#Asset Management Database
Explore tagged Tumblr posts
Text
Why Accurate As-Built Documentation Matters in Large-Scale Projects?

In construction, especially on large-scale projects, one of the most critical yet often underappreciated aspects is the need for accurate As-Built Documentation. These documents ensure that the final constructed structure is precisely recorded, reflecting any changes or deviations made during the construction phase compared to the original design. This information becomes invaluable for future renovations, maintenance, or asset management. However, inaccurate or incomplete as-built documentation can lead to costly errors, inefficiencies, and complications down the road.
Accurate As-Built Documentation plays an essential role in several areas of construction, including As-Built Drawings, data integration with the COBie Database, and effective Asset Management. This article will explore why as-built documentation is so vital for large-scale construction projects and how it contributes to the project's overall success.
What is As-Built Documentation?
As-Built Documentation refers to a collection of records, including drawings, plans, and models, that depict the actual conditions of a building or structure at the time of project completion. These documents reflect any modifications, design changes, or adjustments that occur during the construction process. The accuracy of these documents is vital because they serve as the "final blueprint" for the building.
There are different components to As-Built Documentation, including:
As-Built Drawings: These are detailed illustrations showing the final design and construction details. As-built drawings are typically updated throughout the construction phase to ensure they capture any deviations from the original plans.
COBie Database (Construction Operations Building Information Exchange): COBie is a standard for managing and exchanging facility information. As-built documentation can be integrated into the COBie Database, ensuring that important asset data is maintained for future use, especially for facility management and operations.
The Role of As-Built Drawings in Large-Scale Projects
Large-scale construction projects require a significant amount of coordination, and As-Built Drawings serve as the foundation for this coordination. They provide a visual record of what was built versus what was designed, helping all stakeholders—including architects, contractors, and asset managers—understand the final construction.
Key Benefits of Accurate As-Built Drawings
Improved Communication Between Stakeholders: As-built drawings provide a clear and accurate picture of the finished project, allowing for better communication between all parties involved. Whether it’s facility managers maintaining the building or contractors working on renovations, these drawings ensure everyone is on the same page.
Cost and Time Savings: Accurate as-built drawings can save time and reduce costs in the long run by preventing misunderstandings and mistakes during future projects. When facility managers or contractors have accurate drawings, they are less likely to encounter surprises that lead to delays or additional costs.
Compliance with Regulations: Large-scale construction projects often require strict adherence to building codes and regulations. As-built drawings help to confirm that the final construction complies with these codes, which can prevent legal issues or penalties.
Foundation for Future Modifications: When it comes time to renovate, expand, or retrofit a large-scale building, accurate as-built drawings serve as a reliable starting point. Without accurate documentation, future construction teams may encounter significant setbacks due to discrepancies between the actual building and the original plans.
Integrating As-Built Documentation into the COBie Database
For large-scale projects, managing facility data is a daunting task, especially when it comes to asset management. Integrating As-Built Documentation into the COBie Database simplifies this task by organizing information in a format that can be used throughout the building's lifecycle.
What is COBie?
COBie, or Construction Operations Building Information Exchange, is a data standard that helps project teams capture and manage asset data throughout the building’s lifecycle. It is used to organize data such as equipment lists, product data, warranties, and maintenance schedules. By integrating as-built documentation with COBie, facility managers and asset managers gain access to vital information needed for the building's operation and maintenance.
Benefits of Using COBie with As-Built Documentation
Streamlined Asset Management: Incorporating as-built documentation into COBie ensures that critical asset information is easily accessible. This helps facility managers keep track of equipment and building systems, simplifying maintenance and future renovations.
Enhanced Facility Maintenance: COBie allows facility managers to access information about building components such as HVAC systems, electrical systems, and plumbing. With accurate as-built documentation, these systems can be maintained more efficiently, ensuring they operate at peak performance.
Lifecycle Management: One of the main benefits of COBie is that it supports the entire lifecycle of a building. When combined with accurate as-built documentation, the database provides a robust resource for managing the building’s performance, maintenance, and operational costs over time.
Importance of Accurate As-Built Documentation for Asset Management
Effective Asset Management relies heavily on the accuracy of As-Built Documentation. In large-scale projects, where the cost of maintenance and operations can be substantial, having a reliable and detailed record of the building’s structure, systems, and assets is crucial.
How As-Built Documentation Enhances Asset Management
Informed Decision-Making: Asset managers can make more informed decisions about repairs, upgrades, and renovations with accurate as-built documents. They can easily reference the specific location of building components and assess their condition.
Improved Planning for Renovations: Accurate as-built documentation helps asset managers plan renovations more effectively. They can identify areas where systems are aging or where expansions are possible without disrupting existing systems.
Cost Control: With accurate data on the building's components, asset managers can more effectively budget for repairs and upgrades, minimizing the risk of unexpected expenses.
Sustainability and Efficiency: As-built documentation also plays a role in enhancing the sustainability and efficiency of a building. Accurate records allow asset managers to monitor the performance of energy systems and identify areas where efficiency can be improved, reducing operational costs and the building's carbon footprint.
Conclusion
Accurate As-Built Documentation is essential for large-scale construction projects. From improving communication between stakeholders to facilitating asset management and integrating with the COBie Database, as-built documentation ensures that buildings are well-documented, compliant, and easier to manage over their lifecycle. As-Built Drawings provide the detailed visual information needed for future projects, while the COBie Database organizes asset data for better facility management. Ultimately, investing in accurate as-built documentation helps ensure that large-scale projects are completed successfully and maintained efficiently in the long run.
0 notes
Text
how to build a digital music collection and stuff
spotify sucks aaaass. so start downloading shit!!
file format glossary
.wav is highest quality and biggest
.mp3 is very small, but uses lossy compression which means it's lower quality
.flac is smaller than .wav, but uses lossless compression so it's high quality
.m4a is an audio file format that apple uses. that's all i really know
downloading the music
doubledouble.top is a life saver. you can download from a variety of services including but not limited to apple music, spotify, soundcloud, tidal, deezer, etc.
i'd recommend ripping your music from tidal or apple music since they're the best quality (i think apple music gives you lossless audio anyway. .m4a can be both lossy and lossless, but from the text on doubledouble i assume they're ripping HQ files off apple music)
i also love love love cobalt.tools for ripping audio/video from youtube (they support a lot of other platforms too!)
of course, many artists have their music on bandcamp — purchase or download directly from them if you can. bandcamp offers a variety of file formats for download
file conversion
if you're downloading from apple music with doubledouble, it spits out an .m4a file.
.m4a is ok for some people but if you prefer .flac, you may wanna convert it. ffmpeg is a CLI (terminal) tool to help with media conversion
if you're on linux or macOS, you can use parameter expansion to batch convert all files in a folder. put the files in one place first, then with your terminal, cd into the directory and run:
for i in *.m4a; do ffmpeg -i "$i" "${i%.*}.flac"; done
this converts from .m4a to .flac — change the file extensions if needed.
soulseek
another way to get music is through soulseek. soulseek is a peer-to-peer file sharing network which is mainly used for music. nicotine+ is a pretty intuitive (and open-source) client if you don't like the official one.
you can probably find a better tutorial on soulseek somewhere else. just wanted to make this option known
it's bad etiquette to download from people without sharing files of your own, so make sure you've got something shared. also try to avoid queuing up more than 1-2 albums from one person in a row
tagging & organizing your music
tagging: adding metadata to a music file (eg. song name, artist name, album) that music players can recognize and display
if you've ripped music from a streaming platform, chances are it's already tagged. i've gotten files with slightly incorrect tags from doubledouble though, so if you care about that then you might wanna look into it
i use musicbrainz picard for my tagging. they've got pretty extensive documentation, which will probably be more useful than me
basically, you can look up album data from an online database into the program, and then match each track with its file. the program will tag each file correctly for you (there's also options for renaming the file according to a certain structure if you're into that!)
there's also beets, which is a CLI tool for... a lot of music collection management stuff. i haven't really used it myself, but if you feel up to it then they've got extensive documentation too. for most people, though, it's not really a necessity
how you wanna organize your music is completely up to you. my preferred filestructure is:
artist > album > track # track

using a music player
the options for this are pretty expansive. commonly used players i see include VLC, foobar2000, clementine (or a fork of it called strawberry), and cmus (for the terminal)
you can also totally use iTunes or something. i don't know what audio players other systems come with
i personally use dopamine. it's a little bit slow, but it's got a nice UI and is themeable plus has last.fm support (!!!)
don't let the github page fool you, you don't have to build from source. you can find the releases here
click the "assets" dropdown on the most recent release, and download whichever one is compatible with your OS
syncing
if you're fine with your files just being on one device (perhaps your computer, but perhaps also an USB drive or an mp3 player), you don't have to do this
you can sync with something like google drive, but i hate google more than i hate spotify
you can get a free nextcloud account from one of their providers with 2GB of free storage. you can use webDAV to access your files from an app on your phone or other device (documents by readdle has webDAV support, which is what i use)
disroot and blahaj.land are a couple providers i know that offer other services as well as nextcloud (so you get more with your account), but accounts are manually approved. do give them a look though!!
if you're tech-savvy and have an unused machine lying around, look into self-hosting your own nextcloud, or better yet, your own media server. i've heard that navidrome is a pretty good audio server. i unfortunately don't have experience with self-hosting at the moment so i have like zero advice to give here. yunohost seems to be a really easy way to manage a server
afterword
i don't know if any of this is helpful, but i just wanted to consolidate my personal advice in one place. fuck big tech. own your media, they could take it away from you at any moment
2K notes
·
View notes
Text
Lancer Tactics dialogue layout crisis of faith
(from this month's backer update)
Every so often, I'll run into something in development that eats away at me until it pushes me to a crisis of faith and I have a breakdown, burn down a bunch of work, and build something better from the ashes. These are moments of transformation and we're almost always able to come out the other side with something much better than what we started with.
This all sounds very dramatic until you take a step back and see the issue in question is just, like, the layout of a menu. But if medieval priests were able to have schisms over angels on pins I can have strong feelings about graphic design, dammit!
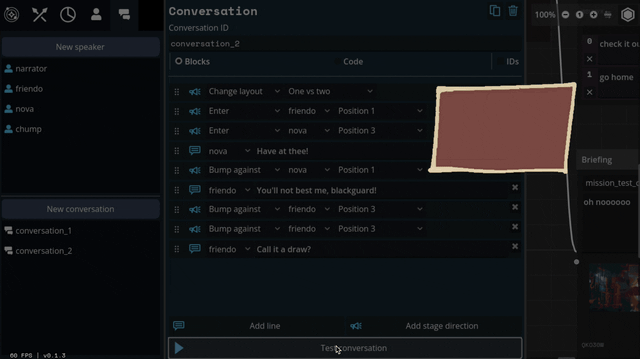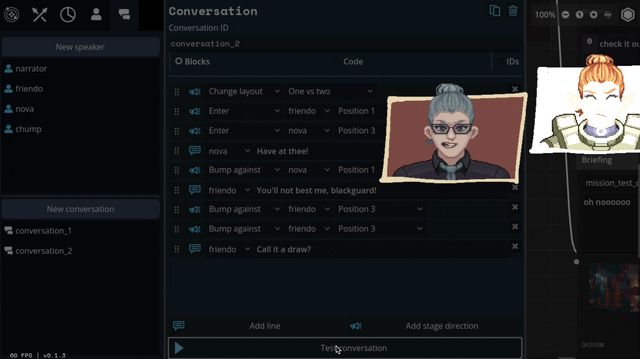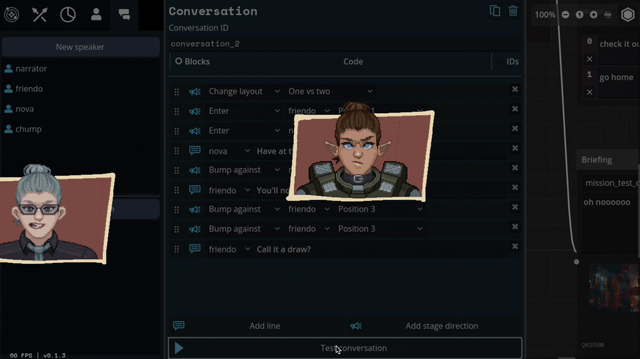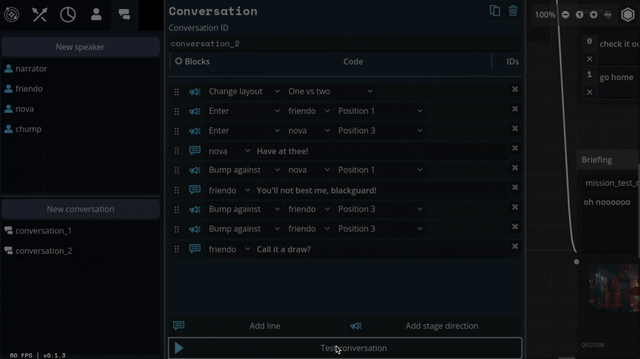
This month's episode revolved around how we're doing character dialogue. For reference the plan was to do a standard 4-slot visual-novel talking heads layout. I call it a 4-slot because there's usually four positions that characters can stand; two on the left, two on the right:
I had it ingame, and it was working. But... something felt off. Do you see the difference between every one of the above examples and this?
It's all about perspective, baby.
Answer: all the character art in those examples are drawn at a slight angle so they can be flipped back and forth to be made like they're looking at each other.
Trying to do this with the perspective we chose early — straight on — makes for a chorus line of weirdos who are looking directly into your soul as they ostensibly chat with each other. Credulity is strained; the illusion of these puppets interacting in the same space is paper-thin.
(I was skeptical of choosing this perspective for this reason, but we ultimately went with it to make the customizable assets in the portrait maker easier to fit together)
We tried a bunch of different layouts, but they all at least one of these problems:
they'd stare into your soul while ostensibly directing comments elsewhere.
they felt like text messages; this would be fine if that's what we were going for, but we wanted something that could represent face-to-face conversations. (Tactical Breach Wizards was able to pull this style off because they had little 3D dioramas to go along with it)
or, most damning of all, they felt like zoom calls.

So, my heart aflutter and spirit in want, I spent a day doing a research dive into various dialogue layouts (bless the Game UI Database!) to see if any other games had managed to pull this character art perspective off. I ended up with this massive non-chronological taxonomic tree:
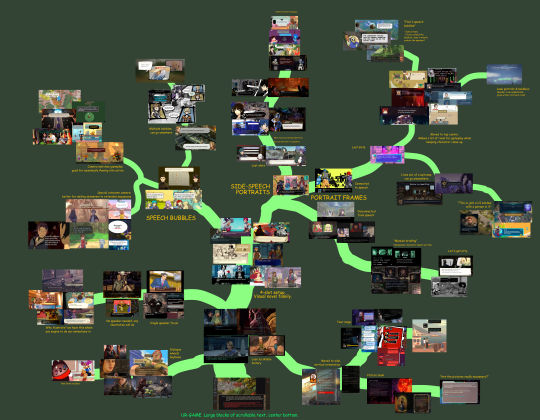
(fullsize here)
The type of layout that particularly caught my eye was this style where each character had their own little box. These layouts borrow a concept from comic books called "closure" where the space and time between characters are left blank. Freed from the constraints of trying to simulate a single space, these layouts allow the reader to fill in the blanks with something that feels more true-to-life than anything we'd be able to render ourselves.
I was especially impressed with the dynamism of Tales of Symphonia and The World Ends With You; rather than sticking to single slots they would animate the entire panels moving around to indicate motion an relative position of characters.
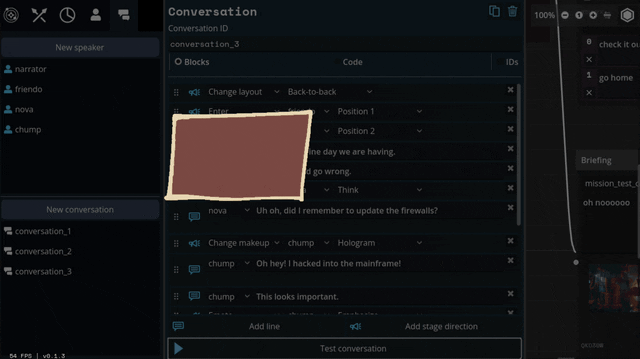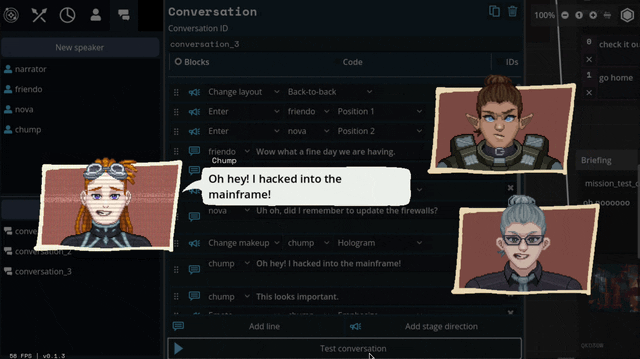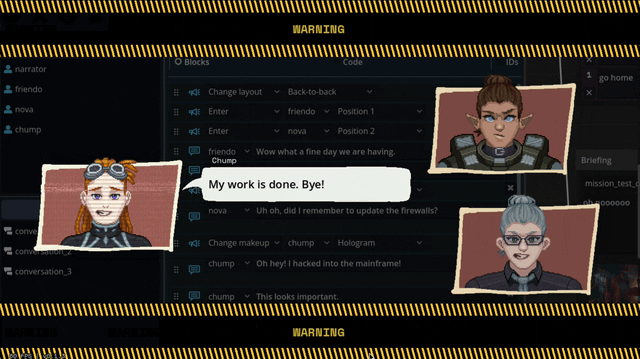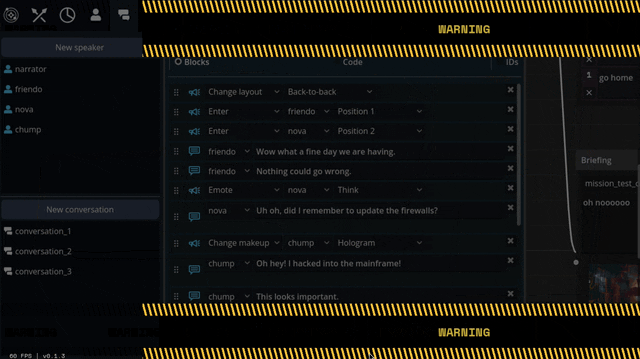
So we threw out the old code and copied them. Here's what we've come up with:
We'll be able to have portraits interact, like smacking each other (I felt like a kid hitting two action figures together, lol)
We can also apply effects like princess-leia-holograms and full-screen "lighting" effects like warning banners:
Carpenter and I came up with a number of arrangements that the portraits can smoothly transition between:

I've also implemented support for choices during a dialogue, potentially leading to branching paths.

Overall, I feel SO much better about this system than our initial designs. It might feel a little more cartoony, but I think we're making a cartoony game so that's not a problem.
Whew. We bit a lot off to chew with this project. I feel like I just made a second visual novel game engine inside of the first. Fingers crossed that it all ends up worth it.
475 notes
·
View notes
Text
And who would've thought... it figures
My attention has been very recently drawn to this very telling non-announcement:


[Source: https://hq.rostr.cc/insider/news/the-fratellis-sign-wtth-toura-toura; announcement published on February 24, 2025]
And surely enough, this was quietly confirmed by Toura Toura on the company's socials. It would also seem they have been collaborating for a while, now, even before the info was disclosed:

[Source: https://www.instagram.com/ltdtouratoura/]

[Source: https://www.facebook.com/touratourahq/]
It is even on the Booking Agent Info professional database:


[Source: https://bookingagentinfo.com/celebrity/the-fratellis/]
To quote: 'The Fratellis' managers used to be Anthony McGill' (..)'. Operative concept - 'used to'. Past tense. The three of them managers seem to have vanished into thin air. Oh my, what on Earth could have happened?
According to Companies' House, UK Government company register, Kevin Fitzgerald is the sole owner of two companies. The first company is Toura Toura Ltd, which nature of business is 'sound recording and music publishing activities':


[Source: https://find-and-update.company-information.service.gov.uk/company/11826082]
... and Toura Toura Festivals Ltd, which nature of business is 'performing arts' and which is doing just slightly better - its paperwork is ok, for the time being:


[Source: https://find-and-update.company-information.service.gov.uk/company/12502492]
The accounts' analysis is interesting, in a way, for there seems to have been very little (if any) turnover/profit in both companies for the last three years, with very mediocre balance sheet reports to boot:

... and...

Anyways, I am rather tempted to follow-up and report if anything new pops in, which might happen rather shortly, with last year's report overdue for the first company and due in about two weeks for the second one.
You might be forgiven of superficially thinking this entrepreneurial profile looks like another person's (ahem). It doesn't: his net assets are positive, despite the reporting negligence as far as Toura Toura Ltd is concerned. And the COVID pandemic might explain those financials, at least partially. For instance, in May 2023, Toura Toura Festivals landed in hot water, when the Wolverhampton Council completely let them down, canceling for the third year in a row the city's Creation Day Festival:

[Source and more details, here: https://accessaa.co.uk/toura-toura-festivals-seeking-legal-advice-after-creation-day-postponed-for-third-year-running/]
The man seems to have a good reputation in the business. I found this pre-COVID interview (February 2020) for a specialized blog very honest and quite endearing - excerpts follow:


[Source: https://vanadianavenue.co.uk/2020/02/12/indieterria-meets-kevin-fitzgerald-of-toura-toura/ ]
And then look who's on The Fratellis' following Instagram roster...?

[Source: https://www.instagram.com/thefratellis/following/]
Alan McGee, Fitzgerald's providential first client! Yes. Connections are always important, irrespective of the industry, but perhaps even more in that particular industry.
I strongly suggest you'd give five minutes to Mr. Fitzgerald's story of a single dad who has been through loss and found the power to reinvent himself. Clearly a very hands-on, proactive work ethic and perhaps the reason The Fratellis signed with him, after all?
So you see, I think there is a difference between 'working in the shadows' and being non-existent/not giving a flying fuck. I even surprised myself feeling glad for a perfectly unknown person's apparent comeback.
You might also think McGill's got other clients?
Chances are he doesn't, plus his profile isn't even claimed - now, why would that be?

[Source: https://bookingagentinfo.com/managers/anthony-mcgill/]
For comparison purposes: the profile is checked by Fitzgerald himself and the clients are there. I didn't bother to look further - it's crystal clear.


[Source: https://bookingagentinfo.com/managers/kevin-fitzgerald/]
You knew this will immediately follow, right?
youtube
You're welcome.
PS: Thank you for the tip. As always, superb and easy to follow. You know who you are 😘😘😘😘.
165 notes
·
View notes
Text
Th’ell ya’ doing here, lady? (Monty x reader)
Chapter 2. Who th’ell are ya’, lady?
Summary
Oh no!
It looks like you’re not a registered character in the Plex’s system, how unfortunate.
Good thing Montgomery Gator here realized you aren’t human! He will be in charge of escorting you back to the daycare.
Warnings: Mild swearing.
Headcanons used:
Monty is glad to be a rockstar but is jealous of Feedy being fan favorite.
Monty is very gentle with children.
“It’s past closing hours, lady, what th’ell ‘ya doing here?”
—————
You stared up at the much larger animatronic, optics widened in terror. If your voice box was operational, you’d probably be screaming by now. You felt your CPU buzz loudly inside your chestplate, frantically calculating an escape route while you stood frozen. The gator was massive, being a good few feet taller than you, and looked like he could easily bench press a car if he wanted to.
You shakily brought your hands up and in a placating gesture and shook your head, trying to signal that you meant no harm. You glanced behind the gator, trying to judge the distance you’d have to run if you could slip past him. This only seemed to aggravate the already aggressive animatronic.
Monty felt his security module continuously ping his processor on the steps he needed to take now that he has located a trespasser to ‘keep Freddy Fazbear’s Mega Pizza Plex a safe place for all families to enjoy.’ He blinked at her rapid movements, becoming irritated if not confused on what you were trying to convey other than a frantic gesture.
He internally pinged Vanessa about the situation, needing a human employee to process any human infringement.
Bringing his attention back to the shorter animatronic, he spoke up. “You stay here, an officer is going ta come talk to ya’ on how you’ll be processed fer trespassing on private property.” He said, pulling back a bit as he kept his harsh gaze on you, the response automatic and robotic as ever.
You winced at it’s scowl aimed towards you. At the mention of an officer getting involved in the situation, you began to panic. It hasn’t even asked who you we’re!
He stared at you for a moment longer before he noticed that you weren’t quite…well, human.
“…What in the—?”
He jerked his head back to get a better look before quickly running a full body scan. When his system revealed to him that he was, in-fact, talking to another animatronic, he didn’t quite know what to do.
Why weren’t you in his database? Surely they would’ve added the ID of a new member to the plex when they issued you. …Or maybe not, heck, this corporation isn’t known for being the nicest to their… assets.
The gator stared at you for another tense moment before stepping back, letting go of the recharge station. A flicker of embarrassment was present in his face but was quickly masked by a scowl.
“Who th’ell are ya, lady?” He asked, crossing his arms as he stared you down. “I ain’t ever seen ya ‘round here before.”
You began to sign frantically, using your digits to convey what an answer to what was asked of you.
‘I’m the Daycare Attendant’s helper! Sorry if I intruded, I didn’t mean to wander so far or know that it would cause any problems.’ You looked up at the gator animatronic apologetically, after you gave him your name, equally embarrassed as you held your hands close to your chest.
Monty felt his scowl soften a bit when he realized you couldn’t speak. His optics quickly caught on to your ASL, already having been downloaded in his programming as a part of the ‘PCA’ part of his purpose during events. He decided not to comment on your lack of speech.
“You from the Daycare, huh? You don’t look as creepy as those clowns, heard management’s gonna to do something ‘bout their faceplates soon.” He replied, tilting his head to the side as he grimaced at the thought of the Daycare Attendant’s appearance.
Whoever designed their likeness sure didn’t know what they were doing, those bots look creepy as hell. They did them so dirty. He quickly linked a quick picture of you and your name into a file for later.
“Didn’t even have ya in my system. I’m guessing you’re new then.” He added, letting out a hiss of pressured air past his nostrils in a pretend huff.
That made sense. The human staff you’ve interacted with didn’t seem particularly interested in any of the bots. To leave out coding your addition to the animatronic staff does seem like something the would do, even intentionally.
“Moon’s allowed to come out of the Daycare during his rounds, he must be near Roxy Raceway by now. Sun, on the other hand, his programming won’t let the bot set foot outta the place, heck, I don’t think he can even think about doing so.” The gator mused, feeling himself relax slowly while he pinged Vanessa once again, this time to take back his request.
“I don’t know nothing ‘bout you though, if ya can or can’t.” He said, his scrutinizing gaze remaining fixed on you as he waited for a reply.
You blinked once, twice. Adverting your gaze, knowing full well that your programming doesn’t exactly specify whether or not you’re allowed to leave the daycare. You do, however, have a high clearance than Sun, being that you can leave without your joints locking up as soon as you crossed the Daycare doors.
You shrugged, deciding to change the topic.
‘You’re pretty intimidating, all the animatronics here as tall as you?’ Okay, maybe not the best way to divert the subject, but an attempt nonetheless.
The gator snorted at your words. If there’s one thing he’s good at, it’s being intimidating. He brought a hand up to tilt his glasses down his snout and gave the shorter animatronic a grin. “Most of us, yeah, we’re pretty tall, modeled after th’ same endo.” He said, sliding his purple shades back up his snout.
‘Well, I may not be tall, but I am softer than most animatronics here. They gave me a complete silicone casing and memory foam pads on my hands.’ You signed, bringing your hands up for demonstration. ‘You can see for yourself.’
Monty’s smile faltered at your trusting gesture, looking down at her extended hand with a surprised expression. His jaw clicked shut as he processed your offer. You was offering to let him touch you. Him? Slowly, the bulky animatronic brought his clawed hand up to gently rest it in yours. Despite his reputation for being a destructive individual, the gator animatronic can be gentle. He’s gentle with the children, he’s never hurt one. She was true to her word, her servos were, in-fact, soft, silicone coating her palms.
A slow thumping noise was heard behind the gator and he quickly pulled away, an embarrassed expression painting his mostly static face. His tail had been wagging, and he mentally cursed the the programmer that had decided to add that involuntary reaction into his software. He looked away and crossed his arms, scowling once again.
You quirked a brow in amusement at his abrupt motion, effectively putting some distance between the both of you.
“Yeah, well, ya should probably head back to the daycare if ya aren’t on patrol, it’s dangerous out here.” He grumbled.
You agreed, it was probably best for you to return to the daycare. However, you’d like to catch the gator’s name before you left, he was the first person outside your daycare duties that you’ve meet, after all.
‘Right, of course, but, before I leave, may I get your name?’ You signed, waiting patiently for his reply.
He glanced back at you, narrowing his eyes. Did you really not know who he was? Did you not know who the band was? Wait…then that means you don’t know who Freddy is, or about his reputation, which also means that you can’t compare him to Freddy like everyone else. The opportunity just walked right into his very hands, an opportunity he’s not going to miss.
Monty turned to face you, brining a clawed digit to tilt his bright, purple shades down and winked at you. “Name’s Montgomery, Montgomery Gator, but ya can call me Monty, doll-face.” He said, knowing this is his shot on making a memorable introduction with his southern charm.
You felt your fans kick up a notch at the pet name, but payed no other mind to it.
“I’m the band’s bassist, you could say I’m a fan favorite, got my own golf course an’ all.” The gator drawled rather arrogantly, brining his hands to his hips as he grinned toothily.
“You should come by some time, I’ll show ya how ta play, it’s on the house.” Monty offered smoothly, looking down at you through the violet hue of his signature shades.
You smiled at his offer, perhaps you should make going out of the daycare part of your routine. It would be a nice change.
‘That would be nice.’
His grin widened.
As you turned on your heel, you hesitated. You really didn’t want to get lost again, and Monty did seem like a person who knew the place well. Turning back towards him, you signed.
“Nah, don’t worry about it, I know this place like th’ strings on my bass.” He said, brushing you off as he brushed one of his hands over his mohawk in a causal manner. “I can help you out, easy, wouldn’t want you to run into any other members of the band and throw yourself into a locker or something.” Monty teased, a loud bark of laughter escaping him before as he walked past you, already making his way to the Daycare.
He also didn’t want you running into Freddy, but the gator would never admit that. If you met him, he’s certain she’d realize how much of a mess the Gator actually is plus how much better the bear was compared to him. You’d forget all about Montgomery Gator. He can’t let that happen, he won’t let that happen. Shoving the dark thought back into the depths of his processor, he focused on the situation at hand.
“‘Sides, Moon can cover for me, he does owe me one.” The gator added as he looked back at her from over his shoulder with a grin.
“Get over here, short stack.” He called, gesturing for her to follow him.
You quickly followed after him, running to catch up to the larger animatronic. Falling into step beside him, you glanced up at the gator. His color scheme was a lot different to Sun and Moon’s, his attire as well. While the Daycare attendant sported s circus themed outfit, the glamrock wore a much more eighties-esque type aesthetic, reminiscent of the 80’s rockstar, David Bowie.
He glanced down at you and you adverted your gaze quickly, embarrassed to have been staring. Deciding that the floor was much more interesting, you kept your eyes glued to the tiles. The gator chuckled, much to your chagrin. Monty was used to the attention, either good or bad, having eyes on him wasn’t a new feeling, rather just as normal as recharging for him.
As you two passed the band’s green rooms, you perked, pointing at the show rooms as you turned your head to look up at the gator.
Using your other hand to sign at him simply, you asked. ‘Your friends?’
“Hm? Oh, yeah, that’s where th’ band and I have our showrooms.” Monty replied, keeping his optics trained on you for any other signs.
His tail slowly swept back and forth behind him, another indicator of his better mood. The gator’s eyes landed on Freddy’s room, and he fought back the urge to bare his teeth, instead, smiling down at the little lady.
“Maybe I can show ya ‘round some time, give ya a tour and all that jazz.” Monty added, glancing at his room’s door.
The bulky animatronic grimaced a bit, optics quickly switching to his room’s visual feed. He’d have to get a S.T.A.F.F. bot to clean up the mess he made after his temper tantrum earlier in the day. He returned his gaze back to the shorter animatronic as they neared the Daycare entrance.
“If you’re lucky, I might even take a picture with ya.” The reptilian animatronic said with a grin. “You’ll be a certified Montgomery Gator fan!”
You clapped your hands excitedly, relying more on your body language and actions to get your mood across. That would be nice, wouldn’t it?
When your eyes landed on the Daycare’s doors, you balked. You didn’t want to end your conversation with Monty just yet, you’d just gotten to know him.
‘Will is see you again?’
The animatronic gator blinked down at the you, surprise evident on his face as his optics widened. You wanted to see him again? Him, Montgomery Gator? Suck on that Fazbear!
With a toothy grin, he brought his hand to your forehead, flicking your faceplate, making you lurch back with a surprised expression. “Sure ya will, doll.”
Stepping back, he looked past the netted wall that separated the daycare from the gift shop area. “Say hi to Sun for me, alright?” Monty said, returning his focus to you.
You rubbed at your forehead, watching him with narrowed eyes. This made Monty grin wider as he continued.
“And don’t let me catch you wandering where you shouldn’t, just ping me if you need someone to—” he gave her a mischievous grin, “‘assist a new bot with directions’.”
He quickly found your data signature in the Plex’s network and shot you a quick message, just a simple ‘hey’. “You can use th’ network to message me after hours or during your break, usually only security guards use it, but it’s pretty nifty for us bots to stay in touch.”
You jerked a bit at the message popping up in your visual feed before grinning, giving him a thumbs up.
”I’ll see you—“
The daycare doors opened suddenly, cutting the animatronic gator off. You both turned to look at what had interrupted your little conversation.
“Sunshine! I’m so glad you’re back, I got worried when I couldn’t find you anywhere! Moon went out to look for you and—…” the sun-themed animatronic tilted his faceplate when he noticed the band’s bassist standing next to you.
His milky white optics seemed to darken, though perhaps that was just the lighting. “Oh! You brought the gator…with you.”
#monty fnaf#fnaf security breach#fnaf#fnaf daycare attendant#fnaf sun#fnaf fanfic#Monty#monty x reader#monty x y/n#fanfiction#TYDHL
30 notes
·
View notes
Text
1. Structural Framework of the Privilege Visa System
1.1 Legislative Foundations
Established under Royal Thai Police Order No. 327/2557 (2014)
Administered by Thailand Privilege Card Company Limited (TPC), a subsidiary of the Tourism Authority of Thailand
Operates parallel to but distinct from the Elite Visa program
1.2 Program Evolution
2014 Launch: Initial 5-year membership structure
2019 Restructuring: Introduction of tiered benefits system
2023 Enhancements: Digital integration and expanded concierge services
2. Comprehensive Benefit Structure
2.1 Immigration Advantages
Dedicated Immigration Channel: 24/7 access at 8 international airports
Multiple Re-entry Permit: Embedded in visa validity
90-Day Reporting: Optional (can be handled by TPC staff)
2.2 Lifestyle Concierge Services
Real Estate Acquisition Support: Curated property portfolio access
Education Placement: Partnership with 17 international schools
Medical Coordination: Priority at 38 partner hospitals
2.3 Financial Infrastructure
Thai Bank Account: Expedited opening with minimum deposit waiver
Tax Advisory: Complimentary 10-hour annual consultation
Currency Exchange: Preferred rates at Siam Commercial Bank
3. Eligibility & Application Scrutiny
3.1 Vetting Criteria
Financial Health Check:
Liquid assets verification (minimum THB 3M equivalent)
Source of funds audit
Background Clearance:
Interpol database cross-check
Thai security agency review
3.2 Document Requirements
Primary Applicant:
10-year passport history
Certified financial statements
Health insurance (USD 100,000 coverage)
Dependents:
Legalized marriage/birth certificates
Academic records (for student dependents)
3.3 Approval Timeline
StageDurationKey ConsiderationsPreliminary Screening7-10 daysDocument completeness checkFinancial Verification15-20 daysBank confirmation processSecurity Clearance30-45 daysEnhanced for certain nationalitiesFinal Issuance5 daysCard production and delivery
4. Tax & Legal Implications
5.1 Residency Status
Non-Tax Resident: For members spending <180 days/year
Tax Resident: Automatic after 183 days with additional reporting
4.2 Asset Management
Property Ownership: Condo purchases permitted under foreign quota
Investment Vehicles: Access to SET through special foreign investor accounts
4.3 Inheritance Planning
Will Registration: Mandatory for property holdings
Succession Tax: 10% on Thai-situs assets exceeding THB 100M
5. Operational Realities & Limitations
5.1 Practical Constraints
Work Prohibition: No employment rights without separate work permit
Business Activities: Passive investment only
Political Activities: Complete restriction
5.2 Service Level Agreements
Response Times:
Emergency: 30 minutes
Standard: 4 business hours
Guarantees:
Airport processing within 15 minutes
Medical appointment scheduling within 24 hours
6. Comparative Analysis with Competing Programs
ParameterThailand GOLDMalaysia MM2HUAE Golden VisaMinimum StayNone90 days/year1 day every 6 monthsHealthcareTHB 500K annual creditMandatory insurancePremium coverageEducation15% tuition discountLocal school accessInternational optionsPath to PRNoAfter 10 yearsAfter 5 years
7. Strategic Utilization Framework
7.1 Optimal User Profiles
High-Net-Worth Retirees: Age 50+ with global income streams
Global Nomads: Location-independent entrepreneurs
Family Offices: Multi-generational wealth management
7.2 Financial Optimization
Currency Hedging: THB-denominated asset allocation
Tax Year Planning: Residency day counting system
Insurance Structuring: International policy portability
8. Emerging Program Developments
8.1 2024 Enhancements
Digital Nomad Add-on: Remote work endorsement (Q3 rollout)
Crypto Wealth Verification: BTC/ETH acceptance for qualification
Regional Hub Access: Expanded services in Chiang Mai and Phuket
8.2 Pending Regulatory Changes
Family Office Recognition: Special provisions under discussion
Art Import Privileges: Proposed duty-free allowances
Yacht Registration: Streamlined process for members
9. Critical Evaluation & Recommendations
9.1 Value Proposition Assessment
Strengths:
Unmatched concierge infrastructure
Banking and financial access
Healthcare coordination
Weaknesses:
No path to permanent residency
Rigid membership tiers
Limited business activity
9.2 Implementation Checklist
Pre-Application:
6-month financial trail preparation
Dependent document legalization
Active Membership:
Annual benefit utilization audit
Tax residency monitoring
Renewal Planning:
180-day advance evaluation
Tier upgrade analysis
Final Verdict:
The GOLD membership represents Thailand's most sophisticated non-immigrant residency solution for affluent individuals prioritizing lifestyle quality over economic activity rights. While not a pathway to citizenship, its operational advantages and service infrastructure remain unparalleled in Southeast Asia for those meeting the financial thresholds.
#thailand#immigration#thai#visa#visainthailand#thaivisa#thailandvisa#thailandprivilegevisa#privilegevisainthailand#thailandprivilegevisagoldmembership#thaipr#immigrationinthailand#thaiimmigration
4 notes
·
View notes
Text
Pro-Kremlin media outlets claim that US and Ukrainian forces were instrumental in toppling al-Assad, the EU East Stratcom Task Force reported on Thursday morning. The task force was set up by the EU in 2015 as part of the European External Action Service (EEAS). Its flagship project is a database of articles on fake news. From the start of the war in Ukraine, it has been publishing weekly news about Russia’s disinformation and information manipulation. While the Syrian people and most of the world celebrated the ending of the Assad family’s 54-year-long dictatorship, Moscow saw it differently. At the Doha Forum in Qatar on 7 December, a day before the fall of the regime and Assad’s escape to Russia, Foreign Minister Lavrov was quick to blame the US and its NATO allies for a global plot. Given the Kremlin’s backing of the dictatorship during the civil war in Syria, the official Russian line deployed on all main state outlets was not to give it prominent coverage. In coverage of the topic, the line was to stick with the usual practice of blaming the US as the mastermind behind the events. Russian media also claimed that Ukraine had supported terrorist groups in Syria and that Israel could be behind them. The Assad regime collapsed after a surprise military offensive by the Islamist militia Hayat Tahrir al-Sham (HTS). Encouraged by Turkey, the rebels took advantage of the opportunity when Assad’s allies Iran and Hezbollah had been weakened in the war with Israel and agreed to a ceasefire in Lebanon. Russia was unable to divert troops and intervene because of its war of aggression against Ukraine. Up until the fall of the Assad regime, Russia insisted on the so-called "Astana format" of negotiations (Russia, Iran, Turkey) to manage developments in Syria and bring about a political solution. This format is now recognized by Kremlin as lost. Both Russia and Iran, who supported the regime, have been forced to leave Syria and lost their military assets there.
continue reading
6 notes
·
View notes
Text
What Is The Difference Between Web Development & Web Design?
In today’s world, we experience the growing popularity of eCommerce businesses. Web designing and web development are two major sectors for making a difference in eCommerce businesses. But they work together for publishing a website successfully. But what’s the difference between a web designers in Dubai and a web developer?
Directly speaking, web designers design and developers code. But this is a simplified answer. Knowing these two things superficially will not clear your doubt but increase them. Let us delve deep into the concepts, roles and differentiation between web development and website design Abu Dhabi.

What Is Meant By Web Design?
A web design encompasses everything within the oeuvre of a website’s visual aesthetics and utility. This might include colour, theme, layout, scheme, the flow of information and anything related to the visual features that can impact the website user experience.
With the word web design, you can expect all the exterior decorations, including images and layout that one can view on their mobile or laptop screen. This doesn’t concern anything with the hidden mechanism beneath the attractive surface of a website. Some web design tools used by web designers in Dubai which differentiate themselves from web development are as follows:
● Graphic design
● UI designs
● Logo design
● Layout
● Topography
● UX design
● Wireframes and storyboards
● Colour palettes
And anything that can potentially escalate the website’s visual aesthetics. Creating an unparalleled yet straightforward website design Abu Dhabi can fetch you more conversion rates. It can also gift you brand loyalty which is the key to a successful eCommerce business.
What Is Meant By Web Development?
While web design concerns itself with all a website’s visual and exterior factors, web development focuses on the interior and the code. Web developers’ task is to govern all the codes that make a website work. The entire web development programme can be divided into two categories: front and back.
The front end deals with the code determining how the website will show the designs mocked by a designer. While the back end deals entirely with managing the data within the database. Along with it forwarding the data to the front end for display. Some web development tools used by a website design company in Dubai are:
● Javascript/HTML/CSS Preprocessors
● Template design for web
● GitHub and Git
● On-site search engine optimisation
● Frameworks as in Ember, ReactJS or Angular JS
● Programming languages on the server side, including PHP, Python, Java, C#
● Web development frameworks on the server side, including Ruby on Rails, Symfony, .NET
● Database management systems including MySQL, MongoDB, PostgreSQL
Web Designers vs. Web Developers- Differences
You must have become acquainted with the idea of how id web design is different from web development. Some significant points will highlight the job differentiation between web developers and designers.
Generally, Coding Is Not A Cup Of Tea For Web Designers:
Don’t ever ask any web designers in Dubai about their coding knowledge. They merely know anything about coding. All they are concerned about is escalating a website’s visual aspects, making them more eyes catchy.
For this, they might use a visual editor like photoshop to develop images or animation tools and an app prototyping tool such as InVision Studio for designing layouts for the website. And all of these don’t require any coding knowledge.
Web Developers Do Not Work On Visual Assets:
Web developers add functionality to a website with their coding skills. This includes the translation of the designer’s mockups and wireframes into code using Javascript, HTML or CSS. While visual assets are entirely created by designers, developer use codes to implement those colour schemes, fonts and layouts into the web page.
Hiring A Web Developer Is Expensive:
Web developers are more expensive to hire simply because of the demand and supply ratio. Web designers are readily available as their job is much simpler. Their job doesn’t require the learning of coding. Coding is undoubtedly a highly sought-after skill that everyone can’t entertain.
Final Thoughts:
So if you look forward to creating a website, you might become confused. This is because you don’t know whether to opt for a web designer or a developer. Well, to create a website, technically, both are required. So you need to search for a website design company that will offer both services and ensure healthy growth for your business.
2 notes
·
View notes
Text
Structured Query Language (SQL): A Comprehensive Guide
Structured Query Language, popularly called SQL (reported "ess-que-ell" or sometimes "sequel"), is the same old language used for managing and manipulating relational databases. Developed in the early 1970s by using IBM researchers Donald D. Chamberlin and Raymond F. Boyce, SQL has when you consider that end up the dominant language for database structures round the world.
Structured query language commands with examples
Today, certainly every important relational database control system (RDBMS)—such as MySQL, PostgreSQL, Oracle, SQL Server, and SQLite—uses SQL as its core question language.
What is SQL?
SQL is a website-specific language used to:
Retrieve facts from a database.
Insert, replace, and delete statistics.
Create and modify database structures (tables, indexes, perspectives).
Manage get entry to permissions and security.
Perform data analytics and reporting.
In easy phrases, SQL permits customers to speak with databases to shop and retrieve structured information.
Key Characteristics of SQL
Declarative Language: SQL focuses on what to do, now not the way to do it. For instance, whilst you write SELECT * FROM users, you don’t need to inform SQL the way to fetch the facts—it figures that out.
Standardized: SQL has been standardized through agencies like ANSI and ISO, with maximum database structures enforcing the core language and including their very own extensions.
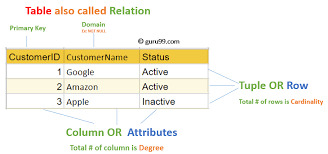
Relational Model-Based: SQL is designed to work with tables (also called members of the family) in which records is organized in rows and columns.
Core Components of SQL
SQL may be damaged down into numerous predominant categories of instructions, each with unique functions.
1. Data Definition Language (DDL)
DDL commands are used to outline or modify the shape of database gadgets like tables, schemas, indexes, and so forth.
Common DDL commands:
CREATE: To create a brand new table or database.
ALTER: To modify an present table (add or put off columns).
DROP: To delete a table or database.
TRUNCATE: To delete all rows from a table but preserve its shape.
Example:
sq.
Copy
Edit
CREATE TABLE personnel (
id INT PRIMARY KEY,
call VARCHAR(one hundred),
income DECIMAL(10,2)
);
2. Data Manipulation Language (DML)
DML commands are used for statistics operations which include inserting, updating, or deleting information.
Common DML commands:
SELECT: Retrieve data from one or more tables.
INSERT: Add new records.
UPDATE: Modify existing statistics.
DELETE: Remove information.
Example:
square
Copy
Edit
INSERT INTO employees (id, name, earnings)
VALUES (1, 'Alice Johnson', 75000.00);
three. Data Query Language (DQL)
Some specialists separate SELECT from DML and treat it as its very own category: DQL.
Example:
square
Copy
Edit
SELECT name, income FROM personnel WHERE profits > 60000;
This command retrieves names and salaries of employees earning more than 60,000.
4. Data Control Language (DCL)
DCL instructions cope with permissions and access manage.
Common DCL instructions:
GRANT: Give get right of entry to to users.
REVOKE: Remove access.
Example:
square
Copy
Edit
GRANT SELECT, INSERT ON personnel TO john_doe;
five. Transaction Control Language (TCL)
TCL commands manage transactions to ensure data integrity.
Common TCL instructions:
BEGIN: Start a transaction.
COMMIT: Save changes.
ROLLBACK: Undo changes.
SAVEPOINT: Set a savepoint inside a transaction.
Example:
square
Copy
Edit
BEGIN;
UPDATE personnel SET earnings = income * 1.10;
COMMIT;
SQL Clauses and Syntax Elements
WHERE: Filters rows.
ORDER BY: Sorts effects.
GROUP BY: Groups rows sharing a assets.
HAVING: Filters companies.
JOIN: Combines rows from or greater tables.
Example with JOIN:
square
Copy
Edit
SELECT personnel.Name, departments.Name
FROM personnel
JOIN departments ON personnel.Dept_id = departments.Identity;
Types of Joins in SQL
INNER JOIN: Returns statistics with matching values in each tables.
LEFT JOIN: Returns all statistics from the left table, and matched statistics from the right.
RIGHT JOIN: Opposite of LEFT JOIN.
FULL JOIN: Returns all records while there is a in shape in either desk.
SELF JOIN: Joins a table to itself.
Subqueries and Nested Queries
A subquery is a query inside any other query.
Example:
sq.
Copy
Edit
SELECT name FROM employees
WHERE earnings > (SELECT AVG(earnings) FROM personnel);
This reveals employees who earn above common earnings.
Functions in SQL
SQL includes built-in features for acting calculations and formatting:
Aggregate Functions: SUM(), AVG(), COUNT(), MAX(), MIN()
String Functions: UPPER(), LOWER(), CONCAT()
Date Functions: NOW(), CURDATE(), DATEADD()
Conversion Functions: CAST(), CONVERT()
Indexes in SQL
An index is used to hurry up searches.
Example:
sq.
Copy
Edit
CREATE INDEX idx_name ON employees(call);
Indexes help improve the performance of queries concerning massive information.
Views in SQL
A view is a digital desk created through a question.
Example:
square
Copy
Edit
CREATE VIEW high_earners AS
SELECT call, salary FROM employees WHERE earnings > 80000;
Views are beneficial for:
Security (disguise positive columns)
Simplifying complex queries
Reusability
Normalization in SQL
Normalization is the system of organizing facts to reduce redundancy. It entails breaking a database into multiple related tables and defining overseas keys to link them.
1NF: No repeating groups.
2NF: No partial dependency.
3NF: No transitive dependency.
SQL in Real-World Applications
Web Development: Most web apps use SQL to manipulate customers, periods, orders, and content.
Data Analysis: SQL is extensively used in information analytics systems like Power BI, Tableau, and even Excel (thru Power Query).
Finance and Banking: SQL handles transaction logs, audit trails, and reporting systems.
Healthcare: Managing patient statistics, remedy records, and billing.
Retail: Inventory systems, sales analysis, and consumer statistics.
Government and Research: For storing and querying massive datasets.
Popular SQL Database Systems
MySQL: Open-supply and extensively used in internet apps.
PostgreSQL: Advanced capabilities and standards compliance.
Oracle DB: Commercial, especially scalable, agency-degree.
SQL Server: Microsoft’s relational database.
SQLite: Lightweight, file-based database used in cellular and desktop apps.
Limitations of SQL
SQL can be verbose and complicated for positive operations.
Not perfect for unstructured information (NoSQL databases like MongoDB are better acceptable).
Vendor-unique extensions can reduce portability.
Java Programming Language Tutorial
Dot Net Programming Language
C ++ Online Compliers
C Language Compliers
2 notes
·
View notes
Text
The Trump administration is replacing some of the nation’s top tech officials with Silicon Valley talent tied to Elon Musk and companies associated with Peter Thiel. This could make it easier for Musk’s so-called Department of Government Efficiency (DOGE) engineers to gain access to sensitive government systems, sources and experts say.
Over the past few weeks, several Musk-aligned tech leaders have been installed as chief information officers, or CIOs, at the Office of Management and Budget, the Office of Personnel Management, and the Department of Energy. CIOs manage an agency’s information technology and oversee access to sensitive databases and systems, including classified ones.
"Federal agency CIOs have authority over all agency asset management, which includes software used to monitor civil servant laptops and phones,” a former Biden official with firsthand knowledge of a CIO’s capabilities tells WIRED. “CIO shops manage and control IT access to all agency databases and systems, and have oversight over all the IT contracts per FITARA [the Federal Information Technology Acquisition Reform Act]. They have lots of IT budget and head count that Musk might want to take over. In agencies, CIOs are functionally as powerful as OIGs [the Office of Inspectors General].”
So far, these new CIOs have all been appointed. At most agencies, however, the position is filled by career civil servants. Last week, the Office of Personnel Management (OPM) issued a new memo that would reclassify those nonpartisan roles, essentially allowing the Trump administration to replace CIOs at will in order to better carry out its agenda. The appointments made so far may serve as an indicator of who will take over IT departments throughout the government once the order goes into effect.
Late last month, Gregory Barbaccia was hired as the federal chief information officer, a position within the Office of Management and Budget (OMB), which oversees the performance of all federal agencies and administers the budget. Barbaccia’s LinkedIn shows that he’s spent most of his career in tech, including a 10-year stint at Palantir. When Barbaccia left Palantir in 2020, his role was head of intelligence and investigations. Palantir CEO Alex Karp recently referenced the “disruption” of DOGE’s cost-cutting initiatives and said, “Whatever is good for America will be good for Americans and very good for Palantir.” The company has made billions in government contracts. Palantir shares hit an all-time high last week after a better-than-expected quarterly earnings report. Last week, Palantir announced plans to integrate Musk’s large language model Grok with Palantir’s AI platform.
Ryan Riedel was installed as chief information officer of the Department of Energy (DOE) last week, according to reports from E&E News. At the DOE specifically, the CIO oversees all technology operations as well as cybersecurity initiatives, in addition to elements of the National Nuclear Security Administration, which oversees the US’s nuclear weapons stockpiles. Riedel reportedly worked as a “lead network security engineer” at Musk’s rocket company SpaceX.
While not every new CIO has direct ties to Musk or Palantir, they do all have deep Silicon Valley connections. Greg Hogan is now the CIO of OPM, which is essentially the US government’s HR department. Hogan has been alleged to be a special government employee and not a full-time OPM employee, according to a recent lawsuit. Hogan previously worked at Comma.AI, a company that builds automated driving software. Musk allegedly floated a job offer to Comma.AI’s former CEO George Hotz in 2015 to work on self-driving tech, but the deal reportedly soured after Hotz claimed his self-driving tech was superior to Tesla’s.
OPM confirmed that Hogan now serves as CIO. OMB and DOE did not immediately respond to requests for comment from WIRED.
The reclassification of the CIO role doesn’t affect current CIOs, but their job security is uncertain. In January, Trump signed an executive order that could remove civil servant protections, turning potentially thousands of employees into “at will” workers. By doing so, the Trump administration would make it easier to fire career civil servants in what it calls “policy-influencing” roles. In a memo last week, Charles Ezell, acting OPM director, says that the CIO reclassification is due to the office’s increased influence on policy across agencies.
“No longer the station of impartial and apolitical technocrats, the modern agency CIO role demands policy-making and policy-determining capabilities across a range of controversial political topics,” Ezell wrote.
Last week, federal workers’ unions sued the White House, arguing that the order oversteps Trump’s presidential authority.
Already, Musk associates have infiltrated a number of government agencies. WIRED has extensively reported on the DOGE staffers, many of them young, with links to Musk’s various companies and little to no government experience, gaining access to sensitive systems at a number of agencies, including the Treasury Department. DOGE is being led by a variety of Musk associates, including Steve Davis and Nicole Hollander, who helped the billionaire acquire Twitter in 2022. Thomas Shedd, a former Tesla engineer, now heads Technology Transformation Services, which is housed within the General Services Administration.
Are you a current or former government worker with insight into what's going on? We'd like to hear from you. Using a nonwork phone or computer, contact the reporter securely using a personal device on Signal at makenakelly.32.
4 notes
·
View notes
Text
What exactly is Blockchain
A Comprehensive Guide for All: What is Blockchain?
Try to picture yourself with a notebook in which you record every purchase or sale. Each time you do a transaction, you note it in the notebook. Now, what if you distributed this notebook amongst your friends and everyone had one? All of your buddies would scrutinize your entry before adding it to their notes. This way, nobody could fake an old entry, since everyone else would spot it.
Something known as blockchain is built upon this basic concept — sharing a record of transactions open for everyone to verify. Though it may sound intimidating, it is a technology gaining traction in the financial and computer sector. We will clarify it in this blog in simple words, so anybody may follow it.
What Exactly Does Blockchain Mean?
Fundamentally, blockchain is simply a unique form of digital record-keeping. Think of it as a series of blocks (hence the name “blockchain”), each block including transaction information. These blocks are related in a way that makes them quite stable and difficult to change.
Step by step, this is how it works:
A Transaction Occurs: Suppose Alice wants to give Bob $10. This is an interaction.
The transaction is registered: the information of this transaction is passed to a network of computer nodes instead of being written in one notebook.
Everyone Checks the Transaction: The computers in the network check to make sure Alice has $10 to transmit. By examining her past deals kept in earlier blocks, they do this.
The transaction is added to a block: Once everyone concurs it is legitimate, it gets formed with other transactions into a block.
The Block Is Sealed, attached: The block is assigned an individual code (known as a hash) and then included in the chain of already existing blocks. This makes a fixed, permanent record of the deal. There it is! It is like one huge, common ledger keeping track of all system events.
What Makes Blockchain Different?
Now, one might be wondering, “Why not simply use a normal database or spreadsheet?” Fantastic issue! Blockchain distinguishes itself by several distinct qualities.
It is distributed across.
Most models today have one main custodian — be it a bank, company, or government — that manages the records. The entire system can crumble if something goes wrong with that central authority — say, hacking or corruption.
Blockchain relies on many, but not one authority. It rather distributes the blame amongst several computers (nodes). Every node has a full blockchain copy, therefore no individual or group may manage it. This all but prevents evil actors from using the data.
It is transparent.
Given that each transaction is visible to all people in the network, and recorded on the blockchain, it is clear. You can observe when and where money or assets traveled from one location to another. Since no one can hide anything, this openness fosters confidence.
Consider how a nonprofit uses blockchain to monitor contributions, for instance. Donors might observe very clearly how their funds are used, therefore guaranteeing that they reach the intended beneficiaries without middlemen siphoning off funds.
Safe.
Adding a transaction to the blockchain makes it virtually irrevocable.
Therefore: Every block has its distinct code (hash), including the one from the preceding block. Trying to change a block would also require one to re-compute the hashes for every subsequent block, hardly a small job.
Since the blockchain is decentralized, hackers would have to simultaneously compromise more than half of the computers in the network to fiddle with the data. Considering how vast these networks can usually be, this is virtually impossible.
Such a level of security makes blockchain perfect for sensitive uses including medical records, banking, and voting systems
It cuts out intermediaries.
Usually, when you want to buy anything online or move funds, you go via middlemen including banks, payment processors, or even legal practitioners. These intermediaries increase both costs and time for the project.
Blockchains free you from the need for intermediaries. Transactions take place between parties on their own, therefore saving both time and financial means. Sending funds abroad the old way can take days and incur large charges, for example. Using blockchain-based cryptocurrencies like Bitcoin, the same transaction can take minutes for a small percentage of the cost.
Examples of blockchain in the real world:
To know more about how blockchain operates in practice, let us look at some instances:
Cryptocurrencies
Cryptocurrencies like Bitcoin and Ethereum have the most well-known applications of blockchain. People can transfer money and accept it without a bank using these digital currencies. Each time somebody sends Bitcoin to another, the blockchain notes the transaction.
Supply Chain Management Tracking
As goods traverse the supply chain, enterprises including IBM and Walmart use blockchain to monitor them. If you buy a mango, you can scan a QR code, for instance, and find exactly where it came from, who touched it, and when it reached the store. This ensures product quality and reduces fraud.
Election processes
Some nations are trying voting systems based on blockchain. Blockchain might help to lower voter fraud and raise public faith in election results since it is open and safe.
Health information
Ways hospitals and clinics could leverage blockchain for patient records storage are under investigation. This would let doctors quickly access precise and current data while permitting patients complete control of their information.
Some popular misunderstandings surrounding blockchain
Though blockchain is growing in popularity, some questions remain about its nature and usage. Those should be cleared away:
“Blockchain Is Just for Cryptocurrencies.”
Though cryptocurrencies were the first significant application of blockchain, the technology itself has great applications beyond finance. Industries including logistics, healthcare, and government are discovering creative applications of blockchain.
Blockchain is anonymous.
Though blockchain provides privacy, it is not entirely anonymous. Since transactions are listed publicly, anyone can see them. Users’ identities are typically expressed by codes — rather than actual names — thus granting some level of pseudonymity.
“Blockchain is flawless.”
Though very secure, blockchain is not free from dangers. Thankfully, such attacks are really rare because of the complexity and size of the majority of blockchain networks — for instance, if someone gains control of more than 50% of the computing power of the network, they could theoretically manipulate the blockchain in what is known as a “51% assault.”
The Future of Blockchains
Though blockchain is still fairly new, its possibilities are vast. Improvements in general efficiency, openness, and security across the board will probably follow the more widespread acceptance of it. Some professionals think that blockchain could transform everything from our personal data management to our voting.
Still, popular usage will need time. Scalability (managing vast transaction numbers), regulation (governments determining how to deal with blockchain), and education (assisting people in understanding and embracing the technology) are obstacles to be tackled.
Wraps up.
So, at its most basic, blockchain is a decentralized, clear, and secured means of documentation. Whether it is assisting farmers in obtaining fair prices for their products, accelerating international payments, or safeguarding sensitive medical information, blockchain has the capacity to change our lives and employment fundamentally.
Next time you learn about blockchain, recall the notebook analogy: It’s a shared, tamper-proof book everyone can view but no one can edit. And who knows? Maybe someday soon, blockchain will become as common as smartphones or the internet!
Even a small tip goes a long way!
ETH: 0x788571C4c836ec733a72ff84c626BF7F20736d76
Thanks for reading Aadit’s Substack! Subscribe for free to receive new posts and support my work.
3 notes
·
View notes
Text
love my gayass fuckin job so much. just ended an email about digital asset allocation & organization with:
"If there is anything else you might need assistance with, please let me know! It would be my pleasure to lend a hand~ :D"
like that tilde is doing major work to lessen the energy of me frantically trying to manage whatever is happening in terms of our databases but i'm trying to at once run this shit like the navy & be a whimsical fagtastic personality hire
#syaruru.msg#i'm embracing being an evil corporate bugwoman but i'm also kind of a happy go lucky angel in those zoom meetings despite being a menace#for context i work in the publishing industry so it's like a bunch of gay hippies in a zoom trying to be serious LMAOOOOO
2 notes
·
View notes
Text
Binance clone script — Overview by BlockchainX
A Binance Clone Script is a pre-built, customizable software solution that replicates Binance's features, connect with BlockchainX

What is Binance Clone Script
A Binance clone script refers to the ready-made solution of the Binance platform that deals with core functions parallel to the widely acclaimed cryptocurrency exchange platform associated with Binance. It enables companies to establish their own platforms like Binance, perfectly parameterized in terms of functionality and user interface of world-famous exchanges. The clone script provides display flexibility with built-in functionality such as spot trading software, futures trading configurations, and wallet systems that are extremely secure.
Basically, it reduces development costs and latency because things like these are already built. And as this is a startup for many young entrepreneurs, they can have saved on their capital to expand or grow their business.
The script is blessed as its feature set caters to future demands in the field. One can enjoy a safe trading experience to customers while ensuring that every peculiarity of Binance’s success opens up to investors of the script.
How does the Binance clone script work?
The Binance clone script works to provide a ready-made platform that replicates Binance’s core features, such as user registration, wallet management, trade and enables users to create accounts, deposit or withdraw cryptocurrency, and trade digital assets through an interface easily and safely. The platform supports various trading methods such as market orders, limit orders and forward trading. It has built-in security features like two-factor authentication (2FA) to save the user money. Admin dashboards allow platform owners to manage users, manage tasks, and set up billing. The script can be tailored to your brand, connecting liquidity sources to make trading more efficient. In short, the Binance clone script provides everything needed to create a fully functional crypto exchange.
key features of a Binance Clone Script
The key features of a Binance Clone Script are designed to make your cryptocurrency exchange platform secure, user-friendly, and fully functional. Here’s a simple overview of these features:
User-Friendly Interface
Multi-Currency Support
Advanced Trading Engine
Secure Wallet System
KYC/AML Integration
Admin Dashboard
Security Features
Trading Options
These features help ensure that your Binance-like exchange is efficient, secure, and ready for the growing crypto market.
Technology Stack Used by BlockchainX
Technology stack used for developing the Binance clone script involves the most advanced technology combination that ensures that the platform must have so much security, scalability, and performance to make it a platform that is secure, scalable, and high-performance as well. Here are a few key technologies and their brief descriptions:
Blockchain Technology:
The underlying part of the cryptocurrency exchange is Blockchain because it ensures the safe and decentralized processing of transactions.
Normally executed on either Ethereum or BSC (Binance Smart Chain) to carry out smart contracts and token transfers.
Programming Languages:
Frontend: For frontend, React or Angular could be engaged in actualization of the user interface leading to a responsive and interactive experience on the various devices.
Backend: In backend, languages like Node.js, Python, or Ruby on Rails can be applied on how internal logic is being run by server and arbitration of user interaction with the module is foremost.
Databases:
These two databases, MySQL or Postgresql, are typically used in user information storage, transaction records, and other exchange information.
NoSQL such as MongoDB or other databases might be used for horizontal scalability and high-volume transaction storage.
Smart Contracts:
It is used to generate and send out smart contracts for auto-trading, token generation, and other decentralized functionalities.
Blockchain Wallets:
Fundamentally, this automatically links famous wallet systems such as MetaMask, Trust Wallet, or Ledger for the secure storage and transactions of cryptocurrency.
Advantages of using a Binance Clone Script
Here are the advantages of using a Binance Clone Script:
Faster Time-to-Market
Cost-Effective
Customizable Features
Liquidity Integration
Multiple Trading Options
So, when entering the marketplace of the cryptocurrencies it would be the most possible work of something to pay off at a rapid pace: the Binance Clone Script proves so.
How to Get Started with BlockchainX’s Binance Clone Script
It is quite a straightforward process to begin working with a BlockchainX Binance Clone Script-this involves the first step of getting in touch with the company for an initial consulting period to understand more about what you require, need, or customize for the site, and what your goals are. When BlockchainX has an understanding of your needs, they offer a detailed list of what a proposal would entail before they can start the work; afterward, they will estimate the costs needed to do the project. Once both sides accept both the presentations and all features and timelines are agreed with, BlockchainX starts working on the development process of building a Binance Clone Script tailored to the brand, user interface, and other features.
After the entire platform is created, it passes through severe testing to ensure that everything functions excellently. Deployment follows the thorough test. BlockchainX customizes your user interface and more extensions, after deployment. BlockchainX also commits to supporting and sustaining your exchange so that it runs successfully and securely.
Conclusion:
At the end, your confusion may as well be cut short. Yes, the Binance Clone Script will be a resilient solution to spark up the exchange platforms synthesizing user-generated cryptocurrency dreams in the blockchain, even without bankroll when it comes to developing the app. Turning with BlockchainX expertise, you can make an adjustment and scale a powerful platform stocked with the likes of Binance that produced Blockchains, while still containing some specific set-ups for your masterpiece. More amazing features are exclusive to the clone script, moreover, such as support for multiple currencies, high-end security, real-time data, and a smooth user interface that completes the trading process for your users without any glitch.
This solution gives easy access to ready-made solutions. It could have quality Depending on the time you conveniently let BlockchainX’s be and use both exchanges or any variation of the two permutations. After all, who decides to couple up with a one-experienced Crypto Exchange developer who is struggling to offer anything new.
#binance clone script#binance clone script development#binance clone script development service#blockchain technology#blockchain#cryptocurrency#cryptocurrencies
2 notes
·
View notes
Text
JCPenney Merges With Aéropostale Parent to Form Retail Powerhouse

JCPenney is shaking up the retail world by merging with Sparc Group to create Catalyst Brands, a massive 1,800-store powerhouse ready to dominate the mall experience.
A strategic alliance: The merger combines JCPenney's iconic department store presence with Sparc Group's portfolio of brands, including Forever 21, Brooks Brothers, and Eddie Bauer. Simon Property Group and Brookfield, who co-own JCPenney post-bankruptcy, are major stakeholders in both entities, enabling a streamlined approach to retail operations.
Retail revamp: Catalyst is shedding non-core assets, such as Reebok’s U.S. operations, while exploring options for Forever 21. Key intellectual properties like Nautica and Lucky Brand, licensed by Sparc from Authentic Brands Group, remain central to its retail strategy, signaling a focus on maximizing brand alignment and efficiency.
Zoom in: Catalyst plans to tap into its database of 60 million customers, leveraging AI to enhance supply chain operations and improve customer engagement. This strategy aligns with the retail shift toward e-commerce, personalization, and agile inventory management.
3 notes
·
View notes
Text
How-To IT
Topic: Core areas of IT
1. Hardware
• Computers (Desktops, Laptops, Workstations)
• Servers and Data Centers
• Networking Devices (Routers, Switches, Modems)
• Storage Devices (HDDs, SSDs, NAS)
• Peripheral Devices (Printers, Scanners, Monitors)
2. Software
• Operating Systems (Windows, Linux, macOS)
• Application Software (Office Suites, ERP, CRM)
• Development Software (IDEs, Code Libraries, APIs)
• Middleware (Integration Tools)
• Security Software (Antivirus, Firewalls, SIEM)
3. Networking and Telecommunications
• LAN/WAN Infrastructure
• Wireless Networking (Wi-Fi, 5G)
• VPNs (Virtual Private Networks)
• Communication Systems (VoIP, Email Servers)
• Internet Services
4. Data Management
• Databases (SQL, NoSQL)
• Data Warehousing
• Big Data Technologies (Hadoop, Spark)
• Backup and Recovery Systems
• Data Integration Tools
5. Cybersecurity
• Network Security
• Endpoint Protection
• Identity and Access Management (IAM)
• Threat Detection and Incident Response
• Encryption and Data Privacy
6. Software Development
• Front-End Development (UI/UX Design)
• Back-End Development
• DevOps and CI/CD Pipelines
• Mobile App Development
• Cloud-Native Development
7. Cloud Computing
• Infrastructure as a Service (IaaS)
• Platform as a Service (PaaS)
• Software as a Service (SaaS)
• Serverless Computing
• Cloud Storage and Management
8. IT Support and Services
• Help Desk Support
• IT Service Management (ITSM)
• System Administration
• Hardware and Software Troubleshooting
• End-User Training
9. Artificial Intelligence and Machine Learning
• AI Algorithms and Frameworks
• Natural Language Processing (NLP)
• Computer Vision
• Robotics
• Predictive Analytics
10. Business Intelligence and Analytics
• Reporting Tools (Tableau, Power BI)
• Data Visualization
• Business Analytics Platforms
• Predictive Modeling
11. Internet of Things (IoT)
• IoT Devices and Sensors
• IoT Platforms
• Edge Computing
• Smart Systems (Homes, Cities, Vehicles)
12. Enterprise Systems
• Enterprise Resource Planning (ERP)
• Customer Relationship Management (CRM)
• Human Resource Management Systems (HRMS)
• Supply Chain Management Systems
13. IT Governance and Compliance
• ITIL (Information Technology Infrastructure Library)
• COBIT (Control Objectives for Information Technologies)
• ISO/IEC Standards
• Regulatory Compliance (GDPR, HIPAA, SOX)
14. Emerging Technologies
• Blockchain
• Quantum Computing
• Augmented Reality (AR) and Virtual Reality (VR)
• 3D Printing
• Digital Twins
15. IT Project Management
• Agile, Scrum, and Kanban
• Waterfall Methodology
• Resource Allocation
• Risk Management
16. IT Infrastructure
• Data Centers
• Virtualization (VMware, Hyper-V)
• Disaster Recovery Planning
• Load Balancing
17. IT Education and Certifications
• Vendor Certifications (Microsoft, Cisco, AWS)
• Training and Development Programs
• Online Learning Platforms
18. IT Operations and Monitoring
• Performance Monitoring (APM, Network Monitoring)
• IT Asset Management
• Event and Incident Management
19. Software Testing
• Manual Testing: Human testers evaluate software by executing test cases without using automation tools.
• Automated Testing: Use of testing tools (e.g., Selenium, JUnit) to run automated scripts and check software behavior.
• Functional Testing: Validating that the software performs its intended functions.
• Non-Functional Testing: Assessing non-functional aspects such as performance, usability, and security.
• Unit Testing: Testing individual components or units of code for correctness.
• Integration Testing: Ensuring that different modules or systems work together as expected.
• System Testing: Verifying the complete software system’s behavior against requirements.
• Acceptance Testing: Conducting tests to confirm that the software meets business requirements (including UAT - User Acceptance Testing).
• Regression Testing: Ensuring that new changes or features do not negatively affect existing functionalities.
• Performance Testing: Testing software performance under various conditions (load, stress, scalability).
• Security Testing: Identifying vulnerabilities and assessing the software’s ability to protect data.
• Compatibility Testing: Ensuring the software works on different operating systems, browsers, or devices.
• Continuous Testing: Integrating testing into the development lifecycle to provide quick feedback and minimize bugs.
• Test Automation Frameworks: Tools and structures used to automate testing processes (e.g., TestNG, Appium).
19. VoIP (Voice over IP)
VoIP Protocols & Standards
• SIP (Session Initiation Protocol)
• H.323
• RTP (Real-Time Transport Protocol)
• MGCP (Media Gateway Control Protocol)
VoIP Hardware
• IP Phones (Desk Phones, Mobile Clients)
• VoIP Gateways
• Analog Telephone Adapters (ATAs)
• VoIP Servers
• Network Switches/ Routers for VoIP
VoIP Software
• Softphones (e.g., Zoiper, X-Lite)
• PBX (Private Branch Exchange) Systems
• VoIP Management Software
• Call Center Solutions (e.g., Asterisk, 3CX)
VoIP Network Infrastructure
• Quality of Service (QoS) Configuration
• VPNs (Virtual Private Networks) for VoIP
• VoIP Traffic Shaping & Bandwidth Management
• Firewall and Security Configurations for VoIP
• Network Monitoring & Optimization Tools
VoIP Security
• Encryption (SRTP, TLS)
• Authentication and Authorization
• Firewall & Intrusion Detection Systems
• VoIP Fraud DetectionVoIP Providers
• Hosted VoIP Services (e.g., RingCentral, Vonage)
• SIP Trunking Providers
• PBX Hosting & Managed Services
VoIP Quality and Testing
• Call Quality Monitoring
• Latency, Jitter, and Packet Loss Testing
• VoIP Performance Metrics and Reporting Tools
• User Acceptance Testing (UAT) for VoIP Systems
Integration with Other Systems
• CRM Integration (e.g., Salesforce with VoIP)
• Unified Communications (UC) Solutions
• Contact Center Integration
• Email, Chat, and Video Communication Integration
2 notes
·
View notes
Text
What Are the Qualifications for a Data Scientist?
In today's data-driven world, the role of a data scientist has become one of the most coveted career paths. With businesses relying on data for decision-making, understanding customer behavior, and improving products, the demand for skilled professionals who can analyze, interpret, and extract value from data is at an all-time high. If you're wondering what qualifications are needed to become a successful data scientist, how DataCouncil can help you get there, and why a data science course in Pune is a great option, this blog has the answers.
The Key Qualifications for a Data Scientist
To succeed as a data scientist, a mix of technical skills, education, and hands-on experience is essential. Here are the core qualifications required:
1. Educational Background
A strong foundation in mathematics, statistics, or computer science is typically expected. Most data scientists hold at least a bachelor’s degree in one of these fields, with many pursuing higher education such as a master's or a Ph.D. A data science course in Pune with DataCouncil can bridge this gap, offering the academic and practical knowledge required for a strong start in the industry.
2. Proficiency in Programming Languages
Programming is at the heart of data science. You need to be comfortable with languages like Python, R, and SQL, which are widely used for data analysis, machine learning, and database management. A comprehensive data science course in Pune will teach these programming skills from scratch, ensuring you become proficient in coding for data science tasks.
3. Understanding of Machine Learning
Data scientists must have a solid grasp of machine learning techniques and algorithms such as regression, clustering, and decision trees. By enrolling in a DataCouncil course, you'll learn how to implement machine learning models to analyze data and make predictions, an essential qualification for landing a data science job.
4. Data Wrangling Skills
Raw data is often messy and unstructured, and a good data scientist needs to be adept at cleaning and processing data before it can be analyzed. DataCouncil's data science course in Pune includes practical training in tools like Pandas and Numpy for effective data wrangling, helping you develop a strong skill set in this critical area.
5. Statistical Knowledge
Statistical analysis forms the backbone of data science. Knowledge of probability, hypothesis testing, and statistical modeling allows data scientists to draw meaningful insights from data. A structured data science course in Pune offers the theoretical and practical aspects of statistics required to excel.
6. Communication and Data Visualization Skills
Being able to explain your findings in a clear and concise manner is crucial. Data scientists often need to communicate with non-technical stakeholders, making tools like Tableau, Power BI, and Matplotlib essential for creating insightful visualizations. DataCouncil’s data science course in Pune includes modules on data visualization, which can help you present data in a way that’s easy to understand.
7. Domain Knowledge
Apart from technical skills, understanding the industry you work in is a major asset. Whether it’s healthcare, finance, or e-commerce, knowing how data applies within your industry will set you apart from the competition. DataCouncil's data science course in Pune is designed to offer case studies from multiple industries, helping students gain domain-specific insights.
Why Choose DataCouncil for a Data Science Course in Pune?
If you're looking to build a successful career as a data scientist, enrolling in a data science course in Pune with DataCouncil can be your first step toward reaching your goals. Here’s why DataCouncil is the ideal choice:
Comprehensive Curriculum: The course covers everything from the basics of data science to advanced machine learning techniques.
Hands-On Projects: You'll work on real-world projects that mimic the challenges faced by data scientists in various industries.
Experienced Faculty: Learn from industry professionals who have years of experience in data science and analytics.
100% Placement Support: DataCouncil provides job assistance to help you land a data science job in Pune or anywhere else, making it a great investment in your future.
Flexible Learning Options: With both weekday and weekend batches, DataCouncil ensures that you can learn at your own pace without compromising your current commitments.
Conclusion
Becoming a data scientist requires a combination of technical expertise, analytical skills, and industry knowledge. By enrolling in a data science course in Pune with DataCouncil, you can gain all the qualifications you need to thrive in this exciting field. Whether you're a fresher looking to start your career or a professional wanting to upskill, this course will equip you with the knowledge, skills, and practical experience to succeed as a data scientist.
Explore DataCouncil’s offerings today and take the first step toward unlocking a rewarding career in data science! Looking for the best data science course in Pune? DataCouncil offers comprehensive data science classes in Pune, designed to equip you with the skills to excel in this booming field. Our data science course in Pune covers everything from data analysis to machine learning, with competitive data science course fees in Pune. We provide job-oriented programs, making us the best institute for data science in Pune with placement support. Explore online data science training in Pune and take your career to new heights!
#In today's data-driven world#the role of a data scientist has become one of the most coveted career paths. With businesses relying on data for decision-making#understanding customer behavior#and improving products#the demand for skilled professionals who can analyze#interpret#and extract value from data is at an all-time high. If you're wondering what qualifications are needed to become a successful data scientis#how DataCouncil can help you get there#and why a data science course in Pune is a great option#this blog has the answers.#The Key Qualifications for a Data Scientist#To succeed as a data scientist#a mix of technical skills#education#and hands-on experience is essential. Here are the core qualifications required:#1. Educational Background#A strong foundation in mathematics#statistics#or computer science is typically expected. Most data scientists hold at least a bachelor’s degree in one of these fields#with many pursuing higher education such as a master's or a Ph.D. A data science course in Pune with DataCouncil can bridge this gap#offering the academic and practical knowledge required for a strong start in the industry.#2. Proficiency in Programming Languages#Programming is at the heart of data science. You need to be comfortable with languages like Python#R#and SQL#which are widely used for data analysis#machine learning#and database management. A comprehensive data science course in Pune will teach these programming skills from scratch#ensuring you become proficient in coding for data science tasks.#3. Understanding of Machine Learning
3 notes
·
View notes