#tmp 32
Explore tagged Tumblr posts
Text
That's it. That's email

#tmp#the magnus protocol#tmagp#tmp spoilers#gwen tmagp#gwen bouchard#gwendolyn bouchard#tmp 32#tmagp 32#tmagp shitpost#tmagp season 2#tmagp spoilers#tmp colin#tmagp colin
2K notes
·
View notes
Text

Who’s hand this might be?


#tmagp#the magnus protocol#tmagp spoilers#tmagp 31#tmagp 32#alice dyer#gwen bouchard#colin becher#magpod#tmp#digital art#like seriously I thought that Colin was fully DISCARDED#so I have only one logical explanation for this hand#jonathan sims#martin blackwood#elias bouchard#jonah magnus#tma#tma spoilers#tmagp ep 31#tmagp ep 32
999 notes
·
View notes
Text
alice’s lack of media literacy is astounding. she didn’t even pick up on the anti-capitalist and anti-imperialist tones of the case! she didn’t comprehend the basis of the commentary at all </3
#the magnus archives#tma#tma podcast#tmp#tmp s2 spoilers#tmp 32 spoilers#alice dyer#the magnus protocol podcast#the magnus protocol#tmagp
111 notes
·
View notes
Text

if i had a nickel for every irritated conscious building...
115 notes
·
View notes
Text


The Magnus Protocol
Episode 32: Restructuring
Apart from the original pencil sketch brush, I challenged myself to use just watercolour procreate brushes to colour this one.
#the magnus protocol#tma#tmagp#tmp#the magnus archives#tmp spoilers#tmagp spoilers#tmagp fanart#tmagp 32
32 notes
·
View notes
Text
TMAGP 32 spoilers
See? Colin is alive and alright! He's even ready to give them his helping hand! Or his helping teeth!
#tmagp#the magnus protocol#tmagp 32#tmagp spoilers#tmp spoilers#what is even happening#i would love analise this episode but im not smart enough for this one#it's very cool though!
23 notes
·
View notes
Text
new tmp episode is my fave so far- love hearing from jonah, really cool spooky statement, and some interesting mystery elements 👀
#tmp#mossy thoughts#i really hope they dont take 32 episodes to get to the actual plot tho#i could barely handle the extreme slow burn on first listen of tma and i was binging it#pleasee what is the fucking deal with the magnus institute
0 notes
Text
i know one thing tho when the magnus protocol comes out we are not going to refer to the episodes as “mag (number)” for example mag 32 will never refer to the 32nd episode of tmp, we have to simply call it tmp 32 bc mag 32 will ALWAYS be hive. mag 32 hive simply CANNOT be overruled.
124 notes
·
View notes
Text
i started typing a lot because i love talking about the intricacies of the fears so erm. sorry this is basically just me rambling oops
i really dont think this is the case but im gonna be honest if the “reconfiguration” of the entities that jonny mentioned is just that theyre desires instead now i would be deeply disappointed. i think people conceptualize them as “fears” in a far too literal sense which gives way to a misunderstanding of how they functioned in tma in the first place?
its technically more accurate to call them entities or forces when talking about how they function in practice because calling them fears is a bit of a simplification, a very nice one for worldbuilding though! a lot of avatars will refer to them as fears in conversation because it rolls off the tongue easier when talking casually, but people who attempt to study the entities while being relatively unbound/unaligned (e.g. leitner, smirke) tend to use entities as a term more often for accuracy. it serves its purpose in universe so its not redundant just a bit unclear. i just think thats neat 👍
anyways that said the entities already embody desire as well to an extent, im not gonna say its like a yin yang type deal but its still very much present. im gonna pull out the entities fan holy grail here with a transcript from mag 111 (with the understanding that jons suggestion here that the entities “do” anything is wrong because the forces are technically incapable of thought, barring the web and possibly to a much lesser extent the end as well)

the avatars do have free will, depending on how you define it, but becoming a full avatar requires an active choice on the avatars part; so its questionable to say that theyre corrupted by their entities when its more accurate to say that theyre tempted in some way, either by coming into contact with something connected to an entity, or just naturally having a general inclination towards what they represent and things associated with them.
avatars always get something from the entity they align with, not necessarily power but something more abstract that the avatar desires; avatars of the dark get to indulge in simple ignorant bliss, those of the stranger gain complete anonymity and freedom from identity, and avatars of the corruption get to let their toxic obsession fester and feel a wholly encompassing love that they desire as much as they fear. i could go on literally forever but my point is that the fears are already intrinsically linked to desire and so people can be drawn to them, both avatar and victim alike.
the trend of the episodes of tmp thatve come out so far (3 btw.) oversimplified is that the statement giver wants something and is supernaturally granted it in a fucked up way, presumably by this worlds entities. but that is literally just what happens to avatars. go listen to mag 89 jude perrys statement or mag 32 jane prentiss’ statement or mag 152 hezekiah wakelys statement where they literally draw parallels to jane prentiss, its just already in line with how the entities manifest. im curious to see how they get changed but it definitely isnt that theyre like desires instead this time sorry
3 notes
·
View notes
Text
Abstract In modern industrial applications, precise temperature monitoring is crucial for ensuring product quality, safety, and operational efficiency. The advent of multiplex temperature testers, specifically those with 8 or 16 channels, has revolutionized the way industries monitor temperature across multiple points simultaneously. This paper provides an in-depth analysis of the 8/16 channels temperature tester, focusing on the LISUN TMP-16 Multiplex Temperature Tester. We explore its technical specifications, working principles, application scope, and best practices for optimal utilization. Additionally, we present data tables to illustrate the tester’s capabilities and performance metrics. 1. Introduction Temperature monitoring is a fundamental aspect of various industrial processes, from manufacturing and quality control to research and development. Traditional single-point temperature measurement devices often fall short when multiple temperature points need simultaneous monitoring. The introduction of multiplex temperature testers, particularly those offering 8 or 16 channels, addresses this limitation by allowing concurrent monitoring of multiple temperature points. The LISUN TMP-16 Multiplex Temperature Tester exemplifies such advanced instrumentation, offering robust features tailored for diverse industrial applications. 2. Technical Specifications of the LISUN TMP-16 The LISUN TMP-16 is designed to provide accurate and efficient temperature monitoring across multiple channels. Its key specifications include: • Number of Channels: 16 • Thermocouple Compatibility: K-type • Temperature Range: -40°C to 300°C • Measurement Accuracy: Class 0.5 • Monitoring Capabilities: Circular monitoring Single-channel monitoring • Software Compatibility: English software compatible with Windows 7, 8, 10, and 11 • Data Management: Supports communication with PC software for data recording and report generation Table 1: Technical Specifications of the LISUN TMP-16 Specification Details Number of Channels 16 Thermocouple Type K-type Temperature Range -40°C to 300°C Measurement Accuracy Class 0.5 Monitoring Modes Circular, Single-channel Software Compatibility Windows 7, 8, 10, 11 Data Management PC communication for data recording and reporting 3. Working Principle of the 8/16 Channels Temperature Tester The LISUN TMP-16 operates by connecting to multiple K-type thermocouples, each placed at specific measurement points. The device sequentially scans each channel, capturing temperature data in real-time. This data is then processed by an internal 32-bit high-speed CPU, ensuring rapid and accurate readings. The tester’s software facilitates data storage, analysis, and report generation, enhancing the user’s ability to monitor temperature variations effectively. LISUN 4. Application Scope The versatility of the 8/16 channels temperature tester makes it suitable for a wide range of applications, including: • Home Appliances: Monitoring temperature in devices like ovens, refrigerators, and heaters to ensure safety and performance. • Electric Motors: Assessing temperature rise in motor components to prevent overheating and prolong lifespan. • Electric Heaters: Ensuring uniform heating and preventing hotspots in industrial heaters. • Transformers: Monitoring winding and core temperatures to maintain efficient operation and prevent failures. • Laboratory Research: Conducting experiments that require precise temperature control across multiple points. 5. Best Practices for Using the LISUN TMP-16 To maximize the efficacy of the LISUN TMP-16, consider the following best practices: • Proper Installation: Ensure the device is installed away from heat sources and in well-ventilated areas to prevent external temperature interference. • Regular Calibration: Periodically calibrate the thermocouples and the tester to maintain measurement accuracy. • Environmental Considerations: Avoid placing the tester in areas with high humidity, vibration, or corrosive gases, as these can affect performance. • Data Management: Utilize the PC software for real-time data monitoring and analysis, enabling prompt responses to any temperature anomalies. 6. Comparative Analysis with Other Temperature Testers When compared to traditional single-channel temperature testers, the LISUN TMP-16 offers significant advantages: • Efficiency: Simultaneously monitors up to 16 temperature points, reducing the time and effort required for comprehensive assessments. • Data Integration: Consolidates data from multiple channels into a single interface, simplifying analysis and reporting. • Cost-Effectiveness: Eliminates the need for multiple single-channel devices, reducing equipment costs and maintenance requirements. Table 2: Comparison Between Single-Channel and 16-Channel Temperature Testers Feature Single-Channel Tester LISUN TMP-16 16-Channel Tester Number of Channels 1 16 Data Integration Limited Comprehensive Monitoring Efficiency Low High Equipment Cost Higher (multiple units) Lower (single unit) Maintenance More complex Simplified 7. Case Study: Implementing the LISUN TMP-16 in a Manufacturing Setting A manufacturing facility specializing in electric heaters implemented the LISUN TMP-16 to monitor temperature across multiple production lines. By utilizing the tester’s 16 channels, the facility achieved: • Improved Quality Control: Real-time monitoring allowed for immediate detection of temperature fluctuations, reducing defects. • Increased Efficiency: Automated temperature logging streamlined data collection, saving time and labor. • Cost Savings: Reduced the need for multiple single-channel testers, lowering equipment and maintenance costs. • Enhanced Safety: Continuous monitoring ensured compliance with safety regulations, minimizing overheating risks. 8. Advantages and Challenges of Using the LISUN TMP-16 The LISUN TMP-16 comes with a host of advantages but also some challenges to consider. Advantages: Multiple Channel Monitoring: The ability to monitor up to 16 temperature points simultaneously streamlines operations, providing a comprehensive overview of the temperature profile across multiple areas or components. • High Accuracy: With Class 0.5 accuracy, the device ensures precise measurements, which is vital in applications where temperature consistency is critical. • User-Friendly Interface: The PC software that accompanies the LISUN TMP-16 makes data logging, analysis, and report generation simple, enhancing ease of use for operators. • Cost-Effective: As compared to purchasing several single-channel temperature testers, the LISUN TMP-16 offers a more affordable, streamlined solution. Challenges: • Initial Setup Complexity: Setting up a multiplex temperature tester with multiple channels may require more time and expertise compared to using single-point devices. However, this challenge is mitigated by the comprehensive user manual and support available. • Environmental Sensitivity: Though the LISUN TMP-16 is durable, its performance can be affected by extreme environmental conditions such as high humidity or excessive vibration, which may require the user to carefully select an optimal installation location. 9. Future Trends in Multiplex Temperature Testing As industries continue to innovate, the demand for more sophisticated temperature monitoring systems is expected to grow. Future trends in the field of multiplex temperature testing may include: • Integration with IoT: The next generation of multiplex testers may incorporate IoT capabilities, enabling real-time remote monitoring, alerts, and predictive maintenance, thus further enhancing operational efficiency. • Increased Number of Channels: Manufacturers may expand the number of channels beyond 16, offering even greater versatility for industries with more complex temperature monitoring needs. • Improved User Interfaces: As user experience becomes increasingly important, future versions of temperature testers will likely feature even more intuitive interfaces, further simplifying the process of setup, monitoring, and data analysis. • Enhanced Durability: Future models may offer greater resistance to harsh environmental factors, including waterproofing, dustproofing, and resistance to extreme temperatures, making them suitable for a wider range of applications. 10. Conclusion The LISUN TMP-16 8/16 channels temperature tester represents a significant advancement in temperature monitoring technology. Its ability to monitor multiple temperature points simultaneously not only increases operational efficiency but also ensures higher levels of accuracy and consistency across various industrial applications. By integrating this device into production and quality control processes, companies can achieve better control over product quality, reduce downtime, and ultimately improve their bottom line. The data management capabilities, combined with the device’s versatility, make it an invaluable tool in fields ranging from home appliances to heavy industrial machinery. Despite some challenges, the LISUN TMP-16 is poised to become a critical asset for any operation requiring precise and continuous temperature monitoring. Read the full article
0 notes
Text
Several people have pointed out my tags, but I forgot there was a tag limit and tumblr deleted a bunch of info (and I wasn't expecting people to read them! Whoops!), so I've written them up into a more coherent form for you all (with links to more angst!)
First off, a disclaimer: While I did do a shitton of maths to get this as accurate as I could, I was also cribbing from headcanon and guesstimates and dubiously canon novels, and then took artistic license with the diagram anyway. I do not claim this to be 100% accurate, I was just Overcome By Emotion and needed to get it out. Feel free to let me know if I've missed something, but please note this art was more about representation than wholly accurate data. (Sorry, Spock!)
I drew this after watching the short film Unification that came out last year. I don't usually acknowledge Generations for the sake of my own sanity (if I think about it for too long I will cry) but the short film made me think about both Jim AND Spock's deaths (and also the fact that Bones wasn't there, which I am. so cool and fine with. Not.) and that sent me into a little spiral at 4am (pictured below).

I scribbled this in my planner in the faint glimmer of moonlight, half-hanging out of my bed, looking up dates and becoming more and more distraught as my cat looked on in bemusement. My initial thoughts were as follows:
Hang on, how old was Jim when he died?
EXCUSE ME??
How old were Spock and Bones when they bit it??
WHAT??
How long did they all actually know each other for???
WHAT THE FUCK??????
WHAT DO YOU MEAN THEY WERE ONLY TOGETHER* FOR 25 YEARS?????
THAT CAN'T BE FUCKING RIGHT.
And then I cried for a good while. And eventually slept. And then woke up and did even more maths.
My calculations were as follows:
Jim was 32 at the start of the 5ym, Spock was 35, and Bones was 38. According to the dates on the Memory Alpha Wiki (death date minus birth year, counting all canon time travel etc as negligible since it's only a few months difference at most afaik), Jim lived to be 60 (not including his time in the Nexus, since that's more like the afterlife to me), Bones lived to be 141, and Spock lived to be 161 (that's a little confusing if you look at the wiki, since he died in the alternate universe and the stardates over there are different, but trust me). Bones lived for 75 years after Jim disappeared, and Spock lived for 98 (23 of those after Bones died, too). Almost an entire century. :)
They were only together as a trio for ~25 years. Jim took command of the Enterprise in 2265, and went into the Nexus in 2293. That's 28 years, minus 3 for the post-5YM/pre-TMP estrangement. Twenty five years. That's all. That's. Not fucking fair. That's less than half Jim's life. He lived over half his life before meeting Spock, and having his two best friends - his heart and mind - actually with him. And then. And then…
He did know Bones for longer. I headcanon that Jim and Bones were friends, or at least friendly acquaintances for ~11 years before Bones becomes CMO (and thus meets Spock), so that's their overlap on the diagram - of course, there was probably some time together without Spock later on but not enough to change that amount drastically. Plus, most of their friendship before Bones became CMO was likely long-distance and intermittent, given that they weren't (afaik) ever stationed together (and I tend to think Bones didn't even join the fleet till shortly before he became CMO). So that means they were together for 36 years at most (just over half Jim's life).
Jim and Spock have the smallest overlap. I think I factored in SNW and estimated it at about 5 years cumulative (the years they know each other in SNW + a bit extra just in case). So that gives them 30 years total together (exactly half Jim's life!)
And then there's Spock and Bones. Hoo fucking boy. They met because of Jim. They lived 25 years of their life with him. The three of them, working so well together, balancing each other out. And then Jim is gone. By my estimate, it was just the two of them for 75 years. Three times the amount of time they were all together. And all of this post-Jim's disappearance. They knew each other far longer than either of them ever knew Jim, and their relationship after his disappearance must have been altered by his absence, but they did stay good friends - and then there's also the fact that Spock could feel Jim was 'alive' somewhere, but had no idea where or how to get to him. Just that he was happy. Without them. If I think about that too much I will start biting.
And also. I really can't get over the fact that Bones lived so long. I expected Spock to outlive him by a wide margin (and I bet they all expected him to), but no. Both Bones and Spock lived for well over double Jim's lifespan, and lived without him for triple (nearly quadruple, in Spock's case) the time they knew him. Jim dying at 60 is young, they could have had so many more years together - they probably thought they would, after cheating death so many times and still coming back together! But Jim dies, and Spock must have, on some level, expected to outlive him, but not so soon. For a Vulcan, he has a remarkably short life, and Bones was alive for so long and they were together but without Jim, and then - even worse! - Bones dies and Spock leaves for Romulus (and ultimately another fucking universe) because there's no one left for him anymore. And he takes that pendant of Jim with him, and (I like to think) still has an impression of Bones in his head from the katra-sharing, and he lives 23 more years without them with him, not really, but they're still a fundamental part of him. Even though they were only really all together for 25 years and it's been almost a century since he last saw Jim, his Jim. Twenty five years. That's all they get.
*when I say together, I mean on friendly terms, in fairly regular contact - essentially that they were in each other's lives. That's why I'm not counting the pre-Motion Picture divorce era, and why my numbers for their one-on-one time are hazy, since I imagine they might have had other falling-outs or time alone, and Bones and Jim especially might have gone long stretches without communicating before Bones became CMO, since they weren't living near each other - and I think it's likely Spock and Bones did so post-Jim, too, especially since Spock became an ambassador and likely moved around a lot. At least they had their post-katra-sharing mind link, though.
That's what I was trying to articulate with this art - how lifespans can overlap, and how you can never match your life up perfectly to someone else's, and you'll always end up leaving or being left behind, eventually, even if you all want to stay together. I was thinking about my parents as I drew this, and how I will, most likely, outlive them by a wide margin. I have no idea how long I'll live without my current friends, too. It's bittersweet, to me. I know it's impossible to keep even one person close for your entire life, but I still wish I could.
Spock outlived both his best friends, and both he and Bones far outlived Jim. The three of them were together for those precious 25 years. It's at once so long, and not nearly long enough.
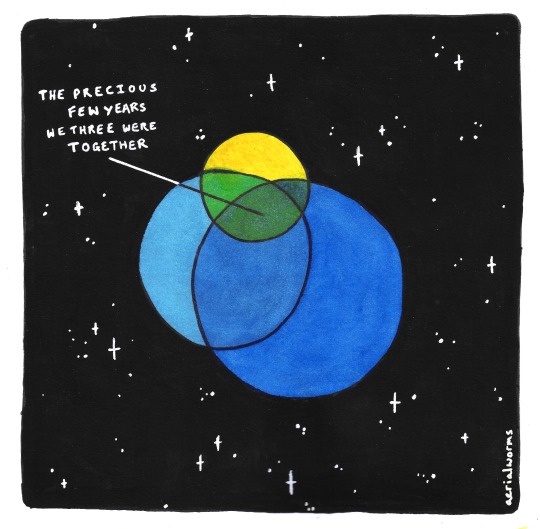
Lifespans.
(ID under cut)
[Image ID: A three-way venn diagram floating against a starfield. The circles are coloured; one yellow, one light blue, one a darker shade of blue. The yellow is the smallest, the two blue ones over double its size, with the darker blue the biggest. The yellow is half covered by the two blue circles, while it takes up a small amount of the two blues. The centre overlap between all three is labelled "the precious few years we three were together".
There is very little overlap between the yellow and the darker blue without the lighter blue.
The work is digned 'aerialworms'./End ID]
#star trek#mcspirk#my art#meta#tos#artie talks#i was not expecting this to get so many notes so quickly! my condolences to everyone crying in the tags#if it helps i made myself cry like two more times writing this up 😭👍#also don't mind the destiel there#if i start thinking about THAT i'll start crying again too
2K notes
·
View notes
Text
Mandiant Finds UNC5820 FortiManager For Data Exfiltration

Mandiant and Fortinet worked together in October 2024 to look into the widespread abuse of FortiManager appliances across more than fifty potentially compromised FortiManager devices in a range of businesses. A threat actor can use an unauthorized, threat actor-controlled FortiManager device to run arbitrary code or commands against susceptible FortiManager devices with the vulnerability, CVE-2024-47575 / FG-IR-24-423.
As early as June 27, 2024, Mandiant saw a new threat cluster that is currently monitor as UNC5820 taking advantage of the FortiManager vulnerability. The configuration information of the FortiGate devices controlled by the compromised FortiManager was staged and exfiltrated by UNC5820. Along with the users and their FortiOS256-hashed passwords, this data includes comprehensive configuration details for the controlled equipment. UNC5820 might utilize this information to target the enterprise environment, advance laterally to the controlled Fortinet devices, and further attack the FortiManager.
The precise requests that the threat actor made in order to take advantage of the FortiManager vulnerability were not yet documented in the data sources that Mandiant examined. Furthermore, as of this point in Google cloud study, there is no proof that UNC5820 used the configuration data it had acquired to migrate laterally and endanger the environment even more. It therefore don’t have enough information at the time of publication to evaluate actor location or motivation. Mandiant will update this blog’s attribution assessment as new information emerges from investigations.
A forensic investigation should be carried out right away by any organizations whose FortiManager may be exposed to the internet.
Exploitation Details
The first known instance of Mandiant being exploited was on June 27, 2024. Several FortiManager devices were connected to the default port TCP/541 on that day via the IP address 45[.]32[.]41[.]202. Around the same time, the file system stored the staging of different Fortinet configuration files in an archive called /tmp/.tm that was compressed using Gzip. The files and folders mentioned in below Table were included in this bundle.FilenameDescription/var/dm/RCSFolder containing configuration files of managed FortiGate devices/var/dm/RCS/revinfo.dbDatabase containing additional information of the managed FortiGate devices/var/fds/data/devices.txtContains a list of FortiGate serials and their corresponding IP addresses/var/pm2/global.dbGlobal database that contains object configurations, policy packages, and header and footer sensor configuration for IPS/var/old_fmversionContains current FortiManager version, build, and branch information
Mandiant noticed a second attempt at exploitation using the same symptoms on September 23, 2024. Outgoing network traffic happened soon after the archive was created in both exploitation scenarios. The size of the archive is marginally less than the number of bytes delivered to the corresponding destination IP addresses. The specifics of this action are listed in below Table .
The threat actor’s device was linked to the targeted FortiManager during the second exploitation attempt. Figure shows the timestamp at which the illegal FortiManager was introduced to the Global Objects database.
The threat actor’s unknown Fortinet device showed up in the FortiManager console after they had successfully exploited the FortiManager.
The files /fds/data/subs.dat and /fds/data/subs.dat.tmp contain additional indicators of the exploitation that include an associated disposable email address and a company name as listed in Figure .SerialNumber=FMG-VMTM23017412|AccountID= [email protected]|Company=Purity Supreme|UserID=1756868
Lack of Follow-On Malicious Activity
Mandiant examined rootfs.gz, the device’s initramfs (RAM disk) that is mounted to /bin. During the period of exploitation activity, did not discover any malicious files that had been produced or altered.
Affected clients who displayed comparable activities in their environments were alerted by Google Cloud. In order to help identify Fortinet device exploit attempts, Google Cloud Threat Intelligence also conducted retrohunts while creating detections for this activity and manually escalated Pre-Release Detection Rule notifications to impacted SecOps customers.
Apart from working with Mandiant, Fortinet made aggressive efforts to notify its clients in advance of their advise so that they may improve their security posture before it was widely made public.
Mitigation Strategies / Workaround
Restrict only authorized internal IP addresses from accessing the FortiManager admin portal.
Permitted FortiGate addresses should be the only ones allowed to connect to FortiManager.
Deny FortiManager access to unidentified FortiGate devices.
Available 7.2.5, 7.0.12, 7.4.3 and later (not functional workaround on 7.6.0). config system global set fgfm-deny-unknown enable end
Detection
YARA-L
IOCs mentioned in this blog post can be prioritized using Applied Threat Intelligence, and rules were released to the “Mandiant Intel Emerging Threats” rule pack (in the Windows Threats group) if you are a Google SecOps Enterprise+ customer.
Relevant Rules
Suspicious FortiManager Inbound and Outbound Connection
UNC5820 Fortinet Exploitation and File Download
UNC5820 Fortinet Exploitation and non-HTTPS Command and Control
UNC5820 Fortinet Exploitation and HTTPS Command and Control
Other SIEMs
Create searches for the following pertinent IOCs using Fortiguard logs. Specifically, if activated, the Malicious Fortinet Device ID need to deliver a high quality alert.
In the FortiManager logs, establish baselines and thresholds for distinct processes. Specifically, “Add device” and “Modify device” procedures can be infrequent enough for your company to issue a useful warning until this vulnerability is fixed.
In the FortiManager logs, baseline and establish thresholds for the changes field. When the word “Unregistered” appears in the changes field, take into account a higher sensitivity.
Every day, count the Fortigate devices and notify you when a device name that hasn’t been seen in the logs is detected.
Indicators of Compromise (IOCs)
Registered users can access a Google Threat Intelligence Collection of IOCs.
Read more on govindhtech.com
#MandiantFinds#UNC5820FortiManager#GoogleSecOps#Googlecloud#DataExfiltration#ThreatIntelligence#AdditionalKeywords#Workaround#MitigationStrategie#MaliciousActivity#technology#technews#news#govindhtech
0 notes
Photo

TMP Page 32 Announcement
The finale page has been finished and available for my supporters to read. But I will thank everybody whether they are Patreon supporters or not for reading this comic all the way to the end. https://www.patreon.com/posts/mysterious-page-108674237?utm_medium=clipboard_copy&utm_source=copyLink&utm_campaign=postshare_creator&utm_content=join_link
Posted using PostyBirb
0 notes
Text
“...James Acaster has pointed out to me, that Jamali is truly happy, only when Lee messes something up.”
- Ed Gamble, Taskmaster Podcast, Episode 32
#taskmaster#ed gamble#lee mack#jamali maddix#taskmaster podcast#TMP#TMP EP 32#tms11#taskmaster s11#taskmaster series 11#James Acaster
56 notes
·
View notes
Text
Some notes, if you‘re planning on doing Daily Twin Peaks:
Rewatchers, please tag your spoilers for both FWWM and Twin Peaks, in general! There will likely be first-time watchers!
First-time watchers, make sure you block those tags! While FWWM IS a prequel, make sure you watch it AFTER the original run! Not only does it spoil the main mystery, but it also includes stuff introduced later. Also, make sure to watch the Log Lady intros. If you don’t have the Blu-Rays, they can be found on YouTube.
Here are the days I have determined each episode of the original run to take place:
Pilot: Fri, Feb 24, 1989
Episode 1: Sat, Feb 25, 1989 (the second episode)
Episode 2: Sun, Feb 26, 1989
Episode 3: Mon, Feb 27, 1989
Episode 4: Tue, Feb 28, 1989
Episode 5: Wed, Mar 1, 1989
Episode 6: Thu, Mar 2, 1989
Episode 7: Thu, Mar 2, 1989 (the same day as Episode 6, the seventh episode)
Episode 8: Fri, Mar 3, 1989
Episode 9: Sat, Mar 4, 1989
Episode 10: Sun, Mar 5, 1989
Episode 11: Mon, Mar 6, 1989
Episode 12: Tue, Mar 7, 1989
Episode 13: Wed, Mar 8, 1989
Episode 14: Thu, Mar 9, 1989
Episode 15: Fri, Mar 10, 1989
Episode 16: Sun, Mar 12, 1989 (note the time skip)
Episode 17: Wed, Mar 15, 1989 (note the time skip)
Episode 18: Thu, Mar 16, 1989
Episode 19: Fri, Mar 17, 1989
Episode 20: Sat, Mar 18, 1989
Episode 21: Sun, Mar 19, 1989
Episode 22: Mon, Mar 20, 1989
Episode 23: Tue, Mar 21, 1989
Episode 24: Wed, Mar 22, 1989
Episode 25: Thu, Mar 23, 1989
Episode 26: Fri, Mar 24, 1989
Episode 27: Sat, Mar 25, 1989
Episode 28: Sun, Mar 26, 1989
Episode 29: Mon, Mar 27, 1989
Rewatchers can pretty much sandwich the original run between FWWM (Feb 23) and TMP (Mar 28), but, below the cut, I have broken those down into days.
First-time watchers, for the books, I recommend the following order:
S1
Episode 8 (the ninth episode)
Diane… (short tape/audiobook)
S2
Access Guide to the Town (book)
My Life, My Tapes (book)
The Secret Diary of Laura Palmer (book)
Fire Walk With Me
The Missing Pieces
The Secret History of Twin Peaks (book)
The Return (S3)
The Final Dossier (book)
Alright, here are some timecodes for FWWM, if you want to break it down into days (things get weird with the timeline):
Tue, Feb 9, 1988: 0:00:00-0:02:49; 1:28:30-1:29:18; 1:29:55-1:30:08; 1:30:10-1:30:53 (last three are flashbacks)
Wed, Feb 10, 1988: 0:03:04-0:19:26
Thu, Feb 11, 1988: 0:19:26-0:26:56
Fri, Feb 12, 1988: 0:31:16-0:33:47
Thu, Feb 16, 1989: 0:26:56-0:31:16
Fri, Feb 17, 1989: 0:33:47-0:46:45
Sat, Feb 18, 1989: 0:46:45-1:04:48
Sun, Feb 19, 1989: 1:40:47-1:42:15; 1:04:48-1:23:59
Mon, Feb 20, 1989: 1:23:59-1:34:09
Tue, Feb 21, 1989: 1:34:09-1:40:47
Wed, Feb 22, 1989: 1:42:15-1:46:19
Thu, Feb 23, 1989: 1:46:19-2:14:44
And scene numbers for TMP:
Tue, Feb 9, 1988: 21
Wed, Feb 10, 1988: 1; 2
Thu, Feb 11, 1988: 3; 4; 5
Fri, Feb 12, 1988: 6
Thu, Feb 16, 1989: 7
Fri, Feb 17, 1989: 8; 9; 10; 11
Sat, Feb 18, 1989: 12; 13; 14; 15
Sun, Feb 19, 1989: 16; 17; 18; 19
Mon, Feb 20, 1989: 20
Tue, Feb 21, 1989: 22; 23
Wed, Feb 22, 1989: 24; 25; 26
Thu, Feb 23, 1989: 27; 28; 29; 30; 31
Fri, Feb 24, 1989: 32
Tue, Mar 28, 1989: 33
February 9, 1988 includes a couple earlier, unspecified days.
7 notes
·
View notes