Don't wanna be here? Send us removal request.
Text
Key Differences Between DeepSeek AI and ChatGPT
Choosing the right AI model? Here’s a detailed comparison to help you decide.

Conclusion Understanding these differences can help users choose the right AI model based on their specific needs—whether that’s technical precision with DeepSeek AI or engaging conversational interactions with ChatGPT.
#DeepSeek AI#ChatGPT#AI Comparison#Natural Language Processing#AI Models#Machine Learning#Artificial Intelligence#Technical AI#Conversational AI#Open Source AI#Freemium AI#AI Architecture#Content Moderation#AI Performance#AI Capabilities#AI Cost#Deep Learning#AI Technology#MoE Architecture#Transformer Models
0 notes
Text
The Future of Tech Startups and Venture Capital: Trends to Watch in 2025
The tech startup ecosystem is constantly evolving, and venture capital is at the forefront of this transformation. Here are the top trends shaping the future of tech startups and VC funding in 2025.

Staying ahead of these trends can help your startup attract funding and thrive in a competitive market.
0 notes
Text
Advantages of Integrating OpenAI's O3 Model into agentic workflows
Integrating OpenAI's O3 Model into agentic workflows offers significant advantages that enhance efficiency and productivity. From accurate code generation to superior reasoning capabilities, O3 empowers teams to streamline processes and focus on strategic initiatives. Read More About OpenAI's O3 Model

#OpenAI#O3Model#ArtificialIntelligence#MachineLearning#AIGeneralIntelligence#DeepLearning#AIResearch#TechInnovation#Coding#DataScience#AIApplications#FutureOfWork#Automation#AIReasoning#DigitalTransformation#SmartTechnology
0 notes
Text
Four Common Types of NoSQL Databases
NoSQL databases are categorized into four primary types, each designed to address specific data storage and retrieval needs. Read More

#NoSQL#DatabaseTechnology#DataManagement#BigData#DataStorage#TechTrends#CloudComputing#DataAnalytics#DigitalTransformation#DatabaseSolutions#DataModeling
0 notes
Text
Which is better Open AI Sora or Google Veo 2?
Google Veo 2 and OpenAI Sora are prominent AI video generation tools with distinct features. This comparison highlights their differences in video quality, realism in motion, content duration, target audience, and editing capabilities. Read More

#AIVideoCreation#VideoEditing#GoogleVeo2#OpenAISora#AIVideoTools#ContentCreation#CreativeEditing#TechComparison#DigitalContent#VideoMarketing#AIInMedia#VideoTechnology#ContentCreators
0 notes
Text
Effective Recruitment Strategies for VMware Engineers
To successfully recruit VMware engineers, consider implementing the following strategies: Read More
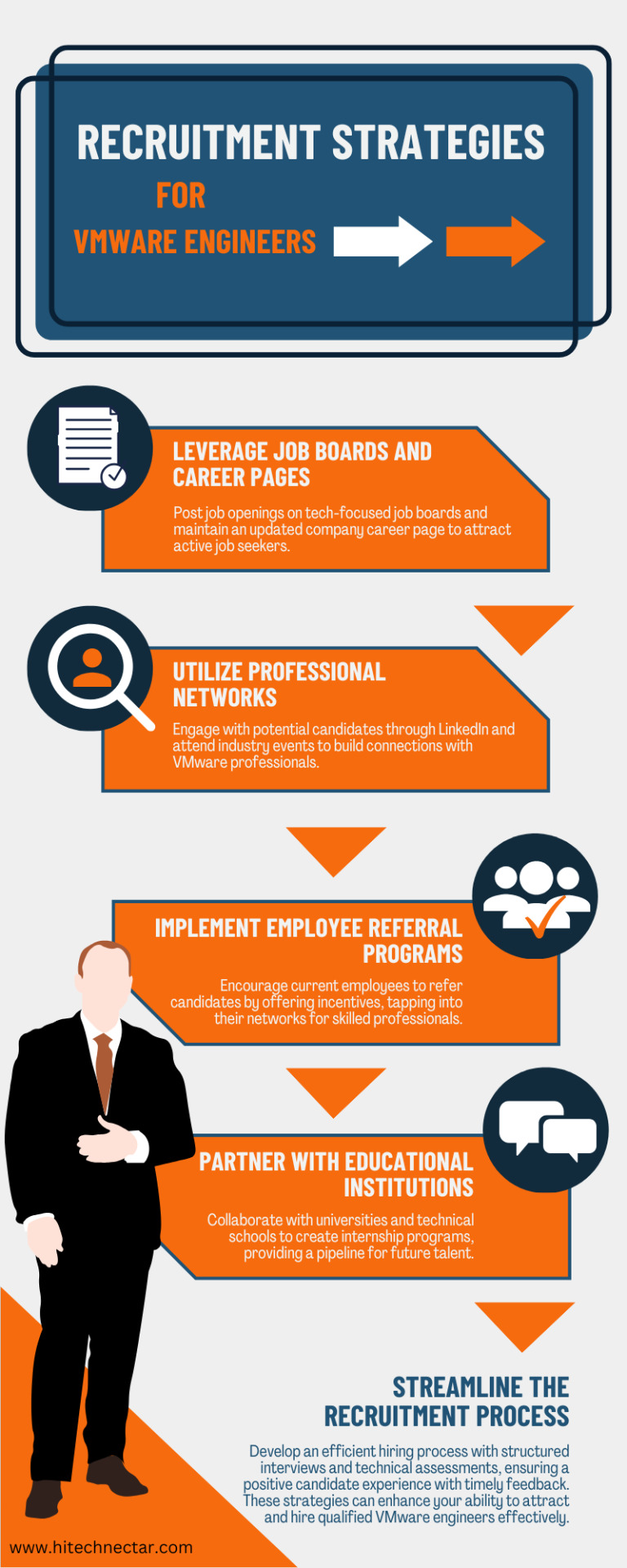
#VMware#RecruitmentStrategies#TechHiring#ITJobs#VMwareEngineers#TalentAcquisition#HiringTips#JobSearch#Virtualization#EmployeeReferrals#TechTalent#CareerOpportunities#JobBoards#ProfessionalNetworking#SourcingCandidates#RecruitmentProcess#HiringTrends#WorkplaceCulture#EngineeringJobs#CloudComputing
0 notes
Text
Top 5 Benefits of Remote Monitoring Systems
Remote Monitoring Systems (RMS) are transforming the way industries operate by providing real-time insights and control over equipment and processes. Here are the top five benefits that make RMS an essential tool for businesses looking to enhance their operations: Read More

0 notes
Text
How can organizations balance risk and reward when adopting Generative AI
Organizations can balance risk and reward when adopting Generative AI (GenAI) by implementing a strategic approach that emphasizes due diligence, ethical frameworks, and robust governance. Here are key strategies to achieve this balance:
#generative ai#risk management#ai governance#ethical ai#data security#compliance#ai strategy#innovation#ai ethics
0 notes
Text
5 methods of Instructional Design and Delivery for Employee Training
Explore five effective methods for designing and delivering employee onboarding and training. These approaches enhance learning experiences, improve engagement, and ensure skill development in the workplace.

#EmployeeOnboarding#NewHire#OnboardingProcess#WorkplaceIntegration#EmployeeExperience#HRBestPractices#EmployeeTraining#CompanyCulture#WelcomeNewEmployees#TalentManagement#OnboardingBestPractices#EmployeeEngagement#NewEmployeeOrientation#WorkplaceSuccess#HRStrategies
0 notes
Text
Zoom's Timeline: A Journey of Innovation and Growth
Zoom's journey from a startup to a leading video conferencing platform is marked by key milestones that highlight its rapid growth and innovation. Here’s a brief timeline of significant events in Zoom's history:

Zoom's evolution showcases its commitment to innovation and adaptability in the ever-changing landscape of digital communication.
0 notes
Text
Will Power BI Work on a Mac? Exploring Compatibility and Alternatives
If you're a Mac user interested in using Power BI, you might be wondering about its compatibility with macOS. Unfortunately, Microsoft Power BI Desktop is not natively supported on Mac systems. However, there are several workarounds that enable you to access this powerful business intelligence tool on your Mac.

Here’s a quick overview of your options:
Use Power BI Service via Web Browser The simplest way to use Power BI on a Mac is through the Power BI Service, which is accessible via any modern web browser. Just sign up for an account, and you can create reports and dashboards directly online without needing any additional software.
Run Power BI on a Virtual Machine You can install Windows on your Mac using virtualization software like Parallels Desktop or VMware Fusion. This allows you to run Windows applications, including Power BI Desktop, seamlessly alongside macOS.
Boot Camp Apple's Boot Camp Assistant lets you install Windows on your Mac, enabling you to switch between macOS and Windows. This method provides better performance since it runs Windows natively on your hardware.
Remote Access to a Windows PC If you have access to a Windows PC, you can install Power BI there and use remote desktop applications like Microsoft Remote Desktop, TeamViewer, or AnyDesk to access it from your Mac.
Consider Alternatives If these options seem cumbersome, you might explore alternative business intelligence tools that are compatible with macOS, such as Holistics or Looker, which offer similar functionalities without the need for Windows.
In conclusion, while Power BI does not directly support macOS, these alternatives allow you to leverage its capabilities effectively. Whether through web access or running Windows on your Mac, you can still harness the power of Power BI for your data analysis needs!
0 notes
Text
Top 10 Essential Tools for Effective Remote Team Collaboration
Effective remote team collaboration is essential for maintaining productivity and communication in a distributed work environment. With the right tools, teams can streamline their workflows, enhance communication, and foster a sense of connection. Discover how technology is transforming collaboration, productivity, and the overall workplace experience! Click here "Remote Work Technology – Redefining How We Connect and Collaborate"
Here’s a look at the top 10 essential tools for effective remote team collaboration.

Slack: Slack is a messaging platform that allows teams to communicate in real-time through channels and direct messages. It supports file sharing and integrates with numerous other tools, making it ideal for keeping conversations organized and efficient.
Zoom: Zoom is a leading video conferencing tool that enables virtual meetings with features like screen sharing, breakout rooms, and recording capabilities. It’s perfect for team meetings, webinars, and one-on-one check-ins.
Asana: Asana is a project management tool that helps teams organize tasks and projects visually. Users can create lists, boards, and timelines to track progress and ensure everyone is aligned on goals.
Trello: Trello uses a card-based system to help teams manage projects visually. It allows users to create boards for different projects and move tasks through various stages, providing a clear overview of project status.
Google Workspace: Google Workspace (formerly G Suite) offers a suite of productivity tools including Google Docs, Sheets, and Drive. These applications enable real-time collaboration on documents and easy file sharing among team members.
Microsoft Teams: Microsoft Teams combines chat, video conferencing, and file collaboration in one platform. It’s particularly beneficial for organizations already using Microsoft Office products, allowing seamless integration across tools.
Basecamp: Basecamp is an all-in-one project management tool that helps teams organize tasks, share files, and communicate effectively. It provides to-do lists, message boards, and schedules to keep everyone on track.
Dropbox: Dropbox is a cloud storage service that allows teams to store and share files easily. Its user-friendly interface makes it simple to collaborate on documents while ensuring data security.
Loom: Loom is a video messaging tool that allows users to record their screens or themselves to share quick updates or tutorials. This asynchronous communication tool helps reduce the need for meetings while providing clear instructions.
ClickUp: ClickUp is a versatile project management tool that offers features for task management, goal tracking, and document sharing. Its customizable interface allows teams to tailor their workspace according to their needs.
These tools are designed to enhance collaboration among remote teams by improving communication, organization, and productivity. By integrating these technologies into daily workflows, teams can work more efficiently and maintain strong connections regardless of their physical locations.
#remote work#online work#technology#team management#communication#organization#chatbots#planning#tools#programs#productivity
0 notes
Text
What is Enterprise Architecture (EA)?
Enterprise Architecture (EA) is a strategic framework that provides a comprehensive view of an organization's structure and operations. It aligns business processes, information systems, and technology to support the organization’s goals and objectives. EA serves as a blueprint, documenting current IT assets and processes while guiding the transition to a desired future state.

At its core, enterprise architecture identifies how various components—such as applications, data, and technology—interconnect and interact within the organization. This holistic approach enables organizations to understand their capabilities, optimize resources, and respond effectively to changes in the business environment. The importance of EA lies in its ability to bridge the gap between IT and business strategies. By providing a common language and framework, it facilitates better communication among stakeholders, ensuring that technology investments align with business priorities. Additionally, EA helps organizations identify gaps and inefficiencies in their operations, paving the way for innovation and improved performance. In summary, enterprise architecture is essential for organizations looking to navigate complex environments, drive digital transformation, and achieve long-term success.
0 notes
Text
What are the main security updates in WordPress 6.7
WordPress 6.7 includes several important security updates aimed at enhancing the protection of websites.

Here are the main security enhancements: Restricted Modification Permissions: This update limits modification permissions to admin users only, reducing the risk of unauthorized changes that could compromise site integrity.
Stronger Protection Against Common Attacks: WordPress 6.7 improves defenses against vulnerabilities like cross-site scripting (XSS) and SQL injection attacks, helping to safeguard sensitive data and maintain site security.
Advanced Authentication Mechanisms: The release incorporates more robust authentication methods to protect against various security threats, ensuring that only authorized users can access critical areas of the site.
These updates collectively enhance the overall security posture of WordPress sites, making version 6.7 a significant step forward in protecting user data and maintaining site reliability.
0 notes
Text
10 Best Use Cases of AI in E-Commerce
Artificial intelligence (AI) is revolutionizing the e-commerce industry by enhancing customer experiences, optimizing operations, and driving sales growth. Here are the ten best use cases of AI in e-commerce that are shaping the future of online shopping:

Personalized Product Recommendations AI analyzes customer data, including browsing history and purchase behavior, to provide personalized product recommendations. This enhances the shopping experience by suggesting items that align with individual preferences, leading to increased conversion rates. For instance, Amazon’s recommendation engine significantly contributes to its sales.
Chatbots and Virtual Assistants AI-powered chatbots offer 24/7 customer support, answering queries and assisting with purchases in real time. Brands like Sephora use chatbots to guide customers through product selections and provide styling advice, improving customer satisfaction while reducing the workload on human agents.
Dynamic Pricing AI enables dynamic pricing strategies that adjust prices based on real-time market conditions, competitor pricing, and customer behavior. This allows retailers to optimize their pricing for maximum profitability while remaining competitive in the market.
Inventory Management and Demand Forecasting AI algorithms predict demand trends by analyzing historical sales data, helping businesses manage inventory efficiently. This reduces costs associated with overstocking or stockouts and ensures that popular products are always available.
Visual Search Technology AI-powered visual search allows customers to upload images to find similar products online. This technology enhances product discovery and caters to customers who may not know the exact keywords to use in a search.
Enhanced Customer Segmentation AI helps businesses analyze customer data to create detailed customer segments based on purchasing behavior and preferences. This allows for targeted marketing strategies that resonate with specific groups, improving engagement and conversion rates.
Fraud Detection and Prevention AI systems monitor transactions for unusual patterns that may indicate fraudulent activity. By using machine learning algorithms, e-commerce platforms can detect and prevent fraud in real time, protecting both businesses and consumers.
Automated Marketing Campaigns AI can automate marketing efforts by analyzing customer data to create personalized email campaigns and targeted advertisements. This ensures that marketing messages are relevant and timely, leading to higher engagement rates.
Voice Commerce With the rise of voice-activated devices, AI enables voice commerce capabilities that allow customers to make purchases using voice commands. Retailers like Walmart have integrated voice shopping features with Google Assistant, making the shopping experience more convenient.
Predictive Analytics for Customer Insights AI leverages predictive analytics to provide insights into future customer behavior based on historical data. This helps businesses make informed decisions regarding inventory management, marketing strategies, and product development. Conclusion The integration of AI in e-commerce is transforming how businesses operate and interact with customers. By leveraging these use cases, e-commerce companies can enhance efficiency, improve customer satisfaction, and drive growth in an increasingly competitive landscape.
#ai#artificial intelligence#ecommerce#chatbots#ai technology#business#marketing#visual search#success#branding
0 notes
Text
What is Bluesky Social Used For?

Bluesky Social is a decentralized social media platform designed to provide users with a more user-friendly and autonomous online experience. Built on the AT Protocol, Bluesky allows individuals to share short messages, images, and videos while engaging in discussions with a community that values openness and creativity. Unlike traditional social media platforms, Bluesky emphasizes user control over content and data, making it an attractive alternative for those seeking a more personalized social media experience.
Users can utilize Bluesky to connect with friends, follow interests, and discover new content without the overwhelming influence of algorithms that prioritize engagement over user satisfaction. The platform features a chronological feed, enabling users to see posts from accounts they follow in real-time. Additionally, Bluesky fosters a friendlier atmosphere, free from advertisements and excessive moderation, making it an appealing space for sharing ideas and engaging in meaningful conversations. Explore more about Bluesky Social and its unique features>> Here
0 notes
Text
What Are Zero Trust Principles?
In today’s cybersecurity landscape, Zero Trust Architecture (ZTA) is essential for protecting sensitive data against evolving threats. At its core, Zero Trust operates on the principle of "never trust, always verify." Here are the key principles that define this approach:

1. Verify Identity and Access
Always authenticate users and devices before granting access. Implementing multi-factor authentication (MFA) ensures that only authorized individuals can access sensitive resources.
2. Least Privilege Access
Users should have the minimum level of access necessary for their roles. This limits potential damage from compromised accounts and insider threats.
3. Micro-Segmentation
Divide the network into smaller segments to enforce strict security policies. This containment strategy helps prevent lateral movement by attackers within the network.
4. Continuous Monitoring and Analytics
Employ real-time monitoring and analytics to detect anomalies in user behavior and network traffic, enabling swift incident response.
5. Assume Breach
Operate under the assumption that a breach may occur. This proactive mindset helps organizations prepare for and respond to security incidents effectively.
6. Secure All Endpoints
Ensure all devices accessing the network are secure and compliant with security policies, utilizing endpoint detection and response (EDR) solutions.
Best Zero Trust Vendors:
To implement Zero Trust effectively, consider leading vendors: For more insights on these vendors, check out on Best Zero Trust Vendors.
Adopting Zero Trust principles is crucial for enhancing cybersecurity in an increasingly complex digital landscape. By implementing these strategies, organizations can better protect their data and systems against potential breaches.
#zero trust#cybersecurity#informationsecurity#dataprotection#networksecurity#identitymanagement#accesscontrol#microsegmentation#continuousmonitoring#cyberthreats#itsecurity#endpoint security
0 notes