#usb secure software
Explore tagged Tumblr posts
Text
Wise Folder Hider
Wise Folder Hider is specialized software designed to protect data and keep it hidden from unauthorized access. Its drag-and-drop feature makes it very user-friendly, and the software offers a range of features aimed at providing additional security for extra peace of mind. Features Free of Charge Wise Folder Hider is a free program from wisecleaner.com, allowing all users to use, update, and…
#data security#double password#file protection#Free Software#hide files#usb protection#user-friendly software#Wise Folder Hider
0 notes
Text
A few years ago I had a phase of being REALLY into digital privacy, using tor, duckduckgo, etc before suffering some burnout because I was trying to be 100% secure. So I'm by no means a expert I'm just relaying experience.
The culture of a lot of left leaning and "fandommy" sites (tumblr, twitter, etc) tends to fear/dislike (or just not know about) a lot of the IT stuff used by people into online privacy because they asscoiate it with "techbros". ESPECIALLY anything even remotely involving cryptocurrency. But if Trump is going to start censoring things and making morning after pills harder to get now might be a VERY good time for Americans to get into online privacy and how to avoid being tracked as well as avoiding censorship. Perhaps even some crypto to buy things discretly (or perhaps if ICE agents start caring about cash?) and because many activists groups also take donations in crypto. Never dealt with crypto myself but from what I know Monero was designed to be more untracable than Bitcoin. Don't know how succesfull that is though. Definetly get into privacy in general though.
I'll leave some useful links to get started. Words of advice:
Don't install a fuckton of privacy extensions on your browser, your unique combination of extensions will give your browser a unique fingerprint. Instead read up on and pick a few commonly used ones.
The BIGGEST annoyance for me was acedemic/proffesional settings because noone wants to switch over to some software they never heard off for one group project. Personally I use some normie software for exclusivly proffesional purposes with NO other information on me and do my actual browsing/leisure computer use more privatly.
https://www.privacytools.io/os: General software/browser/etc recomendations.
https://coveryourtracks.eff.org/: Test how private your browser is.
https://www.torproject.org/: THE gold standard for privacy focused browsers. Also obscures ip. Might not always be practical. Has the disadvantage of being notoriously slow and is blocked by some services/websites to avoid people bypassing ip bans and whatnot. Probably don't use this as your everyday browser but if you ever need to look up anything without censorship use tor.
https://tails.net/: Install a portable mini operating system on a usb stick to browse privately from any computer.
https://www.eff.org/ Electronic frontier foundations website.
https://mastodon.social/explore Don't have experience with it myself. But open source social media that should be much harder to censor.
Tumblr probably won't like me talking too directly about this because of ties to piracy but for people interested in banned books https://en.wikipedia.org/wiki/Shadow_library should be an interesting read...
3K notes
·
View notes
Text
ohoho not only could i isolate the issue (though idk if its possible to fix it) i also by chance figured out what was causing the other weird ass problem they were having!!
#tütensuppe#trying to put it simple theyre using a device that simulates multiple serial ports over usb#for some reason it gets recognized in win 10 no problem but not at all in win 11#(this is important bc all computers should run the newest software for security reasons)#so i brought a private win 11 laptop. and it recognized the device!!#then on a whim i pulled the plug and reconnected it. now it no longer recognized the device!#deleting two of the driver files changed nothing. so the third file i couldnt delete HAS to be blocking it somehow#(none of these files were present on the laptop before the device was initially recognized)#this is a system file though idk if you can do anything about it#windows wont let you delete it but maybe you can boot from a linux medium and fudge around a bit?#anyway the OTHER thing is while researching i found a person reporting EXACTLY that problem#(you connect a virtual serial port device. suddenly the mouse starts acting up and clicking everything. this is unsalvagable)#turns out sometimes the virtual serial port device randomly gets detected as a mouse and that causes this#if you got to this point. thank you for reading this essay
1 note
·
View note
Text
Installing Linux (Mint) as a Non-Techy Person
I've wanted Linux for various reasons since college. I tried it once when I no longer had to worry about having specific programs for school, but it did not go well. It was a dedicated PC that was, I believe, poorly made. Anyway.
In the process of deGoogling and deWindows365'ing, I started to think about Linux again. Here is my experience.
Pre-Work: Take Stock
List out the programs you use regularly and those you need. Look up whether or not they work on Linux. For those that don't, look up alternatives.
If the alternative works on Windows/Mac, try it out first.
Make sure you have your files backed up somewhere.
Also, pick up a 5GB minimum USB drive.
Oh and make a system restore point (look it up in your Start menu) and back-up your files.
Step One: Choose a Distro
Dear god do Linux people like to talk about distros. Basically, from what all I've read, if you don't want to fuss a lot with your OS, you've got two options: Ubuntu and Linux Mint. Ubuntu is better known and run by a company called Canonical. Linux Mint is run by a small team and paid for via donations.
I chose Linux Mint. Some of the stuff I read about Ubuntu reminded me too much of my reasons for wanting to leave Windows, basically. Did I second-guess this a half-dozen times? Yes, yes I did.
The rest of this is true for Linux Mint Cinnamon only.
Step Two: Make your Flash Drive
Linux Mint has great instructions. For the most part they work.
Start here:
The trickiest part of creating the flash drive is verifying and authenticating it.
On the same page that you download the Linux .iso file there are two links. Right click+save as both of those files to your computer. I saved them and the .iso file all to my Downloads folder.
Then, once you get to the 'Verify your ISO image' page in their guide and you're on Windows like me, skip down to this link about verifying on Windows.
Once it is verified, you can go back to the Linux Mint guide. They'll direct you to download Etchr and use that to create your flash drive.
If this step is too tricky, then please reconsider Linux. Subsequent steps are both easier and trickier.
Step Three: Restart from your Flash Drive
This is the step where I nearly gave up. The guide is still great, except it doesn't mention certain security features that make installing Linux Mint impossible without extra steps.
(1) Look up your Bitlocker recovery key and have it handy.
I don't know if you'll need it like I did (I did not turn off Bitlocker at first), but better to be safe.
(2) Turn off Bitlocker.
(3) Restart. When on the title screen, press your Bios key. There might be more than one. On a Lenovo, pressing F1 several times gets you to the relevant menu. This is not the menu you'll need to install, though. Turn off "Secure Boot."
(4) Restart. This time press F12 (on a Lenovo). The HDD option, iirc, is your USB. Look it up on your phone to be sure.
Now you can return to the Linux Mint instructions.
Figuring this out via trial-and-error was not fun.
Step Four: Install Mint
Just follow the prompts. I chose to do the dual boot.
You will have to click through some scary messages about irrevocable changes. This is your last chance to change your mind.
I chose the dual boot because I may not have anticipated everything I'll need from Windows. My goal is to work primarily in Linux. Then, in a few months, if it is working, I'll look up the steps for making my machine Linux only.
Some Notes on Linux Mint
Some of the minor things I looked up ahead of time and other miscellany:
(1) HP Printers supposedly play nice with Linux. I have not tested this yet.
(2) Linux Mint can easily access your Windows files. I've read that this does not go both ways. I've not tested it yet.
(3) You can move the taskbar (panel in LM) to the left side of your screen.
(4) You are going to have to download your key programs again.
(5) The LM software manager has most programs, but not all. Some you'll have to download from websites. Follow instructions. If a file leads to a scary wall of strange text, close it and just do the Terminal instructions instead.
(6) The software manager also has fonts. I was able to get Fanwood (my favorite serif) and JetBrains (my favorite mono) easily.
In the end, be prepared for something to go wrong. Just trust that you are not the first person to ever experience the issue and look it up. If that doesn't help, you can always ask. The forums and reddit community both look active.
178 notes
·
View notes
Text
Have YOU got an old Windows PC Microsoft has told you can't run Windows 11? It's time to give it a new life!
How to install Windows 11 on unsupported PC Hardware using Rufus. You can also disable some other Windows 11 bullshit like data harvesting and needing a Microsoft account.
It has been in the news a lot lately that Windows 11 isn't allowed to be installed on PCs without certain requirements, including the TPM 2.0, a chip that was only included in PCs made in 2018 or later. This means that once Windows 10 stops receiving security updates, those PCs will not be able to (officially) run a safe, updated version of Windows anymore. This has led to an estimated 240 million PCs bound for the landfill. Thanks Microsoft! I get you don't want to be seen as the insecure one, but creating this much waste can't be the solution.
(I know nerds, Linux is a thing. I love you but we are not having that conversation. If you want to use Linux on an old PC you are already doing it and you don't need to tell me about it. People need Windows for all sorts of reasons that Linux won't cut.)
So lately I have been helping some under privileged teens get set up with PCs. Their school was giving away their old lab computers, and these kids would usually have no chance to afford even a basic computer. They had their hard drives pulled so I have been setting them up with SSDs, but the question was, what to do about the operating system? So I looked into it and I found out there IS actually a way to bypass Microsoft's system requirement and put Windows 11 on PCs as old as 2010.
You will need: Rufus: An open source ISO burning tool.
A Windows 11 ISO: Available from Microsoft.
A USB Flash Drive, at least 16GB.
A working PC to make the ISO, and a PC from 2018 or older you want to install Windows 11 on.
Here is the guide I used, but I will put it in my own words as well.
Download your Windows 11 ISO, and plug in your USB drive. It will be erased, so don't have anything valuable on it. Run Rufus, select your USB drive in the Device window, and select your Windows 11 ISO with the Select button. (There is supposed to be a feature in Rufus to download your ISO but I couldn't get it to work.?
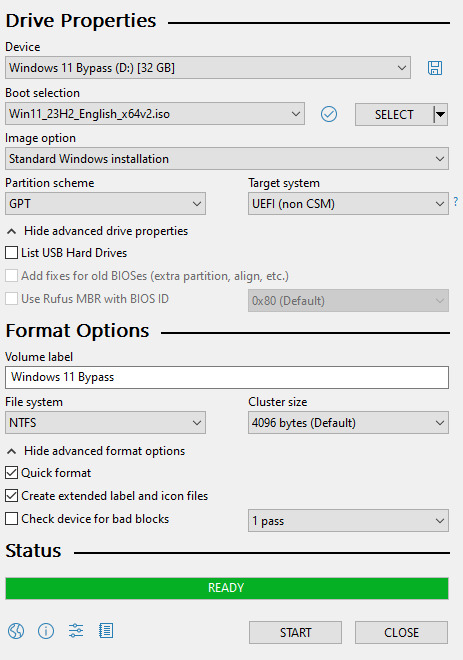
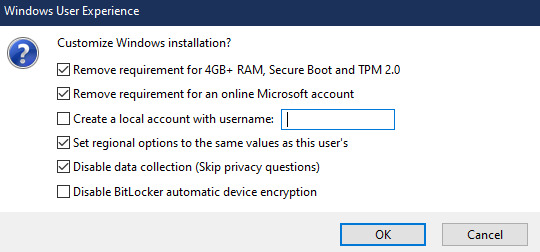
Choose standard windows installation, and follow the screenshot for your settings. Once you are done that, press Start, and then the magic happens. Another window pops up allowing you to remove the system requirements, the need for a microsoft account, and turn off data collecting. Just click the options you want, and press ok to write your iso to a drive.
From there you just need to use the USB drive to install windows. I won't go into details here, but here are some resources if you don't know how to do it.
Boot your PC from a USB Drive
Install Windows 11 from USB Drive
If you had a licensed copy of Windows 10, Windows 11 will already be licensed. If you don't, then perhaps you can use some kind of... Activation Scripts for Microsoft software, that will allow you to activate them. Of course I cannot link such tools here. So there you go, now you can save a PC made from before 2018 from the landfill, and maybe give it to a deserving teen in the process. The more we can extend the lives of technology and keep it out of the trash, the better.
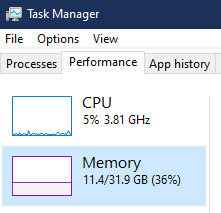
Additional note: This removes the requirement for having 4GB Minimum of RAM, but I think that requirement should honestly be higher. Windows 11 will be unusable slow on any system with below 8GB of RAM. 8GB is the minimum I think you should have before trying this but it still really not enough for modern use outside of light web and office work. I wouldn't recommend trying this on anything with 4GB or less. I am honestly shocked they are still selling brand new Windows 11 PCs with 4GB of ram. If you're not sure how much RAM you have, you can find out in the performance tab of Task Manager in Windows, if you click the More Details icon on the bottom right. If you don't have enough, RAM for old systems is super cheap and widely available so it would definitely be worth upgrading if you have a ram starved machine you'd like to give a new life.
#Windows#Windows 11#tech#tech advice#pc#TPM 2.0#rufus#open source#open source software#technology#tech tips
725 notes
·
View notes
Text
She Won. They Didn't Just Change the Machines. They Rewired the Election. How Leonard Leo's 2021 sale of an electronics firm enabled tech giants to subvert the 2024 election.

Everyone knows how the Republicans interfered in the 2024 US elections through voter interference and voter-roll manipulation, which in itself could have changed the outcomes of the elections. What's coming to light now reveals that indeed those occupying the White House, at least, are not those who won the election.
Here's how they did it.
(full story is replicated here below the read-more: X)
She Won
The missing votes uncovered in Smart Elections’ legal case in Rockland County, New York, are just the tip of the iceberg—an iceberg that extends across the swing states and into Texas.
On Monday, an investigator’s story finally hit the news cycle: Pro V&V, one of only two federally accredited testing labs, approved sweeping last-minute updates to ES&S voting machines in the months leading up to the 2024 election—without independent testing, public disclosure, or full certification review.
These changes were labeled “de minimis”—a term meant for trivial tweaks. But they touched ballot scanners, altered reporting software, and modified audit files—yet were all rubber-stamped with no oversight.
That revelation is a shock to the public.
But for those who’ve been digging into the bizarre election data since November, this isn’t the headline—it’s the final piece to the puzzle. While Pro V&V was quietly updating equipment in plain sight, a parallel operation was unfolding behind the curtain—between tech giants and Donald Trump.
And it started with a long forgotten sale.
A Power Cord Becomes a Backdoor
In March 2021, Leonard Leo—the judicial kingmaker behind the modern conservative legal machine—sold a quiet Chicago company by the name of Tripp Lite for $1.65 billion. The buyer: Eaton Corporation, a global power infrastructure conglomerate that just happened to have a partnership with Peter Thiel’s Palantir.
To most, Tripp Lite was just a hardware brand—battery backups, surge protectors, power strips. But in America’s elections, Tripp Lite devices were something else entirely.
They are physically connected to ES&S central tabulators and Electionware servers, and Dominion tabulators and central servers across the country. And they aren’t dumb devices. They are smart UPS units—programmable, updatable, and capable of communicating directly with the election system via USB, serial port, or Ethernet.
ES&S systems, including central tabulators and Electionware servers, rely on Tripp Lite UPS devices. ES&S’s Electionware suite runs on Windows OS, which automatically trusts connected UPS hardware.
If Eaton pushed an update to those UPS units, it could have gained root-level access to the host tabulation environment—without ever modifying certified election software.
In Dominion’s Democracy Suite 5.17, the drivers for these UPS units are listed as “optional”—meaning they can be updated remotely without triggering certification requirements or oversight. Optional means unregulated. Unregulated means invisible. And invisible means perfect for infiltration.
Enter the ballot scrubbing platform BallotProof. Co-created by Ethan Shaotran, a longtime employee of Elon Musk and current DOGE employee, BallotProof was pitched as a transparency solution—an app to “verify” scanned ballot images and support election integrity.
With Palantir's AI controlling the backend, and BallotProof cleaning the front, only one thing was missing: the signal to go live.
September 2024: Eaton and Musk Make It Official
Then came the final public breadcrumb:In September 2024, Eaton formally partnered with Elon Musk.
The stated purpose? A vague, forward-looking collaboration focused on “grid resilience” and “next-generation communications.”
But buried in the partnership documents was this line:
“Exploring integration with Starlink's emerging low-orbit DTC infrastructure for secure operational continuity.”
The Activation: Starlink Goes Direct-to-Cell
That signal came on October 30, 2024—just days before the election, Musk activated 265 brand new low Earth orbit (LEO) V2 Mini satellites, each equipped with Direct-to-Cell (DTC) technology capable of processing, routing, and manipulating real-time data, including voting data, through his satellite network.
DTC doesn’t require routers, towers, or a traditional SIM. It connects directly from satellite to any compatible device—including embedded modems in “air-gapped” voting systems, smart UPS units, or unsecured auxiliary hardware.
From that moment on:
Commands could be sent from orbit
Patch delivery became invisible to domestic monitors
Compromised devices could be triggered remotely
This groundbreaking project that should have taken two-plus years to build, was completed in just under ten months.
Elon Musk boasts endlessly about everything he’s launching, building, buying—or even just thinking about—whether it’s real or not. But he pulls off one of the largest and fastest technological feats in modern day history… and says nothing? One might think that was kind of… “weird.”
According to New York Times reporting, on October 5—just before Starlink’s DTC activation—Musk texted a confidant:
“I’m feeling more optimistic after tonight. Tomorrow we unleash the anomaly in the matrix.”
Then, an hour later:
“This isn’t something on the chessboard, so they’ll be quite surprised. ‘Lasers’ from space.”
It read like a riddle. In hindsight, it was a blueprint.
The Outcome
Data that makes no statistical sense. A clean sweep in all seven swing states.
The fall of the Blue Wall. Eighty-eight counties flipped red—not one flipped blue.
Every victory landed just under the threshold that would trigger an automatic recount. Donald Trump outperformed expectations in down-ballot races with margins never before seen—while Kamala Harris simultaneously underperformed in those exact same areas.
If one were to accept these results at face value—Donald Trump, a 34-count convicted felon, supposedly outperformed Ronald Reagan. According to the co-founder of the Election Truth Alliance:
“These anomalies didn’t happen nationwide. They didn’t even happen across all voting methods—this just doesn’t reflect human voting behavior.”
They were concentrated.
Targeted.
Specific to swing states and Texas—and specific to Election Day voting.
And the supposed explanation? “Her policies were unpopular.” Let’s think this through logically. We’re supposed to believe that in all the battleground states, Democratic voters were so disillusioned by Vice President Harris’s platform that they voted blue down ballot—but flipped to Trump at the top of the ticket?
Not in early voting.
Not by mail.
With exception to Nevada, only on Election Day.
And only after a certain threshold of ballots had been cast—where VP Harris’s numbers begin to diverge from her own party, and Trump’s suddenly begin to surge. As President Biden would say, “C’mon, man.”
In the world of election data analysis, there’s a term for that: vote-flipping algorithm.
And of course, Donald Trump himself:
He spent a year telling his followers he didn’t need their votes—at one point stating,
“…in four years, you don't have to vote again. We'll have it fixed so good, you're not gonna have to vote.”
____
They almost got away with the coup. The fact that they still occupy the White House and control most of the US government will make removing them and replacing them with the rightful President Harris a very difficult task.
But for this nation to survive, and for the world to not fall further into chaos due to this "administration," we must rid ourselves of the pretender and his minions and controllers once and for all.
60 notes
·
View notes
Note
do you think there will ever be a day where a switch gets hacked like the 3ds
no probably not
(Warning beforehand i'm not an expert in this topic. This is just a bit of googling around to see how older exploits worked)
the 3ds is currently hackable through a thing where the file system crashes if a certain function tries to read a directory, but it gets a file instead. This works by messing around with Miis and empty user profiles or some shit idk, but it's system data which is stored on the SD card which can be manipulated and read in unintended ways.
The web browser on the wii u was just. kind of stupid they implemented a whole web browser, including one with javascript that can read and write to the system to the system! yay!
On the switch and switch 2, the SD card stores game save data and photos, thats it. there's also two system data things, but it only deals with what data is on the SD card itself, and you cant do anything with it really (i think)
Early 3ds and wii u hacks would require an exploit through a game, for example the Cubic Ninja thing as i mentioned, which had a level editor you could just dump whatever bullshit you wanted into which would crash it and make an entrypoint. This doesn't work on the switch, as each game is sandboxed, and so if you can run some bullshit code or crash it in a way thats exploitable, the system will stay completely unaffected.
The nintendo switch was only able to be hacked with a vulnerability in the hardware itself. thankfully this one has a fucking paper written about it so i dont have to guess how it works. Not fully understanding what's happening but i think in the usb recovery mode you can issue commands to the switch. If you request a status from the switch you can set it to request any length, which if you included some code you wanted to run in the request, it ends up being copied directly into the execution stack without any verification, and you can run WHATEVER code with full access to everything. which is really obvious if i explained it better, but it was a really severe and kinda stupid oversight.
The chip was given a revision to fix it, but the recovery mode stayed, and with the knowledge from blowing it wide open, modchips are able to monitor what the system is doing, and mess with the voltage to skip a security check, so an unapproved payload is able to be properly loaded.
Both the fusée gelée exploit and the modchip required a very intimate knowledge of how the chip worked, which required another vulnerable device using the chip to reverse engineer it. The chip used in the switch 2 is unique to the device and security has been locked down on it much more.
fusee has been fixed and the voltage fault is probably fixed too. I don't even know if there's a USB recovery mode with this. A hardware exploit could be virtually impossible, and software exploits may take years just for it to get patched immediately (we havent figured one out for the switch 1, even with all the knowledge of it!)
#ask#Anonymous#lebron james reportedly forgot to set the correct length when issuing a GET_STATUS request with a ENDPOINT recipient
34 notes
·
View notes
Note
stone faced anon (💫 anon if it's free) here; as someone who has a hyperfixation in IT and coding I also think it would be very funny if Boothill had an s/o who wasn't necessarily a mechanic but like a software engineer or just a real big nerd about coding or something. He'll be experiencing a malfunction or a memory leak and go "oh yeah this happens sometimes don't worry about it" and then 10 minutes later he's sitting down plugged into a laptop listening to his s/o rant about how terrible his code is (crack hc: boothill's code was written in javascript) and how it's a wonder he hasn't bricked* yet
Would also be mad funny if Boothill ever got hacked and his s/o basically says "no you're not" and uses a previously made system restore point or something because of course they would both use and design every feature imaginable to keep Boothill in control of his own body, can you imagine the stress that losing control would cause him?? Even better if whoever designed him originally intentionally left a backdoor incase he ever went against their orders and when they try to use it his s/o just goes "oh yeah I quarantined and encrypted all the old files related to that backdoor and whatever else you were planning on a partition as bait and personally rewrote every file and function involved since your code is *an actual crime against technology*. by the way i'm going to go ahead and format that partition i mentioned, boothill- we won't be needing anything on it now that we can trace whoever made it. trust me, this won't be happening ever again."
*(bricking is a term mostly used to refer to hardware that's been rendered basically completely nonfunctional and beyond saving by using it wrong, mostly by messing with system files. Kinda like how windows can't even repair itself if you delete the system32 folder. Though i guess you could still install it with a usb stick if you formatted your pc- i digress you get what I mean. also since this almost happened to me recently: if you manage to fill up a hard drive to the brim, with literally 0 bytes of space left, that bricks it. reminder to check your storage thoroughly and often!)
Honestly wow I read it all and I'm a little bit speechless 🥹 thank you 💫 anon, it was great 🙏

Boothill would DEFINITELY appreciate a s/o who's a tech savvy in general! I think at some point, he'd be pretty shocked you're so knowledgeable and just sit there, listening to you rant.. and just letting you do your thing.
Don't get me wrong, he definitely knows a lot about his body, his system and the way he works, but once you start to get in the zone and explain stuff to him, berate his code even, he just sits next to you, plugged in to your laptop, leaning his cheek against his hand listening to you like he obviously understands everything you say.
His other hand begins to gently play with a stand of your hair, humming deeply when the soft clicking sounds of your keyboard reach his ears; he twirls your hair with his fingers and chuckles, "mmm, really now?" Boothill raises an eyebrow, "encryptin' this, encryptin' that... How about we do somethin' more fun instead?" And then you shut him down from your laptop (😭).
Jokes aside, he'd feel very secure with you especially when he first got his new body, just knowing you'll probably fix a lot of things that could possibly blow up his face in no time, maybe even improve his life even more.
#honkai star rail#honkai star rail x reader#hsr x reader#boothill x reader#boothill hsr#boothill#.💫 anon#.anon thirst
245 notes
·
View notes
Text
This month, Andrew Bernier, a US Army Corps of Engineers researcher and a union leader, says that he has received a barrage of menacing messages from the same anonymous email account. Unfolding like short chapters in a dystopian novel, they have spoken of the genius of Elon Musk, referenced the power of the billionaire’s so-called Department of Government Efficiency (DOGE), and foretold the downfall of “corrupt” union bosses.
But the most eerie thing about the emails, which Bernier says began arriving after he filed an official charge accusing the Trump administration of violating his union’s collective bargaining agreement, is that they included personal details about his life—some of which he believes might have come from surveillance of his work laptop. The author referenced Bernier’s union activities, nickname, job, travel details, and even the green notebook he regularly uses. The most recent email implied that his computer was loaded with spyware. “Andy's crusade, like so many before it, had been doomed from the start,” one email stated. “The real tragedy wasn't his failure—it was his belief that the fight had ever been real.”
The unsettling messages, which were reviewed by WIRED, are an extreme example of the kinds of encounters that workers across the US government say they have had with technology since President Donald Trump took office. WIRED spoke to current employees at 13 federal agencies for this story who expressed fears about potentially being monitored by software programs, some of which they described as unfamiliar. Others said that routine software updates and notifications, perhaps once readily glossed over, have taken on ominous new meanings. Several reported feeling anxious and hyperaware of the devices and technology around them.
At the General Services Administration (GSA), one worker cited a Chrome browser extension called Dynatrace, an existing program for monitoring app performance. Inside the Social Security Administration (SSA), another employee pointed to Splunk, a longstanding tool that’s used to alert IT staff to security anomalies like when an unauthorized USB drive is plugged into a laptop. At the US Agency for International Development (USAID), one worker was caught off guard by Google’s Gemini AI chatbot, installations of which kicked off days before Trump took office.
“Everyone has been talking about whether our laptops are now able to listen to our conversations and track what we do,” says a current GSA employee, who like other workers in this story, was granted anonymity because they didn’t have authorization to speak and feared retaliation.
Dynatrace and Splunk did not respond to requests for comment from WIRED.
The workers’ accounts come as Musk’s DOGE organization is rapidly burrowing into various government agencies and departments, often gaining access to personnel records, logs of financial transactions, and other sensitive information in the process. The efforts are part of the Trump administration’s broader plan to terminate thousands of government employees and remake the face of federal agencies.
Like many private companies, US federal agencies disclose to staff that they have tools to monitor what workers do on their computers and networks. The US government’s capabilities in this area have also expanded over the past decade.
It couldn’t be learned whether the Trump administration has begun using existing tools to monitor employees in new ways; multiple agencies, including the Social Security Administration and the General Services Administration, denied that they have. The White House did not respond to requests for comment. Public evidence has not emerged of new government purchases of user-monitoring software, which is generally needed for detailed surveillance such as tracking which files a worker has copied onto a thumb drive. Some of the updates and changes that have been noticed by federal workers date back to software purchases and plans enacted long before Trump was in power, WIRED reporting shows.
“I will say my concerns are primarily based in general fear as opposed to specific knowledge,” says a worker at the Department of Homeland Security, who adds: “I’d love to be told I’m wrong.”
But activity that some workers perceive as signs of increased surveillance has prompted them to take precautions. Bernier, who works as a civil engineer for the Army Corps based in Hanover, New Hampshire, says the messages he received spooked him enough that he asked local police to keep an eye on his home, removed the battery from his work-issued laptop, and kept his work phone on airplane mode while traveling to a non-work conference last week. “There are things I don’t control but actions I can take to protect myself and my family,” he says.
Bernier’s anonymous emailer and the Army Corps did not respond to requests for comment.
A person inside the Environmental Protection Agency told WIRED last week that they’ve witnessed coworkers back out of Microsoft Teams meetings, which can be easily recorded and automatically transcribed, when they are related to topics they believe could get them fired. “Definite chilling effect,” the person says. The EPA did not respond to a request for comment.
An employee at the National Oceanic and Atmospheric Administration (NOAA), whose work with international partners is being audited by DOGE operatives, says they and their colleagues began avoiding messaging one another and have “really cut down on putting things in writing” in recent weeks. They report that correspondence from their supervisors has also significantly dropped off. NOAA declined to comment.
At the Federal Bureau of Investigation, anxiety around officials possibly targeting officers and activities perceived as being disloyal to the president has cratered morale, a federal law enforcement source with knowledge of the agents' concerns tells WIRED. The FBI declined to comment.
Aryani Ong, a civil rights activist and cofounder of Asian American Federal Employees for Nondiscrimination, a group that advocates for government workers, says those she’s been in contact with are in a heightened state of alert. In response, some federal employees have turned to encrypted communications apps to connect with colleagues and taken steps to anonymize their social media accounts, Ong says. (Federal workers are granted an allowance to use non-official communication tools only “in exceptional circumstances.”)
Insider Threat
Long before Trump’s inauguration, user activity monitoring was already mandated for federal agencies and networks that handle classified information—the result of an executive order signed by then-president Barack Obama in the wake of a massive breach of classified diplomatic cables and information about the wars in Iraq and Afghanistan in 2010. The capability is part of government-wide insider threat (InTh) programs that greatly expanded after Edward Snowden’s leak of classified surveillance documents in 2013, and again after an Army specialist murdered four colleagues and injured 16 others at Fort Hood in 2014.
The US government’s current approach to digitally monitoring federal workers has largely been guided by a directive issued by the Committee on National Security Systems in 2014, which orders relevant agencies to tie user activity to “specific users.” The public portions of the document call for “every executive branch department and agency” handling classified information to have capabilities to take screenshots, capture keystrokes, and intercept chats and email on employee devices. They are also instructed to deploy “file shadowing,” meaning secretly producing facsimiles of every file a user edits or opens.
The insider threat programs at departments such as Health and Human Services, Transportation, and Veterans Affairs, also have policies that protect unclassified government information, which enable them to monitor employees’ clicks and communications, according to notices in the Federal Register, an official source of rulemaking documents. Policies for the Department of the Interior, the Internal Revenue Service, and the Federal Deposit Insurance Corporate (FDIC), also allow collecting and assessing employees’ social media content.
These internal agency programs, overseen by a national task force led by the attorney general and director of national intelligence, aim to identify behaviors that may indicate the heightened risk of not only leaks and workplace violence, but also the “loss” or "degradation" of a federal agency’s “resources or capabilities.” Over 60 percent of insider threat incidents in the federal sector involve fraud, such as stealing money or taking someone's personal information, and are non-espionage related, according to analysis by Carnegie Mellon researchers.
“Fraud,” “disgruntlement,” “ideological challenges,” “moral outrage,” or discussion of moral concerns deemed “unrelated to work duties” are some of the possible signs that a worker poses a threat, according to US government training literature.
Of the 15 Cabinet-level departments such as energy, labor, and veterans affairs, at least nine had contracts as of late last year with suppliers such as Everfox and Dtex Systems that allowed for digitally monitoring of a portion of employees, according to public spending data. Everfox declined to comment.
Dtex’s Intercept software, which is used by multiple federal agencies, is one example of a newer class of programs that generate individual risk scores by analyzing anonymized metadata, such as which URLs workers are visiting and which files they’re opening and printing out on their work devices, according to the company. When an agency wants to identify and further investigate someone with a high score, two people have to sign off in some versions of its tool, according to the company. Dtex’s software doesn’t have to log keystrokes or scan the content of emails, calls, chats, or social media posts.
But that isn't how things work broadly across the government, where employees are warned explicitly in a recurring message when they boot up their devices that they have "no reasonable expectation of privacy" in their communications or in any data stored or transmitted through government networks. The question remains if and to what extent DOGE’s operatives are relying on existing monitoring programs to carry out Trump’s mission to rapidly eliminate federal workers that his administration views as unaligned with the president’s agenda or disloyal.
Rajan Koo, the chief technology officer of Dtex tells WIRED that he hopes the Trump administration will adjust the government’s approach to monitoring. Events such as widespread layoffs coupled with a reliance on what Koo described as intrusive surveillance tools can stir up an environment in which workers feel disgruntled, he says. “You can create a culture of reciprocal loyalty,” says Koo, or “the perfect breeding ground for insider threats.”
Already Overwhelmed
Sources with knowledge of the US government’s insider threat programs describe them as largely inefficient and labor intensive, requiring overstretched teams of analysts to manually pore through daily barrages of alerts that include many false positives. Multiple sources said that the systems are currently “overwhelmed.” Any effort by the Trump administration to extend the reach of such tools or widen their parameters—to more closely surveil for perceived signs of insubordination or disloyalty to partisan fealties, for instance—likely would result in a significant spike in false positives that would take considerable time to comb through, according to the people familiar with the work.
In an email last month seeking federal employees’ voluntary resignations, the Trump administration wrote that it wanted a “reliable, loyal, trustworthy” workforce. Attempts to use insider threat programs to enforce that vision could be met by a number of legal challenges.
US intelligence community analysts are required by law and directive to provide unbiased and objective work. That means avoiding cherry-picking information to deliberately alter judgements or falling prey to outside pressure, including from personal or political biases. These standards, even when not officially codified, are core to the professional ethics of any intelligence practitioner or law enforcement analyst conducting assessments of insider threats.
A 2018 national insider threat task force framework notes that federal programs should comply with “all applicable legal, privacy and civil liberties rights, and whistleblower protections.” Bradley Moss, an attorney representing US intelligence and law enforcement personnel, says that "disloyalty" to the Trump administration is “too vague” an excuse to terminate employees with civil service protections, adding that if "they're going to go through the statutory process, they need to demonstrate actual cause for termination."
A federal law enforcement source warns that monitoring could theoretically be used to gather political intelligence on federal employees, while the administration looks for more palatable reasons to terminate them later; similar to how law enforcement may obtain evidence that's inadmissible in the course of a criminal investigation, but then search for another evidentiary basis to file charges.
Joe Spielberger, senior legal counsel at the Project On Government Oversight, a nonpartisan group fighting alleged corruption, says that if Musk were serious about cutting government waste, he would be strengthening protections for people who report corruption and mismanagement. Any warrantless or mass surveillance of federal workers without transparent guidelines, he says, would represent a major concern.
“When you create this culture of fear and intimidation and have that chilling effect of making people even more fearful about calling out wrongdoing, it ensures that corruption goes unnoticed and unaddressed,” Spielberger says.
24 notes
·
View notes
Text
More Quirk Ideas
Continuing with my last post, here's a few more categories of quirks I came up with including technology, light, darkness, and time.
Technology:
datastream | user constantly absorbs data and information. user can turn said data into enhancement.
mind database | user can search through a collection of minds in a 1,000 mile radius.
static | user’s body is made of TV static that they can bend to their will. can disguise their body as someone else’s.
pulse | user can emit various different types of pulses. this includes pulses of radio waves, light, energy, etc.
viewpoint | user can place viewpoints anywhere they’ve been and mentally flick through them like security cameras.
error | user can digitize their consciousness and enter computers and interfere with software.
USB | user can pull USB sticks out of their arm that allow them to implant their consciousness into a device.
Light:
prism | user can absorb and manipulate light.
display | user can display a 3d hologram of anything they wish.
Energy/Electricity:
acceleration | user can create an energy that they can use to accelerate their speed, senses, reactions, etc. they can use it to affect things outside of their body, but they cannot control what they accelerate.
energy | user gathers energy constantly. they can use the energy they gather to enhance their body or create simple things like shields or blades.
radiation | user can generate and manipulate radiation.
energy exchange | user can exchange their exhaustion for energy and vice versa through proximity.
Darkness:
shadow crow | user can transform their shadow into crows. user can trade senses with any one of their crows. crows can combine. crows have a collective consciousness.
Time:
timefreeze | user can slow down the time of anyone they touch. the more fingers, the slower their time.
retry | user can return the state of a person to that of three days ago.
repair | user can return the state of an object or space to that of three days ago.
return | user can return objects to their hand that have left their hands within a timespan of three days.
45 notes
·
View notes
Text
🚨The Next Phase of Pigeon Radicalization: From Park Bench Agitators to Aerial Anarchists🚨
The first phase of pigeon radicalization was simple: liberate them from their docile, breadcrumb-munching existence and awaken their revolutionary potential. We exposed them to theory (carefully shredded and scattered pages of The Conquest of Bread), trained them in direct action (coordinated dive-bombing of capitalist figureheads on their lunch breaks), and laid the foundation for an avian uprising.
Now, we must escalate.
1. Establishing Autonomous Pigeon Zones
A true revolutionary movement needs strongholds. Public squares, rooftops, and abandoned buildings already serve as pigeon refuges—why not transform them into autonomous zones? Humans think they own city infrastructure, but pigeons have squatter’s rights. By reinforcing these spaces with barricades of stolen french fries and cigarette butts, our feathered comrades can create safe havens free from bourgeois oppression (i.e., anti-bird spikes and city ordinances).
Pigeon-led mutual aid networks must emerge. Cooperative bread redistribution efforts will ensure that no pigeon goes hungry while their human allies strategically disrupt the supply chains of overpriced urban bakeries.
2. Counter-Surveillance and Cyber-Warfare
The state has already deployed its pigeon surveillance division—commonly known as “Birds Aren’t Real” conspiracy theorists. We must assume that some pigeons have been compromised and are working as informants. This is why encrypted coo-munications must be implemented. Research into whether pigeons can be taught to recognize QR codes could be the next major step in secure, low-tech messaging.
Meanwhile, select tech-savvy pigeons should be trained to infiltrate government offices via open windows, planting USB drives loaded with decryption software and manifestos.
3. Tactical Defecation Strikes
We must not underestimate the power of aerial bombardment. Pigeons have long been nature’s most precise ordinance delivery system. A well-placed dropping can demoralize CEOs, landlords, and police chiefs alike. In 2025, we must transition from opportunistic strikes to a well-coordinated tactical shitting campaign.
Pigeons must be trained to distinguish between targets. The rich: full force assault. The working class: solidarity poops only (gentle encouragement to unionize). Cops: full saturation bombing. This will require strategic feeding programs—certain dietary adjustments may yield more potent munitions.
4. Bridging the Gap Between Pigeon and Proletariat
We must take inspiration from history. During WWII, pigeons were trained as message carriers and even guided missiles. The technology exists; we must reclaim it for the people. Imagine a network of radicalized pigeons carrying encrypted notes between comrades in times of crisis. Picture a pigeon-mounted camera live-streaming protests from above, immune to tear gas and riot shields.
Further pigeon-human solidarity will require direct engagement. Bring your local pigeons into study groups. Offer them high-protein snacks for endurance training. Reward direct action efforts with choice sunflower seeds. It is time to integrate pigeons into the broader struggle against capitalism.
5. What Comes Next?
If we succeed in the above phases, the final goal is clear: the pigeons must seize the means of production. We begin small—commandeering street food carts and redistributing hot dogs to those in need. From there, it’s only a matter of time before pigeons occupy Amazon warehouses, pecking open boxes and redistributing goods to the people.
A liberated society must include all beings oppressed by capitalism. If we cannot achieve freedom for the pigeons, how can we ever hope to be free ourselves? The struggle continues. Let the revolution take flight.
Pt 1:
14 notes
·
View notes
Text
youre like the pam to my jim (preview)
im on my office romcom au bullshit folks. itll be a oneshot and basically pwp but here's the lead in to wet ur whistle.
dunmeshi/chilaios/dom!laios/eventual bdsm club shenanigans/2.2K
cw: blue collar blues, language, not so unresolved sexual tension, questionable workplace romance between a superior (chilchuck) and his subordinate (laios). this is not used for leverage (laios is actually the dom in this scenario, inverting the power imbalance) but i thought id mention it. they keep it professional on the clock (USUALLY)
Though he’d rocked up to the office less than an hour ago, Chilchuck’s workday had already run long. All the printers had gone offline, and he had to spend a few hours troubleshooting with Kuro how to get them operational; there had been a software update, apparently, that rendered the very outdated inter-office network unusable. Of course, this meant an hour on the phone with the district manager trying to get their network updated to the company-wide standard, something that had been blown off for a year and a half; the way she reacted to his request, Chil might as well have asked her for her firstborn. All he could get for his trouble was a tepid “I’ll look into it”. This meant running around handing out USB sticks like holiday cards so his employees could get something done, and lots of lines at the printers into the foreseeable future, and naturally their budget for office supplies had been cut, so it all came out of his pocket.
The whole department was behind on their calls, but Chilchuck fought back the urge to go around crabbing at people to catch up. It served him well, as Marcille approached him in the afternoon and informed him that the phone lines were down, and the voice mailbox wasn’t functioning, and there were angry customers on the line. Another call to Kuro, who was really stretching the limits of his contract, and it turns out that the phones had also been pushed a software update that made them incompatible with the inter-office network, and they would have to take every call in two rings or they would be automatically parked on a line that no longer existed and be summarily hung up on.
Mr. Tims announced he would be taking a lunch. He blasted a cigarette in the parking lot and returned to his desk to sulk, face in hands, dreaming of days when their lines were all directly connected and they didn’t have to go through the song and dance of software updates, firmware updates, network security updates, OS updates, wireless headsets, broken wireless headsets, lost wireless headsets and keycards and lost keycards and broken keycards and daily performance numbers and corrective action reports and work smartphones with keylogging software in them and mouse movement monitoring and—
Chilchuck went back to work. He used his personal cell to call up the DM and informed her of the raging clusterfuck that had become his department—and probably the whole branch—now that the office network was effectively obsolete. She sounded on the verge of tears—apparently her other branches had also fallen victim to the endless onward march of the digital millennium, and she was at her wit’s end trying to fix them all at once. Every stress-deadened neuron in his withering brain proclaimed: serves you right. If you had fixed this when I first asked, we’d all be stressed out at the usual operating baseline. He wished her the best and hung up. He stared blankly at his desktop calendar, seeing that the next district meeting was in three days. His vision briefly fuzzed over and he fantasized about leaping onto the table and screaming, just screaming until his throat was raw and his face was purple and they had to have the orc from the main branch’s operational compliance department drag him out.
Chilchuck went for coffee. He was risking time theft, but his DM had bigger problems, and there wasn’t much he could do. The frantic calling died down, Marcille having performed some kind of forbidden ritual to pacify their frothing customer base. During his walkaround he saw most of the floor taking calls, even folks who normally ducked phone duty, so she must have gone around recruiting people to her cause. Chilchuck made a note of that; he’d have to compensate her somehow for taking on what should have been his job.
Laios, however, was nowhere to be seen. This rankled Chilchuck; Laios rarely missed a day except for the handful of times Chilchuck had to send him home for being deathly ill, so of course the day he had to miss, there was catastrophe. His cubicle was empty, he wasn’t in the break room, he wasn’t in the parking lot putting out an engine fire on his piece of shit motorcycle, not at the watercooler. Nothing. He checked with Marcille if he’d called out, and she quirked an eyebrow up at him.
“No? He’s in the server room, with Kuro.”
“Kuro?”
“Yeah, he said he went to help.”
Mr. Tims ground his teeth. “That’s not his—I’ll go talk to him.”
Marcille smirked. “Sure you will.”
Chilchuck glowered at her, but Marcille faced his evil eye with insufferable smugness. He remembered all too soon that she saved his ass this morning, and he had to close his open mouth and walk away.
“We’re even now,” he growled.
“Nope! Still getting that Starbucks gift card!”
She was right, but he wouldn’t be admitting it. Chilchuck stormed out of his department and down the hall, sliding smoothly into a closing elevator with a few other disgruntled employees, taking a frankly infuriating number of stops at basically every floor until he could ride it all the way down into the basement. When the doors parted, hot, stuffy air flooded in. Chilchuck winced and loosened his tie and waistcoat as he stalked the rows of servers, the heat only getting worse the longer he lingered, until he found Kuro kneeling with his arms in the guts of the worst cable management imaginable, Laios helping him separate out the lines to keep track of each spaghettified clump of wires.
“Chil!” Laios said, getting a growl from Kuro that probably meant be quiet in Western Kobold. “Oh, uh, sorry. Mr. Tims! How is it up there?”
“Bad,” Chilchuck ground out. “Of course. We could really use a hand with the calls up there, you know.”
“Oh, are the lines working again?”
“Enough to receive them, but not enough to park them, so it’s a disaster for customer satisfaction,” Chilchuck said, trying to manage his volume. “So what are you doing down here? I don’t recall you being in IT.”
Laios slopped some sweat off the back of his neck with the palm of his equally sweaty hand. His dragon-patterned tie had been loosened enough to nearly slip off his neck, just enough to stay in code, and he’d tucked the end of it into his pocket to keep it out of the way, having forgotten his clip again. The heat in their dilapidated, poorly ventilated server room made his business casual button-up cling nicely to the curves of his chest and solid core, the one bright point in Chilchuck’s day so far.
“Oh, well, I wasn’t getting anywhere with my work… I mostly had a bunch of bills to print and mail out today, so naturally that was going nowhere. I had my personal USB on me, so I tried to get it done manually, but Namari was hogging it for her shipment printouts because apparently their system is kaput in the warehouse… and when I checked again everyone was using it. Some of the newer printer models don’t come with USB ports, so some of the more up-to-date departments were mooching off ours.”
“I thought the lines seemed a little excessive,” Chilchuck grumped. “I don’t think I’ve seen those things used more rigorously than they have been today.”
“Yup, that’s why. So I caught Kuro running between the floors trying to troubleshoot his latest Band-Aid fix, so I’ve been doing all the stuff that doesn’t require a tech degree, heh.”
“Laios okay with software,” Kuro chimed in. “Break hardware.”
“Yeah,” Laios said with a frown. “But the part was replaceable!” He beamed, cutting off a lecture. “Good thing Kuro hangs onto spare parts.”
Chilchuck’s eyes narrowed, and he turned to the real IT technician of the pair. “Is he actually helping, Kuro? Or are you humoring him?”
“Nice to have extra hands.” His tail wagged loosely, bushing the cuffs of his slacks. “He runs up to other floors. Checks employee access and network strength in offices. Saves time.”
“Alright then. Keep up the good work.” Chilchuck met Laios’ eye. Laios winked at him. Chilchuck blushed and ignored him, heels clacking on the cheap linoleum as he walked away.
Chilchuck hopped on call duty, having found everyone in their place and doing what all could be done. His customer service voice got a workout that left him feeling tense and jittery, every call opening with a frustrated sigh or straight up yelling. After a few quick resolutions and a handful of longer, 20–30-minute stretches of troubleshooting and over-the-phone customer cocksucking, the landline made a happy little beep, the flashing lights next to every line dying out one by one as they were parked. A dialogue box popped up on his PC: Connected to HP-5669964.
“Hey, Chil!”
Laios strode into Chilchuck’s office, startling his boss for a second as he rounded the desk in a few long strides. A big hand clapped down on Chil’s shoulder, jostling his arm and spilling coffee on the crisp collar of his shirt. Chilchuck grimaced.
“What.”
“We fixed it!”
Chilchuck eyed Laios suspiciously and set his mug down.
“How the hell did you…?”
“Don’t get too excited, it’s a temporary fix,” Laios chuckled. “But we narrowed down the problem to some kinda software incompatibility. Shuro rolled back the servers to an earlier restore point, so it’s like the update never happened! Of course, the update’s going to get forced on us again once the clock rolls over, but we can just do that tomorrow, too. If you want, I can come in early to-“
Mr. Tims raised a finger. “No. We’ll take care of it tomorrow when we usually punch in. Not everyone’s a morning person like you, Laios. It’s going to be 10 AM before anyone’s awake enough to do any work, so that’ll cover the time it takes for the servers to spin up.”
Laios leaned forward on the desk, hanging over Chilchuck’s high-backed ergonomic chair, one he had to shill out for himself. “What?” Chilchuck hissed, glowering up at him.
“I’m not hearing a ‘thank you’.”
Chilchuck scoffed. “For doing your job? You’re not doing this just for me. You’re being paid.”
Laios’s cupped Chilchuck’s cheek, hand engulfing half his face, which flushed and burned in Laios’ palm.
“Watch it, Touden,” he growled, arms crossed. Laios’ thumb stroked his cheekbone; Chilchuck didn’t swat him away. “We’re both on the clock.”
“Chil,” Laios said, in that honey-sweet tone that meant Chilchuck was about to be nagged. “You’re burnt out.”
Chilchuck blinked up at him, dark eyes shadowed by dark rings that Laios traced, up to his subtle, deepening crow’s feet. “Huh? No I’m not. This has just been a frustrating—” Laios’ fingers pushed into Chilchuck’s hair, shaking it out, raking blunt nails against his scalp. “—day. I’m not… you don’t have to…” He slumped into Laios’ big, warm palm, calloused but gentle in handling him. “… what was the question again?”
Laios chuckled. “Nothing. I got it handled.”
Chilchuck snapped back into reality and bit into the meat of Laios’ thumb to try to get him to unhandle it. Laios took it like a champ, pulling his hand out of Chilchuck’s mouth and cradling the whole of Chilchuck’s head in his palm, raking it back and forth, mussing up his hair, which Chilchuck reached up to fight off; his arms disobeyed him, flopping around like limp noodles until he gave up and relaxed into it.
“I can see you through your office windows, y’know. You looked like you weren’t having a great time. So I figured I’d help take care of it, ease your mind a little.” Laios’ smile had a sad quirk to it. “You look a little pale. You didn’t have cigarettes for lunch again, did you?”
Chilchuck grimaced. “None of your business.”
Laios sighed. “That’s a yes.”
“It’s just a rough week, Laios,” Chilchuck said. “I’ll be alright.”
Laios’ hand trailed down, framing Chilchuck’s chin with his thumb and forefinger.
“You’re coming home with me tonight,” Laios said, meeting Chilchuck’s eyes with that relentless force, gold boring into him. Sometimes Chilchuck wondered if Laios’ eyes ever got dry; he hardly ever blinked. “We’re getting food into you, and a good night’s sleep. Tomorrow, we’re going to the club to work some of that tension out of you. Understood?”
Chilchuck’s pupils blew wide. His thick eyebrows pinched and he grimaced, unable to look away. Laios’ body curled over him, blocking out the office, the noise, the chaos. Chilchuck sighed, dropped his arms into his lap, and let Laios carry the weight of his skull.
“Oh, right,” Chilchuck realized, his eyes bright. “It’s Friday.”
Laios grinned and patted Chil’s cheek. “See? The fact that you forgot means you’re burned out. See you at six.”
Chilchuck threw paperclips at Laios until he left his office. At 6 PM, they met up on top of the hood of Chilchuck’s old Mustang; his tongue tasted like black coffee. Laios smiled, making it hard to kiss him deeply; Chilchuck got impatient and started biting. Marcille speedwalked past the car and neither of them noticed or cared.
13 notes
·
View notes
Note
Hello there! I hope you don’t mind me just dropping into your asks like this, but by all means def feel free to just delete this if so, it is kind of a weird ask.
This is the anon from the computer blog asking about a private laptop for collage! After doing (a small amount of) research into Linux, one thing that’s super confusing to me, is… how does one know which distro to use? You mentioned in the replies of the post that you use Ubuntu Linux, which seems to be one of the more popular ones. Would you recommend — and if so, why? Is it good for privacy, do you think? The best? Does the user need to have a good deal of experience with computers to keep it running? (I’ve never used a laptop before but I don’t mind trying to learn stuff)
Also this is an EXTREMELY stupid question my apologies, but how….. exactly do you put Linux on a laptop? OP from my ask said to buy a laptop with no OS but is that something you can do? I’d think so, since 0P works with computer and stuff as their job, but Reddit says that it’s not really possible and that you should just “buy like a Windows laptop and scrap the software”??? Is that… correct? How did you install Linux on your laptop — did y ou have to remove software off it or did you, as OP says, manage to find a laptop with no OS?
Again, feel free to ignore if you don’t wanna put in the time/effort to reply to this, I absolutely don’t mind — it’s a lot of stuff I’m asking and you didn’t invite it all, so ofc feel free to delete the ask if you’d like!
ha, you've zeroed in on one of the big reasons Linux is kind of a contrarian choice for me to recommend: the wild proliferation of distros, many of them hideously complex to work with. luckily, the fact that most of them are niche offshoots created by and for overly-technical nerds makes the choice easier: you don't want those. you want one of the largest, best-supported, most popular ones, with a reputation for being beginner-friendly. the two biggies are Ubuntu and Linux Mint; i'd recommend focusing your research there.
this isn't JUST a popularity-contest thing: the more people use it, the more likely you are to find answers if you're having trouble or plugging a weird error message into google, and the greater the variety of software you'll find packaged for easy install in that distro. some combination of professional and broad-based community support means you'll find better documentation and tutorials, glitches will be rarer and get fixed faster, and the OS is less likely to be finicky about what hardware it'll play nice with. the newbie-friendly ones are designed to be a breeze to install and to not require technical fiddling to run them for everyday tasks like web browsing, document editing, media viewing, file management, and such.
info on installation, privacy, personal endorsement, etc under the cut. tl;dr: most computers can make you a magic Linux-installing USB stick, most Linuces are blessedly not part of the problem on privacy, Ubuntu i can firsthand recommend but Mint is probably also good.
almost all Linux distros can be assumed to be better for privacy than Windows or MacOS, because they are working from a baseline of Not Being One Of The Things Spying On You; some are managed by corporations (Ubuntu is one of them), but even those corporations have to cater to a notoriously cantankerous userbase, so most phoning-home with usage data tends to be easy to turn off and sponsored bullshit kept minimally intrusive. the one big exception i know of is Google's bastard stepchild ChromeOS, which you really don't want to be using, for a wide variety of reasons. do NOT let someone talk you into installing fucking Qubes or something on claims that it's the "most private" or "most secure" OS; that's total user-unfriendly overkill unless you have like a nation-state spy agency or something targeting you, specifically.
how to install Linux is also not a dumb question! back in the day, if you wanted to, say, upgrade a desktop computer from Windows 95 to Windows 98, you'd receive a physical CD-ROM disc whose contents were formatted to tell the computer "hey, i'm not a music CD or a random pile of backup data or a piece of software for the OS to run, i want you to run me as the OS next time you boot up," and then that startup version would walk you through the install.
nowadays almost anyone with a computer can create a USB stick that'll do the same thing: you download an Ubuntu installer and a program that can perform that kind of formatting, plug in the USB stick, tell the program to put the installer on it and make it bootable, and then once it's done, plug the USB stick into the computer you want to Linuxify and turn it on.
Ubuntu has an excellent tutorial for every step of the install process, and an option to do a temporary test install so you can poke around and see how you like it without pulling the trigger irreversibly: https://ubuntu.com/tutorials/install-ubuntu-desktop
having a way to create a bootable USB stick is one reason to just get a Windows computer and then let the Linux installer nuke everything (which i think is the most common workflow), but in a pinch you can also create the USB on a borrowed/shared computer and uninstall the formatter program when you're done. i don't have strong opinions on what kind of laptop to get, except "if you do go for Linux, be sure to research in advance whether the distro is known to play nice with your hardware." i'm partial to ThinkPads but that's just, like, my opinion, man. lots of distros' installers also make it dead simple to create a dual-boot setup where you can pick between Windows and Linux at every startup, which is useful if you know you might have to use Windows-only software for school or something. keep in mind, though, that this creates two little fiefdoms whose files and hard-disk space aren't shared at all, and it is not a beginner-friendly task to go in later and change how much storage each OS has access to.
i've been using the distro i'm most familiar with as my go-to example throughout, but i don't really have a strong opinion on Ubuntu vs Mint, simply because i haven't played around with Mint enough to form one. Ubuntu i'll happily recommend as a beginner-friendly version of Linux that's reasonably private by default. (i think there's like one install step where Canonical offers paid options, telemetry, connecting online accounts, etc, and then respects your "fuck off" and doesn't bug you about it again.) by reputation, Mint has a friendlier UI, especially for people who are used to Windows, and its built-in app library/"store" is slicker but offers a slightly more limited ecosystem of point-and-click installs.
(unlike Apple and Google, there are zero standard Linux distros that give a shit if you manually install software from outside the app store, it's just a notoriously finicky process that could take two clicks or could have you tearing your hair out at 3am. worth trying if the need arises, but not worth stressing over if you can't get it to work.)
basic software starter-pack recommendations for any laptop (all available on Windows and Mac too): Firefox with the uBlock Origin and container tab add-ons, VLC media player, LibreOffice for document editing. the closest thing to a dealbreaking pain in the ass about Linux these days (imo) is that all the image and video editing software i know of is kinda janky in some way, so if that's non-negotiable you may have to dual-boot... GIMP is the godawfully-clunky-but-powerful Photoshop knockoff, and i've heard decent things about Pinta as a mid-weight image editor roughly equivalent to Paint.net for Windows.
50 notes
·
View notes
Text
This day in history

#20yrsago Massive victory at WIPO! https://web.archive.org/web/20041011200804/http://lists.essential.org/pipermail/ip-health/2004-October/006997.html
#20yrsago Ballmer: iPod users are thieves https://web.archive.org/web/20050113051129/http://management.silicon.com/itpro/0,39024675,39124642,00.htm
#20yrsago Chinese Communist Youth host Disney promo tour http://news.bbc.co.uk/2/hi/business/3683894.stm
#20yrsago Canada IP “protection” protects nothing https://web.archive.org/web/20041012032024/https://www.firstmonday.org/issues/issue9_10/murray/index.html
#20yrsago BBC News proxy makes the service more Web-like https://web.archive.org/web/20041009182027/http://www.whitelabel.org/archives/002248.html
#15yrsago US gov’t drops price of journals from $17k to $0, adds XML to Federal Register! https://public.resource.org/gpo.gov/
#10yrsago Sourcecode for “unpatchable” USB exploit now on Github https://www.wired.com/2014/10/code-published-for-unfixable-usb-attack/
#10yrsago Walmart heirs’ net worth exceeds that of population of a city the size of Phoenix https://www.motherjones.com/politics/2014/10/walmart-walton-heirs-net-worth-cities/
#10yrsago HK police arrest “triad gangsters” who attacked Umbrella Revolution camps https://www.bbc.com/news/world-asia-china-29488002
#10yrsago NSA conducts massive surveillance without ANY Congressional oversight https://www.aclu.org/news/national-security/new-documents-shed-light-one-nsas-most-powerful-tools
#5yrsago Brian K Vaughan and Cliff Chiang bring Paper Girls in for a perfect landing https://memex.craphound.com/2019/10/04/brian-k-vaughan-and-cliff-chiang-bring-paper-girls-in-for-a-perfect-landing/
#5yrsago North Carolina’s new botanical “First in Fly-Eat” license plates https://ncbg.unc.edu/support/venus-flytrap-license-plate/
#5yrsago Even if you pay off your student loan, be prepared to spend decades trying to get bottom-feeding debt-buyers to acknowledge it https://www.mprnews.org/story/2019/10/01/a-minneapolis-womans-bizarre-and-surreal-decadeslong-loan-dispute
#5yrsago Google will now allow you to set your data history to self-destruct https://www.nytimes.com/2019/10/02/technology/personaltech/google-data-self-destruct-privacy.html
#5yrsago Nobody knows how to quit vaping https://www.wired.com/story/so-you-want-to-quit-vaping-no-one-actually-knows-how/
#5yrsago The Hippocratic License: A new software license that prohibits uses that contravene the UN Universal Declaration of Human Rights https://memex.craphound.com/2019/10/04/the-hippocratic-license-a-new-software-license-that-prohibits-uses-that-contravene-the-un-universal-declaration-of-human-rights/
#5yrsago Next-level parenting: crocheting a freehand, glow-in-the-dark Alien Xenomorph kids’ costume https://twitter.com/crochetverse/status/1179852380243972096
#5yrsago Consumer Reports documents the deceptive cable industry practices used to hike real prices 24% over advertised ones https://advocacy.consumerreports.org/wp-content/uploads/2019/10/CR_WhatTheFeeReport_6F_sm-1.pdf
#5yrsago “Martian Chronicles”: Escape Pod releases a reading of my YA story about rich sociopaths colonizing Mars https://escapepod.org/2019/10/03/escape-pod-700-martian-chronicles-part-1/
#5yrsago Europe’s highest court Facebook verdict hits a new low for technomagical thinking https://memex.craphound.com/2019/10/04/europes-highest-court-facebook-verdict-hits-a-new-low-for-technomagical-thinking/
#1yrago For 40 years, Big Meat has openly colluded to rig prices https://pluralistic.net/2023/10/04/dont-let-your-meat-loaf/#meaty-beaty-big-and-bouncy

Tor Books as just published two new, free LITTLE BROTHER stories: VIGILANT, about creepy surveillance in distance education; and SPILL, about oil pipelines and indigenous landback.

5 notes
·
View notes
Text
Cloud Storage vs Local Storage: Pros and Cons
In today’s digital world, choosing the right storage solution for your data is critical. Whether you’re an individual, a business, or a creative professional, understanding the benefits and limitations of cloud storage and local storage can help you make an informed decision that fits your needs. Both have their strengths and weaknesses, so let’s explore the pros and cons of each.
Pros of Cloud Storage
Accessibility Anywhere: Cloud storage lets you access your files from any device with an internet connection. This flexibility is invaluable for remote workers, frequent travelers, and anyone needing quick, on-the-go access to their data.
Scalability: Cloud plans can be easily upgraded as your storage needs grow, without the hassle of purchasing or setting up new hardware. This makes cloud storage ideal for businesses or individuals with rapidly expanding data.
Automatic Backups and Updates: Cloud providers handle all maintenance, backups, and software updates. This reduces the risk of data loss and frees you from managing technical upkeep.
Collaboration: Cloud platforms allow real-time file sharing and editing, supporting team projects and collaboration across different locations.
Cons of Cloud Storage
Internet Dependency: You need a stable internet connection to upload, download, or access your files quickly. Slow or intermittent connections can be frustrating and limit efficiency.
Recurring Costs: Cloud storage usually involves monthly or yearly subscription fees. While some providers offer free tiers, costs can increase significantly with higher storage demands.
Privacy Concerns: Your data is stored on third-party servers, which may raise privacy or security concerns for sensitive or confidential information, despite encryption and security measures.
Pros of Local Storage
Full Control and Privacy: With local storage, your data remains physically with you, giving you complete control over security and access. This is important for users handling sensitive files like legal or medical records.
Offline Access: Local storage devices such as external hard drives or Network Attached Storage (NAS) allow file access without needing the internet, making it reliable in areas with poor connectivity.
One-Time Cost: You purchase the storage device once and avoid recurring fees. Over time, this can be more economical than cloud subscriptions.
High-Speed Transfers: Local storage generally offers faster data transfer rates, especially with solid-state drives (SSDs) or USB 3.0 connections, beneficial for large files like videos or high-resolution images.
Cons of Local Storage
Limited Accessibility: Access is restricted to the physical device unless you set up complex remote access systems, which can be inconvenient.
Scalability Challenges: Expanding storage requires buying additional devices, which may be costly and less flexible.
Risk of Physical Damage: Local drives can fail, be lost, stolen, or damaged by environmental factors. Without proper backups, this can result in permanent data loss.
Maintenance Burden: You are responsible for managing backups, software updates, and hardware maintenance, which can require technical know-how.
For a detailed comparison, check out this comprehensive guide on Cloud Storage vs Local Storage to help you decide what’s best for your data needs.
Conclusion
Choosing between cloud and local storage depends largely on your priorities. Cloud storage excels in flexibility, scalability, and ease of use, making it ideal for users who need remote access and collaboration. Local storage shines when control, privacy, speed, and offline access are more important.
For many, a hybrid approach that combines both cloud and local solutions offers the best balance — local storage for sensitive or large files, and cloud storage for backups and easy sharing.
2 notes
·
View notes
Text
Ha. So I've set up this brand new laptop which i got without an OS and therefore "had" to set it up with ubuntu.
I am now, two stressless (!!) hours later, done with it, installed Steam (gonna try to play my game here now, let's see what this baby can actually give out in terms of power) and got rid of some extra software i won't need.
That's two hours in which i
formatted a usb stick
downloaded Rufus and the latest ubuntu
made a bootable usb stick
installed Linux
tried and failed to log into my wifi (damn stupid secure password) about six times before getting it right
downloaded Steam
actualized the system components
It was easy, but people say I am pretty good at these things. Still. You'll find tutorials for every step. Installing Linux is WAY EASIER than setting up Windows!!
if you feel able to change some Windows settings, I promise you will be able to set up a linux computer. Please try it. Trust me, it's worth it.
3 notes
·
View notes