#malware detection and classification
Explore tagged Tumblr posts
Text


What if he was human chat (he is human)
#tropical's art#digital art#art#collinlock16#minecraft arg but the protagonist is tired#I also find it super interesting that Kevin somehow made an antivirus that can detect entities#And in general just seems like a pretty solid antivirus#I also find it interesting that Digital Satan was a type of Malware (Worm) that also just so happened to be a sentient AI#Which I guess isn't really a paranormal entity#But falls under it I reckon#Do other entities have Malware classifications (that would be quite funny)#(Though only if the Kevin antivirus picks it up)#Kevin stop being a paranormal mercenary the cybersecurity world needs you#He is now a Computer Science major (headcanon) (dude should be in the industry) (he is a coder) (what a nerd)
70 notes
·
View notes
Text
The New Standard: Why AI Enablement and Built-in Security Are Must-have Features on Modern Storage Environments
Modern enterprises are generating data at an unprecedented pace, forcing IT teams to rethink storage from the ground up. Storage environments must now be more than scalable—they must be intelligent and inherently secure. This shift has made it clear that AI Enablement and Built-in Security Are Must-have Features on modern storage environments.

Gone are the days of reactive IT strategies. Businesses now require storage systems that anticipate demands, respond to threats in real time, and optimize themselves continuously. At Businessinfopro, we help organizations adopt modern storage solutions that are built with AI and security at the core—because anything less is a risk to both operations and innovation.
The Shift to Smart, Secure Storage
The traditional role of storage was simple: archive data and retrieve it when needed. But this approach doesn’t scale in today’s world of 24/7 operations, remote workforces, and real-time analytics. Enterprises need storage that performs, adapts, and protects.
Here’s why AI Enablement and Built-in Security Are Must-have Features on Modern Storage Environments:
AI powers efficiency, predictive maintenance, and workload optimization.
Built-in security reduces exposure to ransomware, data leaks, and unauthorized access.
Combined, they create a resilient infrastructure that drives digital transformation.
To know more visit us @ https://businessinfopro.com/
Unlocking the Power of AI in Storage Systems
AI is transforming how storage environments function. It allows infrastructure to "learn" from usage patterns and adjust configurations automatically—freeing up IT resources and improving performance.
Key benefits of AI in storage include:
Proactive Issue Resolution: Predicts disk failures and auto-initiates replacements before disruption occurs.
Real-Time Data Classification: Tags sensitive data and routes it through secure channels.
Usage Analytics: Identifies inefficiencies in storage allocation to reduce waste.
Self-Tuning Systems: Dynamically adjusts performance thresholds based on activity levels.
The result is smarter infrastructure where AI Enablement and Built-in Security Are Must-have Features on Modern Storage Environments for efficiency and uptime.
Read More @ https://businessinfopro.com/ai-enablement-and-built-in-security-are-must-have-features-on-modern-storage-environments/
Integrated Security: Not Just a Layer, But a Foundation
Security threats are evolving faster than traditional defenses can handle. That’s why built-in security is now essential in the design of modern storage systems.
Here’s what integrated security looks like:
Zero Trust Architecture: No one is trusted by default—every access request is verified.
Immutable Backups: Data snapshots that cannot be altered or deleted, ensuring ransomware resilience.
Encryption Everywhere: Secure data at rest, in transit, and during processing.
Access Control Policies: Enforce who sees what, when, and from where.
When AI Enablement and Built-in Security Are Must-have Features on Modern Storage Environments, companies gain a proactive, policy-driven defense system embedded at the data layer.
To know more visit us @ https://businessinfopro.com/
AI + Security = Intelligent Threat Response
AI isn’t only used to improve operational efficiency—it’s also crucial for bolstering storage security.
Here’s how AI enhances protection:
Anomaly Detection: Recognizes patterns in access behavior and flags suspicious activity.
Rapid Threat Containment: Automatically isolates infected files or users before malware spreads.
Predictive Alerts: Warns administrators before security vulnerabilities are exploited.
Compliance Automation: Maintains audit trails and generates regulatory reports with minimal manual effort.
By embedding AI into security layers, storage platforms become active guardians of enterprise data—another reason AI Enablement and Built-in Security Are Must-have Features on Modern Storage Environments.
Read More @ https://businessinfopro.com/ai-enablement-and-built-in-security-are-must-have-features-on-modern-storage-environments/
Use Cases of AI-Enabled Secure Storage
Organizations across industries are already reaping the benefits of AI-driven, secure storage:
Healthcare: AI speeds up image recognition while secure systems protect patient records.
Finance: Fraud detection tools require rapid, encrypted access to transactional data.
Retail: Personalized shopping experiences are powered by AI models trained on safely stored customer data.
Logistics: Smart inventory tracking systems rely on secure, real-time data feeds from distributed nodes.
These examples highlight why AI Enablement and Built-in Security Are Must-have Features on Modern Storage Environments across every vertical.
To know more visit us @ https://businessinfopro.com/
Choosing a Future-Ready Storage Solution
When evaluating a storage system, organizations should look beyond basic features like capacity and speed. In today’s landscape, the real value lies in intelligence and security.
Must-have capabilities include:
AI-driven diagnostics and optimization
Built-in threat detection and recovery
End-to-end encryption and MFA
Cloud-native compatibility and edge deployment
Real-time monitoring dashboards and analytics
By prioritizing platforms where AI Enablement and Built-in Security Are Must-have Features on Modern Storage Environments, businesses future-proof their operations.
Read More @ https://businessinfopro.com/ai-enablement-and-built-in-security-are-must-have-features-on-modern-storage-environments/
The Cost of Inaction
Without AI and built-in security, organizations face escalating risks:
Operational Downtime from hardware failures
Cyber Breaches leading to financial loss and reputational damage
Compliance Violations with hefty legal penalties
Resource Drain from manual monitoring and patching
Today, it’s not a matter of if an enterprise should modernize—it’s how fast. Because the longer companies wait, the higher the cost of recovery and competition.
Read Full Article : https://businessinfopro.com/ai-enablement-and-built-in-security-are-must-have-features-on-modern-storage-environments/
About Us: Businessinfopro is a trusted platform delivering insightful, up-to-date content on business innovation, digital transformation, and enterprise technology trends. We empower decision-makers, professionals, and industry leaders with expertly curated articles, strategic analyses, and real-world success stories across sectors. From marketing and operations to AI, cloud, and automation, our mission is to decode complexity and spotlight opportunities driving modern business growth. At Businessinfopro, we go beyond news—we provide perspective, helping businesses stay agile, informed, and competitive in a rapidly evolving digital landscape. Whether you're a startup or a Fortune 500 company, our insights are designed to fuel smarter strategies and meaningful outcomes.
0 notes
Text
AI in Cybersecurity: Enhancing Threat Detection and Response

The cybersecurity landscape is a relentless battleground, characterized by an ever-increasing volume of threats, the sheer sophistication of attacks, and a critical shortage of human talent. Traditional rule-based and signature-based security systems, while foundational, often struggle to keep pace with polymorphic malware, zero-day exploits, and the sheer volume of alerts generated daily. This is where Artificial Intelligence (AI) steps in, transforming the fight by dramatically enhancing our ability to detect threats and respond with unprecedented speed.
AI is not a magic bullet, but rather a powerful augmentation to human capabilities, acting as a force multiplier for security teams.
The Challenge: Overwhelmed Defenders
Consider the typical Security Operations Center (SOC) analyst. They face:
Alert Fatigue: Millions of alerts from various security tools, many of which are false positives, leading to analyst burnout and missed critical threats.
Sophisticated Attackers: Adversaries use AI and automation themselves, making attacks more stealthy, adaptive, and rapid.
Data Overload: The sheer volume of log data, network traffic, and threat intelligence is humanly impossible to process effectively.
Skill Gap: A global shortage of cybersecurity professionals means teams are often understaffed and overworked.
How AI Enhances Threat Detection
AI excels at processing massive datasets, recognizing complex patterns, and learning from experience – capabilities perfectly suited for modern threat detection.
Anomaly Detection:
Beyond Signatures: Instead of looking for known attack signatures, AI (especially unsupervised learning models) can establish a baseline of "normal" behavior for users, networks, and systems.
Spotting the Unusual: Any significant deviation from this baseline – an unusual login time, an unexpected file access, a sudden surge in network traffic – is flagged as an anomaly, potentially indicating a zero-day exploit or insider threat that traditional tools would miss.
Examples: User and Entity Behavior Analytics (UEBA) leveraging AI to detect compromised accounts or insider sabotage.
Advanced Malware Detection and Classification:
Deep Learning for Malware Analysis: AI models can analyze static (code structure, headers) and dynamic (runtime behavior) features of files at scale.
Polymorphic Malware: AI can identify characteristics of polymorphic malware (which changes its code to evade signature-based detection) by looking at its behavior or structural patterns rather than fixed signatures.
Automated Reverse Engineering: Generative AI can assist in disassembling and understanding malicious code, accelerating the threat intelligence process.
Intelligent Phishing and Spam Detection:
Contextual Analysis: AI goes beyond simple keyword matching, analyzing email headers, sender reputation, language patterns, sentiment, and even visual cues (like fake logos) to determine if an email is a phishing attempt.
Evolving Tactics: Machine learning models can adapt to new phishing campaigns and social engineering tricks much faster than manual updates.
Vulnerability Prioritization:
Risk-Based Approach: Instead of simply listing vulnerabilities, AI can analyze factors like exploit availability, potential impact, asset criticality, and attacker behavior to prioritize which vulnerabilities pose the highest immediate risk, guiding remediation efforts.
Threat Intelligence Augmentation:
Natural Language Processing (NLP): AI can process vast amounts of unstructured threat intelligence from blogs, research papers, dark web forums, and news feeds.
Pattern Identification: Identify emerging attack campaigns, threat actor groups, and TTPs (Tactics, Techniques, and Procedures) that might otherwise be buried in data.
Summarization: Generate concise summaries of complex threat reports for security analysts.
How AI Enhances Incident Response
Once a threat is detected, rapid and effective response is paramount to minimize damage. AI significantly streamlines this process.
Automated Incident Triage and Prioritization:
Contextualization: AI can correlate alerts from disparate security tools, creating a holistic view of an incident and reducing false positives.
Automated Routing: Automatically route incidents to the most appropriate security team or analyst based on severity and type.
Faster Root Cause Analysis:
Log Analysis: AI can rapidly sift through millions of log entries across different systems to pinpoint the initial point of compromise and the full scope of an attack.
Attack Path Mapping: Visualize the attacker's path through the network, helping security teams understand how an attack unfolded.
Automated Containment and Remediation:
SOAR Integration: AI can integrate with Security Orchestration, Automation, and Response (SOAR) platforms to trigger automated actions like isolating compromised endpoints, blocking malicious IPs, or rolling back configurations.
Pre-emptive Actions: Based on detected patterns, AI might suggest or even initiate pre-emptive actions to prevent further compromise.
Intelligent Playbook Generation:
Dynamic Response Plans: Generative AI can dynamically generate step-by-step incident response playbooks tailored to the specific characteristics of an ongoing attack, guiding human analysts.
Post-Incident Analysis and Reporting:
Automated Reporting: AI can compile detailed incident reports, summarizing timelines, affected systems, and remediation steps, freeing up analyst time.
Lessons Learned: Analyze past incidents to identify trends and suggest improvements for future security posture.
The Future: Human-AI Collaboration
AI is not here to replace human cybersecurity professionals, but to empower them. The most effective cybersecurity strategies in the future will be those that foster a collaborative environment where AI handles the heavy lifting of data analysis and automation, allowing human experts to focus on strategic decision-making, complex problem-solving, and the creative intelligence needed to outsmart human adversaries. Embracing AI in cybersecurity is no longer an option; it's a necessity for robust and resilient defenses in our hyper-connected world.
0 notes
Text

SHORT STORY:
Nyxien's cyberattack on Black Ridge University
Nyxien Xiyang executed an audacious senior prank in Black Ridge University before his induction into the enigmatic group known as the "Ordeus Repentium" and during his time as a Stella Botrus Stargrazer, a stunt that ultimately led to his classification as a dangerous cybercriminal. The prank was not merely a jovial mishap; Nyxien meticulously crafted a sophisticated virus, skillfully integrating characteristics of both a worm and trojan horse, transcending the boundaries of his academic coursework and delving into uncharted territories of programming.
For several weeks, he devoted countless hours to coding and refining this intricate project, utilising a virtual machine to test its functionality and resilience. The virus was designed with a deceptive allure; it presented users with a file ominously titled "my secrets <3." Intrigued users who clicked to unveil its contents were met with a singular—yet embarrassingly revealing—image of Nyxien himself, caught mid-expression in a moment of sheer absurdity. This was merely the beginning of the malicious journey that awaited them.
On clicking the image, users were greeted by an obnoxious message that read, "You're a fool. <3," before bearing witness to a cacophony of full-screen clips featuring sensitive (a type specifically made for adults) media—an ironic twist that compounded the surprise and embarrassment. Behind this façade, the worm stealthily operated under the cover of the trojan interface, operating with alarming efficiency to siphon funds from victims' bank accounts directly into Nyxien’s intergalactic account, all while eluding detection. When Nyxien unleashed this malware, it was six weeks before the close of the university year, a strategic timing that he calculated would maximise chaos. The ramifications were swift and sweeping—every device connected to the institution’s Wi-Fi network fell prey to his digital onslaught. In the aftermath, Nyxien amassed an astonishing fortune of over $5 billion from the exploit.
However, the law eventually caught up with him. Federal agents, through diligent investigation, tracked Nyxien down, but by this time, he had already woven himself into the fabric of the Ordeus Repentium. His newfound affiliations provided him a shield, rendering him untouchable and allowing him to evade arrest for the transgressions he had committed during that unforgettable prank.

0 notes
Text
AWS Transfer Family and GuardDuty Malware Protection for S3

S3 malware protection
Protecting against malware using AWS Transfer Family and GuardDuty
Businesses often must deliver online content safely. Public file transfer servers put the firm at risk from threat actors or unauthorised users submitting malware-infected files. Businesses can limit this risk by checking public-channel files for malware before processing.
AWS Transfer Family and Amazon GuardDuty may scan files transferred over a secure FTP (SFTP) server for malware as part of a transfer operation. GuardDuty automatically updates malware signatures every 15 minutes instead of scanning a container image, avoiding the need for human patching.
Prerequisites
What you need to implement the solution:
AWS account: This solution requires AWS access. If you don't have an AWS account, see Start developing today.
CLI: AWS Command Line Interface Install and link the AWS CLI to your account. Configure AWS account environment variables using your access token and secret access key.
The sample code will be fetched from GitHub using Git.
Terraform: Automation will use Terraform. Follow Terraform installation instructions to download and install.
Solution overview
This solution uses GuardDuty and Transfer Family. Smart threat detection service GuardDuty and secure file transfer service Transfer Family may be used to set up an SFTP server. AWS accounts, workloads, and data are protected by GuardDuty from odd and hazardous activity. The high-level solution uses these steps:
Transfer Family SFTP servers receive user file uploads.
Transfer Family workflows call AWS Lambda to conduct AWS Step Functions workflows.
Workflow begins after file upload.
Partial uploads to the SFTP server trigger an error handling Lambda function to report an error.
After a step function state machine runs a Lambda function to move uploaded files to an Amazon S3 bucket for processing, GuardDuty scans.
Step gets GuardDuty scan results as callbacks.
Clean or move infected files.
The process sends results using Amazon SNS. This might be an alert about a hazardous upload or problem that happened during the scan, or it could be a message about a successful upload and a clean scan that can be processed further.
Architecture and walkthrough of the solution
GuardDuty Malware Protection for S3 checks freshly uploaded S3 things. GuardDuty lets you monitor object prefixes or design a bucket-level malware defence approach.
This solution's procedure begins with file upload and continues through scanning and infection classification. From there, adjust the procedures for your use case.
Transfer Family uploads files using SFTP.
A successful upload starts the Managed Workflow Complete workflow and uploads the file to the Unscanned S3 bucket using Transfer Family. Successful uploads are managed by the Step Function Invoker Lambda function.
The Step Function The invoker starts the state machine and process by calling GuardDuty Scan Lambda.
GuardDuty Scan moves the file to Processing. The scanned files will come from this bucket.
GuardDuty automatically checks uploaded items. This implementation develops a Processing bucket malware prevention strategy.
After scanning, GuardDuty sends Amazon EventBridge the result.
A Lambda Callback function is invoked by an EventBridge rule after each scan. EventBridge calls the method with scan results. See Amazon EventBridge S3 item scan monitoring.
Lambda Callback alerts GuardDuty Scan using callback task integration. The Move File task receives GuardDuty scan results after returning to the Scan function.
If the scan finds no threats, the transport File operation will transport the file to the Clean S3 bucket for further processing.
Move File now posts to Success SNS to notify subscribers.
The Move File function will send the file to the Quarantine S3 bucket for extra analysis if the conclusion suggests that the file is dangerous. To warn the user to the upload of a potentially hazardous file, the function will further delete the file from the Processing bucket and publish a notification in the SNS’s Error topic.
Transfer Family will commence the Managed procedure Partial process if the file upload fails and is not entirely uploaded.
Controlled Workflow The Error Publisher function, which is used to report errors that emerge anywhere in the process, is called by the Partial error handling workflow.
The issue Publisher function detects the type of issue and adjusts the error status appropriately, depending on whether it is due to a partial upload or a problem elsewhere in the process. Then it will send an error message to the SNS Error Topic.
The GuardDuty Scan job has a timeout to broadcast an event to Error Topic if the file isn't scanned, requiring a manual intervention. If GuardDuty Scan fails, the Error clean up Lambda function is invoked.
Finally, the Processing bucket has an S3 Lifecycle policy. This ensures no file stays in the Processing bucket longer than a day.
Code base
The GitHub AWS-samples project implements this method using Terraform and Python-based Lambda functions.This solution may be built with AWS CloudFormation. The code includes everything needed to finish the procedure and demonstrate GuardDuty's malware protection plan and Transfer Family.
Install the fix
Applying this solution to testing.
Clone the repository to your working directory with Git.
Enter the root directory of the copied project.
Customise Terraform locals.tf's S3 bucket, SFTP server, and other variables.
Execute Terraform.
If everything seems good, run Terraform Apply and select Yes to construct resources.
Clear up
Preventing unnecessary costs requires cleaning up your resources after testing and examining the solution. Remove this solution's resources by running the following command in your cloned project's root directory:
This command deletes Terraform-created SFTP servers, S3 buckets, Lambda functions, and other resources. Answer “yes” to confirm deletion.
In conclusion
Follow the instructions in the post to analyse SFTP files uploaded to your S3 bucket for hazards and safe processing. The solution reduces exposure by securely scanning public uploads before sending them to other portions of your system.
#MalwareProtectionforS3#MalwareProtection#AWSTransferFamilyandGuardDuty#AWSTransferFamily#GuardDuty#SFTPserver#Technology#TechNews#technologynews#news#govindhtech
0 notes
Text
How to Train Your Team for Cybersecurity Incidents

In an era where cyber threats are constantly advancing, organizations must understand that experiencing a cybersecurity incident is not a question of if but when, necessitating a laser focus on preparedness. At the heart of this preparedness lies a well-trained team capable of recognizing, reporting, and responding to potential security breaches. This blog post will explore the best practices for incident response training, emphasizing the crucial role of regular training exercises and simulations in equipping employees to handle cybersecurity challenges effectively.
Understanding Cybersecurity Incident Response
A cybersecurity incident is any event that threatens the confidentiality, integrity, or availability of an organization's information systems. These incidents range from malware infections and phishing attempts to more complex attacks like ransomware or advanced persistent threats (APTs).
An effective incident response plan includes several key components.
Preparation.
Detection and Analysis.
Containment.
Eradication.
Recovery.
Post-Incident Review.
While having a robust technical infrastructure is crucial, the human element is equally vital in incident response. Employees are often the first line of defense against cyber threats, making their training and awareness paramount to an organization's security posture.
Build a Culture of Cybersecurity Awareness
Creating a security-conscious workforce starts at the top. Leadership must demonstrate a commitment to cybersecurity, integrating it into the company's core values and decision-making processes. This top-down approach helps foster a culture where employees understand their role in maintaining security for the organization.
Rather than viewing cybersecurity training as a one-time event or annual requirement, organizations should strive to make it an ongoing process. Regular updates, reminders, and discussions about security best practices help keep cybersecurity at the forefront of employees' minds, making it an integral part of their daily routines.
Essential Elements of Cybersecurity Training
Threat Recognition
Train employees to identify common types of cyber threats, including:
Phishing emails and websites.
Social engineering tactics.
Malware and ransomware.
Insider threats.
Training should cover the red flags associated with these threats, such as suspicious email attachments, unusual requests for sensitive information, or unexpected system behavior.
Incident Reporting Procedures
Clear, well-communicated protocols for reporting suspicious activities are crucial. Employees should know exactly who to contact and how to report potential security incidents. Emphasize the importance of timely reporting, as quick action can often mitigate the impact of a security breach.
Role-specific Training
While all employees need a foundational understanding of cybersecurity, tailor the training to different departments and responsibilities. For example:
IT staff may need advanced training in threat detection and response.
Finance teams should focus on recognizing financial fraud attempts.
HR personnel need to be vigilant about protecting sensitive employee data.
Password Management and Access Control
Proper password hygiene and access control are fundamental to cybersecurity. Train employees on:
Creating and maintaining strong, unique passwords.
The importance of multi-factor authentication.
Adequate handling of access credentials.
The risks associated with password sharing.
Data Handling and Privacy
Employees should understand their responsibilities in protecting sensitive information and complying with relevant regulations such as GDPR or HIPAA, including proper data classification, secure data storage and transmission practices, and data retention and destruction guidelines.
Effective Training Methods
To ensure engaging and effective cybersecurity training, implement a mix of the following methods:
Interactive Workshops
Hands-on exercises and real-world scenarios help employees apply their knowledge in practical situations. Group discussions can foster collaborative problem-solving and allow employees to learn from each other's experiences.
E-learning Modules
Self-paced online courses offer flexibility and can be easily updated to reflect the latest threats and best practices. Regular knowledge checks and quizzes reinforce learning and identify areas needing additional focus.
Simulated Phishing Campaigns
Conducting safe, controlled phishing tests can help employees recognize real-world threats. These campaigns provide valuable insights into your training programs' effectiveness and highlight areas for improvement.
Tabletop Exercises
Simulating various incident scenarios allows teams to practice response procedures in a low-pressure environment. These exercises can reveal gaps in your incident response plan and help refine your processes.
Gamification
Incorporating game-like elements into your training program can increase engagement and motivation. Consider implementing a points system, leaderboards, or rewards for completing training modules and demonstrating good security practices.
Conducting Effective Cybersecurity Simulations
Cybersecurity simulations are powerful tools for testing and improving your organization's incident response capabilities. When planning simulations:
Design realistic scenarios based on current threat intelligence and your organization's specific risks.
Involve all relevant departments, not just IT and security teams.
Set clear objectives and metrics for measuring performance.
Conduct thorough debriefings to identify lessons learned and areas for improvement.
Use simulation outcomes to refine your incident response plan and training programs.
Measuring Training Effectiveness
To ensure your cybersecurity training program is achieving its goals, consider the following key performance indicators:
Reduction in successful phishing attempts
Increase in reported security incidents
Improved response times during simulations
Higher scores on security awareness assessments
Regularly collect employee feedback on the training content and delivery methods, then use this information with performance metrics to continuously refine and improve your training program.
Staying Current with Evolving Threats
The cybersecurity landscape is constantly changing, with new threats emerging regularly. To keep your training program effective:
Update training materials frequently to reflect the latest threats and best practices.
Leverage threat intelligence to inform your training content and simulation scenarios.
Encourage continuous learning by providing resources for employees to stay informed about cybersecurity trends.
Consider offering advanced training or certification opportunities for employees with a particular aptitude or interest in cybersecurity.
Empowering Your Team with Cybersecurity Training
A well-trained, security-conscious workforce is your organization's best defense against cyber attacks in today’s evolving cyber threat landscape. By implementing comprehensive cybersecurity training programs and regular simulations, you can create a resilient team capable of recognizing, reporting, and responding to potential security incidents effectively.
Finding a trusted partner is crucial to ensuring your team gets the support they need. A company like Asylum Technologies is just that partner. They understand the critical role that employee training plays in maintaining a robust cybersecurity posture. Their expert team, led by a Microsoft Alumni with over 20 years of IT experience, offers cutting-edge cybersecurity and compliance solutions tailored to your organization's needs. They specialize in:
Implementing zero-trust methodologies to enhance your security posture
Ensuring compliance with industry standards and frameworks
Providing advanced identity and access management solutions
Accelerating cloud adoption with secure, scalable solutions
Offering staff augmentation to bolster your cybersecurity capabilities
By partnering with Asylum Technologies, you gain access to a wealth of expertise and practical experience in implementing effective cybersecurity measures. They design their solutions to be understandable, compliant, and secure, helping you confidently navigate the complex world of cybersecurity.
Don't wait for a security incident to highlight gaps in your company’s preparedness. Take proactive steps to enhance your organization's cybersecurity training and incident response capabilities and build a resilient, security-conscious workforce ready to face the challenges of today's digital landscape. Remember, in the world of cybersecurity, your employees are your most valuable asset. Invest in their knowledge and skills, and they will form an impenetrable human firewall, protecting your organization's digital assets and reputation.
0 notes
Text
Machine Learning and Cybersecurity: A Growing Alliance

In an era dominated by digital technologies, the exponential growth of cyber threats has pushed organizations to seek innovative solutions to secure their sensitive information. Traditional cybersecurity measures are no longer sufficient to combat the ever-evolving landscape of cyber attacks. This has led to the rise of machine learning as a powerful ally in the battle against cyber threats, complemented by the emergence of certifications such as the Blockchain Council Certification.
The Landscape of Cyber Threats
The Evolving Nature of Cyber Attacks
As technology advances, so do the tactics employed by cybercriminals. From simple malware attacks to sophisticated ransomware campaigns, the threat landscape has become more diverse and challenging to navigate. Understanding the dynamic nature of cyber threats is crucial in developing effective defense mechanisms, prompting the need for certified AI experts and AI developers in cybersecurity.
Limitations of Traditional Cybersecurity
Traditional cybersecurity approaches, such as signature-based detection and rule-based systems, have served as the backbone of defense mechanisms. However, their limitations have become increasingly apparent in the face of advanced and adaptive threats. The inability to detect zero-day attacks and the high rate of false positives highlight the need for a paradigm shift in cybersecurity strategies, emphasizing the importance of AI certifications for professionals.
The Role of Machine Learning in Cybersecurity
An Overview of Machine Learning
Machine learning (ML) is a subfield of artificial intelligence (AI) that focuses on the development of algorithms and models that enable computers to learn from data and make predictions or decisions without being explicitly programmed. In the realm of cybersecurity, AI in cybersecurity has become synonymous with ML algorithms, creating a demand for AI certification exams for professionals aiming to become AI experts in the field.
Types of Machine Learning in Cybersecurity
Supervised Learning:
Supervised learning involves training a model on a labeled dataset, where the algorithm learns to map input data to corresponding output labels. In cybersecurity, supervised learning is employed for tasks such as malware detection and classification, a domain where certified AI chatbot experts can contribute significantly.
Unsupervised Learning:
Unsupervised learning does not rely on labeled data; instead, the algorithm identifies patterns and relationships within the data on its own. This is particularly useful in anomaly detection, where deviations from normal behavior can indicate potential security threats, underscoring the need for AI prompt engineer certification.
Reinforcement Learning:
Reinforcement learning involves training a model to make sequences of decisions by rewarding or penalizing its actions. While not as commonly used in cybersecurity, reinforcement learning shows promise in adaptive and dynamic threat response, making it an area of interest for AI developer certification programs.
Applications of Machine Learning in Cybersecurity
Malware Detection:
ML algorithms excel in recognizing patterns associated with malware. By analyzing file behavior and characteristics, machine learning models can detect and classify malware, even when dealing with previously unseen variants. The integration of AI chatbots in incident response further enhances the capabilities of cybersecurity teams.
Anomaly Detection:
ML plays a crucial role in identifying anomalous behavior within network traffic or user activities. Deviations from established baselines can indicate potential security incidents, allowing for prompt intervention by certified AI professionals.
Phishing Detection:
Phishing remains a prevalent cyber threat, and machine learning models can analyze email content, sender behavior, and other features to identify phishing attempts with a high degree of accuracy, making AI certification essential for professionals in this domain.
Behavioral Analysis:
ML algorithms can learn the normal behavior of users and systems, enabling them to detect suspicious activities or deviations from established patterns. This proactive approach is essential in mitigating insider threats and emphasizes the need for AI certifications in behavioral analysis.
Challenges and Considerations in Implementing ML in Cybersecurity
Data Quality and Diversity
Data Quality:
The effectiveness of ML models heavily relies on the quality of training data. Inaccurate or biased data can lead to flawed models that may fail to generalize well to new and unseen threats, highlighting the importance of AI certifications in data management.
Data Diversity:
Cyber threats manifest in various forms, and ML models need diverse datasets to learn effectively. Lack of diversity may result in models that are too specialized and struggle with novel attack vectors, emphasizing the role of AI certification programs in promoting diverse skill sets.
Explainability and Interpretability
Black Box Models:
Many advanced ML models, such as deep neural networks, are often considered "black boxes" due to their complex architectures. Understanding and interpreting the decisions of these models is a challenge, raising concerns about accountability and trust in cybersecurity applications, emphasizing the need for transparent AI certifications.
Explainable AI (XAI):
Efforts are being made to develop explainable AI techniques that provide insights into how ML models arrive at specific decisions. This is crucial in the context of cybersecurity, where transparent decision-making is essential for trust and accountability, aligning with the principles of AI certification.
Adversarial Attacks
Manipulating ML Models:
Adversarial attacks involve manipulating input data to deceive ML models. In the context of cybersecurity, attackers may attempt to exploit vulnerabilities in ML algorithms to evade detection or cause false positives, highlighting the importance of continuous learning and artificial intelligence(AI) for adaptive defense mechanisms.
Robust ML Models:
Building robust ML models that can withstand adversarial attacks is a significant challenge. Researchers are exploring techniques such as adversarial training to enhance the resilience of cybersecurity-focused ML models, a critical aspect for AI developer certification programs.
Future Trends and Innovations
Integration with Threat Intelligence
Real-Time Threat Intelligence:
The integration of machine learning with real-time threat intelligence feeds enables security systems to adapt rapidly to emerging threats. ML models can leverage up-to-date information to enhance detection accuracy and response times, fostering a need for AI certification in threat intelligence integration.
Collaborative Threat Detection:
Collaboration between different organizations and their ML-powered cybersecurity systems can create a networked defense infrastructure. Sharing threat intelligence and collaborative analysis can significantly improve the collective ability to counter cyber threats, necessitating a collaborative approach in AI certification programs.
Quantum Computing and Cybersecurity
Quantum Threats:
As quantum computing evolves, new cryptographic challenges arise. Machine learning can play a role in developing quantum-resistant encryption algorithms to safeguard data against the potential threats posed by quantum computers, aligning with the advanced topics covered in AI expert certification programs.
Quantum Machine Learning:
Exploring the intersection of quantum computing and machine learning opens new avenues for enhancing cybersecurity. Quantum machine learning algorithms may provide unprecedented capabilities for analyzing complex datasets and improving threat detection, showcasing the need for specialized AI certifications in quantum machine learning.
Autonomous Cybersecurity Systems
Automated Threat Response:
Machine learning can contribute to the development of autonomous cybersecurity systems that not only detect threats but also respond to them in real-time. Automated threat response mechanisms can help organizations mitigate the impact of cyber attacks swiftly, emphasizing the role of AI certifications in developing and maintaining autonomous systems.
Human-Machine Collaboration:
The future of cybersecurity may involve a harmonious collaboration between human analysts and machine learning systems. Augmenting human decision-making with machine-generated insights can lead to more effective and adaptive cyber defenses, showcasing the need for interdisciplinary AI certifications that bridge the gap between human expertise and machine intelligence.
Conclusion
The alliance between machine learning and cybersecurity, underscored by the need for certified AI professionals, represents a pivotal shift in the way we defend against evolving cyber threats. As organizations continue to leverage the power of machine learning algorithms for detecting, analyzing, and responding to cyber attacks, it is essential to address the challenges associated with data quality, model explainability, and adversarial attacks.
Looking ahead, the integration of machine learning with threat intelligence, the impact of quantum computing, and the development of autonomous cybersecurity systems will shape the future of cybersecurity, necessitating ongoing education and certification initiatives such as those offered by the Blockchain Council Certification. By fostering innovation, collaboration, and continuous learning, we can build a robust defense infrastructure capable of safeguarding our digital world.
0 notes
Text
Malware Analysis: Unveiling the Secrets of Digital Threats
In the realm of cybersecurity, one of the key aspects that ethical hackers and security researchers delve into is the analysis of malware. Malware analysis is a vital practice that enables experts to unravel the inner workings of malicious software, understand its behavior, and develop effective strategies to counter its impact.
Let’s explore the key aspects that pave the way for a successful path in ethical hacking. So, buckle up and get ready for an adventure into the world of hacking from The Best Software Testing Training Institute.

Some Key Aspects And Techniques Involved In Malware Analysis:
Understanding Malware Analysis: Malware analysis is the process of dissecting and comprehending malicious software, such as viruses, worms, Trojans, and ransomware. It involves studying the functionality, origins, and potential implications of the malware. By analyzing malware, ethical hackers gain valuable insights into the techniques employed by attackers, aiding in the development of robust defense mechanisms.
Static Analysis: Static analysis is a preliminary technique that involves examining the malware without executing it. Analysts scrutinize the binary code, file headers, and strings to decipher the malware’s structure and potential IOCs. Static analysis provides a foundation for further investigation and helps in identifying key characteristics of malware.
Dynamic Analysis: Dynamic analysis involves executing the malware in a controlled environment to observe its behavior in real-time. By monitoring network traffic, system calls, file modifications, and other actions, analysts gain a deeper understanding of the malware’s capabilities. Dynamic analysis reveals the malware’s command and control communication, payload delivery mechanisms, and data exfiltration techniques.
Code Reverse Engineering: Malware often employs obfuscation techniques to evade detection. Code reverse engineering involves decompiling or disassembling the malware to unravel its logic, algorithms, and functionality. This technique unveils encryption methods, identifies vulnerabilities, and aids in developing effective countermeasures.
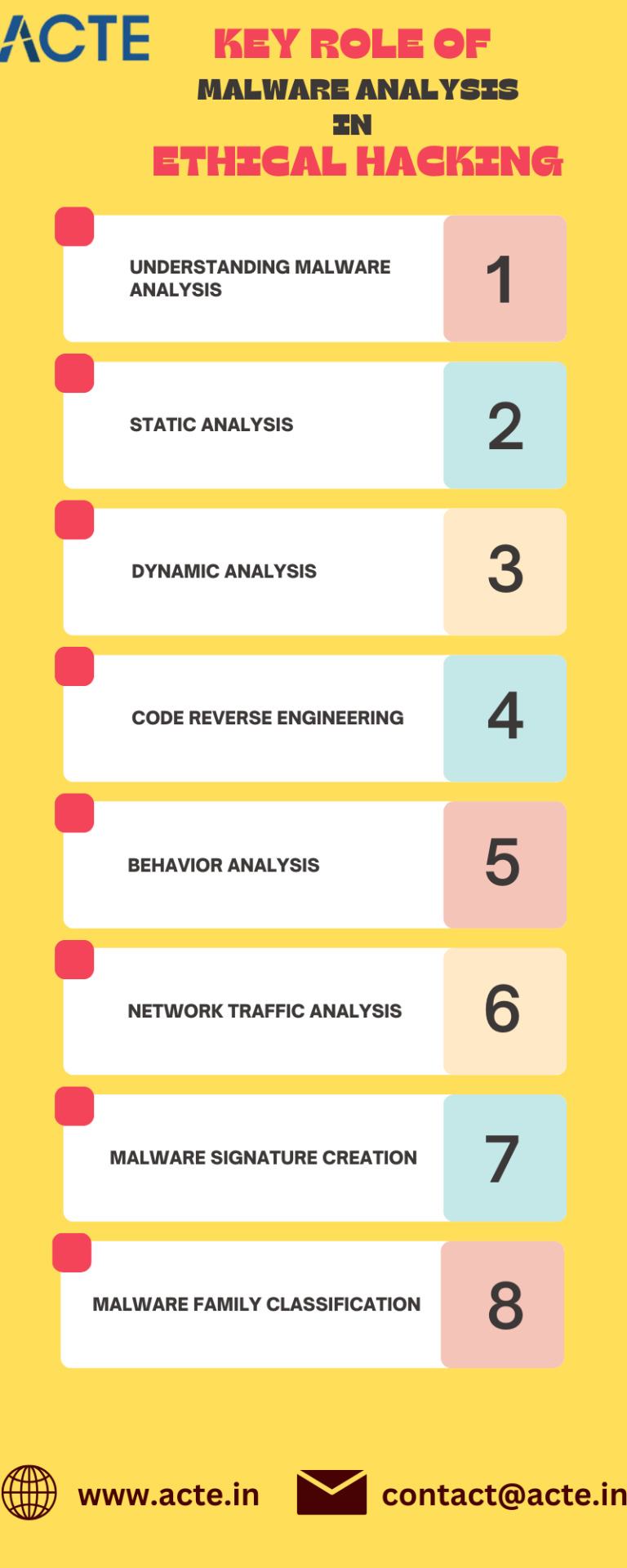
5. Behavior Analysis: Analyzing the behavior of malware during execution is crucial in understanding its objectives and potential impact on a system. By monitoring file system modifications, registry changes, and network communication, analysts can uncover the malware’s malicious actions. Behavior analysis helps in identifying evasion techniques and devising strategies to mitigate the impact of malware.
6. Network Traffic Analysis: Malware often relies on network communication to receive commands, exfiltrate data, or download additional payloads. Analyzing the network traffic generated by malware provides insights into its command and control infrastructure, communication protocols, and potential data leakage. Network traffic analysis aids in identifying communication patterns and strengthening network defenses.
8. Malware Signature Creation: Malware signatures are patterns or characteristics unique to specific malware variants. Analysts create these signatures based on their analysis findings, enabling antivirus software and security tools to detect and block known threats. By developing effective signatures, ethical hackers contribute to early detection and prevention of malware infections.
9. Malware Family Classification: Malware analysis involves categorizing and classifying malware into families or groups based on shared characteristics and behavior. This classification allows analysts to understand the broader context of the malware, identify its origins, and develop more effective detection and mitigation strategies.
Malware analysis is an indispensable component of ethical hacking and cybersecurity. By dissecting and understanding the inner workings of malicious software, analysts gain valuable insights into attackers’ techniques and motives.
Static and dynamic analysis, code reverse engineering, behavior analysis, network traffic analysis, and malware signature creation are among the key techniques employed in this field. By investing in malware analysis, ethical hackers play a crucial role in safeguarding digital systems and combating the ever-evolving landscape of cyber threats.
If you want to learn ethical hacking I will highly recommend the best ethical hacking course with certification .Every challenge is an opportunity to grow and contribute to the dynamic field of cybersecurity. Happy hacking!
0 notes
Text
The Role of Machine Learning in Big Data
Understanding Machine Learning and Big Data
Machine learning (ML) is a subset of artificial intelligence (AI) that helps software or apps be accurate in detecting and predicting results.
Its algorithms estimate new outcomes or output values based on historical data. It has diverse uses, including fraud detection, malware threat identification, recommendation engines, spam filtering, healthcare, and many more.
The term “big data” refers to enormous or dense data that is difficult to keep or that typical database systems cannot handle manually. Both organized and unorganized data makes this collection.
Difference between Machine Learning and Big Data
1. To anticipate data for the future based on applied data and prior experience, machine learning is used.
a. The term “big data” refers to enormous or dense data that is challenging to keep and that typical database systems cannot handle manually.
2. Supervised learning, unsupervised learning, semi-supervised learning, and reinforcement learning are the main types under which ML can be divided.
b. The three categories of big data include structured, unstructured, and semi-structured data.
3. ML uses a variety of algorithms to examine input datasets.
c. Big Data facilitates the analysis, storage, management, and organization of enormous amounts of unstructured data.
4.Through the use of various algorithms, computers or systems that use machine learning can learn from training data to forecast future outcomes.
d.Big data primarily focuses on collecting raw data and digging for trends that support smart decisions.
5. As ML only uses low-dimensional data, identifying features is relatively simpler.
e. Big data uses high-dimensional data, which makes it difficult to recognise the features.
6. Better customer service, product suggestions, virtual personal assistance, email spam filtering, automation, speech/text recognition, and other services can all benefit from machine learning.
f. Big Data is useful in a variety of fields, including stock market research, healthcare, agriculture, gaming, and environmental protection.
Uses of Machine Learning in Big Data
The Cloud Networks
A research company wishes to analyze a lot of medical data, but doing so on-site would be prohibitively expensive because it would require servers, internet storage, networking, and security equipment. Some types of machine learning models include text classification and GPU-accelerated image recognition. These algorithms can be disseminated and supported by a content delivery network (CDN) because they don’t learn after they are implemented.
Scraping the web
Consider how an electronic appliance maker would study market trends and customer satisfaction trends from a retailer’s quarterly report. The firm decides to web-scrape the vast amount of existing data related to online customer feedback and product reviews to learn what the reports might have missed. The manufacturer learns how to enhance and more effectively explain its items, which leads to higher sales, by gathering this data and feeding it to a deep-learning model. Despite the massive amount of data that web scraping produces, it is important to remember that selecting the sources for the data is the most crucial step in the procedure.
Exercising with Actual Data
Imagine you want to develop a machine-learning algorithm but don’t have the huge amount of data needed to train it. Maybe you read that derived computed data could be used in place of genuine data that you produced. But take care: An ideal algorithm needs a certain kind of data to learn from because it should address a particular problem. Using derived data nearly always results in the trained algorithm not performing to its full potential because it rarely closely resembles the real data the algorithm requires to solve the problem. The most secure approach is to experiment with actual data.
Being Clear About Your Goals
Don’t let the buzz about the combination of machine learning and big data lead you to have a false view of the issue you’re trying to address. You risk giving your algorithm the wrong data or using the right data incorrectly if you have identified a difficult problem but are unsure of how to use your data to solve it. Instead, spend the time needed to gather your data before digging into an algorithm to improve the power of big data. So that you may utilize (and train) an algorithm relevant to your problem when the time comes, you can become knowledgeable about your data.
Adaptive Tools
Due to these technologies, we have improved our ability to solve problems and offer the possibility of scaling entire businesses, as well as other tools (in the areas of finance, marketing, etc.).
Conclusion
Here, it is clear that the data has a significant role. Despite the numerous differences between the two, big data and machine learning can be used in collaboration to train machine learning models using high-quality data from vast amounts of both structured and unstructured data. Also, they have several applications of big data and machine learning that bring about remarkable outcomes.
1 note
·
View note
Text
Protect Your Business with AI Cybersecurity | FloatChat

Introduction
In today's increasingly digitized world, cyber threats loom larger than ever. As organizations become more reliant on interconnected systems and data flows, they also become more vulnerable to attacks. Recent years have seen a surge in hacking, malware, ransomware, and other cybercrimes that result in massive financial and reputational damages.
To defend against these rapidly advancing threats, traditional cybersecurity approaches are no longer sufficient. This is where revolutionary AI technologies come in - to provide next-generation protection powered by intelligence, adaptability and precision.
The Growing Menace of Cybercrime
Some key statistics highlight the severity of the cyber threat landscape:
Cybercrime is expected to inflict damages totaling $10.5 trillion annually by 2025.
A business falls victim to a ransomware attack every 14 seconds.
The average cost of a data breach now exceeds $4 million.
Phishing attacks increased by 15% in 2020 amid the remote work shift caused by the pandemic.
Hackers and cybercriminals are using increasingly sophisticated tools and tactics such as social engineering, malware infections, supply chain compromises, vulnerabilities in legacy systems, and inadequate employee training. As a result, the global cybersecurity skills shortage has reached over 3 million unfilled positions.
Why AI is a Game-Changer for Cybersecurity
Artificial intelligence refers to a range of technologies like machine learning and deep learning that enable computer systems to mimic human cognitive abilities. AI allows software to continuously learn from data to improve at specific tasks like pattern recognition, classifications, predictions, and decision making.
In cybersecurity, AI augments human analysts and security tools with the ability to:
Analyze enormous volumes of data at machine speed to detect anomalies and uncover subtle indicators of compromise. This enables real-time threat identification.
Identify zero-day threats and new attack patterns instead of just reacting to known threats. This allows organizations to keep pace with rapidly shifting attacker tactics.
Automate mundane and repetitive tasks to enable human analysts to focus on higher value investigations and response. AI is a force multiplier for security teams.
Provide explainable threat alerts instead of just signaling that something is wrong. This context helps analysts investigate and respond to alerts more efficiently.
Adapt cyber defenses dynamically as the threat landscape evolves. Self-learning algorithms ensure AI security maintains the edge over attackers.
In essence, AI allows cybersecurity to scale effectively and provides integrated intelligence that augments human capabilities.
Key Applications of AI for Cybersecurity
Some major areas where AI is revolutionizing cybersecurity include:
Malware Identification
Traditional signature-based antivirus solutions struggle to detect new strains of malware. AI algorithms overcome this by analyzing large volumes of data — metadata, binaries, behavior patterns — to accurately identify malware and prevent infections.
Insider Threat Detection
By profiling normal behavior patterns for users and assets, AI can detect anomalous actions indicative of insider risks. User behavior analytics serves as an extra security layer.
Network Security and Threat Hunting
AI algorithms perform real-time monitoring of network traffic to identify suspicious patterns like data exfiltration or command-and-control actions by bad actors. This enables early threat detection and rapid response.
Fraud Prevention
AI analyzes large amounts of customer data and activity to create robust profiles. Deviations from normal profiles are analyzed as potential fraud in real-time before damages occur.
Incident Response
AI automation assists overburdened security teams by aggregating alerts, aiding investigations, and enacting responses to confirmed threats. This reduces dwell time.
The AI Cybersecurity Platform Built by Floatchat
Floatchat is a cybersecurity vendor leveraging bleeding-edge AI research to deliver next-generation solutions. Founded by industry veterans and former NSA cyber experts in 2019, Floatchat has quickly grown to become a leader in AI-powered cybersecurity.
Floatchat’s platform integrates advanced AI that performs real-time data analysis to detect risks across an organization’s entire digital footprint - endpoints, networks, cloud, IoT devices, and users. Key capabilities include:
Robust Data Collection: Extracts and aggregates security data from diverse sources across IT infrastructure. This provides comprehensive visibility.
Continuous Behavior Modeling: Develops dynamic models customized to organization’s environments and risk profile. Flags deviations as threats.
Explainable AI: Provides contextual threat alerts with insights into reasons for raised alerts. Boosts productivity.
Dynamic Adaptability: Automatically adapts to changing attacker tactics, tech stacks, and business workflows to maintain edge.
Holistic Protection: Unified platform that secures networks, endpoints, cloud, identities, and critical data assets via AI.
Managed Services: Floatchat experts provide continuous monitoring, management and support services backed by AI/ML.
Securing Healthcare Networks with AI
The healthcare industry is highly susceptible to cyberattacks given the sensitive personal data involved. Floatchat's AI solutions are playing a key role in securing hospital networks.
For a healthcare provider in Florida, Floatchat detected early signs of a network compromise by analyzing communications patterns between medical devices and hospital servers. The threat was contained before any data could be stolen.
In another case, Floatchat AI pinpointed unauthorized data transfers initiated from the CFO's laptop indicative of insider threat. Further investigation revealed that the laptop was breached, averting a major financial fraud attempt.
The Road Ahead for Cybersecurity AI
While AI cybersecurity is already mature, there are several emerging trends and technologies poised to expand its capabilities:
Use of cybersecurity-specific AI chips like graph processors for accelerating threat detection.
Adoption of digital twin technology to model entire ecosystems and identify risks through simulation.
Predictive analytics by analyzing patterns over time to forecast the most likely emerging threats.
Improved natural language capabilities for extracting insights from security analyst notes and reports.
Conclusion
As cyber risks accelerate, AI delivers new hope for gaining an upper hand over attackers. AI provides the sophisticated detection, speed, adaptability and multifaceted protections needed against today's elusive threats. Organizations must embrace AI-powered cybersecurity platforms such as Floatchat to future-proof their defenses.
#AIForCybersecurity#CybersecurityAI#AIProtection#CyberDefense#AIinSecurity#DigitalSecurity#CyberSafety#ThreatDetection#AIResilience#SecureWithAI#TechSecurity#CyberThreats#AIforPrivacy#DataProtection#AIandCyber#CyberGuardians#AIInnovations#SecureTech#AIinProtection#CyberAwareness
0 notes
Text
The Art of Link Detection and Tracking: A Comprehensive Guide
In today's digital age, the world is interconnected by a vast web of information. The internet, with its seemingly endless array of websites, social media platforms, and online resources, has become an integral part of our daily lives. However, this interconnectedness also brings about new challenges, especially when it comes to digital forensics services. In this comprehensive guide, we will delve into the intricate art of link detection and tracking, exploring its significance in the realm of digital forensics.
Understanding the Digital Landscape
Before we embark on the journey of link detection and tracking, it's crucial to comprehend the complex digital landscape we navigate every day. Our lives are intertwined with the internet, whether we're conducting business, communicating with friends and family, or seeking information. Each click, each interaction leaves a digital footprint.
This digital footprint is a treasure trove for digital forensics experts. It can provide critical insights into cybercrimes, security breaches, and even personal matters like online harassment. In the context of digital forensics services, link detection and tracking play a pivotal role in unraveling the mysteries hidden within this vast digital world.
The Significance of Link Detection
Link detection is the process of identifying and cataloging the various web links associated with a particular digital asset. These assets can include emails, websites, social media profiles, or even files stored in the cloud. For digital forensics services, link detection serves several vital purposes:
Evidence Gathering: Links can be a gateway to critical evidence in a digital investigation. By identifying and cataloging links, digital forensics experts can trace the digital trail left by suspects, potential witnesses, or victims.
Malware Analysis: In cases involving malware or cyberattacks, analyzing links can reveal the source of the attack and its propagation methods. This is crucial for understanding the extent of the breach and developing strategies to mitigate it.
Contextual Understanding: Links can provide context to digital communications and interactions. This context is invaluable in understanding the motives and intentions behind various online activities.
Chain of Custody: Establishing a chain of custody for digital evidence is vital in legal proceedings. Properly tracking links ensures the integrity and admissibility of evidence in court.
The Art of Link Detection
Link detection is not a straightforward task; it requires a combination of technical skills, software tools, and investigative intuition. Here are the key steps involved in the art of link detection:
Data Collection: The first step is to gather all relevant data, which may include emails, social media profiles, website logs, and files. This is a critical phase as missing data can lead to incomplete link tracking.
Parsing and Extraction: Digital forensics software tools are used to parse and extract links from the collected data. These tools can identify links within text, attachments, and metadata.
Classification: Links are classified based on their origin, type, and relevance to the investigation. This step helps prioritize which links to investigate further.
Follow the Trail: Following links often involves traversing through a maze of websites, servers, and redirects. Digital forensics experts need to employ techniques such as URL analysis, IP tracking, and DNS resolution to trace the path of a link.
Metadata Analysis: Link metadata, such as timestamps and user agents, can provide crucial insights. Experts analyze this data to establish timelines and identify the parties involved.
Cross-Referencing: Links are rarely isolated entities. They are part of a larger network of digital interactions. Cross-referencing links with other digital artifacts, such as chat logs or email exchanges, can uncover hidden connections.
Documentation: Every step of the link detection process must be meticulously documented. This documentation is essential for maintaining the integrity of the evidence and for presenting findings in court if necessary.
The Role of Link Tracking
While link detection helps identify and catalog links, link tracking takes it a step further by monitoring the activities associated with those links. Link tracking is particularly valuable in ongoing investigations and cybersecurity efforts. Here's why it matters:
Real-time Monitoring: In cases involving cyber threats or ongoing criminal activities, link tracking provides real-time insights into the actions of suspects or malicious actors.
Attribution: Link tracking can help attribute specific actions to individuals or entities, aiding in the identification and apprehension of culprits.
Preventative Measures: By tracking links, organizations and individuals can proactively identify and mitigate potential threats before they escalate.
Enhanced Security: In the world of cybersecurity, link tracking is a critical component of threat intelligence, helping security teams stay one step ahead of evolving threats.
Digital Forensics Services and Link Detection
Digital forensics services are at the forefront of investigations involving cybercrimes, corporate espionage, and even personal disputes. The art of link detection and tracking is an indispensable tool in the toolkit of digital forensics experts.
By employing advanced techniques and software tools, experts in digital forensics services can navigate the intricate web of digital interactions, uncover hidden evidence, and provide crucial support to law enforcement, legal proceedings, and cybersecurity efforts.
conclusion
The digital age has ushered in a new era of interconnectedness and information exchange. With this increased connectivity comes the need for robust digital forensics services. The art of link detection and tracking is an essential skill in this domain, allowing experts to unravel the complexities of the digital landscape, gather critical evidence, and ensure the integrity of digital investigations. As we continue to navigate the digital realm, the significance of link detection and tracking in safeguarding our digital lives cannot be overstated.
So here IBRANDtech is the best cyber security service providing agency that offers forensic chargesheet preparation, Forensic Cyber Audit, forensic cyber trail, Forensic Data Recovery and Cloning, Link detection and tracking, Spoofing email trail and Server trial, Suspect detailed profiling, Suspect Tracking and Location Detection services in all over the India. Our dedicated team of experts is committed to delivering the finest cybersecurity services tailored to your needs. We take pride in the opportunity to assist you in achieving top-notch cybersecurity solutions.
0 notes
Text
How to Build AI-Powered Cybersecurity Applications

The cybersecurity landscape is a relentless battleground, demanding innovative solutions to combat ever-evolving threats. Artificial Intelligence (AI), particularly machine learning and increasingly generative AI, offers a powerful arsenal for defenders. Building AI-powered cybersecurity applications can significantly enhance threat detection, automate responses, and provide deeper insights into complex security challenges.
But how do you go from concept to a functional, effective AI-driven security tool? This guide outlines the key steps and considerations for building AI-powered cybersecurity applications.
1. Define the Problem and Use Case
Before writing a single line of code, clearly define the specific cybersecurity problem you aim to solve with AI. AI is not a magic bullet; it's a tool that excels at certain tasks.
Examples of AI use cases in cybersecurity:
Anomaly Detection: Identifying unusual network traffic patterns, user behaviors, or system activities that might indicate a breach.
Malware Detection and Classification: Analyzing code or file behavior to identify and categorize malicious software.
Phishing Detection: Identifying deceptive emails or websites.
Vulnerability Management: Prioritizing vulnerabilities based on exploitability and impact.
Threat Intelligence Processing: Automating the analysis and summarization of vast amounts of threat data.
Automated Incident Response: Developing AI-driven playbooks for rapid threat containment.
Clearly defining your use case will guide your data collection, model selection, and overall architecture.
2. Data Collection and Preparation
AI models are only as good as the data they are trained on. This is arguably the most critical and time-consuming step.
Identify Data Sources: This could include network logs (firewall, IDS/IPS), endpoint logs (EDR), security information and event management (SIEM) data, threat intelligence feeds, malware samples, user behavior logs, and vulnerability scan results.
Data Volume and Variety: Ensure you have sufficient data volume and variety to train a robust model. Cybersecurity data is often imbalanced (e.g., far more normal events than malicious ones), which needs to be addressed.
Data Cleaning and Preprocessing: Raw security data is messy. You'll need to:
Handle Missing Values: Decide how to deal with incomplete data.
Normalize Data: Scale numerical data to a standard range.
Feature Engineering: Extract meaningful features from raw data that the AI model can learn from (e.g., frequency of connections, packet sizes, API call sequences, email headers). This often requires deep domain expertise.
Labeling: For supervised learning, you'll need accurately labeled data (e.g., "malicious" vs. "benign," "phishing" vs. "legitimate"). This can be a significant challenge in cybersecurity.
3. Model Selection and Training
Choosing the right AI model depends on your problem, data type, and desired outcome.
Machine Learning Algorithms:
Supervised Learning: For classification (e.g., phishing/not phishing) or regression (e.g., predicting risk scores) when you have labeled data. Algorithms include Support Vector Machines (SVMs), Random Forests, Gradient Boosting Machines (XGBoost, LightGBM), and Neural Networks.
Unsupervised Learning: For anomaly detection or clustering when you don't have labeled data (e.g., K-Means, Isolation Forest, Autoencoders).
Deep Learning: For complex pattern recognition in large, unstructured data (e.g., image recognition for malware analysis, natural language processing for threat intelligence).
Generative AI (LLMs): For tasks involving natural language, code generation, summarization, or creating realistic simulations (e.g., generating phishing emails, incident reports, or security awareness content).
Model Training: Train your chosen model using your prepared dataset. This involves splitting data into training, validation, and test sets, and iteratively adjusting model parameters.
4. Evaluation and Refinement
A model's performance is crucial. Don't just look at accuracy; consider metrics relevant to cybersecurity.
Metrics:
Precision and Recall: Especially important for anomaly detection, where false positives (alert fatigue) and false negatives (missed threats) have significant consequences.
F1-Score: A balance between precision and recall.
ROC AUC: For evaluating binary classifiers.
Bias Detection: Ensure your model isn't biased against certain data patterns, which could lead to missed threats or unfair assessments.
Adversarial Robustness: Test how your model performs against deliberately crafted adversarial examples designed to fool it. Attackers will try to bypass your AI.
Iterative Refinement: Based on evaluation, refine your features, adjust model parameters, or even try different algorithms. This is an ongoing process.
5. Deployment and Integration
Once your model is performing well, you need to deploy it into your cybersecurity ecosystem.
Scalability: Ensure your application can handle the volume of data and requests in a real-world environment.
Real-time Processing: Many cybersecurity applications require real-time or near real-time analysis.
Integration with Existing Tools: Integrate your AI application with your SIEM, EDR, SOAR (Security Orchestration, Automation, and Response) platforms, and other security tools to enable seamless data flow and automated actions.
Monitoring and Maintenance: Continuously monitor your AI application's performance in production. Models can drift over time as threat landscapes change, requiring retraining or recalibration.
6. Human-in-the-Loop and Ethical Considerations
AI in cybersecurity should augment, not replace, human expertise.
Human Oversight: Always keep a human in the loop for critical decisions. AI can flag anomalies, but human analysts provide context and make final judgments.
Explainability (XAI): Strive for explainable AI models where possible, allowing analysts to understand why a model made a particular prediction or flagged an event. This builds trust and aids in incident investigation.
Ethical AI: Address potential biases, ensure data privacy, and consider the ethical implications of using AI in sensitive security contexts.
Building AI-powered cybersecurity applications is a complex but incredibly rewarding endeavor. By following these steps, focusing on data quality, rigorous evaluation, and a collaborative human-AI approach, you can develop powerful tools that significantly bolster your organization's defenses in the face of escalating cyber threats.
0 notes
Text
𝗦𝗶𝗴𝗻𝗮𝘁𝘂𝗿𝗲 𝗟𝗲𝘀𝘀 𝗗𝗲𝘁𝗲𝗰𝘁𝗶𝗼𝗻 𝗧𝗲𝗰𝗵𝗻𝗼𝗹𝗼𝗴𝘆 𝗠𝗮𝗿𝗸𝗲𝘁 | #industryarc
𝗗𝗼𝘄𝗻𝗹𝗼𝗮𝗱 𝗿𝗲𝗽𝗼𝗿𝘁 𝘀𝗮𝗺𝗽𝗹𝗲 @ https://lnkd.in/gtXhWsTd 𝗞𝗲𝘆 𝗧𝗮𝗸𝗲𝗮𝘄𝗮𝘆𝘀 : ◾ #Machinelearning system is supposed to evolve to the maximum possible level. Precise description of the desired solution (using PCA) is appropriate. The key explanation for improved classification is that the former is focused on bagging and boosting. ◾ In the #signature-less #identification industry, #northamerica is projected to achieve the largest market share. High gaps to defense are fuelling market demand. The emergence of the #ecommerce industry fuels company development in North America. ◾ Signature-based detection issues remain, as revised and fresh risks can’t be predicted or observed. Businesses also have to continuously update existing signatures and invest #money in the long term. ◾ #EDR programs provide full visibility into endpoints, use machine learning techniques and Large #Data predictive insights to ensure signature-less recognition. Signature-less identification prevents APTs, #malware, #spam, #viruses and phishing #mails, as well as testing back #inputs. 𝗔𝗰𝗰𝗲𝘀𝘀 𝗳𝘂𝗹𝗹 𝗿𝗲𝗽𝗼𝗿𝘁 @ https://lnkd.in/gYZuhiBA 𝗠𝗮𝗷𝗼𝗿 𝗸𝗲𝘆𝗽𝗹𝗮𝘆𝗲𝗿𝘀 : Quick Heal | CloudBrick | Cisco | McAfee | Trend Micro | Palo Alto Networks | AT&T | Darktrace | FireEye, Inc. | Qualys | Fortinet | Securiti | ImmuniWeb | Darktrace | COFENSE | Nuance Communications | F5 | Kenna Security #security #testing #communications #cisco #fortinet #qualys #paloaltonetworks #technology
#𝗦𝗶𝗴𝗻𝗮𝘁𝘂𝗿𝗲 𝗟𝗲𝘀𝘀 𝗗𝗲𝘁𝗲𝗰𝘁𝗶𝗼𝗻 𝗧𝗲𝗰𝗵𝗻𝗼𝗹𝗼𝗴𝘆 𝗠𝗮𝗿𝗸𝗲𝘁#𝗦𝗶𝗴𝗻𝗮𝘁𝘂𝗿𝗲 𝗟𝗲𝘀𝘀 𝗗𝗲𝘁𝗲𝗰𝘁𝗶𝗼𝗻 𝗧𝗲𝗰𝗵𝗻𝗼𝗹𝗼𝗴𝘆 𝗠𝗮𝗿𝗸𝗲𝘁 share#𝗦𝗶𝗴𝗻𝗮𝘁𝘂𝗿𝗲 𝗟𝗲𝘀𝘀 𝗗𝗲𝘁𝗲𝗰𝘁𝗶𝗼𝗻 𝗧𝗲𝗰𝗵𝗻𝗼𝗹𝗼𝗴𝘆 𝗠𝗮𝗿𝗸𝗲𝘁 size
0 notes
Text
Cybersecurity Challenges in the Era of Remote Work and BYOD

The rapid shift to remote work and the widespread use of Bring Your Own Device (BYOD) policies have introduced new cybersecurity challenges for organizations. The expanded attack surface, increased reliance on personal devices, and remote network access create vulnerabilities that cybercriminals can exploit. Understanding and addressing these challenges is crucial for maintaining a secure remote work environment. Let’s explore some of the key cybersecurity challenges in the era of remote work and BYOD.
1. Endpoint Security: With remote work and BYOD, employees connect to corporate networks using various devices, including personal laptops, smartphones, and tablets. Ensuring the security of these endpoints becomes critical. Organizations must implement strong endpoint protection measures such as antivirus software, firewalls, and encryption to mitigate the risk of malware infections and unauthorized access.
2. Secure Remote Access: Remote work necessitates secure remote access to corporate resources. VPNs, multi-factor authentication (MFA), and secure remote desktop protocols are essential for encrypting connections and verifying user identities. Organizations should enforce strict access controls and monitor remote access activities to detect any suspicious behavior or unauthorized access attempts.
3. Data Protection and Privacy: The remote work environment increases the risk of data breaches and privacy violations. Sensitive data may be stored and transmitted outside the corporate network, making it more susceptible to unauthorized access. Implementing data protection measures such as encryption, data loss prevention (DLP), and data classification policies is crucial to safeguard sensitive information.
4. Phishing and Social Engineering: Cybercriminals exploit the vulnerabilities of remote workers through phishing attacks and social engineering tactics. Employees working outside the corporate network may be more susceptible to malicious emails, fake websites, and social engineering scams. Regular employee training and awareness programs can help mitigate these risks by educating employees about common attack vectors and best practices for identifying and reporting suspicious activities.
5. Home Network Security: Home networks may lack the robust security measures implemented in corporate environments. Weak passwords, unpatched routers, and outdated firmware can create vulnerabilities that cybercriminals can exploit. Educating employees about home network security best practices and providing guidelines for securing their home networks can help mitigate these risks.
6. Data Backup and Recovery: With remote work, the risk of data loss due to device theft, hardware failure, or human error increases. Regular data backups, both locally and in the cloud, are essential to prevent data loss and enable quick recovery in case of incidents. Organizations should establish clear data backup policies and ensure employees adhere to them.
7. Shadow IT: The use of unauthorized applications and services (Shadow IT) can introduce security risks. Employees may adopt unsanctioned cloud services or collaboration tools without proper security controls. Organizations should provide secure alternatives and educate employees about the risks associated with using unauthorized applications.
8. Compliance and Regulatory Considerations: Remote work may introduce compliance challenges, particularly with data protection and privacy regulations. Organizations must ensure that remote work practices align with regulatory requirements, including data handling, storage, and cross-border data transfer. Regular audits and assessments can help identify compliance gaps and ensure adherence to relevant regulations.
Addressing the cybersecurity challenges in the era of remote work and BYOD requires a multi-layered approach. Organizations should implement robust security measures, provide ongoing cybersecurity awareness training, enforce policies and best practices, and regularly assess the effectiveness of their security controls. By prioritizing cybersecurity and staying vigilant, organizations can maintain a secure remote work environment and protect sensitive data from evolving threats.
If you need assistance in implementing secure remote work solutions, strengthening your cybersecurity posture, or have any other technology-related questions, visit us at www.infradapt.com or call us at 484-546-2000. Our team of experts can provide guidance, support, and tailored solutions to address your specific cybersecurity challenges.
https://www.infradapt.com/news/cybersecurity-challenges-remote-work-and-byod/
0 notes
Text
Sunday Round Up - 25th of August 2019
amzn_assoc_ad_type = "banner"; amzn_assoc_marketplace = "amazon"; amzn_assoc_region = "US"; amzn_assoc_placement = "assoc_banner_placement_default"; amzn_assoc_campaigns = "amzn_vicc_cloudcam_1017"; amzn_assoc_banner_type = "category"; amzn_assoc_isresponsive = "true"; amzn_assoc_banner_id = "1J0CHGJT75D586M66602"; amzn_assoc_tracking_id = "kraljevicn1-20"; amzn_assoc_linkid = "c122cc4768b349b4aab7d3099b74ea1c";
Sunday Round up for this week!
Articles:
Im publishing an infosec book
Open Finance First, Open Data Second – AVC
Dr.Semu - Malware Detection and Classification Tool Based on Dynamic Behavior
Using WebThings Gateway notifications as a warning system for your home – Mozilla Hacks : the Web developer blog
Analysis of King Ouroboros Ransomware
If you found some other interesting stuff this week feel free to leave a link to it in the comments section. Otherwise feel free to check out the last roundup here.
These round ups are brought to you by PassVult.
#PassVult#publishing a book#infosec book#random fiber router#Open Finance#Open data#Dr.Semu#malware detection and classification#dynamic behaviour#webthings#notifications#for your home#mozilla hacks#king ouroboros#ransomware#analysis
2 notes
·
View notes
Photo

Leveraging Electromagnetic Signals for Obfuscated Malware Classification
The Internet of Things (IoT) is constituted of devices that are exponentially growing in number and in complexity. They use numerous customized firmware and hardware, without taking into consideration security issues, which make them a target for cybercriminals, especially malware authors.
We will present a novel approach of using side channel information to identify the kinds of threats that are targeting the device. Using our approach, a malware analyst is able to obtain precise knowledge about malware type and identity, even in the presence of obfuscation techniques which may prevent static or symbolic binary analysis. We recorded 100,000 measurement traces from an IoT device infected by various in-the-wild malware samples and realistic benign activity. Our method does not require any modification on the target device. Thus, it can be deployed independently from the resources available without any overhead. Moreover, our approach has the advantage that it can hardly be detected and evaded by the malware authors. In our experiments, we were able to predict three generic malware types (and one benign class) with an accuracy of 99.82%. Even more, our results show that we are able to classify altered malware samples with unseen obfuscation techniques during the training phase, and to determine what kind of obfuscations were applied to the binary, which makes our approach particularly useful for malware analysts.
3 notes
·
View notes