#rest api authentication
Explore tagged Tumblr posts
Text
#CodeIgniter App#Web Application Development#Backend Development#REST API with CodeIgniter#PHP MVC#CRUD Operations#CodeIgniter Authentication#CodeIgniter Form Validation
0 notes
Text
Django REST Framework: Authentication and Permissions
Secure Your Django API: Authentication and Permissions with DRF
Introduction Django REST Framework (DRF) is a powerful toolkit for building Web APIs in Django. One of its key features is the ability to handle authentication and permissions, ensuring that your API endpoints are secure and accessible only to authorized users. This article will guide you through setting up authentication and permissions in DRF, including examples and…
#custom permissions#Django API security#Django JWT integration#Django REST Framework#DRF authentication#Python web development#token-based authentication
0 notes
Text
Wish me luck tomorrow with my exam

#as soon as i finish it im gonna erase it from my mind#I'm all alone this weekend#time to study hard and code until 3 am#also if i get nervous in the exam im gonna 'cheat'#im sorry i pay 10$ a month Im going to use it if I need to#but probably wont need it#i hope#symfony its easy just put some commands and import everything in order#but its just 2 points#the rest it's going to be API#im afraid of the authentication part but I have a couple of examples#so glhf#next is JS que 0 problemas#diseño va a poner ejercicios que 100% seguro estan en internet xq es mas vago ...#y despliegues el último y el unico para el que tengo que estudiar realmente y si en el ultimo casi penco pero también ese lo puso a mala lec#he#tag rant
1 note
·
View note
Text
Boost Productivity with Databricks CLI: A Comprehensive Guide
Exciting news! The Databricks CLI has undergone a remarkable transformation, becoming a full-blown revolution. Now, it covers all Databricks REST API operations and supports every Databricks authentication type.
Exciting news! The Databricks CLI has undergone a remarkable transformation, becoming a full-blown revolution. Now, it covers all Databricks REST API operations and supports every Databricks authentication type. The best part? Windows users can join in on the exhilarating journey and install the new CLI with Homebrew, just like macOS and Linux users. This blog aims to provide comprehensive…

View On WordPress
#API#Authentication#Azure Databricks#Azure Databricks Cluster#Azure SQL Database#Cluster#Command prompt#data#Data Analytics#data engineering#Data management#Database#Databricks#Databricks CLI#Databricks CLI commands#Homebrew#JSON#Linux#MacOS#REST API#SQL#SQL database#Windows
0 notes
Text
Streaming today!
Come witness @essential-randomness tackle a new project: building her consulting resume on her Astro website as she revamps her worksona for her next era (The One With a Job™).
Twitch Link
The idea of this series is to approach it like a "build in public" project: what does it take to go from individual contributor, to open source project(s) lead, to consultant? Let's (hopefully) find out together!
Also, small update on LAST WEEK's work: the bobabot discord example now refreshes the authentication token, making it fully possible to host your own Discord bot that posts to a BobaBoard instance!
See the bot here And see it being built (and learn about REST APIs) in last week's video!
9 notes
·
View notes
Text
Integrating Third-Party Tools into Your CRM System: Best Practices
A modern CRM is rarely a standalone tool — it works best when integrated with your business's key platforms like email services, accounting software, marketing tools, and more. But improper integration can lead to data errors, system lags, and security risks.

Here are the best practices developers should follow when integrating third-party tools into CRM systems:
1. Define Clear Integration Objectives
Identify business goals for each integration (e.g., marketing automation, lead capture, billing sync)
Choose tools that align with your CRM’s data model and workflows
Avoid unnecessary integrations that create maintenance overhead
2. Use APIs Wherever Possible
Rely on RESTful or GraphQL APIs for secure, scalable communication
Avoid direct database-level integrations that break during updates
Choose platforms with well-documented and stable APIs
Custom CRM solutions can be built with flexible API gateways
3. Data Mapping and Standardization
Map data fields between systems to prevent mismatches
Use a unified format for customer records, tags, timestamps, and IDs
Normalize values like currencies, time zones, and languages
Maintain a consistent data schema across all tools
4. Authentication and Security
Use OAuth2.0 or token-based authentication for third-party access
Set role-based permissions for which apps access which CRM modules
Monitor access logs for unauthorized activity
Encrypt data during transfer and storage
5. Error Handling and Logging
Create retry logic for API failures and rate limits
Set up alert systems for integration breakdowns
Maintain detailed logs for debugging sync issues
Keep version control of integration scripts and middleware
6. Real-Time vs Batch Syncing
Use real-time sync for critical customer events (e.g., purchases, support tickets)
Use batch syncing for bulk data like marketing lists or invoices
Balance sync frequency to optimize server load
Choose integration frequency based on business impact
7. Scalability and Maintenance
Build integrations as microservices or middleware, not monolithic code
Use message queues (like Kafka or RabbitMQ) for heavy data flow
Design integrations that can evolve with CRM upgrades
Partner with CRM developers for long-term integration strategy
CRM integration experts can future-proof your ecosystem
#CRMIntegration#CRMBestPractices#APIIntegration#CustomCRM#TechStack#ThirdPartyTools#CRMDevelopment#DataSync#SecureIntegration#WorkflowAutomation
2 notes
·
View notes
Text

Crypto Exchange API Integration: Simplifying and Enhancing Trading Efficiency
The cryptocurrency trading landscape is fast-paced, requiring seamless processes and real-time data access to ensure traders stay ahead of market movements. To meet these demands, Crypto Exchange APIs (Application Programming Interfaces) have emerged as indispensable tools for developers and businesses, streamlining trading processes and improving user experience.
APIs bridge the gap between users, trading platforms, and blockchain networks, enabling efficient operations like order execution, wallet integration, and market data retrieval. This blog dives into the importance of crypto exchange API integration, its benefits, and how businesses can leverage it to create feature-rich trading platforms.
What is a Crypto Exchange API?
A Crypto Exchange API is a software interface that enables seamless communication between cryptocurrency trading platforms and external applications. It provides developers with access to various functionalities, such as real-time price tracking, trade execution, and account management, allowing them to integrate these features into their platforms.
Types of Crypto Exchange APIs:
REST APIs: Used for simple, one-time data requests (e.g., fetching market data or placing a trade).
WebSocket APIs: Provide real-time data streaming for high-frequency trading and live updates.
FIX APIs (Financial Information Exchange): Designed for institutional-grade trading with high-speed data transfers.
Key Benefits of Crypto Exchange API Integration
1. Real-Time Market Data Access
APIs provide up-to-the-second updates on cryptocurrency prices, trading volumes, and order book depth, empowering traders to make informed decisions.
Use Case:
Developers can build dashboards that display live market trends and price movements.
2. Automated Trading
APIs enable algorithmic trading by allowing users to execute buy and sell orders based on predefined conditions.
Use Case:
A trading bot can automatically place orders when specific market criteria are met, eliminating the need for manual intervention.
3. Multi-Exchange Connectivity
Crypto APIs allow platforms to connect with multiple exchanges, aggregating liquidity and providing users with the best trading options.
Use Case:
Traders can access a broader range of cryptocurrencies and trading pairs without switching between platforms.
4. Enhanced User Experience
By integrating APIs, businesses can offer features like secure wallet connections, fast transaction processing, and detailed analytics, improving the overall user experience.
Use Case:
Users can track their portfolio performance in real-time and manage assets directly through the platform.
5. Increased Scalability
API integration allows trading platforms to handle a higher volume of users and transactions efficiently, ensuring smooth operations during peak trading hours.
Use Case:
Exchanges can scale seamlessly to accommodate growth in user demand.
Essential Features of Crypto Exchange API Integration
1. Trading Functionality
APIs must support core trading actions, such as placing market and limit orders, canceling trades, and retrieving order statuses.
2. Wallet Integration
Securely connect wallets for seamless deposits, withdrawals, and balance tracking.
3. Market Data Access
Provide real-time updates on cryptocurrency prices, trading volumes, and historical data for analysis.
4. Account Management
Allow users to manage their accounts, view transaction history, and set preferences through the API.
5. Security Features
Integrate encryption, two-factor authentication (2FA), and API keys to safeguard user data and funds.
Steps to Integrate Crypto Exchange APIs
1. Define Your Requirements
Determine the functionalities you need, such as trading, wallet integration, or market data retrieval.
2. Choose the Right API Provider
Select a provider that aligns with your platform’s requirements. Popular providers include:
Binance API: Known for real-time data and extensive trading options.
Coinbase API: Ideal for wallet integration and payment processing.
Kraken API: Offers advanced trading tools for institutional users.
3. Implement API Integration
Use REST APIs for basic functionalities like fetching market data.
Implement WebSocket APIs for real-time updates and faster trading processes.
4. Test and Optimize
Conduct thorough testing to ensure the API integration performs seamlessly under different scenarios, including high traffic.
5. Launch and Monitor
Deploy the integrated platform and monitor its performance to address any issues promptly.
Challenges in Crypto Exchange API Integration
1. Security Risks
APIs are vulnerable to breaches if not properly secured. Implement robust encryption, authentication, and monitoring tools to mitigate risks.
2. Latency Issues
High latency can disrupt real-time trading. Opt for APIs with low latency to ensure a smooth user experience.
3. Regulatory Compliance
Ensure the integration adheres to KYC (Know Your Customer) and AML (Anti-Money Laundering) regulations.
The Role of Crypto Exchange Platform Development Services
Partnering with a professional crypto exchange platform development service ensures your platform leverages the full potential of API integration.
What Development Services Offer:
Custom API Solutions: Tailored to your platform’s specific needs.
Enhanced Security: Implementing advanced security measures like API key management and encryption.
Real-Time Capabilities: Optimizing APIs for high-speed data transfers and trading.
Regulatory Compliance: Ensuring the platform meets global legal standards.
Scalability: Building infrastructure that grows with your user base and transaction volume.
Real-World Examples of Successful API Integration
1. Binance
Features: Offers REST and WebSocket APIs for real-time market data and trading.
Impact: Enables developers to build high-performance trading bots and analytics tools.
2. Coinbase
Features: Provides secure wallet management APIs and payment processing tools.
Impact: Streamlines crypto payments and wallet integration for businesses.
3. Kraken
Features: Advanced trading APIs for institutional and professional traders.
Impact: Supports multi-currency trading with low-latency data feeds.
Conclusion
Crypto exchange API integration is a game-changer for businesses looking to streamline trading processes and enhance user experience. From enabling real-time data access to automating trades and managing wallets, APIs unlock endless possibilities for innovation in cryptocurrency trading platforms.
By partnering with expert crypto exchange platform development services, you can ensure secure, scalable, and efficient API integration tailored to your platform’s needs. In the ever-evolving world of cryptocurrency, seamless API integration is not just an advantage—it’s a necessity for staying ahead of the competition.
Are you ready to take your crypto exchange platform to the next level?
#cryptocurrencyexchange#crypto exchange platform development company#crypto exchange development company#white label crypto exchange development#cryptocurrency exchange development service#cryptoexchange
2 notes
·
View notes
Text
What is Argo CD? And When Was Argo CD Established?

What Is Argo CD?
Argo CD is declarative Kubernetes GitOps continuous delivery.
In DevOps, ArgoCD is a Continuous Delivery (CD) technology that has become well-liked for delivering applications to Kubernetes. It is based on the GitOps deployment methodology.
When was Argo CD Established?
Argo CD was created at Intuit and made publicly available following Applatix’s 2018 acquisition by Intuit. The founding developers of Applatix, Hong Wang, Jesse Suen, and Alexander Matyushentsev, made the Argo project open-source in 2017.
Why Argo CD?
Declarative and version-controlled application definitions, configurations, and environments are ideal. Automated, auditable, and easily comprehensible application deployment and lifecycle management are essential.
Getting Started
Quick Start
kubectl create namespace argocd kubectl apply -n argocd -f https://raw.githubusercontent.com/argoproj/argo-cd/stable/manifests/install.yaml
For some features, more user-friendly documentation is offered. Refer to the upgrade guide if you want to upgrade your Argo CD. Those interested in creating third-party connectors can access developer-oriented resources.
How it works
Argo CD defines the intended application state by employing Git repositories as the source of truth, in accordance with the GitOps pattern. There are various approaches to specify Kubernetes manifests:
Applications for Customization
Helm charts
JSONNET files
Simple YAML/JSON manifest directory
Any custom configuration management tool that is set up as a plugin
The deployment of the intended application states in the designated target settings is automated by Argo CD. Deployments of applications can monitor changes to branches, tags, or pinned to a particular manifest version at a Git commit.
Architecture
The implementation of Argo CD is a Kubernetes controller that continually observes active apps and contrasts their present, live state with the target state (as defined in the Git repository). Out Of Sync is the term used to describe a deployed application whose live state differs from the target state. In addition to reporting and visualizing the differences, Argo CD offers the ability to manually or automatically sync the current state back to the intended goal state. The designated target environments can automatically apply and reflect any changes made to the intended target state in the Git repository.
Components
API Server
The Web UI, CLI, and CI/CD systems use the API, which is exposed by the gRPC/REST server. Its duties include the following:
Status reporting and application management
Launching application functions (such as rollback, sync, and user-defined actions)
Cluster credential management and repository (k8s secrets)
RBAC enforcement
Authentication, and auth delegation to outside identity providers
Git webhook event listener/forwarder
Repository Server
An internal service called the repository server keeps a local cache of the Git repository containing the application manifests. When given the following inputs, it is in charge of creating and returning the Kubernetes manifests:
URL of the repository
Revision (tag, branch, commit)
Path of the application
Template-specific configurations: helm values.yaml, parameters
A Kubernetes controller known as the application controller keeps an eye on all active apps and contrasts their actual, live state with the intended target state as defined in the repository. When it identifies an Out Of Sync application state, it may take remedial action. It is in charge of calling any user-specified hooks for lifecycle events (Sync, PostSync, and PreSync).
Features
Applications are automatically deployed to designated target environments.
Multiple configuration management/templating tools (Kustomize, Helm, Jsonnet, and plain-YAML) are supported.
Capacity to oversee and implement across several clusters
Integration of SSO (OIDC, OAuth2, LDAP, SAML 2.0, Microsoft, LinkedIn, GitHub, GitLab)
RBAC and multi-tenancy authorization policies
Rollback/Roll-anywhere to any Git repository-committed application configuration
Analysis of the application resources’ health state
Automated visualization and detection of configuration drift
Applications can be synced manually or automatically to their desired state.
Web user interface that shows program activity in real time
CLI for CI integration and automation
Integration of webhooks (GitHub, BitBucket, GitLab)
Tokens of access for automation
Hooks for PreSync, Sync, and PostSync to facilitate intricate application rollouts (such as canary and blue/green upgrades)
Application event and API call audit trails
Prometheus measurements
To override helm parameters in Git, use parameter overrides.
Read more on Govindhtech.com
#ArgoCD#CD#GitOps#API#Kubernetes#Git#Argoproject#News#Technews#Technology#Technologynews#Technologytrends#govindhtech
2 notes
·
View notes
Text
SQL Injection in RESTful APIs: Identify and Prevent Vulnerabilities
SQL Injection (SQLi) in RESTful APIs: What You Need to Know
RESTful APIs are crucial for modern applications, enabling seamless communication between systems. However, this convenience comes with risks, one of the most common being SQL Injection (SQLi). In this blog, we’ll explore what SQLi is, its impact on APIs, and how to prevent it, complete with a practical coding example to bolster your understanding.

What Is SQL Injection?
SQL Injection is a cyberattack where an attacker injects malicious SQL statements into input fields, exploiting vulnerabilities in an application's database query execution. When it comes to RESTful APIs, SQLi typically targets endpoints that interact with databases.
How Does SQL Injection Affect RESTful APIs?
RESTful APIs are often exposed to public networks, making them prime targets. Attackers exploit insecure endpoints to:
Access or manipulate sensitive data.
Delete or corrupt databases.
Bypass authentication mechanisms.
Example of a Vulnerable API Endpoint
Consider an API endpoint for retrieving user details based on their ID:
from flask import Flask, request import sqlite3
app = Flask(name)
@app.route('/user', methods=['GET']) def get_user(): user_id = request.args.get('id') conn = sqlite3.connect('database.db') cursor = conn.cursor() query = f"SELECT * FROM users WHERE id = {user_id}" # Vulnerable to SQLi cursor.execute(query) result = cursor.fetchone() return {'user': result}, 200
if name == 'main': app.run(debug=True)
Here, the endpoint directly embeds user input (user_id) into the SQL query without validation, making it vulnerable to SQL Injection.
Secure API Endpoint Against SQLi
To prevent SQLi, always use parameterized queries:
@app.route('/user', methods=['GET']) def get_user(): user_id = request.args.get('id') conn = sqlite3.connect('database.db') cursor = conn.cursor() query = "SELECT * FROM users WHERE id = ?" cursor.execute(query, (user_id,)) result = cursor.fetchone() return {'user': result}, 200
In this approach, the user input is sanitized, eliminating the risk of malicious SQL execution.
How Our Free Tool Can Help
Our free Website Security Checker your web application for vulnerabilities, including SQL Injection risks. Below is a screenshot of the tool's homepage:
Upload your website details to receive a comprehensive vulnerability assessment report, as shown below:
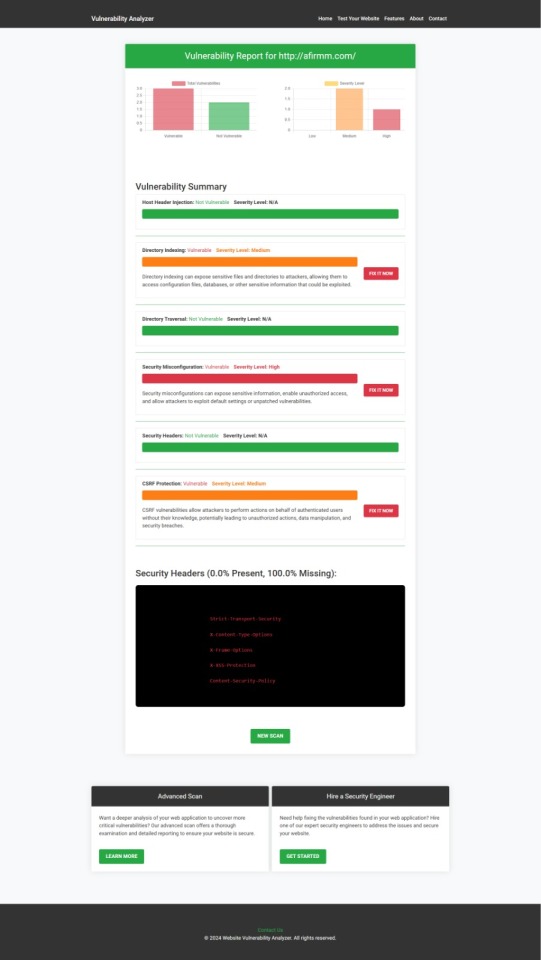
These tools help identify potential weaknesses in your APIs and provide actionable insights to secure your system.
Preventing SQLi in RESTful APIs
Here are some tips to secure your APIs:
Use Prepared Statements: Always parameterize your queries.
Implement Input Validation: Sanitize and validate user input.
Regularly Test Your APIs: Use tools like ours to detect vulnerabilities.
Least Privilege Principle: Restrict database permissions to minimize potential damage.
Final Thoughts
SQL Injection is a pervasive threat, especially in RESTful APIs. By understanding the vulnerabilities and implementing best practices, you can significantly reduce the risks. Leverage tools like our free Website Security Checker to stay ahead of potential threats and secure your systems effectively.
Explore our tool now for a quick Website Security Check.
#cyber security#cybersecurity#data security#pentesting#security#sql#the security breach show#sqlserver#rest api
2 notes
·
View notes
Text
Critical Vulnerability (CVE-2024-37032) in Ollama

Researchers have discovered a critical vulnerability in Ollama, a widely used open-source project for running Large Language Models (LLMs). The flaw, dubbed "Probllama" and tracked as CVE-2024-37032, could potentially lead to remote code execution, putting thousands of users at risk.
What is Ollama?
Ollama has gained popularity among AI enthusiasts and developers for its ability to perform inference with compatible neural networks, including Meta's Llama family, Microsoft's Phi clan, and models from Mistral. The software can be used via a command line or through a REST API, making it versatile for various applications. With hundreds of thousands of monthly pulls on Docker Hub, Ollama's widespread adoption underscores the potential impact of this vulnerability.
The Nature of the Vulnerability
The Wiz Research team, led by Sagi Tzadik, uncovered the flaw, which stems from insufficient validation on the server side of Ollama's REST API. An attacker could exploit this vulnerability by sending a specially crafted HTTP request to the Ollama API server. The risk is particularly high in Docker installations, where the API server is often publicly exposed. Technical Details of the Exploit The vulnerability specifically affects the `/api/pull` endpoint, which allows users to download models from the Ollama registry and private registries. Researchers found that when pulling a model from a private registry, it's possible to supply a malicious manifest file containing a path traversal payload in the digest field. This payload can be used to: - Corrupt files on the system - Achieve arbitrary file read - Execute remote code, potentially hijacking the system The issue is particularly severe in Docker installations, where the server runs with root privileges and listens on 0.0.0.0 by default, enabling remote exploitation. As of June 10, despite a patched version being available for over a month, more than 1,000 vulnerable Ollama server instances remained exposed to the internet.
Mitigation Strategies
To protect AI applications using Ollama, users should: - Update instances to version 0.1.34 or newer immediately - Implement authentication measures, such as using a reverse proxy, as Ollama doesn't inherently support authentication - Avoid exposing installations to the internet - Place servers behind firewalls and only allow authorized internal applications and users to access them
Broader Implications for AI and Cybersecurity
This vulnerability highlights ongoing challenges in the rapidly evolving field of AI tools and infrastructure. Tzadik noted that the critical issue extends beyond individual vulnerabilities to the inherent lack of authentication support in many new AI tools. He referenced similar remote code execution vulnerabilities found in other LLM deployment tools like TorchServe and Ray Anyscale. Moreover, despite these tools often being written in modern, safety-first programming languages, classic vulnerabilities such as path traversal remain a persistent threat. This underscores the need for continued vigilance and robust security practices in the development and deployment of AI technologies. Read the full article
2 notes
·
View notes
Text
Best Practices for Designing RESTful Services
RESTful services are integral to modern web applications, enabling seamless system communication via HTTP. Effective design involves clear resource naming (e.g., /users), correct use of HTTP methods (GET, POST, PUT, DELETE), and plural nouns for collections (/users). Consistent naming conventions, graceful error handling (e.g., 404), versioning (e.g., /v1/users), comprehensive documentation, robust authentication (OAuth, JWT), performance optimization (caching, pagination), scalability design (load balancing, indexing), HATEOAS for dynamic navigation, and API usage monitoring ensure reliability and security. These practices ensure APIs are robust, secure, and user-friendly.
3 notes
·
View notes
Text
Building a RESTful API with Django REST Framework
Learn how to build a RESTful API with Django REST Framework. This guide covers setup, models, serializers, views, authentication, and best practices for creating efficient APIs
Introduction Django REST Framework (DRF) is a powerful and flexible toolkit for building Web APIs in Django. It simplifies the process of creating RESTful APIs and provides tools for serialization, authentication, and view handling. This guide will walk you through building a RESTful API with DRF, covering everything from setting up the project to creating endpoints and handling…
#API development#authentication#best practices#Django#Django REST Framework#Python#RESTful API#serialization#web development
0 notes
Text


18.02.2024 | 16:04
I've started to work on a backend project which was actually a home task for .NET Backend Dev position with aim of developing REST API. Also started to read 'An Introduction to APIs' by Brian Cooksey'(I wish I discovered this while I was still studying, clear explanation for absolute beginners) because I figured that my C# and web skills got rusty a bit since I was using Python for a long time for both Flask projects and autonomous robot development. Application works fine right now, I tested via Postman but wanna try testing via Swagger one more time to learn what it is because the company I applied was using that. I am also planning to apply JWT authentication today and we will see how it will go.
3 notes
·
View notes
Text
The Dynamic Role of Full Stack Developers in Modern Software Development
Introduction: In the rapidly evolving landscape of software development, full stack developers have emerged as indispensable assets, seamlessly bridging the gap between front-end and back-end development. Their versatility and expertise enable them to oversee the entire software development lifecycle, from conception to deployment. In this insightful exploration, we'll delve into the multifaceted responsibilities of full stack developers and uncover their pivotal role in crafting innovative and user-centric web applications.

Understanding the Versatility of Full Stack Developers:
Full stack developers serve as the linchpins of software development teams, blending their proficiency in front-end and back-end technologies to create cohesive and scalable solutions. Let's explore the diverse responsibilities that define their role:
End-to-End Development Mastery: At the core of full stack development lies the ability to navigate the entire software development lifecycle with finesse. Full stack developers possess a comprehensive understanding of both front-end and back-end technologies, empowering them to conceptualize, design, implement, and deploy web applications with efficiency and precision.
Front-End Expertise: On the front-end, full stack developers are entrusted with crafting engaging and intuitive user interfaces that captivate audiences. Leveraging their command of HTML, CSS, and JavaScript, they breathe life into designs, ensuring seamless navigation and an exceptional user experience across devices and platforms.
Back-End Proficiency: In the realm of back-end development, full stack developers focus on architecting the robust infrastructure that powers web applications. They leverage server-side languages and frameworks such as Node.js, Python, or Ruby on Rails to handle data storage, processing, and authentication, laying the groundwork for scalable and resilient applications.
Database Management Acumen: Full stack developers excel in database management, designing efficient schemas, optimizing queries, and safeguarding data integrity. Whether working with relational databases like MySQL or NoSQL databases like MongoDB, they implement storage solutions that align with the application's requirements and performance goals.

API Development Ingenuity: APIs serve as the conduits that facilitate seamless communication between different components of a web application. Full stack developers are adept at designing and implementing RESTful or GraphQL APIs, enabling frictionless data exchange between the front-end and back-end systems.
Testing and Quality Assurance Excellence: Quality assurance is paramount in software development, and full stack developers take on the responsibility of testing and debugging web applications. They devise and execute comprehensive testing strategies, identifying and resolving issues to ensure the application meets stringent performance and reliability standards.
Deployment and Maintenance Leadership: As the custodians of web applications, full stack developers oversee deployment to production environments and ongoing maintenance. They monitor performance metrics, address security vulnerabilities, and implement updates and enhancements to ensure the application remains robust, secure, and responsive to user needs.
Conclusion: In conclusion, full stack developers embody the essence of versatility and innovation in modern software development. Their ability to seamlessly navigate both front-end and back-end technologies enables them to craft sophisticated and user-centric web applications that drive business growth and enhance user experiences. As technology continues to evolve, full stack developers will remain at the forefront of digital innovation, shaping the future of software development with their ingenuity and expertise.
#full stack course#full stack developer#full stack software developer#full stack training#full stack web development
2 notes
·
View notes
Text
25 Python Projects to Supercharge Your Job Search in 2024

Introduction: In the competitive world of technology, a strong portfolio of practical projects can make all the difference in landing your dream job. As a Python enthusiast, building a diverse range of projects not only showcases your skills but also demonstrates your ability to tackle real-world challenges. In this blog post, we'll explore 25 Python projects that can help you stand out and secure that coveted position in 2024.
1. Personal Portfolio Website
Create a dynamic portfolio website that highlights your skills, projects, and resume. Showcase your creativity and design skills to make a lasting impression.
2. Blog with User Authentication
Build a fully functional blog with features like user authentication and comments. This project demonstrates your understanding of web development and security.
3. E-Commerce Site
Develop a simple online store with product listings, shopping cart functionality, and a secure checkout process. Showcase your skills in building robust web applications.
4. Predictive Modeling
Create a predictive model for a relevant field, such as stock prices, weather forecasts, or sales predictions. Showcase your data science and machine learning prowess.
5. Natural Language Processing (NLP)
Build a sentiment analysis tool or a text summarizer using NLP techniques. Highlight your skills in processing and understanding human language.
6. Image Recognition
Develop an image recognition system capable of classifying objects. Demonstrate your proficiency in computer vision and deep learning.
7. Automation Scripts
Write scripts to automate repetitive tasks, such as file organization, data cleaning, or downloading files from the internet. Showcase your ability to improve efficiency through automation.
8. Web Scraping
Create a web scraper to extract data from websites. This project highlights your skills in data extraction and manipulation.
9. Pygame-based Game
Develop a simple game using Pygame or any other Python game library. Showcase your creativity and game development skills.
10. Text-based Adventure Game
Build a text-based adventure game or a quiz application. This project demonstrates your ability to create engaging user experiences.
11. RESTful API
Create a RESTful API for a service or application using Flask or Django. Highlight your skills in API development and integration.
12. Integration with External APIs
Develop a project that interacts with external APIs, such as social media platforms or weather services. Showcase your ability to integrate diverse systems.
13. Home Automation System
Build a home automation system using IoT concepts. Demonstrate your understanding of connecting devices and creating smart environments.
14. Weather Station
Create a weather station that collects and displays data from various sensors. Showcase your skills in data acquisition and analysis.
15. Distributed Chat Application
Build a distributed chat application using a messaging protocol like MQTT. Highlight your skills in distributed systems.
16. Blockchain or Cryptocurrency Tracker
Develop a simple blockchain or a cryptocurrency tracker. Showcase your understanding of blockchain technology.
17. Open Source Contributions
Contribute to open source projects on platforms like GitHub. Demonstrate your collaboration and teamwork skills.
18. Network or Vulnerability Scanner
Build a network or vulnerability scanner to showcase your skills in cybersecurity.
19. Decentralized Application (DApp)
Create a decentralized application using a blockchain platform like Ethereum. Showcase your skills in developing applications on decentralized networks.
20. Machine Learning Model Deployment
Deploy a machine learning model as a web service using frameworks like Flask or FastAPI. Demonstrate your skills in model deployment and integration.
21. Financial Calculator
Build a financial calculator that incorporates relevant mathematical and financial concepts. Showcase your ability to create practical tools.
22. Command-Line Tools
Develop command-line tools for tasks like file manipulation, data processing, or system monitoring. Highlight your skills in creating efficient and user-friendly command-line applications.
23. IoT-Based Health Monitoring System
Create an IoT-based health monitoring system that collects and analyzes health-related data. Showcase your ability to work on projects with social impact.
24. Facial Recognition System
Build a facial recognition system using Python and computer vision libraries. Showcase your skills in biometric technology.
25. Social Media Dashboard
Develop a social media dashboard that aggregates and displays data from various platforms. Highlight your skills in data visualization and integration.
Conclusion: As you embark on your job search in 2024, remember that a well-rounded portfolio is key to showcasing your skills and standing out from the crowd. These 25 Python projects cover a diverse range of domains, allowing you to tailor your portfolio to match your interests and the specific requirements of your dream job.
If you want to know more, Click here:https://analyticsjobs.in/question/what-are-the-best-python-projects-to-land-a-great-job-in-2024/
#python projects#top python projects#best python projects#analytics jobs#python#coding#programming#machine learning
2 notes
·
View notes