompt
4. From the Google OAuth screen, select either "privacy policy" or "terms of service"
Result: The "privacy policy" and "terms of service" links on Bozt's Google OAuth consent screen take the user to a dead link
Expected: The "privacy policy" and "terms of service" links on Bozt's Google OAuth consent screen should take the user to valid privacy policies and terms of service for the app.

Download and launch the app...

Choose the "Sign in with Google" option...

Select the "Continue" option to advance to the OAuth consent screen...

Select either the "privacy policy" or "terms of service" links on this OAuth consent screen...

User is left here - not a valid URL.
0 notes
Text
Advanced Techniques in Full-Stack Development

Certainly, let's delve deeper into more advanced techniques and concepts in full-stack development:
1. Server-Side Rendering (SSR) and Static Site Generation (SSG):
SSR: Rendering web pages on the server side to improve performance and SEO by delivering fully rendered pages to the client.
SSG: Generating static HTML files at build time, enhancing speed, and reducing the server load.
2. WebAssembly:
WebAssembly (Wasm): A binary instruction format for a stack-based virtual machine. It allows high-performance execution of code on web browsers, enabling languages like C, C++, and Rust to run in web applications.
3. Progressive Web Apps (PWAs) Enhancements:
Background Sync: Allowing PWAs to sync data in the background even when the app is closed.
Web Push Notifications: Implementing push notifications to engage users even when they are not actively using the application.
4. State Management:
Redux and MobX: Advanced state management libraries in React applications for managing complex application states efficiently.
Reactive Programming: Utilizing RxJS or other reactive programming libraries to handle asynchronous data streams and events in real-time applications.
5. WebSockets and WebRTC:
WebSockets: Enabling real-time, bidirectional communication between clients and servers for applications requiring constant data updates.
WebRTC: Facilitating real-time communication, such as video chat, directly between web browsers without the need for plugins or additional software.
6. Caching Strategies:
Content Delivery Networks (CDN): Leveraging CDNs to cache and distribute content globally, improving website loading speeds for users worldwide.
Service Workers: Using service workers to cache assets and data, providing offline access and improving performance for returning visitors.
7. GraphQL Subscriptions:
GraphQL Subscriptions: Enabling real-time updates in GraphQL APIs by allowing clients to subscribe to specific events and receive push notifications when data changes.
8. Authentication and Authorization:
OAuth 2.0 and OpenID Connect: Implementing secure authentication and authorization protocols for user login and access control.
JSON Web Tokens (JWT): Utilizing JWTs to securely transmit information between parties, ensuring data integrity and authenticity.
9. Content Management Systems (CMS) Integration:
Headless CMS: Integrating headless CMS like Contentful or Strapi, allowing content creators to manage content independently from the application's front end.
10. Automated Performance Optimization:
Lighthouse and Web Vitals: Utilizing tools like Lighthouse and Google's Web Vitals to measure and optimize web performance, focusing on key user-centric metrics like loading speed and interactivity.
11. Machine Learning and AI Integration:
TensorFlow.js and ONNX.js: Integrating machine learning models directly into web applications for tasks like image recognition, language processing, and recommendation systems.
12. Cross-Platform Development with Electron:
Electron: Building cross-platform desktop applications using web technologies (HTML, CSS, JavaScript), allowing developers to create desktop apps for Windows, macOS, and Linux.
13. Advanced Database Techniques:
Database Sharding: Implementing database sharding techniques to distribute large databases across multiple servers, improving scalability and performance.
Full-Text Search and Indexing: Implementing full-text search capabilities and optimized indexing for efficient searching and data retrieval.
14. Chaos Engineering:
Chaos Engineering: Introducing controlled experiments to identify weaknesses and potential failures in the system, ensuring the application's resilience and reliability.
15. Serverless Architectures with AWS Lambda or Azure Functions:
Serverless Architectures: Building applications as a collection of small, single-purpose functions that run in a serverless environment, providing automatic scaling and cost efficiency.
16. Data Pipelines and ETL (Extract, Transform, Load) Processes:
Data Pipelines: Creating automated data pipelines for processing and transforming large volumes of data, integrating various data sources and ensuring data consistency.
17. Responsive Design and Accessibility:
Responsive Design: Implementing advanced responsive design techniques for seamless user experiences across a variety of devices and screen sizes.
Accessibility: Ensuring web applications are accessible to all users, including those with disabilities, by following WCAG guidelines and ARIA practices.
full stack development training in Pune
2 notes
·
View notes
Text
With Reddit carpet bombing free third party apps, one thing I worry about in the idea of going back to all individual forums is I have really really liked not having to make a new account on hundreds of websites. I stopped using Google and Facebook token sign in years ago because they already know too much and I haven't seen an OAuth option in years, but it's been really nice that most of the forum-like communities I've wanted to dip into have been on a megaplatform where I already have a few accounts.
The downside of returning to balkanized communities is having to either go back to spreading an email address all over the internet or creating many more email addresses and having to keep track of all of those, which puts even more reliance on a password manager.
3 notes
·
View notes
Text
API Integration Services in delhi with Investment solutions company in Delhi

In the digital age, seamless system integration is the backbone of innovation. Whether you’re running a fintech startup, an eCommerce platform, or a customer support service, APIs (Application Programming Interfaces) help you connect, automate, and scale. Delhi, as a leading tech hub, is home to ekyc solution for stock broker some of the most experienced and advanced API service providers in India.
Let’s explore the top API service providers in Delhi including specialists in WhatsApp Business API integration, ekyc solution provider in delhi custom API development, and business automation.
Why APIs Matter in 2025
APIs enable different software systems to talk to each other. Whether you’re processing payments, verifying customer identity, or sending WhatsApp messages, APIs make it happen instantly and securely.
Faster automation
Improved user experience
Streamlined business processes
Seamless third-party integrations
This is why choosing the right API integration company in Delhi can give your business a serious competitive edge.
Top API Integration Services in Delhi
Several Delhi-based companies offer advanced API integration services that support businesses in fintech, healthcare, logistics, and retail. These services include:
Integration with third-party platforms like Razorpay, Google Maps, Twilio, Stripe
Connecting CRMs, ERPs, and internal tools
Automating lead capture, transactions, or order fulfillment
Cloud and on-premise API deployment
These companies ensure Investment solutions company in delhi end-to-end support—from planning and development to deployment and maintenance.
API Development Services in Delhi
Apart from integration, many businesses require custom API development services in Delhi to meet unique operational needs. Key features include:
RESTful & GraphQL API development
Scalable architecture with OAuth, JWT, and other authentication protocols
Secure data handling compliant with global standards
Real-time data exchange and analytics
Whether you’re building a customized solution in delhi platform or integrating multiple digital tools, custom APIs ensure customized solution in delhi everything runs smoothly and securely.
Leading API Integration Company in Delhi
Delhi houses several reputed firms specializing in full-cycle API solutions. A reliable API integration company in Delhi offers:
Consultation & architecture planning
Custom API development
Integration with legacy systems and third-party services
Monitoring and optimization
These providers often have a strong portfolio in industries like finance, healthcare, and logistics, helping clients automate and grow efficiently.
WhatsApp API Integration Service in Delhi
With over 500 million WhatsApp users in India, businesses are using the platform for customer engagement, support, and notifications. WhatsApp API integration services in Delhi offer:
Two-way messaging
Automated alerts and customer onboarding
Secure user verification and eKYC
Chatbot and CRM integration
Ideal for banks, fintechs, and eCommerce platforms, WhatsApp APIs boost engagement and streamline communication.
Top WhatsApp Business API Services in Delhi
The top WhatsApp Business API services in Delhi help brands communicate professionally at scale. These services include:
Green Tick verification
Customer support automation
Rich media messages (PDFs, images, CTA buttons)
Integration with CRM and ticketing platforms
With custom solutions for sectors API Integration Company in delhi like real estate, healthcare, education, and finance, these providers help businesses drive better results through chat automation.
Best WhatsApp Business API Provider in Delhi
Choosing the best WhatsApp Business API provider in Delhi means partnering with a team that offers:
Fast API deployment
99.9% uptime with scalable infrastructure
Smart analytics and campaign tracking
Seamless integration with existing tools
These providers ensure your WhatsApp channel becomes a reliable, high-converting customer communication tool.
Best WhatsApp API Integration Service in Delhi
When it comes to automation, customer experience, and lead generation, the best whatsapp api integration services in delhi go beyond just setup. They deliver:
End-to-end support from setup to training
Chatbot design and automation workflows
Integration with payment gateways and support systems
Custom APIs for KYC, onboarding, and order tracking
Whether you’re a startup or an enterprise, these services enable personalized customer journeys via WhatsApp.
Final Thoughts
From API integration to business messaging, Delhi is home to some of the most innovative API service providers in India. These companies enable brands to build one kyc solution in india smarter workflows, automate customer touchpoints, and scale operations with agility.
If your business depends on automation, customer communication, or cross-platform data exchange partnering with the right API experts in Delhi can drive measurable growth.
0 notes
Text
Hướng dẫn fix 💥 Lỗi 400: `redirecturimismatch` khi đăng nhập bằng Google – cách khắc ph ục 💖👉🍀
💥 Lỗi 400: `redirecturimismatch` khi đăng nhập bằng Google – cách khắc phục 💖👉🍀 🧨 Lỗi bạn gặp: ❗Đã chặn quyền truy cập: Yêu cầu của ứng dụng này không hợp lệ Lỗi 400: redirect\uri\mismatch 🔍 Nghĩa là: URI mà ứng dụng gửi trong quá trình OAuth không trùng khớp với URI đã khai báo trong Google Cloud Console → Google từ chối xác thực. ✅ Hướng dẫn khắc phục từng bước 🔹 Bước 1: Kiểm tra lại…
0 notes