#end to end encryption
Text
UPDATE! REBLOG THIS VERSION!
#reaux speaks#zoom#terms of service#ai#artificial intelligence#privacy#safety#internet#end to end encryption#virtual#remote#black mirror#joan is awful#twitter#instagram#tiktok#meetings#therapy
23K notes
·
View notes
Text
Better Videos With End-to-End Procurement Partners

In this article, we will explore the advantages of working with a procurement partner to elevate your video marketing efforts.
The Role of End-to-End Procurement Partners in Video Production
End-to-end procurement partners specialize in sourcing, negotiating, and managing all aspects of the video production process. From securing the right equipment and crew to managing logistics and post-production, these partners can handle every step of the process, allowing you to focus on your core business objectives. By leveraging their expertise and industry connections, you can access top-tier resources and talent that may not be readily available to you otherwise.
Benefits of Partnering with a Procurement Partner for Video Production
Cost Efficiency: Procurement partners have the buying power and industry knowledge to negotiate favorable rates for equipment, services, and talent, saving you money in the long run.
Time Savings: By delegating the procurement process to a specialized partner, you can free up your time and resources to focus on other aspects of your business.
Quality Assurance: Procurement partners have established relationships with reliable vendors and suppliers, ensuring that you receive high-quality equipment and services for your video production needs.
Streamlined Process: With a procurement partner managing all aspects of the production process, you can enjoy a streamlined and efficient workflow from start to finish.
How to Choose the Right Procurement Partner for Your Video Production Needs
When selecting a procurement partner for your video production needs, it is essential to consider several factors:
Industry Experience: Look for a partner with a proven track record in the video production industry and a portfolio of successful projects then approach Benchkart.
Resource Network: A reputable procurement partner should have access to a wide network of vendors, suppliers, and industry professionals to meet your specific needs.
Client References: Ask for client references and testimonials to gauge the partner's reputation and customer satisfaction levels.
Communication Skills: Effective communication is key to a successful partnership, so choose a partner who listens to your needs and provides clear updates throughout the production process.
Partnering with an end-to-end procurement partner can significantly enhance the quality and efficiency of your video production efforts.
By leveraging their expertise, resources, and industry connections, you can create compelling video content that resonates with your target audience and drives results for your business. So, why not consider working with a procurement partner to take your video marketing to the next level?
Source: https://benchkart.com/blog/better-videos-with-end-to-end-procurement-partners/
#video production#benchkart#partners#end to end encryption#Video production#enterprise solution#IT outsourcing
1 note
·
View note
Text
The Apple story I wish I'd had time to write this week: The company caves on RCS
'
After Apple killing off the Lightning connector on the iPhone (if only they would remember to do likewise with their input devices), the story I’ve most looked forward to writing about that company would involve it raising the lowest common denominator for Android-to-iPhone text messaging from its current miserable and unencrypted state.
So of course that news broke, in the form of an Apple…

View On WordPress
#getthemessage#chat features#encryption in transit#end to end encryption#green bubbles#GSMA#iMessage#MMS#RCS#SMS#texting#texts
0 notes
Text
And the Winner Is . . . Secure My Email
Free to Consumers and Free 30-Day Trial for Busineses.
https://www.securemyemail.com
youtube
View On WordPress
#best encrypted email#best private email#encrypted email#end to end encryption#free encrypted email#internet privacy#internet security#secure my email#witopia#Youtube
0 notes
Text
"fascinating to hear about a dark money fund advocating to make end to end encryption illegal because, “think of the children”"
#dark money#children#capitalism#end to end encryption#encryption#privacy#right to privacy#invasion of privacy#internet#opensource#class war#ausgov#politas#auspol#tasgov#taspol#australia#fuck neoliberals#neoliberal capitalism#anthony albanese#albanese government#fuck the gop#fuck the police#fuck the supreme court#fuck the patriarchy#antiauthoritarian#antinazi#antinationalist#software#humanrights
0 notes
Text
This article is very strong on the anti-encryption.
I found the headline for this article didn't protray what is being talked about.
1 note
·
View note
Text
Apple Scraps CSAM Detection Tool for iCloud Photos
Apple Scraps CSAM Detection Tool for iCloud Photos
Home › Endpoint Security
Apple Scraps CSAM Detection Tool for iCloud Photos
By Ryan Naraine on December 08, 2022
Tweet
Apple has scrapped plans to ship a controversial child pornography protection tool for iCloud Photos, a concession to privacy rights advocates who warned it could have been used for government surveillance.
Instead, the Cupertino, California device maker said it would expand…
View On WordPress
#Apple#APT#backdoor#csam#CSAM detection tool for iCloud Photos#data backup#end to end encryption#exploits#government surveillance#icloud#in-the-wild#iOS#ipad#iPhone#itw exploits#nation-state#privacy#privacy rights#zero-day
1 note
·
View note
Text
0 notes
Text
#tamll news#tamizhtechie#tamil news#tamizh#technology#tech#tech news#end to end encryption#encrypted messages#encryption
0 notes
Text

This crossed my dash again and like ... we all understand why you should not press that link, yeah? Infosec can be hard, but this example isn't. Right?
Even if this is not a honey pot, praxis is need-to-know basis. A whole Discord server does never need to know. You should just not organize over the internet in general, but if you still want to (why would you want to?), Discord is not the way to do it.
45 notes
·
View notes
Text
An adversarial iMessage client for Android
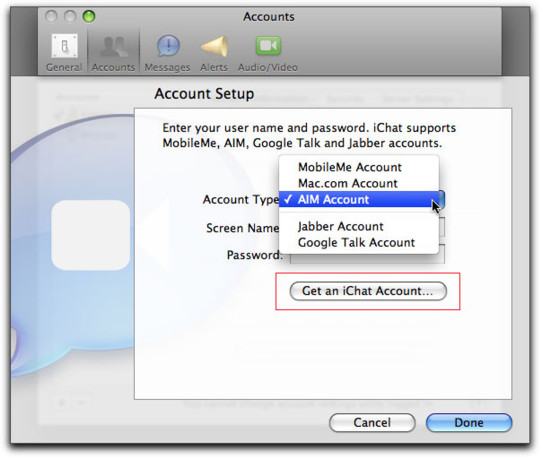
Adversarial interoperability is one of the most reliable ways to protect tech users from predatory corporations: that's when a technologist reverse-engineers an existing product to reconfigure or mod it (interoperability) in ways its users like, but which its manufacturer objects to (adversarial):
https://www.eff.org/deeplinks/2019/10/adversarial-interoperability
"Adversarial interop" is a mouthful, so at EFF, we coined the term "competitive compatibility," or comcom, which is a lot easier to say and to spell.
Scratch any tech success and you'll find a comcom story. After all, when a company turns its screws on its users, it's good business to offer an aftermarket mod that loosens them again. HP's $10,000/gallon inkjet ink is like a bat-signal for third-party ink companies. When Mercedes announces that it's going to sell you access to your car's accelerator pedal as a subscription service, that's like an engraved invitation to clever independent mechanics who'll charge you a single fee to permanently unlock that "feature":
https://www.techdirt.com/2023/12/05/carmakers-push-forward-with-plans-to-make-basic-features-subscription-services-despite-widespread-backlash/
Comcom saved giant tech companies like Apple. Microsoft tried to kill the Mac by rolling out a truly cursèd version of MS Office for MacOS. Mac users (5% of the market) who tried to send Word, Excel or Powerpoint files to Windows users (95% of the market) were stymied: their files wouldn't open, or they'd go corrupt. Tech managers like me started throwing the graphic designer's Mac and replacing it with a Windows box with a big graphics card and Windows versions of Adobe's tools.
Comcom saved Apple's bacon. Apple reverse-engineered MS's flagship software suite and made a comcom version, iWork, whose Pages, Numbers and Keynote could flawlessly read and write MS's Word, Excel and Powerpoint files:
https://www.eff.org/deeplinks/2019/06/adversarial-interoperability-reviving-elegant-weapon-more-civilized-age-slay
It's tempting to think of iWork as benefiting Apple users, and certainly the people who installed and used it benefited from it. But Windows users also benefited from iWork. The existence of iWork meant that Windows users could seamlessly collaborate on and share files with their Mac colleagues. IWork didn't just add a new feature to the Mac ("read and write files that originated with Windows users") – it also added a feature to Windows: "collaborate with Mac users."
Every pirate wants to be an admiral. Though comcom rescued Apple from a monopolist's sneaky attempt to drive it out of business, Apple – now a three trillion dollar company – has repeatedly attacked comcom when it was applied to Apple's products. When Apple did comcom, that was progress. When someone does comcom to Apple, that's piracy.
Apple has many tools at its disposal that Microsoft lacked in the early 2000s. Radical new interpretations of existing copyright, contract, patent and trademark law allows Apple – and other tech giants – to threaten rivals who engage in comcom with both criminal and civil penalties. That's right, you can go to prison for comcom these days. No wonder Jay Freeman calls this "felony contempt of business model":
https://pluralistic.net/2023/11/09/lead-me-not-into-temptation/#chamberlain
Take iMessage, Apple's end-to-end encrypted (E2EE) instant messaging tool. Apple customers can use iMessage to send each other private messages that can't be read or altered by third parties – not cops, not crooks, not even Apple. That's important, because when private messaging systems get hacked, bad things happen:
https://en.wikipedia.org/wiki/2014_celebrity_nude_photo_leak
But Apple has steadfastly refused to offer an iMessage app for non-Apple systems. If you're an Apple customer holding a sensitive discussion with an Android user, Apple refuses to offer you a tool to maintain your privacy. Those messages are sent "in the clear," over the 38-year-old SMS protocol, which is trivial to spy on and disrupt.
Apple sacrifices its users' security and integrity in the hopes that they will put pressure on their friends to move into Apple's walled garden. As CEO Tim Cook told a reporter: if you want to have secure communications with your mother, buy her an iPhone:
https://finance.yahoo.com/news/tim-cook-says-buy-mom-210347694.html
Last September, a 16-year old high school student calling himself JJTech published a technical teardown of iMessage, showing how any device could send and receive encrypted messages with iMessage users, even without an Apple ID:
https://jjtech.dev/reverse-engineering/imessage-explained/
JJTech even published code to do this, in an open source library called Pypush:
https://github.com/JJTech0130/pypush
In the weeks since, Beeper has been working to productize JJTech's code, and this week, they announced Beeper Mini, an Android-based iMessage client that is end-to-end encrypted:
https://beeper.notion.site/How-Beeper-Mini-Works-966cb11019f8444f90baa314d2f43a54
Beeper is known for a multiprotocol chat client built on Matrix, allowing you to manage several kinds of chat from a single app. These multiprotocol chats have been around forever. Indeed, iMessage started out as one – when it was called "iChat," it supported Google Talk and Jabber, another multiprotocol tool. Other tools like Pidgin have kept the flame alive for decades, and have millions of devoted users:
https://www.eff.org/deeplinks/2021/07/tower-babel-how-public-interest-internet-trying-save-messaging-and-banish-big
But iMessage support has remained elusive. Last month, Nothing launched Sunchoice, a disastrous attempt to bring iMessage to Android, which used Macs in a data-center to intercept and forward messages to Android users, breaking E2EE and introducing massive surveillance risks:
https://www.theverge.com/2023/11/21/23970740/sunbird-imessage-app-shut-down-privacy-nothing-chats-phone-2
Beeper Mini does not have these defects. The system encrypts and decrypts messages on the Android device itself, and directly communicates with Apple's servers. It gathers some telemetry for debugging, and this can be turned off in preferences. It sends a single SMS to Apple's servers during setup, which changes your device's bubble from green to blue, so that Apple users now correctly see your device as a secure endpoint for iMessage communications.
Beeper Mini is now available in Google Play:
https://play.google.com/store/apps/details?id=com.beeper.ima&hl=en_US
Now, this is a high-stakes business. Apple has a long history of threatening companies like Beeper over conduct like this. And Google has a long history deferring to those threats – as it did with OG App, a superior third-party Instagram app that it summarily yanked after Meta complained:
https://pluralistic.net/2023/02/05/battery-vampire/#drained
But while iMessage for Android is good for Android users, it's also very good for Apple customers, who can now get the privacy and security guarantees of iMessage for all their contacts, not just the ones who bought the same kind of phone as they did. The stakes for communications breaches have never been higher, and antitrust scrutiny on Big Tech companies has never been so intense.
Apple recently announced that it would add RCS support to iOS devices (RCS is a secure successor to SMS):
https://9to5mac.com/2023/11/16/apple-rcs-coming-to-iphone/
Early word from developers suggests that this support will have all kinds of boobytraps. That's par for the course with Apple, who love to announce splashy reversals of their worst policies – like their opposition to right to repair – while finding sneaky ways to go on abusing its customers:
https://pluralistic.net/2023/09/22/vin-locking/#thought-differently
The ball is in Apple's court, and, to a lesser extent, in Google's. As part of the mobile duopoly, Google has joined with Apple in facilitating the removal of comcom tools from its app store. But Google has also spent millions on an ad campaign shaming Apple for exposing its users to privacy risks when talking to Android users:
https://www.theverge.com/2023/9/21/23883609/google-rcs-message-apple-iphone-ipager-ad
While we all wait for the other shoe to drop, Android users can get set up on Beeper Mini, and technologists can kick the tires on its code libraries and privacy guarantees.

If you'd like an essay-formatted version of this post to read or share, here's a link to it on pluralistic.net, my surveillance-free, ad-free, tracker-free blog:
https://pluralistic.net/2023/12/07/blue-bubbles-for-all/#never-underestimate-the-determination-of-a-kid-who-is-time-rich-and-cash-poor
#pluralistic#multiprotocol#interoperability#adversarial interop#beeper#reverse engineering#blue bubbles#green bubbles#e2ee#end to end encrypted#messaging#jjtech#pypushbeeper mini#matrix#competitive compatibility#comcom
1K notes
·
View notes
Text



not enough zommoth content lately. in fact there is never enough zommoth content. have a fungus /ref
the alive version is based on atlas moths because they are big and cool and about the same color as alive leif
#bug fables#bug fables spoilers#zommoth#bf leif#stuff i made tag#everytime we draw ophie (<-silly nickname) it gets like 10% fluffier#at this rate she's going to be more fuzz than fungus by the end of october#translations for the zombie speak >#img 1: our son who has every disease#img 2: little sibling. little baby sibling#that was written using an encryption code from a book we read in middle school lol#reblogs>likes again. look at our sibling boy
139 notes
·
View notes
Text

real
#the thick of it#no idea what emma ended up doing after 4x07 but i bet it was something high-up and scary.#if ollie got to be caesar she must have done. by series 4 she had an encrypted phone to no. 10 that stewart didn't
9 notes
·
View notes
Text
Did Rita fill the guys in on their eye and why they have ice powers later…?
#if they did it'd be one sentence in the emergency encrypted groupchat to discuss who's holding which word in the prank reveal#a single line of text.#'ah. just so you know.#that ice storm was me. that's the gokkan's king's power.'#(like how they just open the meeting with 'i think the world ia going to end' i. ep6)#a single true sentence that explained nothing#*rita is offline… typing… typing… offline*#*Moffun 'keep it a secret' line stamp*#kingohger#wrong blog whatever#myechoes
4 notes
·
View notes
Text
HAH

HAHAHAHA I AM VICTORIOUS, GOT THE LINKLE MOD WORKING ON ACTUAL HARDWARE
#it was a pain in the ass figuring out what went wrong the first few times#i think the files ended up corrupted during the decryption and re-encryption most likely#BUT I WIN#BRIAR WINS IN THE END#HAHA
5 notes
·
View notes