#need of encryption and decryption in cryptography
Explore tagged Tumblr posts
Text
Safeguarding Success: The Crucial Role of Data Protection in E-Commerce Business
#Safeguarding Success: The Crucial Role of Data Protection in E-Commerce Business#starting your business on the right side of the law#what is the use of firewall in a computer#computers privacy & data protection#business#e-commerce#need of encryption and decryption in cryptography#small business credit card processing#starting a business legally#data protection and artificial intelligence#ecommerce success#business communication#the power of personalization: unlocking e-commerce success (free planning kit)
1 note
·
View note
Text
Scientific lore analysis that proves that Bill Cipher is destined to be a bottom.

More under the cut.
Let's start with who Bill Cipher is. He's a two-dimensional interdimensional dream demon from the now destroyed dimension, Euclydia. Formerly existent only in the Mindscape, Bill briefly succeeded in gaining access to the real world and a physical form. Known for his mysterious demeanor and sadistic humor, Bill is the main antagonist of the overall series. (wiki) However, let's stick with the fact that he's a big liar, too. A code in Theraprism cipher on the book's cover says it directly: even his lies are lies.

So, when overlooking his design with prevailing yellow, which symbolises deceit, power and manipulation, we might also invert it (because his appearance may also "lie" to us). And we will see that it's mainly blue.

Why blue? I think it's intentional move done by Alex Hirsch to prove his point that Bill Cipher is not what he seems. This symblolizes a deeper connection with character design and his personality.

In literature, blue is known as a color of honesty, peace, sadness and commitment. Like this, he is honest to us, open and commited. However, let's focus on the sadness part.
Sadness is a feeling that can develop into depression, if you are stuck with it for a long time (over 2 weeks, for example). And depression IS when you are at the BOTTOM of your life. And yeah, what color will that be? Blue. And blue is the exact opposite of the color that Bill wants to be shown!
He is yellow, because he wants to act all-powerful, pretending to be in charge. However, people who really are in charge don't need to prove it constantly. The way Bill acts shows that deep inside, he overcompensates the need for someone to take him down, he's the jester-like character, waiting to be humilated the right way.
Power is nothing but an act of roleplay to him, he wants for someone to make this illusion go away. His fear of vulnerability is really giving out.
Bill Cipher, what a cool name, right? But why is he called that?
His name is believed to be a combination of "bill" for dollar one and "cipher" for cryptogram stuff. But is it that easy? Let's dive deeper
His "Bill" part is based on the Eye of Providence, which is most commonly seen on the back of the american dollar.

It's a 1-dollar bill, the lowest of the banknotes available. It's the BOTTOM of the quantity value. No matter the dollar price, it will stay there. Maybe that’s where it’s supposed to be.
Moreover, Bill is a common used name among the people. It is a dull, boring, meaning nothing one. It giving "overcompensating suburban villain" ifykyk.
Cipher? What is a cipher?

In cryptography, a cipher is an algorithm for performing encryption or decryption. (wiki) It can be also a mathematical zero — something that cannot be valued by itself.
But what does it mean for our character? He is nothing without the context, his identity depends on whoever is there in charge, he is blank without someone pulling the strings. He is a code that needs to be cracked and he cannot exist without someone "decoding" him. BOTTOM energy, if you ask me.
Since we started on this topic, let's discuss his appearance. A triangle? Why?
In hierarchy, the base of the triangle supports the pyramid, it's the foundation itself, when the apex (which is in both the Eye, and Bill's design himself) is small and it has to depens on anything that is beneath him. That way, his "top of the pyramid" thing is not dominant. He axists only when there's solid groung beneath him, holding him


His whole design is made after the Eye, but the whole point of it is watching and never interfering directly. He sees everything, but he needs the others to act. He doesn't create a thing, he reacts on thers' actions. Bottom energy, if you ask me - all his power depends directly on others.
The shape's pointed nature can convey a sense of movement and energy, often associated with action and even conflict. In physics, the Greek letter delta (Δ), which is a triangle, is used to represent change. Triandles aren't as stable as circles or squares. Instead, they are usually stuck or falling - they cannot adapt, cannot roll.
As a triangle, Bill is shown ready to change for anyone's need, destined to fall at the BOTTOM.
Bill Cipher is shaped like an equilateral triangle. It is proven with the poem in the choose-your-own-adventure book. The axolotl tells it Dipper when he asks about Cipher.

"Sixty degrees that come in threes". According to geometry book for the 4th grade, that would make him an equiangular triangle, since all of his angles are 60°, the same measure. If a triangle is equiangular, then it's also equilateral, or meaning that all sides are the same length.
In the Bible, 60 can represent periods of waiting or completeness, as well as divine provision and the fulfillment of promises, it is considered as the threshold of when a person enters the last major phase of their life. It means that 60 is the bottom of someone's existence, waiting for recognition, something bigger to come. Once again, it's not acting up, interfering with someone. Instead, it is waiting for something on the outside to react.


An equilateral triangle is something that adheres to external laws of geometry - his construction is perfectly stable. Despite him claiming to be chaotic, his literal shape is a complete submission to mathematical laws. His obidience is built-in since his birth.
Symmetrical shapes are easier to be abused: split, centered, framed and entered into.

His own Zodiac circle is a proof for this: he's in the middle, framed. He's not assymetrical and not trying to be it - instead, he is built like something that awaits to be disrupted and ruined.
Instead of being chaos, he's the most predictable polygon. He doesn't move and his structure is a rule itself. Despite his acting, his design reveals his fate: to be in balance, order, awaiting for an inner force to bring him into the chaos he desires.
Moving on, before gaining physical form, he is shown to us as a shadow twice throughout the series.


But what is a shadow?
A shadow is a dark area or shape created when an object blocks light. It occurs because light travels in straight lines and cannot bend around an opaque object, resulting in a dark silhouette on the opposite side.

How is this related? Well, look where the shadows are formed. Guess where are they. BOTTOM of the object presented. Sun can move wherever it is, but the shadow always stays there. Destinied it is.
Now, let's talk about the American Revolution. This war's result was that the United States of America achieved independence from British rule. But, the country originally struggled at the start due to the lack of government.

The Articles of Confederation was the first attempt on national US government. The problem with this was that states maintained their independence and such document didn’t didnt the federal government power to unite the states together. They lacked many necessary powers. No executive or judicial branch, no power to tax or create a national currency, and a 9/13 majority needed to pass laws, the Articles could not support the country. The founding father set out to create the Constitution, what would be the basis of government today.
As the Constitution went into effect, the system of check and balances was formed. This allowed for each branch of the government to “check” each other and prevent one single branch from being corrupt and taking control of all the national power.

Bill would represent the judicial branch, a branch with only self-placed checks and not necessarily constitutional checks. Bill Cipher can easily take advantage of this and take over the whole government.

Chaos he relates to is often related with power, however, it is a state of utter confusion or disorder; a total lack of organization or order. He's projecting dominance, trying to hide his vulnerability. He talks constantly, only to be shut with someone interrupting him, arguing. He doesn't only need power, he wants others to believe he has it. True dominance doesn’t beg for acknowledgment, but Bill does - it is a facade he's put. The whole Weirdmageddon is nothing but an attempt to break free from his "bottom energy". But did it really help?
Moreover, Bill's afraid of interacting with someone on a deeper level. He's always manipulative, mocking, but never vulnerable - he's a control freak, secretly wising for losing it.
The only reason he mocks human emotions is because he cannot fully engage in them. It's fully shown in the "Sock Opera", where he attempts to manipulate twins by how unstable their relationship is.


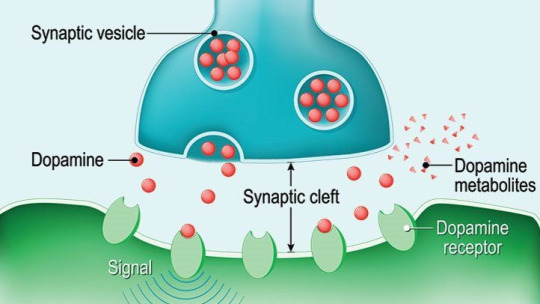
Psychologically, it is that Bill’s desire for power is started from the frontal cortex, specifically the orbitofrontal cortex. The idea of the power given to him is a desire for him to grow. This is deeply connected with dopamine, that his braing releases. He's a BOTTOM, desperately trying to top.
While looking at the BC abbreviation you may think it sounds familiar. It is a common abbreviation for the term "Before Christ" used in dating systems to denote years prior to the traditional start of the Christian era. And when looking at it, BC is located at the bottom of the timeline, alligning where he belongs.

As you can see, Bible was mentioned twice throughout the analysis. This can mean only that Bill has a deep connection with its dogmas.
And it is proven by the holy trinity: a concept, involving three holy figures, just like three sides of Bill. The number three itself holds significance, representing perfection, integration, and the unity of dualities. A full harmony on the outside, deep inside it is a conflict revolving.
This is EXACTLY the way Ohm's triangle works. It is a simple visual tool used to remember the relationship between voltage (V), current (I), and resistance (R) in electrical circuits.

The Ohm’s Law triangle is the same shape as Bill Cipher — an upright triangle.
Bill's show as a voltage in it. He only exists if something else conducts or resists him. He is the top of the triangle, but the triangle only functions if something below him is doing the work.

Voltage — is the power that needs to be conducted and resisted to mean anything.
That’s not dominance. That’s literal dependence on someone, who'll do all the work. Energy only flows when it confronts resistance.
You see, chaos (Bill) only becomes real voltage when he submits to resistance and lets current move through him. He’s not the master of the circuit — he is defined by its work.
Now, let's talk about posession. As wiki says, it's the state of having, owning, or controlling something.
To posess someone, you need to abandon your own form, becoming dependent on someone else. That’s not power - it is submission to someone else’s structure.
It is a vulnerable state of mind and body - a posessed can resist, fight back, and then the posessed one gets destroyed. It requires submission to other's body functioning. It’s a fragile dominance — and fragile dominance is just bottoming with extra steps.
#i cant take it srs#bill cipher#gravity falls#tbob#billford#the book of bill#journal 3#analysis#bottom bill
31 notes
·
View notes
Text
Second-most audacious thing I did in my academic career happened in a cryptography exam. One question gave us a message to encrypt, the method we had to use, and some of the numbers that would be used. We were allowed to choose the remaining values for the encryption algorithm. We had to choose values that would be appropriate and show the process needed to calculate the encryption and decryption keys and show the encryption and decryption process.
The encryption method used exponents and modulo in the encryption and decryption process and instead of actually doing any math on it, I realized I could exploit Fermat's (pronounced fair-ma) little theorem (which the professor had taught earlier that semester) using the numbers the professor gave to make the encryption key equal to 1. As a result, I was able to skip the entire process of showing the encryption process, determining the decryption key, and decrypting the message, because the encryption key I made literally didn't change the message at all.
When I got the exam back, the professor made it very clear how annoyed he was with my answer but gave me full points because I did technically demonstrate how the algorithm works. I'm glad too cause that question was 20% of the exam grade.
He even called me out for my shenanigans when he went over the exam later and modified the question for future semesters to stop others from using my exploit.
192 notes
·
View notes
Text
How To Become Cybersecurity Expert: Scope, Skills, and Salary
In today's digitally interconnected world, it is of utmost importance to secure your company from online threats. Cybersecurity experts play a crucial role in achieving this goal. Their primary responsibility is to proactively identify and prevent potential attacks. They conduct scans and analyze network data to detect any weaknesses and dangers in networks, data centres, and software systems. Additionally, they ensure that hardware and software are always kept up-to-date.
In this article, we'll explore what a cybersecurity professional does, the skills they need, the career growth possibilities, and the typical salary. You can enhance your knowledge in this field by taking a cybersecurity certification online course to learn about modern information and system protection technologies.
What Does a Cybersecurity Specialist Do?
A cyber security specialist is essentially a guardian of computer networks and systems. Their primary mission is to shield these digital domains from a multitude of cyber threats while ensuring the confidentiality, integrity, and availability of critical data. Here are some key responsibilities of a cyber security specialist:
Identifying Vulnerabilities: Their first task is to hunt down and fix security weaknesses in networks, data centres, and software systems. Think of them as the digital detectives who uncover potential entry points for cybercriminals.
Implementing Security Controls: Cyber security specialists employ a variety of security measures such as firewalls, encryption, and multi-factor authentication to fortify digital assets against potential attacks. These measures act as digital barriers, thwarting unauthorized access.
Monitoring Activity: They keep a vigilant eye on network and system activity, looking for any signs of intrusion or suspicious behaviour. This proactive approach enables them to respond swiftly to potential threats.
Responding to Incidents: In the event of a cyberattack, cyber security specialists jump into action. They react swiftly, notifying law enforcement, restoring backups, and communicating with the affected parties through public statements.
Keeping Up with Trends: The ever-evolving nature of cyber threats means that cyber security specialists must stay updated on the latest trends and technologies in the field. Being one step ahead is essential in this game.
Depending on their specialization and level of expertise, cyber security specialists may have different job titles, including:
Cybersecurity Analyst: Responsible for planning, implementing, and monitoring security strategies within an organization.
Cybersecurity Engineer: Designing and building systems to safeguard digital information.
Cybersecurity Architect: Developing and overseeing an organization's entire cyber security strategy.
Cybersecurity Manager: Formulating and implementing security policies while managing security teams.
Penetration Tester: Simulating cyberattacks to identify security weaknesses and providing recommendations.
Chief Information Security Officer: Leading an organization's cybersecurity efforts and collaborating with other executives.
Information Security Crime Investigator: Reviewing evidence to determine if cybercrimes have occurred and assisting law enforcement in apprehending suspects.
Cybersecurity Consultant: Advising organizations on how to identify and mitigate network risks.
Cybersecurity Specialist Skills
Cybersecurity specialist requirements include a blend of technical and soft skills. Here's a breakdown:
Technical Skills:
Network Security: The ability to protect networks from unauthorized access, misuse, or disruption is a foundational skill.
Cryptography: Understanding mathematical techniques to encrypt and decrypt data is essential for securing sensitive information.
Risk Management: Assessing and mitigating potential threats to an organization's information systems is crucial to avoid vulnerabilities.
Cybersecurity Tools and Technologies: Proficiency in using various software and hardware tools for tasks like scanning, testing, and auditing is vital.
Soft Skills:
Communication Skills: Effectively conveying security concepts and findings to both technical and non-technical audiences is essential for collaboration and understanding.
Problem-Solving Skills: The ability to analyze complex situations and find effective solutions is key to navigating the ever-changing cyber landscape.
Critical Thinking Skills: Evaluating information objectively and logically helps make informed decisions in high-pressure situations.
Strategic Thinking Skills: Planning and anticipating future scenarios enable proactive security measures.
How to Become a Cybersecurity Specialist?
Entering the field of cyber security can be achieved through various avenues. Here are some common paths:
Formal Education: Enroll in college or university programs that offer degrees or diplomas in cyber security or related fields. This provides a solid academic foundation.
Self-Study and Certification: Study independently using online resources and obtain relevant certifications to showcase your knowledge and skills. This self-driven approach allows flexibility.
Volunteering and Training: Seek opportunities to volunteer or join organizations offering cybersecurity training programs or internships. Practical experience is invaluable.
Entrepreneurship: Consider starting your own cybersecurity business or joining a team of experts. This path offers autonomy and the chance to work on diverse projects.
What Certifications are Needed for Cybersecurity?
Cyber security certifications are vital for validating your expertise and commitment to the field. They also provide a structured path for acquiring the necessary skills and knowledge. Here are some common certifications:
Certified Cybersecurity Expert™: Ideal for entry-level professionals, this certification covers the fundamentals of cyber security, including network security, threat management, and cryptography.
Certified Information Security Executive™: Designed for experienced professionals, it delves into advanced aspects like security architecture, risk management, and governance.
Certified White Hat Hacker™: Specializing in offensive security, this certification covers ethical hacking techniques, including penetration testing, vulnerability assessment, and malware analysis.
Salary Expectations for Cybersecurity Specialists
The salary of a cyber security specialist can vary based on factors such as location, experience, education, and certifications. However, the average salary in the United States is approximately $117,419 per year. Experienced professionals can command even higher earnings, while those with advanced degrees or certifications enjoy enhanced job prospects.
In conclusion, cyber security is a dynamic and rewarding field that offers a wide array of career opportunities. By understanding the role, acquiring the necessary skills and certifications, and exploring salary prospects, you can embark on a fulfilling journey to become a cybersecurity specialist. Online cyber security certification courses are readily available to help you gain knowledge and skills in modern information and system protection technologies. With dedication and the right tools, you can help safeguard the digital world from cyber threats and play a crucial role in our increasingly digital lives.
If you're interested in pursuing cyber security or blockchain security certifications with a focus on emerging technologies like blockchain, consider exploring the offerings provided by the Blockchain Council. The Blockchain Council is a respected consortium of subject matter experts and enthusiasts dedicated to advancing blockchain research and development, exploring use cases and products, and disseminating knowledge for a better world.
2 notes
·
View notes
Text
Why Enterprises Need Quantum-Safe Cryptography in SAP: Securing the Future with NeuVays

In today’s digital-first business environment, enterprise data security is no longer a back-office IT function—it is a strategic priority. Organizations worldwide depend on the SAP Business Technology Platform (SAP BTP) to power innovation, analytics, and process automation. However, the rapid evolution of quantum computing is threatening the cryptographic foundations of even the most secure SAP landscapes.
To stay ahead of this curve, enterprises must act now to adopt quantum-safe cryptography in SAP, safeguarding their most valuable digital assets before quantum decryption capabilities become mainstream. NeuVays, a forward-looking SAP partner, is pioneering Quantum-Safe SAP BTP Architecture to help enterprises secure their digital ecosystems—today and tomorrow.
🔐 The Threat: Quantum Computing and Cryptographic Risk
Traditional encryption algorithms such as RSA and ECC have protected enterprise data for decades. But with the advancement of quantum computing, these classical methods are at risk. Quantum machines, once powerful enough, can break current encryption schemes in a fraction of the time required by classical computers.
The risk is particularly alarming for enterprises using SAP systems to store and process:
Financial transactions
Personal identifiable information (PII)
Intellectual property (IP)
Supply chain data
This creates a scenario known as "harvest now, decrypt later," where malicious actors capture encrypted data today to decrypt it in the near-future once quantum capabilities mature.
🧬 What Is Quantum-Safe Cryptography?
Quantum-safe cryptography, also called post-quantum cryptography (PQC), refers to cryptographic algorithms designed to be secure against quantum computing attacks. These include methods like:
Lattice-based cryptography
Code-based cryptography
Multivariate polynomial equations
Hash-based signatures
These algorithms are being standardized by global institutions like NIST and ISO, signaling their importance in future-proofing digital infrastructures.
💡 Why Enterprises Need Quantum-Safe Cryptography in SAP
1. Future-Proof Enterprise Data Security
SAP systems hold the digital DNA of an organization. From customer data to business logic and financials, a breach in SAP can cripple operations and trust. Adopting quantum-safe encryption ensures that enterprise data stored or transmitted via SAP BTP remains secure in the quantum era.
2. Regulatory Compliance and Long-Term Confidentiality
Data protection laws like the GDPR, DPDP Act (India), and HIPAA mandate long-term confidentiality of sensitive data. Quantum-safe cryptography ensures encrypted records remain compliant decades into the future.
3. Defending Against “Harvest Now, Decrypt Later” Attacks
Even if a quantum attack doesn’t happen tomorrow, data exfiltrated today may still be decrypted later. With SAP BTP encryption framework, NeuVays integrates hybrid encryption models that combine traditional and post-quantum algorithms to eliminate such risks.
4. Strengthening the SAP BTP Security Framework
SAP BTP provides several native tools to manage security—role-based access, identity authentication, logging, and encryption. Quantum-safe cryptography enhances the existing SAP BTP security model by securing its weakest links: long-lived secrets and cryptographic keys.
🧱 Quantum-Safe SAP BTP Architecture by NeuVays
NeuVays has engineered a specialized framework—Quantum-Safe SAP BTP Architecture—to transform enterprise SAP landscapes into resilient, future-ready environments. This includes:
✔ Integration of Post-Quantum Algorithms
Leveraging NIST-recommended quantum-resistant algorithms like CRYSTALS-Kyber and Dilithium to replace RSA and ECC in key exchanges and digital signatures.
✔ Hybrid Cryptographic Framework
Combining quantum-safe and classical algorithms to ensure backward compatibility while securing future transmissions.
✔ SAP BTP Encryption Framework Optimization
Strengthening the SAP BTP encryption framework to support advanced cryptographic libraries, including customer-managed keys and key lifecycle automation.
✔ Zero-Trust Architecture Alignment
Ensuring that quantum-safe cryptography supports a Zero Trust security model, including continuous verification, least privilege access, and secure identity management.
🔎 SAP BTP Security Best Practices: How NeuVays Delivers End-to-End Protection
While quantum-safe cryptography addresses emerging threats, it’s only one part of a comprehensive defense. At NeuVays, we integrate SAP BTP security best practices to build robust environments, including:
Role-based access control (RBAC) and SSO integrations
Multi-factor authentication (MFA) enforcement
Encrypted APIs and service connections
Continuous logging and anomaly detection
Data isolation and tenant segregation
Our approach ensures that even if quantum threats evolve, your SAP landscape remains secure across all layers.
📈 Industry Use Case: Quantum-Safe Data in Action
A global logistics enterprise running on SAP BTP approached NeuVays to secure sensitive route optimization and partner data. The company anticipated major competition and potential state-sponsored threats to its proprietary algorithms.
NeuVays’ solution:
Upgraded SAP BTP security configurations
Integrated lattice-based quantum-safe algorithms for data encryption
Applied hybrid cryptography to secure data in transit and at rest
Customized dashboards to monitor cryptographic performance
Result: The enterprise achieved long-term data protection and compliance while gaining a competitive edge as a future-ready organization.
🧠 Preparing for a Quantum Future with NeuVays
The quantum era is no longer hypothetical—governments and big tech companies are investing billions into quantum R&D. With SAP BTP being the central nervous system of digital enterprises, ensuring its security is non-negotiable.
NeuVays guides enterprises in:
Assessing quantum risk to existing SAP environments
Creating roadmaps to quantum-safe architecture
Integrating encryption best practices and identity management
Aligning with upcoming global security standards
🚀 Why Choose NeuVays for SAP BTP Security
NeuVays is not just a SAP implementation partner—we are a SAP-certified partner and security-first technology firm specializing in SAP BTP security and enterprise data security. Our unique positioning allows us to:
Blend functional expertise with advanced cryptography
Deploy scalable security architecture across industries
Offer 24/7 SAP BTP performance and threat monitoring
Future-proof your business before cyber threats catch up
✅ Conclusion
Quantum computing is set to revolutionize industries—and cyber threats. Enterprises that continue to rely on classical encryption without upgrading will risk losing data integrity, compliance status, and stakeholder trust.
Why do enterprises need quantum-safe cryptography in SAP? Because waiting is not an option.
With NeuVays' Quantum-Safe SAP BTP Architecture, robust encryption frameworks, and SAP BTP best practices, your enterprise can confidently protect what matters most—now and in the future.
📞 Ready to build quantum-safe SAP security? Contact NeuVays to get started today.
0 notes
Text
Q-Day Bitcoin must update quantum computing in 5 years

In five years, Q-Day Bitcoin must develop or be defeated by quantum computing.
A quantum attack might shatter Bitcoin's 16-year-old trust unless it updates its core cryptography in the next five years. Updates are needed immediately to secure the most popular cryptocurrency.
After the 2008 financial crisis, Satoshi Nakamoto created a decentralised monetary system using elliptic curve cryptography, revolutionising money. Decentralisation and exact math blended nicely, drawing many people and corporations, including BlackRock. Bitcoin is sixteen years old and has never been hacked.
Quantum computing, Bitcoin's biggest threat since its inception, may change this. Quantum computers, once considered science fiction, may crack Bitcoin's cryptography in five years or even next year, according to quantum commentator Michele Mosca.
Rise of Supercomputers
Microsoft's Majorana processor, released this year, has cut the time needed to build a useful quantum supercomputer from decades to a few years. This chip is tackling key challenges in this technical breakthrough and enabling dependable and scalable quantum systems. McKinsey predicts 5,000 quantum computers by 2030, up from 100 today. These faster machines belong to a new class that can do operations in parallel, which kills classical cryptography like Bitcoin's private key encryption using ECDSA.
At least 30% of Bitcoin, 6.2 million, are held in “pay-to-public-key (P2PK)” or “reused P2PK-hash addresses,” making them vulnerable to quantum threats. Besides incurring permanent financial loss for Bitcoin holders, a breach would damage the ecosystem by disproving the system's impenetrability. BlackRock acknowledged the quantum danger to Bitcoin in its updated spot ETF registration.
Q-Day Bitcoin
It depicts the moment quantum computers will be powerful enough to break cryptography. Bitcoin vulnerability: Bitcoin transactions verified and secured ten years ago may still be at danger on Q-Day. Because the blockchain is transparent and its data is always available on the ledger.
“Harvest now, decrypt later” threat: Malkers are collecting encrypted data for Q-Day. This method is called “harvest now, decrypt later”. Possible simultaneous attacks: Quantum attacks could occur simultaneously worldwide as Q-Day approaches.
Bitcoin must be ready for this. The community must advance Bitcoin and prepare for Q-Day now rather than later. Bitcoin is most threatened by complacency, not quantum computing.
Readying for Q-Day
Quantum computers will break cryptography on “Q-Day”. Bitcoin transactions approved and secured today or ten years ago may still be at risk since the blockchain is open and its data is constantly available. Hostile actors are also practicing “harvest now, decrypt later” by gathering encrypted material for Q-Day, which might lead to global strikes. Bitcoin must prepare for this.
Post-Quantum Future
Legacy blockchains must be hard forked to switch to post-quantum cryptography. This difficult problem in the crypto ecosystem may generate user experience concerns, liquidity dispersion, network splitting, and long-term user alienation. Layered security models, quantum-secure key management infrastructure, and hybrid systems that prioritise transaction security without changing the base layer are alternatives.
Given Bitcoin's cautious and slow growth, this adjustment is not a cure. In a post-quantum future, Bitcoin cannot survive, so decisions and solutions must be made fast.
Satoshi Nakamoto's new monetary system is meant to change. The community must decide on evolution and prepare for Q-Day now, not later. Bitcoin is most threatened by complacency, not quantum computing.
#QDayBitcoin#quantumcomputing#Bitcoin#MicrosoftMajoranachip#cryptography#blockchain#postquantumcryptography#News#Technews#Technology#Technologytrends#Govindhtech
1 note
·
View note
Text
Post Quantum Encryption: Future of Unbreakable Digital Security
What if all that we believed was safe—our bank transfer, confidential messages, and national secrets—can be wiped out instantly because of quantum computers? The digital era, fueled by classical cryptography, is on the verge of being revolutionized. Because quantum computing is growing exponentially, traditional cryptographic techniques are failing. The solution to this impending threat is a breakthrough technology in the form of Post Quantum Encryption—a quantum-proof method that is capable of deflecting even the most aggressive quantum attacks.
This emerging technology is reshaping the future of cybersecurity by preparing for a world where quantum computers can crack current encryption standards in seconds. In this article, we’ll discover what Post-Quantum Encryption is, why it is relevant, how it works, and how it is changing the future of unbreakable digital security.
Rethinking Digital Safety: The Post-Quantum Landscape
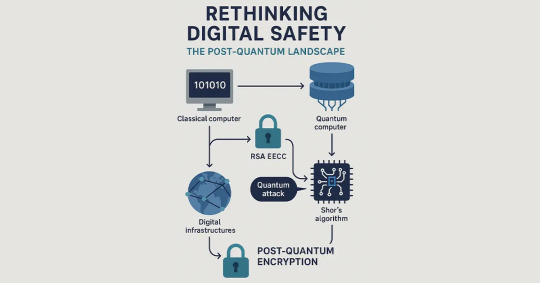
Quantum computers apply the principles of quantum mechanics for calculations that surpasses the limits of functionality of classical computers.. The foundations of today’s encryption, RSA and ECC, can be hacked using algorithms like Shor’s algorithm literally in a split second across classical computers. That is with the coming of age of quantum computing, current encryption will become obsolete.
Post-Quantum Encryption refers to cryptographic schemes that are quantum- and classical computer-resistant. It is not quantum-mechanical but rather mathematical problems believed to be hard for both machine classes. Using these crypto techniques now, we can start to protect digital infrastructures well before quantum attacks are mainstream.
AI and Data Protection: A New Methodology for Future Security

Redefining Our Strategy for AI-Safe Systems
In order to have a safe and ethical future where artificial intelligence (AI) is both ethical and not at the cost of human data, we need to redefine our digital defenses. Data protection is the linchpin—not merely for privacy, but to ensure that AI doesn’t become cataclysmically autonomous.
A. Quantum-Resistant Data Security
The highest priority is to create secure, decentralized models for encrypted data storage. Post-Quantum Encryption has a crucial role to play here. In contrast to conventional models, post-quantum cryptographic models are quantum-proof against decryption attacks. For example, blockchain-based projects such as NCOG Earth Chain have already started deploying decentralized storage systems driven by post-quantum algorithms. This empowers users with control over their data and excludes the possibility of centralized attacks or AI manipulation. Mass-scale adoption of post-quantum encryption...
#post quantum encryption#post quantum blockchain#post quantum security#post quantum cryptography#quantum computers#quantum computing#ncog earth chain#data security#quantum-resistant#quantum security#quantum blockchain
1 note
·
View note
Text
The Impact of Quantum Computing on the Future of Cyber Security

For decades, cybersecurity has relied on the seemingly impenetrable mathematical fortresses of classical cryptography. Our digital world, from secure online banking to encrypted communications, is built on the assumption that breaking these codes would take even the most powerful supercomputers an impossibly long time – trillions of years, in some cases.
But a seismic shift is on the horizon, one that promises to dismantle these fortresses with frightening speed: quantum computing. While still in its early stages, the rapid advancements in quantum technology signal a fundamental re-evaluation of how we protect our most sensitive information. This isn't just an upgrade; it's a revolution that will impact every facet of cybersecurity.
The Looming Threat: What Quantum Computers Can Break
The primary concern revolves around Shor's Algorithm. Developed by Peter Shor, this quantum algorithm can efficiently factor large numbers and solve discrete logarithm problems – the very mathematical bedrock upon which widely used public-key encryption standards like RSA and Elliptic Curve Cryptography (ECC) are built.
Imagine this: the encryption securing your online transactions, your VPN connection, your digital signatures, and even the confidentiality of critical government data could theoretically be cracked in mere seconds or minutes by a sufficiently powerful quantum computer. This isn't a distant threat; it's a future that cybersecurity professionals are actively preparing for.
Another quantum algorithm, Grover's Algorithm, while not directly breaking encryption, can significantly speed up brute-force attacks on symmetric-key algorithms like AES (Advanced Encryption Standard). This means that to maintain the same level of security, we'll need to double the key lengths of these algorithms.
The implications are profound, leading to fears of a "quantum apocalypse" where much of today's encrypted data becomes vulnerable. This also gives rise to "harvest now, decrypt later" attacks, where malicious actors collect encrypted data today, knowing they can decrypt it once quantum capabilities become available.
The Silver Lining: Quantum Computing as a Shield
It's not all doom and gloom. The relationship between quantum computing and cybersecurity is a double-edged sword. Just as quantum computing poses threats, it also offers unprecedented opportunities to build more robust and future-proof security solutions:
Post-Quantum Cryptography (PQC): This is the most crucial line of defense. PQC involves developing new cryptographic algorithms that are resistant to attacks from both classical and quantum computers. Organizations like the National Institute of Standards and Technology (NIST) are actively standardizing these new algorithms, which are based on different mathematical problems that are believed to be hard for even quantum computers to solve (e.g., lattice-based, hash-based, and code-based cryptography). The transition to PQC will be a monumental effort, requiring upgrades across all digital infrastructure.
Quantum Key Distribution (QKD): This technology leverages the fundamental laws of quantum mechanics to enable two parties to establish a shared encryption key with provable security. Any attempt by an eavesdropper to intercept the key would inevitably alter its quantum state, immediately alerting the communicating parties. While QKD offers theoretical "unhackable" communication, its practical implementation faces challenges related to distance and infrastructure.
Enhanced Threat Detection: The immense processing power of quantum computers could revolutionize threat detection and response. Quantum algorithms might be able to analyze vast datasets of network traffic and system logs at unprecedented speeds, identifying anomalies and sophisticated attack patterns far more efficiently than current AI/ML systems. This could lead to real-time, proactive defense capabilities.
The Road Ahead: Preparation is Key
While a fully fault-tolerant, universal quantum computer capable of breaking current encryption may still be years, or even a decade or two, away, the cybersecurity community is not waiting. The timeline for the "quantum safe" transition is long, and history shows that cryptographic migrations can take well over a decade.
Organizations, governments, and individuals must start preparing now:
Inventory Cryptographic Assets: Identify all systems, applications, and data that rely on current public-key cryptography.
Assess Quantum Risk: Determine the level of risk quantum attacks pose to your critical data and infrastructure.
Develop a PQC Migration Roadmap: Plan for the phased adoption of quantum-resistant algorithms, considering hybrid approaches that combine classical and PQC methods during the transition.
Invest in Crypto Agility: Build systems that can easily swap out cryptographic algorithms as new standards emerge and threats evolve.
Stay Informed: Keep abreast of the latest developments in quantum computing and post-quantum cryptography research.
The quantum era will undoubtedly redefine cybersecurity. While it brings significant challenges to our existing security paradigms, it also ushers in an exciting era of innovation, promising a future where our digital defenses are stronger and more resilient than ever before. The time to prepare for this quantum reckoning is now.
0 notes
Text
Abstract The literature review is on the digital signature and the opinions of different writers who have written on this topic. There have been some articles written on the topic of digital signature, a problem on cryptography needs to be solved, there are different companies and organizations that continuously use computers to carry out transactions between them and their customers. A system that cannot allow outsiders to access the insider information on these companies needs to be set up; this will help to prevent the possibility of the company computers being hacked into. Introduction A digital signature is quite effective in the sense that any person who tries to get into the companies database but does not have the access code is immediately denied access. The administrators can also be able to determine whether the information that they are receiving from their clients is genuine. The digital signature helps a person to know that the information is original and that it has not been interfered with. Companies that make use of digital signatures are able to curb the possibility of receiving falsified information. These signatures are used in some countries as a form of authenticating the information that has been put on the internet or in any computer application, this helps to determine whether the information is just as the writer intended it to be. A lot of companies are establishing the use of digital signatures in most of their transactions, thereby enhancing the importance of encryption of data in all companies’ computer systems. Cryptography is important as it facilitates the maintenance of security of any company’s data and ensures that only the right people access the company data. In an article on a method for obtaining a digital signature, Rivest et al (1978) have discussed their view of encryption widely. They state that: An encryption method is presented with the novel property that publicly revealing an encryption key does not thereby reveal the corresponding decryption key. This has two important consequences: (1) Couriers or other secure means are not needed to transmit keys, since a message can be enciphered using an encryption key publicly revealed by the intended recipient. Only he can decipher the message, since only he knows the corresponding decryption key. (2) A message can be “signed” using a privately held decryption key. Anyone can verify this signature using the corresponding publicly revealed encryption key. Signatures cannot be forged, and a signer cannot later deny the validity of his signature (p.120). They give information on the encryption concept and an explanation of how it works. According to them, the process is quite useful because even when a person knows the key-encryption key, he would not be able to access the data contained in that computer if the person was not able to access the decryption key. It, therefore, means that only the person who knows both keys can be able to access the company data. There are two issues on cryptography that have been discussed by Diffie and Hellman (1976) in their article on cryptography. They state that “Widening applications of teleprocessing have given rise to a need for new types of cryptographic systems, which minimize the need for secure key distribution channels and supply the equivalent of a written signature.” They also claim that there is a need to find solutions to the problems that arise due to encryption. Their article also “discusses how the theories of communication and computation are beginning to provide the tools to solve cryptographic problems of long-standing” (p. 644). There is a connection between the issues that the article writers talked about. They seem to have been writing about how the majority of companies are trying to protect the data that they have saved in their computers, the majority of the transactions between the companies and their clients are electronic. With the advent of electronic transactions, there are risks that the data could be accessed by unauthorized persons and therefore be interfered with. The notion of digital signature was coined by Heyst and Chaum (1991), the idea of a person signing on behalf of other persons on receiving a message on a computer is quite convenient for the whole company. The idea that an employee can sign documents on behalf of others in a company, without the receiver realizing that the message that he received was not signed by who he expects to have signed, saves time for the other employees. Only one person has access to the group signature password so the signature cannot be used by unauthorized persons, the administrators can therefore be able to verify who it was that used the signature (p.257). The concept of signatures based on identity has been recommended, this is according to Rivest et al (1978). However, this concept had certain disadvantages that include the expensive “Bilinear pairing” from which it comes from. The use of this ring without pairing is, therefore, more affordable. There is therefore a recommendation for use of ring signature based on “quadratic residue” which is more efficient (p.122). Miyazaki et al (2006), claim that when a digital signature has been used, the contents of the documents cannot be changed thereafter. This is mostly done to reduce the possibility of the contents being interfered with and the meaning of the document being changed (p.343). An article by Niccache et al (2008), introduces the notion of “twinning”, which makes the signing of short messages possible, and the writer, therefore, has to sign twice in his message by a signature scheme (p.20). Wireless network sensor (WNS) makes it impossible to use “asymmetrical cryptography”; this is according to Driessen et al (2008), in the article that they wrote on the security of the wireless network. There is also a need for the concerned parties to make sure that they receive each other’s signatures on the internet, this will enhance security for both companies as they will have evidence of each other’s commitments to the contract that they had both agreed to honor (p.31), this is what Wang (2005) states in his article about the conference on the world wide web in Japan (p.412). Summary/ Evaluation The ten articles that have been reviewed contain information on encryption by different companies, and why it is important in the security of any company, with encryption the company’s data and private information cannot be assessed by unauthorized people. The use of digital signatures also ensures that only genuine businesses are conducted and that the company is not conned by online fraudsters. Electronic signatures use can be found in many different transactions, among them is in the use of e-mail on the internet and also in money transfer which is carried out electronically. Diffie and Hellman (1976), claim that it is easy to use encryption and decryption and that both processes are similar; in both, there is the use of public numbers and confidential numbers (p.646). The companies today always conduct their transactions electronically, that being the case, Subramanya and Li (2006) in their article on digital signatures, claim that there is a need for the companies who conduct their businesses electronically to guard their data against their competition and online fraudsters, this ensures that the data has not been interfered with and that the information on the company that they had offered to their customers is still the same and is authentic. Digital signatures serve the same purpose as manual signatures; their function is to authenticate documents that are sent online as opposed to being sent manually. The concept of digital signatures is relatively new but there is a high possibility that many more companies will adopt it accordingly (p.5). Group signatures are a quite important concept in all companies, Chaum and Heyst (1991) came up with it, a person can be able to make signatures for other people whom she works with, if she has a prestigious position, then she can not only be able to sign for fellow workers who are in similar positions, but also for workers who are of lower status. The data can be a lot or little depending on the number of people involved but in some cases, the person who makes the signatures can be easily recognized. The article was written on ring signatures by Rivest, Shamir, et al (1978) contains a lot of information on identity-based ring signatures, the writers state that these kinds of signatures have been under scrutiny by different people just as they have been recommended by a lot of people. The fact that the signatures which are not paired are more popular is apparent, based on the article, the ring signatures which are made from “bilinear pairing” are too costly and that is why the majority of people prefer to use the “ID-based ring signatures based on quadratic residues (p.123).” These kinds of signatures are more efficient as compared to the ones which are paired. What makes it more efficient is the fact that is less likely to be falsified by the people who would like to sabotage the company. Only the person who gave the mandate to make the signature can be able to use the ID-based ring signatures as compared to other signatures. When a document has been written and a digital signature has been put on the document, the content of the documents cannot be changed under any circumstance. This is according to Miyazaki et al (2006) in a document that they wrote concerning a conference on “Information, computer, and communications Security”, which was held in Taiwan. They however recommend that there is a need for an opportunity for the document to have some form of changes done on the document; nonetheless, the modifications should be done about the safety of the overall documents. The information contained in the document should be changed accordingly so that the meaning of the document does not change (p.344). The writers further say that in the case of formal documents, the private information is in most cases shrouded in such a way that, only an authorized person can be able to assess the information. The same case applies in “national security” documents which the state does not want to fall into the wrong hands. In most cases, only certain information can be revealed when a person asks for it. When the information that has been requested is done through the “current digital signature scheme”, there is a possibility that the person requesting the information will not be able to assess the information that they are looking for because the private information, in that case, has been protected from interference (p.345). Read the full article
0 notes
Text
Sao Culture | A Forgotten African Civilization
youtube
In cryptography, a cipher (or cypher) is an algorithm for performing encryption or decryption—a series of well-defined steps that can be followed as a procedure. An alternative, less common term is encipherment. To encipher or encode is to convert information into cipher or code. In common parlance, "cipher" is synonymous with "code", as they are both a set of steps that encrypt a message; however, the concepts are distinct in cryptography, especially classical cryptography.
The Pan-Nigerian alphabet is a set of 33 Latin letters standardised by the National Language Centre of Nigeria in the 1980s. It is intended to be sufficient to write all the languages of Nigeria without using digraphs.[1]
History
Several hundred different languages are spoken in Nigeria. The different Latin alphabets made it impractical to create Nigerian typewriters. In the 1980s the National Language Centre (NLC) undertook to develop a single alphabet suitable for writing all the languages of the country, and replacing use of Arabic script, taking as its starting point a model proposed by linguist Kay Williamson in 1981.[citation needed] A typeface was developed in 1985–1986 by Edward Oguejofor and Victor Manfredi, in co-operation with the NLC, with technical assistance from Hermann Zapf.
🇷🇴🇷🇴🇷🇴🇷🇴🇷🇴🇷🇴🇷🇴🇷🇴🇷🇴🇷🇴🇷🇴🇷🇴🇷🇴🇷🇴🇷🇴🇷🇴🇷🇴🇷🇴🇹🇹🇹🇹🇹🇹🇹🇹🇹🇹🇹🇹🇹🇹🇹🇹🇹🇹🇹🇹🇹🇹🇹🇹🇹🇹🇹🇹🇹🇹🇹🇹🇹🇹🇹🇹
CLIVE OBASI
0 notes
Text
Google’s Willow chip to challenge cryptography, but Bitcoin will hold steady, players believe
Google unveils Willow quantum chip, posing potential threat to Bitcoin security, but experts believe decryption remains distant with 105 qubits.
Google has unveiled its Willow quantum computing chip, which some speculate could “crack” Bitcoin. However, cryptocurrency experts argue that decrypting a Bitcoin typically requires around 13 million qubits, far exceeding Willow’s 105 qubits.
On Monday,Alphabet and Google CEO Sundar Pichai announced the development of Willow on social media platform X. He stated that the quantum computing chip can reduce errors exponentially as Google scales up using more qubits, cracking a 30-year challenge in the field. In benchmark tests, Willow solved a standard computation in less than five minutes, unlike a supercomputer that would require indefinite time.
A qubit, or a quantum bit, is the basic unit of quantum information in quantum computing. Unlike a classical bit or a binary of 0 or 1, a qubit can represent both 0 and 1, allowing quantum computers to process many combinations simultaneously.
Existential risk?
Twitter user Monetary Commentary pointed out that this development is potentially alarming for Bitcoin and other cryptos that rely on public-key cryptography.
The user explained that Bitcoin’s security is supported by elliptic curve cryptography (ECC), a system designed to be computationally impossible for traditional computers to break within a reasonable timeframe. However, quantum computers like Willow, with exponentially reduced error rates and vast computational power, pose a direct threat to ECC.
Quantum algorithms can factorise large integers and compute discrete logarithms — either of which can break ECC. A machine like Willow that can perform computations in minutes that would take other supercomputers infinitely longer, represents an existential risk to Bitcoin’s security model.
“The idea of quantum computers cracking Bitcoin is still far off. Google’s Willow chip, with 105 qubits, is impressive, but lightyears away from the millions needed to challenge Bitcoin’s security. Think of qubits as the ‘power cores’ — the more you have, the more powerful the computer. Even if Willow’s qubits are ground-breaking and hold promise for addressing challenges like climate modelling and drug discovery, it’s not enough to break Bitcoin’s encryption,” observed Himanshu Maradiya, Chairman and Founder of CIFDAQ.
Obstacles like scaling and error correction remain. However, while the crypto world is building quantum-resistant solutions with the evolution of quantum technology, industries from finance to cybersecurity will need to adapt, ensuring that they are future-ready, he said.
Utkarsh Tiwari, the chief strategy office of KoinBX, resounded this, saying that while some discussions link quantum advancements to the potential for “cracking” it, Bitcoin is based on cryptographic algorithms like SHA-256, which would require more than a million qubits to pose a genuine threat.
“Willow’s capabilities, while impressive, do not yet pose an immediate risk to the cryptographic foundations. The estimated computational power required to compromise Bitcoin’s encryption methods is still far beyond what Willow can achieve,” said Balaji Srihari, Vice-President, CoinSwitch.
A call to action
Quantum computing could theoretically solve cryptographic puzzles faster than classical systems. However, the timeline to achieve such capabilities remains uncertain, says Sathvik Vishwanath, the co-founder and CEO of Unocoin. Willow’s demonstration focuses on specific benchmarks rather than direct cryptographic attacks.
However, Mohammed Roshan Aslam, the co-founder & CEO of GoSats, feels that new cryptography practices and encryption methodology will have to be developed to address any potential challenge posed by Google’s Willow.
Nearly 105 qubits fall short of the necessary 13 million qubits to complete Bitcoin’s decryption, he pointed out. “If subsequent R&D in Google Willow manages to integrate such computational power in the future, cryptography and encryption developments may align with addressing this challenge. Additional software upgrades like hard fork in blockchain may be implemented to address this issue, but that may not be the ideal solution. For now, we have only limited understanding of Google Willow, and crypto and tech stakeholders will have to work in tandem to find an amicable solution for this.”
The Willow development serves as both a breakthrough and a call to action, with quantum computing potentially reshaping financial systems, including Bitcoin, in the future. However, Unocoin’s Vishwanath added, the Bitcoin community remains resilient, focusing on maintaining long-term security and technological advancements to counter potential quantum threats.
www.cifdaq.com #CIFDAQ #CRYPTO #TRADING #BLOCKCHAIN
0 notes
Text

Google’s Willow chip to challenge cryptography, but Bitcoin will hold steady, players believe
Google has unveiled its Willow quantum computing chip, which some speculate could “crack” Bitcoin. However, cryptocurrency experts argue that decrypting a Bitcoin typically requires around 13 million qubits, far exceeding Willow’s 105 qubits.
On Monday,Alphabet and Google CEO Sundar Pichai announced the development of Willow on social media platform X. He stated that the quantum computing chip can reduce errors exponentially as Google scales up using more qubits, cracking a 30-year challenge in the field. In benchmark tests, Willow solved a standard computation in less than five minutes, unlike a supercomputer that would require indefinite time.
A qubit, or a quantum bit, is the basic unit of quantum information in quantum computing. Unlike a classical bit or a binary of 0 or 1, a qubit can represent both 0 and 1, allowing quantum computers to process many combinations simultaneously.
Existential risk?
Twitter user Monetary Commentary pointed out that this development is potentially alarming for Bitcoin and other cryptos that rely on public-key cryptography.
The user explained that Bitcoin’s security is supported by elliptic curve cryptography (ECC), a system designed to be computationally impossible for traditional computers to break within a reasonable timeframe. However, quantum computers like Willow, with exponentially reduced error rates and vast computational power, pose a direct threat to ECC.
Quantum algorithms can factorise large integers and compute discrete logarithms — either of which can break ECC. A machine like Willow that can perform computations in minutes that would take other supercomputers infinitely longer, represents an existential risk to Bitcoin’s security model.
“The idea of quantum computers cracking Bitcoin is still far off. Google’s Willow chip, with 105 qubits, is impressive, but lightyears away from the millions needed to challenge Bitcoin’s security. Think of qubits as the ‘power cores’ — the more you have, the more powerful the computer. Even if Willow’s qubits are ground-breaking and hold promise for addressing challenges like climate modelling and drug discovery, it’s not enough to break Bitcoin’s encryption,” observed Himanshu Maradiya, Chairman and Founder of CIFDAQ.
Obstacles like scaling and error correction remain. However, while the crypto world is building quantum-resistant solutions with the evolution of quantum technology, industries from finance to cybersecurity will need to adapt, ensuring that they are future-ready, he said.
Utkarsh Tiwari, the chief strategy office of KoinBX, resounded this, saying that while some discussions link quantum advancements to the potential for “cracking” it, Bitcoin is based on cryptographic algorithms like SHA-256, which would require more than a million qubits to pose a genuine threat.
“Willow’s capabilities, while impressive, do not yet pose an immediate risk to the cryptographic foundations. The estimated computational power required to compromise Bitcoin’s encryption methods is still far beyond what Willow can achieve,” said Balaji Srihari, Vice-President, CoinSwitch.
A call to action
Quantum computing could theoretically solve cryptographic puzzles faster than classical systems. However, the timeline to achieve such capabilities remains uncertain, says Sathvik Vishwanath, the co-founder and CEO of Unocoin. Willow’s demonstration focuses on specific benchmarks rather than direct cryptographic attacks.
However, Mohammed Roshan Aslam, the co-founder & CEO of GoSats, feels that new cryptography practices and encryption methodology will have to be developed to address any potential challenge posed by Google’s Willow.
Nearly 105 qubits fall short of the necessary 13 million qubits to complete Bitcoin’s decryption, he pointed out. “If subsequent R&D in Google Willow manages to integrate such computational power in the future, cryptography and encryption developments may align with addressing this challenge. Additional software upgrades like hard fork in blockchain may be implemented to address this issue, but that may not be the ideal solution. For now, we have only limited understanding of Google Willow, and crypto and tech stakeholders will have to work in tandem to find an amicable solution for this.”
The Willow development serves as both a breakthrough and a call to action, with quantum computing potentially reshaping financial systems, including Bitcoin, in the future. However, Unocoin’s Vishwanath added, the Bitcoin community remains resilient, focusing on maintaining long-term security and technological advancements to counter potential quantum threats.
www.cifdaq.com #CIFDAQ #CRYPTO #BLOCKCHAIN #WEB3
0 notes
Text
Google’s Willow chip to challenge cryptography, but Bitcoin will hold steady, players believe Google unveils Willow quantum chip, posing potential threat to Bitcoin security, but experts believe decryption remains distant with 105 qubits. Google has unveiled its Willow quantum computing chip, which some speculate could “crack” Bitcoin. However, cryptocurrency experts argue that decrypting a Bitcoin typically requires around 13 million qubits, far exceeding Willow’s 105 qubits. “The idea of quantum computers cracking Bitcoin is still far off. Google’s Willow chip, with 105 qubits, is impressive, but lightyears away from the millions needed to challenge Bitcoin’s security. Think of qubits as the ‘power cores’ — the more you have, the more powerful the computer. Even if Willow’s qubits are ground-breaking and hold promise for addressing challenges like climate modelling and drug discovery, it’s not enough to break Bitcoin’s encryption,” observed Himanshu Maradiya, Chairman and Founder of CIFDAQ. www.cifdaq.com
0 notes
Text
What Is Commvault & New Post-Quantum Cryptography Abilities

Commvault: What is it? Post-quantum cryptography strengthens data security against new threats.
Commvault, a major cyber resilience and hybrid cloud data protection company, has made substantial post-quantum cryptography (PQC) advances. These advances should allow governments and companies to protect long-term, sensitive data from new, undiscovered cyberthreats. Commvault is among the first vendors of cyber resilience to allow PQC.
Included in this significant upgrade is support for the Hamming Quasi-Cyclic (HQC) algorithm. HQC is a novel code-based technique designed specifically to guard against the dangerous “harvest now, decrypt later” hazard. This type of attack involves malicious actors intercepting and storing encrypted network communications with the express purpose of decrypting them later, when quantum computers have the massive capacity to break conventional encryption methods.
This expanded PQC capability is a natural progression of Commvault’s current cryptographic agility (crypto-agility) technology, which was initially introduced in August 2024. Based on suggestions from NIST, Commvault has supported a number of quantum-resistant encryption standards since its inception. Among the well-known algorithms are CRYSTALS-Dilithium, SPHINCS+, FALCON, and CRYSTALS-Kyber. Users can manage rapidly evolving threats without having to overhaul their existing systems because to the Commvault Cloud platform’s built-in crypto-agility framework.
According to Commvault Chief Security Officer Bill O’Connell, “the quantum threat isn’t theoretical.” He emphasized that one of the first cyber resilience providers to address the challenges presented by post-quantum computing was Commvault. By enhancing their crypto-agility architecture and including new algorithms like HQC, Commvault aims to provide users with the resources they require to successfully navigate this demanding environment. “We intend to help our customers keep their data protected as quantum computing threats emerge,” said O’Connell. This is Commvault’s declared objective.
The pressing necessity for proactive PQC adoption is highlighted by the quick development of quantum computing. Quantum computing analyzes data and solves complex issues that conventional computers would take decades to solve. These technological advances pose enormous security dangers and provide huge opportunities. Threat actors could use quantum computing to break and unlock encryption, rendering present security measures useless.
Strong figures further highlight the urgency:
According to the Information Systems Audit and Control Association’s (ISACA) Quantum Computing Pulse Poll, a significant 63% of technology and cybersecurity professionals think that quantum computing would increase or alter cybersecurity vulnerabilities.
Moreover, half of these experts think that quantum computing will lead to new problems with compliance and regulations. These statistics provide compelling evidence in favor of the conclusion that “now is the time to prepare and take action.”
Commvault’s improved PQC capabilities are especially advantageous for companies that need to preserve sensitive data over an extended period of time. These include sectors including banking, healthcare, and government. In order to fortify network tunnels against potential quantum-based intrusions, the new features provide a range of safeguards. Additionally, Commvault’s integrated Risk Analysis tools enable clients to effectively identify and classify their data, enabling them to determine the precise locations where these state-of-the-art cryptographic measures are most crucial. These new features are easy to deploy, often requiring only a checkbox decision, which facilitates customer uptake.
Consumers and business analysts have commended Commvault’s forward-thinking approach. Phil Goodwin, Research VP at IDC, stated that “quantum readiness has become a business imperative,” particularly for organizations that handle data that must remain sensitive for many decades. Because of its early implementation of quantum-resistant cryptography, Commvault is “at the forefront among data protection software vendors in proactively addressing quantum threats,” Goodwin continued.
Customer testimonials further emphasize the advantages of Commvault’s innovations:
Jeff Day, the deputy chief information security officer for the Nevada Department of Transportation, hailed Commvault as a “valuable partner” in their pursuit of enhanced cyber resilience. He emphasized that in order to meet stringent government security requirements and protect extremely sensitive data from emerging quantum threats, Commvault’s crypto-agility framework and leadership in implementing PQC are exactly what is needed. Peter Hands, Chief Information Security Officer at the British Medical Association, said he had “great confidence” that Commvault’s prompt incorporation of quantum standards, especially HQC, would protect their critical data “now and well into the future.” He also emphasized the importance of Commvault’s commitment to crypto-agility for healthcare organizations like the BMA.
The most recent post-quantum cryptography capabilities of Commvault, such as full support for NIST’s HQC algorithm, are now instantly available to Commvault Cloud clients. Customers can now simply deploy quantum-resistant protection if they are utilizing software version CPR 2024 (11.36) or later. Commvault, the “gold standard in cyber resilience,” helps over 100,000 organizations maintain data safety and business resilience with a platform that combines data protection and quick recovery at enterprise scale, across any workload, at the lowest total cost of ownership.
What’s Commvault?
Software for data management and security is offered by Commvault to businesses of all sizes. Businesses in the manufacturing, retail, healthcare, and financial services sectors use the company’s products and services.
The Commvault Data Platform, a unified platform for data security, management, and governance, is our flagship offering. Commvault Data Platform safeguards hybrid, cloud, and on-premises data. Included are data replication, compression, and deduplication.
Among the many goods and services provided by Commvault is the Data Platform:
Commvault HyperScale data security and management devices. A solution for disaster recovery Cloud, hybrid, and on-premises data are all protected by Commvault Orchestrate.
Activate Commvault: Analyze data to gain insights.
Commvault products are adopted and managed by organizations with the use of consulting experience.
Commvault is the industry leader in data management and security software. Its solutions and services are used by businesses of all sizes to safeguard their data against loss, corruption, and illegal access.
#Commvaul#postquantumcryptography#cyberthreats#quantumcomputing#quantummechanics#News#Technews#Technology#Technolgynews#Technologytrends#Govindhtech
0 notes
Text
Quantum-Secure Blockchain: Why Your Wallet Needs It NOW!

Blockchain networks implementing cryptographic methods to guard against quantum computing threats are referred to as Quantum-Secure Blockchain. Traditional blockchain networks utilize RSA (Rivest-Shamir-Adleman) and ECC (Elliptic Curve Cryptography) as their cryptographic mechanisms, but remain secure from classical computer attacks while remaining completely vulnerable to quantum-enabled Shor’s Algorithm.
Shor’s Algorithm demonstrates formidable capabilities in factorizing vast numbers as well as conducting discrete logarithm calculations, which undermine existing blockchain network protection mechanisms. The progressive development of quantum computers creates vulnerable cryptographic systems through broken encryption, preventing blockchain security and protected information from remaining secure.
Quantum-Secure Blockchain implements cryptography from the quantum-resistant category that delivers an entire blockchain defense against attacks from quantum computers. Quantum-Secure Blockchain implements cryptographic techniques that exhibit quantum resistance instead of conventional methods that quantum attacks can penetrate. Three quantum-resistant cryptographic methods include lattice-based cryptography, hash-based cryptography, and multivariate quadratic equations.
Lattice-based cryptography, for example, is based on the hardness of solving problems in high-dimensional spaces for the same reason that attacks conventional encryption, to which quantum computers don’t seem to be able to do in an uncomplicated manner. Hash-based cryptography is based on the hash function being secure, and multivariate quadratic equations involve mathematical computations that are difficult for quantum computers to solve efficiently.
Through the implementation of these innovative methods, quantum Secure Blockchain makes sure that even when the quantum computers have reached their fullest development, they won’t be able to breach the cryptographic security of the system.
The most important things about Quantum-Secure Blockchain are beyond the fact that it makes use of quantum-resistant algorithms. One of the key characteristics of Quantum-Secure Blockchain is that it employs bigger key sizes and more intricate mathematical bases than conventional blockchain systems. Quantum computers, which can perform enormous amounts of data in parallel, can take advantage of smaller key sizes and less complex mathematical issues much more efficiently than traditional computers.
Using bigger keys and more challenging mathematical hurdles, Quantum-Secure Blockchain keeps quantum computers at bay and ensures that neither can break into the encryption quite so readily. This additional layer of cryptographic strength makes Quantum-Secure Blockchain extremely resistant to attacks by quantum devices, protecting blockchain transactions and data in a fashion that ordinary cryptographical processes simply can’t match.
Another crucial aspect of Quantum-Secure Blockchain is that it employs post-quantum cryptography and forward secrecy protocols. Forward secrecy assures that even if one’s cryptographic key gets compromised in the future, historical communications and transactions are safe. This becomes particularly relevant in terms of quantum computers because quantum computers might decrypt archived data in the future.
Through applying post-quantum cryptography protocols, Quantum-Secure Blockchain can safeguard not only future data but even past data in a manner such that data placed on the blockchain is impenetrable even if today’s data were intercepted and broken at some later date. With proactive security, it pre-protects blockchain networks from the increasing capabilities of quantum computing.
The vision of Quantum-Secure Blockchain is to anticipate and pre-empt the security threat represented by quantum computers before this can materialize into a genuine danger. By implementing quantum-resistant cryptography now, Quantum-Secure Blockchain creates an essential layer of protection that resists sensitive information against the unforeseen capacity of quantum computers.
The continuous development of quantum computing poses a constantly changing threat to cybersecurity, but Quantum-Secure Blockchain is designed with foresight and ingenuity to remain ahead of the curve. It is not only concerned with the present situation of cryptographic attacks, but also thinking ahead to developing blockchain systems for the future when quantum computers can potentially decrypt conventional encryption algorithms with ease.
By tackling such challenges head-on, Quantum-Secure Blockchain enables blockchain technology as a secure and reliable platform for digital transactions despite the advent of quantum computing. The more superior and powerful that quantum computers will become, the more critical will be Quantum-Secure Blockchain.
Not only is it theoretically imperative to transition to quantum-secure encryption methods, but an urgent imperative, as the future of blockchain hangs in the balance of quantum defense against attack. Quantum-Secure Blockchain, with its robust cryptographic processes and innovative thinking, provides the security needed to maintain the integrity of blockchain systems against impending quantum attacks.
Quantum Computing vs. Blockchain: The Security Solution

The connection between blockchain and quantum computing is that of danger and potential boon. The stupendous amount of computational power available with quantum computing would completely upset blockchain technology by breaking the very cryptography algorithms underpinning it. Blockchain relies strongly on asymmetric cryptography, which, as secure against traditional computers as it currently is, would be vulnerable to the sophisticated algorithms quantum computers would employ, specifically Shor’s algorithm.
Such an algorithm can potentially factor large numbers quickly and accurately, undermining RSA and elliptic curve cryptography (ECC) that protects blockchain transactions today. But this weakens it yet. Quantum-Secure Blockchain is a promising resolution that can secure the guarantee of continued safety and reliability of blockchain against quantum threats.
Asymmetric cryptography stands as the core protection mechanism of blockchain security because public and private keys enable encryption and decryption functions. Traditional computers encounter great computational challenges when attempting to either factorize large numbers or determine discrete logarithms.
Quantum computers, which employ the principles of quantum mechanics, can accomplish this exponentially quicker, hence rendering current encryption outdated. This is where the real adversarial potential of blockchain and quantum computing comes into play. If quantum computers advance to a point, they can potentially undermine blockchain security by decrypting encrypted data and manipulating transactions, exposing blockchain networks to attack.
But Quantum-Secure Blockchain reverses this script. Instead of simply falling victim to the potential threat of quantum computing, Quantum-Secure Blockchain has been designed specifically to resist such future attacks. The cryptographic approach of Quantum-Secure Blockchain offers security by resisting all potential unauthorized access from quantum computers that might break standard encryption.
The secure quantum-resistant algorithms use mathematical challenges that quantum computers cannot easily resolve through three types of cryptography: lattice-based, hash-based signatures, and code-based. Through the incorporation of these new strategies, Quantum-Secure Blockchain allows blockchain systems to remain resolute, maintaining their fundamental purpose of offering secure, transparent, and decentralized transactions.
Transition to Quantum-Secure Blockchain is not an anticipatory measure, but it is unavoidable. Blockchain’s application of asymmetric cryptography is its weak point in the event of quantum computing. Existing cryptographic infrastructures might be sufficient to provide sufficient security against attacks based on classical computation, but they are no match for the brute force processing capability of quantum computers.
Quantum-Secure Blockchain has never been more necessary, since quantum computers continue to move closer to being powerful enough to decrypt the methods used to safeguard digital transactions for decades. Therefore, Quantum-Secure Blockchain is not merely a future upgrade to be done optionally; it is the new standard that blockchain networks will have to adopt to survive in the post-quantum era.
The quantum computing threat to making blockchain susceptible exists, but now with the emergence of Quantum-Secure Blockchain, there is a simple answer. Using proper cryptographic techniques, blockchain networks will be able to survive even in the quantum era. Developing and using Quantum-Secure Blockchain is needed to make sure blockchain networks will withstand the brunt of heavy quantum computing attacks looming on the horizon.
The ongoing expansion and deployment of blockchain across sectors like finance, healthcare, and government necessitate the level of vision that Quantum-Secure Blockchain provides. Besides averting quantum attacks from undermining data integrity, it also guarantees the long-term sustainability of blockchain technology in securing transactions and establishing trust within industries.
The development path of quantum computing requires quantum-secure blockchain to secure blockchain systems from threats generated by the emerging computational strength. The Quantum-Secure Blockchain solution shows how to create blockchain networks with modern quantum attacks prevention while maintaining complete security principles. With the advent of quantum-resistant algorithms, Quantum-Secure Blockchain guarantees that blockchain will continue to be the linchpin of secure digital transactions and is a primary solution to the problem of quantum computing.
Quantum-Secure Blockchain is not only a security measure for blockchain against quantum computing, but also charts the future of blockchain in itself. Global infrastructure growth of blockchain networks creates a stronger demand for Quantum-Secure Blockchain technologies.
The lack of Quantum-Secure Blockchain would make blockchain networks susceptible to quantum-based attacks, so that trust in decentralized systems would decrease. However, with Quantum-Secure Blockchain, blockchain can be designed to address the needs of a quantum-energy-rich world, such that its authenticity is guaranteed through the next century.
The emergence of quantum computing is a threat and a prospect to blockchain technology. Quantum computers are not only capable of deciphering the cryptographic methods used to protect blockchain transactions, but Quantum-Secure Blockchain presents a pre-emptive strike in proposing quantum-resistant encryption techniques. Asymmetric cryptography for blockchain is a vulnerability that needs to be eliminated, and blockchain security’s future rests on Quantum-Secure Blockchain.
The normal practice of the future will be Quantum-Secure Blockchain because it protects blockchain from quantum attacks while ensuring its operation during such potential threats. Through the implementation of Quantum-Secure Blockchain, organizations can protect blockchain technology as an essential secure digital transaction solution even after quantum computers become operational.
Why Quantum-Secure Blockchain is Essential for Crypto Survival

Cryptocurrency remains in an important stage of development because its global market value exceeds $2 trillion. The market has grown to an enormous size and adoption, but it also has enormous problems to solve. Of particular concern is the quantum threat. While traditional blockchains such as Bitcoin and Ethereum are secure against vanilla computers, they are not secure against quantum attacks by design.
As quantum computers are developing, they may be able to break through the cryptographic technologies that secure blockchains today. Unless something is done in advance, the prospects of cryptocurrencies become doubtful, and Quantum-Secure Blockchain...
#quantum-secure blockchain#blockchain security#post quantum secure blockchain#post quantum blockchain#blockchain technology#secure blockchain#post quantum cryptography#decentralized database#ncog#quantum resistant blockchain
1 note
·
View note
Text
“The idea of quantum computers cracking Bitcoin is still far off. Google’s Willow chip, with 105 qubits, is impressive, but lightyears away from the millions needed to challenge Bitcoin’s security. Think of qubits as the ‘power cores’ — the more you have, the more powerful the computer. Even if Willow’s qubits are ground-breaking and hold promise for addressing challenges like climate modelling and drug discovery, it’s not enough to break Bitcoin’s encryption,” observed Himanshu Maradiya, Chairman and Founder of CIFDAQ.
Obstacles like scaling and error correction remain. However, while the crypto world is building quantum-resistant solutions with the evolution of quantum technology, industries from finance to cybersecurity will need to adapt, ensuring that they are future-ready, he said.
www.cifdaq.com
0 notes