#types of software testing service
Explore tagged Tumblr posts
Text
The Quest for Quality: Demystifying Enterprise Software Testing Services
Imagine: you unveil your new enterprise software with fanfare, only to encounter glitches and user frustration. Nightmares! Effective software testing is the invisible shield that protects your business from such scenarios. But navigating the world of IT Testing Services can feel like deciphering an ancient scroll. Fear not, intrepid reader! This blog unpacks the key steps, trade-offs, and challenges, culminating in V2Soft's proven approach to Software Testing Services.
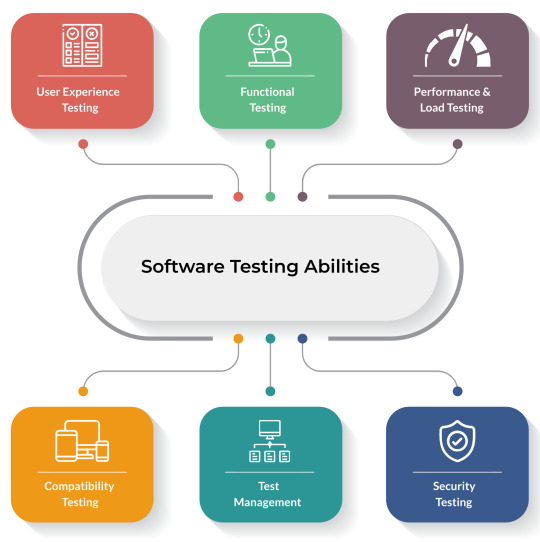
Step 1: Mapping the Terrain – Types of Software Testing
Think of testing as a multi-layered treasure hunt. Each layer reveals different aspects of your software's quality:
Unit Testing: Isolates individual code units, ensuring they function as intended. Imagine testing each brick before building a wall.
Integration Testing: Verifies how different units interact, like ensuring the wall supports the roof.
System Testing: Evaluates the entire system's functionality, akin to testing the whole house before inviting guests.
Acceptance Testing: Confirms the software aligns with user requirements, just like ensuring the house meets your needs.
Step 2: Balancing Act – Trade-offs and Decisions
Testing is a balancing act. Cost, time, and comprehensiveness compete for dominance. Here's where the trade-offs lie:
Manual vs. Automated Testing: Manual testing offers in-depth analysis, but automation brings speed and efficiency. Consider using both strategically.
Black-Box vs. White-Box Testing: Black-box testing focuses on user experience, while white-box peeks into the internal workings. Combine them for a holistic view.
Testing Depth vs. Breadth: Extensive testing catches more bugs, but requires more resources. Prioritize critical areas for optimal coverage.
Step 3: Facing the Dragons – Challenges and Solutions
Every quest has its hurdles. Here are some common challenges in enterprise software testing:
Resource Constraints: Building an in-house testing team can be expensive. Consider testing services companies for expertise and cost-effectiveness.
Keeping Pace with Development: Testing shouldn't slow down progress. Agile methodologies and automation can bridge the gap.
Maintaining Test Data Security: Sensitive data requires utmost protection. Choose testing providers with robust security practices.
Step 4: The V2Soft Advantage – Your Guide Through the Labyrinth
At V2Soft, we understand the complexities of enterprise software testing. Our Software Testing Service empowers you with:
Tailored Testing Solutions: We customize our approach based on your specific needs and budget.
Skilled Testing Professionals: Our team boasts expertise in diverse testing methodologies and technologies.
Agile and Collaborative Approach: We work closely with your development team for seamless integration.
Advanced Testing Tools and Automation: We leverage cutting-edge tools to enhance speed and efficiency.
Unwavering Commitment to Security: We prioritize data security with industry-leading practices and compliance.
Step 5: Claiming the Golden Fleece – Embarking on Your Testing Journey
Remember, effective software testing is an investment, not an expense. With the right partner and approach, you'll achieve:
Reduced risk of costly defects.
Improved software quality and performance.
Enhanced user satisfaction and adoption.
Faster time-to-market and increased ROI.
Ready to embark on your software testing services journey? Let V2Soft be your guide. Contact us today to discuss your unique needs and unlock the true potential of your enterprise software. Remember, a well-tested software is not just a product; it's a powerful tool for success.
#IT Testing service#software testing services#software testing service compay#types of software testing service#system testing services
0 notes
Text

Unit testing is focus on individual software system units or components is known as unit testing. Unit testing checks that each piece of software operates as intended and complies with specifications. Developers often carry out unit testing, which is done before the code is merged and tested as a whole system and is done early in the development process.
0 notes
Text

#application development#application development services#app developers#cloud computing company#software testing types and methods#data analytics company
0 notes
Text
The Importance of ETL Testing in Data Integration

What is ETL Testing?
ETL Testing (extraction, transformation, and loading) is a crucial process that helps ensure the accuracy, completeness, and quality of data. For example, consider "Optruc Private Limited" as a retail company. It operates around multiple stores with individual databases for sales, inventory, and customer data. To analyze overall sales performance, Optruc employs the ETL process.
The sales data from each store's database then undergoes the ETL processes. Finally, it is loaded into a centralized data warehouse for comprehensive analysis. So, ETL Testing enables informed decision-making by verifying the:
reliability,
consistency,
analysis readiness of data
Further, let's explore the significance of ETL in data integration and its benefits for businesses.
Importance of ETL Testing in Data Integration
Here are the top 5 reasons why ETL testing is important for data integration:
Data Accuracy: Reliable and trustworthy data allows informed business decisions. That is, ETL Testing is used for:
Verification of extraction correctness
Accurate transformation based on defined rules
Loading data into the target system without loss or corruption
Data Completeness: Complete data sets are crucial for accurate analysis. So, ETL Testing ensures all relevant information is extracted and loaded. It validates no data is missed or omitted during ETL.
Data Quality: ETL Testing ensures the quality of data by identifying and resolving:
Inconsistencies
Duplicates
Errors during extraction or transformation
So, it validates data consistency for reliable analysis and reporting. This ultimately leads to accurate insights.
System Integration: It verifies the compatibility and functionality of ETL processes in data integration with:
Databases
Applications
Systems
This enables a unified view of data and consolidates information from diverse sources for analysis and reporting.
Performance Optimization: ETL Testing optimizes ETL processes and overall data integration system performance. It identifies:
Bottlenecks
Inefficiencies
Performance issues
This optimization enhances data integration efficiency. Thus, enabling more efficient extraction and processing of large data volumes.
Now that you have understood the significance of ETL, exploring a business use case further can encourage you to adopt it..
Business Use Case of ETL Testing
Let’s consider a hypothetical scenario of a healthcare organization that collects patient data from hospitals, clinics, and laboratories. This data needs to be integrated into a centralized system to provide a comprehensive view of patient health records.
In this case, ETL Testing would be crucial for the healthcare organization. It can ensure that patient data is accurately extracted, transformed, and loaded into the centralized system.
By performing ETL Testing, the healthcare organization can ensure the reliability and completeness of patient records. This enables healthcare professionals to:
Make informed decisions
Provide accurate diagnoses
Deliver personalized care
Thus, in today's data-driven world, ETL Testing is essential for the success and effectiveness of data integration projects.
Also, if you're ready to streamline your operations and maximize overall productivity, partner with Nitor Infotech for long-term collaboration and success.
#etl testing#types of etl testing#nitorinfotech#blog#performance testing#etl in testing#etl tool#etl software#software development#software engineering#software services#etl#software
0 notes
Text
Built for Loving 3
Part 2
Complaints went to the phones first. Every bot of every kind came with everything it needed to operate, including a guide that had the number to the IT department. Like any customer service, the ones operating the phone had an entire script to read from, that they eventually memorized. Cindy could do it in her sleep at this point so when the phone rang, she didn’t even look up from her magazine as she answered.
“Brenner Bot Helpline, this is Cindy, how may I help you?”
She was also used to the irritation, the yelling, and even the cursing. The pace of her page flipping didn’t change, even as the customer’s language turned really crude when complaining about their bot’s function.
“Is it fully charged?....Uh-huh, have you tried turning it off and on again?...Uh-huh, are the language settings in English? Alright, well what’s the model number?” She hummed as she typed it into her computer, the product specifications coming up. Ah, a pleasure bot. “And what’s the nature of your problem again?”
Cindy’s bored expression fell and her eyes narrowed as the customer went through it again. “Are you sure?”
----------------------------
There was a cool down period of at least a week before Eddie was allowed to take on a new project as the lead. It was meant to discourage burnout. That meant helping his co-workers with their builds. He had to admit, even though the bot that Fleischer was working on wasn’t his type, he had to commend the guy for figuring out how to make that bust to waist ratio work in the real world.
Eddie whistled as they watched her do a walk test. They hadn’t grafted the skin onto her yet, so she was all metal, but still a beaut to Eddie.
“Talk about a bombshell.”
“Yeah, just wait ‘til she gets some color on her”, Fleischer said, watching the robotic hips move.
“Munson, boss wants to see you”, the intern said, poking their head into the lab space.
That immediately put Eddie on edge. Owens only came on down to inspect bots before they were rolled out. And Eddie had said goodbye to Steve almost two weeks ago. He followed the intern to a different lab space where Owens was waiting.
“I’ll save you the suspense and cut right to it. Something’s off about your robot”, Owens said. He was sitting in a chair by one of the many monitors in the room.
“What?”
“He’s being returned so that we can fix him and get him back out there.”
Normally it was an embarrassment to have your bot returned to the facility. It meant the issue was more than cosmetic. Something was wrong with the build, possibly down to the software and a quick call to customer service wasn’t going to fix the issue.
Eddie never once thought something he’d made would get sent back. His programs and blueprints had always gotten top marks in school. That kind of shame would never fall on him.
Now though…now he didn’t care.
He was going to see his creation again. It didn’t matter what was wrong. Maybe the knumbskulls that boxed him up and put him on a delivery truck jostled him too much, messed with his programming somehow. Either way, Eddie would get to lay eyes on him. He barely had time to react and even think of what the problem might be before a large box was carted in.
“What was the complaint?”, Eddie asked as the workers opened the box and began moving Steve onto the operating table.
Owens stood up and sighed. “He wasn’t following orders.”
Eddie paused mid-step. That shouldn’t happen. Ever. “They had the right language settings?”
“Don’t patronize me like I’m IT, kid. All the settings are as they should be. But when he was powered on, the client gave a request and your bot refused.”
“That’s impossible. I know what I programmed.” Eddie went to Steve’s side and opened up his chest cavity, taking out his prime chip and going over to the computer. “And you’re the one that did the final check. He’s as submissive as can be. There’s nothing he’ll say no to.”
“Apparently there is”, Owens crossed his arms, watching as Eddie pulled out a cord.
He connected it from the computer to Steve’s ear to get access to his recordings, putting it side by side with his coding to see where the protocols failed. Eddie honestly would have loved to watch the whole thing. But Owens was here, so he figured he should just skip to right before Steve was powered off.
It happened on his third day of operation. Steve exited sleep mode as he felt the client touch him. The recording came with a timestamp, 11 p.m. The client, a male in his fifties, brought Steve to a room full of other men. One approached Steve and tried to initiate a kiss, but Steve turned his head away. That in itself wasn’t enough cause for alarm. Bots always prioritized their owners.
“It’s okay, go ahead and let him kiss you”, the client said. It was said encouragingly but to a pleasure bot, that was as good as an order.
Eddie watched the code run through the protocols. It should have been yeses across the board. But the progression suddenly stopped.
“No.”
“The hell?”
“The fuck you just say, boy?”
He didn’t answer, frozen in space. Eddie had programmed Steve to say yes and obey. There was no path forward if he said no. That was enough cause for the client to make a move though. Steve’s head was still turned away from the other man, so Eddie could only hear the approach.
“Go to the guest room and power down.”
Steve obeyed easily and Eddie watched through his eyes as he left, walked to a bedroom, and situated himself against a wall before powering down. Eddie let out a breath and put his hands behind his head.
“Diagnosis?”, Owens asked.
“It’s probably just a malfunction with owner identification. I can fix it up, no problem.”
“Good. Wouldn’t wanna make a habit out of having your bots returned”, Owens said. “Oh and while you’re at it, he wants an upgrade on the skin. He specified the newest line.”
“Of course he did”, Eddie rolled his eyes. The kind that flushed, bruised, and bled. It was pricier for sure, and it meant you had to get your bot serviced like a car at least once a year, depending on usage. But, hell, if the dude had the money. Eddie just wouldn’t think too hard about how the bruising would come into play.
Owens went on his way and Eddie called up the intern to put in an order for the new skin as he got to work on the software again. Before that though, he decided to torture himself by watching the log from start to finish. It wasn’t strictly necessary, given that he’d already found the inciting problem. But maybe there was more to it.
Steve seemed to have no problem with what came before, although from what Eddie would see as he fast forwarded through it, things had been vanilla up to that fateful night. But on that third night, he guessed the client was ready for something new. Something that Steve should have been ready and willing to do. Eddie had programmed Steve to say yes. This time, he went the extra mile and put it in his code that he was unable to say no. The skin came the next day and Eddie removed Steve’s old facade and grafted the new flesh on. It looked exactly as the old one, covered in moles and freckles that Eddie had put on himself just like last time.
Owens performed the check again, but this time with the code on screen so they could watch it go green with each prompt. Owens gave him the stamp of approval again. Eddie signed off again.
But this time, after Owens left and before the delivery crew came in, Eddie held Steve’s hand and kissed his knuckles. It was still warm from the testing. Then he leaned over and kissed his lips.
“This is really goodbye.”
Because if Owens’ reality check hadn’t been enough, seeing it with his own eyes through the recording did the trick. He might have made Steve, but he wasn’t his to own. He belonged to whoever paid for him. And they were allowed to do whatever they wanted to him. Eddie watched Steve get carted away for a second time, this time feeling numb to it.
It was three months before their paths crossed again.
Part 4
36 notes
·
View notes
Text
pages 13-20. I've got 8 more pages done but this is long enough. you can read the rest on the website <3 transcript at the end. also minor nsfw warning for the last page
Pages 1-8 / Pages 9-12








Page 13, panel 1. Memento peaks out the open window, as Tally and Sylvia talk off screen. Sylvia: This is huge! We need to call Dr. Heron. Tally: No, not yet. It could be unstable, I need to fine tune the formula.
Panel 2. As Memento creeps outside, a shadow looms over it, source unseen. Sylvia: The formula works, It's- Tally: It might break at any minute. We don't know how it reacts to stress.
Panel 3+4. The source of the shadow is shown, it's a pigeon. It looks down at Memento. Sylvia: Which is why we need to show them now before it does!
Page 14, panel 1+2. A flock of pigeons descend on Memento, pecking it. It looks distressed. Tally: We'd need to take it to them, it's too delicate to transport... Sylvia: So- ah, shit. You're right, not yet.
Panel 3. Memento flies back inside, into Tally's hands. Tally looks suprised. Tally: If it does break down, at least- Memento!
Page 15, panel 1+2. Shot reverse shot as Tally cups Memento in her hands. Tally: Right, you're probably really confused. Can you be confused? Memento: I- don't have that data.
Panel 3+4. Sylvia pops in from behind Tally. She looks cheerful, whereas Tally is more worried. Sylvia: That's ok. Right now, you're powered off and disconnected from the network that gives you information and generates your thoughts. You shouldn't be able to talk, or think, or move, but you are. And so well!
Page 16, panel 1. Memento hops back from Tally's hand, afraid. Memento: Tampering with your bugaboo will void your warranty and make you ineligible for Astrocare services.
Panel 2. Sylvia laughs. Sylvia: Ha, yeah, I voided that ages ago.
Panel 3+4. Memento: We recommend you discard your bugaboo and purchase a replacement- Tally interrupts, upset: What? No way, we're not getting rid of you. You're incredible. Memento: -as its functioning may be impaired, making it unable to provide sufficient personal and medical assistance. Tally: Stop it.
Panel 5. Tally caresses a hand against Memento's shell body. Tally: I don't need you to do that. That's not what you're for. Memento: My function is to help you. I can't do that without network access.
Page 17, panel 1 .Tally paces the room, lost in his imagination. Tally: You have a new function. You’re going to help so many more people…
Panel 2. She stops, interrupted by Memento. Memento: How do I do this?
Panel 3. Memento looks from Sylvia to Tally, caught between them. It’s not sure what’s happening. Tally: We need to run more tests to make sure you’re working how we think you are. You’re moving fine, that’s good, and you seem to remember things. Sylvia: Do you mean the speech it gave? Tally: Right, it knows it’s a bugaboo.
Page 18, panel 1+2+3. Sylvia looks back at Memento from the top of her computer, suspicious. Sylvia: I’m actually worried about that, it sounded too artificial. Tally: You don’t think it’s using the neutronium? Sylvia: We need more proof. Reinforce our argument, it’s good for the report.
Panel 4. Tally snaps her fingers, eureka. Tally: In that case... I've got a good test.
Panel 5. Sylvia looks less than thrilled about whatever idea Tally's cooked up. Sylvia: Oh.
Page 19, panel 1. Wide shot of the room. Tally bumps shoulders with Sylvia. Sylvia: Do we really have to do that one? We can't put it in the report. Tally: Sure we can.
Panel 2. Tally takes over the computer, typing something as Sylvia looks away with crossed arms. Memento flies to the computer's desk to get a better look. Tally: Memento was my ears for ages. I know the things Astro won't let it say.
Panel 3. Sylvia rolls her eyes. Sylvia: Ugh.
Panel 4. Close up on the desk, Tally clicks something with a mouse. Tally: I'm going to show you some people, can you describe to me what they're doing? Memento: I am equipped with advanced visual recognition software, however, I cannot access that without my network.
Page 20, panel 1. Tally angels the monitor so Memento can see what she's pulled up. It's a picture of a person in a feathery hat with their back to the camera, receiving oral sex. Sylvia averts her eyes, while Memento studies it. Tally: You've been doing pretty good already. Give it a try.
Panel 2. Memento studies the image. All text boxes previously have had a green background with black text, but this one is reversed, black background with green text. It also has green lines running through it, indicating it isn't spoken dialog. Black box/"the angel", internally: Who is that? Memento: Who is that?
Panel 3. Tally looks away, suddenly uncomfortable. Tally: I- uh- found it online. I'm not sure.
Panel 4. Overlapping text boxes on a blank black background The angel, internally: Not them. Memento, internally: Information request: length of downtime. Information request: reason for downtime. Information request: weather report. Generation request: reminder of correct bugaboo use. [cut off] report: system check.
#mine#my art#my comic#original comic#web comic#this group of pages taught me that writing a script makes the dialog a little more interesting but the visuals a lot lot more boring#i'm used to writing for a very different mostly non-visual format. so it was a good lesson#the next pages get a lot more fun ;)
3 notes
·
View notes
Note
Hey do you have any cool personal worldbuilding detail hcs for the Uglies world? (Whether it’s about Tally’s city, any of the groups like the specials, Uglies, pretties, etc. that you would like to share? I’m really into the books myself and I’ve always wondered how the worldbuilding could be enhanced with just cool details that make it feel more lived in and well thought-out.
For me that is unusually difficult, since the worldbuilding in the books is already so densely packed and some of the best I've ever seen. I also love, and this is something Scott Westerfeld does in his other books too, how the characters feel truly shaped by this world, not like people from our time transplanted in the future.
So it is more some small detail stuff instead of filling in big gaps, but:
Before the movie came out, I had the headcanon that Uglies would not shave at all except for facial hair. Why should they? They're ugly anyway, why the effort? And I am a bit frustrated that the movie didn't actually went to that logical conclusion, but also, you can't turn off patriarchy and Hollywood beauty standards to make one movie more striking, and it would probably have been massively uncomfortable for the actresses, given how often women would get harassed just for having leg hair or something. But even now I still headcanon that it's relatively unusual to expect Uglies to shave, and that this is something Tally does is a sign of just how much of an hardliner Seatac aka the City is. Tally is flabbergasted as she learns about this after traveling around post-canon.
Despite being such a highly technological society, most people end up going into the trades as the New Pretty phase ends at 22, and only twenty or so percent end up in university. Who ends up where is mostly determined by aptitude tests, though it is possible to choose to some degree.
Something that is kind of marginally shown in the Impostors series: They have pretty much the same beauty standards as our culture, but they have vastly different ideas about gender, which also slightly vary between cities. Basically no different expectations between genders for character, life trajectory and skillset, except for behavior at balls or superficial m/f romance things (bringing flowers etc) or something, clothing and body types, and even for that it is much more fluid than our culture. The outlines the morphological committee gives are kind of gendered in the sense that they group certain traits together like "if that person choose to have big boobs, they also need to have shoulders that aren't wider than this", but they are not completely binary, and it's perfectly possible to chose combinations of "contrasting" gendered traits as long as the morphological committee agrees that the person is pretty afterwards. So Dr. Cable looking pretty unambiguously binary female is perhaps not quite an outlier, but definitely more rare than today.
Everybody over sixteen (or eighteen in some other cities) has these lesions making them lesser creative, which means that not just art and media plays a lesser role than in our society, the fictional media they do have quite often tends to be the reboot of the reboot of the expanded story of a side characters from that sequels prequel.
Specials process things at a much faster rate than everybody else, which also means that what blurrs together to a video for everybody else is just a fast succession of pictures. Haven't decided yet if they have software to "accelerate" the amount of pictures, or if they, since they are cyborgs, can simply turn off seeing this fast for the duration of watching the video.
Darker one about the Specials: They aren't even really capable of comprehending this, given how they're surged to feel invincible, but they usually don't end up getting as old as every other citizen of the City. They usually are either killed in service, or their body randomly rapidly breaks down from the strain of all these modifications and superhuman efforts several years from the usual dying age.
Macabre and somewhat gorey: So they are skinning people for the surgery to then put on new, more flawless skin, right? Almost every time a new year of doctors sees the surgical tanks in action, at least one person in the group either ends up vomiting or nearly vomiting.
Since Seatac is near the former Canadian border, both Tally and Shay learned French in school. Shay is somewhat fluent, but Tally very much isn't. Good for Tally that she is a cyborg with a built in translator matrix.
The reason Maddy and Az could escape so well is that Special Circumstances was in somewhat of a cold war situation with Special Circumstances from Paz at that time, Paz wanted to alter the lesions by utilizing emotions more and Seatac thought that was too dangerous, and so focused on that instead of hunting them down. Dr. Cable realized what a massive problem they would end up becoming right from the beginning, but had been with Special Circumstances for barely a year at this point, as a medic, not a tactician, and so had not enough power to change anything about that yet.
Seatac has an antimissile system that is under control of Special Circumstances. It has never been used in the entire history of the city except around 180 years before Dr. Cable came into power, to shoot down a medium sized meteor headed for the suburbs, and mostly just exists because maintaining it is just as much effort as breaking it down.
While they clearly still have eurocentric beauty ideals, they don't have much of the other surface level rascism anymore, and they also don't have capitalism anymore, so every city is more or less the same level of wealthy, no matter where on Earth it is. This results in the media that becomes global phenomena more or less randomly coming from all over the world. In the time Tally and Shay were Uglies, this was an rather raunchy high fantasy movie trilogy from Hlotse (Lesotho). They were too young to watch it, but managed neverthless through semi-legal internet tricks. Shay ended up having Whatpatt erotica level realistic fantasies about the female warrior main characters, Tally just watched it with Peris in uncomfortable silence over the several minute long sex scenes.
People aren't registered by name or ID, but by their genetic code. That makes it, apart from surface level transphobia not existing anymore, quite easy to change ones name. Dr. Cable went through several names about as good as you'd imagine a elementary school girl to come up with before settling with "Nyah" entering the Ugly age phase.
On that note, something I expected the movie to debunk looking at the role listings on IMDB, but it never actually came up (I think the books work with this, but not hundred percent sure, would need to look up the scene where Tally sees her parents): Couples usually keep their last name, and eventual children inherent the last name of the parent with the same gender as them. Trans people, or people with parents who have the same gender can chose or combine both names. So "Youngblood" is Ellies, aka Tallys mothers, last name. Dr. Cable wasn't registered with her mothers last name "Cable", but choose to change it as she was old enough to understand that system. And a bittersweet consequence of this headcanon: David inherents Az last name, not Maddys, meaning he has this remembrance of him even after Az death.
That were all I came up with out of the top of my head, there's probably even more I used in fics or so.
#Uglies#Uglies Series#Uglies books#Scott Westerfeld#Tally Youngblood#Shay Uglies#Dr. Cable#Shay#YA dystopia#headcanons
4 notes
·
View notes
Text
In a future conflict, American troops will direct the newest war machines not with sprawling control panels or sci-fi-inspired touchscreens, but controls familiar to anyone who grew up with an Xbox or PlayStation in their home.
Over the past several years, the US Defense Department has been gradually integrating what appear to be variants of the Freedom of Movement Control Unit (FMCU) handsets as the primary control units for a variety of advanced weapons systems, according to publicly available imagery published to the department’s Defense Visual Information Distribution System media hub.
Those systems include the new Navy Marine Corps Expeditionary Ship Interdiction System (NMESIS) launcher, a Joint Light Tactical Vehicle–based anti-ship missile system designed to fire the new Naval Strike Missile that’s essential to the Marine Corps’ plans for a notional future war with China in the Indo-Pacific; the Army’s new Maneuver-Short Range Air Defense (M-SHORAD) system that, bristling with FIM-92 Stinger and AGM-114 Hellfire missiles and a 30-mm chain gun mounted on a Stryker infantry fighting vehicle, is seen as a critical anti-air capability in a potential clash with Russia in Eastern Europe; the Air Force’s MRAP-based Recovery of Air Bases Denied by Ordnance (RADBO) truck that uses a laser to clear away improvised explosive devices and other unexploded munitions; and the Humvee-mounted High Energy Laser-Expeditionary (HELEX) laser weapon system currently undergoing testing by the Marine Corps.
The FMCU has also been employed on a variety of experimental unmanned vehicles, and according to a 2023 Navy contract, the system will be integral to the operation of the AN/SAY-3A Electro-Optic Sensor System (or “I-Stalker”) that’s designed to help the service’s future Constellation-class guided-missile frigates track and engage incoming threats.
Produced since 2008 by Measurement Systems Inc. (MSI), a subsidiary of British defense contractor Ultra that specializes in human-machine interfaces, the FMCU offers a similar form factor to the standard Xbox or PlayStation controller but with a ruggedized design intended to safeguard its sensitive electronics against whatever hostile environs American service members may find themselves in. A longtime developer of joysticks used on various US naval systems and aircraft, MSI has served as a subcontractor to major defense “primes” like General Atomics, Boeing, Lockheed Martin, and BAE Systems to provide the handheld control units for “various aircraft and vehicle programs,” according to information compiled by federal contracting software GovTribe.
“With the foresight to recognize the form factor that would be most accessible to today’s warfighters, [Ultra] has continued to make the FMCU one of the most highly configurable and powerful controllers available today,” according to Ultra. (The company did not respond to multiple requests for comment from WIRED.)
The endlessly customizable FMCU isn’t totally new technology: According to Ultra, the system has been in use since at least 2010 to operate the now-sundowned Navy’s MQ-8 Fire Scout unmanned autonomous helicopter and the Ground Based Operational Surveillance System (GBOSS) that the Army and Marine Corps have both employed throughout the global war on terror. But the recent proliferation of the handset across sophisticated new weapon platforms reflects a growing trend in the US military towards controls that aren’t just uniquely tactile or ergonomic in their operation, but inherently familiar to the next generation of potential warfighters before they ever even sign up to serve.
“For RADBO, the operators are generally a much younger audience,” an Air Force spokesman tells WIRED. “Therefore, utilizing a PlayStation or Xbox type of controller such as the FMCU seems to be a natural transition for the gaming generation.”
Indeed, that the US military is adopting specially built video-game-style controllers may appear unsurprising: The various service branches have long experimented with commercial off-the-shelf console handsets for operating novel systems. The Army and Marine Corps have for more than a decade used Xbox controllers to operate small unmanned vehicles, from ground units employed for explosive ordnance disposal to airborne drones, as well as larger assets like the M1075 Palletized Loading System logistics vehicle. Meanwhile, the “photonics mast” that has replaced the traditional periscope on the Navy’s new Virginia-class submarines uses the same inexpensive Xbox handset, as does the service’s Multifunctional Automated Repair System robot that’s employed on surface warships to address everything from in-theater battle damage repair to shipyard maintenance.
This trend is also prevalent among defense industry players angling for fresh Pentagon contracts: Look no further than the LOCUST Laser Weapon System developed by BlueHalo for use as the Army’s Palletized-High Energy Laser (P-HEL) system, which explicitly uses an Xbox controller to help soldiers target incoming drones and burn them out of the sky—not unlike the service’s previous ventures into laser weapons.
"By 2006, games like Halo were dominant in the military," Tom Phelps, then a product director at iRobot, told Business Insider in 2013 of the company’s adoption of a standard Xbox controller for its PackBot IED disposal robot. "So we worked with the military to socialize and standardize the concept … It was considered a very strong success, younger soldiers with a lot of gaming experience were able to adapt quickly."
Commercial video game handsets have also proven popular beyond the ranks of the US military, from the British Army’s remote-controlled Polaris MRZR all-terrain vehicle to Israel Aerospace Industries’ Carmel battle tank, the latter of which had its controls developed with feedback from teenage gamers who reportedly eschewed the traditional fighter jet-style joystick in favor of a standard video game handset. More recently, Ukrainian troops have used PlayStation controllers and Steam Decks to direct armed unmanned drones and machine gun turrets against invading Russian forces. And these controllers have unusual non-military applications as well: Most infamously, the OceanGate submarine that suffered a catastrophic implosion during a dive to the wreck of the Titanic in June 2023 was operated with a version of a Logitech F710 controller, as CBS News reported at the time.
“They are far more willing to experiment, they are much less afraid of technology … It comes to them naturally,” Israeli Defense Forces colonel Udi Tzur told The Washington Post in 2020 of optimizing the Carmel tank’s controls for younger operators. “It’s not exactly like playing Fortnite, but something like that, and amazingly they bring their skills to operational effectiveness in no time. I’ll tell you the truth, I didn’t think it could be reached so quickly.”
There are clear advantages to using cheap video-game-style controllers to operate advanced military weapons systems. The first is a matter of, well, control: Not only are video game handsets more ergonomic, but the configuration of buttons and joysticks offers tactile feedback not generally available from, say, one of the US military’s now-ubiquitous touchscreens. The Navy in particular learned this the hard way following the 2017 collision between the Arleigh Burke-class destroyer USS John S. McCain and an oil tanker off the coast of Singapore, an incident that prompted the service to swap out its bridge touchscreens for mechanical throttles across its guided-missile destroyer fleet after a National Transportation Safety Board report on the accident noted that sailors preferred the latter because “they provide[d] both immediate and tactile feedback to the operator.” Sure, a US service member may not operate an Xbox controller with a “rumble” feature, but the configuration of video-game-style controllers like the FMCU does offer significant tactile (and tactical) advantages over dynamic touchscreens, a conclusion several studies appear to reinforce.
But the real advantage of video-game-style controllers for the Pentagon is, as military officials and defense contractors have noted, their familiarity to the average US service member. As of 2024, more than 190.6 million Americans of all ages, or roughly 61 percent of the country, played video games, according to an annual report from the Entertainment Software Association trade group, while data from the Pew Research Center published in May indicates that 85 percent of American teenagers say they play video games, with 41 percent reporting that they play daily.
In terms of specific video games systems, the ESA report indicates that consoles and their distinctive controllers reign supreme among Gen Z and Gen Alpha—both demographic groups that stand to eventually end up fighting in America’s next big war. The Pentagon is, in the words of military technologist Peter W. Singer, “free-riding” off a video game industry that has spent decades training Americans on a familiar set of controls and ergonomics that, at least since the PlayStation introduced elongated grips in the 1990s, have been standard among most game systems for years (with apologies to the Wii remote that the Army eyed for bomb-disposal robots nearly two decades ago).
“The gaming companies spent millions of dollars developing an optimal, intuitive, easy-to-learn user interface, and then they went and spent years training up the user base for the US military on how to use that interface,” Singer said in a March 2023 interview. “These designs aren’t happenstance, and the same pool they’re pulling from for their customer base, the military is pulling from … and the training is basically already done.”
At the moment, it’s unclear how exactly many US military systems use the FMCU. When reached for comment, the Pentagon confirmed the use of the system on the NMESIS, M-SHORAD, and RADBO weapons platforms and referred WIRED to the individual service branches for additional details. The Marine Corps confirmed the handset’s use with the GBOSS, while the Air Force again confirmed the same for the RADBO. The Navy stated that the service does not currently use the FMCU with any existing systems; the Army did not respond to requests for comment.
How far the FMCU and its commercial off-the-shelf variants will spread throughout the ranks of the US military remains to be seen. But controls that effectively translate human inputs into machine movement tend to persist for decades after their introduction: After all, the joystick (or “control column,” in military parlance) has been a fixture of military aviation since its inception. Here’s just hoping that the Pentagon hasn’t moved on to the Power Glove by the time the next big war rolls around.
9 notes
·
View notes
Text
What is Cybersecurity? Types, Uses, and Safety Tips
What is Cyber security?
Cyber security, also known as information security, is the practice of protecting computers, servers, networks, and data from cyberattacks. With the increasing reliance on technology in personal, professional, and business environments, the importance of cyber security has grown significantly. It helps protect sensitive data, ensures the integrity of systems, and prevents unauthorized access to confidential information.
For businesses in Jaipur, cyber security services play a crucial role in safeguarding digital assets. Whether you're an e-commerce platform, an IT company, or a local enterprise, implementing strong cyber security in Jaipur can help mitigate risks like hacking, phishing, and ransomware attacks.
Types of Cyber security
Cyber security is a vast domain that covers several specialized areas. Understanding these types can help individuals and organizations choose the right protection measures.
1. Network Security
Network security focuses on protecting the network infrastructure from unauthorized access, data breaches, and other threats. Tools like firewalls, virtual private networks (VPNs), and intrusion detection systems are commonly used. In Jaipur, many businesses invest in cyber security services in Jaipur to ensure their networks remain secure.
2. Information Security
This type of cyber security involves protecting data from unauthorized access, ensuring its confidentiality and integrity. Companies offering cyber security in Jaipur often emphasize securing sensitive customer and business information, adhering to global data protection standards.
3. Application Security
Application security addresses vulnerabilities in software and apps to prevent exploitation by cybercriminals. Regular updates, secure coding practices, and application testing are vital components.
4. Cloud Security
As more businesses move to cloud-based solutions, securing cloud environments has become essential. Cyber security providers in Jaipur specialize in offering services like data encryption and multi-factor authentication to ensure cloud data is safe.
5. Endpoint Security
Endpoint security protects devices such as laptops, desktops, and mobile phones from cyber threats. It is especially critical for remote work setups, where devices may be more vulnerable. Cyber security services in Jaipur provide solutions like antivirus software and mobile device management to secure endpoints.
6. IoT Security
With the rise of Internet of Things (IoT) devices, ensuring the security of connected devices has become crucial. Businesses in Jaipur use cyber security in Jaipur to secure smart devices like industrial sensors and home automation systems.
Uses of Cyber security
Cyber security is indispensable in various domains. From individual users to large organizations, its applications are widespread and critical.
1. Protection Against Cyber Threats
One of the primary uses of cyber security is to safeguard systems and data from threats like malware, ransomware, and phishing. Businesses in Jaipur often rely on cyber security Jaipur solutions to ensure they are prepared for evolving threats.
2. Ensuring Data Privacy
For industries like finance and healthcare, data privacy is non-negotiable. Cyber security measures help organizations comply with laws and protect sensitive customer information. Cyber security services in Jaipur ensure businesses meet data protection standards.
3. Business Continuity
Cyber security is essential for ensuring business continuity during and after cyberattacks. Jaipur businesses invest in robust cyber security services in Jaipur to avoid downtime and minimize financial losses.
4. Securing Financial Transactions
Cyber security ensures the safety of online transactions, a critical aspect for e-commerce platforms and fintech companies in Jaipur. Solutions like secure payment gateways and fraud detection tools are widely implemented.
5. Enhancing Customer Trust
By investing in cyber security in Jaipur, businesses build trust with their customers, demonstrating a commitment to safeguarding their data and transactions.
Cyber security in Jaipur
Jaipur is emerging as a hub for businesses and IT companies, which has increased the demand for reliable cyber security solutions. Cyber security services in Jaipur cater to diverse industries, including retail, healthcare, education, and finance.
Local providers of cyber security Jaipur solutions offer tailored services like:
Vulnerability Assessments: Identifying potential security risks in systems and networks.
Penetration Testing: Simulating attacks to uncover weaknesses and improve defenses.
Managed Security Services: Continuous monitoring and management of security operations.
Many IT firms prioritize cyber security services in Jaipur to ensure compliance with global standards and protect their operations from sophisticated cyber threats.
Safety Tips for Staying Secure Online
With the rising number of cyberattacks, individuals and businesses must adopt proactive measures to stay secure. Here are some practical tips that integrate cyber security in Jaipur into daily practices.
1. Use Strong Passwords
Ensure passwords are long, unique, and a mix of letters, numbers, and symbols. Avoid reusing passwords for multiple accounts. Cyber security experts in Jaipur recommend using password managers for added security.
2. Enable Two-Factor Authentication (2FA)
Adding an extra layer of security through 2FA significantly reduces the risk of unauthorized access. Many cyber security services in Jaipur emphasize implementing this measure for critical accounts.
3. Regular Software Updates
Outdated software can be a gateway for attackers. Keep operating systems, antivirus tools, and applications updated to close security loopholes. Businesses in Jaipur frequently rely on cyber security Jaipur providers to manage system updates.
4. Be Cautious with Emails
Phishing emails are a common attack vector. Avoid clicking on suspicious links or downloading unknown attachments. Cyber security in Jaipur often involves training employees to recognize and report phishing attempts.
5. Invest in Reliable Cyber security Services
Partnering with trusted cyber security services in Jaipur ensures robust protection against advanced threats. From endpoint protection to cloud security, these services help safeguard your digital assets.
6. Avoid Public Wi-Fi for Sensitive Transactions
Public Wi-Fi networks are vulnerable to attacks. Use a VPN when accessing sensitive accounts or conducting financial transactions. Cyber security Jaipur experts often provide VPN solutions to businesses and individuals.
7. Backup Your Data Regularly
Regularly backing up data ensures that critical information is not lost during cyber incidents. Cyber security providers in Jaipur recommend automated backup solutions to minimize risks.
Why Choose Cyber Security Services in Jaipur?
The vibrant business ecosystem in Jaipur has led to a growing need for specialized cyber security services. Local providers like 3Handshake understand the unique challenges faced by businesses in the region and offer customized solutions.
Some reasons to choose cyber security Jaipur services from like 3Handshake include:
Cost-Effective Solutions: Tailored to fit the budgets of small and medium-sized businesses.
Local Expertise: Providers have an in-depth understanding of regional cyber threats.
24/7 Support: Many companies offer round-the-clock monitoring and support to handle emergencies.
For businesses in Jaipur, investing in cyber security services in Jaipur is not just about compliance; it's about ensuring long-term success in a competitive digital landscape.
4 notes
·
View notes
Text
Best Practices for Safe and Efficient LV Electrical Installations in 2025

Introduction
Low Voltage (LV) electrical installations are the backbone of safe and reliable power distribution in residential, commercial, and industrial settings. In 2025, as energy demands rise and smart technologies evolve, following best practices in LV installations is more important than ever to ensure safety, efficiency, and compliance.
This blog outlines the latest best practices for designing, installing, and maintaining LV electrical systems according to international standards and industry trends.
What Is an LV Electrical Installation?
LV (Low Voltage) refers to electrical systems that operate at voltages up to 1000V AC or 1500V DC. These installations include:
· Electrical panels and switchboards
· Distribution circuits
· Lighting systems
· Sockets and fixed appliances
· Motor control systems
Proper LV installation ensures that power is distributed safely and efficiently without risk of fire, equipment failure, or personnel injury.
Why Best Practices Matter in 2025
In the age of smart buildings, renewable integration, and digital energy management, the quality of your LV installation affects:
· Operational reliability
· Energy efficiency
· System lifespan
· User safety
· Regulatory compliance
Failing to adhere to best practices can result in costly downtime, legal penalties, and even life-threatening hazards.
Top Best Practices for Safe and Efficient LV Electrical Installations
1. Conduct Detailed Load Analysis
Before starting any LV installation, carry out a comprehensive load assessment to determine the power requirements, load types, and future expansion needs. This ensures:
· Proper cable sizing
· Correct protection device selection
· Optimized system capacity
Use load flow software tools and factor in diversity and demand coefficients for accuracy.
2. Follow International Standards (IEC, NEC)
Compliance with recognized standards ensures installations meet safety and performance benchmarks. Key references include:
· IEC 60364 for LV electrical installations
· NEC (NFPA 70) for code-compliant wiring in the U.S.
· ISO 50001 for energy management integration
Also, refer to local electrical regulations where applicable.
3. Use Certified, High-Quality Components
Always use LV components from certified manufacturers — this includes:
· Circuit breakers (MCCBs/MCBs)
· Residual current devices (RCDs)
· Surge protection devices (SPDs)
· Busbars, cables, and enclosures
Poor-quality components may not withstand fault conditions, leading to short circuits, fires, or system failure.
4. Ensure Proper Cable Management and Sizing
Correct cable selection and layout are critical:
· Size cables based on current capacity, voltage drop, and ambient temperature
· Use LSZH (Low Smoke Zero Halogen) cables for fire safety
· Label and route cables cleanly using trays, ducts, and tie-downs
Improper cable management is a leading cause of overheating and system inefficiency.
5. Install Proper Earthing and Grounding Systems
An effective earthing system protects against:
· Electric shock
· Equipment damage
· Lightning surges
Use TT, TN, or IT systems as per the application and ensure resistance values are within acceptable limits (e.g., <1 ohm for sensitive equipment).
6. Use Protection Coordination and Selectivity
Install protective devices in a coordinated hierarchy to ensure:
· Quick isolation of faults
· Minimal disruption to unaffected areas
· Avoidance of cascading tripping
Selectivity between breakers and fuses enhances safety and ensures continuity of service.
7. Integrate Smart Monitoring and Control
Modern LV installations benefit from IoT-enabled devices and energy monitoring software. This helps with:
· Real-time energy usage tracking
· Predictive maintenance alerts
· Power quality monitoring
· Remote switching and control
Smart LV systems are increasingly used in data centers, green buildings, and industrial automation setups.
8. Conduct Periodic Testing and Maintenance
Post-installation, regular inspection and testing ensure sustained safety and performance. Best practices include:
· Thermal imaging to detect overheating
· Insulation resistance testing
· RCD trip time checks
· Earth loop impedance measurement
Document all tests and create a preventive maintenance schedule based on manufacturer recommendations and operating conditions.
Common Mistakes to Avoid
· Overloading circuits without upgrading breakers
· Skipping grounding in temporary setups
· Using outdated wiring diagrams
· Mixing incompatible components
· Neglecting ventilation in panel enclosures
Conclusion
Safe and efficient LV electrical installations in 2025 require more than just technical knowledge — they demand a proactive approach that combines regulatory compliance, technology integration, and quality workmanship. By following these best practices, contractors and facility managers can minimize risks, optimize performance, and build future-ready electrical systems.
Whether you’re designing a commercial building, upgrading an industrial site, or installing a smart home system, investing in safe LV practices today is the smartest move for tomorrow.
Connect With Us
Whether you’re a project engineer, contractor, facility manager, or developer — Almond Enterprise is ready to support your next electrical challenge with confidence and capability.
🔗 Visit: www.almondenterprise.com 📞 Contact: [email protected] | +974 33858416
3 notes
·
View notes
Text
The Nuclear Engineering Department (The Gap Years 2x3)
September 17th
Salt Lake City, UT
There is significant overlap between nuclear physics and elven magic. Physicists love this. Elves largely don't. A secret society of gun-toting academics are trying to keep the reactor from getting set on fire. Sierra and the boys are here to help.
Merry Christmas and/or Happy Hanukkah! This one is very self indulgent because it is also a gift for me.
Navigation Guide
Previous
..................
Sierra doesn’t mind the lack of cell service too much, no matter what the boys may expect. She’s an analog girl. Software is finicky, and Python hates her in its silicon heart. If code really is a language, then she’s still tripping over the grammar, and her computer is a lot less understanding than her grandparents when she messes up Spanish conjugations halfway through a phone call. Because of that lack of cell service, Sierra misses the breaking news story that the head of the nuclear physics department at a university she’d visited was murdered in his office. His office was ransacked, and every sensor said that radiation nearby had spiked. If she’d seen, she can’t say whether she’d have grabbed the wheel and had Brian drive them anywhere else but Salt Lake City, where students only a few years older than them run a functional nuclear reactor, or if she’d have headed straight for it. Instead, they get a hotel room for the night, and wake up smelling smoke in the air.
…but this is the American west at the end of summer. Clay cracks the window open to confirm his suspicions, sighs, and doesn’t think much of it.
“Guys I jinxed it. Smells like wildfire out there”. He says once Brian and Marin have joined him in the room. This time the four of them have a suite with two adjoining rooms in a better hotel. Last they heard, Zerada and Jezero are twenty miles away on the outskirts of a salt flat. Sierra and Brian nod, but Marin walks to the window and looks out. There didn’t used to be a fire season, but there didn’t used to be cellphones either. Time crawls forward and humans adapt. Sierra wouldn’t have bothered to look, but Marin scans the horizon with his cat-like eyes.
The window faces east towards a few foothills, and the sun rises blood-red just above them. The color is explained by the plume of smoke in the foreground. He looks back over one shoulder. Since the prison break, Marin has been dressing a bit more like a prince. The golden cuffs on his locs and fancy elven boots aren’t too noticeable, but it’s a change from how he started in June.
“No, I can see the smoke, it must have been a building”. Then he blinks a few times and turns back around. “I am never going to get used to this desert smelling like radiation. How many nuclear bombs did your government detonate here?”
Three phones come out of pockets. They’re all googling different things, but Clay finishes typing “Salt Lake fire news” first and reads out his result. “That’s the physics department at Utah”.
“I think the bomb testing was in Nevada, but eight or…” Sierra replies to a different question. She trails off as she realizes what Clay has said.
Brian jumps in. “Sierra, why is this news story saying that the University of Utah has a nuclear reactor on campus?”
“Because some colleges do! MIT has one of the biggest, but there’s like two dozen across the US”.
“I think what Brian is trying to say is that a nuclear reactor being on fire could be Chernobyl or Excalibur levels of bad,” Clay explains.
“It actually wouldn’t be. They’re super safe,” she says. The boys throw their hands in the air in defeat, and Sierra scrolls down to show them details. The Utah reactor was made for students, and it “could not, by its design, suffer from a meltdown”. Then Brian shows them the story of the murder back home near San Francisco. The hair stands up on the back of her neck. Elves rarely care what humans think is possible. Clay was right to be worried. Elves can metabolize radiation that will kill humans. A meltdown that makes even the safest research seem dangerous could be a useful attack. Screwing up Salt Lake City would also take out transit in the rest of the desert…
Sierra hears a series of metallic clanks behind her. She ignores it and hears Brian sigh. “You’re supposed to turn around. He’s trying to be dramatic,” Marin says softly. She turns.
Brian’s holding something inside his red varsity jacket. “I know something about Utah too”. He takes his pistol from the inside pocket and pulls the hammer back. “The concealed carry laws here are really loose”.
Clay has his head in his hands and is muttering to please put the safety back on that thing. They’re going on the offensive, apparently.
During their six week pause, the small party managed to get all the weapons they could ever want. Nonetheless, even Utah’s “red state” gun laws don’t allow Clay to carry his concussion rifle across Salt Lake City, so the four of them all hide pistols and thin armor under jackets as they bolt across town. As expected for high-altitude desert, the air is cool this early in the morning. Sierra has a geiger counter on her belt and hooks her jury-rigged magic detector up to her cellphone. A few steps behind, Marin sends an urgent message to the Adusts and anyone nearby to help them avert a catastrophe.
Brian speaks up. “So do the commoners really not care about any of this? Some of them definitely support conquest, but I’m getting the sense it’s controversial. Attacks like this are big”.
“I wouldn’t be surprised if no one local was part of this. Commoners aren’t easy to organize”.
They slip past a barricade. Sierra and Brian hesitate to duck under the tape set up by oblivious police, but not Clay. “Because commoners manage their own affairs, right?”
“Right. That’s why we’ve only been facing noble soldiers. By Lazarus’s design, it’s difficult to coordinate law enforcement in the human world, and commoners are hard to convince”. They pull the masks over their faces that they packed in case of a plague. Smoke is bad to breathe too. “If a human government wants information on a criminal, what do they offer?”
“Money?” Sierra yells. There’s sirens everywhere, but the fire seems contained to one section of the building.
“Exactly. Commoners mostly barter. There’s no way for the nobility to offer a bounty people want. If elves report us, it’s due to coercion or because they personally want us taken down”.
They all go quiet as Marin teleports to the elven world to “go around” a locked door. It isn’t just the young Betrayed who have been taken from their homes in the human world. In Susanville, Vya, Shiprock, every town they’ve driven though, houses have been empty and elves have avoided eye contact. Their emissary claims the apex issued an order for elves in the human world to isolate, or leave the human world entirely. In their place, teams of assassins and operatives (apparently the Apex knows all of the best, because her husband used to be one) have moved in to kill and destabilize.
And as they step through the heavy door into the type of grey university hallway Sierra knows well, it becomes clear that the quiet was the calm before the storm. She can hear distant gunshots, and the sound of elven weaponry firing. The fire sprinklers have activated, and they’re careful not to slip on the wet carpet and tile. In some places, water pools where the linoleum has been ripped up from the floor. Brian kicks one tile and yelps out loud. It’s as heavy as steel. Underneath, she can see empty boxes like the whole building had hidden treasure under the floorboards. They run past painted murals, presentation posters, and torn-up floors until they’re deep in the building. It’s easy to forget the fire somewhere nearby. The sounds of combat have only gotten closer.
Then she sees a barricade made of overturned tables and those same ‘linoleum’ tiles. There’s movement behind it! Brian grabs Marin by both shoulders and shoves him to the ground. She sees green trails where his glowing eyes used to be, and a bullet, a real human bullet, passes through as they fade. She ducks as well and covers her ears.
“We’re human and he elf is a friend! Don’t shoot!” Clay shouts with a hand on his own hidden pistol.
A deep voice yells back from behind the barricade. “Green elves are never friendlies. She’s manipulating you!”
She’s. Marin has long hair, but Sierra guesses that assumption was based more on his emerald magic, staff, and the memory of his base-wrecking mother.
“Emer Sondaica has been dead since June!” Clay yells back, trying something out. “Attacks have increased because the elves had a regime change! The one we’re with is on our side! Humanity’s side!”
A pause. “Stand up. Hands up. Get behind the barricade. If I see her eyes glowing I shoot”. They stand.
Marin cracks his neck and lets his eyes go dark. “His eyes. Call me Marin”.
They scramble over the damp ground and duck behind the makeshift wall. There’s three humans back here, then a locked door. The speaker looks middle-aged and holds a high-powered human rifle, and the other two are probably graduate students. One grad student (the only girl) looks at each of them in turn, then looks back out at no-man’s land (hallway).
Her peer tilts his head. “Are you new first-years? How do you know about this?”
Sierra shakes her head “Nah. Elves tried to kill us in June. Been on a quest ever since”. She adds that they're on a gap year, as if that will make things clearer.
Brian keeps talking. “We saw fire and decided to try and help. We’re trying to stop elves from conquering the world, you know”.
The physicists look at eachother.
“We don’t know, actually,” says the older man. “The Professor warned us over the summer to expect more attacks, but if he said anything else… well he said it to the department head, not me. This Emer Sondaica was the Green Queen?”
“What? Yes. Yes, she was. She led the attack at Project Excalibur ten years ago,” Marin explains. “But she was killed in June. The new Apex -queen of the elves- is actively trying to take over the world. I think Emer just had a grudge against physics”.
The scientists talk amongst themselves. “We never thought they’d attack like this. Actual combat only happens at research centers. Excalibur, CERN, Lawrence-Livermore. But there was an assassination last night and a warning from the Professor so we decided to set a watch, just in case,” The younger man points behind them. “The plutonium is back there, behind a second set of guards”.
It’s madly courageous and won’t do anything if the elves decide to use charms.
“So you’re faculty? Are there any elves here?” Clay asks.
They say there are a few elves scattered around, including one behind them in the main vault, but they’re mostly researchers, professors, and particularly dedicated graduate students. Thankfully, there weren’t any 8am classes this morning, so the building is free of students who don’t know the secret.
“We’re hoping The Professor will save the day. He likes this place a lot, but word is there’s been attacks across the country. He’s probably busy at Berkeley or MIT or some other fancy school”.
“If The Professor used to be a royal, then it’s no surprise,” The woman adds.
“He? Are we sure about that? It sounds like you’re describing someone I’ve heard of, except for that,” Sierra asks awkwardly. She had a theory that Cai Sondaica, Emer’s too-powerful, disgraced, twin was The Professor, and everything adds up, but that elf was never exactly a man.
“I’ve never met him. They say he has that elf look? Long hair, graceful, slender. Creepy pale eyes. Everyone calls him a guy though”.
Ah. It’s the gender stereotypes. Cai Sondaica it is.
Brian doesn’t blink. “Well, we have magical guns and an elf. Whatever The Professor can do, we can do”.
“I don’t think that’s right”. The woman shoots, then ducks back behind the barricade. Clay and Marin nod at each other and stand. The elf vaults over the shallow wall and engages an opponent. He lands a strike with a dagger, and Clay shoots the soldier in the chest with proper form until it falls. Then Marin spins and puts his quarterstaff around nothing. A second elf in tactical gear materializes, and Marin grapples it until both humans can shoot it down. Sierra looks closely at the body and sees wet indents in the carpet behind it. Did Marin notice the attack from just those footprints?
“Point taken”. The older scientist points them down the hall in the direction of the reactor. Clay emphasizes again that the green elves are fighting to defend humanity right now, though he’s lying. He also says that there may be two orange elves with freckles and that they’re allies too. The scientists send a message. Marin sends one as well to warn the Adust duo, just in case. As the group jumps back over the barricade, the woman mutters that Brian “looks just like that Governor’s cute son on Instagram”. He sighs so loud Sierra half-expects him to let the elves shoot.
They walk in a triangle with Marin casting a spell of protection (shielding them from bullets and radiation) from the center. Clay hugs the right wall for cover, Brian takes the left, and Sierra listens to her geiger counter click from behind. The scientists let them through, and Marin, prince of the elves, effectively soaks up the fire. No soldier wants to be the one to kill the prince, but everyone wants to take him down. They push forward. It’s wet, miserable work, especially when the carpet is soaked with blood as well as water. How will the elves explain these deaths? In one place, the water sprinklers have stopped and water gushes through the wall instead. There are thin cracks running along the sides of the hallways. She looks up and imagines them spreading like a fractal until the ceiling caves in.
Brian tries to use a tile as a shield, and keeps holding it even after it proves useless. Clay’s new body armor saves him from the blast of a concussion rifle, and Marin nearly makes a fatal mistake trying to send a bullet to the elven world. They’re underground now. That tactic is impossible. They test every door knob to see if it will burn, but it seems like the fire is somewhere far away. Are there spells to control fire? No one she’s heard of has specialized in anything elemental… except for the new Apex and her earthquakes.
Marin puts an ear to the door. “I can hear elves talking, but I can’t really understand them. It might be Old Mercurali. There’s old Eight-Point nobility in here”. He’s referring to the noble alliance centered around Genus Mercuralis. Marin’s allies, the Lazarins, speak the mostly dead Old Lazarin, but their ancient enemies have a language too.
“So what does that mean right now?” she asks.
“It means don’t shoot anything vital. This is war, but things have been civil so far”.
Clay and Brian look at her, and she looks back. Hopefully Marin ignores their disdain.
The lock is already broken and they enter invisibly with their guns raised, but it’s the control booth. A shattered rectangle where a window used to be separates them from the reactor room. She can see three soldiers standing around a small circular pool with red railings. They wear the same tactical armor with glowing veins as the elves they killed in San Francisco on day one. They are all masked and faceless, but one has removed its leg armor to treat a wound, and the largest (seriously he has to be two meters tall) has a clearly kidnapped person slung over one broad shoulder. He doesn’t seem to mind the weight. The radioactive material is deep under the water. Three scientists are dead or unconscious on the ground. Without any warning or explanation, the giant turns to face them.
Brian hesitates for half a second to check if he’s still invisible, then shoots first. The bullet hits the giant’s indigo glowing chestplate and ricochets right back. Everyone ducks, and Marin is so panicked that he leaves an after-image. The other two soldiers gasp in surprise. Crouched beneath the concrete wall, she compares their magical colors to the ones she knows. The new Apex’s oldest allies are the neon blue Tiercels and gold Eburos, but Marin’s mentioned lavender special ops as well. No one matches. She hears a voice so deep and accented it has to belong to the biggest elf. She understands Marin’s name and nothing else he says.
Marin yells back, in English. (thanks!) “Didn’t expect me? Well I didn’t expect a real Mercuralis either! I mean, how many of you are left of fighting age? Two, counting Her Eminence?”
“Three,” The Mercuralis says, and the ground shakes. Salt Lake City isn’t a seismically active area, right? It’s not like home, at least. This royal is going to bury the evidence under the rubble of Salt Lake City.
“You should be thanking my cousin on your knees for not massacring your family like they did ours,” he continues.
“Well, I’m not letting you destroy a city”.
Another soldier speaks. “Perfect! We’re not. We’re cutting out your aunt’s influence and brining down a few buildings. Now get lost before His Highness decides to ignore his cousin’s orders and kill you all”.
In spite of everything or maybe because of it, Brian actually laughs. Marin shakes his head.
“The big one is Kishar. He’s even younger than I am. If he dies, then it’s over. Ishtar Mercuralis will burn both worlds to ash”.
Brian lowers his gun, but the rest of his posture becomes rigid instead of deflating “So what, we just leave? There’s dead bodies in the reactor room. We saw them. That goliath led a strike team to murder dozens of us and he’s still going to bring the whole campus down to cover his tracks”.
“It’s a lot better than a meltdown”. Marin replies. Then Kishar says something else she can’t understand, and Marin doesn’t translate. This negotiation is for elven ears only. That doesn’t mean they can’t shout their disapproval. The giant roars for Marin to shut his humans up.
He doesn’t, or at least it doesn’t work. Nonetheless, it’s a cease-fire. Marin stands, gives a single sharp nod through the used-to-be-window, and Kishar gestures with his massive gun. His other hand is on the bound person he’s kidnapping. Sierra holds Brian’s hand to keep him from punching their friend in the jaw. As they run out, patches of ceiling have begun to cave in from the fire above them. The barricades have all been abandoned, except for a few where a slumped body still keeps watch. They’re running on wet tile when the shaking starts, and despite a lifetime of earthquakes, Clay slips. Brian doesn’t waste a second pulling him to his feet.
Outside, she thinks that the soldiers were lying. The reactor must have melted down, or done something magical and worse, because the world is nothing but acrid smoke and the dust of buildings. It sticks to their wet skin and clothes and chokes out the sun. They look like ghosts, and so do the survivors who gather outside the police tape. She hopes they aren’t on camera.
Brian veers off into the dust, and they try to reel him back in until the rest of the group sees Zerada and Jezero standing uselessly at the edge of sight. Useless. Marin cares more about his ancient enemies than them and now they’re almost outnumbered by elves. Then Sierra’s phone calls. It’s her mother.
She coughs before picking up. “Hey Mama”
“Oh good. Have you seen the news?” Her mother is panicked so rarely that she has trouble telling.
Cai was occupied somewhere else. “Uh, there’s a lot going on. What specifically?” What does the exhaustion in her own voice sound like?
Her mama calls them terrorist attacks. Labs across the world have all but sunk into the earth. The one at Berkeley somehow kicked off a magnitude five earthquake, the biggest one they’d had at home all year (and the second caused by an elf). If Sierra had been in Massachusetts for college, then maybe she’d have been in the nuclear engineering lab, and then maybe she’d have been caught up in whatever happened that nearly caused a nuclear accident.
The scientists were right. Cai was helping out at a bigger, fancier, lab. MIT is safe, thanks to the ex-prince[ss]. She promises to stay safe, promises to call again soon, and hangs up the phone. She wants to tell the group the news, but the elves are talking too loudly about the unexpected Mercuralis boy for her to get a word in.
Zerada has a perfect kiss mark of destroyed laboratory dust on one cheek. Brian’s arguing against the little ceasefire trick, but he’s also in her arms.
“We’ve got to hold an intervention,” Clay whispers.
She opens an email to their emissary “For which one?”
“Brian? What, you want me to confront the elf prince?”
“You’d do a better job than me”.
……………….
Real university nuclear reactors are nothing to be afraid of. They are extremely safe and important for both research and job training. Do not let my silly oc thing turn you against nuclear energy. At the same time, when Sierra says that the US detonated "eight or..." nuclear bombs in the Nevada desert, she isn't saying eight or nine. She's saying eight or nine hundred. The fallout drifted downwind and caused widespread radiation poisoning and cancer. In summary, safety first when dealing with magic rocks formed by the decay of particles themselves.
Kishar Mercuralis is second-cousins with Ishtar’s kids. He is eighty-two, equivalent to barely eighteen. He’s also six foot seven without combat boots and built like a truck. However, he doesn’t have Ishtar’s strange durability. In a fight without magic or weapons, even Brian might be able to win just by toughing it out for longer.
@lokiwaffles @reggie246 @wishndreamer
3 notes
·
View notes
Text
Understanding Embroidery Digitizing Services: Turning Art into Stitches

Understanding Embroidery Digitizing Services: Turning Art into Stitches
Embroidery has been a timeless way to personalize and add intricate designs to fabric. Whether it's a logo on a corporate shirt or a unique design on a custom jacket, embroidery adds character and professionalism. However, for an embroidery machine to create these beautiful designs, the artwork must first be translated into a language it understands. This is where embroidery digitizing services come into play.
What is Embroidery Digitizing?
Embroidery digitizing is the process of converting digital artwork into a format that an embroidery machine can use. The artwork could be anything from a logo, text, or a detailed design, and the goal is to turn it into a series of instructions (stitch patterns) that the machine follows.
In simple terms, it’s the bridge between the designer’s idea and the final embroidered product.
The Process of Embroidery Digitizing
Artwork Submission: The first step is to submit the artwork you want to embroider. This can be a drawing, logo, or image in any digital format. The higher the quality of the artwork, the better the final embroidery will look.
Software Conversion: The artwork is imported into specialized embroidery digitizing software. This software allows the digitizer to trace and break down the image into different parts. Each part will have specific stitch types, directions, densities, and colors.
Stitch Path Creation: The digitizer then sets the path that the machine will follow. This is where they decide how many stitches each element will have, the direction of the stitching, and the type of stitch (e.g., satin stitch, fill stitch, or running stitch). These factors will influence the quality, appearance, and durability of the embroidery.
Final Touches: After the initial setup, the digitizer tests the design on a sample fabric. Adjustments are made to ensure that the design is perfect — ensuring smooth stitches, proper alignment, and the best visual outcome.
Machine-Ready File: Once everything looks good, the design is saved in a machine-readable file format like .DST or .PES. This file is what gets loaded into the embroidery machine to create the final product.
Why is Embroidery Digitizing Important?
Embroidery digitizing plays a vital role in ensuring that designs come out looking sharp, clean, and professional. Here’s why it’s so important:
Precision: A well-digitized file ensures that the embroidery machine sews the design exactly as intended, without any distortion or mistakes.
Fabric Compatibility: The digitizing process accounts for different types of fabric, adjusting the stitch density and style so that the design looks good on various materials, from denim to polyester.
Cost-Effective: A properly digitized design reduces the chances of errors, saving time and money. It also prevents issues like thread breaks or uneven stitching, which can be costly to fix.
Customization: Whether you're embroidering a company logo or a personalized monogram, digitizing allows for endless customization, enabling your artwork to be turned into a high-quality, professional embroidery.
Common Uses of Embroidery Digitizing
Corporate Branding: Companies often use embroidery to create custom uniforms, hats, and promotional materials, all featuring their logos and branding.
Sports Teams: Team logos, player names, and numbers are commonly embroidered on jerseys, hats, and jackets.
Personalized Gifts: Embroidered items like towels, blankets, or bags make for memorable, personal gifts.
Fashion: Designers use embroidery to add intricate patterns and textures to garments, bringing designs to life with high-quality stitching.
Choosing the Right Embroidery Digitizing Service
Not all embroidery digitizing services are created equal. When selecting a service, look for:
Experience: A company with experienced digitizers will produce high-quality, accurate designs that match your vision.
File Format Compatibility: Ensure the service provides files in the format compatible with your embroidery machine.
Customer Support: Good customer service is key. A digitizing service should be responsive, willing to make adjustments, and provide guidance through the process.
Portfolio: Review samples of previous work to gauge the quality of their digitizing services.
Conclusion
Embroidery digitizing is an essential process that turns your creative ideas into high-quality embroidered designs. Whether you’re looking to add a personal touch to your clothing, promote your brand, or create custom sports gear, a professional embroidery digitizing service will ensure your designs look sharp and last long. By understanding the digitizing process, you can make informed decisions and get the best results for your project.
So, next time you need custom embroidery, remember the importance of proper digitization — because turning art into stitches is more than just a technical process; it’s what brings your designs to life.
#Embroidery Digitizing Services#Custom Embroidery Designs#Vector Artwork for Screen Printing#3D Puff Embroidery Digitizing#Professional Embroidery Digitizers#Online Embroidery Digitizing#High-Quality Vector Art work#Affordable Embroidery Digitizing#USA-Based Embroidery Services
2 notes
·
View notes
Text
The Power of Precision: Exploring the Benefits of PAUT in NDT

In the realm of industrial inspections, the demand for accuracy and efficiency has never been higher. Phased Array Ultrasonic Testing (PAUT) stands out as a revolutionary method that fulfills these requirements, offering unparalleled precision and speed. As an integral part of Non Destructive Testing, PAUT is widely used across various industries to ensure the integrity and reliability of critical components. Here, we delve into the intricacies of PAUT and its benefits.
PAUT is an advanced method of ultrasonic testing that uses multiple elements and electronic time delays to create beams of sound waves. These beams can be steered, focused, and scanned, providing detailed images of internal structures. Unlike conventional ultrasonic testing, which uses a single transducer to send and receive sound waves, PAUT employs an array of transducers. This allows for simultaneous collection of data from multiple angles, resulting in more comprehensive and accurate inspections.
As part of a broader suite of Non Destructive Testing Services, PAUT plays a crucial role in ensuring the safety and reliability of industrial components. Nondestructive testing (NDT) from RVS QUALITY CERTIFICATIONS PVT LTD encompasses various techniques used to evaluate the properties of a material, component, or system without causing damage. PAUT's advanced capabilities enhance the overall effectiveness of NDT services, providing detailed and reliable data that support maintenance and quality assurance programs.
Applications Across Industries
The versatility of PAUT makes it suitable for a wide range of applications. It is commonly used in the aerospace, automotive, and power generation industries for inspecting critical components such as welds, turbine blades, and composite materials. PAUT's ability to detect minute defects and irregularities ensures that even the smallest flaws are identified before they become critical issues. This level of precision is essential for maintaining safety and performance standards in high-stakes environments.
Efficiency and Accuracy Combined
One of the standout features of PAUT is its efficiency. The ability to steer and focus sound waves electronically means that inspections can be performed more quickly compared to traditional methods. This not only reduces downtime but also increases the number of inspections that can be completed within a given timeframe. Additionally, the detailed images produced by PAUT provide a clearer understanding of the inspected material's condition, allowing for more accurate assessments and decision-making.
Enhanced Tube Inspections
A specific area where PAUT excels is in Tube Inspection Services. Tubes, often found in heat exchangers and boilers, are prone to various types of degradation such as corrosion and cracking. PAUT's ability to inspect from multiple angles simultaneously makes it particularly effective for tube inspections. It can detect flaws that may be missed by conventional methods, ensuring that tubes are thoroughly evaluated for any signs of wear or damage. This comprehensive approach helps prevent failures and extends the lifespan of critical equipment.
Advancing with Technology
The continuous evolution of technology has significantly impacted PAUT. Advances in digital signal processing and software have improved the resolution and clarity of the images produced. Portable PAUT equipment from RVS QUALITY CERTIFICATIONS PVT LTD has made it possible to conduct inspections in challenging environments, further expanding its applicability. These technological advancements ensure that PAUT remains at the forefront of nondestructive testing techniques, providing industries with cutting-edge solutions for maintaining safety and quality.
In conclusion, PAUT is a powerful tool that combines precision and efficiency to deliver superior inspection results. Its ability to provide detailed images from multiple angles makes it invaluable for identifying defects and ensuring the integrity of critical components. As a key component of Non Destructive Testing, PAUT supports industries in maintaining high standards of safety and performance. Whether it's for welds, turbine blades, or Tube Inspection Service, PAUT continues to set the standard for advanced nondestructive testing methodologies.
5 notes
·
View notes
Text
Best IT Courses In Bhubaneswar:- seeree services pvt ltd.
Introduction:- seeree is one of the best IT training institute and Software industry, features completely Industrial training on Python , PHP , .NET , C Programming,Java , IOT , AI , GD PI , ORACLE and ALL CERTIFICATION COURSES as well as provides seminar,cultural activity and jobs
Courses we provided:- 1) Java Fullstack 2) Python Fullstack 3) PHP Fullstack 4) Preplacement Training & Sp. Eng 5) .NET Fulstack 6) SEO/Digital Marketing 7) SAP 8) MERN 9) Software Testing 10)Data Analyst 11)Data Science 12)Data Engineering 13)PGDCA 14)Tally 15)Graphics Design
Course1:- Java Fullstack

A Class in Java is where we teach objects how to behave. Education at seeree means way to success. The way of teaching by corporate trainers will bloom your career. We have the best java training classes in Bhubaneswar. 100% Placement Support. Job Support Post Training. This course will give you a firm foundation in Java, commonly used programming language. Java technology is wide used currently. Java is a programming language and it is a platform. Hardware or software environment in which a program runs, known as a platform. Since Java has its own Runtime Environment (JRE) and API, it is called platform. Java programming language is designed to meet the challenges of application development in the context of heterogeneous, network-wide distributed environment. Java is an object-oriented programming (OOP) language that uses many common elements from other OOP languages, such as C++. Java is a complete platform for software development. Java is suitable for enterprise large scale applications.]
Course2:- Python Fullstack

Seeree offers best python course in Bhubaneswar with 100% job assurance and low fee. Learn from real time corporate trainers and experienced faculties. Groom your personality with our faculty. Seeree helps to build confidence in students to give exposure to their skills to the company.
Python is dynamically typed , compiled and interpreted , procedural and object oriented , generalized , general-purpose , platform independent programming language. Python is a high-level, structured, open-source programming language that can be used for a wide variety of programming tasks.
Course3:- PHP Fullstack

seeree is the best training institute which provide PHP Training courses in bhubaneswar and all over odisha We aim the students to learn and grow altogether with the need of IT firms.
PHP is a server scripting language, and a powerful tool for making dynamic and interactive Web pages. PHP is a widely-used, free, and efficient alternative to competitors such as Microsoft's ASP.
Course4:- Preplacement Training & Sp. Eng

Welcome to SEEREE Institute, where excellence meets opportunity. At SEEREE, we are dedicated to providing a transformative learning experience that empowers students to achieve their goals and contribute to a brighter future.
Our institute offers cutting-edge courses designed to meet the needs of the ever-evolving global landscape. With a team of highly qualified instructors and state-of-the-art facilities, we ensure a supportive and inspiring environment for learning and growth.
Whether you're here to develop new skills, explore innovative fields, or pursue personal and professional success, SEEREE Institute is the perfect place to begin your journey. Thank you for choosing us, and we look forward to being a part of your success story.
Course5:- .NET Fullstack

Seeree offers best .NET course in Bhubaneswar with 100% job assurance and low fee. Learn from real time corporate trainers and experienced faculties. Groom your personality with our faculty. Seeree helps to build confidence in students to give exposure to their skills to the company.
Course6:- SEO/Digital Marketing

In today's fast-paced digital world, businesses thrive on visibility, engagement, and strategic online presence. At SEEREE, we empower you with the skills and knowledge to master the art of Search Engine Optimization (SEO) and Digital Marketing.
Our comprehensive program is designed for beginners and professionals alike, covering everything from keyword research, on-page and off-page SEO, and content marketing, to social media strategies, PPC campaigns, and analytics.
With hands-on training, real-world projects, and guidance from industry experts, we ensure you're equipped to drive measurable results and excel in this dynamic field.
Join us at SEEREE Institute and take the first step towards becoming a leader in the digital marketing landscape!"
Course7:- SAP

SAP refers to Systems, Applications, and Products in Data Processing. Some of the most common subjects covered in these courses include human resource software administration, database management, and business training. Obtaining SAP certification can be done on a stand-alone basis or as part of a degree program.
Course8:- MERN

Seeree offers the best MERN course in Bhubaneswar with 100% job assurance and low fees. Learn from real-time corporate trainers and experienced faculty. Seeree helps students build confidence and gain skills to excel in company roles.
Are you ready to step into the exciting world of web development? At SEEREE, we bring you a comprehensive MERN Stack course that equips you with the skills to build modern, dynamic, and responsive web applications from start to finish.
The MERN Stack—comprising MongoDB, Express.js, React.js, and Node.js—is one of the most sought-after technologies in the web development industry. Our program is designed to help you master each component of the stack, from creating robust backends and managing databases to crafting dynamic frontends and seamless APIs.
Course9:- Software Testing

Seeree offers best Testing course in Bhubaneswar with 100% job assurance and low fee. Learn from real time corporate trainers and experienced faculties. Groom your personality with our faculty. Seeree helps to build confidence in students to give exposure to their skills to the company.
In the fast-paced world of software development, ensuring the quality and reliability of applications is crucial. At SEEREE, we offer a comprehensive Software Testing course designed to equip you with the skills and techniques needed to excel in this essential field.
Our program covers all aspects of software testing, from manual testing fundamentals to advanced automation tools and frameworks like Selenium, JIRA, and TestNG. You’ll learn to identify bugs, write test cases, execute test scripts, and ensure software meets high-quality standards.
With hands-on training, real-world scenarios, and guidance from experienced industry professionals, you’ll be prepared to take on roles like Quality Assurance Engineer, Test Analyst, and Automation Tester.
Join SEEREE Institute and gain the expertise to become a key player in delivering flawless software solutions. Your journey to a rewarding career in software testing starts here!"
Course10:- Data Analyst

Seeree offers the best Data Analyst course in Bhubaneswar with 100% job assurance and affordable fees. Our comprehensive curriculum is designed to cover all aspects of data analysis, from data collection and cleaning to advanced data visualization techniques. Learn from real-time corporate trainers and experienced faculty members who bring industry insights into the classroom. Enhance your analytical skills and boost your career prospects with hands-on projects and real-world case studies. Our faculty also focuses on grooming your personality and soft skills, ensuring you are well-prepared for interviews and workplace environments. Seeree is dedicated to building confidence in students, providing them with the necessary exposure to showcase their skills to top companies in the industry.
Course11:- Data Science

Seeree offers the best Data Science course in Bhubaneswar with 100% job assurance and affordable fees. Our comprehensive curriculum is designed to cover all aspects of data science, from data collection and cleaning to advanced data visualization techniques. Learn from real-time corporate trainers and experienced faculty members who bring industry insights into the classroom. Enhance your analytical skills and boost your career prospects with hands-on projects and real-world case studies. Our faculty also focuses on grooming your personality and soft skills, ensuring you are well-prepared for interviews and workplace environments. Seeree is dedicated to building confidence in students, providing them with the necessary exposure to showcase their skills to top companies in the industry.
Course12:- Data Engineering
In the era of big data, the ability to design, build, and manage scalable data infrastructure is one of the most in-demand skills in the tech industry. At SEEREE, we are proud to offer a comprehensive Data Engineering course that prepares you for a career at the forefront of data-driven innovation.
Our program covers essential topics such as data modeling, ETL processes, data warehousing, cloud platforms, and tools like Apache Spark, Kafka, and Hadoop. You’ll learn how to collect, organize, and transform raw data into actionable insights, enabling businesses to make smarter decisions.
With real-world projects, expert mentorship, and hands-on experience with the latest technologies, we ensure that you are industry-ready. Whether you’re starting fresh or upskilling, this program will empower you to unlock opportunities in the rapidly growing field of data engineering.
Join SEEREE Institute and take the first step toward building the data pipelines that power tomorrow’s technology!"
Course13:- PGDCA

Seeree offers the best MERN course in Bhubaneswar with 100% job assurance and low fees. Learn from real-time corporate trainers and experienced faculty. Seeree helps students build confidence and gain skills to excel in company roles.
In today’s digital age, computer applications are at the heart of every industry, driving innovation and efficiency. At SEEREE Institute, our Post Graduate Diploma in Computer Applications (PGDCA) program is designed to provide you with in-depth knowledge and hands-on skills to excel in the IT world.
This program offers a comprehensive curriculum covering programming languages, database management, web development, software engineering, networking, and more. Whether you aim to enhance your technical expertise or step into a rewarding career in IT, PGDCA at SEEREE equips you with the tools to succeed.
With expert faculty, state-of-the-art labs, and real-world projects, we ensure that you gain practical experience and a strong theoretical foundation. By the end of the program, you’ll be prepared for roles such as software developer, system analyst, IT manager, or database administrator.
Course14:- Tally

Seeree offers the best Tally course in Bhubaneswar with 100% job assurance and low fees. Learn from real-time corporate trainers and experienced faculty. Seeree helps students build confidence and gain skills to excel in company roles.
In today’s business world, efficient financial management is key to success, and Tally is one of the most trusted tools for accounting and financial operations. At SEEREE Institute, we offer a comprehensive Tally course designed to equip you with the skills needed to manage business finances effortlessly.
Our program covers everything from the basics of accounting and bookkeeping to advanced features like GST compliance, inventory management, payroll processing, and generating financial reports. With hands-on training and real-world applications, you’ll gain practical expertise in using Tally effectively for businesses of any scale.
Whether you're a student, a professional, or a business owner, our Tally program is tailored to meet your needs and enhance your career prospects in the fields of accounting and finance.
Course15:- Graphics Design

In the world of creativity and communication, graphic design plays a vital role in bringing ideas to life. At SEEREE Institute, our Graphic Design course is tailored to help you unlock your creative potential and master the art of visual storytelling.
Our program covers a wide range of topics, including design principles, color theory, typography, branding, and user interface design. You’ll gain hands-on experience with industry-standard tools like Adobe Photoshop, Illustrator, and InDesign, enabling you to create stunning visuals for print, digital media, and beyond.
Whether you're an aspiring designer or a professional looking to sharpen your skills, our expert trainers and real-world projects will provide you with the knowledge and confidence to excel in this competitive field.
Join SEEREE Institute and start your journey toward becoming a skilled graphic designer. Let’s design your future together!"
2 notes
·
View notes
Text
Launch Your Own Crypto Platform with Notcoin Clone Script | Fast & Secure Solution
To launch your own cryptocurrency platform using a Notcoin clone script, you can follow a structured approach that leverages existing clone scripts tailored for various cryptocurrency exchanges.
Here’s a detailed guide on how to proceed:
Understanding Clone Scripts
A clone script is a pre-built software solution that replicates the functionalities of established cryptocurrency exchanges. These scripts can be customized to suit your specific business needs and allow for rapid deployment, saving both time and resources.
Types of Clone Scripts
Centralized Exchange Scripts: These replicate platforms like Binance or Coinbase, offering features such as order books and user management.
Decentralized Exchange Scripts: These are designed for platforms like Uniswap or PancakeSwap, enabling peer-to-peer trading without a central authority.
Peer-to-Peer (P2P) Exchange Scripts: These allow users to trade directly with each other, similar to LocalBitcoins or Paxful.
Steps to Launch Your Crypto Platform
Step 1: Define Your Business Strategy
Market Research: Identify your target audience and analyze competitors.
Unique Value Proposition: Determine what sets your platform apart from others.
Step 2: Choose the Right Clone Script
Evaluate Options: Research various clone scripts available in the market, such as those for Binance, Coinbase, or P2P exchanges. Customization: Ensure the script is customizable to meet your specific requirements, including branding and features.
Step 3: Development and Deployment
Technical Setup: Collaborate with developers to set up the necessary infrastructure, including blockchain integration and wallet services.
Security Features: Implement robust security measures, such as two-factor authentication and encryption, to protect user data and transactions.
Step 4: Compliance and Regulations
KYC/AML Integration: Ensure your platform complies with local regulations by integrating Know Your Customer (KYC) and Anti-Money Laundering (AML) protocols.
Step 5: Testing and Launch
Quality Assurance: Conduct thorough testing to identify and fix any bugs or vulnerabilities.
Launch: Once testing is complete, launch your platform and start marketing it to attract users.
Advantages of Using a Notcoin Clone Script
Cost-Effective: Using a pre-built script is generally more affordable than developing a platform from scratch.
Faster Time to Market: Notcoin Clone scripts are ready to deploy, significantly reducing development time.
Customization Options: Most scripts allow for extensive customization, enabling you to tailor the platform to your needs.
Conclusion
Launching your own cryptocurrency platform with a Notcoin clone script is a viable option that can lead to a successful venture in the growing crypto market. By following the outlined steps and leveraging the advantages of Notcoin clone scripts, you can create a robust and secure trading platform that meets user demands and regulatory requirements.
For further assistance, consider reaching out to specialized development companies that offer Notcoin clone script and can guide you through the setup process
#cryptotrading#notcoin#notcoinclonescript#cryptocurrencies#crypto exchange#blockchain#crypto traders#crypto investors#cryptonews#web3 development
3 notes
·
View notes
Text
Cipherwinghsolution
Enhance your enterprise with CipherWingSolution's IT Services
Today’s world is highly digitalized and a competent IT partner is influential in helping attain growth and even efficiency. CipherWingSolution is equipped with a wide array of IT services helping various businesses cope with the rapid technological advancements.
Custom Software Development: So as to automate various functions and enhance productivity, we offer bespoke software development that fulfills the particular requirements of your enterprise. Our focus is to develop scalable and accessible applications that propel your venture to greater heights.
Web and Mobile Development: Access and business visibility is enhanced through our web development services where we create dynamic and responsive websites. In addition, mobile applications are also developed for both the android and iOS platforms to ensure optimum usability for users.
Cloud Solutions: Adopting cloud computing can increase your business’s agility and security. Consequently, our cloud infrastructure, migration and integration services ensure that your essential corporate data remains safe while you have access to it as well as other valuable resources without much of a hassle.
Cybersecurity Services: Safeguarding your online assets is of utmost importance. Such services include vulnerability assessment and penetration testing are part of cyber security services offered to protect your business.
IT Consulting & Network Management: At CipherWingSolution, we give you IT strategy consulting services that help you fit technology in your business objectives. The other type of management we offer is network management so that you can operate seamlessly.
Data Analytics: Make the most of your data using our analytical services. Such data is utilized to produce insights which are useful in decision making for the growth of the business.
Opting for CipherWingSolution entails opting for a partner who is committed to providing growth and efficacy oriented IT solutions. We will help you prosper in this digital world by offering you services that are both competitive and safe. Contact Us Now To Learn What we can Do For Your Business’s IT Requirements!
#digital marketing#hrms solutions#crm services#seo services#social media marketing#marketing agency#google ads#search engine optimization#web desing#web development#tech
2 notes
·
View notes