#orm software
Explore tagged Tumblr posts
Text
0 notes
Text
Power of SaaS: How Cloud-Based Software is Revolutionizing the Way We Work
In today’s digital age, Software as a Service (SaaS) has become an essential tool for businesses of all sizes. With its high reach and scalability, SaaS has revolutionized the way we work, making it easier to access and manage software applications from anywhere, at any time. This cloud-based solution has not only increased efficiency but also reduced costs, making it an attractive option for entrepreneurs and business leaders.
“SaaS Benefits: What You Need to Know”
With SaaS, users can access a wide range of applications, from customer relationship management (CRM) to project management tools, all from a single platform. This centralized approach enables real-time collaboration, increased productivity, and improved decision-making.
But what about Online reputation management (ORM)? In today’s digital landscape, a company’s online reputation is crucial for building trust with customers and establishing credibility in the market. By leveraging SaaS solutions, businesses can monitor their online presence, respond to customer feedback, and maintain a positive reputation.
“Why SaaS is a Game-Changer for Business”
In conclusion, SaaS has transformed the way we work, offering a range of benefits that enhance productivity, collaboration, and customer engagement. By adopting SaaS solutions, businesses can improve their online reputation management, increase efficiency, and stay ahead of the competition.
1 note
·
View note
Text
New Trick – Organizing Prisma Models with the MERN Stack – Prisma #16
In this blog, we will explore “New Trick – Organizing Prisma Models with the MERN Stack”. Here, you will learn how to split and organize Prisma models, enums & types from the prisma.schema file into multiple files and import predefined data from JSON files. Let’s dive in and check it out:
#prisma#mongodb#reactjs#react#mern#mernstack#nosql#javascript#js#nodejs#npm#prismaorm#orm#database#redundancy#highavailability#replica#replicaset#developers#developer#software#softwaredeveloper#programming#programminglanguage#javascriptprogramming#advancedjavascript#techtrick#trick
0 notes
Text
Elevate your customer experience and boost your brand with Best Online Reputation Management (ORM) tools by Rannkly.
Unlock the power of Best Online Reputation Management Tools by using Rannkly's exclusive guide tothe finest ORM tools for businesses. Rannkly Provides Best Online Reputation Management Tools to enhance BusinessReputation and create custom review and feedback in a single dashboard.Easy to manage reviews,create social media postings, generate smart automated replies,and attract the right customer with your effective reviews.
Visit https://www.rannkly.com/ to know more.
0 notes
Text
What is the best ORM tool?
Discover top ORM tools to effectively manage your online reputation and enhance brand perception.
www.quickmetrix.com
#Best online reputation tool#Top ORM software#ORM tools for businesses#ORM solutions India#Online reputation management#ORM software comparison#India ORM service#Reputation monitoring tools#ORM agencies in India#Compare ORM platforms#Effective ORM strategies
0 notes
Note
I feel like I made a cursed loophole genie wish.
I was hoping there would be more Arthur/Orm (brother/brother) fic after the new Aquaman movie dropped. There is.
But... It is written almost entirely by Chinese fans. (I'm talking dozens of fics in an otherwise quiet tag.) I'm happy for those freaky little fans feeding each other with ship content. Just wish I could read what they're posting. 😅 (Yeah, translation software exists, but we all know how bad they come out.)
the monkeys paw granted your wish

24 notes
·
View notes
Text
How to Prevent

Preventing injection requires keeping data separate from commands and queries:
The preferred option is to use a safe API, which avoids using the interpreter entirely, provides a parameterized interface, or migrates to Object Relational Mapping Tools (ORMs). Note: Even when parameterized, stored procedures can still introduce SQL injection if PL/SQL or T-SQL concatenates queries and data or executes hostile data with EXECUTE IMMEDIATE or exec().
Use positive server-side input validation. This is not a complete defense as many applications require special characters, such as text areas or APIs for mobile applications.
For any residual dynamic queries, escape special characters using the specific escape syntax for that interpreter. (escaping technique) Note: SQL structures such as table names, column names, and so on cannot be escaped, and thus user-supplied structure names are dangerous. This is a common issue in report-writing software.
Use LIMIT and other SQL controls within queries to prevent mass disclosure of records in case of SQL injection.
bonus question: think about how query on the image above should look like? answer will be in the comment section
4 notes
·
View notes
Text
Protect Your Laravel APIs: Common Vulnerabilities and Fixes
API Vulnerabilities in Laravel: What You Need to Know
As web applications evolve, securing APIs becomes a critical aspect of overall cybersecurity. Laravel, being one of the most popular PHP frameworks, provides many features to help developers create robust APIs. However, like any software, APIs in Laravel are susceptible to certain vulnerabilities that can leave your system open to attack.

In this blog post, we’ll explore common API vulnerabilities in Laravel and how you can address them, using practical coding examples. Additionally, we’ll introduce our free Website Security Scanner tool, which can help you assess and protect your web applications.
Common API Vulnerabilities in Laravel
Laravel APIs, like any other API, can suffer from common security vulnerabilities if not properly secured. Some of these vulnerabilities include:
>> SQL Injection SQL injection attacks occur when an attacker is able to manipulate an SQL query to execute arbitrary code. If a Laravel API fails to properly sanitize user inputs, this type of vulnerability can be exploited.
Example Vulnerability:
$user = DB::select("SELECT * FROM users WHERE username = '" . $request->input('username') . "'");
Solution: Laravel’s query builder automatically escapes parameters, preventing SQL injection. Use the query builder or Eloquent ORM like this:
$user = DB::table('users')->where('username', $request->input('username'))->first();
>> Cross-Site Scripting (XSS) XSS attacks happen when an attacker injects malicious scripts into web pages, which can then be executed in the browser of a user who views the page.
Example Vulnerability:
return response()->json(['message' => $request->input('message')]);
Solution: Always sanitize user input and escape any dynamic content. Laravel provides built-in XSS protection by escaping data before rendering it in views:
return response()->json(['message' => e($request->input('message'))]);
>> Improper Authentication and Authorization Without proper authentication, unauthorized users may gain access to sensitive data. Similarly, improper authorization can allow unauthorized users to perform actions they shouldn't be able to.
Example Vulnerability:
Route::post('update-profile', 'UserController@updateProfile');
Solution: Always use Laravel’s built-in authentication middleware to protect sensitive routes:
Route::middleware('auth:api')->post('update-profile', 'UserController@updateProfile');
>> Insecure API Endpoints Exposing too many endpoints or sensitive data can create a security risk. It’s important to limit access to API routes and use proper HTTP methods for each action.
Example Vulnerability:
Route::get('user-details', 'UserController@getUserDetails');
Solution: Restrict sensitive routes to authenticated users and use proper HTTP methods like GET, POST, PUT, and DELETE:
Route::middleware('auth:api')->get('user-details', 'UserController@getUserDetails');
How to Use Our Free Website Security Checker Tool
If you're unsure about the security posture of your Laravel API or any other web application, we offer a free Website Security Checker tool. This tool allows you to perform an automatic security scan on your website to detect vulnerabilities, including API security flaws.
Step 1: Visit our free Website Security Checker at https://free.pentesttesting.com. Step 2: Enter your website URL and click "Start Test". Step 3: Review the comprehensive vulnerability assessment report to identify areas that need attention.
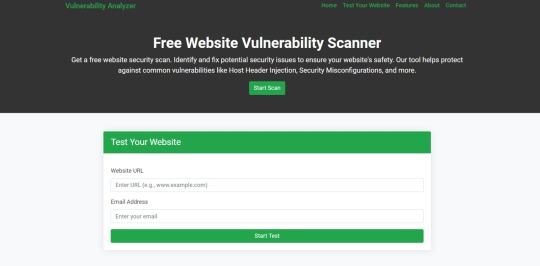
Screenshot of the free tools webpage where you can access security assessment tools.
Example Report: Vulnerability Assessment
Once the scan is completed, you'll receive a detailed report that highlights any vulnerabilities, such as SQL injection risks, XSS vulnerabilities, and issues with authentication. This will help you take immediate action to secure your API endpoints.
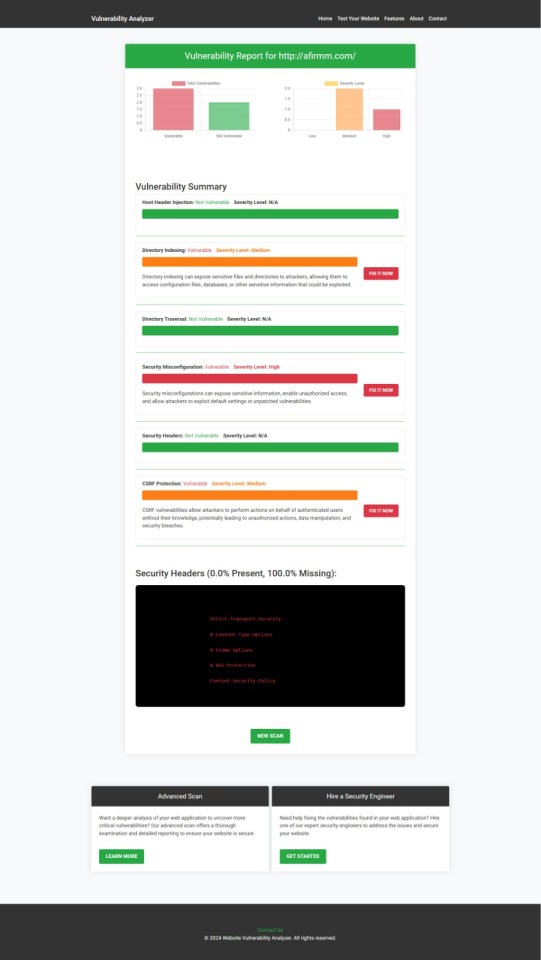
An example of a vulnerability assessment report generated with our free tool provides insights into possible vulnerabilities.
Conclusion: Strengthen Your API Security Today
API vulnerabilities in Laravel are common, but with the right precautions and coding practices, you can protect your web application. Make sure to always sanitize user input, implement strong authentication mechanisms, and use proper route protection. Additionally, take advantage of our tool to check Website vulnerability to ensure your Laravel APIs remain secure.
For more information on securing your Laravel applications try our Website Security Checker.
#cyber security#cybersecurity#data security#pentesting#security#the security breach show#laravel#php#api
2 notes
·
View notes
Text
Boosting Brand Image: Effective Online Reputation Management Tactics
In today’s virtual age, an individual's or corporation’s reputation may be made or marred in moments. Online reputation management (ORM) has emerged as a critical method to shape public perceptions, safeguard credibility, and maintain a favorable image within the virtual area. This guide dives deep into the concept of ORM, its significance, techniques, equipment, and best practices.

What is Online Reputation Management?
Online Reputation Management (ORM) is the process of monitoring and influencing how your business or brand is perceived online. It involves a variety of strategies to neutralize negative sentiments and promote positive ones, ultimately shaping the online conversation around your brand.
ORM combines public relations, digital marketing, and SEO (search engine optimization) strategies to preserve or improve a good online presence.
Why is ORM Important?
First Impressions Matter
A majority of humans now turn to the net before making choices. Whether it’s a product purchase, task software, or partnership, online data regularly forms the first effect.
Impact on Business Success
Businesses thrive on acceptance as true. Positive critiques, excessive ratings, and clean online recognition can extensively grow customer acquisition and retention quotes.
Career Advancement
For people, especially specialists and public figures, an online reputation can make or wreck professional possibilities. Recruiters and employers regularly evaluate applicants' online presence before hiring.
Crisis Management
In the digital global, statistics spread unexpectedly. A single negative incident can spiral right into a complete-blown disaster if now not controlled effectively. ORM mitigates such risks and forestalls long-term damage.
Building Credibility
Strong online recognition reinforces trust among stakeholders, whether they’re clients, customers, or followers. Transparency and responsiveness are regularly visible as markers of reliability.
Key Components of Online Reputation Management
Monitoring
Constantly song online mentions opinions, and discussions about your brand or call.
Tools like Google Alerts, Mention, and Hootsuite can automate this manner.
Regular audits of search results, social media platforms, and evaluation websites provide valuable insights.
Engagement
Respond to both wonderful and terrible comments directly and professionally.
Show appreciation for compliments and address court cases with answers.
Engaging with the target audience fosters loyalty and acceptance as true.
Content Management
Publish amazing, high-quality content material to dominate search engine consequences.
Maintain energetic blogs, social media money owed, and websites with up-to-date information.
Address inaccuracies or outdated content material promptly.
Review Management
Encourage glad customers to go away with fantastic critiques.
Address poor critiques constructively and in a well-mannered way.
Use structures like Yelp, Google My Business, and Trustpilot to collect and showcase comments.
Crisis Management
Have a clear action plan to address surprising reputation challenges.
Transparency, responsibility, and swift responses are essential in managing crises.
Employ expert PR or ORM offerings for complicated conditions.
Effective Strategies for ORM
Proactive Approach
Don’t anticipate troubles to get up; continually nurture a fantastic online presence.
Build a strong foundation of favorable content material and interactions.
Search engine marketing for Reputation Management
Optimize fine content with applicable keywords to improve visibility in seeking consequences.
Push down bad content material by using developing greater excessive-ranking, tremendous pages.
Leverage Social Media
Use systems like Twitter, LinkedIn, Instagram, and Facebook to interact together with your target market and percentage updates.
Monitor social media mentions and cope with issues in real time.
Transparency and Authenticity
Be sincere and prematurely in all communications.
Acknowledge errors and take duty whilst necessary.
Soliciting Feedback
Actively request evaluations and testimonials from satisfied clients.
Use surveys to apprehend and enhance regions of dissatisfaction.
Professional ORM Services
Consider hiring specialists if dealing with popularity becomes overwhelming.
Agencies focus on restoring and retaining a positive online image.
Tools for Online Reputation Management
Google Alerts
Free tool for monitoring mentions of keywords related to your logo or name.
Hootsuite
Social media management device that tracks mentions and schedules posts.
ReviewTrackers
Helps collect and examine consumer critiques from a couple of structures.
SEMrush
SEO device for monitoring keyword performance and optimizing content material visibility.
Reputation.Com
Comprehensive ORM platform for organizations.
Yext
Helps control commercial enterprise listings and online opinions.
BuzzSumo
Identifies trending content and mentions to apprehend public sentiment.
Case Studies: ORM in Action
Corporate Example:
A well-known airline confronted backlash due to negative customer service captured on video. By apologizing publicly, compensating the purchaser, and enhancing its policies, the airline managed to rebuild its recognition through the years.
Individual Example:
A public parent received negative press over an arguable statement. By issuing a heartfelt apology, undertaking network paintings, and specializing in wonderful initiatives, they gradually shifted public notion.
Best Practices for Online Reputation Management
Stay Vigilant
Regularly screen your online presence to cope with troubles right away.
Be Responsive
Engage along with your audience and address comments constructively.
Focus on Value Creation
Share content that educates, entertains or conjures up your audience.
Maintain Consistency
Ensure messaging aligns with your logo values throughout all systems.
Learn from Mistakes
View complaints as an opportunity for growth and development.
Build Strong Relationships
Cultivate authentic connections with clients, employees, and stakeholders.
Challenges in ORM
Fake Reviews and Trolls
Managing fabricated critiques or malicious feedback calls for careful handling to keep away from escalation.
Rapid Information Spread
Negative incidents can cross viral, necessitating rapid and powerful responses.
High Expectations
Customers count on instant responses, which may strain resources.
Complex Algorithms
Navigating seek engine algorithms and social media guidelines needs expertise.
Future of Online Reputation Management
The importance of ORM will grow because the net will become increasingly vital to regular lifestyles. Key tendencies include:
AI and Automation: Enhanced equipment for monitoring and sentiment analysis.
Video Content: Growing significance of handling video content on systems like YouTube and TikTok.
Personal Branding: Individuals more and more making an investment in expert ORM offerings.
Ethical Considerations: Greater emphasis on authenticity and moral practices.
3 notes
·
View notes
Text
Clones and Features
A back-end programmer who is fluent in his programming language of choice, database/ORM, web framework, plain HTML or whatever CSS template, javascript library, or front-end framework, can probably write his own simplified version of Reddit, Twitter, Instagram, Wordpress, or StackOverflow over one weekend.
If it doesn't need to scale past five users or the proof-of-concept stage, our programmer could even write his own little live streaming or video sharing site.
Of course, if you wanted to approximate the features of the real Tumblr, of Reddit, of StackOverflow, it would take you years, and writing a bare-bones version that could actually scale to serve thousands of users could take you a month, not a week-end.
This matters less than you might think. You can attract early users because you wrote a bare-bones clone of something else. You can attract contributors because the code base is small and easy to understand. You can attract people who want to shape the feel and the tone of a new community. You can attract users who want something small that doesn't eat their RAM.
These people are early adopters not because they know what will later become popular, but because they like using software that is new, or joining communities that are small. A major driver of the adoption of mastodon in 2017 wasn't that Mastodon wasn't Twitter, or that Mastodon was better than twitter, but that the Fediverse is smaller than Twitter. It's not novelty. It's the cosy feeling of a small community.
The main problem of writing your own YouTube clone is not how you scale video storage and delivery to millions of users. The problem is managing your community as it grows to a thousand. The problem is how you retain the first couple dozens of knowledgeable answerers who joined precisely because your Q&A site wasn't StackOverflow. The problem is deciding whether you need cash-tags, or if feature parity with Twitter isn't really worth it.
11 notes
·
View notes
Text
#social listening#social listening tools#orm tools#online response management tools#online reputation management tools#orm software
0 notes
Text
Top Tools and Technologies Every Full Stack Java Developer Should Know
In today's fast-paced software development landscape, Full Stack Java Developers are in high demand. Companies seek professionals who can work across both the frontend and backend, manage databases, and understand deployment processes. Whether you're just starting your career or planning to upskill, mastering the right set of tools and technologies is key.
If you're considering a full stack java training in KPHB, this guide will help you understand the essential technologies and tools you should focus on to become industry-ready.

1. Java and Spring Framework
The foundation of full stack Java development starts with a deep understanding of Core Java and object-oriented programming concepts. Once you’ve nailed the basics, move to:
Spring Core
Spring Boot – simplifies microservices development.
Spring MVC – for building web applications.
Spring Security – for handling authentication and authorization.
Spring Data JPA – for database operations.
Spring Boot is the most widely adopted framework for backend development in enterprise applications.
2. Frontend Technologies
A full stack Java developer must be proficient in creating responsive and interactive UIs. Core frontend technologies include:
HTML5 / CSS3 / JavaScript
Bootstrap – for responsive designs.
React.js or Angular – for building dynamic SPAs (Single Page Applications).
TypeScript – especially useful when working with Angular.
3. Database Management
You’ll need to work with both relational and non-relational databases:
MySQL / PostgreSQL – popular SQL databases.
MongoDB – a widely used NoSQL database.
Hibernate ORM – simplifies database interaction in Java.
4. Version Control and Collaboration
Version control systems are crucial for working in teams and managing code history:
Git – the most essential tool for source control.
GitHub / GitLab / Bitbucket – platforms for repository hosting and collaboration.
5. DevOps and Deployment Tools
Understanding basic DevOps is vital for modern full stack roles:
Docker – for containerizing applications.
Jenkins – for continuous integration and delivery.
Maven / Gradle – for project build and dependency management.
AWS / Azure – cloud platforms for hosting full stack applications.
6. API Development and Testing
Full stack developers should know how to develop and consume APIs:
RESTful API – commonly used for client-server communication.
Postman – for testing APIs.
Swagger – for API documentation.
7. Unit Testing Frameworks
Testing is crucial for bug-free code. Key testing tools include:
JUnit – for unit testing Java code.
Mockito – for mocking dependencies in tests.
Selenium / Playwright – for automated UI testing.
8. Project Management and Communication
Agile and collaboration tools help manage tasks and teamwork:
JIRA / Trello – for task and sprint management.
Slack / Microsoft Teams – for communication.
Final Thoughts
Learning these tools and technologies can position you as a highly capable Full Stack Java Developer. If you're serious about a career in this field, structured learning can make all the difference.
Looking for expert-led Full Stack Java Training in KPHB? ✅ Get industry-ready with hands-on projects. ✅ Learn from experienced instructors. ✅ Job assistance and certification included.
👉 Visit our website to explore course details, check out FAQs, and kickstart your journey today!
0 notes
Text
Best Way – MongoDB Replica Set for Prisma Queries Running – Prisma #15
In this blog, we will explore how to resolve the issue of “MongoDB Replica Set for Prisma queries running”. This error commonly occurs after setting up MongoDB in Prisma ORM and running database queries. Let’s dive in and check it out now
#prisma#mongodb#reactjs#react#mern#mernstack#nosql#javascript#js#nodejs#npm#prismaorm#orm#database#redundancy#highavailability#replica#replicaset#developers#developer#software#softwaredeveloper#programming#programminglanguage#javascriptprogramming#advancedjavascript
0 notes
Text
Advanced Java Training: Become a Skilled Java Developer with Softcrayons Tech Solution
Advanced Java training | Advance java training course | Java training institute
Looking to improve your programming skills and create a strong basis in the software development industry? Enroll in Advanced java training with Softcrayons Tech Solution, a top IT training institution in Noida, Ghaziabad, and Delhi NCR. Our expert-designed course goes beyond the fundamentals and delves deep into enterprise-level Java technology, preparing you for in-demand Java development positions. Whether you are a student pursuing a career in software engineering, a working professional looking for progress, or someone hoping to transfer into backend programming, this advanced java training program is your ticket to success.

Why Choose Advanced Java Training?
Java is one of the most powerful and widely-used programming languages in the world. It’s the backbone of countless enterprise applications, web platforms, Android apps, and software systems. However, basic knowledge of Java is not enough to compete in today’s job market. Employers now look for developers with a comprehensive understanding of Advanced Java—including Servlets, JSP, JDBC, and frameworks like Spring and Hibernate. Our Advanced Java training course is specifically structured to provide deep knowledge and hands-on experience with real-world projects. This ensures you not only learn the theory but also apply it practically—just like you would in a professional Java development environment.
Course Highlights: What You Will Learn
Our Advanced Java training program is tailored to meet the current industry standards. Here’s what you will master in our course:
1. Java Database Connectivity (JDBC)
Learn how to connect Java applications with databases using JDBC. This includes CRUD operations, transaction management, and SQL optimization techniques.
2. Servlets and JavaServer Pages (JSP)
Understand the power of Servlets and JSP in building dynamic web applications. Create interactive web pages, manage sessions, and handle form data with precision.
3. MVC Architecture
Get in-depth knowledge of Model-View-Controller design patterns and how they help organize web applications more efficiently.
4. Spring Framework
Master Spring Core, Spring Boot, and dependency injection. Learn how to build scalable, secure, and robust applications with minimal code.
5. Hibernate ORM
Work with Hibernate for object-relational mapping. Learn how to persist Java objects into relational databases with ease and efficiency.
6. RESTful Web Services
Learn to build REST APIs that are scalable and efficient using Spring MVC and Spring Boot.
7. Version Control with Git
Understand the basics of Git for managing and tracking your code during project development.
8. Real-Time Projects
Apply your skills through hands-on projects that simulate real-world challenges and give you a portfolio to show employers.
Why Softcrayons Tech Solution?
Choosing the right training institute is as important as choosing the right career path. Softcrayons Tech Solution is one of the most trusted names for Advanced Java training in Noida, Ghaziabad, and Delhi NCR. Here’s why thousands of students and professionals prefer us:
Experienced Faculty
Our trainers are Java experts with over a decade of industry experience in companies like TCS, Infosys, Wipro, and HCL.
Updated Curriculum
Our syllabus is regularly updated to reflect the latest trends in Java development and enterprise software engineering.
Placement Assistance
We provide full support in resume building, mock interviews, and job placement. Our strong tie-ups with top IT companies help you land your dream job faster.
Flexible Learning Modes
Choose from classroom sessions, online batches, or weekend classes according to your convenience.
Affordable Pricing
Get industry-standard training without breaking your budget. Easy EMI options are available for all major courses.
Who Should Enroll?
This Advanced Java course is ideal for:
B.Tech/BCA/MCA students
Working software professionals
Freelancers and web developers
Anyone with basic Java knowledge aiming to upgrade their skills
Whether you're a fresher looking for your first job or an experienced coder aiming for a promotion, this course provides the tools and confidence you need to advance in your career.
Career Opportunities After Advanced Java Training
Once you complete the Advanced Java Training at Softcrayons, you'll be qualified for high-paying roles in the tech industry. Here are some of the job profiles you can target:
Java Backend Developer
Full Stack Java Developer
Software Engineer
Java Architect
Web Application Developer
Spring Boot Developer
REST API Developer
Android App Developer (using Java)
Tools and Technologies Covered
Java 8/11
Eclipse & IntelliJ IDE
MySQL / Oracle Database
Git & GitHub
Apache Tomcat
Maven / Gradle
Spring, Spring Boot
Hibernate ORM
REST APIs
JUnit & Testing Frameworks
Locations We Serve
Softcrayons offers top-rated Advanced Java training in Noida, Ghaziabad, and Delhi NCR. Our modern classrooms, experienced mentors, and state-of-the-art lab facilities make us a preferred training destination for tech aspirants across the region.
We also provide online training for students and professionals across India and abroad. So, no matter where you are, you can still benefit from our expert guidance.
Enroll Today and Accelerate Your Java Career!
Our Advanced java training course is more than just a certification; it’s a powerful career boost. With expert supervision, an industry-oriented curriculum, and hands-on practical experience, you’ll be fully equipped to tackle any challenge in the world of Java programming. Contact us
0 notes
Text
Working with Databases: SQLite and SQLAlchemy

Working with Databases: SQLite and SQLAlchemy is a crucial skill in modern application development, especially in data-driven projects. SQLite is a lightweight, serverless, self-contained SQL database engine widely used in mobile apps, desktop software, and small to medium-sized web applications. It requires minimal setup and offers excellent performance for local storage needs.
SQLAlchemy, on the other hand, is a powerful Python ORM (Object Relational Mapper) that allows developers to interact with databases using Pythonic code instead of raw SQL. It supports both high-level ORM queries and low-level SQL expressions, making it a preferred choice for scalable and maintainable applications.
Using SQLAlchemy with SQLite allows for seamless database integration, automatic table creation, and efficient data manipulation. Developers can benefit from features like data model abstraction, query optimization, and easy migration handling. This combination is ideal for beginners and professionals alike who are building Python-based backend systems, APIs, or full-stack applications.
0 notes
Text
The Ultimate Guide to Hiring Django Developers in 2025
If you’re building a scalable, secure, and high-performing web application in 2025, Django remains one of the best frameworks to use. But to unlock its full potential, you need to hire Django developers who understand how to use this Python-based framework to meet your business goals.

Why Choose Django in 2025?
Django is still a top choice for web development in 2025 due to:
Rapid Development: Built-in admin panel, ORM, and modular architecture
Scalability: Used by companies like Instagram, Spotify, and NASA
Security: Protection against XSS, CSRF, and SQL injections
Community Support: A mature and well-documented ecosystem
When Should You Hire a Django Developer?
You should hire Django developers if:
You need to build a custom web application or CMS
You’re planning a secure eCommerce site
You require API development for mobile/web apps
You want a high-performance MVP or startup product
You need a secure backend for SaaS or enterprise software
Key Skills to Look For
Before hiring, make sure the Django developer is skilled in:
Python programming
Django framework (ORM, views, forms, templates)
REST APIs (DRF — Django REST Framework)
Front-end integration (HTML, CSS, JavaScript, React/Angular)
Database systems (PostgreSQL, MySQL, SQLite)
Version control (Git)
Deployment (Docker, AWS, CI/CD)
Hiring Options: Freelancer vs Agency
Option Pros ConsFreelancer Cost-effective, flexible Limited availability, may lack team supportAgency (like Oodles)Scalable, full-stack team, support & QASlightly higher cost
If you want a full-cycle development solution with guaranteed timelines and post-launch support, hiring through an agency is ideal.
Interview Questions to Ask
Here are a few practical questions you can ask during the interview:
What’s the difference between a Django model and a Django form?
How would you handle user authentication in Django?
Explain the role of middleware in Django.
What are signals in Django and when should you use them?
How do you optimize Django for performance?
How Much Does It Cost to Hire Django Developers in 2025?
Freelancers: $20 — $60/hour (based on location & experience)
Agencies: $25 — $100/hour (comes with project managers, QA, and design support)
Dedicated Developer (Full-Time): $2000 — $6000/month
Outsourcing to countries like India gives you access to highly skilled developers at lower cost without compromising quality.
Where to Find Django Developers?
Freelance Platforms: Upwork, Freelancer, Toptal
Developer Marketplaces: Turing, Arc, Gun.io
Agencies: Oodles — Hire Django Developer
Job Boards: StackOverflow, GitHub Jobs, Remote OK
✅ Final Thoughts
Hire Django developers in 2025 is about more than just technical skills. You need someone who understands your business vision, works well with your team, and builds secure, scalable web applications with future growth in mind.
Whether you’re launching a new product, upgrading your tech stack, or expanding your backend, make sure you hire a Django developer who brings value from day one.
Looking to hire Django experts? Partner with Oodles for experienced Django developers who deliver quality, speed, and security.
0 notes