#Advanced Data Protection
Explore tagged Tumblr posts
Text
If you are outside the UK and concerned about who can see your data, ADP adds an extra layer of security by making it unreadable even by Apple. If ADP is disabled, your data could be at risk because it can still be unlocked by Apple, a legal request or a data breach.
#ADP#Advanced Data Protection#Apple#Desktop#Desktop/Laptop#iPad#iPhone#iPhone/iPad#Laptop#Mac#PC#Windows
0 notes
Text
Apple cedează presiunilor autorităților britanice: Criptarea end-to-end pentru iCloud, dezactivată în Marea Britanie
Apple a confirmat oficial că renunță la criptarea end-to-end oferită prin sistemul Advanced Data Protection (ADP) pentru utilizatorii iCloud cu conturi nou create în Regatul Unit, urmând ca și utilizatorii existenți să fie afectați de această decizie. Acest pas marchează un compromis semnificativ în politica de confidențialitate a companiei americane, realizat în urma presiunilor exercitate de…
#ADP#Advanced Data Protection#apple#backdoor#bam#cloud storage#Confidențialitate#criptare end-to-end#cybersecurity#data protection#diagnosis#diagnoza#end-to-end encryption#icloud#Marea Britanie#neamt#online security#privacy#Protecția datelor#Regatul Unit#roman#securitate cibernetică#securitate online#UK#United Kingdom
0 notes
Text
Marshall Commander Fox is scarcely seen without his iconic helmet, even within the confines of the Coruscant guards headquarters. The freshest of shinies usually don’t see his face until a few rotations into their deployment, even then usually in private moments and passing chances. The very rare occasion Fox eats with his corries in the mess hall (the times he actually has time to), glances of Fox in the medical bay being treated after a sideways operation (only after everyone else has been cared for by his firm insistence,) the training assessments he’s able to schedule and be apart of and participate in (swift healing to the pride of cocky shinies he calls to the sparring mat.)
Rather, it’s not impossible that he’s most often unhelmed in the situations of senate view.
Talking down antsy senators is one thing, and there’s numerous reasons why Fox’s number one rule for his Corries to follow is to never remove your helmet in senate view. The ability to decorate yourself and make yourself unique is a freedom the Coruscant guard gets to indulge very little in. They can’t decorate their armor for their own safety, and still enabling them the freedom to decorate their bodies and hair Fox is thankful he’s able to allow. But Fox’s mismatched armor isn’t unique to be hypocritical towards his own rules and troopers. It’s to protect them.
When a senator finds yet another fickle complaint about the troopers in red, they can’t discern amongst a selective Trooper to pin the blame. But in the line of white and red, Fox’s red and white armor catches their eye. There’s someone they can funnel their frustrations towards. Fox’s scars, hardened eyes, and graying hairs is the only face they’ve seen helmetless, the face they think about when building their ire.
#headcanon bittercafanddatapads#drabble bittercafanddatapads#marshal commander fox#star wars commander fox#star wars ask blog#coruscant guard#I hope this makes sense#apologies in advanced for spelling mistakes or odd wording I’m not wearing my contacts#a small thought for y’all as I sit here thinking about it#his helmet also protects his eyes from blue light and the interior screen makes filling out data pads 10 x more convenient
146 notes
·
View notes
Text

The UK no longer has end to end encryption thanks to Keir Starmer’s Labour government reanimating the zombie policy that is the Snoopers Charter, first peddled by Theresa May’s Tory government and rejected by the public.
Apple withdrawing end-to-end encrypted backups from the UK "creates a dangerous precedent which authoritarian countries will surely follow".
UK now likened to authoritarian regimes and why Starmer won’t challenge Trump since he is in lock step with US policies, openly goes after sick, disabled, pensioners and poorest, increasing their hardship rather than tax the mega rich. US policy is UK policy.
So what does this mean for Apple users in the UK?
All your data in the cloud is no longer secure in comparison to having ADP enabled and can be accessed by the government upon request. The GDPR is all but dead in the UK, there are now so many government policies that snoop on us by the back door with even news outlets online now charging us for access without *cookies enabled (data farming you whilst you read with no option to opt out unless you pay)
I checked with the ICO myself and it is a fully approved policy despite its contradiction to the rights of consent, removed in the process.
If you want a workaround here are my suggestions
Cancel your iCloud storage, your data will stay on the cloud until the renewal date, use that time to back it up locally or on a flash drive.

Change your iMessage settings to delete audio messages after 2 minutes and permanently delete messages after 30 days.
Alternatively, use a third party messaging app with a delete on read feature and disable Apple iMessage altogether.
If you are tech savvy you can set up a USB drive or flash drive directly into your router hub (you should have at least one USB slot, some have two) and use FTP to back up over wifi, you can do this on any device, you don’t need a desktop.
Use a VPN service or set one up. If you’re really technical you can use a Raspberry Pi to do this, but you will need to hard code it. Think Mr Robot.
This change does not impact sensitive data like medical details which remain end to end encrypted.
If you want to learn more on the sweeping bills being pushed through government and any action your can take visit Big Brother Watch: https://bigbrotherwatch.org.uk
*If you want to read news articles without paying for the privilege of not handing over your cookie data, simply disable javascript within your browsers settings and refresh the browser page. Remember to turn it back on when your done. Alternatively disable all cookies but know this will impact your online experience and access.
#big brother watch#orwellian#labour government#data privacy#end to end encryption#apple#government#uk politics#equality#discrimination#the matrix#advance data protection#big brother#1984#distopia#keir starmer#authoritarian#totalitarian#fascisim#police state#Theresa May#gdpr#Information Commissioner's Office#ICO
17 notes
·
View notes
Text
Elevate Client Services with Excel: Expert Tips for Financial Consultants by Grayson Garelick

Financial consultants operate in a dynamic environment where precision, efficiency, and client satisfaction are paramount. Excel, as a versatile tool, offers an array of features that can significantly enhance the services provided by financial consultants. Grayson Garelick, an accomplished financial analyst and consultant, shares invaluable Excel tips to help financial consultants elevate their client services and add tangible value.
The Role of Excel in Financial Consulting
Excel serves as the backbone of financial consulting, enabling consultants to analyze data, create models, and generate insights that drive informed decision-making. As the demands of clients become increasingly complex, mastering Excel becomes essential for financial consultants aiming to deliver exceptional services.
1. Customize Excel Templates
One of the most effective ways to streamline workflows and improve efficiency is by creating customized Excel templates tailored to specific client needs. Grayson suggests developing templates for budgeting, forecasting, and financial reporting that can be easily adapted for different clients, saving time and ensuring consistency.
2. Utilize PivotTables for Data Analysis
PivotTables are powerful tools in Excel that allow financial consultants to analyze large datasets and extract meaningful insights quickly. Grayson emphasizes the importance of mastering PivotTables for segmenting data, identifying trends, and presenting information in a clear and concise manner to clients.
3. Implement Conditional Formatting
Conditional formatting is a valuable feature in Excel that allows consultants to highlight important information and identify outliers effortlessly. By setting up conditional formatting rules, consultants can draw attention to key metrics, discrepancies, or trends, facilitating easier interpretation of data by clients.
4. Leverage Excel Add-ins
Excel offers a variety of add-ins that extend its functionality and provide additional features tailored to financial analysis and reporting. Grayson recommends exploring add-ins such as Power Query, Power Pivot, and Solver to enhance data manipulation, modeling, and optimization capabilities.
5. Automate Repetitive Tasks with Macros
Macros enable financial consultants to automate repetitive tasks and streamline workflows, saving valuable time and reducing the risk of errors. Grayson advises recording and editing macros to automate tasks such as data entry, formatting, and report generation, allowing consultants to focus on value-added activities.
6. Master Advanced Formulas and Functions
Excel's extensive library of formulas and functions offers endless possibilities for financial analysis and modeling. Grayson suggests mastering advanced formulas such as VLOOKUP, INDEX-MATCH, and array formulas to perform complex calculations, manipulate data, and create sophisticated models tailored to client needs.
7. Visualize Data with Charts and Graphs
Visualizing data is essential for conveying complex information in an easily digestible format. Excel offers a variety of chart types and customization options that enable consultants to create compelling visuals that resonate with clients. Grayson recommends experimenting with different chart styles to find the most effective way to present data and insights.
8. Collaborate and Share Workbooks Online
Excel's collaboration features enable financial consultants to work seamlessly with clients, colleagues, and stakeholders in real-time. Grayson highlights the benefits of sharing workbooks via OneDrive or SharePoint, allowing multiple users to collaborate on the same document, track changes, and maintain version control.
9. Protect Sensitive Data with Security Features
Data security is a top priority for financial consultants handling sensitive client information. Excel's built-in security features, such as password protection and encryption, help safeguard confidential data and ensure compliance with regulatory requirements. Grayson advises implementing security protocols to protect client data and maintain trust.
10. Stay Updated with Excel Training and Certification
Excel is a constantly evolving tool, with new features and updates released regularly. Grayson stresses the importance of staying updated with the latest Excel training and certification programs to enhance skills, explore new capabilities, and maintain proficiency in Excel's ever-changing landscape.
Elevating Client Services with Excel Mastery
Excel serves as a catalyst for innovation and excellence in financial consulting, empowering consultants to deliver exceptional services that add tangible value to clients. By implementing Grayson Garelick Excel tips, financial consultants can streamline workflows, enhance data analysis capabilities, and foster collaboration, ultimately driving client satisfaction and success. As financial consulting continues to evolve, mastering Excel remains a cornerstone of excellence, enabling consultants to thrive in a competitive landscape and exceed client expectations.
#Financial Consulting#grayson garelick#Customize Excel Templates#Utilize PivotTables#Implement Conditional Formatting#Leverage Excel Add-ins#Automate Repetitive Tasks with Macros#Advanced Formulas and Functions#Visualize Data with Charts and Graphs#Collaborate and Share Workbooks#Protect Sensitive Data with Security#Stay Updated with Excel Training#Elevating Client Services with Excel
3 notes
·
View notes
Text
Apple has taken the unprecedented step of removing its strongest data security tool from customers in the UK, after the government demanded “backdoor” access to user data. UK users will no longer have access to the advanced data protection (ADP) tool, which uses end-to-end encryption to allow only account holders to view items such as photos or documents they have stored online in the iCloud storage service. Apple said it was “gravely disappointed” that it would no longer be able to offer the security feature to British customers, after the UK government asked for the right to see the data. It said the removal of the tool would make users more vulnerable to data breaches from bad actors, and other threats to customer privacy. It would also mean all data was accessible by Apple, which could share it with law enforcement if they had a warrant. Earlier this month the Home Office served Apple a request under the Investigatory Powers Act, which compels firms to provide information to law enforcement agencies, asking for the right to see users’ encrypted data, which currently not even Apple can access. After the change at 3pm on Friday, new users had no access to the ADP tool and existing users would need to disable the security feature at a later date. Messaging services like iMessage and FaceTime would remain end-to-end encrypted by default. Apple said: “We are gravely disappointed that the protections provided by ADP will not be available to our customers in the UK given the continuing rise of data breaches and other threats to customer privacy. Enhancing the security of cloud storage with end-to-end encryption is more urgent than ever before.
continue reading
Not to worry, UK iPhone users, the UK government will never misuse this power, and I'm sure the threat of security breaches is a small price to pay so that the government can snoop on you.
Time to buy a large capacity external drive if you live in the UK.
6 notes
·
View notes
Text
Dark Web Monitoring

🔒 Safeguard Your Business in the Digital Age with Century Solutions Group! 🔒
🚨 Did You Know? The Dark Web is a hidden marketplace where stolen business data is bought and sold—and small businesses are prime targets!
Imagine this: A small online retailer gets hacked, and customer data is exposed on the Dark Web. The result? Loss of trust, reputation damage, and financial setbacks.
💡 How Can You Stay Protected?
🔍 Dark Web Monitoring – With Century Solutions Group, your business is constantly scanned for compromised data. If your credentials appear on illicit platforms, we alert you before the damage is done!
🛡️ Our Cybersecurity-First Approach Includes: ✅ Advanced Threat Protection – Firewalls, encryption, and AI-driven security. ✅ Employee Security Training – Your first line of defense is an informed team! ✅ Multi-Layered Defense – Strong passwords, MFA, and endpoint security. ✅ Secure Payment Transactions – Protect your customers & your revenue.
💼 Why Partner with Century Solutions Group? We’ve been Atlanta’s trusted IT MSP since 1996, offering cutting-edge cybersecurity solutions tailored for small businesses. Our proactive security approach means you can focus on growth—while we keep the bad guys out!
💪 Don’t wait for a cyberattack to react—stay ahead with Century Solutions Group! https://centurygroup.net/cloud-computing/cyber-security/
#CyberSafeBusiness #DarkWebDefense #CenturySolutionsGroup #MSP #SmallBizSecurity #CybersecurityAwareness
#Dark Web Monitoring#Cybersecurity#cybersecurity threats#data backup#Advanced Threat Protection#Employee Security Training#managed it services
2 notes
·
View notes
Text
Cybersecurity Tips to Secure Synology NAS against Ransomware
This month signifies the Cybersecurity Awareness Month. Therefore, I will be discussing some security best practices and offering “Cybersecurity Tips to Secure Synology NAS against Ransomware”. Please see How to disable Ads in Windows 11, How to Backup MacOS to Synology NAS via Time Machine, and how to Turn Off Windows 11 Tips and Suggestions Notifications. Many organisations struggle to manage…
#3-2-1 Backup Rule#configure Synology monitoring#Join Synology to the Domain#Offsite Backup#Synology#Synology Active Insights#Synology Configuration#Synology DS923+ NAS#Synology DSM 7.2#Synology Monitoring#Synology monitoring setup#Synology NAS#Synology NAS backup#Synology NAS monitoring#Synology Time Machine#Tips for Advanced Data Protection#VPN on Synology NAS
0 notes
Text

FIRST-EVER FOOTAGE OF INDONESIAN COELACANTH IN NORTH MALUKU REVEALS NEW INSIGHTS INTO RARE SPECIES
The coelacanth, often dubbed a "living fossil," is one of the most iconic and mysterious marine vertebrates. Long thought extinct until its rediscovery in 1938, only two species are known today—Latimeria chalumnae in the western Indian Ocean, and L. menadoensis in Indonesia. The latter, the Sulawesi coelacanth, lives in deep, difficult-to-access reef habitats and has rarely been observed alive. For the first time, divers using advanced technical diving equipment have filmed a live Indonesian coelacanth in situ, at a depth of over 150 metres in North Maluku, a region where the species had not previously been recorded.

Left profile of the coelacanth, with its unique pattern of white dots. Photo by Alexis Chappuis.

- Localities from whence the Sulawesi Coelacanth, Latimeria menadoensis, has been reported in black stars. White star shows the North Maluku Province, where the first in situ sighting by technical divers was made.
This sighting is more than just a milestone in exploration—it provides critical data on the ecology and distribution of an animal that is evolutionarily unique and highly vulnerable. With few individuals ever seen in the wild, each observation adds valuable insight into how these ancient fish live and where they might still be found. It also underscores the urgency of protecting deep reef habitats that are increasingly at risk from human activities. Understanding and safeguarding the ecosystems that support the coelacanth is essential if we hope to ensure its survival into the future.
Main photo: Deep diver about a meter behind the coelacanth discovered at a depth of -144 m in North Maluku, Indonesia. Photo by Alexis Chappuis.
Reference (Open Access): Chappuis et al. 2025 First record of a living coelacanth from North Maluku, Indonesia. Sci Rep
4K notes
·
View notes
Text
Breakthroughs in Space Technology: What’s on the Horizon?
Introduction
Space technology has always captured our imagination, pushing the boundaries of what is possible. As we venture further into the cosmos, remarkable breakthroughs are paving the way for new discoveries and advancements. In this article, TechtoIO delves into the exciting world of space technology, highlighting the latest innovations and what’s on the horizon for space exploration. Read to continue link
#Innovation Insights#Tagsadvanced propulsion systems#AI in space#colonizing other planets#commercial spaceflight#future of space technology#interstellar exploration#Mars missions#miniaturized satellites#moon missions#private space companies#radiation protection in space#reusable rockets#space debris solutions#space exploration#space technology#space technology breakthroughs#space tourism#space-based solar power#sustainable space exploration#Trends#Nvidia Drive#Analysis#Tech news#Science updates#Digital advancements#Tech trends#Science breakthroughs#Data analysis#Artificial intelligence
1 note
·
View note
Text
The Best Silent Phone License Privacy Protection in the UK

These days, with Silent Phone License Privacy Protection digital privacy becoming compromised more and more, it is critical to identify trustworthy ways to safeguard your private correspondence. The best option for encrypted communication and safe texting is the Silent Phone License. Let's explore how this cutting-edge platform protects your personal information in a world where cybersecurity threats are constantly changing.
#mobilephonedeals#latestmobilephones#smartphonesandaccessories#cellphones#luxuriousmobilephones#buyonlinelatestsmartphone#luxurymobilephonestore#cellphonesmanufactured#kickmobiles#mobilephonemanufacturingdeals#Encrypted Communication#Silent Phone License Secure Messaging#Advanced Encryption#Silent Phone License Data Protection#Silent Phone License
0 notes
Text
How to Choose the Right Antivirus Software: A Comprehensive Guide
In today’s digital age, where our lives are intricately intertwined with technology, safeguarding our digital assets has become paramount. With the proliferation of cyber threats, antivirus software stands as a crucial line of defense against malware, viruses, ransomware, and other malicious entities lurking online. However, the abundance of antivirus options can be overwhelming, making it…

View On WordPress
#A#Advanced Behavioral Analysis Software#Advanced Threat Detection#Antivirus#Antivirus Software#Automated Security Incident Response#Cloud Security Solutions#Cloud-Based Endpoint Security Platform#Comprehensive Data Protection Suite#Continuous Vulnerability Assessment#Cyber Defense#Cybersecurity#Cybersecurity Awareness Training#Data Encryption Software#Data Protection#Defense#Encryption#Endpoint Protection Suite#Endpoint Security#Firewall#Firewall Protection#Identity Theft#Identity Theft Prevention#Integrated Firewall Protection Mechanism#Internet Security Software#Malware#Malware Detection#Malware Removal Tool#Mobile Device Management#Multi-Layered Malware Defense System
0 notes
Text
Sigzen Technologies's Shield: Safeguarding Your Systems Through Advanced Server Patching
Sigzen Technologies’s Shield represents a paradigm shift in the landscape of cybersecurity defenses. Its multifaceted approach encompasses not just basic patching but a holistic, proactive strategy to fortify systems against evolving threats. This section aims to delve deeper into the core innovations that set Sigzen Technologies’s Shield apart in the domain of advanced server patching. Enhanced…
View On WordPress
#Advanced Server Patching#Data Security#Information Security#IT Infrastructure#IT Management#IT Security#Network Protection#Patch Management#Server Management#Server Security#Technology Solutions#Vulnerability Patching
1 note
·
View note
Text
Ethera Operation!!
You're the government’s best hacker, but that doesn’t mean you were prepared to be thrown into a fighter jet.
Bradley "Rooster" Bradshaw x Awkward!Hacker! FemReader
Part I


This was never supposed to happen. Your role in this operation was simple—deliver the program, ensure it reached the right hands, and let the professionals handle the breaching.
And then, of course, reality decided to light that plan on fire.
The program—codenamed Ethera—was yours. You built it from scratch with encryption so advanced that even the most elite cyber operatives couldn’t crack it without your input. A next-generation adaptive, self-learning decryption software, an intrusion system designed to override and manipulate high-security military networks, Ethera was intended to be both a weapon and a shield, capable of infiltrating enemy systems while protecting your own from counterattacks in real-time. A ghost in the machine. A digital predator. A weapon in the form of pure code. If it fell into the wrong hands, it could disable fleets, and ground aircraft, and turn classified intelligence into an open book. Governments would kill for it. Nations could fall because of it.
Not that you ever meant to, of course. It started as a little experimental security measure program, something to protect high-level data from cyberattacks, not become the ultimate hacking tool. But innovation has a funny way of attracting the wrong kind of attention, and before you knew it, Ethera had become one, if not the most classified, high-risk program in modern times. Tier One asset or so the Secret Service called it.
It was too powerful, too dangerous—so secret that only a select few even knew of its existence, and even fewer could comprehend how it worked.
And therein lay the problem. You were the only person who could properly operate it.
Which was so unfair.
Because it wasn’t supposed to be your problem. You were just the creator, the brain behind the code, the one who spent way too many sleepless nights debugging this monstrosity. Your job was supposed to end at development. But no. Now, because of some bureaucratic nonsense and the fact that no one else could run it without accidentally bricking an entire system, you had been promoted—scratch that, forcibly conscripted—into field duty.
And your mission? To install it in an enemy satellite.
A literal, orbiting, high-security, military-grade satellite, may you add.
God. Why? Why was your country always at war with others? Why couldn’t world leaders just, you know, go to therapy like normal people? Why did everything have to escalate to international cyber warfare?
Which is how you ended up here.
At Top Gun. The last place in the world you wanted to be.
You weren’t built for this. You thrive in sipping coffee in a cosy little office and handling cyber threats from a safe, grounded location. You weren’t meant to be standing in the halls of an elite fighter pilot training program, surrounded by the best aviators in the world—people who thought breaking the sound barrier was a casual Wednesday.
It wasn’t the high-tech cyberwarfare department of the Pentagon, nor some dimly lit black ops facility where hackers in hoodies clacked away at keyboards. No. It was Top Gun. A place where pilots use G-forces like a personal amusement park ride.
You weren’t a soldier, you weren’t a spy, you got queasy in elevators, you got dizzy when you stood too fast, hell, you weren’t even good at keeping your phone screen from cracking.
... And now you were sweating.
You swallowed hard as Admiral Solomon "Warlock" Bates led you through the halls of the naval base, your heels clacking on the polished floors as you wiped your forehead. You're nervous, too damn nervous and this damned weather did not help.
"Relax, Miss," Warlock muttered in that calm, authoritative way of his. "They're just pilots."
Just pilots.
Right. And a nuclear warhead was just a firework.
And now, somehow, you were supposed to explain—loosely explain, because God help you, the full details were above even their clearance level—how Ethera, your elegant, lethal, unstoppable digital masterpiece, was about to be injected into an enemy satellite as part of a classified mission.
This was going to be a disaster.
You had barely made it through the doors of the briefing room when you felt it—every single eye in the room locking onto you.
It wasn’t just the number of them that got you, it was the intensity. These were Top Gun pilots, the best of the best, and they radiated the kind of confidence you could only dream of having. Meanwhile, you felt like a stray kitten wandering into a lion’s den.
Your hands tightened around the tablet clutched to your chest. It was your lifeline, holding every critical detail of Ethera, the program that had dragged you into this utterly ridiculous situation. If you could’ve melted into the walls, you absolutely would have. But there was no escaping this.
You just had to keep it together long enough to survive this briefing.
So, you inhaled deeply, squared your shoulders, and forced your heels forward, trying to project confidence—chin up, back straight, eyes locked onto Vice Admiral Beau "Cyclone" Simpson, who you’d been introduced to earlier that day.
And then, of course, you dropped the damn tablet.
Not a graceful drop. Not the kind of gentle slip where you could scoop it back up and act like nothing happened. No, this was a full-on, physics-defying fumble. The tablet flipped out of your arms, ricocheted off your knee, and skidded across the floor to the feet of one of the pilots.
Silence.
Pure, excruciating silence.
You didn’t even have the nerve to look up right away, too busy contemplating whether it was physically possible to disintegrate on command. But when you finally did glance up—because, you know, social convention demanded it—you were met with a sight that somehow made this entire disaster worse.
Because the person crouching down to pick up your poor, abused tablet was freaking hot.
Tall, broad-shouldered, with a head of golden curls that practically begged to be tousled by the wind, and, oh, yeah—a moustache that somehow worked way too well on him.
He turned the tablet over in his hands, inspecting it with an amused little smirk before handing it over to you. "You, uh… need this?"
Oh, great. His voice is hot too.
You grabbed it back, praying he couldn't see how your hands were shaking. “Nope. Just thought I’d test gravity real quick.”
A few chuckles rippled through the room, and his smirk deepened like he was enjoying this way too much. You, on the other hand, wanted to launch yourself into the sun.
With what little dignity you had left, you forced a quick, tight-lipped smile at him before turning on your heel and continuing forward, clutching your tablet like it was a life raft in the middle of the worst social shipwreck imaginable.
At the front of the room, Vice Admiral Beau Cyclone Simpson stood with the kind of posture that said he had zero time for nonsense, waiting for the room to settle. You barely had time to take a deep breath before his voice cut through the air.
“Alright, listen up.” His tone was crisp, commanding, and impossible to ignore. “This is Dr Y/N L/N. Everything she is about to tell you is highly classified. What you hear in this briefing does not leave this room. Understood?”
A chorus of nods. "Yes, sir."
You barely resisted the urge to physically cringe as every pilot in the room turned to stare at you—some with confusion, others with barely concealed amusement, and a few with the sharp assessing glances of people who had no clue what they were supposed to do with you.
You cleared your throat, squared your shoulders, and did your best to channel even an ounce of the confidence you usually had when you were coding at 3 AM in a secure, pilot-free lab—where the only judgment you faced was from coffee cups and the occasional system error.
As you reached the podium, you forced what you hoped was a composed smile. “Uh… hi, nice to meet you all.”
Solid. Real professional.
You glanced up just long enough to take in the mix of expressions in the room—some mildly interested, some unreadable, and one particular moustached pilot who still had the faintest trace of amusement on his face.
Nope. Not looking at him.
You exhaled slowly, centering yourself. Stay focused. Stay professional. You weren’t just here because of Ethera—you were Ethera. The only one who truly understood it. The only one who could execute this mission.
With another tap on your tablet, the slide shifted to a blacked-out, redacted briefing—only the necessary information was visible. A sleek 3D-rendered model of the enemy satellite appeared on the screen, rotating slowly. Most of its details were blurred or omitted entirely.
“This is Blackstar, a highly classified enemy satellite that has been operating in a low-Earth orbit over restricted airspace.” Your voice remained even, and steady, but the weight of what you were revealing sent a shiver down your spine. “Its existence has remained off the radar—literally and figuratively—until recently, when intelligence confirmed that it has been intercepting our encrypted communications, rerouting information, altering intelligence, and in some cases—fabricating entire communications.”
Someone exhaled sharply. Another shifted in their seat.
“So they’re feeding us bad intel?” one of them with big glasses and blonde hair asked, voice sceptical but sharp.
“That’s the theory,” you confirmed. “And given how quickly our ops have been compromised recently, it’s working.”
You tapped again, shifting to the next slide. The silent infiltration diagram appeared—an intricate web of glowing red lines showing Etherea’s integration process, slowly wrapping around the satellite’s systems like a virus embedding itself into a host.
“This is where Ethera comes in,” you said, shifting to a slide that displayed a cascading string of code, flickering across the screen. “Unlike traditional cyberweapons, Ethera doesn’t just break into a system. It integrates—restructuring security protocols as if it was always meant to be there. It’s undetectable, untraceable, and once inside, it grants us complete control of the Blackstar and won’t even register it as a breach.”
“So we’re not just hacking it," The only female pilot of the team said, arms crossed as she studied the data. “We’re hijacking it.”
“Exactly,” You nodded with a grin.
You switched to the next slide—a detailed radar map displaying the satellite’s location over international waters.
“This is the target area,” you continued after a deep breath. “It’s flying low-altitude reconnaissance patterns, which means it’s using ground relays for some of its communication. That gives us a small window to infiltrate and shut it down.”
The next slide appeared—a pair of unidentified fighter aircraft, patrolling the vicinity.
“And this is the problem,” you said grimly. “This satellite isn’t unguarded.”
A murmur rippled through the room as the pilots took in the fifth-generation stealth fighters displayed on the screen.
“We don’t know who they belong to,” you admitted. “What we do know is that they’re operating with highly classified tech—possibly experimental—and have been seen running defence patterns around the satellite’s flight path.”
Cyclone stepped forward then, arms crossed, his voice sharp and authoritative. “Which means your job is twofold. You will escort Dr L/N’s aircraft to the infiltration zone, ensuring Ethera is successfully deployed. If we are engaged, your priority remains protecting the package and ensuring a safe return.”
Oh, fantastic, you could not only feel your heartbeat in your toes, you were now officially the package.
You cleared your throat, tapping the screen again. Ethera’s interface expanded, displaying a cascade of sleek code.
“Once I’m in range,” you continued, “Ethera will lock onto the satellite’s frequency and begin infiltration. From that point, it’ll take approximately fifty-eight seconds to bypass security and assume control."
Silence settled over the room like a thick cloud, the weight of their stares pressing down on you. You could feel them analyzing, calculating, probably questioning who in their right mind thought putting you—a hacker, a tech specialist, someone whose idea of adrenaline was passing cars on the highway—into a fighter jet was a good idea.
Finally, one of the pilots—tall, broad-shouldered, blonde, and very clearly one of the cocky ones—tilted his head, arms crossed over his chest in a way that screamed too much confidence.
“So, let me get this straight.” His voice was smooth, and confident, with just the right amount of teasing. “You, Doctor—our very classified, very important tech specialist—have to be in the air, in a plane, during a mission that has a high probability of turning into a dogfight… just so you can press a button?”
Your stomach twisted at the mention of being airborne.
“Well…” You gulped, very much aware of how absolutely insane this sounded when put like that. “It’s… more than just that, but, yeah, essentially.”
A slow grin spread across his face, far too entertained by your predicament.
“Oh,” he drawled, “this is gonna be fun.”
Before you could fully process how much you already hated this, Cyclone—who had been watching the exchange with his signature unamused glare—stepped forward, cutting through the tension with his sharp, no-nonsense voice.
“This is a classified operation,” he stated, sharp and authoritative. “Not a joyride.”
The blonde’s smirk faded slightly as he straightened, and the rest of the pilots quickly fell in line.
Silence lingered for a moment longer before Vice Admiral Beau Cyclone Simpson let out a slow breath and straightened. His sharp gaze swept over the room before he nodded once.
“All right. That’s enough.” His tone was firm, the kind that left no room for argument. “We’ve got work to do. The mission will take place in a few weeks' time, once we’ve run full assessments, completed necessary preparations, and designated a lead for this operation.”
There was a slight shift in the room. Some of the pilots exchanged glances, the weight of the upcoming mission finally settling in. Others, mainly the cocky ones, looked as though they were already imagining themselves in the cockpit.
“Dismissed,” Cyclone finished.
The pilots stood, murmuring amongst themselves as they filed out of the room, the blonde one still wearing a smug grin as he passed you making you frown and turn away, your gaze then briefly met the eyes of the moustached pilot.
You hadn’t meant to look, but the moment your eyes connected, something flickered in his expression. Amusement? Curiosity? You weren’t sure, and frankly, you didn’t want to know.
So you did the only logical thing and immediately looked away and turned to gather your things. You needed to get out of here, to find some space to breathe before your brain short-circuited from stress—
“Doctor, Stay for a moment.”
You tightened your grip on your tablet and turned back to Cyclone, who was watching you with that unreadable, vaguely disapproving expression that all high-ranking officers seemed to have perfected. “Uh… yes, sir?”
Once the last pilot was out the door, Cyclone exhaled sharply and crossed his arms.
“You realize,” he said, “that you’re going to have to actually fly, correct?”
You swallowed. “I—well, technically, I’ll just be a passenger.”
His stare didn’t waver.
“Doctor,” he said, tone flat, “I’ve read your file. I know you requested to be driven here instead of taking a military transport plane. You also took a ferry across the bay instead of a helicopter. And I know that you chose to work remotely for three years to avoid getting on a plane.”
You felt heat rise to your cheeks. “That… could mean anything.”
“It means you do not like flying, am I correct?”
Your fingers tightened around the tablet as you tried to find a way—any way—out of this. “Sir, with all due respect, I don’t need to fly the plane. I just need to be in it long enough to deploy Ethera—”
Cyclone cut you off with a sharp look. “And what happens if something goes wrong, Doctor? If the aircraft takes damage? If you have to eject mid-flight? If you lose comms and have to rely on emergency protocols?”
You swallowed hard, your stomach twisting at the very thought of ejecting from a jet.
Cyclone sighed, rubbing his temple as if this entire conversation was giving him a migraine. “We cannot afford to have you panicking mid-mission. If this is going to work, you need to be prepared. That’s why, starting next week you will train with the pilots on aerial procedures and undergoing mandatory training in our flight simulation program.”
Your stomach dropped. “I—wait, what? That’s not necessary—”
“It’s absolutely necessary,” Cyclone cut in, his tone sharp. “If you can’t handle a simulated flight, you become a liability—not just to yourself, but to the pilots escorting you. And in case I need to remind you, Doctor, this mission is classified at the highest level. If you panic mid-air, it won’t just be your life at risk. It’ll be theirs. And it’ll be national security at stake.”
You inhaled sharply. No pressure. None at all.
Cyclone watched you for a moment before speaking again, his tone slightly softer but still firm. “You’re the only one who can do this, Doctor. That means you need to be ready.”
You exhaled slowly, pressing your lips together before nodding stiffly. “Understood, sir.”
Cyclone gave a small nod of approval. “Good. Dismissed.”
You turned and walked out, shoulders tense, fully aware that in three days' time, you were going to be strapped into a high-speed, fighter jet. And knowing your luck?
You were definitely going to puke.
Part 2???
#top gun movie#top gun#top gun maverick#top gun fanfiction#top gun one shot#top gun fluff#bradley bradshaw#bradley rooster bradshaw#rooster bradshaw#bradley bradshaw x reader#bradley bradshaw fanfiction#bradley bradshaw imagine#bradley bradshaw x y/n#bradley bradshaw x you#bradley bradshaw x female reader#bradley bradshaw fic#bradley bradshaw fluff#top gun rooster#rooster fanfic#rooster x reader#rooster top gun#top gun maverick fanfic#top gun maverick fluff#top gun maverick x reader#jake seresin#jake seresin x reader#phoenix x reader#bob x reader#top gun hangman#pete maverick mitchell
2K notes
·
View notes
Text
"People across the world, and the political spectrum, underestimate levels of support for climate action.
This “perception gap” matters. Governments will change policy if they think they have strong public backing. Companies need to know that consumers want to see low-carbon products and changes in business practices. We’re all more likely to make changes if we think others will do the same.
If governments, companies, innovators, and our neighbors know that most people are worried about the climate and want to see change, they’ll be more willing to drive it.
On the flip side, if we systematically underestimate widespread support, we’ll keep quiet for fear of “rocking the boat”.
This matters not only within each country but also in how we cooperate internationally. No country can solve climate change on its own. If we think that people in other countries don’t care and won’t act, we’re more likely to sit back as we consider our efforts hopeless.
Support for climate action is high across the world
The majority of people in every country in the world worry about climate change and support policies to tackle it. We can see this in the survey data shown on the map.
Surveys can produce unreliable — even conflicting — results depending on the population sample, what questions are asked, and the framing, so I’ve looked at several reputable sources to see how they compare. While the figures vary a bit depending on the specific question asked, the results are pretty consistent.
In a recent paper published in Science Advances, Madalina Vlasceanu and colleagues surveyed 59,000 people across 63 countries.1 “Belief” in climate change was 86%. Here, “belief” was measured based on answers to questions about whether action was necessary to avoid a global catastrophe, whether humans were causing climate change, whether it was a serious threat to humanity, and whether it was a global emergency.
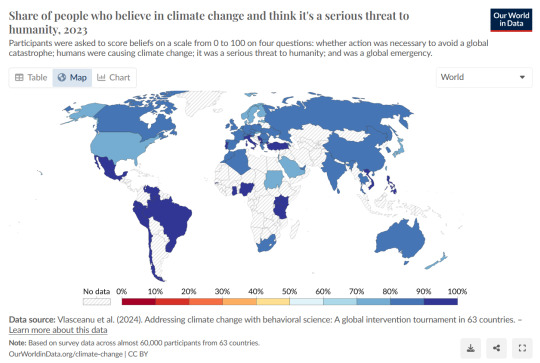
People think climate change is a serious threat, and humans are the cause. Concern was high across countries: even in the country with the lowest agreement, 73% agreed...
The majority also supported climate policies, with an average global score of 72%. “Policy support” was measured as the average across nine interventions, including carbon taxes on fossil fuels, expanding public transport, more renewable energy, more electric car chargers, taxes on airlines, and protecting forests. In the country with the lowest support, there was still a majority (59%) who supported these policies.
These scores are high considering the wide range of policies suggested.
Another recent paper published in Nature Climate Change found similarly high support for political change. Peter Andre et al. (2024) surveyed almost 130,000 individuals across 125 countries.2
89% wanted to see more political action. 86% think people in their country “should try to fight global warming” (explore the data). And 69% said they would be willing to contribute at least 1% of their income to tackle climate change...
Support for political action was strong across the world, as shown on the map below.

To ensure these results weren’t outliers, I looked at several other studies in the United States and the United Kingdom.
70% to 83% of Americans answered “yes” to a range of surveys focused on whether humans were causing climate change, whether it was a concern, and a threat to humanity. In the UK, the share who agreed was between 73% and 90%. I’ve left details of these surveys in the footnote.3
The fact is that the majority of people “believe” in climate change and think it’s a problem is consistent across studies."
-via Our World in Data, March 25, 2024
#climate change#climate action#climate hope#climate crisis#politics#global politics#environment#environmental news#good news#hope
1K notes
·
View notes
Video
youtube
Defending Against Evolving Threats: The Power of AI in Cybersecurity
#youtube#s technology advances and evolves so too does the threat landscape. In this video we'll discuss how AI can be used to protect digital data a
0 notes