#virtual telephone number
Text
Top Leased Line,Internet leased line
Being a skilled enterprise telecom solution provider and Internet Service Provider in India. We stand out to offer an ideal telecom and internet solutions such as Leased Line, Leased line connection, Internet leased line, Internet leased line provider, VOIP, ip phone, Dedicated leased line provider, voip service providers, call centre services, mobile voip, call center solutions, ivr service provider, contact centre solutions, ivr call, ivr service, ivr systems, SIP trunk, virtual telephone number, virtual number, inbound call centre in India. Refer here https://www.pulse.in/
#Internet leased line#Leased Line#Leased line connection#Internet leased line provider#Dedicated leased line provider#ip phone#voip service providers#mobile voip#call centre services#contact centre solutions#ivr systems#virtual telephone number#inbound call centre#contact centre
0 notes
Text
Best Internet leased line
Pulse Telesystems renowned as one of the best Internet Telephony Service Provider and Internet Service Provider in India. We try to suggest the top telecom and Internet solutions like Leased Line, Internet leased line, Leased line connection, Internet leased line provider, Dedicated leased line provider, VOIP, ip phone, voip service providers, mobile voip, call centre services, call center solutions, contact centre solutions, ivr service provider, ivr call, ivr systems, ivr service, SIP trunk, virtual number, virtual telephone number, inbound call centre in India. Visit https://www.pulse.in/
#Leased Line#Internet leased line#Leased line connection#Internet leased line provider#Dedicated leased line provider#VOIP#voip service providers#ip phone#mobile voip#voip services#call centre services#call center solutions#contact centre solutions#ivr service provider#ivr call#ivr systems#virtual telephone number
0 notes
Text
When does Dungeon Meshi take place?
This is an excerpt from Chapter 2 of my paper, "Real World Cultural and Linguistic Influences in Delicious in Dungeon."
Dungeon Meshi takes place in the year 514, however we don’t know how that number relates to anything else in the Dungeon Meshi world, so it isn’t really useful for identifying what era Kui is trying to depict.
It can’t be that the Ancient Cataclysm happened 514 years ago (it was still referred to as ancient history by Thistle and Delgal a thousand years ago), and it can’t be when the current elf queen’s reign began (she’s only 372), so it’s either marking some other major event, like the beginning of the reign of a royal family or the end of a war, or they reset their calendar at regular intervals, such as every two-thousand years for record-keeping purposes.
In the real world, 514 CE would have been the early Medieval era, just after the collapse of the Western Roman Empire, which left Europe fractured into many small Germanic kingdoms competing with each other. It was also the beginning of the Asuka period in Japan, and the end of the Northern Wei Dynasty in China.
This has some similarities to the world we’re shown in Dungeon Meshi: the Western elves have abandoned most of their land in the Eastern hemisphere, leaving the local dwarven, gnomish and tall-man people (whose cultures are primarily Germanic) to fight amongst themselves for the land. A massive upheaval caused by a major imperial power collapsing.
However, based on character behavior, culture, clothing and technology, Dungeon Meshi appears to be set in a vaguely Renaissance (1450 CE-1650 CE) time period, with some elements from classical antiquity (800 BCE-500 CE), the Medieval era (476 CE-1300 CE), as well as some hyper-advanced steampunk/magic technology and modern day anachronisms.
(Potential spoilers beyond the cut.)
The technological and artistic development of the different cultures is very different, with the long-lived races appearing to live a more modern lifestyle than the short-lived races. In the extra materials, Toshiro implies that Falin might find the Island of Wa “primitive” because they lack the social and technological advancements that come from contact with the long-lived races, and the Western elf Fleki calls the Eastern Continent a “primitive land” while complaining about the quality of life.
Based on this and additional evidence, we can reasonably conclude that the elven lands in the West are probably the most “modern”, followed by the lands in the Eastern hemisphere, with the Eastern Archipelago lagging the furthest behind.
Because of this difference between the races, it makes sense that we see a mix of different eras and styles of technology and clothing. For example, we see characters wearing Neolithic fur garments, Greco-Roman tunics, and Medieval garments as everyday clothes at the same time that other characters wear Renaissance and even 19th century-influenced garments.
Meanwhile, many things in the Dungeon Meshi world have also remained unusually stagnant for far longer than they did in the real world. Realistic oil painting seems to have remained unchanged for more than a thousand years, and Medieval-looking clothing that was worn a thousand years ago is still being worn in the “present” day, virtually unchanged.
There are also some things that are much more advanced than the Renaissance period, like steampunk elevators, and magical communication that works through birds/fairies/crystal balls/telephones and allows for instant contact across the globe… A huge advancement that should impact every element of life and society, thanks to the ability to easily exchange information.
In the real world, instant communication is the foundational element that makes things like precise time-keeping, time-zones, advanced banking, stock markets and news reporting possible… So one can assume that some of these things might possibly exist in some form in the Dungeon Meshi setting.
32 notes
·
View notes
Text
"The largest, quickest, and most devastating pandemic in all of human history was the influenza epidemic whose first of three waves began in Kansas in March 1918, and recurred in ever widening and more mortal forms in the autumn and the winter. Yet, this epidemic is distinguished from others by a second reason, the historical amnesia - a virtual blackout of memory - that has greeted it in subsequent generations. Its historian summarizes: "Nothing else - no infection, no war, no famine - has ever killed so many in as short a period. And yet it has never inspired awe."
Between 22 and 30 million people were killed in a year. Half a million of these were in the United States whose troop-ships carrying young men to the Western Front of Europe during World War I, in conditions that were floating test tubes of the virus, brought the 'flu to France, then Germany, England, and Russia, and from the European continent the virus was transmitted along the sea-lanes of European imperialism to Latin America, to West Africa, to India (where 12 million died), to China, Japan, and the Pacific islands. More were killed by the epidemic than were killed by the Civil War or World War I Which Robert Graves called "the Sausage Machine, because it was fed with men, churned out corpses, and remained firmly screwed in place."
The age specific mortality curve of the epidemic was shaped more like a 'W' than a 'U' which is to say that those in the strong middle years of life were as affected, and more so, than the very young or very old. This characteristic deeply worried the official macroparasitic institutions which relied on those in their middle years to produce, to reproduce, and to fight. To them, not so much life, as production and reproduction was the worry. Henry Cabot Lodge was concerned about the productivity of munitions plants. In March 1,000 workers at the Ford Motor Company fell sick. The number of rivets driven per day at the Philadelphia shipyards fell at a rate that alarmed the war producers. The equivalent of two combat divisions of the AEF, or the American Expeditionary Force ("Ass End First"), were incapacitated in France. 40% of U.S. Navy personnel were affected. 37 life insurance companies omitted or reduced their annual stock dividends. The macroparasites and the microparasite were thus in mortal competition for the bodies of the healthy ones in middle life, and that for another reason too. As an air-borne infection, "the rich died as readily as the poor."
(...)
500 were arrested in New York on "Spitless Sunday." Large gatherings were prohibited. Telephone booths were padlocked. Public water fountains were closed. In San Francisco face masks were required to be worn. Cash tellers were equipped with finger bowls. A municipal ordinance of Prescott, Arizona, adopted a suggestion from an obscure newspaper by the Fascist, Benito Mussolini, making it a crime to shake hands. The Army Surgeon General reported that "civilization could easily disappear from the earth."
The middle point of the 'W' grew and as a result the famous 'Lost Generation' of despairing American writers came into being, and yet with the exception of Katherine Anne Porter none wrote about the 'flu epidemic. Was this massive, social, denial? Was this male chauvinism? Was this a sequela of the disease's "profound systemic depression"? They are important, unanswered questions.
Katherine Anne Porter synthesized the times, the creation of the 'new man,' and the 'new woman.' As Prohibition loomed guys started sporting hip flasks, and the new woman took up the cigarette - alcohol and nicotine, traditional responses, since the 1790s, towards epidemics. The government-issue wristwatch became the emblem of the urban individual; it became essential to the urban-and-factory planning of the Twenties. The government drive for money (War Bonds) was the only occasion of permitted gathering, and that under the slogan "Give 'till it Hurts." Indeed, "Sacrifice" was the watchword for the soldier and the 'new' woman alike: give money, give your time, give your labor, give you life."
-Peter Linebaugh, "Lizard Talk: Or, Ten Plagues and Another - An Historical Reprise in Celebration of the Anniversary of Boston ACT UP" (1989)
61 notes
·
View notes
Note
Hey dog, just wondering if you thought out how the phone heads work/how callum made them? I'm working on a fully functional rotary phone head myself and think knowing more of how you think they works might help a ton!
you're gonna laugh. there's actually various sections in my crown lore doc that discusses exactly how his technology functioned in-universe, sometimes contrasted with ours, like in the case of his arm prosthetics (technology which is moving in an inverse direction now, with the development of sensors that read brain functions from *outside* of the head, rather than tapping into nerves).
virtually none of this info would be of much use to you though, as you've already got wireless do-dads to take care of the issues Crown had to get extra creative to tackle, pre-mobile phones existing.
EG: My solution for the first ever phone heads having portable phone access while being compatible with the standard landline system the country used (with switchboard exchanges) involved utilizing shortwave frequency bands that connected a radio feed coming to and from the phone head to a standard landline connection at a switchboard exchange, to put it kinda simply. Like putting a radio up to a phone receiver, with each phone head broadcasting and picking up a unique frequency band.
The solution Crown came up with was ironically using the strengths of radios to get past the limitations of telephones. A solution that he got from his radio + phone connecting him to the outside world (the importance of both devices was emphasized in his story ofc), essentially thinking to combine the technology in a cool, new way that would've even theoretically worked in OUR reality up to a certain number of phone heads in close proximity of each other!
But, none of this information is useful to you as we live in a world of sim cards and bluetooth! you've just gotta construct the casing and figure out how to map functions to the outside of the phone head. my my my
138 notes
·
View notes
Text
The United States used to be firmly opposed to any attempt to restrict the free flow of information technology because it benefited US companies that were dominating global markets. It’s been changing its tune in recent years not because its convictions have changed, but because the real guiding principles were always misunderstood. The global spread of the internet was framed by US lawmakers and tech capitalists as being synonymous with the spread of freedom and democracy — concepts the United States loves to wrap itself in — when it was really about geopolitics and economic power. Now that those goals are threatened, it’s happy to embrace bans to protect its interests, while pressuring its allies to back them and, by extension, accept the position of US tech firms within their economies.
Maybe you’re an American and you think the TikTok ban makes sense. Sure, US tech companies can track virtually everything you (and people in many countries outside the US) do, will hand that data over to the government, and even sell it to a ton of data brokers — but at least they’re US companies. Chinese ones shouldn’t be allowed to do the same thing, at least to US residents. That line of thinking makes no sense to me, but I can see how people only thinking of their own narrow national interests can believe it.
But why should a Canadian, a European, a Brazilian, a South Korean, or people from any number of other countries outside the United States defend that reality or find it in any way acceptable? When previous forms of media like radio, film, or television and communications technologies like the telephone rolled out, countries often placed rules on foreign ownership and content distribution, but with the internet little of that was allowed. Countries were expected to accept US dominance of the new medium, yet now we see what happens when those US firms start to face real competition at home: the US government does exactly what it long said no one else was allowed to do and protects its domestic industry.
5 notes
·
View notes
Text
Character bio of the Asian Pasifika demigod and Afro Latine Native alien hybrid superhero main character part 4
Wrist Mounted Arm Computer:
Attached to their left arm is a human and alien magical and technological mechanical portable wrist computer. It is a personal information processor that is powered by steam, gas, & or electricity. It has knobs, dials, buttons, & switches on the top, bottom, left, & right sides for accessibility. It comes with a red, blue, green, silver, or gold light. It comes with a keyboard. Can function as any number of useful tools. Wrist computer uses include data storage, inventory management, topographical mapping, assisted targeting, medical diagnostics, radio receiver, video player, music player, and portable gaming console, a communicator, a light, a scanner, a smart phone, a smart watch, a portable computer, etc.
It lets him/her/them stay in contact with their handlers and allies. It gives him/her/them mission-specific information. Including where weapon caches are. It keeps track of their credentials. Is also a handheld personal force shield generator. It has crime databases, wiretapping, evidence analysis, a lie detector, and monitors its wearer's heartbeat, blood pressure, & blood sugar to ensure that its use was authorized and to send help if the user is healthy or is in trouble. Can project 3d and 4d holograms. It provides internet access and cellular reception with clear reception and unlimited data anywhere on Earth.
Has clear reception and cellular reception in terraformed and colonized planets, moons, comets, asteroids, & planetoids star systems and galaxies of the multiverse. It uses nanotechnology to physically reconfigure itself to prevent hacking. It also has GPS functionality. Has a hacking tool. Has a compact first aid kit. Is a wearable computer. Has an interface is a holographic 3d wrist-mounted computer complete with a miniature 4d holographic projector.
The wrist communicator is based on an alien memory metal so when they take it off it can flex into a tablet shape. Can hack computers, machines, phones, tablets, robots, & artificial intelligences. It can dispense first-aid, repair and customize equipment, and send and receive phone calls. It can record audio sound and visual video footage for later playback. Using a simple but elegant form of sonar and satellite tracking this wrist mounted computer can map out areas where its user travels.
It acts as a database for the wearer’s personal information and inventory. It is capable of tracking the wearer’s status and organizes the user’s inventory of apparel, junk, weapons, misc, armor, mods, aid, items, & equipment. An overlay of the data is also available. In addition, the device features a built-in radio module. It has an advanced compass.
It has a virtual 3d and 4d map that displays discovered locations. It has a holographic map projector which shows a complete 3D or 4D scan of an area. It has a sonar and motion sensor system that highlights nearby allies, enemies, people, animals, beasts, creatures, and monsters. It is a communicator, a map, a flashlight, a compass, a scanner, a music player, a smart watch, & a portable computer.
It has lighting functionality. A holographic player, video tape, CD player, & DVD player is mounted beneath the display. It is capable of keeping tabs on the user’s health condition, ammo, weapons, armor, apparel, & food and water. It shows the user’s health bar as red, yellow, orange, & green. It has a blue, pink, and purple heath bar system to show laser, plasma, & hard light shields and force fields. It has a silver, gold, & obsidian health bar system to show combat armor, power armor, & mech suit armor condition.
The wrist computer gauntlet’s uses include but are not limited to data storage, inventory management, topographical mapping, assisted targeting, telephone, medical diagnostics, computer, radio receiver, telegram, hacking, music (CD) player, & Video (Video and DVD) Player . It can map out areas. It can take and store notes and memos. It has a built-in radio. It has a geiger counter and toxic gauge for radiation, toxins, & poisons. It has a built-in flash light used to illuminate dark areas.
It needs to be worn as a gauntlet which seals with a biometric lock. It utilizes a revamped 3d or 4d holographic display interface with animated images. It automatically updates using satellites. Additionally, it integrates with the onboard computers of power armor and mech suits allowing a user to access their wrist mounted computer from within the armor via a HUD visor display. The inventory menu is a system used for viewing and managing collected items. The menu also displays total currency and carry weight on the screen.
It is sorted into several tabs. Weapons, Apparel, Aid, Misc, Junk, Mods, Ammo, & Money. All guns, melee weapons, grenades, and mines fall in this tab. Specs of weapons can be viewed and compared as well as equipped and unequipped weapons. It shows their attachments such as silencers or suppressors, compensators or muzzles, grips, flashlights, scopes, red dot sight, red laser sight, or grenade launcher. Shows the damage effect it has on enemies. It shows the weapon’s stats such as range, damage, etc. It shows the weapons condition and shows if it is in need of maintenance and repair.
All armor and clothing appear in this tab. Specs of armor and clothing can be viewed and compared as well as equipped and unequipped apparel. All aid such as medicines, drugs, food, and drinks are sorted here and can be used and consumed in this tab. Miscellaneous items such as keys, cds, dvds, holographic tapes, notes, and items which fall under no other category are in this tab. Mod tab for weapon and armor modifications. Ammo lists all types of ammunition for guns, grenades, & mines currently in inventory. Currency shows all dollars and copper, bronze, brass, silver, gold, & platinum coins, cash, and credits.
A unique feature of the Mark 20 Wrist Computer is an adapter plug attached to the underside of the device. This plug is used to perform diagnostics on power armor and mech suits. It can hack into computers. It has a lockpick module to pick the locks of doors, safes, etc. In addition, the plug is also used to gain control of robots, androids, artificial intelligences, automatons, mech suits. When wearing a power armor or mech suit the user does not interact with the wrist computer directly. Instead all the information is displayed through the suit’s integrated HUD but with a different HUD color.
This implies that the Mark 20 is capable of interfacing with power armor or mech suits onboard systems to allow access to its functionality without having to directly operate the device. It is a wrist gauntlet, wrist bracer or wrist computer. It is a piece of wrist-worn technology. It houses several technologically advanced features. The wrist gauntlet is a small computer device worn on the wrist and features numerous controls for various items of human and alien magic and technology. It has a digitized display. The gauntlet is linked directly into a metahuman and superhuman humanoid’s combat armor, combat helmet, power armor, power armor helmet, & mecha suit and governs many of their functions.
The gauntlet also acts as a power source for these tools although it has only limited capacity and would become depleted with repeated use. However, despite the clearly advanced nature of the technology involved, the wrist gauntlet can be recharged from any common power source such as gas, steam, water, nuclear power, & electricity.
The mark 20 is the most customizable model made. It was the epitome of technology. Each instrument is individually crafted and personally attuned to its recipient. The device is so personalized to its user that it could continuously monitor and report the vital signs of its assigned wearer in real time. It was the quintessential personal data assistant complete with a magical AI modeled after a female humanoid alien and female human. Complete with its own mapping system, navigation system, radio receiver, computer, video and music player, cellphone, & personal inventory tracking software. It’s a souped-up PDA complete with DNA biometric lock.
#indigenous#indigenous artist#indigenous writer#indigenous art#indigenous creator#indigenous rep#indigenous character#native rep#native art#native artist#native writer#native character#native tag#native creator#native representation#queer creator#queer writer#queer representation#queer artist#queer character#trans creator#trans artist#trans writer#trans representation#trans character#disabled art#disabled artist#disabled character#disabled representation#disabled creator
3 notes
·
View notes
Text
When Zhou Fengsuo was looking for a space in New York to display his art collection, he couldn’t believe his luck when he stumbled across 894 6th Avenue in the heart of midtown Manhattan. The numbers of the address – 8946 – were the same as the date he wanted to commemorate: 4 June 1989. It was “unbelievable”, the former student leader marvelled.
That Zhou’s collection, which opened to the public on Friday as part of the June 4th Memorial Museum, ended up in such an uncanny location is the result of a concerted, decades-long campaign by the Chinese Communist party (CCP) to eradicate any remembrance of the 1989 massacre around Tiananmen Square anywhere in the world.
Having virtually eliminated 4 June gatherings in mainland China and Hong Kong, the CCP’s efforts to suppress the memories of that event have increasingly been felt overseas.
In the early hours of 4 June 1989, troops from the People’s Liberation Army rolled into Tiananmen Square, in the heart of Beijing, to disperse thousands of peaceful protesters who had gathered for weeks to demand political reforms. Hundreds of civilians were killed. The Chinese government has never fully acknowledged the massacre.
The opening of the June 4th Memorial Museum in New York was prompted by the closure of one in Hong Kong in 2021 after the imposition of the national security law effectively criminalised 4 June commemorations. But now people who try to light a candle much further from Beijing also encounter difficulties. When plans for the New York museum were announced last year, local Chinese community groups objected to them, accusing the organisers of being divisive.
The first venue the museum’s organisers approached turned them down without giving a specific reason. “We have to be very careful at negotiating [with venues] and be very explicit about our purpose,” Zhou said. That means “making sure that the other party is fully aware of the commitment needed”.
The museum plans to operate a visitor booking system. “We cannot open the door for anyone who wants to come in because we’re really worried they [the Chinese embassy] will send somebody,” said Wang Dan, another former student leader.
Shao Jiang, an exiled 1989 protester, has been helping to organise 4 June vigils in London since 2007. When the Observer tried to reach him by telephone in the days before this month’s event – a protest outside the Chinese embassy – the call was blocked.
Shao said this often happened in the run-up to 4 June. “If I order deliveries, they can’t contact me,” he said. “It’s quite normal, living in exile. Every year I face different difficulties.”
Activists have had to balance the desire to raise awareness of a fading memory with keeping out spies. In the past two years, Hongkongers have swelled the numbers at the London vigil. But attendees are often cautious, reluctant to remove their face masks or trust other people there.
“There are people who take photos at events that are critical of the CCP, including 4 June vigils,” said Yaqiu Wang, a senior China researcher at Human Rights Watch. “It’s never clear who those people are, but likely they are associated with the CCP, and taking photos is a way of intimidating participants. That is also a big reason why overseas students refrain from going to those events.”
In many places, vigils are shrinking. Peng Xiaoming, a Berlin organiser, said: “The number of attendees is reducing because of the Chinese government’s powerful propaganda.”
This includes threats to students that they or their families will face repercussions in China. “Most of the people who attend are old friends and classmates from the past,” Peng said.
Taiwan is alone in the Sinosphere in still holding a significant 4 June event. Hundreds gather to light candles at the Chiang Kai-shek memorial.
In recent years, new Hongkongers arriving in Taiwan have boosted the size of the vigil, and drawn attention to the links between the CCP’s behaviour in 1989 and in Hong Kong in 2019 and 2020.
Beijing sees Taiwan as being part of its territory – and any mention of 4 June is therefore highly undesirable to the CCP. “Every year, there is something to limit our activities,” said Wonka, one of the vigil’s organisers, who uses a pseudonym to protect her identity.
The challenges include vandalism of the event’s signage and, increasingly, fear from potential collaborators. This year, Wonka invited a troupe of 20 musicians to perform at the vigil but several refused because of fear of retaliation from the CCP. In the end, only four or five of the musicians agreed to perform.
“It’s very normal,” said Wonka. “They are afraid of the China issue.”
The Chinese embassies in the UK and Germany did not respond to a request for comment.
Liu Pengyu, a spokesperson for the Chinese embassy in Washington, said: “The Chinese government has already drawn a clear conclusion on the political disturbance in the late 1980s. The great achievements we made in the past 70 years since the establishment of the People’s Republic of China speak volumes about the right development path we have chosen with the endorsement by our people.
“The Chinese people will continue to advance along the path of socialism with Chinese characteristics.”
Additional reporting by Emma Graham-Harrison
The Observer, via The Guardian, June 3, 2023
#the observer#The Guardian#tiananmen square massacre#tiananmen vigil#Zhou Fengsuo#New York#USA#June 4th Memorial Museum#Tiananmen Square#Tiananmen Square massacre#history#conservation#politics#Shao Jiang#Wang Dan#Hong Kong#hong kong national security law#Human Rights Watch#activism#Taiwan#China#六四事件#天安門#八九六四#八九民運#天安門事件#1989 Tiananmen Square protests#8964
7 notes
·
View notes
Text
Cancer Care: Impact of Telemedicine on Positive Health Outcome

We have all been through tough times, especially during the pandemic, and we have all realized the importance of telehealth services. By sitting in our homes, we could get all the services we want, be it for COVID-19 or cancer. Having telehealth and telemedicine services was a blessing in disguise during those tough years.
The National Cancer Institute researched the number of telehealth visits during the pandemic. The finding was based on the analysis of 25,500 telehealth visits. Out of this, more than 11,600 were diagnosed with cancer. They were getting telehealth services and were virtually consulting the clinicians. This shows that there has been an increase in the number of people who have started trusting telemedicine services.
In this article, we will be discussing the positive health outcomes of telemedicine services. However, there are some important things to consider as well. For instance, there are things you need to discuss before receiving telemedicine services. This includes scheduling an appointment and explaining the necessary in-person hospital visits, medication follow-ups, and post-treatment care.
Discussing all these can help individuals get relief from long waiting hours just to schedule their appointments or visit a doctor. During the virtual consultations, the individual also needs to understand and discuss the care plans. Both the doctors and the individuals should be informed about the diagnosis date, tumor stage, schedules, treatment facilities, nutrition, pain management, and health concerns.

Thanks to telemedicine services, no one today has to wait for longer hours and get help anytime they want. You can get professional help with a single tap all at once. Therefore, all you need to do is book your schedule.
If you are diagnosed with a terminal illness, telehealth appointments can save you time and money. In the following, we are going to look at some points to discuss how telemedicine services can help individuals diagnosed with cancer. These points will provide insight into how the healthcare industry has revolutionized faster.
Unlocking the Benefits of Telemedicine Services for Cancer Care
Living with a loved one diagnosed with cancer can turn life upside down. Treatment costs can vary depending on the type of care needed. Be it medications or a cancer care management plan, you just need the right kind of treatment that may cost money. Forget about the expenses related to travel and other medications.
That’s why telehealth services are introduced to help out loved ones with cancer care. In the following, let’s take a look at the numerous benefits of telemedicine services for people diagnosed with cancer.

Meeting Specialized Oncologist
Comprehensive care is needed in the healthcare industry. With an introduction to the telephonic healthcare industry, you get to meet the right specialized doctor for your treatment virtually. There is no need to travel long distances just to meet the doctor. Tap on the screen, get connected to a specialized oncologist virtually, and get help with medical appointments. Due to long waiting hours, there are times when individuals have to wait to get in touch with special care. Telehealth appointments with specialized healthcare professionals get easier.
Reduce Travel Time
There are times when individuals diagnosed with terminal illnesses have difficulty traveling to healthcare providers. They need enough rest and travel restrictions because of the drastic impact on their health. They may get car sickness or have chronic pain due to illnesses. However, with telehealth urgent care, time travel is reduced to some extent. The individual can get help anytime because specialized care is available and they don’t have to travel long hours. The specialized oncologists are here to help the individuals right away with treatment and care.
Regular Health Monitoring
Chronic illnesses can cause several health issues that have long-term effects. That’s why one needs regular health monitoring. However, going to medical institutions can be time-consuming and have a drastic effect on your health. The doctors keep tabs on the vital signs and the symptoms evolving because of the illnesses. That’s why telemedicine appointments can help you a great deal to check on the health of a loved one.
Getting Timely Consultations
Gone are the days when one had to wait for long hours to get a doctor’s appointment. You can simply book your medical schedule right on the phone. The virtual appointments get easier, and one can keep tabs on their health. Getting timely consultations can help you reduce the signs and symptoms of the illness and get the test results online. You don’t need to visit the healthcare center to get the results or speak to the doctor.
Improved Medications with Time
The condition of the illnesses may change over time, so you need to continuously stay updated about your medical updates and health concerns. Having improved medications and knowing about medication management can help an individual take better care of himself or herself. How so? The individual will learn about the adverse impact of medications on health, whether on the phone or online.
In Conclusion,

Telemedicine services have completely transformed the healthcare sector by reducing travel time and improving medications simply by keeping tabs on medical health help needed at times. With timely telehealth appointments, one gets timely consultations about medical health and keeps track of health monitoring.
Thanks to telemedicine services, educating individuals has never been so easy. Today, millions of people have been taking advantage of telemedicine in the long run. Indubitable telemedicine services, in the coming times, will gain extra support from the government and the people as well.
When it comes to cancer care, telehealth counseling can help you save a lot of time and money because you don’t need to wait for prolonged hours. This helps your body get enough rest and provides mental health support in times of utmost need.
2 notes
·
View notes
Note
do you like vaporwave? if so, some of your favs? if not, why not?
Technically yes, but I try to not really engage with vaporwave as a genre or aesthetic because I feel like viewing it that way can negatively impact the way I view an actual work.
Like I dont want to listen to something and think "this is good for vaporwave" or something, yknow, I wanna take stuff on its own merits. That being said I do enjoy what would be considered the "vaporwave sound" and if you watch my streams im very obviously vaporwave/webcore/y2k/etc. adjacent in visual style (tho i think the "outrun" branch kinda sucks and needs to go away.)
The first thing I heard that introduced me to that type of sound was "Flowers" by bEEdEEgEE ft. Lovefoxxx and is still something I come back to. (Photosensitivity warning btw)
youtube
"Vaporwave" wasnt well known as a term yet, so I just knew this particular song hit different at the time.
Then obviously Floral Shoppe hit, which I still think is good even if it has a lot of baggage associated with it nowdays (effectively created the "genre" and "aesthetic" elements that got overused/misunderstood/etc.)
At that point I would probably have said I was a fan, even though I really didn't engage with the scene that much. As such, idk who all turned out to be dirtbags so I'm not gonna vouch for any of them as people except Vektroid who, ironically, I met as a fellow vtuber rather than through her music, still kinda baffled we're mutuals tbh lol.
I think I mostly just listened to
Far Side Virtual,
A Heart Full of Love,
The occasional PrismCorp,
I've enjoyed what I've heard of Windows96
Also enjoyed the rare "can we make this a thing?" stuff like this Especia track,
and honestly just a bunch of shit that appeared on my youtube that is long forgotten.
Over time I started to listen to more Future Funk than Vaporwave because of the Artzie Music youtube channel.
Some songs I would actually go back to are:
youtube
youtube
youtube
youtube
youtube
youtube
youtube
youtube
After listening to some of the stuff in my youtube likes from however many years ago, there absolutely was a lot of "this is good for what it is" type of stuff that I don't think I would listen to again, so I'm just sharing the stuff that I think holds up.
---
Honorable "Maybe not really Vaporwave but occupies the same brain space" Mentions:
The work of Isaac Delusion,
The work of Princess Chelsea, in particular No Church On Sunday & Is It All Okay,
The work of Yeule, in particular Pretty Bones & Pixel Affection
The work of Gang Gang Dance (a member of which is bEEdEEgEE)
And of course the "City Pop was a thing???" era of vaporwave/futurefunk that gave us stuff like Plastic Love (I dont even need to link it, you know.) Fantasy, I Love You So, Telephone Number, Glass No Sogen, etc.
---
Even with all its baggage and for-better-or-worse genre trappings, I think the Vaporwave Era was really inspiring, having hundreds of people who all were taken up in the frenzy and just made shit.
Looking back at some of this stuff really makes me wish I had the knowledge and drive to get back* into music. Maybe someday.
#ask#vaporwave#future funk#music recs#music reccomendations#info dump#link heavy#*I played violin when i was like 7 lol#Photosensitivity warning#flashing lights warning
2 notes
·
View notes
Text
dnd scam camping structure (content, that’s a joke for con-tent)
i dont have much more sonic dnd nonsense to share but i figure i might as well upload some of the other stuff i’ve been doing for my dnd campaigns.
i use a pngtuber program in our group calls to have a virtual avatar for my characters. i started doing this back in i think october of 2021 with my aberrant mind sorcerer lepori: Kokoyo Tipaya.

she has basically three emotional states: normal, seen above. serious, for when on a mission. and her mask over her face, for doing psychic mind dives on people. each state also comes with a “mentally communicating” state with extra purple/blue star effects all over because she has telepathy. for those who don’t know Veadotube (the program I use), you can basically assign an image for when you aren’t talking, and one for when you are. so when im not talking kokoyo (or my druid xoqotea) has their mouth closed, when i talk it swaps to the image of the mouth open. i also made blink variants because there is an option for blinking with mouth closed and blinking with mouth open. xoqotea also has about three or four states: normal, sarcastic/unimpressed, worried, and battle. using my streaming software i can use my scene as a virtual webcam in discord, so whenever i talk my character pops active. its very neat.
my upcoming characters have far more going on. i went all in on them. they will both have 9 states for each number on the keypad. the wizard is already fully completed and i’ll probably put together a bunch of gifs for her later, and the SCP-Campaign cleric only has two states done. i also looked up a tutorial for making a gif in clip studio JUST FOR THIS so be GRATEFUL. i could have used a gif maker online but i didnt want a nasty watermark.
now enjoy a collection of various images from our campaign. for reference: our campaign has my bunny, a bard named Svetlina, a fighter/barbarian named Armor King who looks like Armor King and has a dire jaguar or a dire cat i forget (later replaced with a ghoul druid named Tacitus), and a warlock cowboy tiefling named Andromalius.

one of the first drawings when i decided to give her proficiency in a switch bass (a bass guitar that collapses in size for convenience).
i got a bard to sing a Hildegard Von Blingin song

we had to sneak through a cave of giant monkeys and creepy critters. the clapping cheeks wasn’t canon though. nor was casting Sending to her fiance. although she did have me do that often because i am the group’s psychic telephone.



the player of the bard says some weird shit some times that makes us all WeirdChamp like wanting to spit on an unconscious villain and use prestidigitation to make him smell like piss for six seconds.

i’ve got a bunch more of these to share but i’ll spread the rest out over different posts. who knows. they could go VIRAL like V/H/S VIRAL, but in a good way not like that movie which was imo the worst in the series.
#dnd#d&d#dungeons and dragons#dungeons & dragons#dnd character#d&d character#virtual avatar#pngtuber#repurposing pngtuber tech for dnd webcam#aberrant mind sorcerer#lepori#bard#dnd moments
6 notes
·
View notes
Text
How Does a Cloud-Based Business Telephone System Work? Solving Communication Challenges for Modern Businesses

Introduction
In today's fast-paced business world, seamless communication is the lifeblood of any successful organization. Traditional phone systems have their limitations, making it crucial for businesses to adopt modern solutions that can keep up with the demands of the digital era. Enter Ezeetel Telecommunication, a leading provider of cloud-based Business Telephone Systems. In this blog post, we will explore how Ezeetel's cutting-edge technology works, and how it addresses the communication challenges faced by businesses today.
Understanding the Basics of a Cloud-Based Business Telephone System
A cloud-based Business Telephone System, also known as Voice over Internet Protocol (VoIP), revolutionizes the way organizations communicate. Unlike conventional landline systems, where communication is routed through physical phone lines, VoIP operates over the internet, transmitting voice data as packets. Ezeetel leverages the power of cloud computing to deliver a robust, reliable, and scalable telecommunication solution to businesses of all sizes.
The Inner Workings of Ezeetel's Business Telephone System
Virtualization of Phone Infrastructure: Ezeetel replaces the need for bulky, on-premises hardware with a virtual phone infrastructure hosted in the cloud. This means businesses no longer need to invest in expensive telephone exchange equipment, reducing both upfront costs and maintenance expenses.
Seamless Call Routing and Management: With Ezeetel's cloud-based system, incoming calls are efficiently routed to the intended recipients, regardless of their location. Advanced call management features, such as call forwarding, auto-attendants, and interactive voice response (IVR) systems, ensure that every call is handled professionally.
Scalability and Flexibility: As businesses grow, so do their communication needs. Ezeetel's solution is highly scalable, allowing companies to add or remove phone lines effortlessly. This flexibility ensures that the system can adapt to organizational changes without major disruptions.
Unified Communication: Ezeetel integrates various communication channels, including voice, video, and messaging, into a single platform. This unified communication approach streamlines internal collaboration and enhances external interactions with clients and partners.
Mobility and Remote Work Support: In an increasingly remote and mobile work environment, Ezeetel's Business Telephone System shines. Employees can use their smartphones, laptops, or desktop computers to access the system from anywhere with an internet connection, ensuring uninterrupted connectivity.
Solving Communication Challenges for Businesses
Ezeetel's Business Telephone System addresses several critical challenges faced by modern businesses:
Cost-Effectiveness: By eliminating the need for costly on-premises equipment and offering competitive pricing, Ezeetel significantly reduces the overall telecommunication expenses for businesses.
Reliability and Redundancy: The cloud-based infrastructure ensures high system availability, with built-in redundancy to minimize downtime. Businesses can rest assured that their communication channels remain operational at all times.
Enhanced Collaboration: With integrated voice, video, and messaging features, Ezeetel fosters seamless communication and collaboration among team members, boosting productivity and efficiency.
Business Continuity: In case of natural disasters or emergencies, Ezeetel's cloud-based system ensures that communication remains intact, allowing businesses to continue operations without disruption.
Global Reach: Ezeetel's VoIP system enables businesses to establish virtual phone numbers in multiple countries, expanding their reach and providing a localized experience for customers worldwide.
Conclusion
In conclusion, Ezeetel's cloud-based Business Telephone System represents the next generation of telecommunication solutions, empowering businesses with unparalleled communication capabilities. By virtualizing phone infrastructure, enhancing collaboration, and addressing the challenges of modern communication, Ezeetel enables organizations to thrive in today's dynamic business landscape. Embrace the power of cloud-based telephony and take your business communication to new heights with Ezeetel Telecommunication.
#cloud-based Business Telephone System#Business Telephone System#canada#cloud PBX for small business canada
2 notes
·
View notes
Text
Detective Beaumont
Suzie walked up the street, strayed into a dark alley, and returned to the street as The Killer. The Killer went home.
Detective Beaumont arrived at the scene. "Has there been a murder?"
"Yes, sir."
"Do we know who did it?"
"No, sir."
"Not again!" Beaumont shook his head. "How is it that we are never there when the murder occurs so we can see it occurring?" Beaumont left, not expecting an answer.
He traveled uptown. When he reached the top, he entered a restaurant and sat across from a telephone. He picked it up. "You won't believe what's happened."
"Yes. Your gazpacho is getting cold, Beaumont."
"Please call me Jack."
"We're past that. I've sold all your things. Or had you not noticed?" Beaumont had not. "I’ve moved to Switzerland. Goodbye." His partner hung up. Beaumont shook his head.
He returned to his no longer shared apartment. No coffee machine, no printer, no small table on which to set a printer. Someone had even painted the once off-white walls pure white. He reached to pull out his phone but pulled out a receipt for the sale of his phone. Oh, Beaumont thought.
The Killer entered the police station and nodded at the maitre d'. "I've committed a crime and would like to make amends."
"Please take a number and be seated."
The Killer removed a paper ticket from the machine. The use of a virtual queue was welcome. In a place like this you wouldn't want to make it easy to cut in line. That may illicit a negative response from the individuals in the room, ruffians. There was The Burglar (a knock-off Hermès handbag), The Swindler (posing as a lawyer), The Planned Obsolescencer (got off), The Teacher (taught bad stuff), and Frank (picking up The Forger). They all had names like Frank once. Maybe something more like Franc for The Forger, or Francine, not Franz. The Killer held on to the paper ticket tightly.
"You come here often?" The Burglar asked.
"Not as often as I should." The Killer responded.
"I used to be like-"
Beaumont entered the station in a huff. "A glass of red if you please," he called to the maitre d'. "Who's processing these self-alleged criminals?"
"The Intern."
Beaumont looked over the assemblage. "Are any of you perhaps responsible for the death of a person in an alley?"
The Killer stood up.
"Thank you," Beaumont said. "Meet me in examining room 2. In your own time." He motioned to remove his felt hat and retrieve his felt pen, but neither were on his head.
The Killer entered examining room 2 and exited A Killer. A Killer was summarily rehabilitated and became Suzie. Beaumont received a commendation. "For your steadfast pursuit of Suzie" it said.
Who's Suzie? he wondered. Beaumont shook his head.
3 notes
·
View notes
Text
The Rise and Fall of Matrix 1.0 in Shadowrun
If you know what this is, then we are friends. Hoi chummer.
If you don’t then I’ll first start with what it’s not:
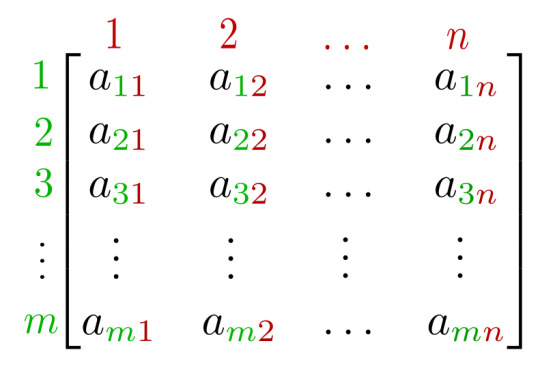
Matrix (mathematics)

John Matrix from Commando
Extracellular matrix
Like most cyberpunk elements within Shadowrun, the use of “matrix” as a virtual-reality driven computer environment derives from William Gibson’s Neuromancer, published in 1984. So yes, Shadowrun rips this off, though not to the infamy that…

…this franchise did.
The Matrix came out in 1999. It was revolutionary in its special effects, realizing Keanu Reeves had a greater range than being Ted, and getting a generation of sci-fi fans to read Baudrillard.

Baudrillard did not write this book.
I’m sure there’s been much written about the central tenet of the movie – that we are living in a simulation – so much so that I’m not bothering to do any research on that topic and get back to the main topic.
Matrix Topology
In college, a group of us Shadowrun nerds tried to recruit a computer-savvy friend to make a character and join our campaign. Naturally, we suggested a decker, and soon had him trying to infiltrate his first system, looking for some mcguffin.txt file that our team was hired to find.
Him: “Well, can’t I just grep it or something?”
Us: “Uhh… that’s not how computers work.”
Him: *already out the door*
The thing to remember about all implementation of computing and hacking in games is that:
It is absolutely nothing like how it works in real life, yet…
…some people will believe it to be chip-truth anyway.
Which is true for every aspect of RPGs – especially combat systems. Sometimes this is amusing – like watching D&D players trying to swing a real sword, and sometimes this leads to the United States Secret Service raiding the offices of Steve Jackson Games over GURPS Cyberpunk.

How can you consider this a threat to the Nation when The World of Synnibarr exists?
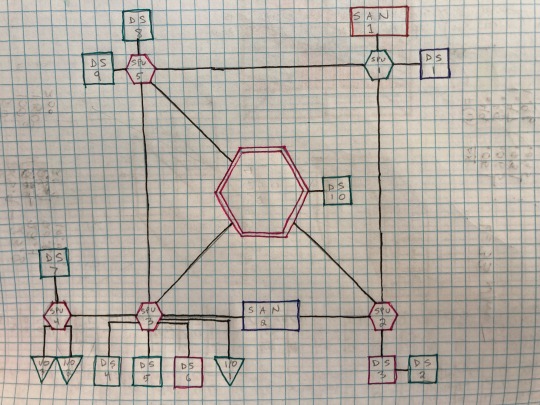
The Matrix – in Neuromancer, in the film franchise, in Shadowrun – is built upon telephone networks. In order to connect to a Bulletin Board System (BBS), your computer’s modem (a telephone that speaks computer) had to dial an old-fashioned phone number. Which meant that you had to know what that number is beforehand – there was no equivalent to Google. This is why in the movie WarGames (1983), Ferris Bueller is wardialing – calling every number in an area code to search for the few that connect to computer systems. So much of the presentation in Shadowrun is based upon knowing the address to where you want to go:
Regional Telecommunications Grid (RTG) – this is analogous to country codes. These are letter codes abbreviating the area. The RTG that covers Seattle is NA/UCAS-SEA (North America, United Canadian & American States, Seattle).
Local Telecommunications Grid (LTG) – this is analogous to a local area code. Every system will have its own LTG, encoded by a number. The examples given all have four digits but presuming there to be more than 10,000 computer systems in Seattle, they could have any value necessary. From the book:
Players should not know what is in the gamemaster's phone book because system owners guard their LTG locations jealously. Player characters will have to hunt down an access code or acquire it during an adventure to know where an LTG system connects. Let them keep their own phone books.
Supposing your decker already has the number, they can try to access the system itself. If connecting from outside (the RTG), then the decker starts off trying to infiltrate the SAN: System Access Node.
Computer systems are constructed out of a network of connected nodes, each of which having a particular purpose, represented by a standard shape, and each actually corresponding to a real part of a computer:
Central Processing Unit (CPU)
Sub-Processing Unit (SPU)
Datastore
Input/Output (I/O) Port
Slave Module
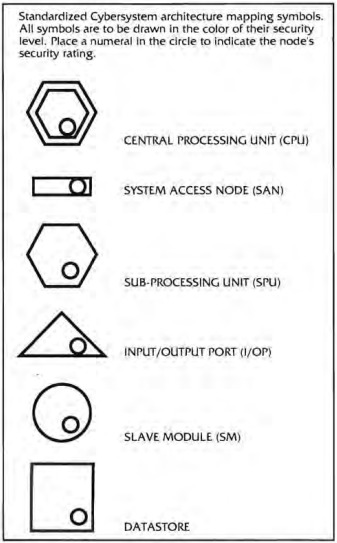
Because the decker (more specifically, the persona program running on their cyberdeck) is intrusive, there are dice rolls involved in gaining illicit access to every node, dice rolls involved in getting the node to execute your commands, dice rolls to deal with the Intrusion Countermeasures (IC, “ice”), and so on.
The Behind the Scenes chapter of the core book gives rules for randomly generating Matrix systems, populating them with ice, and determining the value of any paydata found in datastores.
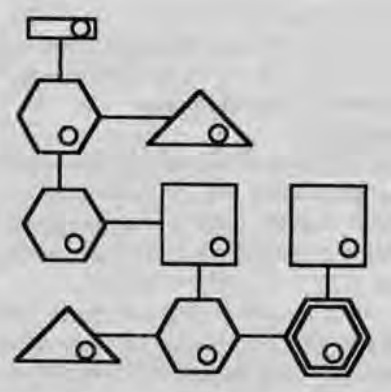
Which is when you realize that Matrix 1.0 is just a reskinned one-PC dungeon crawl.
A dungeon with locked/stuck doors, monsters to protect them, and treasure to be found in them. It became cliché at our table that when it was time for the decker to do their thing, the rest of the party went to get snacks and shoot some hoops outside. Yes, it was thrilling for the decker, but at the end, they either got they needed from the system, or they didn’t. Unless you were running a campaign of all deckers (which would be AWESOME), you’re better off just having an NPC decker as a contact and contract out that work.
So, it was not surprising that, by the time the 2nd Edition version of Virtual Realities was released, it contained a completely different set of mechanics, dubbed Matrix 2.0, which became the standard when 3rd Edition was published, that greatly streamlined and sped up the gameplay.
16 notes
·
View notes
Text
The FSB has identified 12 people suspected of coordinating and carrying out the October 8 explosion on the Crimean Bridge. It named the Main Directorate of Intelligence of the Ministry of Defense of Ukraine, its director Kyrylo Budanov, and its “employees and agents” as organizers of the explosion. The agency also released its official account of the explosion, including a description of how an explosive device reached the Crimean Bridge on a truck. The Ukrainian intelligence agency declined to comment, calling the FSB’s activities “nonsense.”
The FSB announced that it has identified “the organizers and participants in the terrorist act on the Crimean Bridge.” Eight suspects in the case have been arrested. The FSB and Russia’s Investigative Committee identified the organizers of the October 8 explosion as the Main Directorate of Intelligence (GUR) of the Ministry of Defense of Ukraine, its director Kyrylo Budanov, and “its employees and agents.”
The agency identified a total of 12 people suspected of participating in the explosion. The FSB report made only seven suspects’ names known: Ukrainian citizens Mikhail Tsyurkalo, Denis Kovach, Roman Solomko, Vladimir Zloba; Georgian citizens Sandro Inosaridze and “a broker by the name of Levan;” as well as Armenian citizen Artur Terchanian. The participation of five Russian citizens, whose names were not disclosed, was also reported. They were arrested, along with three citizens of Ukraine and Armenia.
According to investigators, the bomb was brought from Odesa through Bulgaria, Georgia, and Armenia, disguised under construction film. According to the FSB, the explosive device was “camouflaged” in 22 pallets of film rolls, weighing 22.8 tons.
In the beginning of August, the FSB reports, the bomb left the Port of Odesa for the Bulgarian city of Ruse. From Bulgaria the cargo was transported to the Georgian port of Poti, and from there to Armenia. It was at customs at the Yerevan Trans Alliance facility from September 29 to October 3, and then crossed the Russia-Georgia border at the Verkhny Lars crossing. After two days, the explosive device was delivered to a wholesale depot in Armavir, in the Krasnodar region, where on September 7 the pallets were loaded onto Makhir Yusubov’s truck, which then left for Simferopol. At around 6:00am Moscow time on October 8, the truck was blown up while crossing the Crimean Bridge.
On October 9, Alexander Bastrykin, head of Russia’s Investigative Committee, spoke about a similar route during a meeting with President Vladimir Putin.
The FSB claims that documents relating to the transport of the explosive device were changed twice during preparations for the explosion. Photographs of these documents have appeared in Russian media. A non-existent firm in Crimea is indicated in the documents as the final recipient of the cargo. According to the agency, a GUR employee who called himself “Ivan Ivanovich” controlled the explosive device’s movements and maintained contact with participants in the transportation scheme. He allegedly used both an anonymous virtual telephone number and a number registered to Kremenchuk resident Sergey Andreychenko.
Russian media, including RIA Novosti, have published an FSB video showing an inspection of the truck and a picture of an x-ray of its contents. However, the Telegram channel Mash had already published a longer version of the inspection on the day of the explosion, and there are inconsistencies between their video and the x-ray picture.
As OSINT analyst Oliver Alexander notes, the video footage shows one truck, while the x-ray image shows another. He called attention, among other things, to a different number of wheels on each truck: the first has five on each side under the trailer, the second has four. The analyst says the video footage shows an International ProStar truck. Baza reported earlier that Yusubov had this type of vehicle.
Presumably, the truck in the x-ray is not the one which exploded, but a DAF truck with Georgian license plates on which, according to the FSB, the explosive device crossed the border between Georgia and Russia. Photos of this truck were published earlier on Telegram. Georgia has said it had no involvement in the incident.
The GUR of the Ukrainian defense ministry refused to comment on the FSB’s announcement, calling the agency’s activities “nonsense.” “All the activities of the FSB and the Investigative Committee are nonsense. They are fake structures, serving the Putin regime, therefore we will not comment on their routine announcements. It’s surprising that they haven’t yet found any business cards in the vicinity of the Crimean Bridge,” GUR spokesman Andriy Yusov told Ukrainian publication Suspilne.
7 notes
·
View notes
Text
The future of cloud PBX providers!
The major roles that contribute to the success and triumph of business communications are "VOIP service providers or Cloud PBX providers." Almost all types of businesses, from small to large, are replacing their old phone systems with modernized ones. Recent surveys and research studies are proving that future communications are ruled by internet telephony services and their providers.
What is CLOUD PBX?
A company phone system that is housed on servers in distant data centers and is operated online is referred to as a "cloud PBX." This indicates that VoIP technology is used by these phone systems to place and receive calls. It is often known as a virtual PBX or hosted PBX, which is an exchange system that is created, built, and hosted in the cloud which is controlled by a third-party service provider and which is accessed over the Internet.
Not from the beginning, but from the past few years, many businesses including some of the large scale ones are switching to cloud PBX. It was previously considered as a con of this hosted PBX regarding data security. But gradually with enhancements done, this is essential to understand that security of cloud PBX will be transferred to the companies that are experts in the field.

Cost Savings of Cloud/Hosted PBX:
Investment is of top priority for any business organization. It has to be calculated twice along with the assessment of the resources as well as the requirements before investing. And, that is a move of wit. Once data security has been promised by the PBX service providers, users started to use it due to the cost saving primarily with respect to the space to be allotted and hardware.
However, hosted PBX saves maintenance cost and the cost of a dedicated tech team to maintain it. The above mentioned factors would save a lump sum in the long run. Besides, integration with other new installations and accessibility increases.
Reasons why these services are referred to as future technology:
Get the services within your budget:
The budget that must be allocated for the purchase of the software or hardware equipment is the first worrying factor that any firm takes into account but this technology is undoubtedly very affordable. Depending upon the company’s requirements get the communication infrastructure and subscriptions.
Flexible
Yes, very flexible and comfortable as one can keep working on the device that is connected to the internet and your service provider even when the individual or team is out of the desk. Cloud PBX solutions erase the geographical limitations to your team if some of them are interested in working remotely.
Features
VoIP dominates every other telecommunication system with absolute free calling and advanced features. For example, when it comes to internal communication of a business team, audio and video calls conferences could be conducted with premium call quality. An important asset that has to be addressed is that Cloud calling provides 99.99% uptime leading to an uninterrupted network.
The most important factor that encouraged firms to replace the legacy systems is the features incorporated with the VOIP phones few among them are:
Ring teams
Unlimited phone calls
Call waiting
Voicemail to email
Online meetings
Using text messages
Automatic attendant
Branch office support
Call forwarding
Pause the music
Billing
DND
Allows customization:
As already discussed, one more good reason for shifting towards the internet telephone is it allows the companies to do their customizations depending upon the firms’ requirements. It is pretty scalable if you want new lines. You can get any number of lines without spending on additional hardware or installation charges. All you need to do is to pay for more bandwidth and the service provider will guide you with the process.
Integrations and multiple storages:
Of course! VoIP can be integrated with any new software easily with no complications. This feature would help you in saving money and time.
You can easily combine cloud data with information already present in company systems, such as CRM integration. You can also integrate with sales applications and the service provider handles data redundancy by keeping identical data on servers located in various locations. Thus, it confirms that this technology is easy to set up and operate.
All processes are automated:
VoIP eliminates the need for manual help by automatically creating reports, billing, and other services reducing the manual effort in the firms.
Customer service:
The VoIP services effectively implement round-the-clock customer support services, increasing business efficiency hence proving that this modernized technology attracts more clients and helps small businesses particularly.
Conclusion:
Installing a cloud PBX system from a reputable service provider is the major step that needs to be taken by businesses, one such firm providing an adaptive environment through their products and services is VITEL GLOBAL COMMUNICATIONS, so don’t delay in searching for the best provider as we are one of the leading Cloud PBX providers focusing and developing your business communications. For more information, visit www.vitelglobal.in
9 notes
·
View notes