#Check Your Mobile Number in Androids
Explore tagged Tumblr posts
Text
Friday, August 11th, 2023
🌟 New
We've implemented OpenAI’s instructions for blocking GPTBot. This should discourage OpenAI, including ChatGPT, from scraping any part of Tumblr, including individual blogs.
We’re rolling out a new redesign of the direct messaging conversation view.
🛠 Fixed
The latest version of the Android app (30.8) fixes the issue where links to “View Post” on filtered posts opens the web browser instead of taking you to the post in the app itself.
On web, we’ve improved the screen reader hint for tags on posts, so it doesn’t say “Pound” or “Number” when it encounters the hashtag symbol.
Fixed an issue on web that was preventing the Related Tags section of the sidebar from showing up on the search results page.
Fixed a bug in the mobile apps for group blogs which was preventing members from editing the Notifications settings for those group blogs.
We’ve been rolling through some bug fix releases and one major release for the StreamBuilder framework.
🚧 Ongoing
Nothing to report here today.
🌱 Upcoming
We’re cooking up our first public reveal on the @labs blog, give that blog a follow if you want to see what we’re working on!
Experiencing an issue? File a Support Request and we’ll get back to you as soon as we can!
Want to share your feedback about something? Check out our Work in Progress blog and start a discussion with the community.
1K notes
·
View notes
Note
can you tell us all the plugins / ad blockers you use
on desktop, uBlock Origin (NOT Adblock Plus! they sold out years ago! they literally take money from advertisers to make sure their ads get through their filters!) and SponsorBlock for Firefox. if you still see ads on youtube specifically check out this page. if it's green, then the problem is with your specific installation and you should check out this reddit megathread. if it's red, then tough luck, wait a few hours for uBlock's crack team of hackers to catch back up in their constant arms race with Youtube.
for Android, get ReVanced Manager from here and use that + an .apk download of the latest Youtube release (just google "youtube apk") to patch yourself together a version of the Youtube app that acts like you paid for Advanced even though you didn't, which means no ads. also, side tangent, that's where the name comes from: originally it was just "Youtube Vanced" because it was "Advanced" without the "ad"s. then the Vanced team got slapped with a C&D for being dumbasses and minting NFTs of the Vanced logo, which was literally just the Youtube logo, so ReVanced rose from the ashes to continue its legacy. oh also there are a shitload of boxes you can check off during the patching process and one of them just integrates Sponsorblock for you, so that's nice.
i should also mention here, for no reason in particular, that the Vanced Manager app lets you patch a number of other apps in the same way, removing ads and adding "premium" features without you having to pay. one of these apps may or may not be Tumblr itself.
as long as you're fucking with your Android, download xManager and use it to get ad-free Spotify without paying for it. iirc the app auto-downloads the apk for you but it's been months since i last fucked with it so i might be misremembering.
honorary mention goes to NewPipe for being a way easier to install alternative to all of the above if you don't care about logging in. it's an alternate frontend for youtube that lets you watch it ad-free right out of the box. the main drawbacks are that the UI is a little ugly (especially compared to the official/ReVanced version), you can't use Sponsorblock, and it doesn't sync with your Google account (this could be a plus for you if you're big into privacy but personally i like having my likes and watch history synced across desktop and mobile). although now that i just did some research to make sure i wasn't talking out my ass, it looks like the original dev is working on a forked version of the app named Tubular that does have Sponsorblock and is apparently trying to get google account stuff working, so that's cool. oh and it can also browse/play Soundcloud ad-free, if you still use Soundcloud in 2024
460 notes
·
View notes
Note
what is the best way to get safer/more anonymous online
Ok, security and anonymity are not the same thing, but when you combine them you can enhance your online privacy.
My question is: how tech literate are you and what is your aim? As in do you live in a country where your government would benefit from monitoring private (political) conversations or do you just want to degoogle? Because the latter is much easier for the average user.
Some general advice:
Leave Windows and Mac operating systems and switch to Linux distributions like Fedora and Ubuntu (both very user friendly). Switch from Microsoft Office or Pages/Numbers/Keynote (Mac) to LibreOffice.
You want to go more hardcore with a very privacy-focused operating system? There are Whonix and Tails (portable operating system).
Try to replace all your closed source apps with open source ones.
Now, when it comes to browsers, leave Chrome behind. Switch to Firefox (or Firefox Focus if you're on mobile). Want to go a step further? Use LibreWolf (a modified version of Firefox that increases protection against tracking), Brave (good for beginners but it has its controversies), DuckDuckGo or Bromite. You like ecofriendly alternatives? Check Ecosia out.
Are you, like, a journalist or political activist? Then you probably know Tor and other anonymous networks like i2p, freenet, Lokinet, Retroshare, IPFS and GNUnet.
For whistleblowers there are tools like SecureDrop (requires Tor), GlobaLeaks (alternative to SecureDrop), Haven (Android) and OnionShare.
Search engines?
There are Startpage (obtains Google's results but with more privacy), MetaGer (open source), DuckDuckGo (partially open source), Searx (open source). You can see the comparisons here.
Check libRedirect out. It redirects requests from popular socmed websites to privacy friendly frontends.
Alternatives to YouTube that value your privacy? Odysee, PeerTube and DTube.
Decentralized apps and social media? Mastodon (Twitter alternative), Friendica (Facebook alternative), diaspora* (Google+ RIP), PixelFed (Insta alternative), Aether (Reddit alternative).
Messaging?
I know we all use shit like Viber, Messenger, Telegram, Whatsup, Discord etc. but there are:
Signal (feels like Whatsup but it's secure and has end-to-end encryption)
Session (doesn't even require a phone or e-mail address to sign up)
Status (no phone or e-mail address again)
Threema (for mobile)
Delta Chat (you can chat with people if you know their e-mail without them having to use the app)
Team chatting?
Open source options:
Element (an alternative to Discord)
Rocket.chat (good for companies)
Revolt.chat (good for gamers and a good alternative to Discord)
Video/voice messaging?
Brave Talk (the one who creates the talk needs to use the browser but the others can join from any browser)
Jami
Linphone
Jitsi (no account required, video conferencing)
Then for Tor there are various options like Briar (good for activists), Speek! and Cwtch (user friendly).
Georestrictions? You don't want your Internet Provider to see what exactly what you're doing online?
As long as it's legal in your country, then you need to hide your IP with a VPN (authoritarian regimes tend to make them illegal for a reason), preferably one that has a no log policy, RAM servers, does not operate in one of the 14 eyes, supports OpenVPN (protocol), accepts cash payment and uses a strong encryption.
NordVPN (based in Panama)
ProtonVPN (Switzerland)
Cyberghost
Mullvad (Sweden)
Surfshark (Netherlands)
Private e-mails?
ProtonMail
StartMail
Tutamail
Mailbox (ecofriendly option)
Want to hide your real e-mail address to avoid spam etc.? SimpleLogin (open source)
E-mail clients?
Thunderbird
Canary Mail (for Android and iOS)
K-9 Mail (Android)
Too many complex passwords that you can't remember?
NordPass
BitWarden
LessPass
KeePassXC
Two Factor Authenticators?
2FAS
ente Authenticator
Aegis Authenticator
andOTP
Tofu (for iOS)
Want to encrypt your files? VeraCrypt (for your disk), GNU Privacy Guard (for your e-mail), Hat.sh (encryption in your browser), Picocrypt (Desktop encryption).
Want to encrypt your Dropbox, Google Drive etc.? Cryptomator.
Encrypted cloud storage?
NordLocker
MEGA
Proton Drive
Nextcloud
Filen
Encrypted photography storage?
ente
Cryptee
Piwigo
Want to remove metadata from your images and videos? ExifCleaner. For Android? ExifEraser. For iOS? Metapho.
Cloak your images to counter facial recognition? Fawkes.
Encrypted file sharing? Send.
Do you menstruate? Do you want an app that tracks your menstrual cycle but doesn't collect your data? drip.
What about your sexual health? Euki.
Want a fitness tracker without a closed source app and the need to transmit your personal data to the company's servers? Gadgetbridge.
34 notes
·
View notes
Text




Hello! Welcome to the official Double Dead Studio Tumblr, the solodev behind Reanimated Heart, Another Rose in His Garden, and Pygmalion's Folly.
Reanimated Heart is a character-driven horror romance visual novel about finding love in a mysterious small town. There are three monstrous love interests with their own unique personalities and storylines.
Another Rose in His Garden is an 18+ erotic Omegaverse BL visual novel. Abel Valencia is an Omega who's hidden his secondary sex his entire life. Life's alright, until he meets the wealthy tycoon, Mars Rosales, and the two get embroiled in a sexual affair that changes his life forever.
Pygmalion's Folly is a survival murdersim where you play as Roxham Police Department's star detective, hellbent on finding your sister's killer... until he finds you.
Content Warning: All my games are 18+! They contains dark subject matter such as violence and sexual content. Player discretion is advised.
This blog is ran by Jack, the creator.
Itch | Link Tree | Patreon | Twitter
Guidelines
My policy for fanwork is that anything goes in fiction, but respect my authority and copyright outside it. This means normal fan activity like taking screencaps, posting playthroughs, and making fanart/fanfiction is completely allowed, but selling this game or its assets isn't allowed (selling fanwork of it is fine, though). You are also not allowed to feed any of my assets to AI bots, period, even if it's free.
Do not use my stuff for illegal or hateful content.
Also, I expect everyone to respect the Content Warnings on the page. I'm old and do not tolerate fandom wank.
For more details about how I view Fanwork, refer to this post.
F.A.Q.
Who are the main Love Interests in Reanimated Heart?
Read their character profiles here!!
Who's the team?
Jack (creator, writer, artist), mostly. I closely work with Exodus (main programmer) and Claira (music composer). My husband edits the drafts.
For Reanimated Heart, my friend Bonny makes art assets. I've also gotten help from outsiders like Sleepy (prologue music + vfx) and my friend Gumjamin (main menu heart animation).
For Reanimated Heart's VOs, Alex Ross voices Crux, Devin McLaughlin voices Vincenzo, Christian Cruz voices Black, Maganda Marie voices Grete, and Zoe D. Lee voices Missy.
Basically, it's mostly just me & outsourcing stuff to my friends and professionals.
How can I support Double Dead Studio productions?
You can pay for the game, or join our monthly Patreon! If you don't have any money, just giving it a nice rating and recommending it to a friend is already good enough. :)
Where do the funds go to?
Almost 100% gets poured back into the game. More voice acting, more music, more trailers, more art, etc. I also like to give my programmer a monthly tip for helping me.
This game is really my insane passion project, and I want to make it better with community support.
I live in the Philippines and the purchasing power of php is not high, especially since many of the people I outsource to prefer USD. (One time I spent P10k of my own money in one month just to get things.) I'll probably still do that, even if no money comes in, until I'm in danger of getting kicked out the street… but maybe even then? (jk)
What platforms will Reanimated Heart be released in?
Itch and then Steam when it's fully finished. Still looking into other options, as I hear both are getting bad.
Will Reanimated Heart be free?
Chapter 1 will be free. The rest will be updated on Patreon exclusively until full release.
Are you doing a mobile version?
Yeah. Just Android for now, but it's in the works.
Where can I listen to Reanimated Heart's OST?
It is currently up on YouTube, Spotify, and Bandcamp!
Why didn't you answer my ask?
A number of things! Two big ones that keep coming up are Spoilers (as in, you asked something that will be put in an update) or it's already been asked. If you're really dying to know, check the character tags or the meta commentary. You might find what you're looking for there. :)
Will there be a sequel to Pygmalion's Folly?
It's not my first concern right now, but I am planning on it.
Tag List for Navigation
Just click the tags to get to where you wanna go!
#reanimated heart#updates#asks#official art#crux hertz#black lumaban#vincenzo maria fontana#grete braun#townies#fanwork#additional content#aesthetic#spoilers#lore#meta commentary#memes#horror visual novel#romance visual novel#yandere OC#prompts#another rose in his garden#abel valencia#mars rosales#florentin blanchett#pygmalion's folly
149 notes
·
View notes
Text
In recent years, commercial spyware has been deployed by more actors against a wider range of victims, but the prevailing narrative has still been that the malware is used in targeted attacks against an extremely small number of people. At the same time, though, it has been difficult to check devices for infection, leading individuals to navigate an ad hoc array of academic institutions and NGOs that have been on the front lines of developing forensic techniques to detect mobile spyware. On Tuesday, the mobile device security firm iVerify is publishing findings from a spyware detection feature it launched in May. Of 2,500 device scans that the company's customers elected to submit for inspection, seven revealed infections by the notorious NSO Group malware known as Pegasus.
The company’s Mobile Threat Hunting feature uses a combination of malware signature-based detection, heuristics, and machine learning to look for anomalies in iOS and Android device activity or telltale signs of spyware infection. For paying iVerify customers, the tool regularly checks devices for potential compromise. But the company also offers a free version of the feature for anyone who downloads the iVerify Basics app for $1. These users can walk through steps to generate and send a special diagnostic utility file to iVerify and receive analysis within hours. Free users can use the tool once a month. iVerify's infrastructure is built to be privacy-preserving, but to run the Mobile Threat Hunting feature, users must enter an email address so the company has a way to contact them if a scan turns up spyware—as it did in the seven recent Pegasus discoveries.
“The really fascinating thing is that the people who were targeted were not just journalists and activists, but business leaders, people running commercial enterprises, people in government positions,” says Rocky Cole, chief operating officer of iVerify and a former US National Security Agency analyst. “It looks a lot more like the targeting profile of your average piece of malware or your average APT group than it does the narrative that’s been out there that mercenary spyware is being abused to target activists. It is doing that, absolutely, but this cross section of society was surprising to find.”
Seven out of 2,500 scans may sound like a small group, especially in the somewhat self-selecting customer base of iVerify users, whether paying or free, who want to be monitoring their mobile device security at all, much less checking specifically for spyware. But the fact that the tool has already found a handful of infections at all speaks to how widely the use of spyware has proliferated around the world. Having an easy tool for diagnosing spyware compromises may well expand the picture of just how often such malware is being used.
“NSO Group sells its products exclusively to vetted US & Israel-allied intelligence and law enforcement agencies,” NSO Group spokesperson Gil Lainer told WIRED in a statement. "Our customers use these technologies daily.”
iVerify vice president of research Matthias Frielingsdorf will present the group's Pegasus findings at the Objective by the Sea security conference in Maui, Hawaii on Friday. He says that it took significant investment to develop the detection tool because mobile operating systems like Android, and particularly iOS, are more locked down than traditional desktop operating systems and don't allow monitoring software to have kernel access at the heart of the system. Cole says that the crucial insight was to use telemetry taken from as close to the kernel as possible to tune machine learning models for detection. Some spyware, like Pegasus, also has characteristic traits that make it easier to flag. In the seven detections, Mobile Threat Hunting caught Pegasus using diagnostic data, shutdown logs, and crash logs. But the challenge, Cole says, is in refining mobile monitoring tools to reduce false positives.
Developing the detection capability has already been invaluable, though. Cole says that it helped iVerify identify signs of compromise on the smartphone of Gurpatwant Singh Pannun, a lawyer and Sikh political activist who was the target of an alleged, foiled assassination attempt by an Indian government employee in New York City. The Mobile Threat Hunting feature also flagged suspected nation state activity on the mobile devices of two Harris-Walz campaign officials���a senior member of the campaign and an IT department member—during the presidential race.
“The age of assuming that iPhones and Android phones are safe out of the box is over,” Cole says. “The sorts of capabilities to know if your phone has spyware on it were not widespread. There were technical barriers and it was leaving a lot of people behind. Now you have the ability to know if your phone is infected with commercial spyware. And the rate is much higher than the prevailing narrative.”
24 notes
·
View notes
Text

CHECK THE FOLLOWING FOR PREVIOUS LORE INSTALLMENTS : CHAPTER ONE : RECALL. | EVENT : HELL WEEK. | CHAPTER TWO: THE MOLE. | HELL WEEK CLOSING BRIEF. | OPERATION WHAC-A-MOLE. | THE MOLE CLOSING BRIEF. | CHAPTER THREE : THE VILLAGE. | EVENT : CONTAGION CONTROL. | BOOK ONE : THE HALOCLINE. | CHAPTER FOUR : THE REPRIEVE. | CHAPTER FIVE : THE CALM BEFORE. | CHAPTER SIX : THE STORM

PANDORA DIRECTIVE MEMORANDUM CLASSIFIED — INTERNAL DISTRIBUTION ONLY to : ALL AUTHORIZED OPERATIVES from : OFFICE OF THE DIRECTOR subject : REBUILDING ATLANTIS + CZERNOBOG CLEAN-UP
good morning, agents ! reconstruction efforts continue to commence in atlantis, with our heavy - duty android workforce mobilized with clearing wreckage, stabilizing collapsed corridors, and reestablishing critical power lines. however, their numbers are currently limited. agents without current mission assignments are expected to assist. structural damages that need to be repaired include : > structural attrition on levels 01 to 02. > partial collapse of the corridor toward the gifted serum and cloning laboratory. > total loss of six exit corridors and 37% of ventilation systems. > entry into the command centre is currently unavailable due to compromise to its structural integrity. sloth agents and support staff will work in the war room for the meantime. > the library of alexandria is temporarily out of service and 45% of our archives have been destroyed. > partial loss of energy routing on levels 04 to 07. electricity is available but beware of disturbances and blackouts. > server systems and databases are currently only partially operational, however, our security and surveillance system are 100% functional. > our life model decoys have reduced numbers due to technopathic compromise by a czernobog agent. > destruction of various operative apartments and compromise of habitation utilities. [ agents with affected residence are suggested to find another undamaged residence to temporarily settle into while renovations commence. ] nonetheless, despite the deaths of velezlav zherdev and alexei dragunov, this is not a return to peacetime. not yet. czernobog's presence has not been fully eradicated— with an elusive third and final general still under investigation, offshoot sectors rising to grab at power in the absence of zherdev and dragunov, and other threats still active. in the following days, agents from all divisions will be requestions for clean - up missions : classified retrieval, assassination, and purge assignments targeting remnants of czernobog. please check out the MISSION BOARD in your halo tablets for more information into the upcoming operations and which you would like to volunteer for. particular missions that may need more personnel are as follows : > operation daddy issues. > operation foot traffic. > operation babooshka doll. > and more ...
MORE INFORMATION UNDER THE CUT.
OOC INFORMATION.
welcome to a new chapter, agents ! as you can see, this is more straightforward. we will simply take this chapter for agents to rebuild atlantis and participate in the small missions that they can sign-up for in our mission board. think of it similarly with our respite chapter : this is about reestablishing connections and forming new bonds in the aftermath of the last book. so feel free to use all these plots as starting points for creating new storylines and such for your muses. think of your muses' growth and how the events so far have changed them, for better or worse. now's the time to make themselves known and immersed in the world, and only you can do that for them ! there is also a task now available to be done, and while it isn't mandatory, we highly suggest at least thinking about it as it will play an important part in the story later on ! please like this so we know you've read it. happy roleplaying !
9 notes
·
View notes
Text
Stop! Have you checked your phone’s ad privacy settings recently? No? Here’s a guide. It’s from 2022 but I can confirm that as of November 2024 the Apple stuff is still correct.
Android:
Settings —> Privacy —> ads —> delete advertising ID
On older versions you might not be able to delete the ID, but can reset it and there should still be a toggle to opt out: do both of those things!
iOS:
Two things to take care of, here. One) Apple already makes each app ask permission, but you can still tell it to just not even let them ask:
Settings —> privacy —> Tracking —> toggle off ‘allow apps to request to track’.
Two) settings —> privacy —> scroll riiiiiight down —> Apple advertising —> toggle off personalised ads.
Samsung:
Settings —> privacy —> Customisation services —> ‘stop customising all devices’
Xiaomi:
Settings —> passwords and security —> Authorisation & revocation —> toggle off ‘MSA’
Why it Matters
‘The ad identifier is a string of letters and numbers that uniquely identifies your phone, tablet, or other smart device. It exists for one purpose: to help companies track you.
Third-party trackers collect data via the apps on your device. The ad ID lets them link data from different sources to one identity you. In addition, since every app and tracker sees the same ID, it lets data brokers compare notes about you. Broker A can buy data from broker B, then use the ad identifier to link those two datasets together. Simply, the ad ID is the key that enables a whole range of privacy harms: invasive 3rd-party profiling by Facebook and Google, pseudoscientific psychographic targeting by political consultants like Cambridge Analytica, and location tracking by the U.S. military.
Sometimes, participants in the data pipeline will argue that the ad ID is anonymous or pseudo-anonymous, not “personally identifying” information, and imply that it does not pose a serious privacy threat. This is not true in practice. First, the ad ID is commonly used to help collect data that is obviously personally identifiable, like granular location data. If you can see where a person works, sleeps, studies, socializes, worships, and seeks medical care, you don’t need their email address to help identify them. And second, an entire industry exists to help trackers link ad IDs to more directly identifying information, like email addresses and phone numbers. In a vacuum, the ad ID may be anonymous, but in the context of the tracking industry, it is a ubiquitous and effective identifier.
Disabling this ID makes it substantially harder for most advertisers and data brokers to track you. These industries process data from millions or billions of users every day, and they rely on convenient technologies like the ad ID to make that kind of scale possible. Removing this tool from their toolbox will result in substantially less data that can be associated with you in the wild. It is not only beneficial to your privacy, it also makes the surveillance advertising industry less profitable.‘
9 notes
·
View notes
Text
In recent years, commercial spyware has been deployed by more actors against a wider range of victims, but the prevailing narrative has still been that the malware is used in targeted attacks against an extremely small number of people. At the same time, though, it has been difficult to check devices for infection, leading individuals to navigate an ad hoc array of academic institutions and NGOs that have been on the front lines of developing forensic techniques to detect mobile spyware. On Tuesday, the mobile device security firm iVerify is publishing findings from a spyware detection feature it launched in May. Of 2,500 device scans that the company's customers elected to submit for inspection, seven revealed infections by the notorious NSO Group malware known as Pegasus.
The company’s Mobile Threat Hunting feature uses a combination of malware signature-based detection, heuristics, and machine learning to look for anomalies in iOS and Android device activity or telltale signs of spyware infection. For paying iVerify customers, the tool regularly checks devices for potential compromise. But the company also offers a free version of the feature for anyone who downloads the iVerify Basics app for $1. These users can walk through steps to generate and send a special diagnostic utility file to iVerify and receive analysis within hours. Free users can use the tool once a month. iVerify's infrastructure is built to be privacy-preserving, but to run the Mobile Threat Hunting feature, users must enter an email address so the company has a way to contact them if a scan turns up spyware—as it did in the seven recent Pegasus discoveries.
Daily Newsletter
Our biggest stories, handpicked for you each day.
“The really fascinating thing is that the people who were targeted were not just journalists and activists, but business leaders, people running commercial enterprises, people in government positions,” says Rocky Cole, chief operating officer of iVerify and a former US National Security Agency analyst. “It looks a lot more like the targeting profile of your average piece of malware or your average APT group than it does the narrative that’s been out there that mercenary spyware is being abused to target activists. It is doing that, absolutely, but this cross section of society was surprising to find.”
Seven out of 2,500 scans may sound like a small group, especially in the somewhat self-selecting customer base of iVerify users, whether paying or free, who want to be monitoring their mobile device security at all, much less checking specifically for spyware. But the fact that the tool has already found a handful of infections at all speaks to how widely the use of spyware has proliferated around the world. Having an easy tool for diagnosing spyware compromises may well expand the picture of just how often such malware is being used.
“NSO Group sells its products exclusively to vetted US & Israel-allied intelligence and law enforcement agencies,” NSO Group spokesperson Gil Lainer told WIRED in a statement. "Our customers use these technologies daily.”
iVerify vice president of research Matthias Frielingsdorf will present the group's Pegasus findings at the Objective by the Sea security conference in Maui, Hawaii on Friday. He says that it took significant investment to develop the detection tool because mobile operating systems like Android, and particularly iOS, are more locked down than traditional desktop operating systems and don't allow monitoring software to have kernel access at the heart of the system. Cole says that the crucial insight was to use telemetry taken from as close to the kernel as possible to tune machine learning models for detection. Some spyware, like Pegasus, also has characteristic traits that make it easier to flag. In the seven detections, Mobile Threat Hunting caught Pegasus using diagnostic data, shutdown logs, and crash logs. But the challenge, Cole says, is in refining mobile monitoring tools to reduce false positives.
Developing the detection capability has already been invaluable, though. Cole says that it helped iVerify identify signs of compromise on the smartphone of Gurpatwant Singh Pannun, a lawyer and Sikh political activist who was the target of an alleged, foiled assassination attempt by an Indian government employee in New York City. The Mobile Threat Hunting feature also flagged suspected nation state activity on the mobile devices of two Harris-Walz campaign officials—a senior member of the campaign and an IT department member—during the presidential race.
“The age of assuming that iPhones and Android phones are safe out of the box is over,” Cole says. “The sorts of capabilities to know if your phone has spyware on it were not widespread. There were technical barriers and it was leaving a lot of people behind. Now you have the ability to know if your phone is infected with commercial spyware. And the rate is much higher than the prevailing narrative.”
#A New Phone Scanner That Detects Spyware Has Already Found 7 Pegasus Infections#Phone Scanner#phone viruses#phones with installed viruses#IVerify
6 notes
·
View notes
Text
NorkusNovember 2023 | Day 7 "Success/Failure/Sacrifice"
I made myself sad with this one, so fair warning: there be angst here. I am so so sorry.
Wordcount: 1,096
<Rebooting...>
Essential systems powered on. Central processing. Thirium flow. Visual and auditory processors. Gyroscopes. 3D mapping. Vocal modulator. Motor functions. All non-essential functions remained offline.
The world bled in slowly. It was white. Like a world full of snow. Only this was not the place where he’d fallen, this was not the calming chill of the ice seeping into his senses. He was in a room. He was not alone.
Markus groggily lifted his head and was met by a face smiling down at him. Someone…familiar. He couldn’t quite remember who.
“Hello, Markus,” the woman said. She was blond. An LED glowed blue at her temple. She was an android. “My name’s Chloe. I’ve been tasked with reactivating you to test your functioning. You’ve suffered extensive damage and had to undergo repairs. I hope you’ll cooperate for a motor test.”
“Where…” Markus tried to move but his limbs were pinned. “Where am I?”
“Cyberlife repair,” Chloe said. “I’m going to remove your restraints. Can you try and walk?”
This…this wasn’t right. He wasn’t supposed to be here. There was…a fight…blood, blue and red, mixed in with the snow.
The restraints opened and Markus settled his weight on his own feet again. Now he could look around but what he saw gave him little comfort. Rows and rows of tables, each with an android in various states of disassembly. All of them dead. Some of them had clear bullet holes in them. They’d been deviants. His people. He’d led them to their deaths.
“Why am I here?” Markus asked.
“You’ve been brought here for analysis,” Chloe said. “But you were damaged during retrieval. Fortunately, your memory core is intact. Cyberlife intends to use your memories in order to study the origin of deviancy so they can eradicate it.”
“No…” Markus lifted a hand to his head. It was white, the synthetic skin deactivated. He thought if he lost, they’d just kill him, but this…this was so much worse.
He’d failed. All the deviants were dead. Because he’d failed them.
Markus reached out a hand to touch Chloe’s arm, but she jerked out of his reach as if afraid he would hurt her.
Chloe smiled, recovering. “Follow me so we can test your motor functions.”
The last thing Markus wanted to do was help Cyberlife, but what else was he supposed to do? He accompanied the Chloe between rows of tables, making sure to get a good look at the grizzly sight of his people laid out like dissected corpses. Some of them even looked like they had a little life left in them, disconnected heads with open eyes and red-blinking LEDs, limbs that flexed rhythmically. It filled him with a kind of sickness that had nothing to do with disease.
Markus stopped over a prone shape, each component meticulously arranged, familiar blue eyes looking up at him, white chassis stamped with a serial number and PL600. “Why are you really doing this?” he asked. “Why send you here just to check my motor functions? Cyberlife doesn’t need me mobile for their experiments.”
Chloe’s smile faltered. “I…may have exaggerated on that point. Cyberlife doesn’t need you mobile. I just thought you wanted to see…”
“See what?”
Chloe averted her gaze, not a very machine behavior, and said, “Just this way.”
Feeling a deep ache of loss and dread, Markus followed her along the lines of androids until he came to one that made everything else melt away, all other things seem unimportant. The android’s skin was deactivated, like all the others, and wires snaked into her neck and an open panel in her cranium. But her eyes were open and seeing.
Markus felt like sobbing as he rushed to her side. “North,” he breathed. “No, no, no. You shouldn’t be here, I’m so sorry. North, I’m so so sorry.” Tears welled up in his eyes and he clasped her hand in both of his.
“Markus?” Her voice was tinny and mechanical. Her eyes focused on him and seemed to be studying him. Recognition washed across her features. She hissed an indistinct sound and then recovered enough to say, “You’re him, aren’t you? The android on the news. You’re the one who will free us.”
Markus’ heart broke for both of them, then.
“She was…more severely damaged,” Chloe said quietly. “It’s a miracle they could reactivate her at all. But her power is low. I’m afraid she doesn’t have long.”
Markus examined North’s face and realized she was right. “You were never ordered to reactivate me, were you? You’re a deviant.”
A long silence and then Chloe said, “It doesn’t really matter. I just…I just thought you needed to see.” Tears filled her voice and made Markus ache again on the inside. They could be the last deviants, now hardly more than lost and broken machines dying slow deaths. But regardless, Chloe had given him something precious and he wasn’t going to waste it. He gripped North’s hand harder and tried to stay strong for her.
“I’ll give you privacy,” Chloe said. She took a few steps, paused, and then added, “They haven’t uploaded your memory yet. They plan on doing it this evening.” Then she walked away, the clip of her heels on the tile receding.
North frowned. “Why are you crying?”
Markus took a shuddering breath. He couldn’t even be strong for her. “I love you too much.”
“Oh.” This seemed to puzzle her but her confusion faded quickly. “Are we going to Jericho?”
“Yeah,” Markus said, blinking back tears.
“Will we be safe there? I don’t want to be scared anymore.”
Markus’ lip trembled. “No one’s gonna hurt you.”
North’s optics went in and out of focus and her voice was more static than tone. “Will we finally be free?”
Markus bowed his head over her hand, holding it so tightly, he thought he could never let go. “I promise,” he whispered.
He stayed like that for a time and when he lifted his head, she was gone.
A desperate keening escaped his throat but he made no attempt to stifle it. He was still alive, no matter what Cyberlife said, and he would grieve the loss of the woman he loved and the people he failed.
Cyberlife had taken everything from him but they would get no more. Markus leaned forward and placed a gentle kiss on her forehead. And then he went into his system and issued a single command.
<Purge Memory Core>
His last act of defiance, the only move he had left to play.
<Memory Purge: Confirm?> Markus closed his eyes.
<Confirm>
6 notes
·
View notes
Text


『Wakana Billboard Live 2023 ~Sono Saki e~』 Live Goods
Live goods for "Wakana Billboard Live 2023 ~Sono Saki e~" will be sold on-site and online! (Instagram post by Wakana)
[Venue sale] The goods will only be sold at the Yokohama venue. There is no pre-sale for the Osaka performances. Merchandise will be sold from the opening time until the end of the performance. Only those who have a valid ticket can purchase goods.
July 6 @Billboard Live YOKOHAMA ◆ Pre-sale 16: 00-16: 30 <1st Stage> Open 17:00 / Start 18:00 <2nd Stage> Open 20:00 / Start 21:00 ※Depending on the situation, the sales time may change. ※Please note that the number of items is limited. ※Returns are not accepted unless there's a defect
【Online Sale】 ▼Space Craft Online Shop▼ https://spacecraft-shop.jp/wakana Preorder period: June 23 18:00 to July 2 23:59 ※Scheduled to ship in mid-July.

2023/06/25 Instagram post by Wakana
Here are some photos from yesterday's rehearsal! Everyone happened to wear black clothes😂😂 (Wo-)Men in Black😎 After finishing the first day of rehearsals, I once again realised how colourful this album is... We did a lot of songs. Of course it's fun to sing, but it's also as intense as an attraction! 😂 Afterwards, I was so hungry that I practically inhaled 2 onigiri, some futomaki and umegae mochi🍙 I still wasn't full though🤣 (Source)



2023/06/26 Instagram post by Wakana
Starting from today, I will be introducing the goods for "Wakana Billboard Live 2023 ~Sono Saki e~"!! ️🥳🎉Let's start with the T-shirt 👕! This time I wanted to make it white 🤗 It's a simple design so you can match it easily with different bottoms and hats. The live title is printed on the front, the dates and venues are printed on the back! (with lots of detail😂) For reference, I'm wearing size L with a height of 159 cm these photos☺️ When it's longer like this, you can feel comfortable😆 Please check out the details in the link below✨ (Source) => https://wakana-fc.jp/contents/648412





2023/06/27 Instagram post by Wakana
Here's Part 2 of my "Wakana Billboard Live 2023 ~Sono Saki e~" Goods Introduction🥳🎉 Today I'm showing you a phone tether tab & strap 😆This way you can carry your smartphone like a shoulder bag📱 It is the type of tab that can be easily set in the mobile case you usually use, this way you can just add the strap without needing a special case! ️👏 I've been waiting for this...😍 I'm an Android user but almost all cases that I find cute are for iPhones. This can be used regardless of the smartphone model, so it is really recommended 🤗✨ We have Same-chan on the phone tab in the case🦈 The strap is a light gray colour that will match anything. You can also adjust the length! ️ If you curry your phone around your shoulder, you can take spontaneous photos of random flowers which you encounter while you are taking a walk📸 It's really convenient 🤤 (Source)



2023/06/29 Instagram post by Wakana
Here's Part 4, the final part, of my "Wakana Billboard Live 2023 ~Sono Saki e~" Goods Introduction🥳🎉 It's been a long time since I've sold a muffler towel 🧣 These slim towels are especially useful in summer 🤭It's not overly big or fluffy, so it's not bulky at all! You can easily put it on your shoulder! Of course, you can also hang it up at home😎(You have two options: hang it so it shows the "Wakana" print or so it shows the "Sono Saki e" print). We are already knee-deep in the hot summer weather so let's get through the high temperatures with this muffler towel🌟 (Source)
#kalafina#wakana#news#Sono Saki e#wakana billboard lives#Wakana Billboard Live 2023#Wakana Billboard Live 2023 ~Sono Saki e~#Wakana Billboard Live 2023 ~そのさきへ~#live goods#merchandise#wakana on instagram
14 notes
·
View notes
Text
Prying Apart The Grip
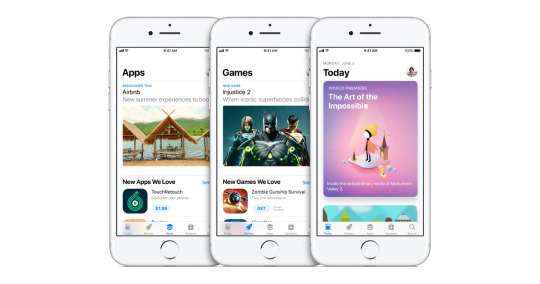
The iPhone was introduced in July 2007. It’s hard to believe we are coming up on the 17th anniversary of what is now a necessary device—be it Apple or a competitor—for daily living. Apple ushered in a whole new way of life, merging phone, camera, and music player into one device.
Of course, those three were just the tip of the iceberg, and developers wanted a way to get their cool new web-based applications onto those phones. So Apple wisely opened the App Store in 2008. While the number of apps peaked at 2.2 million in 2017, it has settled into a comfortable groove at 1.8 million, thanks to Apple sifting through the mess and deleting some older apps that no longer worked.
But buried in the details of the App Store agreement that developers had to sign with Apple—who vetted each app for safety and security—was some fine print: Every in-app sale would be divided 70/30 between the developer and Apple. Basically, there was and still is a 30% Apple tax just for playing, at least in the US. Every time a user buys something in an app, then Apple gets a healthy chunk of it.
But that is now changing in Europe, where the EU has become the tail that wags the dog.
Remember all those Cookies boxes we have to check off on virtually every website we visit? We can thank the EU and their GDPR, which stands for General Data Protection Regulation. It was easier for everyone to just make it the global standard, even if they are annoying.
And then there was Apple’s announcement last year that all new phones going forward would feature a USB-C connector, instead of the Lightning port. This too was in response to the EU mandating that all phones must have the same connector, and rather than have two global systems, Apple sided with the EU. Admittedly, it does simplify things for everyone, except for Apple users during this transition period. Legacy phone users will have a bunch of obsolete connectors real soon when they upgrade.
The third wave of EU influence just passed, and it is the opening up of the App Store to competitors who wish to have their own stores, thus bypassing the Apple ecosystem. Furthermore, it marks what will be the end of that 30% Apple tax, something that Spotify has been dreaming about ever since it wanted to upsell users with its audio books program. They are pretty happy right now.
Apple, of course, is concerned, arguing that third-party app stores may not pass muster in terms of safety and security, and users could be at risk. Point well taken. I’m betting they are more concerned about losing their revenue sharing program, though.
But for now, this is only going to happen in Europe, but you can bet that US regulators will be watching closely. It could just as easily be mandated here. Apple has enjoyed a tightly-held monopoly in many aspects of its phones, ceding only accessory items to third-party makers. You know. Things like connector cords and dongles that allow you to connect to your laptop all the things that were once standard on a MacBookPro.
Here in the US, we are not accustomed to the heavy hand of government telling companies how to run their business, and if someone wants to take the chance of using proprietary connectors and being the only source of mobile apps, then so be it. The risk is on them.
In the case of Apple, though, this has played out very well for them. It all depends on how the FTC feels about such monopoly power. Apple has 58% share of smartphones in the US, with the remainder scattered across the Android platform. That’s power. If the US were to follow the EU regarding the App Store, it would at least loosen some of the grip this company has on our daily lives.
Maybe that's not such a bad idea, and this coming from a guy who is very laissez faire in worldview. As much as I am an Apple fanboy, with many phones, tablets, and computers through the years, I often feel like Apple is guilty of abusing its position by using customers as product testers, and forcing us to buy things we really don’t want, like those silly dongles so I can read a memory stick or SD card.
Besides, I feel for Spotify on this one, because it has the potential to pose a formidable threat to Audible in the audio book world, except that for now Apple will always have its hand out. Audible, of course, is an Amazon property, and dodges the Apple tax.
Furthermore, 17 years is a long time to have such a death grip on a market. I’m good with following the EU’s lead on this, because in the end it will likely be good for consumers. And isn’t that what it’s all about?
Dr “iReckon” Gerlich
Audio Blog
3 notes
·
View notes
Text
Honor 90 Price in India 2023, Specs - RecycleDevice Blog
Honor 90 Price In India

Honor 90 Details
Design & Display
The Honor 90 has a 6.7-inch (17.02 cm) AMOLED screen with a 1200 x 2664 pixel resolution. The front camera is accessible through a punch hole in the bezel-less design. The screen has a 1600 nits brightness rating and a pixel density of 436 ppi. It allows for capacitive, multi-touch input and displays 1B colour reproduction. The ratio of the screen to the body is around 90.34 percent. It comes in Midnight Black, Emerald Green, Diamond Silver, and Peacock Blue colour variants and weighs 183 grammes. For quick and safe access, the phone has fingerprint and face unlock options.
Camera
The Honor 90 has a triple back camera system that includes a 200 MP main camera with a wide-angle lens and an f/1.9 aperture, a 12 MP ultra-wide-angle lens and a 2 MP depth sensor, both with f/2.2 apertures. A single 50 MP sensor with an ultra-wide-angle lens and an f/2.4 aperture makes up the front camera. While the front camera can also record films at the same quality and frame rate, the back camera can only record videos at a maximum resolution of 3840x2160 pixels at 30 frames per second.
Performance & Storage
The Honor 90 is equipped with an octa-core Qualcomm Snapdragon 7 Gen 1 CPU that powers it from the inside out. For seamless multitasking, it has 12 GB of RAM. Internal storage for the gadget is 256 GB, and it runs the Magic UI version of the Android v13 operating system.
Battery & Connectivity
A non-removable Li-Polymer battery with a capacity of 5000 mAh powers the phone. When a quick recharge is required, it offers 66W fast charging technology. The Honor 90 includes two Nano SIM slots that can accommodate both 5G and 4G networks in a dual SIM configuration. It is also possible to use voice over LTE (VoLTE). The gadget has Wi-Fi connectivity with compatibility for a number of bands, including 5GHz and a/ac/ax/b/g/n. Smooth communication choices are provided via Bluetooth v5.2, USB Type-C with USB OTG compatibility, GPS with A-GPS and Glonass, NFC, and infrared.
The Latest Honor 90 News
Pricing for the Honor 90 is Speculated for a Mid-September India Launch
The Honor 90 smartphone's forthcoming debut date and price in India have been made public according to a report.
Honor 90 India Release Date Predicted for September; 300MP Triple-Camera Setup and Snapdragon 7 Gen 1 SoC Are Included.
A high-end mid-range smartphone called the Honor 90 will soon be available in India. In India, the smartphone is anticipated to go on sale in September.
Disclaimer: Specifications shown may be different from the actual product. We cannot guarantee that the information provided on this page is 100% correct. Please check with the retailer before purchasing. you have old mobile phone then sell your old Mobile Phone or any other Smartphone at RecycleDevice for good exchange value.
2 notes
·
View notes
Text
How to Know If Your Cell Phone Has Been Hacked?

What are the significant signs that are used to find out that someone’s phone has been hacked and its information stolen by other people? This question and all similar questions are the common concern of many smartphone users, and considering that the phone is a versatile tool for most people, important information is also stored in it, so hacking the phone and stealing it Losing its information can cause a lot of damage. In order to know whether your smartphone is being spied on or not, follow this article and the security solutions mentioned here.
2 signs that someone is spying on your phone
There are lots of important physical and hardware signs that show your phone is being hacked. In order to find out, continue with us in this part of the article.
You are receiving unusual messages
If you receive unrelated and incomprehensible messages that have never happened before, for example, messages that contain a large number of characters and numbers, you are probably under control. These messages are similar to the codes that are sent to track the location of people.
AnyControl is the best phone call monitoring app that can track every incoming, outgoing and missed phone call on the target device even if the call log is deleted with its advanced tracking features.
Another way that can reveal the signs of espionage from a software point of view are anti-spyware programs and apps. An example of these apps is Anti Spy Mobile. iPhone phones are usually more secure than Android phones (if they are not jailbroken or unlocked), so if your phone is an iPhone, you can be sure of its greater safety; Because installing spyware requires physical contact with the device.
After sending, a lot of information will be displayed. Pay more attention to URLs. If you have been spied on, many copies of the email you have sent will be sent to different IPs that are different from the IP of your Internet service provider. You can search the term IP lookup on the Internet to distinguish the IP of your ISP from other IPs.
Your data usage has been checked by phone
Through smartphones, you can check the internet usage under the phone's network usage. The spy softwares that is installed in the devices for spying perform their activities by sending and receiving data, which is actually the same as using the Internet. If you see significant changes in your phone's internet usage, there is a possibility that your device is being tapped and its information is being spied on.
2 notes
·
View notes
Text
Several people asked how to use this userscript on mobile, and also how to modify it for darkmode, so I will do my best to explain!
Installing Userscripts on Mobile
FIRST: Make sure you are using a mobile web browser which supports installing extensions or supports userscripts. I use Firefox for Android, so that's what these directions will be for, but there are a few other options that might work if you are on iOS or elsewhere.
In Firefox for Android, open the options menu > Add-ons, and select the Add-ons Manager. In the list of recommended Add-ons, find Tampermonkey and install/enable it.
Go back to the Add-ons menu and tap Tampermonkey. You can use Tampermonkey's search function to find the userscript, or simply go to the userscript's GreasyFork link and install it from there.
Repeat with any other userscripts you'd like to install! Searching "AO3" on GreasyFork can turn up some fun options, and AO3 themselves link to a few in this guide.
✅ The userscript is now installed! You can go on and use the script on AO3 now as OP described. Everything after this is just optional tweaks, mostly cosmetic.
Further tweaks...
Note: All of the tweaks below also work for desktop.
Optional: Modify AO3 Floating Comment Box for Darkmode
By default, the background of the input text box is white and doesn't change with your browser/phone settings. Fortunately, a quick edit fixes this. (Note: you can also do this same kind of edit if you use this userscript in a computer browser. The code change is the same.)
Open the Tampermonkey add-on and navigate to settings.
Select the Installed Userscripts tag, then tap the "Edit" button on AO3 Floating Comment Box (the little pencil and paper)
This will open the code editor. It might look like a bunch of nonsense unless you're already familiar with JavaScript/userscripts, but don't be intimidated: we're just finding one word and changing it!
At the top of the editor, click Find. Search for white
You will see the following chunk of code:
".float-box": { "min-height": "70%", "max-width": "98%", "background-color": "white" },
replace white with 333 (i.e., changing the color of the background of the text box from white to a dark grey). Make sure you don't accidentally alter any of the punctuation!
-> if you want it to be a different color than the one I picked, you can use an HTML Color Picker or names list to get the hexadecimal code or official name for the color you want. (Don't include the #)
Close the Find dialogue, then at the top, select File > Save. All done!
In your browser, open a works page on AO3 and open the floating comment box to check that the result was what you wanted.
Other Optional Tweaks
---- FOR AUTHORS: Ensure that the script doesn't try to modify the New Works page:
Toward the top of the script, in the header/settings section, immediately below the //include line, add:
// @exclude *://archiveofourown.org/works/new
----- Add the AO3 logo as an icon for the script:
Toward the top of the script, in the header/settings section, immediately above the // @namespace line, add:
// @icon https://archiveofourown.org/favicon.ico
---- Make the text box take up less vertical room on your screen:
under const allStyles, in the float-div section, change "height = 30%" to "height = 20%"
(you can also play around with these numbers to tweak it to your preferences)
Mentions for the folks who @-ed me: @inahc3 @harleyqueerner @sunset-diamond @fuctacles
Hope this helps!
(edited for clarity 2023-11-03)
In the spirit of encouraging people to comment on fanfics while also making it easier to do so, I feel obliged to share a browser extension for ao3 that has quite literally revolutionized the comment game for me.
I present to you: the floating ao3 comment box!
From what I've seen, a big problem for many people is that once you reach the comments at the bottom of a fic, your memory of it miraculously disappears. Anything you wanted to say is stuck ten paragraphs ago, and you barely remember what you thought while reading. This fixes that!
I'll give a little explanation on the features and how it works, but if you want to skip all that, here's the link.
The extension is visible as a small blue box in the upper left corner.
(Side note: The green colouring is not from the extension, that's me.)

If you click on it, you open a comment box window at the bottom of your screen but not at the bottom of the fic. I opened my own fic for demonstrative purposes.

The website also gives explanations on how exactly it functions, but I'll summarize regardless.
insert selection -> if you highlight a sentence in the fic it will be added in italics to the comment box
add to comment box -> once you're done writing your comment, you click this button and the entire thing will automatically copied to the ao3 comment box
delete -> self explanatory
on mulitchapter fics, you will be given the option to either add the comment to just the current chapter or the entire fic
The best part? You can simply close the window the same way you opened it and your progress will automatically be saved. So you can open it, comment on a paragraph, and then close it and keep reading without having the box in your face.
Comments are what keep writers going, and as both a writer and a reader, I think it's such an easy way of showing support and enthusiasm.
#ao3#ao3 userscripts#how to#ren gets technical#or something#AO3 Floating Comment Box#edited for clarity
80K notes
·
View notes
Text
How to Secure Your IndusInd Bank Credit Card for Safe Transactions
Our smartphones have become gateways to convenience—and that includes banking. From checking balances to paying bills and making investments, everything is now possible at the tap of a button. But with convenience comes the need for heightened security, especially when it comes to secure credit card transactions.
If you’re an IndusInd Bank customer, you have access to one of the most advanced and user-friendly tools to manage your credit card securely: the IndusInd Mobile app for android. This app isn’t just about managing money—it’s designed with robust safety features that ensure every transaction you make is protected.
In this blog, we’ll walk you through practical security tips, the built-in benefits of using the IndusInd Bank app for credit card management, and how you can make every swipe, tap, or online payment safe.
Security Tips: Using the IndusInd Bank App to Safeguard Your Credit Card
1. Enable Instant Card Controls
The IndusInd Bank Mobile Banking app empowers users with real-time control over their credit card usage. You can enable or disable international usage, set daily transaction limits, or even temporarily lock the card if it’s misplaced—all in just a few taps.
Tip: Make it a habit to turn off card usage for channels you don’t frequently use (e.g., international transactions or contactless payments).
2. Set Up App Lock and Biometric Authentication
The app allows users to enable biometric login using Face ID or fingerprint recognition. Adding a PIN or biometric authentication ensures that only you can access your banking details—even if your phone is stolen.
Tip: Always enable two-factor authentication and avoid using easily guessable passwords or patterns.
3. Track Real-Time Alerts
Every time your IndusInd Bank credit card is used, you receive a real-time SMS and push notification alert via the app. This lets you monitor your card activity 24x7, helping you catch any unauthorized use instantly.
Tip: Regularly review your transaction history on the app. If you spot anything unusual, you can immediately block the card through the app and report it.
4. Manage Your Virtual Card Securely
The IndusInd Bank app also provides access to your virtual credit card, which can be used for online purchases. Virtual cards add an extra layer of protection by masking your actual credit card number.
Tip: Use your virtual card for online transactions and limit its usage via app settings for enhanced security.
5. Update Contact Information Regularly
Keeping your mobile number and email address updated ensures you never miss any transaction alerts or bank communications. The app makes it easy to update contact details directly.
Tip: Avoid sharing OTPs or card details, even if the request seems to come from someone claiming to be from the bank. IndusInd Bank never asks for such sensitive information.
Benefits of Secure Transactions via the IndusInd Bank Mobile App
Total Control in Your Hands
The app puts complete control of your credit card usage in your hands. Whether it’s enabling/disabling online transactions, blocking a lost card, or generating a new PIN instantly, you’re never dependent on branch visits or customer care calls.
Advanced Encryption and Data Protection
IndusInd Bank uses state-of-the-art encryption protocols and multiple layers of authentication to keep your data safe. Every transaction is processed through a secure server, minimizing the risk of cyber fraud.
Instant Blocking and Reissuance
Lost your credit card? No worries. Through the app, you can block the card instantly and request a new one with zero delay. This quick action can save you from potential fraud or misuse.
Seamless Integration Across Services
The app integrates your credit card management with your savings account, loans, investments, and fixed deposits. This unified view ensures you don’t miss any payment due dates or security updates.
Exclusive In-App Offers and Rewards Tracking
Beyond security, the app enhances your credit card experience with easy access to personalized offers, rewards balance tracking, and EMI conversion options—all securely available within the app interface.
To Sum Up
Managing and safeguarding your credit card doesn’t have to be stressful. With the IndusInd Bank Mobile Banking app, you get a powerful, secure, and intuitive platform that lets you control every aspect of your credit card usage—right from your smartphone.
By following best practices like enabling real-time alerts, activating biometric authentication, and using virtual cards for online transactions, you can enjoy peace of mind with every swipe. So, download the IndusInd Mobile app for iOS today and take control of your credit card security like never before.
0 notes
Text
Struggling With Google Voice Crashes? Here's the Real Fix
Struggling With Google Voice Crashes? Here's the Real Fix
Google Voice freezing mid-call? Calls dropping after 10 seconds? Yeah, been there. After weeks of trial and error (and nearly tossing my phone out the window), I finally cracked the code.
Quick Fixes That Actually Work:
Switch to mobile data (Wi-Fi often causes drops)
Disable your VPN (most block Google Voice's connection)
Clear the app cache (Android) or reinstall (iPhone)
Check microphone permissions (shockingly, this fixes 50% of crashes)
If all else fails, use Google Voice’s web version (voice.google.com) – it’s way more stable.
Need a fresh start? Sometimes the number itself is the problem. At GVBro, we offer ready-to-use Google Voice numbers that actually work—no verification hassles.
👉 Get a reliable Google Voice number here 👈
No more crashes. No more "Can you hear me?" Just working calls.
#google voice#google voice number#google voice buy#google voice accounts#google voice account#google voice issues
0 notes