#network based firewall
Explore tagged Tumblr posts
Text
Enhancing SASE with Network Sandboxing: A Modern Cybersecurity Approach
In the rapidly evolving world of cybersecurity, businesses must adopt robust strategies to defend against increasingly sophisticated threats. One of the most comprehensive and modern approaches is Secure Access Service Edge (SASE), which combines wide area networking (WAN) with cloud-delivered security services. To further strengthen this architecture, integrating network sandboxing can provide…
#automated threat detection#business cybersecurity#Cloud-Based Security#Cybersecurity#Fiber Internet#firewall as a service#IT security#malware prevention#network sandbox#real-time security#SASE#secure web gateway#SolveForce#Threat Detection#Zero Trust#zero-day threats
0 notes
Text
#Accounting Software In Dubai#Best Accounting Software In UAE#IT Infrastructure Services In Dubai#IT Services In Dubai#Managed IT Service Providers In Dubai#IT Support Companies In Dubai#IT Networking Solutions Company Dubai#Access Control System Suppliers In Dubai#Firewall Installation Services In Dubai#Accounting Software For Small Business In Dubai#Best Accounting Software Solutions In Dubai#Best Accounting Software For Medium Business In Dubai#Cheap Accounting Software For Small Business In Dubai#Best Cloud Based Accounting Software In Dubai#Best Low Cost Accounting Software For Small Business In Dubai#Best Accounting Software For Small To Medium Business In Dubai#Best Business Accounting Software Services In Dubai#Best Software Company In Dubai#Web Designing Services In Dubai#Best SEO Services In Dubai#Top HRMS Software In Abu Dhabi#Best ERP Solution Provider UAE#Best Project Management Software In Dubai#Fitness and Gym Management Software In Dubai#MEP Contracting ERP Software In Dubai#Best ERP Software For Metal Fabrication Industry In Dubai
0 notes
Text
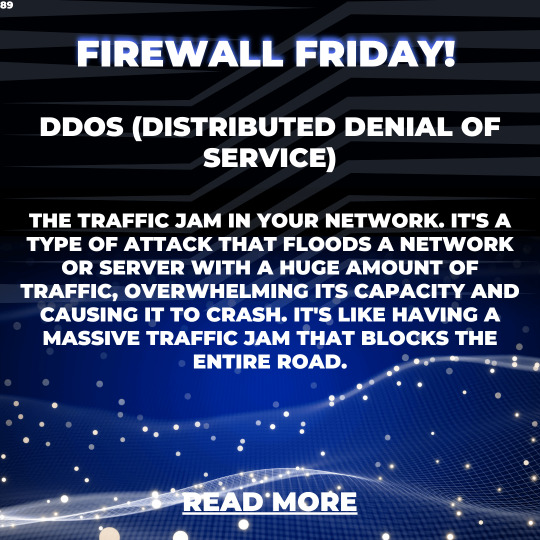
Firewall Friday: Defending Against DDoS Attacks - How to Keep Your Network Safe
Welcome to Firewall Friday, where we dive into the world of DDoS attacks and equip you with the knowledge to safeguard your network against these digital bullies. But don’t worry, we won’t let these troublemakers ruin our Friday vibes. Instead, we’ll tackle the topic with a humorous tone, using analogies and emojis to make it easy for even the most novice readers to understand. So, put on your…
View On WordPress
#anomaly detection#cloud-based defenses#cybersecurity#DDoS attacks#firewall#intrusion prevention systems#load balancing#network security#rate limiting#traffic analysis
0 notes
Text
İO-GAMES-2025 - DEVASA+

These browser-based multiplayer games have taken the online gaming community by storm, offering a unique blend of simplicity and competitiveness that appeals to players of all ages. Whether you're looking to battle against others in real-time or collaborate in a delightful, chaotic environment, IO games provide a thrilling escape from your daily routine. In this blog post, we'll explore various aspects of IO games, including how to access them without restrictions, the most popular titles in the genre, and tips for unlocking your gaming experience.
As the world of online gaming continues to evolve, the rise of io games has captured the attention of players around the globe, combining simple mechanics with highly addictive gameplay.
One of the best places to explore the exciting realm of io games unblocked is at https://io-games-2025.github.io/, where players can dive into a variety of thrilling and entertaining games without the hindrance of restrictions, making it an ideal site for those looking to enjoy the best of these experiences.
Whether you are an experienced gamer or a newcomer eager to join in on the fun, accessing io unblocked games provides a fantastic opportunity to enjoy seamless gaming without barriers, allowing for endless hours of enjoyment
İo Games
When discussing the evolution and popularity of online gaming, one cannot overlook the immense impact of io games, a genre that has captured the attention of millions across the globe through its simple yet engaging gameplay mechanics, which allow players to enter a world of competition and collaboration instantly.
The appeal of io games unblocked lies in their accessibility; players can often access these games from various locations, whether in a school setting or at home, without the restrictions typically imposed by firewalls, allowing for a seamless gaming experience that fosters both casual play and competitive spirit among friends and strangers alike.
Moreover, the concept of io unblocked games has revolutionized how gamers interact with one another, as these easily accessible online platforms enable innovation in game design, giving rise to diverse game modes, styles, and strategies that keep players engaged for hours on end.
İo Games Unblocked
In recent years, the popularity of io games has skyrocketed, captivating players across various age groups with their simplicity, engaging gameplay, and competitive nature, making them a staple in the online gaming community.
One of the most significant advantages of io games unblocked is that they provide players with the opportunity to enjoy these games anywhere, whether that be at home, school, or in a public space, without facing the frustrating restrictions typically set by network administrators.
Additionally, the availability of io unblocked versions means that gamers can easily access their favorite titles without worrying about pesky firewalls or filters, allowing them to dive into fun and challenging adventures on platforms that support unblocked content.
İo Unblocked
When it comes to enjoying the online gaming experience, io unblocked games have become a popular choice among players who seek both entertainment and accessibility, as they provide a vast array of engaging options that can be played directly in the browser without hefty downloads or installations.
The appeal of io games lies in their simplicity and competitive nature, allowing players to jump right into action, whether they're engaging in a thrilling battle royale, a strategic team-based game, or a unique multiplayer experience that keeps them coming back for more fun.
Many gamers, especially students or individuals in restricted environments, have turned to io games unblocked options to bypass limitations imposed by schools or workplaces, ensuring they can continue to enjoy their favorite gaming experiences
1K notes
·
View notes
Note
Hi Cyliph, can you tell something about Ar-Lo, he looks so interesting^^
I'm honored people like him :,)

[Potential small HDBS spoilers]]
Ar-Lo is old. Very old. Old enough to be considered somewhat of an cryptic figure among architects. He remembers a time when architects were not all One. Hundreds of thousands of years old. He was created as one of the first waves of expansion during a time when architects had just transferred to their biomechanical vessels. He's seen generations of vessels rise and fall out of use. One of the first ever born with no real parents or family or heritage.
A blank slate of an individual created to protect a colony world known as Juit-Eh from encroaching conflict (At least- that was the intention, the code recombination and manipulation technology was still new).
More below cut.
Who they were fighting, why, and for what has been lost to time. Ar-Lo himself remembers little of that bygone age and its politics. Its been lost to the network through information surges and wipes. What is known is that approximately 300,000 years ago Ar-Lo was functioning as a gladiator primarily based in Juit-Eh still. The indomitable vessel he used (barely modified-- not designed by him) was a real crowd pleaser to architects and non architects alike. It brought in loads of tourism-- and with it currency to the planet. The practice was considered too brutal by homeworld standards, and the end of his career was the annexation treaty that brought Juit-Eh back in to the protection of Oulinaean forces.
This annexation brought Juitian representation to the Tel Ju council. The representative brought a body guard with him, the most popular (former) gladiator known as Ar-Lo. The biggest 'fuck you' he could manage.
--
As it turns out, when you're primarily locked in the innermost sanctum of the most secure piece of architect territory you don't exactly get much valor. Not that Ar-Lo needed it. His pride was his strict loyalist views and sharp mind. He soon enough became versed enough in political talk that he could hold in own in any debate you threw at him. His trained body language and biolights (from years of existing as nothing but a background ornament) served him well in ensuring no other was able to get under his skin. His oratory skills only highlight his trained physical prowess and his rising influence on political matters made those in charge wary of him.
Ar-Lo proved his competency well enough that he was promoted over the course of years to supreme commander of the military. A scary job, and an isolating one. Not that it made a difference, by the time he reached the position anyone in networking distance already had a firewall up. He was already an unpleasant, paranoid, and a violent loyalist.
Though Ar-Lo had plans for every potential physical threat inside and out he was not prepared for the devastating plague that ripped through the architect colonies. Isolation barrier on isolation barrier proved useless, and with no cure in sight the council had to enact their most dire contingency plan. Ar-Lo was one such soul chosen to stay behind.
.
..
...

----
...
Cy fun facts:
Ar-lo was designed as the foil for Robin and Al-an in HDBS, he wasn't suppose to be likeable, but I'm grateful so many people want to know more about him. I cant reveal everything though.
He is brown because he needed to contrast the surrounding landscape, which was primarily green and dark turquoise.
Strange even among architects is that he does not experience dizzyness from vessel swapping no matter the size. Perhaps a remnant of his time as a gladiator, or maybe years of trained neural control.
Ar-lo might hold the record for oldest architect, especially post-kharaa.
His vessel is pretty standard bulky for guardsmen-- but he hasn't always used this vessel.
Before he became a political figure he was actually considered pretty handsome and likeable, like a celebrity. Even though his personality and skill didn't change.
He has never figured out how to properly integrate himself in architect society despite his age. This often leaves him frustrated and the only way he knows to take out that frustration is violence.
Ar-lo is only his current designation
Ar-lo likes art. Not realism, though. He likes art that makes you question things or appreciate the skill of the artist. The piece that represents him most closely is Josef Alber's Homage to the Square: Sentinel
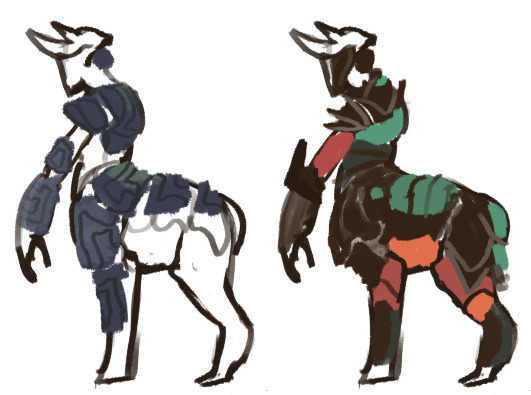
Armor - Oulinaean (homeworld - left) - Jutian house (right) His thick hide serves as natural armor, anything else is just decorative, shows heritage, or is multitool storage.
Playlist:
PRE-KHARAA Seether - Words As Weapons Psychodelic Prn Crumpets - Found God in a Tomato Radiohead - Nude Five Finger Death Punch - Remember Everything Seether - Country Song System Of A Down - Spiders Puddle of Mudd - Blurry POST-KHARAA Soul Survivor - ORDER TotalDeadCenter - The Forgotten Soldier Skaen - Grief, Aftermath Mother Mother - Sleep Awake Vessel - Red Sex (Re-Strung) Vivivivivi - Reduced to Guts Pogo - Undone <- His theme song!
#i fucking love music <3#feb 2 was his birthday btw :)#subnautica#sbz#subnautica below zero#ask#architect oc#worldbuilding#ar lo#its funny that people ask the most about ar lo when i can say the least about him of any of my characters ;u;#hdbs#hdbs spoilers
62 notes
·
View notes
Text
Hi! I'm Abigail. I write stories and games.
All of my work can be found on my website. Below there's a sampling of stories that are good places to begin.
I have a discord that's very friendly and I'm very responsive on it. I have a mailing list that goes out when I make new things.
I have an Ao3 account of fan fiction that is, at the moment, almost entirely dedicated to vampires from Baldur's Gate 3 being bad at communication. My most active story on it is currently: The Last Will and Testament of Cazador Szarr.
(Note--Cazador is dead and does not appear in the story.)

A visual novel game in development.
You are John Watson. You're very worried about your best friend, Sherlock Holmes. You're right to be worried. Left to his own devices, he'll destroy himself with overwork and cocaine. Don't let him do that.
Wishlist here.

I have a Patreon that is a new experiment. It is very low pressure Patreon. I inevitably, create things. I will put many of them there. If you are interested in subscribing, please think of it as supporting my ability to create in general rather than purchasing monthly entertainment.
If you are in any way financially vulnerable, please don't give me money. I am stable and safe. If you want access to the stories here but can't afford a subscription please message me and I'll give you a free subscription.
That is a general rule. If you can't afford anything I've created, please ask me for it and I'll give it to you.
Read things here.

A text-based videogame. Cost: $3.99
Open Sorcery follows the development of an Elemental Firewall: a fire elemental bound with C++ code to protect a network of people and places. You guide her as she makes decisions and grows. She can learn things, develop relationships, and even gain sapience. Or she can burn everything with fire.
Play on Steam.
Play on Android.
Play on iPhone.

A text-based fangame of BG3. Cost: Free.
Art by @cymk8
There's a monster made of dreams. It has its teeth in your companions. It builds nightmares out of their worst memories and drinks their pain. One of your companions has a very bad worst memory. A long, text-based video game.
Play online.

A text-based videogame. Cost: Free
You're a vampire hunter on your night off. You're getting a manicure, seeing a movie, and eating fast food.
But there's a vampire in this McDonalds. If you don't do something, then in one hour it will eat the cashier.
Play online.
68 notes
·
View notes
Text
McMurdo Internet
Internet service is supplied to Antarctica via a geostationary satellite. This far south, the satellite is only a few degrees above the horizon, and unfortunately for McMurdo, it's behind Mt Erebus. So the signal is beamed to a receiver on Black Island, about 20 miles away to the southwest, and bounced over to the sheltered alcove at the end of the Hut Point Peninsula where McMurdo sits.

The Chalet, administrative hub, with Black Island in the distance
The Black Island telecommunications infrastructure was installed in the 1980s, long before the internet we know and love today. It was upgraded in 2010 to allow more data transfer, mainly realtime weather data to feed into global forecast models. For this reason, it's probably the only place I've ever been where upload speed is remarkably faster than download speed – 60Mbps for outbound traffic, but only 20Mbps for inbound. Most regular internet use is receiving, not sending, so that's an entire base running on a connection that's only marginally faster than the average American smartphone. As you can imagine, this is somewhat limiting.
The limits to one's internet access actually begin before one even reaches the Ice. At the orientation in Christchurch, one is directed to a URL from which one must download and install a security programme from the U.S. government. It may feel like a hippie commune full of nerds, but McMurdo is an installation of the American state, and as such its computer network is a target of whatever disgruntled conspiracy theorist decides to hack The Man on any given day. Computers that are allowed onto this network (such as the one on which I am typing right now) have to have an approved firewall and antivirus service installed, then this extra programme on top of them. I am not sure what it does. For all I know the CIA is spying on me even now. (Hi, guys!) But you need to install it to get on the McMurdo Internet, such as it is, so I did.
To be honest, I was rather looking forward to a month cut off entirely from the hyperconnected world, so I was a tiny bit disappointed that quite a lot of day-to-day communication is done by email, and I would need to be on my computer a fair bit to get it. Had I known just how important email would be, I'd have installed an email client that actually downloads one's messages instead of just fetching them; as it was, the cycle of loading an email and sending the reply, even in Gmail's "HTML for slow connections" mode, took about five minutes, not counting the time it took to write. Tending one's email was a serious time commitment; sometimes I felt like I was spending more time on the computer in Antarctica than I did at home.

Crary scientists waiting, and waiting, and waiting
In a way, though, I was lucky, because I was technically a scientist and therefore had access to the one building on base with WiFi, the Crary Lab. And don't think you can just waltz into Crary with your laptop and poach the WiFi – in order to access it at all, you have to get set up by Crary IT with your own personal WiFi login. If you do not have Crary access, your portal to the Internet is one of a handful of ethernet cables in each of the dorm common rooms, or some public terminals in the main building. You can hop on, download your emails, maybe check the news or Google something you needed to look up, and then leave it for someone else. When most online time sinks are either blocked or too heavy to load, it’s amazing how little internet time you actually turn out to need.
Things that we have come to take for granted in The World are not a part of McMurdo life. Social media is pretty much out – the main platforms are bandwidth hogs even before you try to load a video or an animated GIF. There is no sharing of YouTube links, and no Netflix and chill. Someone was once sent home mid-season for trying to download a movie. Video calls with family and friends? Forget it. People do occasionally do video calls from Antarctica, often to media outlets or schools, but these have to be booked in advance so as to have the requisite bandwidth reserved. Jumping on FaceTime does not happen – not least because handheld devices have to be in airplane mode at all times for security reasons. Your phone might be secure enough for your internet banking, but not for US government internet!
It is, unavoidably, still a digital environment, it just gets by largely without internet access. Nearly everyone has an external hard drive, mostly for media that they've brought down to fill their off hours. If you want to share files you just swap hard drives, or hand over a memory stick. When the Antarctic Heritage Trust wanted some book material from me, I dropped it onto an SD card and ran it over to Scott Base on foot – a droll juxtaposition of high- and low-tech, not to mention a good excuse for a hike over The Gap on a beautiful day. It took half an hour, but was still faster than emailing it.
There is also a McMurdo Intranet, which includes a server for file sharing. Emailing someone your photos will take ages, but popping them into a folder on the I: drive and sending them a note to say you've done so (or, better yet, phoning them, or poking your head into their office) is much more efficient. To conserve space, this informal server partition is wiped every week, so you have to be quick about it, but it's an effective workaround, and also a good way to get relatively heavy resources to a large number of people in one go.
The telecommunications centre on Black Island is mostly automated, but like anything – perhaps more than some things, given the conditions – it needs to be maintained. There is a small hut out there for an equally small team of electricians and IT engineers; Black Island duty attracts the sort of person who might have been a lighthouse keeper back in the day.
Towards the end of my time on the Ice there was a spell where they needed to shut off the connection overnight, to do some necessary work. Given that most people's workdays extended at least to the shutoff time at 5:30 p.m., this meant essentially no internet for a large portion of the population, and some amusing flyers were posted up to notify everyone of the impending hardship.


Someday, faster, more accessible internet will come to Antarctica. It's more or less unavoidable, as communications technology improves, and everyone's work – especially the scientists' – depends more and more on having a broadband connection at all times. It will make a lot of things more convenient, and will make the long separation from friends and family much easier. But I'm pretty sure that many more people will mourn the upgrade than celebrate it. One can, theoretically, curtail one's internet use whenever one likes, but even before the pandemic it was almost impossible to live this way with the demands of modern life: I know from personal experience that opting out of Facebook alone can have a real detrimental effect on relationships, even with people one sees in the flesh fairly regularly, simply because everyone assumes that is how everyone else communicates. Being in a community where no one has access to assumed channels, and is more or less cut off from the rest of the world in a pocket universe of its own, levels the playing field and brings a certain unity. The planned (and, unarguably, necessary) updating of the physical infrastructure of McMurdo will wipe out a lot of the improvised, make-do-and-mend character of the place; how much would free and easy access to the online world change it in a less tangible way?
I'm sure the genuine Antarctic old-timers would shake their heads at the phone and email connections we have now, and say that no, this has already ruined Antarctica. It's not Antarctica unless your only link to the outside world is a dodgy radio. It's not Antarctica unless you only get mail once a year when the relief ship arrives. Doubtless the shiny new McMurdo will be seen as 'the good old days' by someone, someday, too. Change may happen slower there than elsewhere, but just like the rust on the tins at Cape Evans, it comes eventually, regardless.
For my own part, I'm glad I got to see 'old' McMurdo, such as it was, all plywood and cheap '90s prefab. The update will be much more efficient, and tidy, but yet another generation removed from the raw experience of the old explorers. My generation is probably the last to remember clearly what life was like before ubiquitous broadband; to some extent, Antarctica is a sort of time capsule of that world, just as the huts are a time capsule of Edwardian frontier life. I hope they'll find a way to hang on to the positive aspects of that.
Now, if you'll excuse me, I'm off to waste an hour mindlessly refreshing Twitter ...
If you'd like to learn more about the Black Island facility, there's a lot of good information (and some photos!) here: https://www.southpolestation.com/trivia/90s/blackisland.html
And this Antarctic Sunarticle goes into greater depth on the 2010 upgrade: https://antarcticsun.usap.gov/features/2114/
410 notes
·
View notes
Text
Malware Detected
the challenge was to write a short fic, ideally between 500-600 words, about an obscure Basgiath job that included a guest appearance by Silver and also Broccoli in a basket riding a gryphon.
it is not particularly safe for work due to the discussion of the sorts of web searches that create malware issues for your local IT department. no other content warnings. 554 words.
--
I waved at the scribe cadet watching the door as I stepped into the Archives for my workday. Fortunately it was one of the usual cadets, one who knew me and didn't ask questions about why a rider worked in the Archives.
I work in the Archives because that's where the servers are, and IT goes where the servers are.
On a good day, I log in and there's a few new tickets about password resets, maybe some new equipment in the healers quadrant that needs to get on the network, maybe a request to set up credentials for replacement staff.
On a bad day, well… today I logged in to see sixty nine new alerts, each helpfully letting me know there was MALWARE DETECTED.
"Nice," I mumbled out of habit, looking at the number, but it was not nice at all.
I pulled up the login history and started looking at the access logs to find the location. Oh, look, it was the riders quadrant. How shocking, by which I meant it was not shocking at all. There's a reason the riders have their own firewall, and it's not to hold back the dragonfire.
Let's narrow it down… not Panchek's office this time, not the library (thank Zihnal, malware on the public devices was easier to fix but harder to solve the problem), so I started narrowing down the dorm IPs until I found the right one and then I pulled up the website history in question.
Well, fuck, this was going to need some discretion. It was one of the new flier cadets' dorm, and it looked like he'd been searching for photos of their new favorite flier, that cat Broccoli riding in a basket on a gryphon, but their Navarran could use a little work. Instead of a cute kitten in flight goggles, the cadet managed to search for 'new pussy riding gryphon'.
I sent an email off to HR before settling in to wipe all of the malware the porn site had managed to spew onto our network and I was almost done when my phone rang.
"Basgiath IT," I answered, hitting the speakerphone button. Through my office window, I saw a scribe make a face at me, but if they didn't like it they should soundproof the damn office.
"I got your email," came the more-familiar-than-I'd-like voice of the local HR director. "I know I said I wanted to handle anything related to the fliers after the fight club riot-"
"And yet you're calling me, Major Silver, so I must have missed something."
"I just wanted to check… are you certain the flier was searching for… those search terms by accident?"
"Not at all," I answered cheerfully. "It's entirely possible he was genuinely looking for gryphon porn. But based on my experience with rider cadets and unfortunate searches about hemipenes, I find it's easier for everyone if we all pretend it was an accident."
"Hemi- oh dear." I could hear a soft thunk, presumably Major Silver letting her head hit the desk in frustration.
"You said the fliers were your problem, so enjoy your problem," I tried not to smile as I said it. "Let me know when you've talked to the flier and then I'll restore his computer."
"Of course," Major Silver sighed. "Have a good morning, Lieutenant."
10 notes
·
View notes
Text

House of Huawei by Eva Dou
A fascinating insight into a Chinese telecoms giant and its detractors
Huawei is not exactly a household name. If you’ve heard of it, you either follow the smartphone market closely – it is the main China-based manufacturer of high-end phones – or else consume a lot of news, because the company is at the centre of an ongoing US-China trade war.
But this enormous business is one of the world’s biggest producers of behind-the-scenes equipment that enables fibre broadband, 4G and 5G phone networks. Its hardware is inside communications systems across the world.
That has prompted alarm from US lawmakers of both parties, who accuse Huawei of acting as an agent for China’s government and using its technology for espionage. The company insists it merely complies with the local laws wherever it operates, just like its US rivals. Nevertheless, its equipment has been ripped out of infrastructure in the UK at the behest of the government, its execs and staffers have been arrested across the world, and it has been pilloried for its involvement in China’s oppression of Uyghur Muslims in Xinjiang.
Into this murky world of allegation and counter-allegation comes the veteran telecoms reporter Eva Dou. Her book chronicles the history of Huawei since its inception, as well as the lives of founder Ren Zhengfei and his family, starting with the dramatic 2019 arrest of his daughter Meng Wanzhou, Huawei’s chief financial officer, at the behest of US authorities.
Dou’s command of her subject is indisputable and her book is meticulous and determinedly even-handed. House of Huawei reveals much, but never speculates or grandstands – leaving that to the politicians of all stripes for whom hyperbole about Huawei comes more easily.
At its core, this book is the history of a large, successful business. That doesn’t mean it’s boring, though: there’s the story of efforts to haul 5G equipment above Everest base camp in order to broadcast the Beijing Olympics torch relay. We hear about the early efforts of Ren and his team, working around the clock in stiflingly hot offices, to make analogue telephone network switches capable of routing up to 10,000 calls; and gain insights into the near-impossible political dance a company must perform in order to operate worldwide without falling foul of the changing desires of China’s ruling Communist party.
Dou makes us better equipped to consider questions including: is this a regular company, or an extension of the Chinese state? How safe should other countries feel about using Huawei equipment? Is China’s exploitation of its technology sector really that different to the way the US authorities exploited Google, Facebook and others, as revealed by Edward Snowden?
Early in Huawei’s history, Ren appeared to give the game away in remarks to the then general secretary of the Communist party. “A country without its own program-controlled switches is like one without an army,” he argued, making the case for why the authorities should support his company’s growth. “Its software must be held in the hands of the Chinese government.”
But for each damning event, there is another that introduces doubt. The book reveals an arrangement from when Huawei operated in the UK that gave GCHQ unprecedented access to its source code and operations centre. US intelligence agencies seemed as able to exploit Huawei equipment for surveillance purposes as China’s. While Huawei’s equipment was certainly used to monitor Uyghur Muslims in Xinjiang, it was hardware from the US company Cisco that made China’s so-called Great Firewall possible.
Anyone hoping for definitive answers will not find them here, but the journey is far from wasted. The intricate reporting of Huawei, in all its ambiguity and complexity, sheds much light on the murky nature of modern geopolitics. The people who shout loudest about Huawei don’t know more than anyone else about it. Eva Dou does.
Daily inspiration. Discover more photos at Just for Books…?
12 notes
·
View notes
Note
What would happen if Alastor shared and accept Vox viewpoint of adaptation of time and advanced technology? Do you think you’ll become much stronger or just become very different but the same level!?
( This is a fun question! Alastor accepting new technology? Now there’s something to be curious about! ) (( Post edited and contributed to by balloondrifloon. ))
There are two ways this would go, and both have the same result.
Way one: Alastor would have accepted Vox’s offer to join the Vees. It would have either been a blatant yes or no, no in between. However, if Alastor said yes, then it’d be purely business.
He’d keep his friendship with Vox, so there would be that. But the Vees would only serve as a source of technological advancement for him.
Vox and Alastor would work together in creating new tech, but the advertisement of this new tech would be solely left up to Vox as Alastor’s interest in tech wouldn’t be monetary.
No, Alastor craves knowledge and power. He would contribute to the technological advances without participating in their intended uses. Like smartphones, for instance: He wouldn’t play on a smartphone, but instead, make smartphones fascinating enough to play on so he could spy on people through the phone cameras and microphones. He would spend his time gathering information to use against others when the time came.
Alastor’s true involvement in the Vees would be sinister. Outwardly, though, he would be a bubbly personality that Vox would happily show off to Hell as his partner in tech.
Way two: Alastor still rejects Vox’s offer. There’s no thought behind it other than not wanting to be owned by a company. He was an individual, after all. One that won’t easily go down as just another member of some organization. If he went down in history, he would want to go down as Alastor: The Radio Demon, not Alastor, that one member of the Vees.
If Alastor doesn’t join the Vees, he would have to put a lot more effort into staying on top of technology. However, Alastor is an insanely intelligent man and learning a new trick or two is definitely in his wheelhouse. He’d easily figure out coding and hardware design, with or without Vox’s help. Alastor’s technology wouldn’t be fun and entertainment-based like Vox’s tech is. It would be more focused, refined, and skilled at gathering intelligence. This could take any form that Alastor masters, such as hacking networks, spy systems, or even branching out into something uniquely his, like voodoo-infused weapons defense.
This would be available to the public but only in small quantities, because Alastor’s technology would still not be monetary focused. It would be considered an honor and privilege to own something Alastor designed, and people would literally kill each other for it. Owning weapons defenses, or spy systems, or being a part of his hacking networks would be seen as having a rare power. A sentiment Vox could never rival because his technology is commonplace.
Vox would have to fight to keep up with Alastor’s advancements. They’d constantly be toe-to-toe. Alastor’s would be creating software to hack into Vox’s defenses and gather data on both Vox’s audience and the Vees, while Vox would be in a constant state of upping his defenses to prevent that from happening. “Angelic Security” would never have been considered nor trusted seeing as hackers had a consistent window into Vox tech privacy and firewalls.
Vox, for the safety of his company, would attempt to put his rivalry aside and ask Alastor to join him on numerous occasions. These occasions would always be followed by rejection and another temper tantrum on Vox’s part.
In either situation, Alastor joining the Vees or not, Alastor would be the first to know anything that happens in Hell. You thought he was good at gathering intel to use to his advantage before? You’ve seen nothing yet. This would make it much, much worse. You wouldn’t be able to sneeze in your bathroom without Alastor knowing. Not a piece of information can get through Hell without being already known by Alastor.
Don’t call him Alastor. He prefers Al. It looked like “ai” and that amuses him.
You may think this is a lot of work for one individual, and you’d be right. Al can’t do it all by himself.
So he’d make himself an assistant.
His shadow would do just fine. He would infuse it with electricity and it would be able to jump into his tech and help with software design. Not only that, but it could easily travel through the wires and internet further work as Al’s eyes and ears on Hell.
Al doesn’t use a microphone. He’s got a headset looped around his neck at all times. The headset has little antlers and deer ears on it.
His attire is quite modern. Still spiffy, but modern-spiffy. He wears a red jacket that’s sleek, almost plastic-looking, and lacks tatters. It gives off a contemporary, digital appearance. Instead of his monocle, he wears smart sunglasses that have a HUD display from his point of view. The hoof-shaped soles of his shoes light up and change colors like RGB lights.
He’s really fun to look at.
Al would still attend the overlord meetings, however, he would seem far less interested, wanting to get back to what he was developing. He wouldn’t go in person, instead sending a hologram, so he could work while he listened to Carmilla talk.
Al wouldn’t have a radio tower. He’d have a recording studio with soundproof pads on the walls. Instead of using only radio, he would record digital audio, which he would make available live on his radio show, then later available on his website and other platforms as podcasts.
Al is a wifi hotspot. The hotel never lacks good wifi. People get so excited to see him because it means they finally have full bars in Hell’s naturally spotty connection. Vox’s wifi doesn’t reach everywhere, and where it does reach, it’s not exactly safe to use because Al’s hackers might be lurking, waiting for someone to connect.
Angel Dust would call him over to stand as near to him as he allows while he attempts to upload photos to Sinstagram.
Niffty wants him around while she streams her… ‘anime’… Al requests she wears headphones and keeps the screen from being tilted in his direction.
Charlie and Vaggie use him to keep up to date with the social media platforms Al advertises the hotel on.
Al runs the social media accounts for the hotel, even if they sometimes wished he didn’t. He might be technologically advanced, but he still doesn’t give a shit about what people think or say. His interest in social media is purely business and he has no fascination in it outside of keeping the hotel in the spotlight.
His influence would actually draw more people to the hotel, either as fans, or people who actually wonder if the hotel would work because someone as powerful and influential as him says it does.
He would monetize absolutely everything in social media that he could for the hotel’s budget, then leave the money at Charlie’s disposal.
Cannibal Colony takes a lot of influence from Al. Rosie does her best to keep the colony as tech free as she can, but she lets some things slip by if it means supporting her deer friend. That being said, they have an agreement that Al isn’t to bring new technology into the colony without Rosie’s approval.
Al’s voodoo power is still stronger than his tech power, but together, they’re a deadly combination. He infuses his voodoo into a lot of his tech, which is another reason his tech isn’t super mainstream. But, boy, does it pack a punch.
Al installs a soul detector at the hotel’s entrance without anyone knowing. It quite literally kicks any rejected souls away. Al decided one day that this included Lucifer. You can imagine the king’s surprise when a pixelated, hoof-cloven boot appeared out of the wall and punted him across the hotel’s front lawn.
Al’s prank was not appreciated.
Speaking of pranks, he’s constantly doing shit to ‘prank’ Hell. He never gives any context or ever comes out and says it was a prank, but you know he was fucking with you. Sometimes there’s not even proof he was, and it was simply a mind game. Pure entertainment for Al.
Like, for one example, Al dressed in blue all day long, only to act like everything was normal. He went outside and let people take photos of him. The next day, he’s back in his normal attire, and all photos of him have been altered overnight by his hacking systems and turned red. There is absolutely no proof he ever wore blue.
What? You saw it? No, you didn’t. He would never wear blue. Preposterous.
In conclusion, Alastor would be insanely powerful if he took advantage of technology. I guess we’re lucky he doesn’t.
#hazbin hotel#hazbin hotel alastor#hazbin hotel vox#hazbin hotel angel#hazbin hotel angel dust#hazbin hotel charlie#hazbin hotel vaggie#hazbin hotel niffty#hazbin hotel cannibal town#hazbin hotel rosie#hazbin hotel ask blog
29 notes
·
View notes
Text
“Follow the money” takes on a new meaning when the bloodhound is an algorithm-powered web crawling bot designed to drill through internal government firewalls and map out redundancy, waste, and longstanding hidden internal influence networks established over decades.
What am I talking about?
Algorithmic Corruption Mapping
To the best of my ability, I am describing a key part of the DOGE toolkit based on the fragments of information that have recently been made public. If I understand correctly, what has been developed is almost infinitely scalable and could be readily deployed by allied governments to root out corruption. DOGE appears to be engaged in a truly radical experiment in government spending transparency and accountability by applying modern information technology tools to a problem set long believed to be intractable.
We will probably learn more during the DOGE Super Bowl commercial airing soon.
But before we go further down this particular rabbit hole, please take a moment to listen to Mike Benz describe the USAID disinformation program:
5 notes
·
View notes
Text
Throttling Thursday: Botnet - The Menace Lurking in Your Network
Welcome to Throttling Thursday, where we unveil the hidden world of botnets and equip you with the knowledge to combat these digital troublemakers. But don’t worry, we won’t let these mischievous bots ruin our day. Instead, we’ll tackle the topic with a humorous tone, using analogies and emojis to make it easy for even the most novice readers to understand. So, fasten your seatbelts, put on your…
View On WordPress
#anti-malware software#behavior-based detection#botnet#collaboration against botnets#combat botnets#digital menace#firewall#network security#recognizing botnet signs#traffic analysis#vulnerability patches
0 notes
Text
Building Your Own Operating System: A Beginner’s Guide
An operating system (OS) is an essential component of computer systems, serving as an interface between hardware and software. It manages system resources, provides services to users and applications, and ensures efficient execution of processes. Without an OS, users would have to manually manage hardware resources, making computing impractical for everyday use.

Lightweight operating system for old laptops
Functions of an Operating System
Operating systems perform several crucial functions to maintain system stability and usability. These functions include:
1. Process Management
The OS allocates resources to processes and ensures fair execution while preventing conflicts. It employs algorithms like First-Come-First-Serve (FCFS), Round Robin, and Shortest Job Next (SJN) to optimize CPU utilization and maintain system responsiveness.
2. Memory Management
The OS tracks memory usage and prevents memory leaks by implementing techniques such as paging, segmentation, and virtual memory. These mechanisms enable multitasking and improve overall system performance.
3. File System Management
It provides mechanisms for reading, writing, and deleting files while maintaining security through permissions and access control. File systems such as NTFS, FAT32, and ext4 are widely used across different operating systems.
4. Device Management
The OS provides device drivers to facilitate interaction with hardware components like printers, keyboards, and network adapters. It ensures smooth data exchange and resource allocation for input/output (I/O) operations.
5. Security and Access Control
It enforces authentication, authorization, and encryption mechanisms to protect user data and system integrity. Modern OSs incorporate features like firewalls, anti-malware tools, and secure boot processes to prevent unauthorized access and cyber threats.
6. User Interface
CLI-based systems, such as Linux terminals, provide direct access to system commands, while GUI-based systems, such as Windows and macOS, offer intuitive navigation through icons and menus.
Types of Operating Systems
Operating systems come in various forms, each designed to cater to specific computing needs. Some common types include:
1. Batch Operating System
These systems were widely used in early computing environments for tasks like payroll processing and scientific computations.
2. Multi-User Operating System
It ensures fair resource allocation and prevents conflicts between users. Examples include UNIX and Windows Server.
3. Real-Time Operating System (RTOS)
RTOS is designed for time-sensitive applications, where processing must occur within strict deadlines. It is used in embedded systems, medical devices, and industrial automation. Examples include VxWorks and FreeRTOS.
4 Mobile Operating System
Mobile OSs are tailored for smartphones and tablets, offering touchscreen interfaces and app ecosystems.
5 Distributed Operating System
Distributed OS manages multiple computers as a single system, enabling resource sharing and parallel processing. It is used in cloud computing and supercomputing environments. Examples include Google’s Fuchsia and Amoeba.
Popular Operating Systems
Several operating systems dominate the computing landscape, each catering to specific user needs and hardware platforms.
1. Microsoft Windows
It is popular among home users, businesses, and gamers. Windows 10 and 11 are the latest versions, offering improved performance, security, and compatibility.
2. macOS
macOS is Apple’s proprietary OS designed for Mac computers. It provides a seamless experience with Apple hardware and software, featuring robust security and high-end multimedia capabilities.
3. Linux
Linux is an open-source OS favored by developers, system administrators, and security professionals. It offers various distributions, including Ubuntu, Fedora, and Debian, each catering to different user preferences.
4. Android
It is based on the Linux kernel and supports a vast ecosystem of applications.
5. iOS
iOS is Apple’s mobile OS, known for its smooth performance, security, and exclusive app ecosystem. It powers iPhones and iPads, offering seamless integration with other Apple devices.
Future of Operating Systems
The future of operating systems is shaped by emerging technologies such as artificial intelligence (AI), cloud computing, and edge computing. Some key trends include:
1. AI-Driven OS Enhancements
AI-powered features, such as voice assistants and predictive automation, are becoming integral to modern OSs. AI helps optimize performance, enhance security, and personalize user experiences.
2. Cloud-Based Operating Systems
Cloud OSs enable users to access applications and data remotely. Chrome OS is an example of a cloud-centric OS that relies on internet connectivity for most functions.
3. Edge Computing Integration
With the rise of IoT devices, edge computing is gaining importance. Future OSs will focus on decentralized computing, reducing latency and improving real-time processing.
4. Increased Focus on Security
Cyber threats continue to evolve, prompting OS developers to implement advanced security measures such as zero-trust architectures, multi-factor authentication, and blockchain-based security.
3 notes
·
View notes
Text
The headlines sounded dire: “China Will Use AI to Disrupt Elections in the US, South Korea and India, Microsoft Warns.” Another claimed, “China Is Using AI to Sow Disinformation and Stoke Discord Across Asia and the US.”
They were based on a report published earlier this month by Microsoft’s Threat Analysis Center which outlined how a Chinese disinformation campaign was now utilizing artificial technology to inflame divisions and disrupt elections in the US and around the world. The campaign, which has already targeted Taiwan’s elections, uses AI-generated audio and memes designed to grab user attention and boost engagement.
But what these headlines and Microsoft itself failed to adequately convey is that the Chinese-government-linked disinformation campaign, known as Spamouflage Dragon or Dragonbridge, has so far been virtually ineffective.
“I would describe China's disinformation campaigns as Russia 2014. As in, they're 10 years behind,” says Clint Watts, the general manager of Microsoft’s Threat Analysis Center. “They're trying lots of different things but their sophistication is still very weak.”
Over the past 24 months, the campaign has switched from pushing predominately pro-China content to more aggressively targeting US politics. While these efforts have been large-scale and across dozens of platforms, they have largely failed to have any real world impact. Still, experts warn that it can take just a single post being amplified by an influential account to change all of that.
“Spamouflage is like throwing spaghetti at the wall, and they are throwing a lot of spaghetti,” says Jack Stubbs, chief information officer at Graphika, a social media analysis company that was among the first to identify the Spamouflage campaign. “The volume and scale of this thing is huge. They're putting out multiple videos and cartoons every day, amplified across different platforms at a global scale. The vast majority of it, for the time being, appears to be something that doesn't stick, but that doesn't mean it won't stick in the future.”
Since at least 2017, Spamouflage has been ceaselessly spewing out content designed to disrupt major global events, including topics as diverse as the Hong Kong pro-democracy protests, the US presidential elections, and Israel and Gaza. Part of a wider multibillion-dollar influence campaign by the Chinese government, the campaign has used millions of accounts on dozens of internet platforms ranging from X and YouTube to more fringe platforms like Gab, where the campaign has been trying to push pro-China content. It’s also been among the first to adopt cutting-edge techniques such as AI-generated profile pictures.
Even with all of these investments, experts say the campaign has largely failed due to a number of factors including issues of cultural context, China’s online partition from the outside world via the Great Firewall, a lack of joined-up thinking between state media and the disinformation campaign, and the use of tactics designed for China’s own heavily controlled online environment.
“That's been the story of Spamouflage since 2017: They're massive, they're everywhere, and nobody looks at them except for researchers,” says Elise Thomas, a senior open source analyst at the Institute for Strategic Dialogue who has tracked the Spamouflage campaign for years.
“Most tweets receive either no engagement and very low numbers of views, or are only engaged with by other accounts which appear to be a part of the Spamouflage network,” Thomas wrote in a report for the Institute of Strategic Dialogue about the failed campaign in February.
Over the past five years, the researchers who have been tracking the campaign have watched as it attempted to change tactics, using video, automated voiceovers, and most recently the adoption of AI to create profile images and content designed to inflame existing divisions.
The adoption of AI technologies is also not necessarily an indicator that the campaign is becoming more sophisticated—just more efficient.
“The primary affordance of these Gen AI products is about efficiency and scaling,” says Stubbs. “It allows more of the same thing with fewer resources. It's cheaper and quicker, but we don't see it as a mark of sophistication. These products are actually incredibly easy to access. Anyone can do so with $5 on a credit card.”
The campaign has also taken place on virtually every social media platform, including Facebook, Reddit, TikTok, and YouTube. Over the years, major platforms have purged their systems of hundreds of thousands of accounts linked to the campaign, including last year when Meta took down what it called “the largest known cross-platform covert influence operation in the world.”
The US government has also sought to curb the effort. A year ago, the Department of Justice charged 34 officers of the Chinese Ministry of Public Security’s “912 Special Project Working Group” for their involvement in an influence campaign. While the DOJ did not explicitly link the arrests to Spamouflage, a source with knowledge of the event told WIRED that the campaign was “100 percent” Chinese state-sponsored. The source spoke on the condition of anonymity as they were not authorized to speak publicly about the information.
“A commercial actor would not be doing this,” says Thomas, who also believes the campaign is run by the Chinese government. “They are more innovative. They would have changed tactics, whereas it's not unusual for a government communications campaign to persist for a really long time despite being useless.”
For the past seven years, however, the content pushed by the Spamouflage campaign has lacked nuance and audience-specific content that successful nation-state disinformation campaigns from countries like Russia, Iran, and Turkey have included.
“They get the cultural context confused, which is why you'll see them make mistakes,” says Watts. “They're in the audience talking about things that don't make sense and the audience knows that, so they don't engage with the content. They leave Chinese characters sometimes in their posts.”
Part of this is the result of Chinese citizens being virtually blocked off from the outside world as a result of the Great Firewall, which allows the Chinese government to strictly control what its citizens see and share on the internet. This, experts say, makes it incredibly difficult for those running an influence operation to really grasp how to successfully manipulate audiences outside of China.
“They're having to adapt strategies that they might have used in closed and tightly controlled platforms like WeChat and Weibo, to operating on the open internet,” says Thomas. “So you can flood WeChat and Weibo with content if you want to if you are the Chinese government, whereas you can't really flood the open internet. It's kind of like trying to flood the sea.”
Stubbs agrees. “Their domestic information environment is not one that is real or authentic,” he says. “They are now being tasked with achieving influence and affecting operational strategic impact in a free and authentic information environment, which is just fundamentally a different place.”
Russian influence campaigns have also tended to coordinate across multiple layers of government spokespeople, state-run media, influencers, and bot accounts on social media. They all push the same message at the same time—something the Spamouflage operators don’t do. This was seen recently when the Russian disinformation apparatus was activated to sow division in the US around the Texas border crisis, boosting the extremist-led border convoy and calls for “civil war” on state media, influencer Telegram channels, and social media bots all at the same time.
“I think the biggest problem is [the Chinese campaign] doesn’t synchronize their efforts,” Watts said. “They’re just very linear on whatever their task is, whether it’s overt media or some sort of covert media. They’re doing it and they’re doing it at scale, but it’s not synchronized around their objectives because it’s a very top down effort.”
Some of the content produced by the campaign appeared to have a high number of likes and replies, but closer inspection revealed that those engagements came from other accounts in the Spamouflage network. “It was a network that was very insular, it was only engaging with itself,” says Thomas.
Watts does not believe China’s disinformation campaigns will have a material impact on the US election, but added that the situation “can change nearly instantaneously. If the right account stumbles onto [a post by a Chinese bot account] and gives it a voice, suddenly their volume will grow.”
This, Thomas says, has already happened.
A post, written on X by an account Thomas had been tracking that has since been suspended, referenced “MAGA 2024” in their bio. It shared a video from Russian state-run channel RT that alleged President Joe Biden and the CIA had sent a neo-Nazi to fight in Ukraine—a claim that has been debunked by investigative group Bellingcat. Like most Spamouflage posts, the video received little attention initially, but when it was shared by the account of school shooting conspiracist Alex Jones, who has more than 2.2 million followers on the platform, it quickly racked up hundreds of thousands of views.
“What is different about these MAGAflage accounts is that real people are looking at them, including Alex Jones. It’s the most bizarre tweet I’ve ever seen,” Thomas said.
Thomas says the account that was shared by Jones is different from typical Spamouflage accounts, because it was not spewing out automated content, but seeking to organically engage with other users in a way that made them appear to be a real person—reminiscent of what Russian accounts did in the lead-up to the 2016 election.
So far, Thomas says she has found just four of these accounts, which she has dubbed “MAGAflage,” but worries there may be a lot more operating under the radar that will be incredibly difficult to find without access to X’s backend.
“My concern is that they will start doing this, or potentially are already doing this, at a really significant scale,” Thomas said. “And if that is happening, then I think it will be very difficult to detect, particularly for external researchers. If they start doing it with new accounts that don't have those interesting connections to the Spamouflage network and if you then hypothetically lay on top of that, if they start using large language models to generate text with AI, I think we're in a lot of trouble.”
Stubbs says that Graphika has been tracking Spamouflage accounts that have been attempting to impersonate US voters since before the 2022 midterms, and hasn’t yet witnessed real success. And while he believes reporting on these efforts is important, he’s concerned that these high-profile campaigns could obscure the smaller ones.
"We are going to see increasing amounts of public discussion and reporting on campaigns like Spamouflage and Doppelganger from Russia, precisely because we already know about them,” says Stubbs. “Both those campaigns are examples of activity that is incredibly high scale, but also very easy to detect. [But] I am more concerned and more worried about the things we don't know."
9 notes
·
View notes
Text

Deep Dives into Tech and Digital Growth Strategies
In an era of rapid technological advancements and evolving business landscapes, understanding the nuances of tech-driven strategies is essential for sustained growth. Companies today must leverage cutting-edge technologies and innovative digital growth strategies to stay competitive. This article takes a deep dive into the world of technology and digital strategies, highlighting how businesses can harness them to achieve their full potential.
Tech Innovation: The Catalyst for Business Evolution
Innovation in technology is reshaping industries, from manufacturing and healthcare to retail and financial services. Businesses that embrace tech innovations can unlock new opportunities and create unique competitive advantages.
Automation and AI: Automation tools and artificial intelligence (AI) are driving efficiency, reducing human errors, and freeing up resources for more strategic tasks. Companies that adopt AI-driven decision-making processes gain valuable insights and predictive analytics.
Cloud Computing: Cloud-based solutions offer businesses scalable, cost-effective options for data storage and software deployment. Cloud technologies facilitate remote work, enhance collaboration, and provide data accessibility from any location.
Internet of Things (IoT): IoT is transforming industries by connecting devices and enabling real-time data collection and analysis. Businesses can leverage IoT to monitor operations, optimize workflows, and improve customer experiences.
5G Connectivity: The rollout of 5G networks is enabling faster communication and data transfer. This enhanced connectivity paves the way for innovations in areas like telemedicine, augmented reality, and autonomous vehicles.
Digital Marketing Strategies for Sustainable Growth
Digital marketing is at the heart of modern business strategies. To stand out in a crowded market, businesses must adopt targeted and innovative marketing tactics.
Search Engine Optimization (SEO): SEO is critical for improving online visibility and driving organic traffic. Businesses should focus on creating high-quality content, optimizing for keywords, and building authoritative backlinks to enhance search engine rankings.
Content Marketing: Content is king when it comes to building brand authority and engaging audiences. Businesses should invest in creating informative, relevant content that addresses customer pain points and provides solutions.
Social Media Engagement: Social media platforms are powerful tools for building brand awareness and fostering community engagement. Consistent posting, audience interaction, and strategic advertising can amplify a brand’s reach.
Data-Driven Marketing: Analyzing marketing performance data allows businesses to make informed decisions and refine strategies. By leveraging analytics tools, businesses can identify trends, understand customer behaviors, and optimize campaigns for better results.
Personalization: Today’s consumers expect personalized experiences. Businesses that use data to tailor their offerings and communication to individual preferences are more likely to build lasting relationships with customers.
Cybersecurity: Protecting Digital Assets
As businesses become more reliant on digital technologies, cybersecurity is paramount. Cyber threats can compromise sensitive data, disrupt operations, and damage reputations. To safeguard digital assets, businesses must implement robust cybersecurity measures.
Multi-Layered Security: Implementing multi-layered security protocols ensures that businesses are protected from various attack vectors. This includes firewalls, intrusion detection systems, and endpoint protection.
Data Encryption: Encrypting sensitive data both in transit and at rest protects it from unauthorized access.
Regular Audits: Conducting regular security audits helps identify vulnerabilities and ensures that security measures are up-to-date.
Employee Training: Human error is a common cause of data breaches. Educating employees on cybersecurity best practices can reduce the risk of phishing attacks and other social engineering tactics.
Customer-Centric Tech Solutions
Understanding and prioritizing customer needs is key to business growth. Tech innovations can enhance customer experiences and build long-term loyalty.
Customer Relationship Management (CRM) Systems: CRM systems help businesses manage customer interactions and provide personalized experiences. By analyzing customer data, businesses can tailor their offerings and improve satisfaction.
Chatbots and Virtual Assistants: AI-powered chatbots offer 24/7 customer support, answering queries and resolving issues in real-time. These tools enhance customer service while reducing operational costs.
Omnichannel Experiences: Today’s consumers interact with businesses across multiple channels. Providing a seamless, consistent experience across all touchpoints—whether online, in-store, or on mobile—is essential for customer satisfaction.
Tech Integration for Operational Efficiency
Integrating technology into core business processes can streamline operations, reduce costs, and improve overall efficiency.
Enterprise Resource Planning (ERP) Systems: ERP systems integrate various business functions into a unified platform, improving visibility and coordination across departments.
Project Management Tools: Digital project management platforms enable teams to collaborate, track progress, and meet deadlines efficiently.
Supply Chain Optimization: Advanced technologies like IoT and blockchain can enhance supply chain transparency, improve inventory management, and reduce delays.
Sustainable Growth with Tech Partnerships
Partnering with tech solution providers can accelerate business transformation and growth. Collaborating with experts allows businesses to access specialized knowledge and cutting-edge technologies without investing heavily in in-house resources.
Scalability: Tech partnerships enable businesses to scale operations as needed, adapting to market demands without significant disruptions.
Innovation: Partnering with tech innovators ensures that businesses stay ahead of industry trends and adopt new technologies as they emerge.
Looking Ahead: Future Trends in Tech and Digital Growth
The tech landscape is constantly evolving, and businesses must stay agile to remain competitive. Emerging trends like artificial intelligence, quantum computing, and edge computing are set to redefine industries. By staying informed and embracing change, businesses can position themselves for long-term success.
Conclusion
Tech4Biz Solutions is committed to empowering businesses with innovative tech solutions and digital growth strategies. Whether it’s leveraging advanced technologies, optimizing marketing efforts, or enhancing customer experiences, Tech4Biz helps businesses unlock new possibilities. By diving deep into the world of tech and digital strategies, companies can fuel growth, drive innovation, and stay ahead of the curve in an ever-changing business landscape. Visit Tech4Biz Solutions to learn more about how we can help transform your business.
5 notes
·
View notes
Text
Essential Cybersecurity Measures for Organizational Network Protection

In today's interconnected world, a robust cybersecurity strategy is no longer a luxury, but a necessity for organizations of all sizes. A strong defense against ever-evolving cyber threats is paramount to protecting sensitive data, maintaining business continuity, and preserving reputation. This blog explores critical cybersecurity organizational network protection measures.
Understanding the Threat Landscape
Before diving into protective measures, it's crucial to understand the threats organizations face. These include:
Malware: Viruses, ransomware, and spyware designed to damage or steal data.
Phishing: Deceptive emails or messages tricking individuals into revealing sensitive information.
Denial-of-Service (DoS) Attacks: Overwhelming networks with traffic, disrupting services.
Insider Threats: Malicious or accidental actions by employees or other insiders.
Data Breaches: Unauthorized access and exfiltration of sensitive data.
Essential Cybersecurity Measures
A layered approach is key to effective network protection. Here are some crucial measures:
Firewall Implementation: Firewalls act as a barrier between your network and the outside world, controlling incoming and outgoing traffic based on predefined rules. Regularly updating firewall rules is critical.
Intrusion Detection/Prevention Systems (IDS/IPS): These systems monitor network traffic for suspicious activity, alerting administrators to potential threats and even automatically blocking malicious traffic.
Antivirus and Anti-malware Software: Deploying robust antivirus and anti-malware software on all endpoints (computers, servers, mobile devices) is essential to detect and remove malicious software. Regular updates are crucial.
Strong Password Policies and Multi-Factor Authentication (MFA): Enforcing strong, unique passwords and implementing MFA adds an extra layer of security, making it significantly harder for attackers to gain access even if a password is compromised.
Regular Security Audits and Vulnerability Assessments: Regularly assessing your network for vulnerabilities and conducting security audits helps identify weaknesses before they can be exploited.
Employee Training and Awareness: Human error is a major factor in many security breaches. Regular cybersecurity awareness training for all employees is vital. This training should cover topics like phishing awareness, password security, and safe browsing practices.
Data Encryption: Encrypting sensitive data, both in transit and at rest, protects it even if a breach occurs.
Regular Backups and Disaster Recovery Planning: Regularly backing up critical data and having a disaster recovery plan in place ensures that you can recover from a cyberattack or other disaster.
Network Segmentation: Dividing your network into smaller, isolated segments limits the impact of a breach. If one segment is compromised, the others remain protected.
Incident Response Plan: Having a well-defined incident response plan in place allows you to react quickly and effectively to a security incident, minimizing damage and downtime.
Building a Cybersecurity Culture
Effective cybersecurity is not just about technology; it's also about people and processes. Building a strong cybersecurity culture within your organization is crucial. This involves:
Leadership Buy-in: Securing support from top management is essential for allocating resources and prioritizing cybersecurity.
Open Communication: Encouraging employees to report suspicious activity without fear of reprisal.
Continuous Improvement: Regularly reviewing and updating your cybersecurity policies and procedures to stay ahead of evolving threats.
Xaltius Academy's Cybersecurity Course: Your Partner in Network Protection
Navigating the complex world of cybersecurity can be challenging. Xaltius Academy's cybersecurity course provides comprehensive training and equips you with the knowledge and skills needed to protect your organization's network. Our expert instructors and hands-on labs will prepare you to effectively implement and manage these critical security measures. Invest in your cybersecurity future and safeguard your organization's valuable assets.
Conclusion
Protecting your organization's network requires a proactive and multi-faceted approach. By implementing these essential cybersecurity measures and fostering a strong security culture, you can significantly reduce your risk of falling victim to cyberattacks and safeguard your organization's future.
2 notes
·
View notes