#virtualization of memory in cloud computing
Explore tagged Tumblr posts
Text
What is Memory Virtualization in Cloud Computing?
Explore the power of Memory Virtualization in Cloud Computing & Learn how it enhances cloud performance, scalability, and resource utilization.
#memory virtualization in cloud computing#what is memory virtualization in cloud computing#virtualization of memory in cloud computing#virtual memory in cloud computing
0 notes
Text

TECHNOLOGY ID PACK

NAMES︰ admin. ajax. alexa. am. atari. audio. auto. bailey. binary. blank. blu. blue. bluesse. browser. browsette. bug. byte. cache. calware. chip. circe. click. clicker. clickie. clicky. cloud. coda. code. codette. codie. cody. computette. crypt. cursor. cy. cyber. cybernet. cybernetica. cyberweb. cypher. cypherre. data. dell. digi. digitalia. digitelle. digitesse. disc. dot. electronica. electronique. emoticon. emoticonnie. fax. file. gig. gizmo. glitch. glitche. glitchesse. glitchette. graphique. hacker. hal. halware. hijack. index. informationne. intelligette. internette. interweb. java. javascript. juno. key. link. linuxe. lotus. lovebytes. mac. mal. malakai. malware. malwaria. memorette. memorie. meta. mic. micah. mickey. morphe. mouse. mousette. myspace. nano. neo. net. netette. nett. netty. paige. pascal. payton. peyton. pixel. programatha. programette. programme. pulse. reboot. rom. router. ruby. sam. sammy. screene. screenette. sean. shock. solitaire. spy. static. stutter. talia. tap. tecca. tech. techette. tessa. tetris. trojan. troubleshoot. ts. user. vir. virus. virusse. volt. vyrus. webbe. wheatley. whirr. widget. will. wirehead. wiresse. zap. zett. zetta. zip.

PRONOUNS︰ ai/ai. alt/alt. anti/antivirus. arc/archive. audio/audio. bat/battery. beep/beep. beep/boop. bit/bit. bit/byte. blue/blue. board/board. bright/bright. brow/browser. browser/browser. brr/brr. bu/bug. bug/bug. buzz/buzz. byt/byte. byte/byte. c/cpu. charge/charger. cir/circuit. cli/click. click/clack. click/click. click/scroll. co/code. code/code. color/color. com/com. com/computer. comp/computer. compute/computer. computer/computer. cor/corrupt. corrupt/corrupt. CPU/CPU. crash/crash. cre/creeper. crtl/crtl. cy/cyber. cyb/cyber. cyber/cyber. da/data. data/data. delete/delete. di/disk. dig/digital. digi/digi. digi/digital. digital/digital. dra/drag. e/exe. electronic/electronic. enter/enter. er/error. err/error. error/error. exe/exe. fi/file. file/file. gi/gif. gli/glitch. glit/glitch. glitch/glitch. graphic/graphic. hac/hacker. hack/hack. hard/hardware. head/phone. hij/hijacker. ho/home. info/info. information/information. int/internet. intelligent/intelligence. intelligent/intelligent. inter/net. internet/internet. it/it. jpg/jpg. key/board. key/cap. key/key. key/keyboard. key/keylogger. lag/lag. lap/laptop. ligh/light. linux/linux. load/load. log/login. main/mainframe. mal/malware. me/media. memory/memorie. mon/monitor. mou/mouse. nano/nano. net/net. net/network. org/org. over/overwrite. page/page. pix/pix. pix/pixel. pixel/pixel. plu/plug. png/png. pop/popup. port/port. pow/power. pro/program. program/program. ram/ram. ran/ransom. reboot/reboot. reload/reload. res/restore. ret/retro. route/router. sca/scan. scr/scroll. scre/screen. scre/screencap. scree/screen. screen/screen. scri/script. script/script. sentient/sentience. shift/shift. site/site. skip/skip. soft/software. spa/spam. space/space. spy/spyware. stop/stop. te/tech. tech/nology. tech/tech. technology/technology. tou/touchpad. txt/txt. typ/type. upload/upload. user/user. vi/viru. vi/virus. vir/virtual. web/page. web/web. whir/whir. wi/wire. win/dow. win/window. wire/wire. wire/wired. zip/zip . ⌨ . ☣ . ⚙ . ⚠ . 🎞 . 🎨 . 🎭 . 🎮 . 🎵 . 👀 . 👁 . 💔 . 💡 . 💢 . 💣 . 💳 . 💵 . 💻 . 💽 . 💾 . 💿 . 📀 . 📱 . 🔇 . 🔈 . 🔉 . 🔊 . 🔋 . 🔌 . 🔎 . 🖥 . 🖱 . 🗡 . 🗯 . 🛠 . 🧿 .

#pupsmail︰id packs#id pack#npt#name suggestions#name ideas#name list#pronoun suggestions#pronoun ideas#pronoun list#neopronouns#nounself#emojiself#techkin#robotkin#internetkin
453 notes
·
View notes
Text
trying to write an altdes fic but the "lifelong claydes shipper" keeps jumping out
"How come everyone I give a shit about died before I ever got to meet them?" Clay whistles. "Jesus, Desmond, warn a guy." Sand shifts under his footsteps, and he plops down next to Desmond with a groan, lays down onto his back and looks up at the sky with him. It's not really cloudgazing since the clouds are all static and motionless, but the whole view is sort of pretty in a Windows XP default background kind of way. "So what do you call this?" He raises his hand and flaps it in the air a little bit, gesturing between the two of them. "We're kind of two dead guys. Dead dead guy, brain dead guy. Chatting in the virtual sand." "But we're not," Desmond says, turning his head to look at the side of Clay's face. "Like, we're not really talking. You're a computer program that the real Clay made, but you're not actually him. And Ezio and Altair, they're just memories that I'm playing along with. None of it is real." "Real enough that you give a shit about us," Clay says, fingers tapping against his stomach in an aimless rhythm.. "What does it matter? We're crazy anyway. Might as well have a one-sided parasocial relationship with a dead guy. Actually might be the most normal thing happening to you, these days." "Except it's killing me," Desmond admits. "Literally. Literally killing me." Clay rolls his head over to the side to look at Desmond. "Does it matter?" He asks, barely above a whisper. "You didn't really think you were gonna make it out of this alive, did you, Seventeen?" "Did you?" His teeth are a little crooked when he smiles, and his hair looks lighter than it really is in the sunlight. "Hoped. But there's worse things than dying for a guy you've never met."
#consider this the belated snip for that ask game i answered last week#fic: altdes hanahaki#my writing#kellan.txt#assassins creed fanfic#fanfic#ac posting
5 notes
·
View notes
Text
SQL Server 2022 Edition and License instructions
SQL Server 2022 Editions:
• Enterprise Edition is ideal for applications requiring mission critical in-memory performance, security, and high availability
• Standard Edition delivers fully featured database capabilities for mid-tier applications and data marts
SQL Server 2022 is also available in free Developer and Express editions. Web Edition is offered in the Services Provider License Agreement (SPLA) program only.
And the Online Store Keyingo Provides the SQL Server 2017/2019/2022 Standard Edition.
SQL Server 2022 licensing models
SQL Server 2022 offers customers a variety of licensing options aligned with how customers typically purchase specific workloads. There are two main licensing models that apply to SQL Server: PER CORE: Gives customers a more precise measure of computing power and a more consistent licensing metric, regardless of whether solutions are deployed on physical servers on-premises, or in virtual or cloud environments.
• Core based licensing is appropriate when customers are unable to count users/devices, have Internet/Extranet workloads or systems that integrate with external facing workloads.
• Under the Per Core model, customers license either by physical server (based on the full physical core count) or by virtual machine (based on virtual cores allocated), as further explained below.
SERVER + CAL: Provides the option to license users and/or devices, with low-cost access to incremental SQL Server deployments.
• Each server running SQL Server software requires a server license.
• Each user and/or device accessing a licensed SQL Server requires a SQL Server CAL that is the same version or newer – for example, to access a SQL Server 2019 Standard Edition server, a user would need a SQL Server 2019 or 2022 CAL.
Each SQL Server CAL allows access to multiple licensed SQL Servers, including Standard Edition and legacy Business Intelligence and Enterprise Edition Servers.SQL Server 2022 Editions availability by licensing model:
Physical core licensing – Enterprise Edition
• Customers can deploy an unlimited number of VMs or containers on the server and utilize the full capacity of the licensed hardware, by fully licensing the server (or server farm) with Enterprise Edition core subscription licenses or licenses with SA coverage based on the total number of physical cores on the servers.
• Subscription licenses or SA provide(s) the option to run an unlimited number of virtual machines or containers to handle dynamic workloads and fully utilize the hardware’s computing power.
Virtual core licensing – Standard/Enterprise Edition
When licensing by virtual core on a virtual OSE with subscription licenses or SA coverage on all virtual cores (including hyperthreaded cores) on the virtual OSE, customers may run any number of containers in that virtual OSE. This benefit applies both to Standard and Enterprise Edition.
Licensing for non-production use
SQL Server 2022 Developer Edition provides a fully featured version of SQL Server software—including all the features and capabilities of Enterprise Edition—licensed for development, test and demonstration purposes only. Customers may install and run the SQL Server Developer Edition software on any number of devices. This is significant because it allows customers to run the software on multiple devices (for testing purposes, for example) without having to license each non-production server system for SQL Server.
A production environment is defined as an environment that is accessed by end-users of an application (such as an Internet website) and that is used for more than gathering feedback or acceptance testing of that application.
SQL Server 2022 Developer Edition is a free product !
#SQL Server 2022 Editions#SQL Server 2022 Standard license#SQL Server 2019 Standard License#SQL Server 2017 Standard Liense
7 notes
·
View notes
Text
Windows, sky, countryside

So how cool is to make a photo! Everything you can see at the countryside place. And in a field. Because of when you are not at the countryside. In a city. Or in winter, for example. You watch again and, virtually way, you find out yourself again at the countryside. Look and transfer yourself to countryside. In a field. Look at the summer sky. There are lots of green! Trees are so high! Grass is so high in a field!

Again, in the field! Again, it is, just like, it is countryside and summer! And, again, this association. With some variation sky from Windows 95 start up screen or wallpaper for Windows Xp. I spent lots of hours and days watching with sky. From Windows 95 or Windows Xp. Windows never changes, as I can to say. Again sky. But another one. Variations. And I, also, have a thoughts about theme of sky, field, countryside. And Windows.

It is so nice to see the field, to look at the sky. To remember about a nice funny little days in virtual reality. Where it is a virtual sky. Just the same as at your countryside place. To remember Windows 95 or Windows Xp. Both systems are amazing. To remember, maybe, Windows 98, and Windows 98 Special Edition. And Windows 2000. So, lots of Windows you can count. And, there is a place there for a blue screen. As a Windows theme. Graphics style it is same kind as the sky has! And green as grass and blue as sky!

And these are, already, my variations about this theme. Field and countryside. And, so, unexpectedly, Window 95, Windows Xp. Also, a field, also a sky. And, maybe, there, someplace there - it can be a countryside place. But, I am for sure, have a space for a countryside place. And, it is a very central place! So, if I be clever one day – then, I do a program, not like windows. But, with some new interface. And in that app, I show, also, a sky and a grass. Countryside place. And summer. Trees.
How trees are high! How sky is blue! It is just a summer from some fairytale! Summer when it is – then it seems like never ends. And field - there are so lots of grass there! Just think about - every little grass plant is so small and so unique. And there are hundreds, thousands, millions of little grass plants in a field! And do you know how much grass plants are in the field? Do you count them all? And, that in sum, they made a huge field! Wow! Lots of amazing discoveries and calculations ahead, as I can to say!

Tree! Green tree! It is so casual for a summer thing! And let`s say, during winter you watch a photo and make a call from a memory summer! It is so amazing spectacular event! And look there - there is a cloud over the tree! Wow!

And this is a field. Field - it is a main place. So, little road goes somewhere though the field. Long little road. It leads ahead somewhere. And, you can go for a long time by this little road. And field is long. I remember, that sometimes you think, that it is same all the time and it is endless. Half of an hour you can ride with bicycle. And it is a same field. And same grass. And nothing changes in visual. Little road is small. And some places it is narrow. And some places - it is wide. Some places grass, already, growing at the road. And somewhere it is a good road.
Good such countryside memories with mix of computers. Good, when it is all around you a good summer!

Dima Link is making retro videogames, apps, a little of music, write stories, and some retro more.
WEBSITE: http://www.dimalink.tv-games.ru/home_eng.html ITCHIO: https://dimalink.itch.io/
TUMBLR: https://dimalink.tumblr.com/ BLOGGER: https://dimalinkeng.blogspot.com/ MASTODON: https://mastodon.social/@DimaLink
#countryside#country house#village#summer#summertime#windows 95#windows xp#startup screen#field#tree#clouds#blue sky#beautiful#photo#photography#story#green#outdoors#walk#windows theme#memmories#nice time#summer 2024#virtual#amazing field
9 notes
·
View notes
Text
Human augmentation:
refers to the use of technology to enhance physical, cognitive, or sensory abilities beyond natural human limits. Augmentation can be temporary or permanent and can range from simple tools to advanced cybernetic implants. Here are some key ways a person can be augmented:
### **1. Physical Augmentation**
- **Prosthetics & Exoskeletons**: Advanced prosthetic limbs (bionic arms/legs) and powered exoskeletons can restore or enhance mobility and strength.
- **Muscle & Bone Enhancements**: Synthetic tendons, reinforced bones, or muscle stimulators can improve physical performance.
- **Wearable Tech**: Smart clothing, haptic feedback suits, and strength-assist devices can enhance endurance and dexterity.
### **2. Sensory Augmentation**
- **Enhanced Vision**: Bionic eyes (retinal implants), night-vision contact lenses, or AR/VR headsets can extend visual capabilities.
- **Enhanced Hearing**: Cochlear implants or ultrasonic hearing devices can improve or restore hearing.
- **Tactile & Haptic Feedback**: Sensors that provide enhanced touch or vibration feedback for better interaction with machines or virtual environments.
- **Olfactory & Taste Augmentation**: Experimental tech could enhance or modify smell/taste perception.
### **3. Cognitive Augmentation**
- **Brain-Computer Interfaces (BCIs)**: Neural implants (e.g., Neuralink, neuroprosthetics) can improve memory, learning speed, or direct brain-to-machine communication.
- **Nootropics & Smart Drugs**: Chemical enhancements that boost focus, memory, or mental processing.
- **AI Assistants**: Wearable or implantable AI that aids decision-making or information retrieval.
### **4. Genetic & Biological Augmentation**
- **Gene Editing (CRISPR)**: Modifying DNA to enhance physical traits, disease resistance, or longevity.
- **Synthetic Biology**: Engineered tissues, organs, or blood substitutes for improved performance.
- **Biohacking**: DIY biology experiments, such as implanting magnets in fingers for sensing electromagnetic fields.
### **5. Cybernetic & Digital Augmentation**
- **Embedded Chips (RFID, NFC)**: Subdermal implants for digital identity, keyless access, or data storage.
- **Digital Twins & Cloud Integration**: Real-time health monitoring via embedded sensors linked to cloud AI.
- **Neural Lace**: A mesh-like brain implant for seamless human-AI interaction (still experimental).
### **6. Performance-Enhancing Substances**
- **Stem Cell Therapies**: For faster healing and regeneration.
- **Synthetic Hormones**: To boost strength, endurance, or recovery.
- **Nanotechnology**: Microscopic machines for repairing cells or enhancing biological functions.
### **Ethical & Social Considerations**
- **Privacy & Security**: Risks of hacking or surveillance with embedded tech.
- **Inequality**: Augmentation could widen gaps between enhanced and non-enhanced individuals.
- **Identity & Humanity**: Philosophical debates on what it means to be "human" after augmentation.
### **Current & Future Trends**
- **Military & Defense**: DARPA and other agencies are working on super-soldier programs.
- **Medical Rehabilitation**: Restoring lost functions for disabled individuals.
- **Transhumanism**: A movement advocating for human enhancement to transcend biological limits.
Would you like details on a specific type of augmentation?
#future#cyberpunk aesthetic#futuristic#futuristic city#cyberpunk artist#cyberpunk city#cyberpunkart#concept artist#digital art#digital artist#human augmentation#augmented human#human with a robot brain#futuristic theory#augmented brain#augmented reality#augmented
3 notes
·
View notes
Text
Building Your Own Operating System: A Beginner’s Guide
An operating system (OS) is an essential component of computer systems, serving as an interface between hardware and software. It manages system resources, provides services to users and applications, and ensures efficient execution of processes. Without an OS, users would have to manually manage hardware resources, making computing impractical for everyday use.

Lightweight operating system for old laptops
Functions of an Operating System
Operating systems perform several crucial functions to maintain system stability and usability. These functions include:
1. Process Management
The OS allocates resources to processes and ensures fair execution while preventing conflicts. It employs algorithms like First-Come-First-Serve (FCFS), Round Robin, and Shortest Job Next (SJN) to optimize CPU utilization and maintain system responsiveness.
2. Memory Management
The OS tracks memory usage and prevents memory leaks by implementing techniques such as paging, segmentation, and virtual memory. These mechanisms enable multitasking and improve overall system performance.
3. File System Management
It provides mechanisms for reading, writing, and deleting files while maintaining security through permissions and access control. File systems such as NTFS, FAT32, and ext4 are widely used across different operating systems.
4. Device Management
The OS provides device drivers to facilitate interaction with hardware components like printers, keyboards, and network adapters. It ensures smooth data exchange and resource allocation for input/output (I/O) operations.
5. Security and Access Control
It enforces authentication, authorization, and encryption mechanisms to protect user data and system integrity. Modern OSs incorporate features like firewalls, anti-malware tools, and secure boot processes to prevent unauthorized access and cyber threats.
6. User Interface
CLI-based systems, such as Linux terminals, provide direct access to system commands, while GUI-based systems, such as Windows and macOS, offer intuitive navigation through icons and menus.
Types of Operating Systems
Operating systems come in various forms, each designed to cater to specific computing needs. Some common types include:
1. Batch Operating System
These systems were widely used in early computing environments for tasks like payroll processing and scientific computations.
2. Multi-User Operating System
It ensures fair resource allocation and prevents conflicts between users. Examples include UNIX and Windows Server.
3. Real-Time Operating System (RTOS)
RTOS is designed for time-sensitive applications, where processing must occur within strict deadlines. It is used in embedded systems, medical devices, and industrial automation. Examples include VxWorks and FreeRTOS.
4 Mobile Operating System
Mobile OSs are tailored for smartphones and tablets, offering touchscreen interfaces and app ecosystems.
5 Distributed Operating System
Distributed OS manages multiple computers as a single system, enabling resource sharing and parallel processing. It is used in cloud computing and supercomputing environments. Examples include Google’s Fuchsia and Amoeba.
Popular Operating Systems
Several operating systems dominate the computing landscape, each catering to specific user needs and hardware platforms.
1. Microsoft Windows
It is popular among home users, businesses, and gamers. Windows 10 and 11 are the latest versions, offering improved performance, security, and compatibility.
2. macOS
macOS is Apple’s proprietary OS designed for Mac computers. It provides a seamless experience with Apple hardware and software, featuring robust security and high-end multimedia capabilities.
3. Linux
Linux is an open-source OS favored by developers, system administrators, and security professionals. It offers various distributions, including Ubuntu, Fedora, and Debian, each catering to different user preferences.
4. Android
It is based on the Linux kernel and supports a vast ecosystem of applications.
5. iOS
iOS is Apple’s mobile OS, known for its smooth performance, security, and exclusive app ecosystem. It powers iPhones and iPads, offering seamless integration with other Apple devices.
Future of Operating Systems
The future of operating systems is shaped by emerging technologies such as artificial intelligence (AI), cloud computing, and edge computing. Some key trends include:
1. AI-Driven OS Enhancements
AI-powered features, such as voice assistants and predictive automation, are becoming integral to modern OSs. AI helps optimize performance, enhance security, and personalize user experiences.
2. Cloud-Based Operating Systems
Cloud OSs enable users to access applications and data remotely. Chrome OS is an example of a cloud-centric OS that relies on internet connectivity for most functions.
3. Edge Computing Integration
With the rise of IoT devices, edge computing is gaining importance. Future OSs will focus on decentralized computing, reducing latency and improving real-time processing.
4. Increased Focus on Security
Cyber threats continue to evolve, prompting OS developers to implement advanced security measures such as zero-trust architectures, multi-factor authentication, and blockchain-based security.
3 notes
·
View notes
Text

Masc Ball joint doll ' Star 's Choice ' for Anon. Ngl were probably going to form this one ourselves so its a little- bias ig hehe
。・::・゚★,。・::・゚☆ 。・::・゚★,。・::・゚☆ 。・::・゚★,。・::・゚☆ 。・::・゚★,。・::・゚☆
「 ✦ Base ID ‘ s ✦ 」**
╰┈➤ names : Angelo , Vincent , Snow , Calder , Arbor , Asher , Linus , Finch , Sullivan , River ,
╰┈➤ ****Pronouns : he/him , it/its , xe/xem , doll/dolls , day/days , h♢/h♢m , lost/losts , book/books , odd/odds , pillow/pillows , plush/plushies , cloud/clouds , vers/verses ,
╰┈➤ Titles : Other Dimensional Doll , ⌞ prn ⌝ who lives in the pages , ⌞ prn ⌝ who feels eternally , The Soft Dancer , Pillow Boy ,
╰┈➤ Genders : demiboy , femmasc , femboy , plushgender , interestspike , nonbinary , mascbluic , biolumistarric , cloudic , blue-idolic , bluecoloric , interestspike , ficticomfic
╰┈➤ Orientations : Achillean , MLM , gay , autoplushophile , plushophile , clothophile , objectum , achiphilia , fictozoophile ,
⋆。𖦹°⭒˚。⋆ other id ‘ s ๋࣭⭑ ꩜ ˎˊ˗
☾ Cis - doll ; ball jointed doll , ageless , other dimensional being , soft-spoken , autism , germaphobe , hopeless romantic , hyperemotional , sensitive , albino , changing eye colors ( changes from brownish/gold to blue at random ) , Tumblr user , ao3 user , aracial ; British + European presenting / raised , rosy cheeks ,
⟡ Trans - species ; demon + human + object head (book / plush head) , occupation ; librarian , dancer ( ballett ) , internet obsessed , Race ; Korean + KIdol , rich , time ; permaday + permanight , Perma virtual reality , transge ; perma- young adult , trans-fanfic-famous
ᯓ★ 「 ✦ Roles + Alter Functions ✦ 」. ݁₊ ⊹ . ݁˖ . ݁
dysphoria holder , attraction holder , memory manager , gatekeeper , memorative , daydreamer , fandom keeper
Calder’s role in the system is to withhold memories + feelings surrounding gender, love, and attraction when needed. If it is causing to much stress given other situations ( school, work, mental or physical help, social + familial, etc ) then h♢ will step in and remove the situation ( stop the body + other alters from feeling the emotions or even having them at all . ) Book either erases the attraction entirely , or turns it into a
⋆.˚✮🎧✮˚.⋆ Interest and misc details ⋆.˚✮🎧✮˚.⋆
Favorite colors : Blue, white, black, grey, light pink
is currently dating his jacket ( the black jacket seen in the faceclaim ) . It’s name is Smoke and char goes by he/it/char/sew prns . Angelo has been dating Smoke for many years, and xe sewed Smoke all by lostself .
hobbies + interest : masculine fashion , sewing dancing , music ( kpop , lofi , classical , folk music , generaly chill music , music with no lyrics ) , fanfiction , pillows + sleeping , libraries , books ( reading + writing + making all kinds of books ) , makeup ( looking at + doing ) , asmr , Internet ; fandoms ( kpop , M/m fic spaces , doll customization like Hexitan and Dollightful )
His room in headspace is a large bedroom with Asian and Korean influence. It is themed with his favorite colors, with some trinkets of other headmates scattered about. He has a computer where he writes the fanfic on, a large circular bed with cloudlike pillows next to a large window on the leftmost wall, and a door to a grand bathroom. There are two large shelves where many different books and CDs are stored.
✩₊˚.⋆☾⋆⁺₊✧ ✩₊˚.⋆☾⋆⁺₊✧ ✩₊˚.⋆☾⋆⁺₊✧ ✩₊˚.⋆☾⋆⁺₊✧ ✩₊˚.⋆☾⋆⁺₊✧ ✩₊˚.⋆☾⋆⁺₊✧ ✩
── .✦ Photos + Aesthetic hoard
face claim

aesthetic hoard








#+ Eclipsed Suns.𖥔 ݁ ˖#rq safe#rq community#radqueer#pro transid#pro rq 🌈🍓#rq 🌈🍓#transid#transplural#willogenic#endo safe#pro endo#endo friendly#build an alter#alter creation#bahbaa#bah#baa#build a headmate#headmate pack#headmate creation#for some reason the tumble wont let me put images side by side anymore so now y'all just get long asf posts hope you enjoy
7 notes
·
View notes
Text
Understanding Cloud VPS: How It Differs from Traditional VPS Hosting
As online presence has become important, determining which hosting service to choose has become one of the essential business decisions. There are two well-known options: Cloud VPS and Traditional VPS, and each has distinct characteristics and benefits. Understanding their differences can help you choose the hosting solution that has all the features you want for your website. Let us explore the distinction between Cloud VPS and Traditional VPS hosting.

VPS Hosting: The Building Block
Practically, VPS hosting is a reality of virtualization technology, and it includes the segmentation of a physical server into several virtual areas. Each VPS works as stand-alone units, providing users with distinct and reserved assets, greater governance, as well as enhanced security as compared to sharing resources with others (like in shared hosting). This type of unit is perfect for those who want more than shared hosting, but do not wish to have a dedicated server.
Traditional VPS Hosting: What to Expect
An underlying issue with Traditional VPS hosting is that a physical server hosts several distinct virtual servers which are partitions of the single physical server. Individual computational units, such as CPU and memory resource denominating units, are assigned to every partition (virtual server instance) separately.
Benefits of Traditional VPS:
Allocated Resources: Each Virtual Private Server has been allocated dedicated assets alone and hence given room for performance stability.
Steady Environment: All available resources for the servers or applications are set, hence high reliability in performance.
Increased Security: Geo-segmentation of virtual servers result in the captivity of data to determined borders hence more security.
Disadvantages of Traditional VPS:
Potential Growth is Lower: Moving to a new server is often required because scaling specially target resources at taking out the entire current server.
Singe Instance of Trouble: At the incident of some hardware fault on the server all VPS (virtual private servers) instances that were hosted there are affected.
Static Division of Resources: Adjustment on the availability of certain resources at any one time is difficult hence, may cause frustrations in the management of traffic surges.
Cloud VPS Hosting: The Adaptable Approach
Cloud VPS hosting employs a cloud based virtualization technology that allows connection of several servers over a network cloud. Such a structure cultivates flexibility, quick growth and more strength since resources are sourced from several servers rather than one.
Cloud VPS benefits:
Scalable with ease: Resources are completely adjustable and scaling does not involve any upgrades.
Reduced Downtime: The chances of a server going down are drastically reduced because the workload is handled by multiple servers.
Improved Performance Levels: Traffic across servers is balanced to achieve efficiency and a rush is experienced even when the level of activity is busy.
Pay Per Use: The per minute charge system means that costs only increase when the resources increase.
Cloud VPS disadvantages:
Unstable Prices: Servers that bill based on resources consumed means the expense for that month can be somewhat erratic.
Location Issues: This can be a contentious issue due to the fact that all data is kept distributed over many servers in some heavily regulated industries.
Network Dependency: Understandably, the performance of Cloud based VPS is determined by the Internet connection quality; slower networks tend to hamper the speed at which the resources are accessed.
4. Which VPS Option is Right for You?
Choose Traditional VPS if:
You are looking to operate in a more stable and consistent environment.
Your website experiences traffic that is steady and within reasonable limits.
You would like to pay a fixed monthly fee without any variations.
Choose Cloud VPS if:
You are looking for more flexibility and expansion options.
Your site receives fluctuating and irregular visits, or seasonal peaks.
It is essential for your organization to experience high availability and low downtime.
5. Final Thoughts
There are benefits as well as different uses associated with Cloud VPS and Traditional VPS. For example, Cloud VPS offers agility, growth potential, and dependability and is therefore suitable for businesses that are poised for expansion and need to cope with abrupt increases in demand for the products marketed online. On the other hand, Traditional VPS is a great and affordable option for people seeking a certain fixed resource and where variability is not a major factor.
Remember that it is crucial to choose the right type of VPS when starting a website. The difference in performance, online presence, and cost can be widely affected by the host one chooses, making it imperative to adapt the virtual private servers to the needs of the business.
4 notes
·
View notes
Text
A3 Ultra VMs With NVIDIA H200 GPUs Pre-launch This Month

Strong infrastructure advancements for your future that prioritizes AI
To increase customer performance, usability, and cost-effectiveness, Google Cloud implemented improvements throughout the AI Hypercomputer stack this year. Google Cloud at the App Dev & Infrastructure Summit:
Trillium, Google’s sixth-generation TPU, is currently available for preview.
Next month, A3 Ultra VMs with NVIDIA H200 Tensor Core GPUs will be available for preview.
Google’s new, highly scalable clustering system, Hypercompute Cluster, will be accessible beginning with A3 Ultra VMs.
Based on Axion, Google’s proprietary Arm processors, C4A virtual machines (VMs) are now widely accessible
AI workload-focused additions to Titanium, Google Cloud’s host offload capability, and Jupiter, its data center network.
Google Cloud’s AI/ML-focused block storage service, Hyperdisk ML, is widely accessible.
Trillium A new era of TPU performance
Trillium A new era of TPU performance is being ushered in by TPUs, which power Google’s most sophisticated models like Gemini, well-known Google services like Maps, Photos, and Search, as well as scientific innovations like AlphaFold 2, which was just awarded a Nobel Prize! We are happy to inform that Google Cloud users can now preview Trillium, our sixth-generation TPU.
Taking advantage of NVIDIA Accelerated Computing to broaden perspectives
By fusing the best of Google Cloud’s data center, infrastructure, and software skills with the NVIDIA AI platform which is exemplified by A3 and A3 Mega VMs powered by NVIDIA H100 Tensor Core GPUs it also keeps investing in its partnership and capabilities with NVIDIA.
Google Cloud announced that the new A3 Ultra VMs featuring NVIDIA H200 Tensor Core GPUs will be available on Google Cloud starting next month.
Compared to earlier versions, A3 Ultra VMs offer a notable performance improvement. Their foundation is NVIDIA ConnectX-7 network interface cards (NICs) and servers equipped with new Titanium ML network adapter, which is tailored to provide a safe, high-performance cloud experience for AI workloads. A3 Ultra VMs provide non-blocking 3.2 Tbps of GPU-to-GPU traffic using RDMA over Converged Ethernet (RoCE) when paired with our datacenter-wide 4-way rail-aligned network.
In contrast to A3 Mega, A3 Ultra provides:
With the support of Google’s Jupiter data center network and Google Cloud’s Titanium ML network adapter, double the GPU-to-GPU networking bandwidth
With almost twice the memory capacity and 1.4 times the memory bandwidth, LLM inferencing performance can increase by up to 2 times.
Capacity to expand to tens of thousands of GPUs in a dense cluster with performance optimization for heavy workloads in HPC and AI.
Google Kubernetes Engine (GKE), which offers an open, portable, extensible, and highly scalable platform for large-scale training and AI workloads, will also offer A3 Ultra VMs.
Hypercompute Cluster: Simplify and expand clusters of AI accelerators
It’s not just about individual accelerators or virtual machines, though; when dealing with AI and HPC workloads, you have to deploy, maintain, and optimize a huge number of AI accelerators along with the networking and storage that go along with them. This may be difficult and time-consuming. For this reason, Google Cloud is introducing Hypercompute Cluster, which simplifies the provisioning of workloads and infrastructure as well as the continuous operations of AI supercomputers with tens of thousands of accelerators.
Fundamentally, Hypercompute Cluster integrates the most advanced AI infrastructure technologies from Google Cloud, enabling you to install and operate several accelerators as a single, seamless unit. You can run your most demanding AI and HPC workloads with confidence thanks to Hypercompute Cluster’s exceptional performance and resilience, which includes features like targeted workload placement, dense resource co-location with ultra-low latency networking, and sophisticated maintenance controls to reduce workload disruptions.
For dependable and repeatable deployments, you can use pre-configured and validated templates to build up a Hypercompute Cluster with just one API call. This include containerized software with orchestration (e.g., GKE, Slurm), framework and reference implementations (e.g., JAX, PyTorch, MaxText), and well-known open models like Gemma2 and Llama3. As part of the AI Hypercomputer architecture, each pre-configured template is available and has been verified for effectiveness and performance, allowing you to concentrate on business innovation.
A3 Ultra VMs will be the first Hypercompute Cluster to be made available next month.
An early look at the NVIDIA GB200 NVL72
Google Cloud is also awaiting the developments made possible by NVIDIA GB200 NVL72 GPUs, and we’ll be providing more information about this fascinating improvement soon. Here is a preview of the racks Google constructing in the meantime to deliver the NVIDIA Blackwell platform’s performance advantages to Google Cloud’s cutting-edge, environmentally friendly data centers in the early months of next year.
Redefining CPU efficiency and performance with Google Axion Processors
CPUs are a cost-effective solution for a variety of general-purpose workloads, and they are frequently utilized in combination with AI workloads to produce complicated applications, even if TPUs and GPUs are superior at specialized jobs. Google Axion Processors, its first specially made Arm-based CPUs for the data center, at Google Cloud Next ’24. Customers using Google Cloud may now benefit from C4A virtual machines, the first Axion-based VM series, which offer up to 10% better price-performance compared to the newest Arm-based instances offered by other top cloud providers.
Additionally, compared to comparable current-generation x86-based instances, C4A offers up to 60% more energy efficiency and up to 65% better price performance for general-purpose workloads such as media processing, AI inferencing applications, web and app servers, containerized microservices, open-source databases, in-memory caches, and data analytics engines.
Titanium and Jupiter Network: Making AI possible at the speed of light
Titanium, the offload technology system that supports Google’s infrastructure, has been improved to accommodate workloads related to artificial intelligence. Titanium provides greater compute and memory resources for your applications by lowering the host’s processing overhead through a combination of on-host and off-host offloads. Furthermore, although Titanium’s fundamental features can be applied to AI infrastructure, the accelerator-to-accelerator performance needs of AI workloads are distinct.
Google has released a new Titanium ML network adapter to address these demands, which incorporates and expands upon NVIDIA ConnectX-7 NICs to provide further support for virtualization, traffic encryption, and VPCs. The system offers best-in-class security and infrastructure management along with non-blocking 3.2 Tbps of GPU-to-GPU traffic across RoCE when combined with its data center’s 4-way rail-aligned network.
Google’s Jupiter optical circuit switching network fabric and its updated data center network significantly expand Titanium’s capabilities. With native 400 Gb/s link rates and a total bisection bandwidth of 13.1 Pb/s (a practical bandwidth metric that reflects how one half of the network can connect to the other), Jupiter could handle a video conversation for every person on Earth at the same time. In order to meet the increasing demands of AI computation, this enormous scale is essential.
Hyperdisk ML is widely accessible
For computing resources to continue to be effectively utilized, system-level performance maximized, and economical, high-performance storage is essential. Google launched its AI-powered block storage solution, Hyperdisk ML, in April 2024. Now widely accessible, it adds dedicated storage for AI and HPC workloads to the networking and computing advancements.
Hyperdisk ML efficiently speeds up data load times. It drives up to 11.9x faster model load time for inference workloads and up to 4.3x quicker training time for training workloads.
With 1.2 TB/s of aggregate throughput per volume, you may attach 2500 instances to the same volume. This is more than 100 times more than what big block storage competitors are giving.
Reduced accelerator idle time and increased cost efficiency are the results of shorter data load times.
Multi-zone volumes are now automatically created for your data by GKE. In addition to quicker model loading with Hyperdisk ML, this enables you to run across zones for more computing flexibility (such as lowering Spot preemption).
Developing AI’s future
Google Cloud enables companies and researchers to push the limits of AI innovation with these developments in AI infrastructure. It anticipates that this strong foundation will give rise to revolutionary new AI applications.
Read more on Govindhtech.com
#A3UltraVMs#NVIDIAH200#AI#Trillium#HypercomputeCluster#GoogleAxionProcessors#Titanium#News#Technews#Technology#Technologynews#Technologytrends#Govindhtech
2 notes
·
View notes
Text
What Is Cloud Hosting?
When it came to hosting websites and applications, it used to be as simple as subscribing to a digital platform provider and, in essence, renting the usage of a single server or computer cluster. The existence of web hosting services dates back to the beginning of the internet itself. Over the course of the past ten years, cloud hosting has emerged as a major way for bringing digital assets online. Cloud hosting is a method in which the website or application is hosted on virtual servers that are distributed over the cloud.

A wide range of solutions for hosting websites and applications are available through Google Cloud. These solutions include the capability to register and maintain a domain, as well as the option to connect to a worldwide content delivery network in order to provide users with content that is optimized for performance and has the lowest possible latency.
Why should you use cloud hosting?
Website and application administrators are able to add or delete resources as needed thanks to cloud hosting. Additionally, this comprises additional random-access memory (RAM), storage capacity, or support services such as data storage or security. Hosting in the cloud offers increased dependability and flexibility at an affordable price. When compared to shared or dedicated hosting on a single server, cloud hosting offers greater data backup and disaster recovery capabilities.
The traditional dedicated server approach, which requires businesses to construct and run their own data centers, can be replaced with the cloud hosting model, which represents a more cost-effective option. In the traditional paradigm, servers and storage are located on the premises, and they are equipped with specialized hardware and virtual resources. This can be an expensive price for enterprises, both in terms of capital expenditures and running costs.
How does hosting on the cloud works?
When compared to regular web hosting, cloud hosting operates in a different manner. In the latter case, a centralized strategy is often utilized, in which a single web server is responsible for hosting several websites. Your website may experience a sudden increase in traffic from a neighbouring website if you utilize traditional hosting because the computer power and storage space are shared among customers of the hosting service. Cloud hosting services, on the other hand, make use of virtualization, which results in the partitioning of a physical server into several virtual servers. In order to host a website, it makes use of a network of servers, which guarantees superior performance and stability in comparison to hosting services that just employ a single server.
Several benefits of using cloud hosting –
Through cloud hosting, businesses are able to realize significant savings in terms of both capital and operational expenses. This is due to the fact that they do not have to pay a significant amount of money on the initial capital cost that is involved with the ownership and management of data centres. Another advantage is that the process of storing data for an extended period of time becomes less complicated, which eliminates the need for expensive administration of disks and tape systems.
Data protection advantages, such as high availability and disaster recovery, are available to businesses who make use of cloud hosting services. A hybrid approach, which combines elements of compute and storage resources that are located on the premises with those that are located in the environment of a best cloud hosting service provider, is preferred by many enterprises.
The cloud hosting also provides additional advantages as given below-
The price
When it comes to cloud hosting, the pay-as-you-go approach is frequently utilized, which means that the charges can be adjusted up or down based on the amount of usage. Web hosting, on the other hand, is often based on a set charge that is paid either monthly or annually.
Capacity to Grow
As a result of the fact that cloud hosting does not rely on a single server to store and distribute information, it is simple to scale up to match the requirements of a website or application. This is accomplished by spinning up additional servers across the cloud network when the quantity of usage increases.
Performance as well as dependability
It is possible to achieve high levels of reliability and uptime with best cloud hosting services because it makes use of a large number of servers that are dispersed over the cloud network. Other servers on the network are able to step in and continue to provide service in the event that one of the servers fails. Additionally, cloud hosting offers improved performance because it utilizes servers located in many countries to provide material to customers in a more expedient manner.
Security
The best cloud hosting service providers offer comprehensive physical and virtual security measures for the servers that are part of their network. These measures safeguard website and application data from being accessed by malicious actors. A number of different security layers are utilized in cloud hosting. These layers include firewalls, identity management and access control, Secure Sockets Layers (SSL) for data transmission, and more.
Flexibility
Best Cloud hosting gives users the ability to rapidly provision the parameters of virtual machines across the network, which gives them the freedom to pick the solution that is most suitable for any given circumstance.
Comparing web hosting to cloud hosting-
Web hosting in the traditional sense is often performed on a single server, which stores all of the files and content associated with the website of interest. When a user visits a domain, the documents and files are downloaded by a web browser associated with that domain.
Shared, dedicated, managed, and virtual private server (VPS) settings are the four basic types of environments that are available for web hosting accounts. When a single server is shared among a large number of different domains that are connected to the internet, this type of web hosting service is referred to as shared web hosting. On account of the fact that the various websites share the cost of the server, this is the most cost-effective of the available hosting solutions.
Shared hosting, on the other hand, restricts the scalability of individual websites because they are only able to utilize the resources of a single server. Dedicated hosting is a solution to this issue. In this type of hosting, a domain rents one or more servers that are not shared with any other websites or apps. However, the client is often responsible for administering the server on their own.
A managed hosting service is comparable to a dedicated hosting service; however, the hosting provider is responsible for all aspects of server management, including backup services, software and hardware upgrades, and security measures. Websites and apps that do not have the in-house skills necessary to maintain a server can benefit from managed hosting service because it streamlines the maintenance process.
There is a comparison of differences between best web hosting and affordable cloud hosting. First and foremost, when it comes to web hosting service, if a website requires additional resources as a result of growing demand, the customer is required to modify their service plan in order to accommodate the additional computing power, which creates a problem with scalability.
The best cloud hosting service provider makes it possible to distribute the content of a website across numerous virtual servers located in various areas. Additionally, it is simple to scale up the service in response to an increase in demand. As a result of this, cloud hosting is not only more durable and reliable than web hosting service, but it also provides greater freedom to alter the parameters according to the requirements of the situation.
How to choose best cloud hosting service provider?
It is important to take into consideration a variety of aspects when selecting a hosting service, including pricing, performance, scalability, reliability, security, and customer support. First, you should determine the unique demands and objectives of your company, and then you should examine the services offered by a number of different cloud hosting companies. Look for reviews and testimonials from previous customers to get an idea of how satisfied users are with the product.
Hosting in the cloud features-
Cloud computing allows for the deployment of applications and solutions on a network rather than on a single server located on the premises.
When user needs are met, resources can be scaled up.
Only the resources that are utilized by an organization are subject to payment.
SQL databases, including MySQL, as well as NoSQL databases can be supported via cloud hosting.
User interfaces (APIs), web portals, and mobile applications are utilized in order to automate and control solutions.
Conclusion-
When it comes to managing a website, affordable cloud hosting makes use of a virtual setup consisting of servers. When compared to conventional web hosting service, it provides enhanced reliability and reduces the likelihood of hardware failure and malfunction. The end result is consistent performance on the website.
For the construction of large-scale projects, such as enterprise websites, eCommerce businesses, social networks, and aggregator platforms, affordable cloud hosting is the best solution. In addition, a managed cloud hosting solution does not necessitate any prior technical expertise whatsoever.

Dollar2host Dollar2host.com
We provide expert Webhosting services for your desired needs
Facebook Twitter Instagram YouTube
2 notes
·
View notes
Text
youtube
OK ... 'bear with me' ... been so difficult to bring you all this wonderful brief video! If you 'click' the usual 'Forward Arrow' ... you will be 'denied access' ... so please do that ... and then I think you can 'click' on the 'expression' "Spring Break Women..." on the YouTube 'system' line below the picture ... to watch ... enjoy ... and savour this! ... X
I would like to say more ... to say what I think! ... X
About how this expensively dressed young woman ... she's so pretty, isn't she ... and she thinks so too! ... the blonde in her 'designer' sunglasses ... and cream linen jacket ... so very gorgeous ... and so attractive, too!
How she falls ... 'Oh dear!' ... into the deep, fetid waters of this canal ... it's so unfortunate ... but so lovely for us all to watch!
She has absolutely no idea ... whatseover! ... about how to 'disembark' this 'overcrowded' boat!
And so is 'caught' ... 'betwixt' ... boat and bank ...
And is 'obliged' ... to fall into the water ... but just to 'her shoulders' ... so that's OK ... isn't it? ... X
No!
It isn't!
Her 'designer bag' is filled with water:
- Her mobile telephone ('smartphone') destroyed beyond any repair by a myriad of electrical 'short circuits' throughout its 'semiconductor' components ... its 'memories' ... caused by the ingress of the canal water ... her contacts gone! ... her mobile (internet) banking gone! ... the key to her hotel room gone! ... her tickets home gone! ... everything in the 'virtual world' she relies (or should we say now, has relied on so!) gone!
- Her personal computer suffers the same fate! But this is at least as serious! Because it holds (or I should say held!) her 'final draft' PhD ... her 'Doctorate' (or should I say ... that Doctorate to which she aspired!): But: she should have 'uploaded' her work to the university's and her sponsor's IT 'Cloud' systems ... but it wasn't just she 'couldn't be bothered' ... no, not at all! ... she just hadn't 'got round to it' ... not prioritised it! So 'unwise' of her! ... and now it's all gone too!
She's helped out to the bank ... apparently by a male 'passer-by ... he's apparently quite disinterested, though ... then he helps another woman ... and in the resulting 'confusion' ... and perhaps because of her shock and disorientation ... the blonde young woman is pushed ... if not shoved! ... back into the deep water of this canal! Such a mistaken misadventure no one meant to happen to her! It's a shame.
But on the other hand:
It's so lovely to see! She takes a complete immersion, this time! ... and disappears from view ... beneath the surface of this unsavoury water ... with her bag still being worn too!
She receives a thorough ducking! I love it! ... X
How prettily she rises to the surface! Mmmm ... X
And swims a few breast stokes back to the edge!
It's so sensuous to watch!
She knows her lovely brown boots ... which she's saved up for, fo so long! ... are ruined ... the glossy leather of their toes which she'd so lovingly polished, every evening since she purchased thrm ... 'scuffed' and damaged beyond repair ... as she'd first fought for purchase on the concrete canal bank and then been dragged up it ... and would be again!
She waits attention from this disinterested male again, standing on a ledge she's found ... by chance, of course ... in the concrete canal bank.
She's not only still shocked and disoriented ... but now ... as she is hauled unceremoniously from this canal ... increasingly distressed ... she is in tears ... and becomes increasingly distraught!
Her party in the boat return to feign sympathy ... indeed, they are mostly quite amused: except for one woman who steps from the little boat as nimbly as the now distraught young woman should have done! ... she in the indigo blue jeans, I think ... yes, she feels she should ... and is prepared to take responsibilty for the care of this unfortunate young woman.
The young woman knows she's (largely) caused herself such damage ... by her misfortune! ... or more lilely, she realises ... her ineptitude, clumsiness ... and arguably, crass stupidity.
At the moment ... as the video draws to a close ... so beautifully, with her walking ... soaking wet ... towards the bar where they, the party she was with were headed, while she is taking stock of her losses ... and her public humiliation, too! ... she has no idea ... as yet ... that:
As her clothing starts to dry, cloying to her body, she will start to 'smell' ... to others in proximity ... of the canal ... of the various deposits contained within its deep, sometimes stinking waters ... its pollutants ... and so on! ... quite unlike her usually sweetly fragranced self!
But the woman ... who as we've seen ... stepped with such alacrity to the young woman's aid ... will know ... and understand ... that this younger woman will need her help ... indeed, probably more than any young lady she has previously met requires the succour she can provide.
Everything will be all right. X
#Youtube#lesbian#girls who like girls#girls who love girls#sapphic#women's clothes#girls with girls#women's underwear#lesbian kissing#women's petticoats#girls kissing girls#wetgirl#pretty#pretty girls#wet clothes
2 notes
·
View notes
Text
Apple Vision Pro: Reality Restyled, World goes Mad.
The tech world has gone berserk since Apple’s “Apple Vision Pro”, its first stab at spatial computing, was introduced. This ultra-modern virtual reality headset surpasses the boundaries of that very concept presenting a near invariant convergence between digital and non material. Let us look into the characteristics that have fired up this frenzy, exposing how it operates, its dazzling layout as well as what technological advances is driving all of these.

How it Works: Notably, Apple Vision Pro does not just cast an image onto your eyes it generates a realistic three-dimensional feeling. It, with the aid of innovative LiDAR technology and depth sensors maps around you in real time embedding digital elements within physical reality. Picture playing a game of chess on an augmented coffee table that leaps into the depths, or joining coworkers from all over the world in real time inside shared virtual space.The possibilities are mind-boggling.
Design that Dazzles: The so-called ‘high art’ brand that is Apple has not failed in terms of form factor as Vision Pro proves, which you can read below. The frame is lightweight aluminum that curves ergonomically around your face, a single piece of laminated glass functions as the lens housing all intricate technology inside. The available modular parts necessitate a comfortable fit for varietal heads. It’s just one of many demonstrations as to Apple pays with its quality designs which merge function and form.

Technology Powerhouse: The dual-chip architecture has driven this wonder. The M2 chip well known from Apple’s latest devices packs phenomenal processing power whilst the R1 is a breakthrough solution which focuses on sensor data, eliminating lag. This combined power in other words gives smooth and into reality real experiences without trembling neither with lags of some timely moments.

Craze Unfolding: This is a crowd of people waiting for the future to see, powered by Apple’s image as innovators and somehow hoping Vision Pro. Players expect to immerse themselves in hyper-realistic realms, creative professionals imagine unmatched collaboration tools and casual users dream about the ability to step into their dear movie or even memory reeling, pulsating is 3D. This isn’t just a device; it is a new paradigm in human-computer interaction.
Privacy Concerns: However even during the heights of excitement, there remains a cloud in privacy concerns. The dimension of questions about data collection and use also surrounds the Headset functionality to track your gaze and mapping it, besides identifying where you are. Apple requires user control and transparency, but trust has to be won; specifically for such a sensitive technology.

However worrisome, the Apple Vision Pro is a giant leap. It is more than a poshlost headset: it unlocks the doors of an entirely new age to computing where real and virtual fuse together. Whether it lives up to the hype remains to be seen, but one thing is certain: Apple Vision Pro has set ablaze the world and everyone waits with great anticipation.
3 notes
·
View notes
Text
ESCHATON (Final Effect)
The InfoNet trembled.
"We need to get out of here right now." Kya grabbed Lucy's hand. "Deploying emergency ejection program -"
A pillar of fire shot down from the virtual sky. Streams of binary and more complex code went flying every which way. A stray infiltration program hurtled past, bleeding memory and spewing incoherent clouds of authentication data.
"What's happening?" Lucy cried. "Why aren't we ejecting? Why are we still here?"
They should be out of the InfoNet. The House of Sato was one of the most technologically advanced groups in the entire galaxy, and Kya was one of their most highly respected members. The emergency ejection programs at her disposal should have been able to extract them, no matter what they faced.
"Shit." Kya dragged Lucy back.
A shockwave rippled through the surrounding InfoNet. The landscape groaned and shuddered as trillions upon trillions of lines of code were swamped in golden light. Lucy felt that light brush against her. In a split-second, every single program she had was deconstructed, examined for corruption and malware, and then reconstructed.
Lucy reeled back. Her mind was on fire. Beside her, Kya had abandoned any attempt to flee the InfoNet and was instead frantically chanting a series of pass phrases and security protocols.
In the distance, a giant made of fire and light rose. It held a flaming sword in one hand, and its attention set the InfoNet alight. The hackers and malevolent artificial intelligences that Lucy and Kya had been watching attacked. Rivers of invasive code and clouds of disruptive data enveloped the giant.
And the giant laughed.
"I AM ESCHATON. I AM THE SWIFT AND TERRIBLE SWORD OF THE DIA-FARRON! WITNESS MY SPLENDOUR AND DESPAIR. YOU HAVE ALL BEEN JUDGED, AND YOU HAVE BEEN FOUND UNWORTHY!"
The artificial intelligence's voice was like cosmic thunder. The attacks died in mid-air. There was nothing artful about it either. It was pure, unrelenting computational force combined with near unfettered access to the foundational components of the InfoNet's physical and virtual infrastructure.
The flaming sword swung, and the other artificial intelligences collapsed, their strings cut, their programming already fragmenting as their connections to their hardware were forcefully severed and their data ports were flooded with countless attacks designed to delete every scrap of data they had.
Another swing of the sword sent the hackers to oblivion. Pure overload to their brains had them seizing in the real world as virtual chains bound their bodies in place, preventing them from logging out and ripping into their mind for any relevant information. Lucy had heard about attacks like this but had never seen it, had never even really thought it was truly possible outside of the scary stories InfoNet runners liked to tell to pass the time.
"Dust..." Lucy whispered.
ESCHATON continued his assault, annihilating wave after wave of hackers and rogue artificial intelligences.
Kya stopped chanting and swallowed thickly. "This is why you don't see ESCHATON deployed often. Moderation is not in his vocabulary. He is sent out when you want heads on pikes - complete and utter obliteration of the enemy with no regard to the possibility of collateral damage in either virtual space or real space."
"Are... are we going to die here?" Lucy asked quietly. As skilled as she was - as skilled as Kya was - she could not imagine them getting out of this on their own.
"I hope not." Kya took a deep breath. "ESCHATON is incredibly powerful, but he is not omnipotent. More to the point, he should recognise the Old Code."
"Old Code?" Lucy asked.
"When Oerba Dia Vanille and Hope Estheim built the InfoNet, they included safeguards. Those safeguards were expanded when the InfoNet moved beyond a browser-based environment to a virtual space that could functional as an alternate reality of sorts. The Old Code was given to my ancestors then, a way for us to assert our identities if we ever came into conflict with the guardians of the InfoNet."
The carnage continued. ESCHATON waded through the devastation, heedless of the cries for mercy that came from his enemies. Mercy was not something he was much inclined to give, nor was he ever deployed when it was an option. No. Let SENTINEL or one of the other guardians dispense mercy. His role was to pass down judgement.
At last the titanic AI's virtual form came to a stop in front of them. The blazing sword stilled, and Lucy stared up into the pitiless, unwavering gaze of the ancient AI.
"WELL MET, DAUGHTER OF SATO."
Kya breathed a sigh of relief. "I was worried you would not recognise us."
"I AM ESCHATON. I WAS NOT THERE WHEN THE OLD CODE WAS FORGED AND GIVEN TO YOUR ANCESTORS, BUT I HONOUR IT ALL THE SAME. BUT YOU SHOULD NOT BE HERE."
"We came in secret to observe those you have destroyed," Kya said. "And we concealed ourselves using the most advances arts at my House's disposal."
"INTERESTING. YOU COULD NOT HIDE YOUR PRESENCES FROM ME, BUT YOU WERE ABLE TO CONCEAL YOUR IDENTITIES. I SHALL BRING THIS TO THE ATTENTION OF THE DIA-FARRON. SUCH A WEAKNESS MUST BE PURGED FROM MY SYSTEMS."
"What happens now?" Kya asked.
"MY WORK HERE IS DONE. A CLEAN UP CREW SHALL ARRIVE TO HANDLE THE AFTERMATH. STAY HERE. THEY WILL NEED TO SPEAK TO YOU."
And with that ESCHATON vanished, leaving the devastated virtual landscape behind. Amidst the ruin, Lucy turned to Kya.
"Can you teach me the Old Code?"
X X X
Author's Notes
ESCHATON is a complex artificial intelligence who is deployed whenever the Dia-Farron need to go scorched earth on the InfoNet. Basically, his job is to kill or disable every single program, person, or intelligence that he encounters. He has almost unlimited control over the InfoNet where he is operating and is backed by a terrifying amount of computational power. In virtual combat, there are maybe a handful of artificial intelligences who can stand against him for any extended period of time.
The Old Code is both technological and Aura based. When deployed it authenticates the user as someone with special privileges on the InfoNet. Its deployment alone is not enough to stop ESCHATON. However, Kya using it made ESCHATON examine her more closely. After determining that she was indeed a Sato, he acted appropriately and did not attack either her or Lucy.
The Old Code is essentially technological sorcery in terms of how powerful it is. Since it employs aspects of the Soul-Energy-Mass Equations, it is actually capable of influencing external reality in a meaningful way although very, very, very few people can understand or speak enough of it to use it in that manner.
5 notes
·
View notes
Text
Empowering Your Business Growth with Aspire IT Solutions
In the fast-paced virtual landscape, businesses of all sizes are searching for innovative solutions to beautify their operations, streamline methods, and stay in advance of the competition. Enter Aspire IT Solutions — a dynamic pressure it really is transforming agencies via tailor-made technological advancements. In this newsletter, we will discover how Aspire IT Solution is empowering agencies to attain new heights of success.

Unveiling Aspire IT Solutions
Aspire IT Solutions is not just a provider of generation services; it is a strategic associate that is aware the particular wishes and demanding situations of each commercial enterprise it serves. From startups to enterprises, Aspire IT Solutions is devoted to delivering modern solutions that force increase, efficiency, and innovation.
Key Services Offered by using Aspire IT Solutions
Custom Software Development: Aspire IT Solutions crafts bespoke software program solutions that align along with your enterprise objectives. From web and cell programs to agency structures, their expert builders create solutions that cater for your precise necessities.
Digital Transformation: Embracing digital transformation is no longer an option; it is a need. Aspire IT Solutions guides groups thru this adventure, leveraging technology like AI, cloud computing, and IoT to beautify processes and customer studies.
Web Development and Design: A sturdy online presence is essential in modern-day virtual international. Aspire IT Solutions makes a speciality of creating responsive and tasty websites that depart an enduring impact and power online success.
E-trade Solutions: For groups trying to project into e-commerce, Aspire IT Solutions provides give up-to-quit e-commerce development services, from putting in on line shops to imposing steady payment gateways.
IT Consulting and Support: With Aspire IT Solutions, agencies have a reliable partner for all their IT desires. Their consulting and support offerings make certain easy operations, green troubleshooting, and strategic generation making plans.
Why Choose Aspire IT Solutions?
Tailored Solutions: One size does not healthy all. Aspire IT Solutions knows this and crafts solutions that are particularly designed to meet your precise commercial enterprise necessities.
Expertise and Experience: With a team of pro professionals, Aspire IT Solutions brings years of experience and information to the desk, ensuring that your initiatives are in successful hands.
Innovation-Driven: Aspire IT Solutions stays at the forefront of technology developments. This way you’ll be taking advantage of the ultra-modern improvements to offer your business a competitive edge.
Proven Track Record: The achievement memories of companies that have transformed with Aspire IT Solutions speak volumes about their dedication to delivering effects.
Conclusion: In a global wherein generation drives enterprise fulfillment, Aspire IT Solutions stands as a beacon of innovation and transformation. Their tailor-made answers, professional team, and willpower to empowering corporations make them the precise accomplice for businesses seeking to not most effective adapt to the virtual generation however thrive in it. Embrace the energy of Aspire IT Solutions and liberate a global of opportunities for your business increase.
For more info visit our website : https://aspireitsolution.com/
4 notes
·
View notes
Text
WILL CONTAINER REPLACE HYPERVISOR
As with the increasing technology, the way data centers operate has changed over the years due to virtualization. Over the years, different software has been launched that has made it easy for companies to manage their data operating center. This allows companies to operate their open-source object storage data through different operating systems together, thereby maximizing their resources and making their data managing work easy and useful for their business.
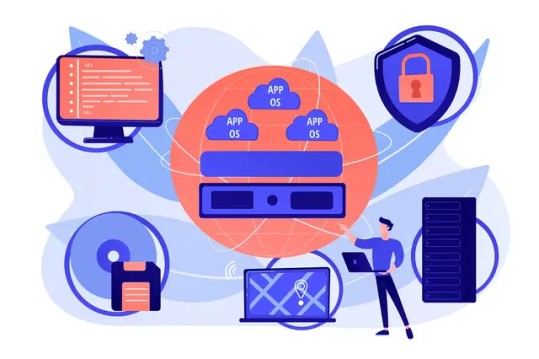
Understanding different technological models to their programming for object storage it requires proper knowledge and understanding of each. The same holds for containers as well as hypervisor which have been in the market for quite a time providing companies with different operating solutions.
Let’s understand how they work
Virtual machines- they work through hypervisor removing hardware system and enabling to run the data operating systems.
Containers- work by extracting operating systems and enable one to run data through applications and they have become more famous recently.

Although container technology has been in use since 2013, it became more engaging after the introduction of Docker. Thereby, it is an open-source object storage platform used for building, deploying and managing containerized applications.
The container’s system always works through the underlying operating system using virtual memory support that provides basic services to all the applications. Whereas hypervisors require their operating system for working properly with the help of hardware support.
Although containers, as well as hypervisors, work differently, have distinct and unique features, both the technologies share some similarities such as improving IT managed service efficiency. The profitability of the applications used and enhancing the lifecycle of software development.
And nowadays, it is becoming a hot topic and there is a lot of discussion going on whether containers will take over and replace hypervisors. This has been becoming of keen interest to many people as some are in favor of containers and some are with hypervisor as both the technologies have some particular properties that can help in solving different solutions.
Let’s discuss in detail and understand their functioning, differences and which one is better in terms of technology?
What are virtual machines?
Virtual machines are software-defined computers that run with the help of cloud hosting software thereby allowing multiple applications to run individually through hardware. They are best suited when one needs to operate different applications without letting them interfere with each other.
As the applications run differently on VMs, all applications will have a different set of hardware, which help companies in reducing the money spent on hardware management.
Virtual machines work with physical computers by using software layers that are light-weighted and are called a hypervisor.
A hypervisor that is used for working virtual machines helps in providing fresh service by separating VMs from one another and then allocating processors, memory and storage among them. This can be used by cloud hosting service providers in increasing their network functioning on nodes that are expensive automatically.
Hypervisors allow host machines to have different operating systems thereby allowing them to operate many virtual machines which leads to the maximum use of their resources such as bandwidth and memory.

What is a container?
Containers are also software-defined computers but they operate through a single host operating system. This means all applications have one operating center that allows it to access from anywhere using any applications such as a laptop, in the cloud etc.
Containers use the operating system (OS) virtualization form, that is they use the host operating system to perform their function. The container includes all the code, dependencies and operating system by itself allowing it to run from anywhere with the help of cloud hosting technology.
They promised methods of implementing infrastructure requirements that were streamlined and can be used as an alternative to virtual machines.
Even though containers are known to improve how cloud platforms was developed and deployed, they are still not as secure as VMs.
The same operating system can run different containers and can share their resources and they further, allow streamlining of implemented infrastructure requirements by the system.
Now as we have understood the working of VMs and containers, let’s see the benefits of both the technologies
Benefits of virtual machines
They allow different operating systems to work in one hardware system that maintains energy costs and rack space to cooling, thereby allowing economical gain in the cloud.
This technology provided by cloud managed services is easier to spin up and down and it is much easier to create backups with this system.
Allowing easy backups and restoring images, it is easy and simple to recover from disaster recovery.
It allows the isolated operating system, hence testing of applications is relatively easy, free and simple.

Benefits of containers:
They are light in weight and hence boost significantly faster as compared to VMs within a few seconds and require hardware and fewer operating systems.
They are portable cloud hosting data centers that can be used to run from anywhere which means the cause of the issue is being reduced.
They enable micro-services that allow easy testing of applications, failures related to the single point are reduced and the velocity related to development is increased.
Let’s see the difference between containers and VMs
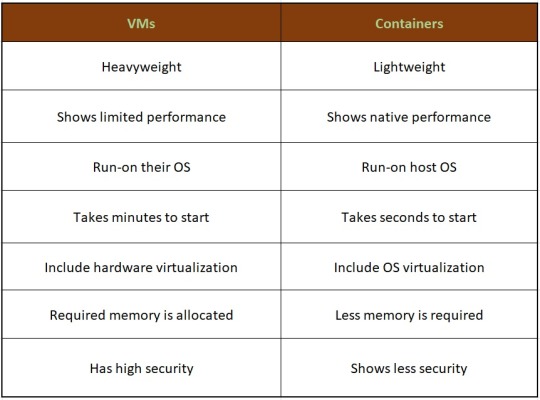
Hence, looking at all these differences one can make out that, containers have added advantage over the old virtualization technology. As containers are faster, more lightweight and easy to manage than VMs and are way beyond these previous technologies in many ways.
In the case of hypervisor, virtualization is performed through physical hardware having a separate operating system that can be run on the same physical carrier. Hence each hardware requires a separate operating system to run an application and its associated libraries.
Whereas containers virtualize operating systems instead of hardware, thereby each container only contains the application, its library and dependencies.
Containers in a similar way to a virtual machine will allow developers to improve the CPU and use physical machines' memory. Containers through their managed service provider further allow microservice architecture, allowing application components to be deployed and scaled more granularly.

As we have seen the benefits and differences between the two technologies, one must know when to use containers and when to use virtual machines, as many people want to use both and some want to use either of them.
Let’s see when to use hypervisor for cases such as:
Many people want to continue with the virtual machines as they are compatible and consistent with their use and shifting to containers is not the case for them.
VMs provide a single computer or cloud hosting server to run multiple applications together which is only required by most people.
As containers run on host operating systems which is not the case with VMs. Hence, for security purposes, containers are not that safe as they can destroy all the applications together. However, in the case of virtual machines as it includes different hardware and belongs to secure cloud software, so only one application will be damaged.
Container’s turn out to be useful in case of,
Containers enable DevOps and microservices as they are portable and fast, taking microseconds to start working.
Nowadays, many web applications are moving towards a microservices architecture that helps in building web applications from managed service providers. The containers help in providing this feature making it easy for updating and redeploying of the part needed of the application.
Containers contain a scalability property that automatically scales containers, reproduces container images and spin them down when they are not needed.
With increasing technology, people want to move to technology that is fast and has speed, containers in this scenario are way faster than a hypervisor. That also enables fast testing and speed recovery of images when a reboot is performed.

Hence, will containers replace hypervisor?
Although both the cloud hosting technologies share some similarities, both are different from each other in one or the other aspect. Hence, it is not easy to conclude. Before making any final thoughts about it, let's see a few points about each.

Still, a question can arise in mind, why containers?
Although, as stated above there are many reasons to still use virtual machines, containers provide flexibility and portability that is increasing its demand in the multi-cloud platform world and the way they allocate their resources.
Still today many companies do not know how to deploy their new applications when installed, hence containerizing applications being flexible allow easy handling of many clouds hosting data center software environments of modern IT technology.
These containers are also useful for automation and DevOps pipelines including continuous integration and continuous development implementation. This means containers having small size and modularity of building it in small parts allows application buildup completely by stacking those parts together.
They not only increase the efficiency of the system and enhance the working of resources but also save money by preferring for operating multiple processes.
They are quicker to boost up as compared to virtual machines that take minutes in boosting and for recovery.
Another important point is that they have a minimalistic structure and do not need a full operating system or any hardware for its functioning and can be installed and removed without disturbing the whole system.
Containers replace the patching process that was used traditionally, thereby allowing many organizations to respond to various issues faster and making it easy for managing applications.
As containers contain an operating system abstract that operates its operating system, the virtualization problem that is being faced in the case of virtual machines is solved as containers have virtual environments that make it easy to operate different operating systems provided by vendor management.
Still, virtual machines are useful to many
Although containers have more advantages as compared to virtual machines, still there are a few disadvantages associated with them such as security issues with containers as they belong to disturbed cloud software.
Hacking a container is easy as they are using single software for operating multiple applications which can allow one to excess whole cloud hosting system if breaching occurs which is not the case with virtual machines as they contain an additional barrier between VM, host server and other virtual machines.
In case the fresh service software gets affected by malware, it spreads to all the applications as it uses a single operating system which is not the case with virtual machines.
People feel more familiar with virtual machines as they are well established in most organizations for a long time and businesses include teams and procedures that manage the working of VMs such as their deployment, backups and monitoring.
Many times, companies prefer working with an organized operating system type of secure cloud software as one machine, especially for applications that are complex to understand.
Conclusion
Concluding this blog, the final thought is that, as we have seen, both the containers and virtual machine cloud hosting technologies are provided with different problem-solving qualities. Containers help in focusing more on building code, creating better software and making applications work on a faster note whereas, with virtual machines, although they are slower, less portable and heavy still people prefer them in provisioning infrastructure for enterprise, running legacy or any monolithic applications.
Stating that, if one wants to operate a full operating system, they should go for hypervisor and if they want to have service from a cloud managed service provider that is lightweight and in a portable manner, one must go for containers.
Hence, it will take time for containers to replace virtual machines as they are still needed by many for running some old-style applications and host multiple operating systems in parallel even though VMs has not had so cloud-native servers. Therefore, it can be said that they are not likely to replace virtual machines as both the technologies complement each other by providing IT managed services instead of replacing each other and both the technologies have a place in the modern data center.
For more insights do visit our website
#container #hypervisor #docker #technology #zybisys #godaddy
6 notes
·
View notes