#pentest tools
Explore tagged Tumblr posts
Text
Top Red Team Tools by Category
Cybersecurity professionals constantly need to stay ahead of potential threats. Red teaming, an exercise where security experts simulate real-world attacks to test an organisation’s defences, requires a specialised toolkit. This comprehensive guide examines the most effective top Red Team Tools by category currently available, categorised by their function in the attack lifecycle. Red teaming…
#command and control#credential dumping#cybersecurity tools#defence evasion#ethical hacking#penetration testing#Penetration Testing Tools#privilege escalation#reconnaissance tools#red team tools#security assessment#Top Pentest Tools
0 notes
Text
Why Vulnerability Scanner Tool is Essential?
Consistent use of vulnerability scanner tool enables organizations to uphold a robust security posture by continuously tracking new vulnerabilities and environmental changes. This proactive approach helps you stay ahead of potential threats and fosters a vigilant security mindset.
0 notes
Text
Are You Sure Your Mobile Apps are Secure?
Your mobile app is in the hands of thousands, maybe millions! Are you sure it’s secure? In today’s mobile-first world, your app is your brand. A single vulnerability can cost more than just data, it can cost trust. AutoSecT, a mobile pentest tool, empowers your team with next-gen mobile app security testing, blending automation, collaboration, and intelligence into one seamless experience.
1 note
·
View note
Text
Your Web App is Not A Grey Area: Importance of Web App Pentest
Apart from regular manual penetration testing, it is essential to use an automated VMDR tool equipped with vulnerability scanning and pentesting capabilities to ensure the holistic security of your web applications. AutoSecT is equipped with all the indispensable features that are needed in a modern web pentest tool to redefine web security, from identifying vulnerabilities in the source code to securing the final application.
1 note
·
View note
Text
Best Cloud Pentesting Tool in 2025 for Azure, AWS, GCP
AutoSecT offers a comprehensive and efficient approach to vulnerability management. It provides automated scanning and penetration testing across web, mobile, cloud, and API platforms, ensuring thorough coverage of potential security risks. With features like real-time vulnerability analysis, customizable reports, and seamless integration with CI/CD pipelines, AutoSecT helps organizations stay ahead of cyber threats.
1 note
·
View note
Text

poob has it for you.
0 notes
Text
youtube
#mimikatz#learntorise#security#cybersecurity#tools#pentesting#penetrationtesting#infosectrain#Youtube
0 notes
Text
youtube
In This Video , i will show you guys how we will Embed a Reverse-Shell/Malware As a clickable Button into a Email-HTML Message , for the victim to download and execute to than infect them . Also in the next 2 clips i will show you guys how we can gather IP,Device,Browser,Timezone Information Of a Victim or Inject a Malicious Javascript Code by the beef-xss Framework Hook. These Attacks can be very dangerous as people that arent good with Computers , can fall for these kind of Attacks by Social-Engineering, even Many Big Companies that are trained could have Weakness To These Type Of Attacks!.Especially with Email-Spoofing, sending a Email as if it was From a Trusted Person , but actually the Malicious Actor sends it.
Ngrok Download:https://ngrok.com/download Serveo Usage:https://serveo.net/
00:0 Introduction 1:25 Malware File Embedding 1:41 Creating Malware/Setting Up Listener With msfvenom/netcat/ngrok 4:25 Coding Malicious HTML/Javascript Page 9:14 Embedding The Link For HTML Email-Messages 12:52 Malicious-Email For Grabbing IP,Device,Browser,Timezone Information From The Victim 16:24 Sending Malicious-Email with beef-xss Hook Injected Inside The Web-Page
-If You Guys Liked The Video , Please Subscribe To My Youtube-Channel For More: https://www.youtube.com/@xenjin450
Social Medias: Instagram:https://www.instagram.com/xenjin450 Twitter:https://www.twitter.com/xenjin450 Tik-Tok:https://www.tiktok.com/@senjin450 Facebook:https://web.facebook.com/profile.php?…
Github-Page: https://github.com/xenjin450
#tumblr#Youtube#hacking#hacker#cybersecurity#blackhat#security#pentesting#technology#knowledge#kalilinux#linux#ethicalhacking#tools#learning#studying#awareness#cyberawareness#2023#javascript#computer#malware#virus#msfvenom#terminal#html#coding#programming#windows#email
0 notes
Text
anyone here heard of the flipper zero

i love this thang, it's a little pentester/hacking tool but it looks like one of those cheap petsim games from the 00's
I just love the little guy in it. I could be coerced to break into secure buildings if this guy told me to
#it's also kind of bnycore....#i watched a video on it and i've literally didn't even know devices like these were a thing#terminal talks
1K notes
·
View notes
Text


found this and couldn't reblog so I'm reposting

image id:
first image: two-part meme of joey from friends. first part is a picture of him smiling at something out of frame, captioned "The hotel's free WiFi is really fast". second part is him staring wide eyed in horror, captioned "Your IP address starts with 172.16.42.x".
second image: lain from the anime "serial experiments lain" sitting in a chair in a dim room, in front of a glowing computer screen, and smiling at the camera. the text boxes in the image say:
Hey, guys. Lain Iwakura here to explain the joke.
You see, when a computer like your laptop or smartphone connects to wifi, the router assigns it a "local IP address" to distinguish it from other machines on the network.
Most routers use IPv4 for this, where an IP address is four numbers separated by periods. The first two or three numbers of your local IP address are usually the same for all machines on the LAN, and the most common schemas for local IP addresses are 192.168.0.x or 10.0.0.x. Those are just common defaults - they can be set to anything in the router's configuration.
The address schema 172.16.42.x is not a common default for a normal router. It is the default for a device called a "WiFi Pineapple", which is a hacking tool primarily intended for "pentesting", i.e. finding exploitable vulnerabilities in a computing or networking system. The WiFi Pineapple acts as a router from the perspective of the computers on the local network, but a malicious actor can use it to passively scan those computers for vulnerabilities, and can even spy on network traffic going through it. Thus, the joke is that the person in the hotel, finding that their local IP address is under 172.16.42.x., realizes to their horror that the hotel's LAN has been pwned by a (likely malicious) rogue access point, possibly causing their computer to be cracked and their sensitive information to be stolen by cybercriminals. In light of this breach, their panic is understandable! Always keep your software up to date and never connect to a suspicious or unsecured wifi network!
/end id
60 notes
·
View notes
Text
Symfony Clickjacking Prevention Guide
Clickjacking is a deceptive technique where attackers trick users into clicking on hidden elements, potentially leading to unauthorized actions. As a Symfony developer, it's crucial to implement measures to prevent such vulnerabilities.

🔍 Understanding Clickjacking
Clickjacking involves embedding a transparent iframe over a legitimate webpage, deceiving users into interacting with hidden content. This can lead to unauthorized actions, such as changing account settings or initiating transactions.
🛠️ Implementing X-Frame-Options in Symfony
The X-Frame-Options HTTP header is a primary defense against clickjacking. It controls whether a browser should be allowed to render a page in a <frame>, <iframe>, <embed>, or <object> tag.
Method 1: Using an Event Subscriber
Create an event subscriber to add the X-Frame-Options header to all responses:
// src/EventSubscriber/ClickjackingProtectionSubscriber.php namespace App\EventSubscriber; use Symfony\Component\EventDispatcher\EventSubscriberInterface; use Symfony\Component\HttpKernel\Event\ResponseEvent; use Symfony\Component\HttpKernel\KernelEvents; class ClickjackingProtectionSubscriber implements EventSubscriberInterface { public static function getSubscribedEvents() { return [ KernelEvents::RESPONSE => 'onKernelResponse', ]; } public function onKernelResponse(ResponseEvent $event) { $response = $event->getResponse(); $response->headers->set('X-Frame-Options', 'DENY'); } }
This approach ensures that all responses include the X-Frame-Options header, preventing the page from being embedded in frames or iframes.
Method 2: Using NelmioSecurityBundle
The NelmioSecurityBundle provides additional security features for Symfony applications, including clickjacking protection.
Install the bundle:
composer require nelmio/security-bundle
Configure the bundle in config/packages/nelmio_security.yaml:
nelmio_security: clickjacking: paths: '^/.*': DENY
This configuration adds the X-Frame-Options: DENY header to all responses, preventing the site from being embedded in frames or iframes.
🧪 Testing Your Application
To ensure your application is protected against clickjacking, use our Website Vulnerability Scanner. This tool scans your website for common vulnerabilities, including missing or misconfigured X-Frame-Options headers.

Screenshot of the free tools webpage where you can access security assessment tools.
After scanning for a Website Security check, you'll receive a detailed report highlighting any security issues:

An Example of a vulnerability assessment report generated with our free tool, providing insights into possible vulnerabilities.
🔒 Enhancing Security with Content Security Policy (CSP)
While X-Frame-Options is effective, modern browsers support the more flexible Content-Security-Policy (CSP) header, which provides granular control over framing.
Add the following header to your responses:
$response->headers->set('Content-Security-Policy', "frame-ancestors 'none';");
This directive prevents any domain from embedding your content, offering robust protection against clickjacking.
🧰 Additional Security Measures
CSRF Protection: Ensure that all forms include CSRF tokens to prevent cross-site request forgery attacks.
Regular Updates: Keep Symfony and all dependencies up to date to patch known vulnerabilities.
Security Audits: Conduct regular security audits to identify and address potential vulnerabilities.
📢 Explore More on Our Blog
For more insights into securing your Symfony applications, visit our Pentest Testing Blog. We cover a range of topics, including:
Preventing clickjacking in Laravel
Securing API endpoints
Mitigating SQL injection attacks
🛡️ Our Web Application Penetration Testing Services
Looking for a comprehensive security assessment? Our Web Application Penetration Testing Services offer:
Manual Testing: In-depth analysis by security experts.
Affordable Pricing: Services starting at $25/hr.
Detailed Reports: Actionable insights with remediation steps.
Contact us today for a free consultation and enhance your application's security posture.
3 notes
·
View notes
Text
Move over, Cobalt Strike. Splinter’s the new post-exploit menace in town

Source: https://www.theregister.com/2024/09/23/splinter_red_team_tool/
More info: https://unit42.paloaltonetworks.com/analysis-pentest-tool-splinter/
2 notes
·
View notes
Text
My Take on Generative "AI"*
Recently I was doing some research into a pentesting technique and I stumbled across a blog supposedly containing a tutorial for the particular tool I was looking into. As I read through this "guide" it started to become clear that it was completely generated via an LLM such as ChatGPT - it had the stilted writing style distinctive of "AI" generated text. What's worse is that even the "screenshots" that the piece featured were generated with an "AI" - something like DALLE or whatever it's called. You'll understand immediately why I could recognise this was generated if you've ever seen one of these image generators try to write text, as it can't actually write text well. The screenshots were garbled. They were total gibberish!
(In my shock I forgot to take a screenshot or even take a copy of the site URL, so you will have to use your imagination as to how the so-called "tutorial" in the previous paragraph looked)
The entire "guide" was useless. None of the text was insightful enough to be of any use, and the images were of nothing.
This made me want to make something clear: none of my tutorials have been, or ever will be, generated by an LLM. None of the images I use have been generated by an image model. My original intention when creating this blog was to strengthen the skills I'm learning by writing about it. I carry out the techniques I teach and any screenshots are taken by me during this process. Truth be told I hardly even use autocorrect while writing (I do try to proofread and correct any errors but I'm sure some slip through - sorry!)
Someone somewhere said this more succinctly than me so to paraphrase:
"Why should I take the time to read this, if someone hasn't taken the time to write it?"
I may one day write some tutorials on hacking LLMs and jailbreaking them, but the actually body of my work is still written by me. Otherwise I don't see the point in writing this. My writing skill isn't the best but I do what I do because I enjoy it and it helps me learn as it hopefully helps you too.
*Throughout this post I have taken care to put certain words in "scare quotes". These should be read in a sarcastic - bordering on mocking - tone. I don't like calling LLMs and image generators "AI" as there is no intelligence to speak of. I use the word for brevity and simplicity however I don't want to lend credence to the idea that a hopped up predictive text is in anyway intelligent.
#AI#artificial intelligence#hacking#hacking guide#linux#hacking tutorials#linux tutorial#god wont someone please make the computers shut up
2 notes
·
View notes
Text
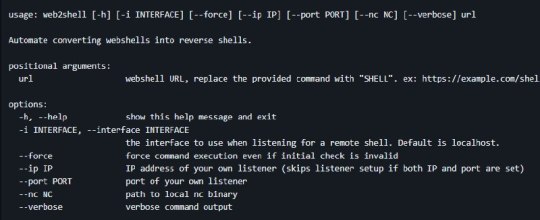
[Media] web2shell
web2shell A Python program used to automate converting webshells into reverse shells. If you regularly do CTF, HTB, or red teaming you've probably spent a good chunk of time testing payloads to convert a webshell into a reverse shell. This tool aims to simplify this process. https://github.com/ejedev/web2shell #infosec #pentesting #redteam
6 notes
·
View notes
Text
ID 1: Joey from friends, looking happy, and then very scared. Text next to each expression reads: "The hotel's free wifi is really fast" / "Your IP address starts with 172.16.42.x"
ID 2: Lain from Serial Experiments Lain, sitting at a computer and turned to look at the camera with a smile. Text reads:
"Hey, guys. Lain Iwakura here to explain the joke.
You see, when a computer like your laptop or smartphone connects to wifi, the router assigns it a "local IP address" to distinguish it from other machines on the network.
Most routers use IPv4 for this, where an IP address is four numbers separated by periods. The first two or three numbers of your local IP address are usually the same for all machines on the LAN, and the most common schemas for local IP addresses are 192.168.0.x or 10.0.0.. Those are just common defaults - they can be set to anything in the router's configuration.
The address schema 172.16.42.x is not a common default for a normal router. It is the default for a device called a "WiFi Pineapple", which is a hacking tool primarily intended for "pentesting", i.e. finding exploitable vulnerabilities in a computing or networking system. The WiFi Pineapple acts as a router from the perspective of the computers on the local network, but a malicious actor can use it to passively scan those computers for vulnerabilities, and can even spy on network traffic going through it. Thus, the joke is that the person in the hotel, finding that their local IP address is under 172.16.42., realizes to their horror that the hotel's LAN has been pwned by a (likely malicious rogue access point, possibly causing their computer to be cracked and their sensitive information to be stolen by cyber-criminals. In light of this breach, their panic is understandable! Always keep your software up to date and never connect to a suspicious or unsecured wifi network!"
END ID


134K notes
·
View notes
Text
According to Cybersecurity Ventures, the annual growth of cybercrimes is anticipated to reach $10.5 trillion by 2025. This represents a significant rise from the $6 trillion cost of cybercrime in 2021. With the increasing prevalence of cybercrimes and the potential impact of security breaches, penetration testing has become an important part of an organization's cybersecurity strategy.
0 notes