#week03
Explore tagged Tumblr posts
Text
Week03 - Visual Journal #2

What I love about this painting is the dominant use of yellow throughout the entire piece. As we learned in class this week, colors evoke different emotions and feelings.
Although this piece doesn't have a written statement, we can still conclude that it comes from a place of love and happiness due to the intimate position of the human figures. The color yellow evokes similar positive emotions: happiness, excitement, enthusiasm, confidence, etc.
I also enjoy the use of complimentary colors for the different shades of yellow throughout the painting. Purple and yellow, blue and orange, purple and green. They bounce off of each other quite well!
1 note
·
View note
Text

Top left: WhaleBoi: 8x8_ 4 Shades
Top right: WhaleBoi: 16x16_4 Shades
Bottom left: WhaleBoi: 32x32_4 Colors
Bottom right: WhaleBoi: 32x32_Any Color
Tools: Procreate
A transformed version of my week03 sketch to pixel art.

1 note
·
View note
Text
Pixelizing Monstrosities

Tools: Photoshop, Aseprite
A transformed version of my week03 sketch to pixel art.

0 notes
Text
CTS A | Week03 Emotional Intelligence
In a recent project, my relationship management skills were highlighted when we worked on a team assignment to write and act out a scenario, requiring strong collaboration and open communication. At first, it was awkward, as it was early in the semester and most team members weren’t very interactive. I eased the tension by asking for their thoughts on the task, guiding responses, and inquiring about their interests and relevant experiences. My aim was to foster a supportive, harmonious environment where everyone felt free to share opinions.
Leading open discussions helped us reconcile differing viewpoints, merging them into a unified scenario. This teamwork encouraged creativity and resulted in a well-rounded presentation that reflected diverse ideas. I realized that respecting each other’s input leads to successful collaboration and meaningful outcomes.
While I consider relationship management a strength, self-management is an area for improvement. I often empathize and help others in team settings, which fosters a positive atmosphere, yet I struggle to manage my own workload when balancing multiple tasks. For example, in a recent studio project, I prioritized supporting others’ ideas in our mind map assignment. However, when it came time to prepare my own work, I ran out of time and felt dissatisfied with the results.
Through this, I realized that developing self-management will not only increase my efficiency but will also positively impact both process and output. Moving forward, I aim to incorporate strategies such as time management and goal-setting to balance my work while continuing to develop my relationship management skills.
(253 words)
0 notes
Text
CTS-B | Week03 Connecting Practice with Society
Modern society is in trouble from a variety of environmental and social issues that become increasingly serious. Human rights abuses, poverty, and climate change are just a few of the issues that have impacted our lives. Designers will be crucial in finding answers and creating innovative ideas that tackle these critical issues.
For example, even with the innumerable scientific and technological advances, there are still situations when people might perish from a lack of access to clean water. People who are forced to drink dirty water are deprived of their right to drink clean water. In these situations, they can reclaim their rights with the aid of designers.
The instance explains the use of straw filters to ensure a right to safe water to drink. The LifeStraw was produced to give people living in regions where drinkable water is scarce access across an easily available water filter option. This type of product is an instance of social design, which aims at solving problems connected with public health instead of merely functional designs. Throughout this process, designers create designs that represent social and environmental principles while fusing form and function and taking the user experience into account. To say it simply, they contribute to upholding social responsibility while also considering technical progress and consumer ease. These products offer outstanding examples of design that transcend much beyond their intended function as water filter systems in terms of social effect.








(237 words)
References:
“Can Design Change the World?” Deerdesigner, https://deerdesigner.com/blog/can-design-change-the-world/.
“Mandatory or Voluntary? South Korea’s Dilemma over Regulating Disposables.” The Straitst Times, SPH Media Limited, 7 July 2024, https://www.straitstimes.com/asia/east-asia/mandatory-or-voluntary-south-korea-s-dilemma-over-regulating-disposables.
The Index Project. “Impact Stories: LifeStraw.” The Index Project, 30 Nov. 2020, https://theindexproject.org/post/impact-stories-lifestraw.
Image references:
A cafe owner putting plastic straws out for customers from: THE KOREA HERALD/ASIA NEWS NETWORK, 8 November 2023 https://www.straitstimes.com/asia/east-asia/mandatory-or-voluntary-south-korea-s-dilemma-over-regulating-disposables
A man drinking water by using LifeStraw from: Index Project, 30 November 2020 https://theindexproject.org/post/impact-stories-lifestraw
Cooperative with others in a socitey from: Geeks for Geeks, 30 May 2024 https://www.geeksforgeeks.org/cooperative-society-meaning-features-and-types/
Examples of poster design for social issues or concerns. Left: The body shop’s campaign to end sex trafficking, Right: Amnesty International’s campaign to ban the use of landmines from: thebodyshop.com and amnesty.org, https://deerdesigner.com/blog/can-design-change-the-world/
Solar energy from: Maria Sibirtseva, 28 October 2019 https://blog.depositphotos.com/sustainable-design.html
0 notes
Text
Week 3: Something Awesome Update
Topic: To build a drone with a raspberry pi.
After some advice from Kris, for my something awesome project, I have decided to change from reverse engineering a drone to building a drone.
The skills that will be learnt will be the same:
Understand telemetry
Learn how to use a raspberry pi
Not sure if I have enough time.
Understand the security flaws in drones
Furthermore, other skills that will be learnt would:
Soldering
2 notes
·
View notes
Photo
[Week 03 - Tech Thoughts]
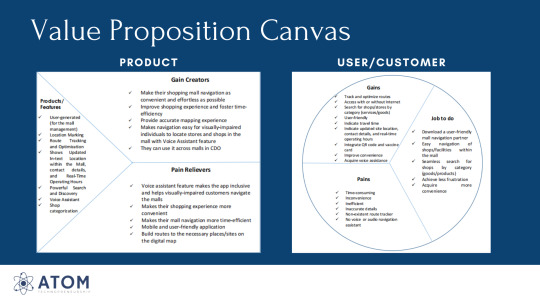
Creating Value Proposition Canvas and Business Template
Engr Marbert Jael headed the plenary class for this week, in which he discussed the importance of creating a value proposition canvas and business template in a startup company.
The discussion was insightful, and I have learned about the process of creating a VPC and business template and the significant role it plays in building a startup company. The Value Proposition Canvas is a business model tool that aids in positioning a company's product or service around the values and demands of its customers. A business model's Value Proposition Canvas is crucial. It aids the company's decision-making and product positioning. It's more than a visual representation of what customers want. Businesses can tailor their strategy to meet the needs of their customers. This can aid in the creation of a product that customers desire.
Creating a value proposition canvas has several advantages:
1. Focused Planning
A Value Proposition Canvas serves as a visual reference. It guarantees a focused approach to creating a high-demand product.
2. Increases the reach of marketing
Launching a new product necessitates a significant amount of marketing and branding effort. It entails informing customers about how purchasing the goods will meet their demands—this aids in creating a solid brand image in customers' eyes. A Value Proposition Canvas is a powerful tool for identifying client needs and developing a plan to address them. With this in place, promotions and advertisements may easily attract the attention of customers.
3. A high level of customer involvement
A Value Proposition Canvas connects the process of identifying and meeting needs. This structure allows you to concentrate on the aspects that clients care about the most. As a result, there is a high level of customer interaction.
4. Easy to use and understand
A Value Proposition Canvas provides a basic summary of the company's operations. Analyzing the product strategy and performance becomes broad while remaining straightforward.
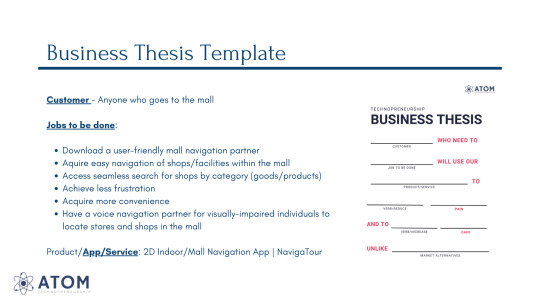
On the other hand, a business thesis template assists businesses in systematically organizing their thoughts and ideas. To define the business goals and how to attain them and identify any potential roadblocks. When the company gets busier, it gives a straightforward approach.
For our startup team, we’ve decided to settle and pursue a mobile application called NavigaTour. NavigaTour is a 2D indoor or mall navigation app that helps customers/tourists seamlessly and conveniently locate areas (shops or facilities) within the mall that they desire to visit.
We conducted an initial interview with ten (10) individuals to assess their needs and help create the user-end of the value propositions canvas and see if their goals, conditions, and desires align with ours. We have identified the gains they want to have, the job they seek to do, and the pains they are encountering. On the product’s end, we concluded that our features, gain creators, and pain relievers are in line with those of our respondents’.
1 note
·
View note
Video
youtube
Paprika by Satoshi Kon (2006)
Paprika is a Japanese animation that explores the concept of a dream device that allows the user to visit and interact with any dreams. However, as the story progresses it reveals the device has been stolen and misused in manipulating people’s perception of dreams and reality. The concept of this dream device represents the idea of Breton’s (1924) definition of the state of “surreality” that combines the conscious and the unconscious. Particularly in this parade scene, the nonsensical random objects contrasting with the city backdrop showcases the merges of the two different states that creates chaos, confusion and questioning of reality. The concept of non-sequiturs as Shaun stated in the week 02 lecture can also be identified in this film to differentiate between the real and unreal.
0 notes
Text
Week03 HW #2 - Remixed Emojis



Remoji_01: Junji Ito inspired cat skull
Remoji_02: Cch-chick pea...? gross... /_\
Remoji_03: Don't f_ck with me.
What went well? - I like the overall composition of my remixed emojis. The little details from the added shadows to the outlined shapes bring out the unique personalities of each emoji.
What was challenging? - Nothing was too hard, but I would like to practice with more colors and layers in the future. I was able to change the colors of selected objects, but I am not sure if I used the most efficient method!
1 note
·
View note
Text
how it feels to play fnf 🎤🔥
#listening to week03 gave me this ideaworm#HAD to be done#friday night funkin#kaguya sama love is war#bardlike
4 notes
·
View notes
Photo

Marketing Quote week 3 2020 “Good content isn’t about good storytelling. It’s about telling a true story well.” - Ann Handley #marketingquote #week03 #quotes #quote #inspiratiequote #jonyc #zzpquote #zelfstandigequote #socialemediaquote #contentquote (bij Rotterdam, Netherlands) https://www.instagram.com/p/B7bmxJUlCQJ/?igshid=196wqjq4inlvi
#marketingquote#week03#quotes#quote#inspiratiequote#jonyc#zzpquote#zelfstandigequote#socialemediaquote#contentquote
0 notes
Text
Week 03: Something Awesome Bandit Game Level 0 - 11
So I’m starting the CTF challenges this week, starting with overthewires bandit game. Starting at 7:30pm
Level 0
First mistake I made was I tried ssh bandit.labs.overthewire.org without the username at the front. I also added it as a trusted host, not sure if that’s bad or not o.O . Great now I know how to ssh into things with username/password/port
Level 0 -> 1
Okay I used ls and found a file called readme. I used cat readme to get the password for level 1. I can’t seem to paste into powershell? Ctrl V works on a clean powershell where I can see what I’m pasting, but I keep getting permission denied error. Okay I’m just going to manually type in the password. Finished at 7:48pm
Level 1 -> 2
Okay so there’s a file called “-”, I can’t cat the file normally like cat -. Okay I found it, you have to do cat ./- to see it. I have the password but I still haven’t managed to figure out how to paste the password in. I’ll just manually type in the password again. Finished at 7:54pm
Level 2 -> 3
I just did cat “spaces in this filename”, and it worked fine. Still can’t paste the password in. Update 8:16pm, I finally got it to work. I switched to windows cmd, right clicking pastes the password in, and it actually works!
Level 3 -> 4
Okay I used cd inhere to move directories to the inhere folder. I used man ls to find all commands for ls, and I’ve tried out ls -a to show all files, even hidden ones. I think the files called .hidden? Yes, cat.hidden gives the password
Level 4 -> 5
So there’s 10 files in here, but only one of them is readable. At first I tried cat -file01 but that doesn’t work because of the dash in the filename. I looked at man find and found a -readable option but that didn’t help. I settled with just going through them one by one i.e. cat ./-file00 ... ./-file01 until I found the password in file07. Finished 8:26pm
Level 5 -> 6
Okay, so there’s a bunch of files, and we need the one that is human readable, 1033 bytes in size and not executable. Going through man find, I’ve found
-readable
-executable
-size n [units, we’ll need c for bytes]
So let’s try find -readable -!executable -size1033c
Okay I just guessed the -!executable, guess that’s not how you’re supposed to do the opposite of something. I took it out and I found one file ./maybehere07/.file2.
Yep I’ve found the password, finished 8:33pm. It’s been an hour I’ll take a break.
Level 6 -> 7
Starting at 9:20pm
Need to find the file that satisfies, owned by user bandit7, owned by bandit6, 33 bytes in size. Okay so using man find again, I think i’ve found the right options.
find -group bandit6 -user bandit7 -size33c
Doesn’t work though, I think the key phrase is “stored somewhere on the server”
Yeah, find by itself will only look at the current directory, and I think any subdirectories.
I did a google search, and found that I should be using find / [conditions], but I got back a ton of permission denied errors, I hope I didn’t do anything wrong
After messing around some more with
find / -group bandit6 -user bandit7 -size 33c
I noticed that among the many many permission denied messages that I got I did see
/var/lib/dpkg/info/bandit7.password
So I did cat /var/lib/dpkg/info/bandit7.password, and yet I found the password
Not sure if this is how you’re supposed to do it though :/
Level 7 -> 8
data.txt is filled with text, password is next to the word millionth
I did 2041 last year, but damn I’ve already forgotten so much about grep and regex.
Okay cool, I got it quickly, cat data.txt | grep millionth. Finished 9:44pm
Level 8 -> 9
Find the only unique key in data.txt
Aha got it, cat data.txt | sort | uniq.-c
Most of the keys have a count of 10 next to them, only one key has 1 next to them i.e. the unique key
Finished 9:49pm
Level 9 -> 10
Okay so the first issue, when I tried using grep it’d always spit out binary file data.txt matches and nothing more. I tried something like cat data.txt | egrep -a ‘=‘, I can see in the mess that comes out ===== password but nothing more.
Aha, I was googling how to grep text in binary file. An answer said to pipe it though strings which strips all binary code leaving just text.
So I tried cat data.txt | strings and I found the password! Finished 10:03pm
Level 10 -> 11
Okay so password is encoded in data.txt as base64
I tried cat data.txt | base64 but I don’t think that’s the password
Ok, looking at man base64, there’s a command -d for decoding
cat data.txt | base64 -d got me the password
Finished 10:07pm
Level 11 -> 12
Need to decrypt the password by rotating all letters forward 13?
Alright I think tr will work here
Maybe something like cat data.txt | tr [n-m] [a-z] ??
Doesn’t work
Maybe cat data.txt |tr [n-m] [a-z] | tr [N-M] [A-Z] ??
Oh, it’s saying that n is greater than m, so it should be m-n?
Okay I googled rot13 and looking at the diagram I’ve got it all wrong. After messing around for a bit, I found something that works. I highly doubt it’s the best way to solve it though
cat data.txt | tr [n-za-m] [a-mn-z] | tr [N-ZA-M] [A-MN-Z]
Got the password nevertheless though! Finished 10:25pm
I think I’ll stop here for today
Reflection
So what did I learn, going through the first 11 games of bandit.
commands like ls/cat I’m quite familiar with
I got to refresh my memory of some instances of grep/tr
I learnt about decrypting base64 files and to filter out binary text with the strings command. Also about the various options of the find command.
I had a blast playing these levels, I was nervous to start though because of the idea of ssh’ing in.
0 notes
Text
Week 3: Security Everywhere - TCP SACK Vulnerability
When a TCP connection takes place between a client and a server, the server sends TCP packets separated into different segments. This is sent to the client but in some cases, packets may be dropped and never reaching the client. Previously, if the first segment is received and the remaining are out of order or some are dropped, the client will only acknowledge the first packet and therefore the server will have to resend the rest, ultimately this is quite ineffective and inefficient.
Selective Acknowledgements (SACK) assisted in solving this issue, where it appended packets that have been received to the acknowledgement packet. It then allows the server to transmit packets that have not been received by the client.
Netflix’s Information Security team have discovered four security flaws in Linux and FreeBSD systems which can allow attackers to remotely crash or slow down servers.
1. The most serious vulnerability is SACK Panic; an attacker can remotely send a specific sequence of TCP Selective Acknowledgments causing an integer overflow leading to a kernel panic in the system. In this case, it was the number 17, once SACK overflowed it led to the kernel to panic.
2. SACK Slowness
3. SACK Slowness
4. Excess Resource Consumption
Reference: https://github.com/Netflix/security-bulletins/blob/master/advisories/third-party/2019-001.md
0 notes
Photo

culmination project of masks, clip masking, and spot healing
0 notes
Text
The first storyboard and simple VR scene
I used the Tiltbrush to finish my storyboard.
My inspiration came from the BBC television--Merlin. The storyboard uses the plot that King Arthur went out to find one of Knights of the Round Table accompanied with Merlin, when they come to a valley, they found a dead village, and in the hole of the rock mountain. A dying wizard was waiting for Merlin to tell him a terrible prediction about King Arthur. Confused Merlin summon his old giant dragon to light him.
This storyboard like a story or also it like a game. I want to build a beautiful valley, at the same time there is a growing crisis, make people pay there attention in this environment and full of curious to this environment.
At the time of building the scene, I find it is difficult for me to draw by myself. Then I have used many templates Tiltbrush offered. Then I finished a simple scene according to my idea.
In our homework, I continually worked to realize my storyboard. But many problems following, just like how can I use two or three landscape to build the work, how I make the characters. So I just did what a beginner can do in this assignment. I think I can work on it in the following weeks.
youtube

0 notes
Video
vimeo
Toto Forever by Max Siedentopf
This sound installation is located in the Namib desert, in Southern Africa that plays Toto’s ‘Africa’ in an infinite loop. The setup of the equipment including the MP3 player and the speakers are solar-powered and allow the song to perform a never-ending concert to a landscape of nothingness. The comedic choice of music considering the location mixed with the undisclosed whereabouts of the installation creates a juxtaposition of distant realities, a surreal commentary on post-modern music consumption all whilst providing someone how may stumble across it with a surreal listening experience.
1 note
·
View note