#Apple iPhone Pegasus
Text

The Apple Arcade game My Little Pony: Mane Merge has been updated to version 1.3.0, with a new app icon to match. This update, based on the Netflix special My Little Pony: Bridlewoodstock, introduces a Lumi-Bloom Festival storybook, a mini-game featuring Ruby Jubilee, and another mini-game featuring Sunny Starscout's cookie decorating skills.
Mane Merge is available with a subscription to Apple Arcade on iPhone, iPad, Mac and Apple TV devices.
The official patch notes are reproduced below.
"Amidst the radiant glow of the Lumi-Bloom flowers, Bridlewood Forest transforms into a majestic location for an awe-inspiring festival. But beneath the surface of enchantment and celebration, a mysterious presence lurks, shrouding the festivities in an air of suspense and intrigue.
NEW BOOK—LUMI-BLOOM FESTIVAL
Look out, everypony; there's a new Pegasus in town! Introducing Ruby Jubilee, the dynamic and charismatic pop sensation whose dazzling performances bring an extra sparkle of magic to the mane stage of the Lumi-Bloom Festival.
OH HOOF! The festival is about to start, but it's yet to be set up! Can you help Pipp and Izzy get Bridlewood ready to PARTY?!
The Lumi-Bloom Festival's mane star is battling creative block! Help Ruby Jubilee overcome it and compose a show-stopping hit song before her performance. Pega-ssist Ruby Jubilee to musical greatness!
NEW MINI-GAME—RUBY JUBILEE'S DANCE PARTY
Get ready to groove with Equestria's biggest pop sensation, Ruby Jubilee.
Tap to the beat and show off your rhythmic skills as you join Ruby Jubilee on stage at the Lumi-Bloom Festival.
Follow the rhythm of her hit single, "Iconic," and master the dance moves to impress the crowd.
NEW MINI-GAME—SUNNY'S COOKIE CREATIONS
Join Sunny at the Crystal Brighthouse and indulge in the art of cookie decorating!
Let your imagination run wild as you experiment with a wide array of colorful toppings, sprinkles, and edible decorations to add the perfect finishing touches to your cookies.
MORE FUN
Keep merging to your heart's content with the brand-new endless mode—"Critter Festival Dress-Up"—where you can deck out your critters with glow sticks, flower crowns, and all the latest festival fashions.
NEW FEATURES
Prove your pony prowess with 9 new achievements that will put your skills to the test.
Expand your sticker collection with 21 new additions inspired by the memorable moments of the Lumi-Bloom Festival!
Miscellaneous bug fixes
So get your dancing hooves ready, unleash your creativity, and get ready to make your mark in the magical forest of Bridlewood!"
17 notes
·
View notes
Quote
セキュリティ研究者は、再起動イベントを保存するシステム ログ ファイルである Shutdown.log をチェックすることで、侵害された Apple モバイル デバイス上で有名なスパイウェア Pegasus、Reign、および Predator による感染を発見できる可能性があることを発見しました。
Kaspersky は、Shutdown.log ファイルの分析プロセスを自動化し、評価しやすい方法でマルウェア感染の潜在的な兆候を認識するのに役立つ Python スクリプトをリリースしました。
Shutdown.log はデバイスの再起動時に書き込まれ、プロセスの終了に必要な時間とその識別子 (PID) を記録します。
iShutdown スクリプト
マルウェアが実行するプロセスの挿入と操作により、デバイスの再起動に測定可能な影響を与えるマルウェアは、侵害を検証するデジタル フォレンジック アーティファクトを残します。
暗号化された iOS バックアップやネットワーク トラフィックを調べるような標準的な手法と比較して、Shutdown.log ファイルははるかに簡単な分析方法を提供すると研究者らは述べています。
Kaspersky は、 3 つの Python スクリプトを公開しました。 研究者が iOS シャットダウン ログ ファイルから再起動データを確認できるようにする iShutdown と呼ばれる
iShutdown_detect.py - ログ ファイルを含む Sysdiagnose アーカイブを分析します
iShutdown_parse.py - tar アーカイブから Shutdown.log アーティファクトを抽出します。
iShutdown_stats.py - ログ ファイルから再起動統計を抽出します。
Shutdown.log ファイルには、侵害後に再起動が実行された場合にのみ、感染の兆候を含むデータが書き込まれるため、カスペルスキーでは、デバイスの感染を頻繁に再起動することを推奨しています。
「どれくらいの頻度で尋ねるかもしれませんか? まあ、それは状況によります! それはユーザーの脅威プロファイルによって異なります。数時間ごと、毎日、またはおそらく「重要なイベント」の前後。これは自由回答の質問として残しておきます。」 - カスペルスキー
Kaspersky の GitHub リポジトリには、Python スクリプトの使用方法と出力例が含まれています。 ただし、結果を適切に評価するには、Python、iOS、ターミナル出力、およびマルウェア インジケーターについてある程度の知識が必要です。
再起動プロセスを遅らせるプロセスを強調表示する出力 (Kaspersky)
Sysdiagnose ファイルは、iOS および iPadOS デバイスのトラブルシューティングに使用される 200 ~ 400 MB の .tar.gz アーカイブであり、ソフトウェアの動作、ネットワーク通信などに関する情報が含まれています。
カスペルスキーは当初、ペガサス スパイウェアに感染した iPhone を分析する手法を使用し、ログ内の感染指標を受け取りました。これは アムネスティ インターナショナルが開発したMVT ツール を使用して確認されました。
「この動作と、分析した他の Pegasus 感染との一貫性が確認されたため、感染分析をサポートする信頼できる法医学的成果物として機能すると信じています。」 - カスペルスキー
研究者らは、感染当日にユーザーがデバイスを再起動しなかった場合、この方法は失敗すると指摘している。 もう 1 つの観察結果は、Pegasus 関連のプロセスが手順を妨げた場合など、再起動が遅延したときにログ ファイルに記録されることです。
これは感染していない携帯電話でも発生する可能性がありますが、カスペルスキーの研究者は、過度と考えられる 4 回を超える遅延は、調査する必要があるログ異常であると考えています。
に感染した iPhone でこの方法をテストしたところ Reign スパイウェア 、研究者らはマルウェアの実行が Pegasus の場合と同じパス「/private/var/db/」から行われていることに気付きました。
Shurdown ログ ファイルに表示される同様のパスは、 Predator スパイウェアによってもよく使用されます。 議員やジャーナリストを標的とした
これに基づいて、カスペルスキーの研究者は、ターゲットが十分な頻度で携帯電話を再起動する場合、ログファイルを使用することで「これらのマルウェア ファミリによる感染を特定できる可能性がある」と考えています。
iShutdown スクリプトは、iPhone 上の iOS スパイウェアの検出に役立ちます
3 notes
·
View notes
Text

2023 / 07
Aperçu of the Week:
"Success has two letters: Do!"
(Johann Wolfgang von Goethe)
Bad News of the Week:
The only serious competition to Silicon Valley is neither in Europe nor in the Far East, but between the Dead, the Red and the Mediterranean Sea: Israel. Unfortunately. Because it's rather frightening innovations that come out of the more than 300 development and research centers around Tel Aviv. And I don't mean the energy that the state puts into cutting-edge technology for the military, surveillance and espionage. But rather the focus that private-sector companies in the region have also chosen.
Three examples: Cellebrite openly advertises that it can crack iDevices. Much to the delight of the FBI, for example, because Apple had refused to crack iPhones for U.S. authorities or to build a backdoor into their encryption. The questionable services are open to any organization, even criminal ones, for a fee, as if it were a normal IT service.
NSO became a global player in commercial spyware. A market that has grown into an industry estimated to be worth twelve billion dollars, estimates The New Yorker. Their tool named Pegasus was found on the phones of politicians, activists, and dissidents under repressive regimes. The suppression of the Catalan independence movement and the murder of Saudi Arabian journalist Jamal Khashoggi with the help of this spyware are documented.
And just last week, investigative media revealed Team Jorge's business model: professional spreading of fake news to influence elections. They were hired for 32 campaigns, 27 of which were verifiably successful, they say. Yes, political success can be bought - at the expense of the opposition.
What these three examples have in common is a perfidious "not giving a fuck" attitude, which goals are pursued and also achieved with their help. For these are clearly directed against such trivialities as free democracy, independent media, functional rule of law or transparent power apparatuses. The main thing is that the money is right. The framework conditions for this seem to be optimal in Israel, of all places. And when I look at the position of Benjamin Netanyahu's newly enthroned right-wing government against an independent judiciary or free media, this will not change.
Good News of the Week:
In mid-February, Munich always hosts the "Munich Security Conference" (MSC), the world's most important meeting of top politicians on international security. While last year appeals to Russia not to attack Ukraine dominated - we all know what happened a few days later - this time it is about the concrete handling of the war that initiated the much-cited "turning point in time":
The unexpectedly dysfunctional NATO is strengthening internally (higher defense budgets) and externally (Sweden and Finland want to join the alliance), new bloc formations are emerging, the arms industry can no longer keep up with demand, Europe is groaning under a wave of refugees, economic sanctions by the West are turning out to be far less effective than expected, Putin is not wavering. War has become the order of the day.
Major strategic news is not to be expected. All countries have already clearly positioned themselves. From clear, even military support for Ukraine (e.g. all NATO members) to an effort of neutrality based on energy policy (e.g. India or Latin America) to support for the Putin course (e.g. Belarus, Syria or Myanmar). All countries have already taken a clear position? No - the elephant in the room is China.
The youngest major security power calls for peace, but does not name Russia as the aggressor. And just yesterday launched "Operation Mosi II," a joint large-scale naval maneuver with Russia and South Africa off the latter's Indian Ocean coast. So there was little hope that the Middle Kingdom - seen by almost all observers as the only power with de facto influence over the Kremlin - would actively do anything to defuse the conflict.
But then Wang Yi, longtime foreign minister of the People's Republic of China, entered the Munich stage - and stunned. By announcing a peace initiative to end Russia's war of aggression against Ukraine, he said, "We will put something forward. And that is the Chinese position on the political settlement of the Ukraine crisis," the Politburo member said Saturday, according to an official translation. "We will stand steadfastly on the side of peace and dialogue." For a safer world, he said, "the principles of the UN Charter are something we must uphold." Good. Very good. Now words just need to be followed by action.
Personal happy moment of the week:
In our countryside, there are plenty of typical Bavarian inns. And, as everywhere, countless Italians and Asians. Rarer are nice cafés where you can have a good breakfast. One we have - thanks to a voucher that I already got last year for my birthday - tried today. Very good coffee, a manageable but balanced menu. With regional products and in a former monastery building. It was worth it. It's always nice to start the Sunday with a delicious breakfast.
I couldn't care less...
...that Ukraine has requested cluster bombs and chemical weapons on the MSC. These are internationally outlawed because they cause massive collateral damage in violation of international law - including to the civilian population. That Russia is not caring about this may be, is even probable. Nevertheless, this quid pro quo logic is too weak for me. If they go low, you (still should) go high.
As I write this...
...I am mourning a little Lothar Wieler quitting his job. As head of the Robert Koch Institute (RKI) he was the Anthony Fauci of Germany. And yet more than just the side kick of the respective health minister. As a politically independent person, he moderated the pandemic in a serious but calm manner. He analyzed, commented, admonished and annoyed. Far away from the day-to-day political business. Against his will, he became a media star, even though he much preferred to sit in the lab and work on his figures. He did what he thought he had to do. Tormented by the thought that "even one more child must die". Big shoes to fill.
Post Scriptum
To be climate neutral, each person should only emit less than one ton of CO2 or similar greenhouse gases per year - currently the average is 11.6 tons. Far ahead of the consumption of beef or air travel to the South, individual transport is the main polluter: the Germans' favorite child, the car. But the will in this country to rely on electromobility seems to be driven more by financial interests than by actual conviction. When gasoline was expensive and electric cars were tax-subsidized in 2022, there was a boom. That plummeted dramatically over the turn of the year, with 83 percent fewer fully electric cars and 87 percent fewer plug-in hybrids registered in January 2023 compared to the previous month. Sigh...
#thoughts#aperçu#good news#bad news#news of the week#happy moments#politics#johann wolfgang von goethe#success#israel#silicon valley#tel aviv#spyware#fake news#cracking#munich#munich security conference#china#Wang Yi#breakfast#sunday#ukraine#weapons#pandemic#climate#neutral#electric cars#russia#quid pro quo#un charter
3 notes
·
View notes
Text

🚨 Urgent Security Warning for Apple Users: Government Flags Critical Vulnerabilities in Devices 🚨
The Indian Computer Emergency Response Team (CERT-In) has issued a significant alert regarding critical security flaws in various Apple products. In an advisory released on August 2, CERT-In identified high-risk vulnerabilities affecting devices like iPhones, iPads, Macs, and others.
🍏 Apple Devices at Risk: Affected Software Versions
The vulnerabilities have been found in several versions of Apple software, including:
📱 iOS and iPadOS: Versions earlier than 17.6 and 16.7.9
💻 macOS: Versions earlier than 14.6 (Sonoma), 13.6.8 (Ventura), and 12.7.6 (Monterey)
⌚ watchOS: Versions earlier than 10.6
📺 tvOS: Versions earlier than 17.6
🕶️ visionOS: Versions earlier than 1.3
🌐 Safari: Versions earlier than 17.3
CERT-In has warned that these security gaps could allow hackers to access sensitive data, run unauthorized code, bypass security protections, trigger denial of service (DoS) attacks, and engage in spoofing. The alert categorizes these vulnerabilities as "high severity."
🔧 Critical Update Needed: Apple Users Advised to Act Now
CERT-In strongly recommends that all Apple users immediately update their software to the latest versions provided by Apple to patch these vulnerabilities and reduce the risk of cyberattacks. The advisory stresses the urgency of this action to safeguard devices from potential threats.
🕵️♂️ Spyware Threat: Apple Alerts Users to Sophisticated Attacks
Alongside these vulnerabilities, Apple has also warned users about potential "mercenary spyware attacks," similar to the notorious Pegasus spyware. These alerts, issued to users in over 150 countries, including India, are meant to highlight the risk of advanced spyware targeting iPhones. Noteworthy individuals such as Iltija Mufti, media adviser and daughter of former Jammu and Kashmir Chief Minister Mehbooba Mufti, and Pushparaj Deshpande of the Foundation have reported receiving these alerts.
🔔 Stay Informed: Follow Us for the Latest Updates
.
.
.
#india#breakingnews#apple#iphone#hack#security#america#áfrica#brazil#iran#chinatravel#travel#viral#inspiration#public
#35mm#education#accounting#ao3#astrophotography#b&w#bodybuilding#astronomy#black and white#biology#academia#writing#writeblr#writers on tumblr#my writing#workout#arknights
1 note
·
View note
Text
Apple warns Indian iPhone users about new Pegasus-style spyware attacks.
Apple has been sending these alerts to users in over 150 countries since 2021.
Iltija Mufti and Pushparaj Deshpande have been informed by Apple about a potential hack on their phones, both being the daughter of ex-J&K chief minister Mehbooba Mufti and the founder of Samruddha Bharat Foundation, respectively.Apple has released a fresh batch of danger notifications to individuals in India and 97…
0 notes
Text
Apple: 98 ülkedeki iPhone sahipleri yeni bir virüs nedeniyle tehlikede

Bu, markanın Nisan ayında 92 ülkeyi kapsayan benzer bir duyurunun ardından 2024'teki ikinci açıklaması oldu.
Apple, 2021'den itibaren 150'den fazla ülkedeki kullanıcılara düzenli olarak bu tür bildirimler gönderiyor. En son uyarı, saldırganları veya kullanıcıların bildirim aldığı belirli ülkeleri tanımlamıyor.
Bildirimde "Apple, iPhone'unuzun, Apple Kimliğiniz -xxx- ile ilişkili aygıtın güvenliğini uzaktan ele geçirmeyi amaçlayan bir casus yazılım saldırısı altında olduğunu tespit etti" ifadesi yer alıyor.
Hindistan'daki kullanıcılar uyarıyı aldıklarını kabul etti. Ekim ayında Apple, ülkedeki birçok gazeteci ve politikacıya da benzer uyarılar göndermişti.
Uluslararası Af Örgütü daha sonra İsrailli şirket NSO Group tarafından geliştirilen Pegasus casus yazılımını önde gelen Hintli gazetecilerin iPhone'larında keşfetti.
Read the full article
0 notes
Link
Apple not too long ago notified sure iPhone customers in India a few potential adware assault that sought to achieve distant management of their gadgets. That is the second such alert the corporate has despatched to customers in India and 98 different international locations all over the world. Since 2021, Apple has despatched comparable notifications to customers in additional than 150 international locations. Apple has reportedly described these assaults, just like these utilized by NSO's Pegasus group, as extremely refined and uncommon. The corporate pressured that these assaults contain important monetary investments and are focused at a really small variety of individuals worldwide. Learn additionally: Microsoft to supply Apple gadgets to workers in China, citing lack of Android companies Everlasting world concernIn its newest communication, Apple warned affected iPhone customers that these assaults are ongoing and have a worldwide attain. Earlier this yr, India’s Laptop Emergency Response Workforce (Cert-In) highlighted vulnerabilities in Apple’s working techniques, notably in flagship merchandise such because the Safari net browser. Cert-In warned that older variations of Safari and iOS might enable attackers to execute arbitrary code on focused gadgets. Learn additionally: LG is not simply an "electronics" firm: that is how automotive software program is altering with augmented actuality and leisure Have you ever ever heard of a mercenary adware assault? In contrast to common cyberattacks, these are extraordinarily focused and expensive. Think about attackers with an enormous quantity of assets specializing in only a handful of individuals. That is what mercenary adware is all about. In line with Apple, these assaults can value hundreds of thousands and are designed to be stealthy, making them troublesome to detect. To guard your self in opposition to adware assaults, listed below are some really helpful suggestions:1. Watch out with downloads and attachments: Obtain software program and open attachments solely from trusted sources. Keep away from free software program downloads which will conceal adware. Do not click on on hyperlinks or attachments in suspicious emails. 2. Use strong safety software program: Set up trusted antivirus packages with anti-spyware and anti-malware capabilities. Preserve all software program updated to learn from the most recent safety patches. 3. Undertake protected looking habits: Keep away from clicking on suspicious pop-up adverts or hyperlinks which will set up adware. Think about using browser extensions to dam pop-ups. 4. Preserve your software program updated: Often replace your working system and software program functions. Updates usually embrace essential safety patches that repair vulnerabilities exploited by adware. 5. Watch out about sharing info on-line: Spyware and adware can steal private info entered on web sites. Watch out about what info you share, particularly when utilizing public Wi-Fi networks. Learn additionally: Samsung Galaxy Z Fold6, Z Flip6 and 5 new devices launched at Unpacked 2024 These measures can considerably enhance your safety in opposition to adware threats. Keep vigilant and prioritize safety to guard your digital gadgets and private knowledge.
0 notes
Text
Modo de isolamento da Apple: resultados mistos

Há quase dois anos, a Apple introduziu o modo Lockdown, um recurso criado para aumentar a segurança dos usuários de dispositivos da marca Apple e, mais especificamente, dos iPhones. Lançado em julho de 2022, esse modo surgiu em um momento em que o mundo estava em polvorosa com as revelações sobre o Pegasus, spyware desenvolvido pelo grupo NSO, capaz de se infiltrar em smartphones e acessar informações confidenciais. Para tranquilizar seus usuários, a empresa introduziu rapidamente o modo Lockdown como uma resposta radical à ameaça do spyware, oferecendo uma camada extra de proteção contra tentativas de acesso não autorizado.
O que é o modo Lockdown?
O modo Lockdown é uma iniciativa da Apple criada para proteger os usuários contra ameaças e ataques digitais direcionados. Ele foi introduzido com os lançamentos do iOS 16, iPadOS 16 e macOS Ventura. O recurso oferece proteções importantes para mensagens, navegação na Web, determinados serviços da Apple, conexões com fio e muito mais. A empresa sediada em Cupertino projetou esse modo especificamente para jornalistas, ativistas, denunciantes e outros indivíduos que podem ser alvo de ameaças sofisticadas.
No entanto, qualquer pessoa pode ativar esse modo.
Para ativar o modo Lockdown em um iPhone ou iPad:
- Abra o aplicativo "Ajustes".
- Toque em "Security and Confidentiality" (Segurança e confidencialidade).
- Na seção "Security" (Segurança), toque em "Lockdown mode" (Modo de bloqueio).
- Por fim, toque em "Activate Lockdown Mode" (Ativar modo de bloqueio).
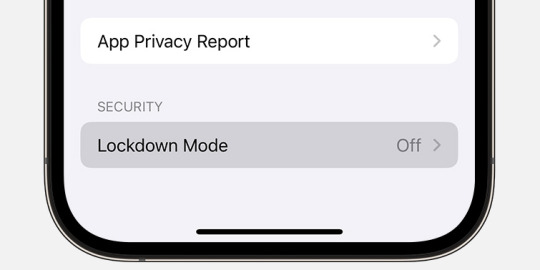
©Apple
Como ativar o modo de isolamento no macOS :
- Selecione o menu Apple > Configurações do sistema.
- No menu lateral, clique em "Privacidade e segurança".
- Role para baixo, clique em "Containment Mode" (Modo de contenção) e depois em "Enable" (Ativar).
- Clique em "Enable Containment Mode" (Ativar modo de contenção). (Poderá ser solicitado que você digite a senha do usuário).
- Clique em "Enable and Restart" (Ativar e reiniciar).
Leia também: Os Macs são realmente seguros contra vírus?
Desvantagens e preocupações com a confidencialidade
Embora o modo Lockdown ofereça benefícios de segurança inegáveis, ele também tem suas desvantagens. Ele continua sendo uma solução bastante extrema devido às muitas concessões que você terá de fazer.
Ao ativar esse modo, os usuários verão muitas de suas funções habituais restritas ou desativadas. Os anexos nas mensagens, com exceção das imagens, serão bloqueados e as visualizações de links serão desativadas.
A navegação também será restrita, com tecnologias como a compilação JavaScript just-in-time (JIT) desativada, exceto para sites confiáveis especificamente excluídos do modo de isolamento.
Os serviços da Apple, como chamadas FaceTime, serão restritos, permitindo apenas contatos com os quais o usuário já tenha interagido.
Além disso, as conexões com fio com o iPhone serão bloqueadas quando o dispositivo estiver bloqueado, e será impossível instalar perfis de configuração ou inscrever-se em uma solução de gerenciamento de dispositivos móveis.
Essas medidas, embora drásticas, foram criadas para proteger o usuário contra as ameaças mais avançadas, mas isso não é tudo.
Uma das principais desvantagens é que isso pode tornar os usuários identificáveis on-line. A ausência de determinados recursos, como o carregamento de fontes personalizadas, pode ser detectada por sites, o que poderia identificar um usuário como estando no modo Lockdown. Além disso, especialistas como John Ozbay apontaram que, em determinados contextos, como na China, ser identificado como um usuário do modo Lockdown pode representar riscos à segurança pessoal.
Medidas adicionais para reforçar a segurança e a confidencialidade
Além do modo Lockdown, várias ferramentas e práticas podem ser adotadas para aumentar a segurança e a confidencialidade do usuário. Observe que isso não é uma alternativa ao modo de bloqueio.
Uso de uma VPN: uma VPN para iPhone protege a confidencialidade da sua navegação criptografando a sua conexão com a Internet. Isso é particularmente útil em redes não seguras, como Wi-Fi público.

©NordVPN pour iOS
Atualizações regulares: mantenha seus dispositivos atualizados com as versões mais recentes dos sistemas operacionais. Essas atualizações geralmente contêm patches de segurança essenciais, como foi o caso em 10 de setembro, quando uma vulnerabilidade silenciosa no iPhone foi exposta.
Conscientização e treinamento: fique atento às ameaças on-line, como tentativas de phishing. Mantenha-se informado e use o bom senso. Nunca entre em pânico ao se deparar com uma mensagem pedindo que você tome uma ação específica.
Autenticação de dois fatores (2FA): ative essa função em suas contas essenciais. Ela oferece segurança extra, exigindo verificação adicional quando você faz login.
Para saber mais: 9 coisas que você pode fazer para proteger seu iPhone
Conclusão: feedback indiferente dos usuários
Desde sua introdução, o modo Lockdown tem recebido reações mistas.
Poucos usuários dizem que usam sistematicamente o modo de isolamento da Apple. Alguns jornalistas admitiram que o ativam quando estão fora de casa. Não encontramos nenhum dado confiável sobre a adoção em massa desse recurso.
Em fóruns como o MacRumors, alguns usuários elogiam seus benefícios de segurança, enquanto outros expressam preocupação com suas reais implicações de privacidade.
Read the full article
0 notes
Text
Zero Click Malware: The Invisible Digital Threat – How to Recognize and Defend Yourself

Estimated reading time: 6 minutes
What is Zero Click Malware
Zero click malware, also known as non-click malware or in-memory malware, is a new type of malware that can infect a device without the user taking any action.
Unlike traditional malware that requires the user to click on a link or open an infected attachment, zero click malware is able to install itself on the victim's device completely silently and invisibly, without any interaction on their part.
How Zero Click Malware Works
This type of malware exploits various vulnerabilities in software and operating systems to gain access to the device. Some common infection vectors include:
- Zero-day vulnerabilities not yet patched
- Bugs in web browsers and messaging apps
- Packet sniffers that intercept network traffic
- Insecure public WiFi networks
- Websites compromised with drive-by exploits
Once initial access is gained, zero click malware uses advanced techniques to keep itself hidden and avoid detection. It can disable antivirus software, hide in RAM memory, encrypt communications, and much more.
Why Zero Click Malware is Dangerous
The completely stealth nature of this malware makes it extremely insidious and difficult to identify. Even the most security-conscious users can be infected without knowing it.
This allows hackers to:
- Monitor all activities performed on the infected endpoint
- Collect sensitive data such as credentials, personal information, browser history
- Collect sensitive data such as credentials, personal information, browser history
- Move laterally within the network to infect other systems
- Use the device for ransomware or denial of service attacks
Furthermore, since no clicks or actions are required, zero click malware can spread very quickly, affecting a large number of victims.
Case Studies and Technical Analysis

Some real-world cases have recently emerged that illustrate the capabilities of this new category of cyber threats.
One of the first zero click exploits to gain attention was Pegasus, developed by cybersecurity firm NSO Group. Used by some governments to spy on journalists and activists, Pegasus exploits zero-day vulnerabilities in iOS and Android to install itself without any user interaction.
Another famous case is ForcedEntry, used to hack the iPhones of several employees in Bahrain. ForcedEntry exploits a vulnerability in iMessage to install spyware without clicking on Apple devices.
These and other cases demonstrate the severity of the threat and the need for advanced protection solutions capable of detecting and preventing zero-click attacks.
How to Detect and Prevent Zero Click Attacks
Since this type of threat leaves no visible traces, identifying and stopping them requires targeted strategies:
- Patching and updates - Always apply the latest security updates to fix known vulnerabilities
- EDR Solutions - Endpoint detection and response technologies that analyze memory-based threats and anomalous behavior
- Advanced web protection - Secure web gateways capable of inspecting all traffic entering and leaving the network
- Network Segmentation - Limit the ability of malware to move laterally by isolating and segmenting critical systems
- Strong Authentication - Enable multi-factor authentication to prevent targeted phishing attacks that often precede zero-clicks
- Awareness Training - Instruct users to recognize and report suspicious activity that may indicate an infection
A layered approach that integrates multiple technologies and policies is essential to defend against this ever-evolving threat.
Increase Prevention with Deception Solutions
One of the most effective strategies against zero-click malware is the use of deception solutions. These solutions create a seemingly attractive environment for malware, but in reality they are traps that detect and isolate threats before they can cause damage. By taking a multi-stage approach to defense, you can dynamically respond to threats as they evolve, defeating attackers with their own techniques.
Continuous Testing and Threat Simulations
Attack simulations and continuous testing of security controls are another key pillar in zero-click malware defense. Services like Posture Guard help organizations verify their security posture by leveraging a vast database of threats, including malware, ransomware, and Advanced Persistent Threats (APTs). These tests help you evaluate the effectiveness of your security tools and optimize your threat prevention and detection capabilities.
Cyber Threat Hunting and Threat Intelligence
Cyber Threat Hunting is crucial to proactively identify threats and sensitive information that may have been compromised. Having a team of experts dedicated to this activity allows you to quickly recover stolen information and organize a more targeted defense. Combined with continuous vulnerability analysis and incident response, this strategy offers significantly improved protection against zero-click attacks.
User training and awareness
While zero-click malware does not require user interaction for infection, a well-informed and aware workforce can still play a crucial role in preventing other types of cyber attacks. Training users on good cybersecurity practices can reduce the risk of malware infections and increase overall security.
Adopt a Dynamic Approach to Security
Taking a dynamic approach to security is essential. Solutions like Active Defense Deception work to respond to attacks during the initial stages, using dynamic techniques to prevent attacks from reaching execution and more advanced stages. This type of proactive defense can deter attackers and make the environment less attractive for malware.
Forecasts and Future Developments
Experts predict that zero-click malware attacks will become one of the most used techniques by hackers in the years to come. As user awareness of malware and phishing grows, cybercriminals will look for new invisible vectors to deliver malicious payloads.
Additionally, the continued rise of IoT devices and smart home technologies presents attackers with an ever-increasing number of potential weak and unpatched targets. Operating environments such as 5G and edge computing could also facilitate the spread of zero-click threats.
To counter these trends, companies and security vendors will need to invest more in threat intelligence, bug bounties, sandboxing and machine learning-based threat detection techniques. Only in this way will it be possible to unmask the rapidly evolving zero-click attacks in no time.
Conclusions
Clickless malware is emerging as one of the most stealthy and dangerous tactics of modern hackers. Its ability to bypass any human interaction to infect entire systems represents a critical challenge for the world of cybersecurity.
To protect individuals and companies from this threat, it is essential to adopt preventive measures at multiple levels, from patching to network monitoring to training. Only by combining awareness and advanced technological solutions will it be possible to combat the phenomenon of zero-click attacks and maintain data integrity and security in the future.
- Your virtual machine with Cloud Server
Read the full article
0 notes
Text
iShutdown: scripts claves para identificar software espía en tu iPhone
Investigadores de seguridad han descubierto que es posible detectar infecciones de los conocidos softwares espía Pegasus, Reign y Predator en dispositivos Apple. Esto se logra examinando el archivo Shutdown.log, que registra los eventos de reinicio del sistema.
Para facilitar este análisis, Kaspersky ha desarrollado tres scripts en Python. Estos scripts automatizan la revisión del archivo…

View On WordPress
0 notes
Text
New iShutdown Method Exposes Hidden Spyware Like Pegasus on Your iPhone
The Hacker News : Cybersecurity researchers have identified a "lightweight method" called iShutdown for reliably identifying signs of spyware on Apple iOS devices, including notorious threats like NSO Group's Pegasus, QuaDream's Reign, and Intellexa's Predator.
Kaspersky, which analyzed a set of iPhones that were compromised with Pegasus, said the infections left traces in a file http://dlvr.it/T1VLzr Posted by : Mohit Kumar ( Hacker )
0 notes
Photo

Amnistía confirma la advertencia de Apple: los iPhone de los periodistas indios están infectados con el software espía Pegasus Las adver... https://ujjina.com/amnistia-confirma-la-advertencia-de-apple-los-iphone-de-los-periodistas-indios-estan-infectados-con-el-software-espia-pegasus/?feed_id=474398&_unique_id=658e9f059871b
0 notes
Quote
Appleは、攻撃に悪用されiPhone、iPad、Macデバイスに影響を与える2つのゼロデイ脆弱性を修正するための緊急セキュリティアップデートをリリースし、年初からパッチが適用されたゼロデイ脆弱性は20件に達した。
「Appleは、この問題がiOS 16.7.1より前のバージョンのiOSに対して悪用された可能性があるという報告を認識している」と 同社は 水曜日に発行した勧告の中で述べた。
この 2 つのバグは WebKit ブラウザ エンジン (CVE-2023-42916 および CVE-2023-42917) で発見され、攻撃者が境界外読み取りの脆弱性を介して機密情報にアクセスしたり、メモリ破損を介して任意のコードを実行したりすることを可能にします。悪意を持って作成された Web ページを介して脆弱なデバイスにバグを引き起こす可能性があります。
同社は、 iOS 17.1.2、iPadOS 17.1.2 、 macOS Sonoma 14.1.2 、 Safari 17.1.2を実行しているデバイスのセキュリティ上の欠陥に対処したと述べています。 入力検証とロックを改善することで、
影響を受ける Apple デバイスのリストは非常に広範囲にわたり、次のものが含まれます。
iPhone XS以降
iPad Pro 12.9インチ 第2世代以降、iPad Pro 10.5インチ、iPad Pro 11インチ 第1世代以降、iPad Air 第3世代以降、iPad 第6世代以降、iPad mini 第5世代以降
macOS を実行している Mac モントレー、ベンチュラ、ソノマ
Google の脅威分析グループ (TAG) のセキュリティ研究者 Clément Lecigne 氏は、両方のゼロデイを発見して報告しました。
Apple は実際に進行中の悪用に関する情報を公開していませんが、Google TAG の研究者は、ジャーナリスト、野党政治家、反体制派などの高リスク個人に対する国家支援のスパイウェア攻撃に使用されているゼロデイを頻繁に発見し、���らかにしています。
2023 年に 20 件のゼロデイが実際に悪用される
CVE-2023-42916 と CVE-2023-42917 は、Apple が今年修正した攻撃で悪用された 19 番目と 20 番目のゼロデイ脆弱性です。
別のゼロデイ バグ ( CVE-2023-42824 ) を明らかにし、攻撃者が脆弱な iPhone や iPad の権限を昇格できるようにしました。 Google TAG は、XNU カーネルの
Apple は最近、Citizen Lab と Google TAG 研究者によって報告され、Predator スパイウェアを展開するために脅威アクターによって悪用された 3 つのゼロデイ バグ ( CVE-2023-41991、CVE-2023-41992、および CVE-2023-41993 ) にパッチを適用しました。
Citizen Lab は、9 月に Apple によって修正 他の 2 つのゼロデイ の一部として悪用された、 され、NSO Group の Pegasus スパイウェアをインストールするためのゼロクリック エクスプロイト チェーン (BLASTPASS と呼ばれる) (CVE-2023-41061および CVE-2023-41064) を明らかにしました。
今年の初め以来、Apple は以下にもパッチを適用しました。
7 月に2 回のゼロデイ (CVE-2023-37450 および CVE-2023-38606)
6 月の3 回のゼロデイ (CVE-2023-32434、CVE-2023-32435、および CVE-2023-32439)
5 月にはさらに 3 回のゼロデイ (CVE-2023-32409、CVE-2023-28204、および CVE-2023-32373)
4 月の2 つのゼロデイ (CVE-2023-28206 および CVE-2023-28205)
2 月には別 の WebKit ゼロデイ (CVE-2023-23529)
Apple、緊急アップデートで 2 つの新しい iOS ゼロデイを修正
2 notes
·
View notes
Text
Segurança no WhatsApp: Uma Nova Camada de Proteção do IP
A segurança dos nossos dispositivos digitais tem sido cada vez mais valorizada. Aprendemos, por exemplo, com o malware Pegasus, que até os iPhones podem ser infectados, levando a Apple a intensificar os seus esforços para proteger os seus utilizadores. A verdade é que não existem sistemas infalíveis, mas é possível limitar a superfície de ataque […]
View On WordPress
0 notes
Link
Apple iPhone Hacked Using Pegasus Spyware from Israel’s NSO Group – The Lifestyle Insider
0 notes
Text
Russian journalist Yevgeny Erlikh, who previously served as the editor-in-chief of a Baltic-based news program for the outlet Current Time, revealed in a Facebook post Thursday that he received a notification from Apple that said his iPhone may have been targeted by “state-sponsored attackers.”
Meduza’s publisher and general director Galina Timchenko received a similar message in June, shortly before cybersecurity experts determined that her device had been infected with Pegasus spyware.
According to Erlikh, his phone, like Timchenko’s, had a Latvian SIM card. In an interview with TV Rain, he said that he received the message from Apple in late August and that he was in Germany at the time.
Maria Epifanova, the general director of Novaya Gazeta Europe, and Yevgeny Pavlov, a correspondent for Novaya Gazeta Baltija, also said Thursday that they both received similar alerts from Apple on August 29. Novaya Gazeta Europe noted that Pavlov is a Latvian citizen and has lived in the country his entire life.
1 note
·
View note