#Access Control as a Service
Explore tagged Tumblr posts
Text
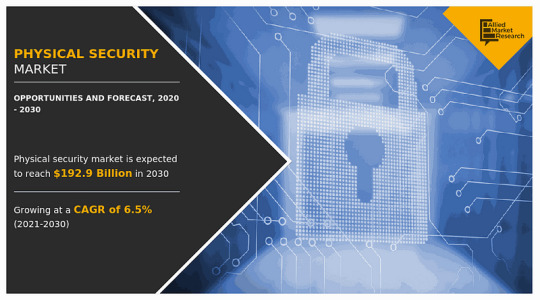
Physical Security Market is booming worldwide with Leading Key Players
According to a new report published by Allied Market Research, titled, “Physical Security Market,” The physical security market size was valued at $104.6 billion in 2020, and is estimated to reach $192.9 billion by 2030, growing at a CAGR of 6.5% from 2021 to 2030.
Physical security is a component of a wider security strategy. Security experts agree that the three most important components of a physical security plan are access control, surveillance, and security testing, which work together to make any space more secure. Access control may start at the outer edge of a security perimeter, which one should establish early in the process. Users can use fencing and video surveillance to monitor access to the facility and secure the outdoor area, especially if they have on-site parking or other outside resources. Furthermore, growth in the number in terror attacks and growing awareness boost the growth of the global physical security market. In addition, growth in technological advancements also positively impacts the growth of the market. However, privacy concerns and lack of physical and logical security integration hamper the market growth. On the contrary, increase in demand for physical security in smart cities is expected to offer remunerative opportunities for expansion of the market during the forecast period.
Depending on industry vertical, IT and telecom segment holds the largest physical security market share as telecommunications industry is facing one of the biggest challenges for managing their networks of base stations. Thus, to properly handle their network issues and to increase the security of telecom operator companies are adopting physical security solutions which is enhancing the growth of the market. However, BFSI segment is expected to witness growth at the highest rate during the forecast period, with the implementation of highly advanced technologies into financial infrastructure, physical security has become an integral part of the BFSI industry. The key drivers of the physical security market in BFSI includes regulatory safety standards’ compliance, risk of data loss, and increase in the adoption of cloud security solutions at data centers, ATMs, corporate buildings, and cash depots.
Region-wise, the physical security market was dominated by North America in 2020 and is the home to major players offering advanced solutions in the physical security market. In addition, increase in security measures across various industry verticals, such as commercial, transportation, government, and others owing to high terrorism incidences in the region, are expected to drive the growth of the market during the forecast period.
However, Asia-Pacific is expected to witness significant growth during the forecast period, owing to the prominent government and police initiatives to enhance physical security software owing to the increase in crime rate. Factors such as increase in insider threats and physical attacks pose great risks on critical infrastructure zones, particularly in developing countries, such as China and India.
Inquiry Before Buying: https://www.alliedmarketresearch.com/purchase-enquiry/2231
With the outbreak of COVID-19, it is challenging to put new tools in place to mitigate risk going forward. Now is a good time to consider updating access control to a more modern, future-proofed system that can still be effective, even if 90% of the office is working remotely. Therefore, it also affected the physical security market growth.
KEY FINDINGS OF THE STUDY
By component, the services segment accounted for the largest physical security market share in 2020.
By region, North America generated highest revenue in 2020 in physical security industry
By enterprise size, large enterprise segment is expected to generate more revenue in the physical security market forecast in 2020.
The key players that operate in the physical security market analysis are ADT Inc., BAE Systems, Cisco system Inc., Genetec Inc., HONEYWELL INTERNATIONAL, INC., Johnson Controls, PELCO corporation, Robert Bosch GmbH, STANLEY CONVERGENT SECURITY SOLUTIONS, INC., and Senstar Corporation. These players have adopted various strategies to increase their market penetration and strengthen their position in the physical security industry.
About Us: Allied Market Research (AMR) is a full-service market research and business-consulting wing of Allied Analytics LLP based in Portland, Oregon. Allied Market Research provides global enterprises as well as medium and small businesses with unmatched quality of “Market Research Reports Insights” and “Business Intelligence Solutions.” AMR has a targeted view to provide business insights and consulting to assist its clients to make strategic business decisions and achieve sustainable growth in their respective market domain.
#Physical Security Market#Physical Security Industry#Physical Security#Infrastructure & Network Security#Access Control as a Service#Video Surveillance as a Service
0 notes
Text
Jason ought to be stubbornly analog where Tim is enthusiastically digital. Tim is impossible to hack because he is very much up to date and on top of cybersecurity. Jason is impossible to hack because you can’t hack a shovel.
#there’s two kinds of very digitally literate people#Babs lives in the digital world#but also she refused the chip implant bc she Doesn’t Trust Like That#it’ll be a cold day in hell before a subscription service controls her access to her own body#jason todd#headcanon
725 notes
·
View notes
Text
Locksmith TX The Woodlands
We are the affordable mobile locksmith in your area, providing 24/7 service with quick, low cost and effective locksmith care! From the day we started providing service our goal was clear, to excel and exceed the standards of excellence for locksmiths! When looking for dependable residential, automotive and commercial locksmiths our skilled services will leave you satisfied! With 24 hour availability our locksmith experts are here to give the best in assistance in the The Woodlands, MA and surrounding areas. We only give honest and dependable answers to all of your locksmith needs whether you need residential, vehicle or commercial locksmith care. We are here to assist you day and night, everyday and holidays to meet your locksmith needs!
Our Services: Security Door Locks Home Security Lockout Service High Security Locks Commercial Door Locks Access Control Systems Lost car key Replacement Car Key Locksmith Lost car Keys Key Duplication
(346) 439- 2474 7 Switchbud Pl, The Woodlands, TX, 77380 Mon - Fri: 08:00am - 08:00pm & Sat - Sun: 09:00am - 05:00pm 24 Emergency Locksmith

#Security Door Locks#Home Security#Lockout Service#High Security Locks#Commercial Door Locks#Access Control Systems#Lost car key Replacement#Car Key Locksmith#Lost car Keys#Key Duplication
3 notes
·
View notes
Text
I don't know I'm not done talking about it. It's insane that I can't just uninstall Edge or Copilot. That websites require my phone number to sign up. That people share their contacts to find their friends on social media.
I wouldn't use an adblocker if ads were just banners on the side funding a website I enjoy using and want to support. Ads pop up invasively and fill my whole screen, I misclick and get warped away to another page just for trying to read an article or get a recipe.
Every app shouldn't be like every other app. Instagram didn't need reels and a shop. TikTok doesn't need a store. Instagram doesn't need to be connected to Facebook. I don't want my apps to do everything, I want a hub for a specific thing, and I'll go to that place accordingly.
I love discord, but so much information gets lost to it. I don't want to join to view things. I want to lurk on forums. I want to be a user who can log in and join a conversation by replying to a thread, even if that conversation was two days ago. I know discord has threads, it's not the same. I don't want to have to verify my account with a phone number. I understand safety and digital concerns, but I'm concerned about information like that with leaks everywhere, even with password managers.
I shouldn't have to pay subscriptions to use services and get locked out of old versions. My old disk copy of photoshop should work. I should want to upgrade eventually because I like photoshop and supporting the business. Adobe is a whole other can of worms here.
Streaming is so splintered across everything. Shows release so fast. Things don't get physical releases. I can't stream a movie I own digitally to friends because the share-screen blocks it, even though I own two digital copies, even though I own a physical copy.
I have an iPod, and I had to install a third party OS to easily put my music on it without having to tangle with iTunes. Spotify bricked hardware I purchased because they were unwillingly to upkeep it. They don't pay their artists. iTunes isn't even iTunes anymore and Apple struggles to upkeep it.
My TV shows me ads on the home screen. My dad lost access to eBook he purchased because they were digital and got revoked by the company distributing them. Hitman 1-3 only runs online most of the time. Flash died and is staying alive because people love it and made efforts to keep it up.
I have to click "not now" and can't click "no". I don't just get emails, they want to text me to purchase things online too. My windows start search bar searches online, not just my computer. Everything is blindly called an app now. Everything wants me to upload to the cloud. These are good tools! But why am I forced to use them! Why am I not allowed to own or control them?
No more!!!!! I love my iPod with so much storage and FLAC files. I love having all my fics on my harddrive. I love having USBs and backups. I love running scripts to gut suck stuff out of my Windows computer I don't want that spies on me. I love having forums. I love sending letters. I love neocities and webpages and webrings. I will not be scanning QR codes. Please hand me a physical menu. If I didn't need a smartphone for work I'd get a "dumb" phone so fast. I want things to have buttons. I want to use a mouse. I want replaceable batteries. I want the right to repair. I grew up online and I won't forget how it was!
70K notes
·
View notes
Text
Purpose of Access Control Systems in Los Angeles and Glendale, CA
Obtaining speedy and requisite help during an emergency is essential. Unfortunately, the public numbers may fail, and the responses may not be as desired. This makes it necessary for residents and employees at various workplaces to use alarm monitoring services in Los Angeles and Long Beach, CA. It is interesting that the services connect all home and/or business alarm systems to a central monitoring point. The skilled and trained professionals at such stations receive alerts from individuals or business entities, verify them, and then dispatch help as and when required. This kind of service has gained popularity lately, with more homeowners relying on it. Some of the specific components of the system need to be checked and informed about before deciding to go with it. The services ensure the following: -
Central Monitoring Station (CMS)—This facility is dedicated to receiving and monitoring alerts. Multiple trained professionals handle the facility who are knowledgeable enough to check the alerts and decide on their seriousness.
Verification—The primary task of setting up this system is to connect all the alarm systems in the hose/workplace to the central monitoring system. Once an alarm is triggered, the signal is forwarded to the CMA. The trained staff at the CMS are equipped to check and verify each alert, thus differentiating between false alerts and genuine ones.
Response- The trained personnel at the CMS may decide on a legitimate alert. They will take the initiative to dispatch the required service providers at the spot of trouble. The CMS may send firefighters, police, and/or other emergency service providers without failing the people in need. Connected Security Systems—Alarm monitoring may be done for several connected systems, with security alarms, burglar alarms, fire alarms, video surveillance systems, and even medical alerts directed to the CMS, which ensures immediate response and assistance as required.
There are multiple advantages of utilizing a centralized monitoring system to ensure the safety and security of the users. Some of the most appreciated benefits of such a monitoring system include the following: -
Improved Security- With 24/7 monitoring of the assorted systems, the users are happy to have their premises under constant surveillance, ensuring their protection regardless of whether the individuals are physically present within the property or not.
Speedy Response- The CMS is entrusted to immediately dispatch the required emergency services. This lessens damage and ensures protection as needed.
Deterring Crimes—Visible security systems such as CCTVs, alarm systems, and burglar alarms are sure to scare potential miscreants off. Constant monitoring can prevent all criminal activities, thus ensuring the prevention of crime to a great extent.
Insurance Benefits—Insurance companies are sure to be satisfied with protecting the concerned property when multiple security systems and a connection to the CMS are installed. As the possibility of potential crimes is lower, insurance companies are happy to provide premiums at a reduced rate.
Business entities are pleased to opt for access control systems in Los Angeles and Glendale, CA, that eliminate the need for physical keys.
#alarm monitoring services in Los Angeles and Long Beach#CA#access control systems in Los Angeles and Glendale
0 notes
Text

Sevenlines Link Security Systems LLC is a leading CCTV company in Dubai, offering advanced surveillance solutions tailored to residential, commercial, and industrial needs. Recognized as one of the top CCTV companies in Dubai, we specialize in providing high-quality security camera systems that ensure round-the-clock safety. From design to deployment, our expert CCTV installers in Dubai guarantee seamless installation with minimal disruption. Our team is SIRA-approved, making us one of the trusted SIRA-approved CCTV companies in Dubai, committed to meeting all compliance and safety standards.
Beyond CCTV, Sevenlines Link excels in access control systems in Dubai, empowering businesses with secure entry management through biometric, RFID, and keypad technologies. We also deliver reliable WiFi solutions in Dubai, ideal for smart homes and offices. Our robust intercom systems in Dubai offer crystal-clear communication and secure entry management, while our comprehensive structured cabling services in Dubai ensure high-performance networks across your premises. Whether you're upgrading an existing system or starting fresh, we provide scalable and future-ready technology.
With a strong track record in system reliability and customer satisfaction, Sevenlines Link is considered the best CCTV installation company in Dubai. We provide tailored security packages along with prompt CCTV maintenance services in Dubai to ensure long-term performance. For clients seeking the best CCTV company in Dubai with a reputation for innovation and support, Sevenlines Link is the clear choice. As one of the most affordable and efficient CCTV maintenance companies in Dubai, we continue to protect what matters most—your peace of mind.
Sevenlines Technologies is a leading CCTV company in Dubai, providing cutting-edge surveillance solutions tailored for residential, commercial, and industrial clients. As one of the best CCTV installation companies in Dubai, we specialize in delivering high-definition camera systems, remote monitoring setups, and advanced security configurations to safeguard your property. Backed by a team of expert CCTV installers in Dubai, we ensure seamless setup and reliable performance, meeting both individual and business security needs.
In addition to CCTV, Sevenlines is also a trusted provider of access control systems in Dubai, helping organizations maintain secure premises through biometric, RFID, and smart card solutions. We are recognized among SIRA-approved CCTV companies in Dubai, ensuring compliance with Dubai Police security standards. Our expertise extends to CCTV maintenance services in Dubai, offering ongoing support, inspections, and system upgrades to keep your surveillance running smoothly at all times.
Expanding beyond surveillance, Sevenlines also delivers high-performance WiFi solutions in Dubai, intercom systems, and structured cabling services that form the backbone of smart, secure environments. Recognized among the top CCTV companies in Dubai, we combine advanced technology, expert integration, and responsive support to deliver unmatched value. Whether you’re searching for the best CCTV company in Dubai or a reliable partner for end-to-end IT infrastructure, Sevenlines is your go-to solution provider.
#cctv company dubai#cctv installers in dubai#access control system dubai#WiFi solutions in Dubai#best cctv company in dubai#cctv maintenance company in dubai#top cctv companies in dubai#Sira approved cctv companies in dubai#intercom system in dubai#structured cabling services in dubai#best cctv installation company in dubai
0 notes
Text
#Gate Diagnostics#Intercom Systems#Gate Installation#Automatic Gates#Call Entry Gate Service#Commercial Gates#Custom Gate Design#Driveway Gates#Electric Gates#Residential Gates#Sliding Gates#Gate Repair#Access Control
1 note
·
View note
Text
Custom Kiosks & Terminals: Tailored Solutions for Smart Parking & Access Management
In an increasingly automated world, businesses and municipalities are turning to custom kiosks and terminals to streamline operations, enhance user experience, and reinforce security. From smart parking systems to access control and visitor management, these customisable solutions serve as vital touchpoints for both users and operators. At Parkomax, we offer advanced custom kiosk and terminal solutions designed to meet the unique operational demands of every environment — whether it’s a mall, office complex, school, or beachfront facility.
What Are Custom Kiosks & Terminals?
Custom kiosks and terminals are standalone or integrated digital systems built with tailored software and hardware features to perform specific tasks. Unlike off-the-shelf options, custom solutions allow organisations to design interfaces, functionalities, and physical layouts that align with their brand, infrastructure, and operational workflows.
They can be configured to handle various applications, including:
Ticketless and ticket-based parking management
Employee access control
Visitor registration and validation
Payment processing
Wayfinding and information display
Key Benefits of Custom Kiosks & Terminals
1. Tailored Functionality for Unique RequirementsEach organisation has its own set of challenges and goals. Custom kiosks allow you to select and integrate only the components you need, ensuring optimal performance and avoiding unnecessary complexity. Whether you need license plate recognition, NFC payment, or biometric authentication, custom kiosks can accommodate it all.
2. Enhanced User ExperienceUser-friendliness is at the heart of a successful kiosk. Custom terminals can be designed with intuitive touchscreens, multilingual support, and ADA-compliant accessibility to create a smooth experience for all users.
3. Seamless Integration with Existing SystemsParkomax custom kiosks integrate effortlessly with your current access control systems, ERP software, or cloud-based management platforms. This makes upgrades more efficient and ensures continuity across operations.
4. Scalable and Future-readyAs your needs evolve, custom kiosks can be easily upgraded or modified to incorporate new features — such as facial recognition or AI-powered analytics — making them a future-proof investment.
5. Brand Alignment and Aesthetic ValuePhysical design plays a crucial role in brand perception. Custom terminals can be manufactured with specific colors, logos, and materials to match your organisation's branding and architectural aesthetics.
Applications Across Industries
1. Smart Parking FacilitiesCustom kiosks are essential components in modern parking systems, enabling ticketless entry, real-time slot updates, mobile payments, and automated exit validation. They reduce congestion and manual oversight, ensuring a smoother parking experience.
2. Commercial Buildings and OfficesUse customised access terminals to control employee and visitor entry, capture attendance, and manage credentials. These systems can also help meet compliance standards for data logging and security audits.
3. Shopping Malls and Entertainment VenuesMalls benefit from kiosks that provide information, validate parking, and offer loyalty program integration. Customisation ensures the kiosks blend seamlessly into the venue's branding and customer service model.
4. Schools and Educational InstitutionsControl visitor access, student attendance, and vehicle entry with custom-built terminals that support biometric recognition, ID scanning, and real-time alerts.
5. Beachfront and Outdoor FacilitiesWeather-resistant custom kiosks can be deployed at open-air locations like beaches, parks, or events, offering features like automated entry tickets, mobile payments, and usage analytics.
Why Choose Parkomax Custom Kiosks & Terminals?
At Parkomax, we specialise in delivering purpose-built kiosk solutions that combine advanced technology, elegant design, and user-centric interfaces. Here’s what sets us apart:
End-to-End Customisation: From software functionality to physical design and user flow, we tailor every component.
Robust Hardware: Our kiosks are built to last, with high-quality enclosures, vandal-proof screens, and weatherproof options.
Smart Integrations: Compatible with ANPR cameras, RFID, barcode scanners, biometric readers, and more.
24/7 Support & Maintenance: Advanced technical support ensures your systems remain functional and secure.
Proven Deployments: Trusted by organisations across the GCC for their parking and access control needs.
Conclusion
Custom kiosks and terminals are no longer a luxury — they are a necessity for modern, efficient, and secure operations. Whether you're managing a high-traffic parking lot or streamlining access to a commercial facility, a tailor-made kiosk can significantly improve both user satisfaction and operational efficiency. With Parkomax’s expertise in smart infrastructure, you can bring your ideal system to life.
Explore our full range of custom kiosk solutions today and discover how Parkomax can help you elevate your space.
#Custom kiosks and terminals#Smart kiosk solutions#Parking management kiosk#Access control terminals#Visitor management kiosks#Tailored kiosk solutions#Self-service kiosk systems#Parkomax kiosk solutions#Ticketless parking kiosk#Ticket-based parking terminal#Payment processing kiosk#Biometric access kiosk#Employee access terminal#License plate recognition kiosk#NFC payment kiosk#Facial recognition kiosk#Real-time attendance kiosk#Wayfinding digital kiosk
0 notes
Text
At the California Institute of the Arts, it all started with a videoconference between the registrar’s office and a nonprofit.
One of the nonprofit’s representatives had enabled an AI note-taking tool from Read AI. At the end of the meeting, it emailed a summary to all attendees, said Allan Chen, the institute’s chief technology officer. They could have a copy of the notes, if they wanted — they just needed to create their own account.
Next thing Chen knew, Read AI’s bot had popped up inabout a dozen of his meetings over a one-week span. It was in one-on-one check-ins. Project meetings. “Everything.”
The spread “was very aggressive,” recalled Chen, who also serves as vice president for institute technology. And it “took us by surprise.”
The scenariounderscores a growing challenge for colleges: Tech adoption and experimentation among students, faculty, and staff — especially as it pertains to AI — are outpacing institutions’ governance of these technologies and may even violate their data-privacy and security policies.
That has been the case with note-taking tools from companies including Read AI, Otter.ai, and Fireflies.ai.They can integrate with platforms like Zoom, Google Meet, and Microsoft Teamsto provide live transcriptions, meeting summaries, audio and video recordings, and other services.
Higher-ed interest in these products isn’t surprising.For those bogged down with virtual rendezvouses, a tool that can ingest long, winding conversations and spit outkey takeaways and action items is alluring. These services can also aid people with disabilities, including those who are deaf.
But the tools can quickly propagate unchecked across a university. They can auto-join any virtual meetings on a user’s calendar — even if that person is not in attendance. And that’s a concern, administrators say, if it means third-party productsthat an institution hasn’t reviewedmay be capturing and analyzing personal information, proprietary material, or confidential communications.
“What keeps me up at night is the ability for individual users to do things that are very powerful, but they don’t realize what they’re doing,” Chen said. “You may not realize you’re opening a can of worms.“
The Chronicle documented both individual and universitywide instances of this trend. At Tidewater Community College, in Virginia, Heather Brown, an instructional designer, unwittingly gave Otter.ai’s tool access to her calendar, and it joined a Faculty Senate meeting she didn’t end up attending. “One of our [associate vice presidents] reached out to inform me,” she wrote in a message. “I was mortified!”
24K notes
·
View notes
Text
Best data security platforms of 2025 - AI News
New Post has been published on https://thedigitalinsider.com/best-data-security-platforms-of-2025-ai-news/
Best data security platforms of 2025 - AI News


With the rapid growth in the generation, storage, and sharing of data, ensuring its security has become both a necessity and a formidable challenge. Data breaches, cyberattacks, and insider threats are constant risks that require sophisticated solutions. This is where Data Security Platforms come into play, providing organisations with centralised tools and strategies to protect sensitive information and maintain compliance.
Key components of data security platforms
Effective DSPs are built on several core components that work together to protect data from unauthorised access, misuse, and theft. The components include:
1. Data discovery and classification
Before data can be secured, it needs to be classified and understood. DSPs typically include tools that automatically discover and categorize data based on its sensitivity and use. For example:
Personal identifiable information (PII): Names, addresses, social security numbers, etc.
Financial data: Credit card details, transaction records.
Intellectual property (IP): Trade secrets, proprietary designs.
Regulated data: Information governed by laws like GDPR, HIPAA, or CCPA.
By identifying data types and categorizing them by sensitivity level, organisations can prioritise their security efforts.
2. Data encryption
Encryption transforms readable data into an unreadable format, ensuring that even if unauthorised users access the data, they cannot interpret it without the decryption key. Most DSPs support various encryption methods, including:
At-rest encryption: Securing data stored on drives, databases, or other storage systems.
In-transit encryption: Protecting data as it moves between devices, networks, or applications.
Modern DSPs often deploy advanced encryption standards (AES) or bring-your-own-key (BYOK) solutions, ensuring data security even when using third-party cloud storage.
3. Access control and identity management
Managing who has access to data is a important aspect of data security. DSPs enforce robust role-based access control (RBAC), ensuring only authorised users and systems can access sensitive information. With identity and access management (IAM) integration, DSPs can enhance security by combining authentication methods like:
Passwords.
Biometrics (e.g. fingerprint or facial recognition).
Multi-factor authentication (MFA).
Behaviour-based authentication (monitoring user actions for anomalies).
4. Data loss prevention (DLP)
Data loss prevention tools in DSPs help prevent unauthorised sharing or exfiltration of sensitive data. They monitor and control data flows, blocking suspicious activity like:
Sending confidential information over email.
Transferring sensitive data to unauthorised external devices.
Uploading important files to unapproved cloud services.
By enforcing data-handling policies, DSPs help organisations maintain control over their sensitive information.
5. Threat detection and response
DSPs employ threat detection systems powered by machine learning, artificial intelligence (AI), and behaviour analytics to identify unauthorised or malicious activity. Common features include:
Anomaly detection: Identifies unusual behaviour, like accessing files outside normal business hours.
Insider threat detection: Monitors employees or contractors who might misuse their access to internal data.
Real-time alerts: Provide immediate notifications when a potential threat is detected.
Some platforms also include automated response mechanisms to isolate affected data or deactivate compromised user accounts.
6. Compliance audits and reporting
Many industries are subject to strict data protection regulations, like GDPR, HIPAA, CCPA, or PCI DSS. DSPs help organisations comply with these laws by:
Continuously monitoring data handling practices.
Generating detailed audit trails.
Providing pre-configured compliance templates and reporting tools.
The features simplify regulatory audits and reduce the risk of non-compliance penalties.
Best data security platforms of 2025
Whether you’re a small business or a large enterprise, these tools will help you manage risks, secure databases, and protect sensitive information.
1. Velotix
Velotix is an AI-driven data security platform focused on policy automation and intelligent data access control. It simplifies compliance with stringent data regulations like GDPR, HIPAA, and CCPA, and helps organisations strike the perfect balance between accessibility and security. Key Features:
AI-powered access governance: Velotix uses machine learning to ensure users only access data they need to see, based on dynamic access policies.
Seamless integration: It integrates smoothly with existing infrastructures across cloud and on-premises environments.
Compliance automation: Simplifies meeting legal and regulatory requirements by automating compliance processes.
Scalability: Ideal for enterprises with complex data ecosystems, supporting hundreds of terabytes of sensitive data.
Velotix stands out for its ability to reduce the complexity of data governance, making it a must-have in today’s security-first corporate world.
2. NordLayer
NordLayer, from the creators of NordVPN, offers a secure network access solution tailored for businesses. While primarily a network security tool, it doubles as a robust data security platform by ensuring end-to-end encryption for your data in transit.
Key features:
Zero trust security: Implements a zero trust approach, meaning users and devices must be verified every time data access is requested.
AES-256 encryption Standards: Protects data flows with military-grade encryption.
Cloud versatility: Supports hybrid and multi-cloud environments for maximum flexibility.
Rapid deployment: Easy to implement even for smaller teams, requiring minimal IT involvement.
NordLayer ensures secure, encrypted communications between your team and the cloud, offering peace of mind when managing sensitive data.
3. HashiCorp Vault
HashiCorp Vault is a leader in secrets management, encryption as a service, and identity-based access. Designed for developers, it simplifies access control without placing sensitive data at risk, making it important for modern application development.
Key features:
Secrets management: Protect sensitive credentials like API keys, tokens, and passwords.
Dynamic secrets: Automatically generate temporary, time-limited credentials for improved security.
Encryption as a service: Offers flexible tools for encrypting any data across multiple environments.
Audit logging: Monitor data access attempts for greater accountability and compliance.
With a strong focus on application-level security, HashiCorp Vault is ideal for organisations seeking granular control over sensitive operational data.
4. Imperva Database Risk & Compliance
Imperva is a pioneer in database security. Its Database Risk & Compliance solution combines analytics, automation, and real-time monitoring to protect sensitive data from breaches and insider threats.
Key features:
Database activity monitoring (DAM): Tracks database activity in real time to identify unusual patterns.
Vulnerability assessment: Scans databases for security weaknesses and provides actionable remediation steps.
Cloud and hybrid deployment: Supports flexible environments, ranging from on-premises deployments to modern cloud setups.
Audit preparation: Simplifies audit readiness with detailed reporting tools and predefined templates.
Imperva’s tools are trusted by enterprises to secure their most confidential databases, ensuring compliance and top-notch protection.
5. ESET
ESET, a well-known name in cybersecurity, offers an enterprise-grade security solution that includes powerful data encryption tools. Famous for its malware protection, ESET combines endpoint security with encryption to safeguard sensitive information.
Key features:
Endpoint encryption: Ensures data remains protected even if devices are lost or stolen.
Multi-platform support: Works across Windows, Mac, and Linux systems.
Proactive threat detection: Combines AI and machine learning to detect potential threats before they strike.
Ease of use: User-friendly dashboards enable intuitive management of security policies.
ESET provides an all-in-one solution for companies needing endpoint protection, encryption, and proactive threat management.
6. SQL Secure
Aimed at database administrators, SQL Secure delivers specialised tools to safeguard SQL Server environments. It allows for detailed role-based analysis, helping organisations improve their database security posture and prevent data leaks.
Key features:
Role analysis: Identifies and mitigates excessive or unauthorised permission assignments.
Dynamic data masking: Protects sensitive data by obscuring it in real-time in applications and queries.
Customisable alerts: Notify teams of improper database access or policy violations immediately.
Regulatory compliance: Predefined policies make it easy to align with GDPR, HIPAA, PCI DSS, and other regulations.
SQL Secure is a tailored solution for businesses dependent on SQL databases, providing immediate insights and action plans for tighter security.
7. Acra
Acra is a modern, developer-friendly cryptographic tool engineered for data encryption and secure data lifecycle management. It brings cryptography closer to applications, ensuring deep-rooted data protection at every level.
Key features:
Application-level encryption: Empowers developers to integrate customised encryption policies directly into their apps.
Intrusion detection: Monitors for data leaks with a robust intrusion detection mechanism.
End-to-end data security: Protect data at rest, in transit, and in use, making it more versatile than traditional encryption tools.
Open source availability: Trusted by developers thanks to its open-source model, offering transparency and flexibility.
Acra is particularly popular with startups and tech-savvy enterprises needing a lightweight, developer-first approach to securing application data.
8. BigID
BigID focuses on privacy, data discovery, and compliance by using AI to identify sensitive data across structured and unstructured environments. Known for its data intelligence capabilities, BigID is one of the most comprehensive platforms for analysing and protecting enterprise data.
Key Features:
Data discovery: Automatically classify sensitive data like PII (Personally Identifiable Information) and PHI (Protected Health Information).
Privacy-by-design: Built to streamline compliance with global privacy laws like GDPR, CCPA, and more.
Risk management: Assess data risks and prioritise actions based on importance.
Integrations: Easily integrates with other security platforms and cloud providers for a unified approach.
BigID excels at uncovering hidden risks and ensuring compliance, making it an essential tool for data-driven enterprises.
9. DataSunrise Database Security
DataSunrise specialises in database firewall protection and intrusion detection for a variety of databases, including SQL-based platforms, NoSQL setups, and cloud-hosted solutions. It focuses on safeguarding sensitive data while providing robust real-time monitoring.
Key features:
Database firewall: Blocks unauthorised access attempts with role-specific policies.
Sensitive data discovery: Identifies risky data in your database for preventative action.
Audit reporting: Generate detailed investigative reports about database activity.
Cross-platform compatibility: Works with MySQL, PostgreSQL, Oracle, Amazon Aurora, Snowflake, and more.
DataSunrise is highly configurable and scalable, making it a solid choice for organisations running diverse database environments.
10. Covax Polymer
Covax Polymer is an innovative data security platform dedicated to governing sensitive data use in cloud-based collaboration tools like Slack, Microsoft Teams, and Google Workspace. It’s perfect for businesses that rely on SaaS applications for productivity.
Key features:
Real-time governance: Monitors and protects data transfers occurring across cloud collaboration tools.
Context-aware decisions: Evaluates interactions to identify potential risks, ensuring real-time security responses.
Data loss prevention (DLP): Prevents sensitive information from being shared outside approved networks.
Comprehensive reporting: Tracks and analyses data sharing trends, offering actionable insights for compliance.
Covax Polymer addresses the growing need for securing communications and shared data in collaborative workspaces.
(Image source: Unsplash)
#2025#access control#access management#Accessibility#Accounts#ai#ai news#AI-powered#alerts#Amazon#amp#analyses#Analysis#Analytics#anomalies#anomaly#anomaly detection#API#application development#applications#approach#apps#artificial#Artificial Intelligence#as a service#assessment#audit#aurora#authentication#automation
0 notes
Text

This thing drove past me in the airport. I have no words
#resisting the urge to be a smart arse and be like#it's called a wheelchair#anyway they originally had this function (app control) to help with parking/ so you can summon your chair from across the room/house#but now they're being used in airports to give ppl more freedom#(airport accessibility services are traditionally. well. not very accessible. If you use them your freedom is pretty restricted)#this is a great alternative tbh. and honestly. if you're worried about getting run down.#maybe you should be a bit more aware of wheelchairs day to day anyway??? if these teach ppl to look out for chairs i won't complain
2K notes
·
View notes
Text
Different kind of Locksmith Services in Grapevine

Being a locksmith isn’t just about unlocking or changing locks anymore. Nowadays, locksmith experts offer a wide variety of services, which are often accessible through service providers and range from simply replacing locks to complicated installation of high-security locks. These services are all related to locks and security systems but their applications also go across different industries. From securing your residential spaces and vehicle to industrial security, there is a corresponding locksmith service that will help you in any kind of security-related situation. Below are some of the common types of locksmith services that are being offered in Grapevine.
Residential locksmith service
Some of the most common locksmith services involve domestic lock and security services. Improving domestic security is among the primary locksmith services that every locksmith company offers, and many of the clients are local homeowners. A residential locksmith is a specialized field and it includes installing an entire lock system throughout the property or simply unlocking the main door when the key is lost. There are also some advanced residential security services that can be requested by homeowners. For example, they might need to install a safe or a vault in a room. For more progressive providers, building an effective room can be a deal. The basic services of residential locksmiths consist of key cutting, duplication, and lock picking.
Commercial locksmith services
Unlike residential locksmiths, commercial technicians are involved in much bigger projects concerning security. Many locksmiths offer complete security solutions to small offices, shops, schools, or even large enterprises such as commercial banks, etc. in essence, a comprehensive commercial locksmith is more trained and deals with advanced tools and techniques. Their services include installing security cameras, motion detectors and sensors, and CCTV cameras, etc. The usual security system also consists of biometric or fingerprint-based locks that are high-security locks and need specialized locksmiths for installation or maintenance.
Car locksmith services
It is not uncommon when someone forgets their key inside the car and locks it. In an event like that, you might need an emergency locksmith service. Today most locksmiths offer call-in requests for a locksmith service so that you can seek their assistance whenever you need them. It doesn’t matter when you are locked out of your car as most professional locksmith services work around the class and will come to you if you are in their working region. So, when people lose their keys, break them in the ignition, or unfortunately lock themselves out of their vehicle, they can make a quick call, inform them about the vehicle and other details so they would come prepared and wait to be rescued.
#24/7 emergency locksmith Grapevine TX#car key replacement Grapevine TX#residential locksmith services Grapevine#commercial locksmith solutions Grapevine#lockout services Grapevine TX#key duplication service Grapevine#high-security locks Grapevine#automotive locksmith Grapevine#lock repair Grapevine TX#access control systems Grapevine
0 notes
Text
Professional Oven Cleaning Services | Hood Guyz

Discover professional oven cleaning services at Hood Guyz. Our expert team specializes in conveyor oven cleaning, providing thorough, eco-friendly solutions for commercial kitchens. Visit our website to learn more.
#Pollution Control Unit#Hood Cleaning#Exhaust Cleaning Company#Hood Cleaning Company Chicago#Appliance Cleaning Service#Access Panel Installation
0 notes
Text
Security Solutions: Safeguarding Your Business with Vivency Global
In today's way of life- and technology-driven society, business safety concerns are so much greater. So many elements are taken into consideration in securing your corporates- physical threats, cyber threats, creating some sense in a comprehensive program thereby protecting assets and employees from becoming files. In a world full of threats, Vivency Global knows that it comes up with the best in state-of-the-art security solutions and has taken vast steps toward diversification of the areas in the industry.
Our Complete Customized Security Solutions
Vivency Global prides itself in a vast array of tailored security solutions in Dubai with insights from leading-edge technology. Whether you are a small-sized business owner or a major industrial or corporate employer, our solutions are here with you in mind to help protect what is most viable to you.
1. Video Surveillance Cameras
Our advanced surveillance solutions are on 24x7 and ensure that you are monitoring your premises at the spur of the moment, high-definition cameras or high-definition video surveillance analytics to provide a system that prevents or discourages unauthorized access and increases operational proficiency.
Accrued from features as under:
High-resolution video capture for clear images.
Internet remote viewing via mobile and fixed applications.
Motion detection and automatic alerts for the user of suspicious activities.
Integration into existing security infrastructure with smooth operation.
2. Access Control Systems
Protection is not possible without knowing who enters and leaves the premises. To secure access while allowing authorized persons ease, several of our access control solutions were crafted.
These are as follows:
The most common is the biometric scanner that reads facial structures and fingerprints.
Another is a card-based system for ease in access to employees.
Cloud-based access control-centralized management.
Another innovative system is integration with time and attendance systems to double the efficiency but not the invasion.
3. Intrusion Detection Systems
In protecting staff members, ideally unauthorized access should be detected and prevented well before it can become a problem. There is a quick warning generated within a couple of seconds of contact in our intrusion detection systems, which come with intelligent algorithms.
The key advantages are as follow:
Guarding premises with movement detectors and alarms
Smart sensors that recognize between real threats and false alarms
Comprehensive monitoring - integrated with surveillance systems
4. Cybersecurity Solutions
Besides the protection of physical space, ensuring security of digital assets through Vivency Global's soft-and hardware is unavoidable, with data breaches and cyber-attacks in the digital world on the rise.
The following, among many, are some of the offerings in cyber protection deployed after the consultancy:
Firewalls and intrusion-prevention systems.
End-to-end encryption for secure data transmission.
Regular vulnerability assessments and penetration testing.
Training programs for employee education on the provens of good cybersecurity practices.
Custom Solutions for Every Industry
Not every business is like another, and thus security plans can't be copied from one to the next. It simply doesn't work that way universally. This is why we focus on learning about every specific requirement that you need and provides solutions that have been designed accordingly.
Our Industries include the following:
Retail: Which includes preventing theft and keeping track of inventory, and better safety for customers.
Education: Includes keeping students and staff safe with campus-wide surveillance and controlled access to buildings, etc.
Healthcare: Involves security for patient data and a safe environment for professionals to work within.
Manufacturing: Here you can ensure the protection of machinery, employees, and intellectual property.
Hospitality: Security and warmth to guests while in residence.
Why Go with Vivency Global?
One must keep in mind that when it comes to choosing a security partner, it must be chosen very wisely, as peace of mind is achieved only through it. We are recognizable because:
Professionalism: The highly skilled team of Vivency Global assures they have experience for the security program design and its execution.
Technology: Vivency Global is proud of the latest that technology security can provide, and offering a solution in innovative security technology.
Customizable: Thus, we have a security system built for you.
Assistance: Installation, maintenance, and upgrading can easily happen because of our stand service provision.
Ensuring a Secure Future with Vivency Global
Your business is worth top security services, and Vivency Global provides it. With our variety of solutions, we aim to create a secure environment, in order to promote the thriving of your business. Reach us right now to figure out how we can serve you and protect your assets so that you can achieve peace of mind.
Make Vivency Global your safe partner to safeguard your most valued assets.


#Security solutions#Business security#Surveillance systems#CCTV cameras#Access control#Intrusion detection#Cybersecurity#Security services#Asset protection#Security systems
0 notes
Text

Sevenlines Technologies is a leading CCTV company in Dubai, providing cutting-edge surveillance solutions tailored for residential, commercial, and industrial clients. As one of the best CCTV installation companies in Dubai, we specialize in delivering high-definition camera systems, remote monitoring setups, and advanced security configurations to safeguard your property. Backed by a team of expert CCTV installers in Dubai, we ensure seamless setup and reliable performance, meeting both individual and business security needs.
In addition to CCTV, Sevenlines is also a trusted provider of access control systems in Dubai, helping organizations maintain secure premises through biometric, RFID, and smart card solutions. We are recognized among SIRA-approved CCTV companies in Dubai, ensuring compliance with Dubai Police security standards. Our expertise extends to CCTV maintenance services in Dubai, offering ongoing support, inspections, and system upgrades to keep your surveillance running smoothly at all times.
Expanding beyond surveillance, Sevenlines also delivers high-performance WiFi solutions in Dubai, intercom systems, and structured cabling services that form the backbone of smart, secure environments. Recognized among the top CCTV companies in Dubai, we combine advanced technology, expert integration, and responsive support to deliver unmatched value. Whether you’re searching for the best CCTV company in Dubai or a reliable partner for end-to-end IT infrastructure, Sevenlines is your go-to solution provider.
#cctv company dubai#cctv installers in dubai#access control system dubai#WiFi solutions in Dubai#best cctv company in dubai#cctv maintenance company in dubai#top cctv companies in dubai#Sira approved cctv companies in dubai#intercom system in dubai#structured cabling services in dubai#best cctv installation company in dubai
0 notes