#iPhone Data Protection
Explore tagged Tumblr posts
Text
Fast iPhone Screen Repairs & Secure Data Recovery at Digimob Phone Repair

Your iPhone is more than just a phone—it’s a lifeline to your personal and professional world. Whether it’s a cracked screen or a sudden data loss, these issues can be extremely frustrating. Fortunately, professional iPhone phone repairs, including iPhone screen repairs and data recovery services, are here to help restore your device to its original functionality. At Digimob Phone Repair, we specialize in fast, reliable, and affordable iPhone repairs to get you back on track in no time. This blog will guide you through our top services, including screen repairs, battery fixes, and data recovery solutions, ensuring your iPhone is always in optimal condition.
Why Choose Professional iPhone Repair Services?
When your iPhone faces any type of damage, you want to ensure it’s repaired properly. While DIY fixes or third-party repair shops might seem like an affordable solution, they can often lead to more harm than good. Here’s why choosing Digimob Phone Repair for your iPhone phone repairs is the best option:
Expert Technicians: Our technicians are highly trained and experienced in all aspects of iPhone repairs, from screen fixes to data recovery.
Genuine Parts: We use only high-quality, genuine replacement parts to ensure your phone works like new.
Fast Turnaround: We understand that your time is valuable. That’s why we offer quick repair services, often completing repairs on the same day.
Warranty: Our repairs come with a warranty, giving you peace of mind that your device is protected.
iPhone Screen Repair: The Most Common Repair
One of the most common issues iPhone users face is a cracked or shattered screen. Whether it’s the result of a drop or pressure applied to your device, a broken screen can make your phone unusable.
Why iPhone Screen Repair is Essential
Your iPhone’s screen isn’t just for display—it’s the interface you use to navigate your device, make calls, send messages, and browse the web. A cracked or damaged screen can not only affect your ability to use your phone but can also pose a safety risk with sharp edges and potential further damage.
How We Fix Your iPhone Screen
At Digimob Phone Repair, we specialize in providing quick and effective iPhone screen repairs. Here’s how we handle the process:
Evaluation: Our technicians assess the extent of the damage to determine the best course of action.
Screen Replacement: We replace the cracked or broken screen with a brand-new one, ensuring that it works like new.
Quality Check: After replacing the screen, we conduct thorough testing to ensure the touch sensitivity, display clarity, and functionality are perfect.
If you’re facing any issues with your iPhone screen, don’t hesitate to reach out for professional iPhone repairs.
Read more: Fast iPhone Screen Repairs & Secure Data Recovery at Digimob Phone Repair
#iPhone Screen Repair#iPhone Data Recovery#iPhone Repair Services#iPhone Phone Repairs#Professional iPhone Repairs#iPhone Repair Experts#Data Recovery for iPhone#iPhone Screen Fix#iPhone Battery Replacement#iPhone Repair Near Me#iPhone Repair Shop#Fast iPhone Repairs#Affordable iPhone Repair#Screen Repair Services#iPhone Data Protection#Digimob Phone Repair#iPhone Recovery Services#Reliable iPhone Repair#Cracked iPhone Screen Repair#iPhone Repair Solutions
0 notes
Text
If you are outside the UK and concerned about who can see your data, ADP adds an extra layer of security by making it unreadable even by Apple. If ADP is disabled, your data could be at risk because it can still be unlocked by Apple, a legal request or a data breach.
#ADP#Advanced Data Protection#Apple#Desktop#Desktop/Laptop#iPad#iPhone#iPhone/iPad#Laptop#Mac#PC#Windows
0 notes
Text
The timing of this silent opt-in to beta testing for iOS is giving me doggie data breach energy. They are extracting as much of our data as they can and feeding into learning engines (LLMs) for ai.
It’s no consolation to me that the hackers are restricted to read only access. Even with redacted data they have extracted enough to make the connections from the systems they’ve breached and the data that’s being collected and assimilated from sources like this new “feature”
hi btw even if you didn’t upgrade to ios 18 with the ai software, apple still switched everything on to learn from your phone.


You have to go into siri settings and apps and then toggle everything off (I left search app on so I can find them, but all else off). You have to do this for every single app 😅
#privacy#data privacy#apple ios#apple intelligence#opt out#turn that shit off#ipados#iPad#iPhone#operating system update#ios 18#stop training ai#protect your data#llms#do this#this has been a psa
137 notes
·
View notes
Text
How to Fix iPhone Unavailable on Lock Screen [2024 Updated] - Technology Org
New Post has been published on https://thedigitalinsider.com/how-to-fix-iphone-unavailable-on-lock-screen-2024-updated-technology-org/
How to Fix iPhone Unavailable on Lock Screen [2024 Updated] - Technology Org
If your iPhone displays the message “iPhone Unavailable” on the lock screen, it means that you have entered an incorrect passcode multiple times, triggering Apple Security measures to safeguard your device from unauthorized access. You may find yourself in a situation where you have forgotten your iPhone password and cannot unlock your device. However, there’s no need to worry. This article will guide you through several methods to fix “iPhone Unavailable” lock screen issue.
When you encounter the “iPhone Unavailable” message, often with a timer, it signifies that you have made multiple consecutive incorrect password attempts within a short period. Your iPhone will then be locked, preventing further access to the device. The lockout time varies from 1 minute to 8 hours or longer. In a nutshell, the more failed attempts, the longer the lockout.
Additionally, depending on your settings and the version of iOS you are using, your iPhone may alternatively display “Security Lockout” or, in earlier versions before iOS 15.2, the prompt will appear as “iPhone is disabled“.
Solution 1: Fix iPhone Unavailable without Computer
Starting from iOS 15.2 and later, iPhone has introduced a helpful feature known as “Erase iPhone” to assist users in resetting their devices. This functionality enables individuals who have forgotten their screen passcode to reset their unavailable iPhone using their Apple ID. It’s worth noting that “Erase iPhone” will permanently erase all content and settings on the device. Follow these steps:
Step 1: On the iPhone Unavailable screen, continue entering the wrong passcode until you see Erase iPhone option in the lower right corner.
Step 2: Tap Erase iPhone > Erase iPhone (for iOS 17 and later, tap Forgot Passcode > Start iPhone Reset), then enter your Apple ID password to sign out of the account. Then follow the onscreen instructions to complete the process.
Step 3: Once the reset is finished, proceed with the setup process, including the option to restore their data from a previous backup, if any.
Solution 2: Unlock iPhone Unavailable using iSumsoft iPhone Passcode Refixer
If you find yourself cannot remember the Apple ID password required to wipe your iPhone, there are other solutions. One of the recommended methods is to use a trusted third-party tool called iSumsoft iPhone Passcode Refixer, which allows you to easily bypass the lock screen and effectively fix the “iPhone Unavailable” screen.
Learn how to use this software:
Step 1: Download and install iSumsoft iPhone Passcode Refixer. After the installation, connect the locked iPhone to the computer and launch the program.
Step 2: On the Home page, select Unlock Lock Screen.
Step 3: Click Start to proceed. Please note that if your iPhone cannot be recognized by the software, try to put the iPhone into recovery mode or DEU mode.
Step 4: Your iPhone info will be loaded and displayed on the interface, and you will be asked to download a firmware package. Click Download to proceed.
Step 5: After the successful download and verification, click Unlock to begin unlocking iPhone.
Step 6: When “Unlock Screen Successfully” appears on the screen, it means that the iPhone Unavailable message has been removed and your iPhone will restart automatically.
Solution 3: Fix iPhone Unavailable with Previous Passcode
For devices running iOS 17 and later, you are allowed to use your previous password to access the device without losing any data. This method, however, is time-limited as it is only valid for 72 hours after changing the screen lock passcode. So, if you are the lucky guy, follow the steps below:
Step 1: From the iPhone Unavailable screen, proceed with entering the wrong passcode. When you see Forgot Passcode? on the lock screen, tap on it.
Step 2: Tap Enter Previous Passcode, then follow the onscreen instructions to create a new passcode.
Solution 4: Bypass iPhone Unavailable Message with iTunes
iTunes serves as an official tool for solving many common iPhone issues, including restoring iPhone when the iPhone says “iPhone Unavailable”. To utilize iTunes for this purpose, you’ll need a computer with the latest version of iTunes installed. Here’s a step-by-step guide on how to restore your iPhone using iTunes:
Step 1: Connect the iPhone to the computer and then put it into recovery mode.
Step 2: Launch iTunes. You will then be asked to Update or Restore. Select Restore and follow the onscreen prompts to reset the iPhone.
Note: If you haven’t signed out of your Apple ID before restoring the iPhone with iTunes, you may be stuck on the Activation Lock, asking for the previous Apple ID and password.
Solution 5: Fix iPhone Unavailable with iCloud
If you prefer not to install the iTunes application on your computer, there is an alternative method to address the “iPhone Unavailable” issue by using the iCloud website. By logging in to the iCloud website, you can resolve the problem without the need for iTunes. However, please note that you will require your Apple ID and password to sign in to iCloud. Here is how to use iTunes to unlock iPhone:
Step 1: Visit iCloud.com and sign in with your account associated with the unavailable iPhone.
Step 2: From the iCloud page, locate Find My and select it. You may be asked to enter your Apple ID passcode.
Step 3: You will then see a list including all devices linked to this account. Select the locked iPhone.
Step 4: Click Erase This Device.
Q1: Is iPhone Unavailable Permanently?
According to some reports, some users can be locked for up to 23,056,476 minutes, rendering the iPhone permanently unavailable. In theory, the amount of time the screen is locked is directly proportional to the number of times an incorrect passcode is entered.5th failed attempt, 5 minutes;
6th failed attempt, 5 minutes;
7th failed attempt, 5 minutes;
8th failed attempt, 15 minutes;
9th failed attempt, 1 hour;
After 10 failed attempts, your iPhone will be locked for more than 1 hour if you enable the “Erase iPhone after 10 failed attempts” feature, or you will be locked for more than 1 hour.
Q2: How to Unlock iPhone Unavailable without Losing Data
To preserve data, fixing an unavailable iPhone without data loss is only possible if you possess the Screen Lock passcode or have a recent backup of your iPhone. Apple prioritizes data protection, which contributes to its immense popularity.
#2024#apple#Article#backup#computer#content#data#data loss#data protection#devices#display#displays#firmware#Hardware & gadgets#how#how to#icloud#iOS#ios 15#iPhone#issues#it#Learn#list#logging#message#Method#One#Other#Other posts
0 notes
Text
Are the means of computation even seizable?
I'm on a 20+ city book tour for my new novel PICKS AND SHOVELS. Catch me in PITTSBURGH in TOMORROW (May 15) at WHITE WHALE BOOKS, and in PDX on Jun 20 at BARNES AND NOBLE with BUNNIE HUANG. More tour dates (London, Manchester) here.

Something's very different in tech. Once upon a time, every bad choice by tech companies – taking away features, locking out mods or plugins, nerfing the API – was countered, nearly instantaneously, by someone writing a program that overrode that choice.
Bad clients would be muscled aside by third-party clients. Locked bootloaders would be hacked and replaced. Code that confirmed you were using OEM parts, consumables or adapters would be found and nuked from orbit. Weak APIs would be replaced with muscular, unofficial APIs built out of unstoppable scrapers running on headless machines in some data-center. Every time some tech company erected a 10-foot enshittifying fence, someone would show up with an 11-foot disenshittifying ladder.
Those 11-foot ladders represented the power of interoperability, the inescapable bounty of the Turing-complete, universal von Neumann machine, which, by definition, is capable of running every valid program. Specifically, they represented the power of adversarial interoperability – when someone modifies a technology against its manufacturer's wishes. Adversarial interoperability is the origin story of today's tech giants, from Microsoft to Apple to Google:
https://www.eff.org/deeplinks/2019/10/adversarial-interoperability
But adversarial interop has been in steady decline for the past quarter-century. These big companies moved fast and broke things, but no one is returning the favor. If you ask the companies what changed, they'll just smirk and say that they're better at security than the incumbents they disrupted. The reason no one's hacked up a third-party iOS App Store is that Apple's security team is just so fucking 1337 that no one can break their shit.
I think this is nonsense. I think that what's really going on is that we've made it possible for companies to design their technologies in such a way that any attempt at adversarial interop is illegal.
"Anticircumvention" laws like Section 1201 of the 1998 Digital Millennium Copyright Act make bypassing any kind of digital lock (AKA "Digital Rights Management" or "DRM") very illegal. Under DMCA, just talking about how to remove a digital lock can land you in prison for 5 years. I tell the story of this law's passage in "Understood: Who Broke the Internet," my new podcast series for the CBC:
https://pluralistic.net/2025/05/08/who-broke-the-internet/#bruce-lehman
For a quarter century, tech companies have aggressively lobbied and litigated to expand the scope of anticircumvention laws. At the same time, companies have come up with a million ways to wrap their products in digital locks that are a crime to break.
Digital locks let Chamberlain, a garage-door opener monopolist block all third-party garage-door apps. Then, Chamberlain stuck ads in its app, so you have to watch an ad to open your garage-door:
https://pluralistic.net/2023/11/09/lead-me-not-into-temptation/#chamberlain
Digital locks let John Deere block third-party repair of its tractors:
https://pluralistic.net/2022/05/08/about-those-kill-switched-ukrainian-tractors/
And they let Apple block third-party repair of iPhones:
https://pluralistic.net/2022/05/22/apples-cement-overshoes/
These companies built 11-foot ladders to get over their competitors' 10-foot walls, and then they kicked the ladder away. Once they were secure atop their walls, they committed enshittifying sins their fallen adversaries could only dream of.
I've been campaigning to abolish anticircumvention laws for the past quarter-century, and I've noticed a curious pattern. Whenever these companies stand to lose their legal protections, they freak out and spend vast fortunes to keep those protections intact. That's weird, because it strongly implies that their locks don't work. A lock that works works, whether or not it's illegal to break that lock. The reason Signal encryption works is that it's working encryption. The legal status of breaking Signal's encryption has nothing to do with whether it works. If Signal's encryption was full of technical flaws but it was illegal to point those flaws out, you'd be crazy to trust Signal.
Signal does get involved in legal fights, of course, but the fights it gets into are ones that require Signal to introduce defects in its encryption – not fights over whether it is legal to disclose flaws in Signal or exploit them:
https://pluralistic.net/2023/03/05/theyre-still-trying-to-ban-cryptography/
But tech companies that rely on digital locks manifestly act like their locks don't work and they know it. When the tech and content giants bullied the W3C into building DRM into 2 billion users' browsers, they categorically rejected any proposal to limit their ability to destroy the lives of people who broke that DRM, even if it was only to add accessibility or privacy to video:
https://www.eff.org/deeplinks/2017/09/open-letter-w3c-director-ceo-team-and-membership
The thing is, if the lock works, you don't need the legal right to destroy the lives of people who find its flaws, because it works.
Do digital locks work? Can they work? I think the answer to both questions is a resounding no. The design theory of a digital lock is that I can provide you with an encrypted file that your computer has the keys to. Your computer will access those keys to decrypt or sign a file, but only under the circumstances that I have specified. Like, you can install an app when it comes from my app store, but not when it comes from a third party. Or you can play back a video in one kind of browser window, but not in another one. For this to work, your computer has to hide a cryptographic key from you, inside a device you own and control. As I pointed out more than a decade ago, this is a fool's errand:
https://memex.craphound.com/2012/01/10/lockdown-the-coming-war-on-general-purpose-computing/
After all, you or I might not have the knowledge and resources to uncover the keys' hiding place, but someone does. Maybe that someone is a person looking to go into business selling your customers the disenshittifying plugin that unfucks the thing you deliberately broke. Maybe it's a hacker-tinkerer, pursuing an intellectual challenge. Maybe it's a bored grad student with a free weekend, an electron-tunneling microscope, and a seminar full of undergrads looking for a project.
The point is that hiding secrets in devices that belong to your adversaries is very bad security practice. No matter how good a bank safe is, the bank keeps it in its vault – not in the bank-robber's basement workshop.
For a hiding-secrets-in-your-adversaries'-device plan to work, the manufacturer has to make zero mistakes. The adversary – a competitor, a tinkerer, a grad student – only has to find one mistake and exploit it. This is a bedrock of security theory: attackers have an inescapable advantage.
So I think that DRM doesn't work. I think DRM is a legal construct, not a technical one. I think DRM is a kind of magic Saran Wrap that manufacturers can wrap around their products, and, in so doing, make it a literal jailable offense to use those products in otherwise legal ways that their shareholders don't like. As Jay Freeman put it, using DRM creates a new law called "Felony Contempt of Business Model." It's a law that has never been passed by any legislature, but is nevertheless enforceable.
In the 25 years I've been fighting anticircumvention laws, I've spoken to many government officials from all over the world about the opportunity that repealing their anticircumvention laws represents. After all, Apple makes $100b/year by gouging app makers for 30 cents on ever dollar. Allow your domestic tech sector to sell the tools to jailbreak iPhones and install third party app stores, and you can convert Apple's $100b/year to a $100m/year business for one of your own companies, and the other $999,900,000,000 will be returned to the world's iPhone owners as a consumer surplus.
But every time I pitched this, I got the same answer: "The US Trade Representative forced us to pass this law, and threatened us with tariffs if we didn't pass it." Happy Liberation Day, people – every country in the world is now liberated from the only reason to keep this stupid-ass law on their books:
https://pluralistic.net/2025/01/15/beauty-eh/#its-the-only-war-the-yankees-lost-except-for-vietnam-and-also-the-alamo-and-the-bay-of-ham
In light of the Trump tariffs, I've been making the global rounds again, making the case for an anticircumvention repeal:
https://www.ft.com/content/b882f3a7-f8c9-4247-9662-3494eb37c30b
One of the questions I've been getting repeatedly from policy wonks, activists and officials is, "Is it even possible to jailbreak modern devices?" They want to know if companies like Apple, Tesla, Google, Microsoft, and John Deere have created unbreakable digital locks. Obviously, this is an important question, because if these locks are impregnable, then getting rid of the law won't deliver the promised benefits.
It's true that there aren't as many jailbreaks as we used to see. When a big project like Nextcloud – which is staffed up with extremely accomplished and skilled engineers – gets screwed over by Google's app store, they issue a press-release, not a patch:
https://arstechnica.com/gadgets/2025/05/nextcloud-accuses-google-of-big-tech-gatekeeping-over-android-app-permissions/
Perhaps that's because the tech staff at Nextcloud are no match for Google, not even with the attacker's advantage on their side.
But I don't think so. Here's why: we do still get jailbreaks and mods, but these almost exclusively come from anonymous tinkerers and hobbyists:
https://consumerrights.wiki/Mazda_DMCA_takedown_of_Open_Source_Home_Assistant_App
Or from pissed off teenagers:
https://www.theverge.com/2022/9/29/23378541/the-og-app-instagram-clone-pulled-from-app-store
These hacks are incredibly ambitious! How ambitious? How about a class break for every version of iOS as well as an unpatchable hardware attack on 8 years' worth of Apple bootloaders?
https://pluralistic.net/2020/05/25/mafia-logic/#sosumi
Now, maybe it's the case at all the world's best hackers are posting free code under pseudonyms. Maybe all the code wizards working for venture backed tech companies that stand to make millions through clever reverse engineering are just not as mad skilled as teenagers who want an ad-free Insta and that's why they've never replicated the feat.
Or maybe it's because teenagers and anonymous hackers are just about the only people willing to risk a $500,000 fine and 5-year prison sentence. In other words, maybe the thing that protects DRM is law, not code. After all, when Polish security researchers revealed the existence of secret digital locks that the train manufacturer Newag used to rip off train operators for millions of euros, Newag dragged them into court:
https://fsfe.org/news/2025/news-20250407-01.en.html
Tech companies are the most self-mythologizing industry on the planet, beating out even the pharma sector in boasting about their prowess and good corporate citizenship. They swear that they've made a functional digital lock…but they sure act like the only thing those locks do is let them sue people who reveal their workings.

If you'd like an essay-formatted version of this post to read or share, here's a link to it on pluralistic.net, my surveillance-free, ad-free, tracker-free blog:
https://pluralistic.net/2025/05/14/pregnable/#checkm8
#pluralistic#apple#drm#og app#instagram#meta#dmca 1201#comcom#competitive compatibility#interop#interoperability#adversarial interoperability#who broke the internet#self-mythologizing#infosec#schneiers law#red team advantage#attackers advantage#luddism#seize the means of computation
428 notes
·
View notes
Text
F1 and Biometrics
Biometric gloves came into play in F1 in 2018 to give medical teams immediate access to important information regarding driver conditions after an incident. It allows for vitals to be measured before, at the time of an incident and after the crash until they are rescued and more advanced monitoring is able to be applied. It is also a big help if a driver is involved in a crash that means they are not accessible straight away or cannot be visualized for monitoring so this allows teams to get immediate access to this information.
According to the FIA website, this was a difficulty by medical teams when Carlos Sainz crashed in the 2015 Russian GP where he hit the barrier head-on at 153km/h (roughly 95mph). The first row of the barrier was resting on top of him, so medical teams had to wait for this to be removed before they had access to him. Thankfully he wasn’t hurt during this crash, but medical teams didn’t know this initially as this technology wasn’t available and being used.
The sensors were basically made custom to F1 drivers. Regular sensors had not been fire tested and were not comfortable enough for the drivers to wear for long races. They use Bluetooth technology and can send data within a 500m and are powered by a small battery that drivers charge before races.
Drivers gloves have a 3mm sensor that is stitched into the palm of the fabric and monitors their vital signs during races. They measure pulse oximetry which measures the amount of oxygen being carried in the blood as well as drivers pulse rates. Obviously if a driver has an injury that is affecting their breathing, this will show in the saturations that would decline rapidly. Having this technology allows physiological readings and biometrics to be continuously monitored throughout the race from start to finish. Data from the sensor transmits to an iPhone app and gives medical crews remote and advance information on the driver’s condition. The small biometric readers are flexible and fire resistant up to 1,800 degrees Celsius (3,272 degrees Fahrenheit) for 22 seconds.


In the future there are even plans to implement sensors for respiratory rate and temperature to further monitor drivers which will not only enhance safety features but allow teams and drivers to monitor performance better.
OMP, an equipment supplier, has been developing wearable biometric monitoring systems since the introduction of the biometric sensors in 2019. An undershirt equipped with sensors and a measurement unit would transmit and record biometric data allowing for real-time monitoring of health through ECG and thoracic expansion. This would allow monitoring of drivers heart rhythms and breathing rate which would not only benefit medical teams in the case of an incident but also help identify stress, fatigue and any alteration in conditions. This would be useful considering the amount of stress drivers have been put through in the past in hot countries for example Saudi Arabia GP 2023 when many drivers retired, had to be taken to medical, threw up in their helmets or passed out after the race.


TV crews can also display biometric data during broadcasts to show the physical condition of a driver as they battle on track. However, there have been questions about the ethics and use of biometrics and why can’t we as an audience see drivers heart rates etc on screen if this data is being constantly collected. The FIA has strict guidelines about the use of raw biometric data. Section 2.4 of the FIA Guidelines for the Collection and Usage of Biometric Data in Motorsport, states that the use of biometric data can be used for more than just medical and performance monitoring and can be used for entertainment and marketing purposes but only if it is changed from raw data into a variable to protect the private health information of the driver. The FIA won’t allow the use of biometric data to be publicly available in the original form/ measurement unless the driver provides informed consent.
Essentially, driver onboard vitals are likely not to be available live due to strict laws on data protection and sharing health related information about drivers as it is protected health information. In the case of an accident or emergency, data is not allowed to be used even if the information is changed to protect the driver unless it is for medical and rescue use and post-accident information.
Sources: (x) (x) (x) (x) (x)
This also led me down a rabbit hole and found another study (it was anonymous but if you’re a sleuth you can probably take a guess at what F1 driver it was) where they monitored his heart rate during qualifying to see what his average was throughout the race to test the cardiovascular strain F1 drivers are put under!
58 notes
·
View notes
Text
Very interesting iPhone vulnerability just dropped. Like most big current 0-days, this one requires chaining together many different vulnerabilities in order to be successful, but what makes this one different is that part of the exploit involves an undocumented hardware feature. Long story short: after boot is complete, all the code (as opposed to data) portions of kernel memory are made unwriteable even by the kernel itself, and this is enforced not in software but in hardware by the memory controller, so in theory it's immune to compromises of the OS. But if you write to a magic region of I/O-mapped memory together with a specific key, it bypasses this protection.
Now, what's very interesting is that this feature is not publicly documented anywhere. The researches say it might have been intended for debugging firmware, but that's only a guess. The fact that it needs a key seems to indicate that Apple probably knows about it internally and put in weak anti-exploit countermeasures, but again, we cannot be sure. So there are several different possibilities here:
Whoever made this exploit found it with brute-force exploration. That's not impossible, but the fact that you need to know the exact IOMM address and a key makes it unlikely.
The feature is known to Apple, which leads to three sub-possibilities: i) they were hacked and the exploit technique was exfiltrated, ii) somebody has a man on the inside who leaked it or iii) they were ordered to put this backdoor there by the Powers That Be.
The feature is not known to Apple and was put there by their chip vendors, and they were the ones who were either hacked, infiltrated, or coerced.
Final note: the entry point of the exploit was, once again, iMessage attachments, so if you have an iDevice and you're worried about stuff like this, AIUI Lockdown Mode would make you immune.
86 notes
·
View notes
Text
The Short Patreon Breakdown
Basic version of this post, for people with no attention span. For details on each of these points, please see the original post.
1. The iOS processing fees are a smokescreen covering up the actual devastating changes that Patreon is forcing creators into—including doing away with the two billing models used by most of the highest-earning creators on the platform, regardless of the impact this will have on their livelihood.
2. Patreon is not going to change course for any reason. This is set in stone. CEO Jack Conte himself has been having one-on-one meetings and calls with the platform's top earners, and clearly has no interest in their actual grievances or how their businesses operate—only in getting them to stop complaining.
3. Patreon has offered no proof of their claims that the iOS app is responsible for 40 percent of the engagement on the platform—and also refuse to define what "engagement" means. Staff rebuff all requests for detailed analytics or data on the revenue share coming from the app, but did not refute the possibility that dismissing an app notification counted as "engagement."
4. Patreon does not have a refund policy in place to work with Apple in order to protect creators from malicious chargebacks, and has given no indication of any intent to work with Apple to shorten the time it takes for funds from iOS purchases to be paid out to creators—which is currently 75 days.
5. Patreon's own graphics meant to explain why this is necessary and how the new fees work are not correct: the fee structure graphic features a copying error that results in incorrect math, and adding together everything on the bar graph showing the daily active users by avenue of access comes to a total of 103 percent. They are woefully unprepared to share this information, and are putting it on us for "not understanding."
6. Patreon refuses to offer any promises to 18+ creators that they will not be removed from the app in order to adhere to Apple's content guidelines, instead only saying they currently have no plans to remove us from the app. Questioning this was met with a reminder that they've had to change the TOS for 18+ creators before.
7. All the features Patreon is insisting are integral for creator growth are inaccessible to 18+ creators, and questions about this were either dismissed, redirected, or ignored. 18+ creators can't even be found on either app, but we're being forced to cater to iOS' terms anyway, with claims that it's because all creators need the app in order to grow. Even though we can't utilize it.
8. Patreon's iOS app is currently* in violation of Apple's guidelines for app ratings; staff did not state any intention to become compliant by raising the app's rating as needed to maintain their 18+ creator community, only declaring that they're "exploring options." Per Apple's guidelines, the "options" are to either raise the rating to 17+, cutting off access for the wealthy teenagers with iPhones to which the platform is so dedicated they'll kneecap their top earner in order to court, or kick all 18+ creators off the platform. (This includes horror, true crime, health, trauma recovery, and more, not just sexual content.) *Current as of August 18, 2024.
Do not let the 30 percent App Store fee distract you from what's really going on here. Patreon is crippling a huge portion of their creators, including a horde of their top earners—and the single most profitable creator on the entire platform—and offering no legitimate reasons why. The amount of money they're losing from these creators restructuring or leaving altogether totals in the millions within a single month of activity. This isn't even about money, it's about something else—and there's no way to know what, because Patreon is giving us nothing.
#patreon#apple#ios app#app store#patreon fees#patreon billing#PSA#creators on tumblr#artists on tumblr#writers on tumblr#please signal boost this if you can
28 notes
·
View notes
Text
Privacy Concerns: How Gen Z is Protecting Their Data?
What’s the first thing you do when a pop-up asks, “Do you accept cookies?”—immediately click “Accept” or hesitate as if pondering the secrets of the universe?
If you’re Gen Z, the answer might surprise you. While they’re often labelled as the oversharing Snapchat generation, they’re also becoming the poster children for digital privacy warriors. Want to know how? Stick around. By the end of this blog, you’ll not only uncover Gen Z’s surprising strategies for safeguarding their data but also pick up a few tips to reclaim control of your own.

The Paradox of Gen Z: Masters of Oversharing, Yet Privacy-Conscious
On the surface, Gen Z seems like the generation that lives for Instagram reels, TikTok challenges, and viral tweets. But underneath the filters and hashtags lies a surprising truth: they care—deeply—about their digital footprints. They may post a dance video on TikTok but won’t hesitate to use pseudonyms on Facebook or create private Instagram accounts (finstas) to keep their personal lives personal.

How Did Gen Z Get So Privacy-Savvy?
Growing Up With Data Breaches
From hearing about massive breaches (remember the infamous Cambridge Analytica scandal?) to watching documentaries like The Social Dilemma, Gen Z grew up knowing that even their memes could fuel someone’s data-mining empire. Lesson learned? Share strategically.

Cybersecurity 101 Is Their Second Nature
For this generation, two-factor authentication isn’t optional—it’s a lifestyle. “123456” as a password? Please, that’s so 2010. Gen Z knows their passwords should look like they smashed their keyboard in frustration.

Tech Education in Schools
Unlike older generations, who stumbled their way through the internet’s dark corners, Gen Z often received digital literacy education. They know the difference between a phishing scam and an actual email from their bank. (Pro tip: If it starts with “Dear Customer,” run.)

Privacy Tips We Can All Steal (Ethically, of Course)
Gen Z is showing us the way, and here are some of their best practices:
Think Before You Link
Clicking on that shady “You’ve Won a Free iPhone!” ad is the digital equivalent of walking into a trap. Gen Z gets it—they avoid suspicious links like the plague.

Limit Permissions
Why should a weather app need access to your contacts? Gen Z regularly audits app permissions, keeping unnecessary snoopers at bay.

Use Burners for Fun
They know that creating a “throwaway” email address for subscriptions keeps spam out of their primary inbox.

The Ironic Humor of Gen Z’s Privacy Stance
Isn’t it ironic that the generation branded as addicted to screens is leading the charge for digital privacy? They’ll meme about data breaches but won’t let companies snoop on their Spotify playlists.

Conclusion: A Balancing Act
Gen Z proves you can live your best digital life and protect your data. Whether it’s using VPNs, switching to encrypted messaging apps, or simply saying no to invasive permissions, they’re rewriting the rules for online privacy.
The takeaway? Protecting your data doesn’t mean going off the grid; it means being intentional with your digital choices.
Do you think Gen Z has cracked the code on balancing online presence and privacy, or are they just lucky digital natives? Drop your thoughts in the comments below!

6 notes
·
View notes
Text
Lately, the government and the top banks of Australia have been pushing for the eradication of payments by cash, leaving phone apps alone, and possibly a medical implant as well.

I have fought against it as best I can, buy there's not much I can do.
It's illegal to have large amounts of cash, and self defense is a crime, so storing at home is not really an option. Besides, I am a disabled pensioner, and the government decided long ago that going through the bank is mandatory.
Covid was the best opportunity they ever had to eliminate personal freedom - I mean, to force everyone to use insecure apps on insecure phones that had insecure operating systems on insecure hardware.
There were scandal when apps were exposed data harvesting, accessing information they didn't have the rights to, and even hacking the microphone and camera of the phone.
https://www.consumerreports.org/electronics-computers/privacy/how-to-protect-yourself-from-camera-and-microphone-hacking-a1010757171/
But the push to do the thing was relentless. You can't stop progress! Nobody else is complaining, the bank told me.
Except people do complain, helpless and hopeless. I worked in tech support, and would hear all day long the agony of those whose assets were cleaned out, and that was in the days of internet banking, when the scammer call centers of India were just a sparkle in Satan's Eye.
You see, the reason banks existed was that they took money in exchange for the service of PROTECTION.
Now, they take your money, and if you get robbed, that's a YOU problem.
And the government is backing them up. Remember the GFC, when most governments expressed their hatred of capitalism by backing banks no matter how badly they embezzled customers?
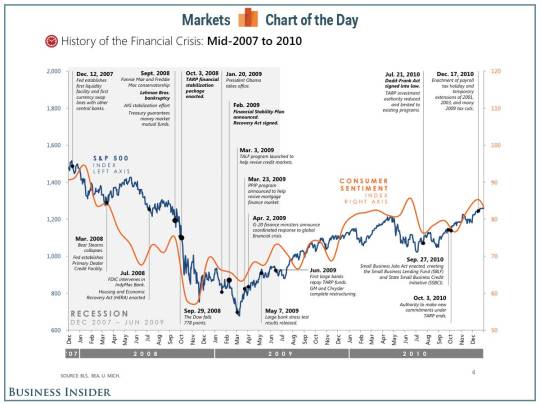
The Bank and the State had merged.
Mussolini's vision had succeeded.
Fascism took a century, but it in the end, it won. But I am not sure even the 1930s fascists could see this coming.
youtube
21 notes
·
View notes
Text
Blog post #3
Has technology reached its limit?
Over time, technology has had many advancements. This has been shown to be a good thing but it also comes with its flaws. When technology began to become popular, it also started to advance but almost to a point in which society could not keep up. Today, we have many different brands and versions of iphones, computers, and artificial intelligence (AI) databases and every year there are more and more new versions coming out. One of the points that is made in the Automating Inequality article by Eubanks, it talks about data collection by different media companies. This is a challenge because it mainly happens with those that are a part of the lower class and happen without their knowledge. I think that if this continues, technology will have reached its limit and there will be nowhere else for it to go.
If so much data collection is happening, can the automated voice be trusted?
Given all the data collection that happens without people’s knowledge, it is hard to tell what can be trusted amongst government websites. When calling government systems such as health care companies, there is an automated voice that asks questions and you have to respond by speaking or typing the answers in. This system is always taking in this information and storing it in their databases and we can never know where all of the information is going. It is taking the process of talking to actual humans out of the picture “We have ceded much of that decision making power to sophisticated machines” (Eubanks, p. 13). In the future, if this process continues, we may end up talking to computers and robots who will gather our information.
Could data collection be avoided?
I think that data collection is something that can’t be completely avoided but some precautionary measures can be taken. This could look like companies making security systems more challenging to get into, making for the government on how and when they can pull our information.
Where do you see technology going in the next ten years?
In the next ten years, I see technology advancing more than it ever has. I think that AI could take over and be used for both good and bad. This could look like AI protecting us for good but for bad could look like people abusing its advancements. I believe that if technology gets too advanced, it could end up being abused by the wrong kind of people.
Eubanks, Automating Inequality. Pdf
7 notes
·
View notes
Text
so, in order. left the house where the person who's ruining my life's at. came back home.
decided to stop by the post office. packages are still at the customs, whatever, it's fine, i'm back home so i'm having a grand day. come back home.
arrive to my neighbors saying i got a letter in the mail from america two hours ago. my stickers have arrived in the most a most thoroughly lovingly crafted and signed envelope ever. i open them, geek out, put them somewhere safe. also put my notebook in front of the heater so as to make sure it doesn't absorb moisture from the air.
circa 6:30. ohhh SHIT, oh SHIT, my bowie tapes have been at the post office for six days now, i'd better go pick them up! leave around 6:50, be there around 7, 7:10. "hello, i'm back, minus the luggage. can you check for another package, please?"
they have it.
i pick up the small air packet. i cannot believe it's in my hands, after two whole months of waiting. i store it in my puffer jacket so as to protect it from the rain in addition to the umbrella above me. it's a very precious package.
midway down the road, i get a call for my brother. "[REDACTED] my dearest, how are you?!" "My DEEEAREST [BROTHER]!!!!" we gush at each other for a while because we haven't spoken in so long and texts have been scarce, so as to not get me in trouble.
yesterday he mentioned having good news. i thought it might have to do with the thing that damn near destroyed my life, but nay, i dare not look forward to what i cannot see lies ahead of me. but i still hope a little bit.
i ask him if it's alright to call him when i get back home in 5-10 minutes. he says it's fine, but he'll spoil me on the best of news a little bit.
"It's got [something] to do with Android. (Cue unbeLIEVABLY large gasp from yours truly.) Nothing solved yet, but we're on a very very good path!"
i walk back home at a brisk but stiff pace (because i'm carrying my package just a taaad bit under my forearm, so i'm very stiff and a bit hunched over to prevent it from falling down my jacket), with a fuzzy head, in total disbelief and completely elated.
i enter my home, drop everything, enter my room, call up my brother. (promptly forgetting about the package, which i only notice when it softly lands on my bed from the jacket. check for damage then place it away.) i ask him to tell me about his day first like he had intended, he does. some daily bummers, but talking helps.
he then tells me the news. he, ironically, found the greatest answer at an apple service clinic. oh, the irony here is stellar - i resent iphones and other apple devices, but let's just say they're called "genius bar" for a reason. they knew exactly what me and my brother have been chasing after for months, and suggested two paths - chip-off (risky, but hella reliable if it works), and something called j-tag. brother subsequently found two people who do this - one being a british group who does chip-off but doesn't specialize in encrypted data recovery, the other being a literal counterintelligence group based in australia that does literally everything we could ask them to. currently they just need to check if they have the appropriate software for my exact phone model (a huawei make) and state the price.
i report the good news about all the packages i received today, plus the artbook i ordered. then my brother has to go eat dinner and stop by the convenience store, so we part.
i walk around the kitchen mostly on my toe tips listening to "i wonder" with my eyes closed and my arms spread out as if i'm ascending to heaven. my happy ending. finally at my doorstep. i feel like i'm about to fly up and into the ceiling.
i'm tired. i'm really tired, and it took me an hour to write this, but this is the contender for the best day in my entire life. i still can't believe that.
#logs#this is the most hopeful happiness-infused post i'll ever make on here. drink it in‚ fellas. drink it alllll in.
7 notes
·
View notes
Text
Buy Apple ID Accounts What Is Apple ID Accounts?Buy Apple ID Accounts. An Apple ID is a user account that allows access to various Apple services and products, such as the App Store, iCloud, iTunes, Apple Music, and more. It serves as a single sign-in across all Apple devices and services. The account is tied to the user’s email address and is used to manage personal information, make purchases, and synchronize data across devices like iPhones, iPads, Macs, and more.Key features of an Apple ID account include:Access to Apple Services: With an Apple ID, users can access Apple services like iCloud for data storage, Apple Music for streaming, iTunes for media purchases, and the App Store for downloading apps.Device Synchronization: Apple ID allows users to sync their settings, photos, contacts, and apps across all their Apple devices using iCloud.Security Features: Apple ID comes with security features like two-factor authentication (2FA) to protect against unauthorized access.Purchase Management: Users can store payment information and make purchases through Apple’s digital stores, including apps, music, movies, and other content.Backup and Recovery: With iCloud, Apple ID provides a way to back up device data and restore it if the device is lost or replaced.Find My iPhone/Mac: This feature helps users locate their devices in case they are lost or stolen by using their Apple ID credentials.Essentially, an Apple ID acts as a digital identity within Apple’s ecosystem, allowing seamless use of Apple’s hardware, software, and services.
24 Hours Reply/Contact Telegram: @smmvirals24 WhatsApp: +6011-63738310 Skype: smmvirals Email: [email protected]
2 notes
·
View notes
Text
What Is Apple ID Accounts?
Buy Apple ID Accounts. An Apple ID is a user account that allows access to various Apple services and products, such as the App Store, iCloud, iTunes, Apple Music, and more. It serves as a single sign-in across all Apple devices and services. The account is tied to the user’s email address and is used to manage personal information, make purchases, and synchronize data across devices like iPhones, iPads, Macs, and more.
Key features of an Apple ID account include:
Access to Apple Services: With an Apple ID, users can access Apple services like iCloud for data storage, Apple Music for streaming, iTunes for media purchases, and the App Store for downloading apps.
Device Synchronization: Apple ID allows users to sync their settings, photos, contacts, and apps across all their Apple devices using iCloud.
Security Features: Apple ID comes with security features like two-factor authentication (2FA) to protect against unauthorized access.
Purchase Management: Users can store payment information and make purchases through Apple’s digital stores, including apps, music, movies, and other content.
Backup and Recovery: With iCloud, Apple ID provides a way to back up device data and restore it if the device is lost or replaced.
Find My iPhone/Mac: This feature helps users locate their devices in case they are lost or stolen by using their Apple ID credentials.
Essentially, an Apple ID acts as a digital identity within Apple’s ecosystem, allowing seamless use of Apple’s hardware, software, and services.
24 Hours Reply/Contact Telegram: @smmvirals24 WhatsApp: +6011-63738310 Skype: smmvirals Email: [email protected]
2 notes
·
View notes
Text
The UK Home Office is demanding that Apple provide the government backdoor access to users’ encrypted data. Not only are they interested in accessing data on British citizens, but the government has stated it needs access to ALL encrypted iCloud data worldwide on the premise of national security and public safety.
The Home Secretary’s office believes the U.K. Investigatory Powers Act of 2016 legally authorizes law enforcement to obtain communications data on the premise of collecting evidence, as the government has deemed everyone a potential threat. Governments do not want the people to have end-to-end encryption that they cannot access.
The Advanced Data Protection program launched by Apple in 2022 provides users with the ability to safely keep their data. Users must enable the service, but it prevents even Apple from having backdoor encryption keys. Edward Snowden warned that the British Government Communications Headquarters (GCHQ) and NSA successfully hacked all iPhones, Androids, and Blackberry devices. The FBI in the United States tried to prevent Apple from launching this program during Trump’s first term, stating it prevented them from properly investigating crimes. The FBI also demanded that Apple provide it with backdoor access back in 2016 after the 2015 release of the iOS 9 that the government could not easily access.
US intelligence cited the San Bernadino mass shooting incident as an example of why the government must have access to user data. One of the shooters owned an iPhone 5C and the FBI and NSA claimed it could not access the device. The US government and Apple battled in court over the FBI’s insistence that Apple create “GovtOS” to override any encryption measures. The government attempted to use the All Writs Act to force Apple into compliance.
3 notes
·
View notes
Text
Citizens of the European Union live in an internet built and ruled by foreign powers. Most people in the EU use an American search engine, shop on an American ecommerce site, thumb American phones, and scroll through American social media feeds.
That fact has triggered increasing alarm in the corridors of Brussels, as the EU tries to understand how exactly those companies warp the economy around them. Five years ago, Shoshana Zuboff’s book The Age of Surveillance Capitalism neatly articulated much of lawmakers’ critique of the tech giants, just as they were preparing to enforce the flagship GDPR privacy law. Now as the EU enacts another historic piece of tech regulation, the Digital Markets Act, which companies must comply with starting tomorrow, March 7, a different critic du jour sums up the new mood in Brussels.
In his 2023 book, Technofeudalism, Yanis Varoufakis argues the big US tech platforms have brought feudalism back to Europe. The former Greek finance minister sees little difference between the medieval serf toiling on land he does not own and the Amazon seller who must subject themselves to the company’s strict rules while giving the company a cut of each sale.
The idea that a handful of big tech companies have subjugated internet users into digital empires has permeated through Europe. Technofeudalism shares bookshelf space with Cloud Empires and Digital Empires, which make broadly similar arguments. For years, Europe’s wanna-be Big Tech rivals, like Sweden’s Spotify or Switzerland’s ProtonMail, have claimed that companies like Google, Meta, and Apple unfairly limit their ability to reach potential users, through tactics like preinstalling Gmail on new Android phones or Apple’s strict rules for the App Store. “It’s not a problem to be a monopoly,” says Sandra Wachter, professor of technology and regulation at Oxford University’s Internet Institute. “It becomes a problem if you're starting to exclude other people from the market.”
Crowbarred Open
In answer to that problem, Brussels’ politicos agreed to the Digital Markets Act in 2022. It is designed to rein in the largest tech companies—almost all of them from the US—that act as gatekeepers between consumers and other businesses. A sibling regulation, the Digital Services Act, which focuses more on freedom of expression, went into effect last month. Wachter says they follow a long tradition of laws trying to protect the public and the economy from state power, wielded either by the government or the monarch. “With the rise of the private sector and globalization, power has just shifted,” she adds. Tech platforms rule over digital lives like kings. The DMA is part of the attempt to keep up.
The rules change tomorrow for platforms deemed “gatekeepers” by the DMA—so far including Alphabet, Amazon, Apple, Meta, Microsoft, and TikTok parent Bytedance. The law essentially crowbars open what the EU calls the gatekeepers’ “core services.” In the past regulators have proposed containing corporate giants by taking them to pieces. EU lawmakers have adopted the motto “Don’t break up big tech companies, break them open.”
In theory, that means big changes for EU residents’ digital lives. Users of iPhones should soon be able to download apps from places other than Apple’s app store; Microsoft Windows will no longer have Microsoft-owned Bing as its default search tool; Meta-owned WhatsApp users will be able to communicate with people on rival messaging apps; and Google and Amazon will have to tweak their search results to create more room for rivals. There will also be limits on how users’ data can be shared between one company’s different services. Fines for noncompliance can reach up to 20 percent of global sales revenue. The law also gives the EU recourse to the nuclear option of forcing tech companies to sell off parts of their business.
Homegrown Challengers
Most tech giants have expressed uncharacteristic alarm about the changes required of them this week. Google has spoken of “difficult trade-offs,” which may mean its search results send more traffic to hotel or flight aggregators. Apple has claimed that the DMA jeopardizes its devices’ security. Apple, Meta and TikTok have all filed legal challenges against the EU, saying new rules unfairly target their services. The argument in favor of the status quo is that competition is actually thriving—just look at TikTok, a technology company launched in the past decade, now designated as one of the so-called gatekeepers.
But TikTok is an exception. The DMA wants to make it normal for new household names to emerge in the tech industry; to “drive innovation so that smaller businesses can really make it,” as the EU’s competition chief Margrethe Vestager explained to WIRED, back in 2022. Many hope some of the new businesses that “make it” will be European. For almost every big tech service, there is a smaller homegrown equivalent: from German search engine Ecosia to French messaging app Olvid and Polish Amazon alternative Allegro. These are the companies many hope will benefit from the DMA, even if there is widespread skepticism about how effective the new rules will be at forcing the tech giants to change.
Today, US-based Epic Games said Apple had terminated its European developer account, soon after Epic announced it would take advantage of the DMA to open a new games store for iOS. Apple told WIRED that Epic was untrustworthy and Apple has the right to terminate the accounts of any of Epic's wholly owned subsidiaries following a 2021 court judgment. “Apple chose to exercise that right,” a statement provided by company spokesperson Rob Saunders said.
App Stores will be an early area of focus for DMA enforcement, Vestager said this week. But Europeans can’t expect the internet to transform overnight. In its early days, the new law’s effects will be more about the power struggles behind the curtain of the world’s biggest companies; not about making netizens’ lives easier. In fact, their online experience is likely to get messier at first. There will probably be even more website pop-ups. “This dominant position that these companies have is partially because we have been so addicted to convenience,” says Anu Bradford, a professor at Columbia Law School and author of Digital Empires: The Global Battle to Regulate Technology. The new rules will mean users have to reengage with what they want their online lives to look like, she adds. Defaults set by US corporations will no longer be chosen for them.
Instead the DMA’s objective is to remind Europeans what they traded in exchange for that convenience in the first place. The DMA is about power, not necessarily convenience. Whether Europeans will be able to remember that as their online worlds are cracked open remains to be seen.
15 notes
·
View notes