#Credential Stuffing Attack
Explore tagged Tumblr posts
Photo

(via Genetics firm 23andMe says user data stolen in credential stuffing attack)
gee how UNEXPECTED
except for everybody that has been expecting this to happen...
29 notes
·
View notes
Text
Securing Access at Machine Speed: Why SASE Is the Architecture for the AI Age
New Post has been published on https://thedigitalinsider.com/securing-access-at-machine-speed-why-sase-is-the-architecture-for-the-ai-age/
Securing Access at Machine Speed: Why SASE Is the Architecture for the AI Age


AI-powered adversaries have redefined what fast looks like. Credential stuffing at machine speed. Behavioral mimicry that defeats anomaly detection. And automated reconnaissance that probes VPNs and lateral movement paths without fatigue or friction. In this threat environment, traditional secure access models are no longer just outdated—they’re dangerous.
According to the 2025 State of Secure Network Access Report, 52% of cybersecurity professionals say remote connectivity is now the single hardest resource to secure. VPNs are breaking under the weight of hybrid work. SaaS and remote endpoints are slipping through fragmented security stacks. The perimeter has not only disappeared—it has dissolved into an unpredictable, cloud-native reality.
In this AI-fueled arms race, Secure Access Service Edge (SASE) isn’t just a security architecture. It’s the foundational control plane for defending the enterprise.
The Real Threat Isn’t Just Exposure — It’s AI-Accelerated Exploitation
Every modern breach involves abuse of access. Whether it’s a compromised VPN session, stolen OAuth token, or overly permissive SaaS role, attackers aren’t breaking in—they’re logging in. AI simply makes this process faster and harder to detect.
Machine learning models can now generate spear phishing payloads tailored to user roles. LLMs are used to write malware and obfuscate scripts. Compromised endpoints feed behavioral data back to attacker systems that refine their evasion tactics in real time.
And yet, most organizations still rely on static policies, brittle network controls, and legacy access methods. The result? An unguarded runway for AI-assisted lateral movement.
SASE: Designed for This Moment
SASE unifies SD-WAN, Zero Trust Network Access (ZTNA), Secure Web Gateway (SWG), Cloud Access Security Broker (CASB), and Firewall-as-a-Service (FWaaS) into a single, cloud-delivered fabric. It treats access not as a static configuration, but as a dynamic decision.
Every request is evaluated in real time. Who is the user? What device are they on? Where are they logging in from? Are they behaving like themselves? Based on this context, access is granted, challenged, or revoked instantly. This is how Zero Trust is enforced in practice—not just in posture decks.
SASE flips the model: users and apps no longer connect to the network. They connect to each other, through policy. And that policy is where your control resides.
Goodbye VPN: Legacy Access Is an Open Door
VPNs are the analog solution to a digital problem. They create flat network access, route traffic inefficiently, and rely on static credentials. They’re slow for users, opaque for defenders, and goldmines for attackers.
The report confirms it: over half of respondents say VPNs are their hardest access layer to secure. High latency. Poor visibility. Inconsistent enforcement. Worse, 42% of organizations say employees themselves are the highest risk group to business security—not outsiders. That’s a damning indictment of legacy access.
SASE eliminates the VPN choke point. Instead of tunneling everything back to a data center, users connect directly to the apps they need—through inspection points that enforce policy, detect anomalies, and block malicious behavior in real time.
AI on Your Side: SASE as Security Infrastructure for Machine Speed
AI threats require AI defenses. But AI can’t protect what it can’t see or control. That’s why SASE is more than just a security delivery model. It’s the infrastructure that enables intelligent, automated defense.
SASE platforms generate unified telemetry across users, devices, locations, apps, and behavior. This rich, normalized data set is what fuels AI-based detection models. It enables machine learning to find patterns, surface anomalies, and continuously optimize policy enforcement.
With SASE in place, you don’t just detect threats faster—you respond in real time. Contextual access controls can throttle bandwidth, trigger re-authentication, or isolate risky sessions automatically. Human responders focus on strategy, not fire drills.
The Choice Is Now: Fragmented or Future-Proof
SASE isn’t a trend. It’s an inevitability. The question is whether organizations adopt it on their terms—or after a breach forces their hand.
In an AI-dominated threat landscape, the winners will be those who design for machine-speed security. Unified visibility. Adaptive controls. Real-time enforcement. These are not future requirements. They are today’s minimums.
SASE makes them possible.
So the real question isn’t whether you can afford to deploy SASE.
It’s whether you can afford not to.
#2025#adversaries#ai#AI-powered#analog#anomalies#anomaly#anomaly detection#apps#architecture#attackers#authentication#Behavior#behavioral data#breach#Business#business security#CASB#Cloud#cloud-delivered#Cloud-Native#connectivity#credential#credential stuffing#credentials#cybersecurity#cybersecurity insiders#data#Data Center#defenders
0 notes
Note
I'm not the most security savvy but two-factor authentication makes me deeply suspicious. Is it actually more secure or is it just annoying? Especially the ones that send a code to your phone that pops up in your notifications.
It is genuinely, massively, TREMENDOUSLY more secure to use 2FA/MFA than to not use it.
One of our clients is currently under attack by a group that appears to be using credential stuffing; they are making educated guesses about the accounts they're trying to lot into based on common factors showing up in the credentials in years of pastes and breaches and leaks. Like, let's say it's a professional arborist's guild and their domain is arborist.tree and they've had three hundred members who have had their credentials compromised in the last ten years and the people looking at all the passwords associated with arborist.tree noticed that the words "arboreal" and "conifer" and "leaf" and "branch" show up over and over and over again in the passwords for the members of the professional arborist's guild.
So they can make an educated guess for how to log in to accounts belonging to the tree-loving tree lover's club, combine that with the list of legitimate emails, and go to town.
And they are in fact going to town. We're getting between 1000 and 4000 login attempts per hour. It's been happening for a couple weeks.
And every single one of those attempts is failing - in spite of some pretty poor password practices that believe me, I have been doing some talking about - as a result of having MFA enforced for the entire group. They all use an app that is synced to their individual accounts with a mobile device, except that sometimes you have trouble getting a code when you're up in a tree so some of them have physical MFA tokens.
People try to sign into my tumblr sometimes. To those people I say: lol, good luck, I couldn't guess my own password with a gun to my head. But if I *did* have some password that was, like "tiny-bastard-is#1" they would also need access to my email address because I've got MFA set up on tumblr. And to THAT I say: lol, good luck, it's complex passwords and MFA all the way down.
Of the types of MFA that most people will run across, the most secure to least secure hierarchy goes physical token>app based one-time-passwords>tie between email and SMS. Email and SMS are less preferred because email is relatively easy to capture and open in transit and cellphone SIMs can be cloned to capture your text messages. But if you are using email or SMS for your authentication you are still miles and miles and miles ahead of people who are not using any kind of authentication.
MFA is, in fact, so effective that I only advise people to turn it on if they are 100% sure that they will be able to access the account if they lose access to the device that had the authenticator on it. You usually can do this by saving a collection of recovery codes someplace safe (I recommend doing this in the secure notes section of your password manager on the entry for the site in question - if this is not a feature that your password manager has, I recommend that you get a better password manager, and the password manager I recommend is bitwarden).
A couple weeks ago I needed to get into a work account that I had created in 2019. In 2022, my boss had completely taken me off of managing that service and had his own account, so I deleted it from my authenticator. Then in 2024 my boss sold the business but didn't provide MFA for a ton of the accounts we've got. I was able to get back into my account because five years earlier I had taken a photo of the ten security codes from the company and saved them in a folder on my desktop called "work recovery codes." If you are going to use MFA, it is VITALLY IMPORTANT that you save recovery codes for the accounts you're authenticating someplace that you'll be able to find them, because MFA is so secure that the biggest problem with it is locking people out of their accounts.
In any kind of business context, I think MFA should be mandatory. No question.
For personal accounts, I think you should be pointed and cautious where you apply it, and always leave yourself another way in. There are SO MANY stories about people having their phones wiped or stolen or destroyed and losing MFA with the device because they didn't have a backup of the app or hadn't properly transferred it to a new device.
But it's also important to note that MFA is not a "fix all security forever" thing - I've talked about session hijacking here and the way you most often see MFA defeated is by tricking someone into logging in to a portal that gives them access to your cookies. This is usually done by phishing and sending someone a link to a fake portal.
That is YET ANOTHER reason that you should be using a good password manager that allows you to set the base domain for the password you're using so that you can be sure you're not logging in to a faked portal. If your password manager doesn't have that feature (setting the domain where you can log in to the base domain) then I recommend that you get a better password manager (get bitwarden.)
In 2020 my terrible boss wanted me to write him a book about tech that he could have run off at a vanity press and could give to prospect customers as a business card. That was a terrible idea, but I worked on the book anyway and started writing it as a book about security for nontechnical people. I started out with a very simple statement:
If every one of our customers did what we recommend in the first four chapters of this book (make good backups, use a password manager and complex unique passwords, enable MFA, and learn how to avoid phishing), we would go out of business, because supporting problems that come from those four things is about 90-95% of our work.
So yes, absolutely, please use MFA. BUT! Save your recovery codes.
830 notes
·
View notes
Note
"Genetics firm 23andMe confirms user data theft in a credential stuffing attack. The hackers released 1 million lines of data targeting Ashkenazi Jews and Chinese descent" this is so scary, wtf
OK followers this is not a drill. This is now the time to start calling out the antisemitism in your friends and family. This is truly some nazi level eugenics shit. I'm at work but I'd appreciate more help boosting what to do.
mod ali
Update:
Please send this to all your Jewish and Chinese friends and family. Stay safe and please boost this.
4K notes
·
View notes
Text
A study of over 19 billion exposed passwords has revealed that only 6 percent of the leaked passwords were unique. The vast majority, 94 percent, were reused or duplicated, making them prime targets for cybercriminals.
Common keyboard patterns and easily guessed strings remain prevalent. The "123456" sequence still dominates, appearing in 338 million passwords, according to the Cybernews study.
Why It Matters
The scale of password breaches and the continued reliance on weak passwords have heightened concerns about "credential stuffing," a tactic in which attackers use automated tools to test stolen credentials across multiple platforms.
Even breach success rates between 0.2 percent and 2 percent can still yield thousands of compromised accounts, according to Cybernews.
The most common password length is eight to 10 characters, and a significant portion contains only lowercase letters and digits, making passwords vulnerable to brute-force attacks.
Compared to just 1 percent in 2022, 19 percent of passwords now mix uppercase, lowercase, numbers, and symbols.
What To Know
The dataset analyzed included 19,030,305,929 passwords sourced from 200 cybersecurity incidents. These came from leaked databases, stealer logs, and combolists.
Paul Walsh, CEO of MetaCert, has emphasized another growing risk vector: phishing attacks targeting phones. He has urged cybersecurity companies to tackle SMS phishing with the same intensity as email security to help mitigate password leaks and breaches.
In an article published on Monday, Walsh told Forbes that MetaCert's latest national SMS phishing test, carried out in March and including carriers such as AT&T, Verizon, T-Mobile and Boost Mobile, was concerning.
"Every phishing message was still delivered," Walsh said. "None were blocked, flagged, or rewritten."
Walsh has written an open letter to the cybersecurity industry asking why the SMS phishing problem wasn't solved long ago.
What Are the Most Common Passwords?
Predictable patterns continue to dominate password choices. "123456" alone appears in 338 million of the passwords in the Cybernews study, while "password" and "admin" were used over 100 million times combined.
Users also often rely on names, with "Ana" appearing in 178.8 million instances. Positive words like "love," "freedom," and pop culture references such as "Batman" are also prevalent. Profanity, surprisingly, is common as well; "ass" alone shows up in 165 million passwords.
Some of the most frequently used pop culture terms in passwords included "Mario" (9.6 million), "Joker" (3.1 million), "Batman" (3.9 million), and "Thor" (6.2 million).
Additionally, seasonal words, food items, and cities frequently feature in password choices, leaving accounts vulnerable to attackers who exploit such predictability. Over 10 million of the passwords featured "apple," 4.9 million "rice," and 3.6 million "orange," while 3.3 million opted for "pizza."
The most popular city for passwords was "Rome" (13 million), while "summer" (3.8 million) was the most popular season.
What People Are Saying
Neringa Macijauskaitė, information security researcher at Cybernews: "We're facing a widespread epidemic of weak password reuse. If you reuse passwords across multiple platforms, a breach in one system can compromise the security of other accounts."
MetaCert CEO Paul Walsh told Forbes: "Criminals have already moved in full force, and the industry is failing to respond."
"The cybersecurity industry has no shortage of experts in email security, endpoint protection, or network defense, but when it comes to SMS infrastructure and security, there is a distinct lack of deep expertise."
What Happens Next
Researchers have urged individuals and organizations to boost password security by using password managers, enforcing minimum length and complexity standards, and enabling multi-factor authentication. Organizations are advised to regularly audit access controls, monitor for credential leaks, and adopt real-time detection solutions.
10 notes
·
View notes
Text
Unnecessarily compiling sensitive information can be as damaging as actively trying to steal it. For example, the Cybernews research team discovered a plethora of supermassive datasets, housing billions upon billions of login credentials. From social media and corporate platforms to VPNs and developer portals, no stone was left unturned.
Our team has been closely monitoring the web since the beginning of the year. So far, they’ve discovered 30 exposed datasets containing from tens of millions to over 3.5 billion records each. In total, the researchers uncovered an unimaginable 16 billion records.
None of the exposed datasets were reported previously, bar one: in late May, Wired magazine reported a security researcher discovering a “mysterious database” with 184 million records. It barely scratches the top 20 of what the team discovered. Most worryingly, researchers claim new massive datasets emerge every few weeks, signaling how prevalent infostealer malware truly is.
“This is not just a leak – it’s a blueprint for mass exploitation. With over 16 billion login records exposed, cybercriminals now have unprecedented access to personal credentials that can be used for account takeover, identity theft, and highly targeted phishing. What’s especially concerning is the structure and recency of these datasets – these aren’t just old breaches being recycled. This is fresh, weaponizable intelligence at scale,” researchers said.
The only silver lining here is that all of the datasets were exposed only briefly: long enough for researchers to uncover them, but not long enough to find who was controlling vast amounts of data. Most of the datasets were temporarily accessible through unsecured Elasticsearch or object storage instances.
What do the billions of exposed records contain?
Researchers claim that most of the data in the leaked datasets is a mix of details from stealer malware, credential stuffing sets, and repackaged leaks.
There was no way to effectively compare the data between different datasets, but it’s safe to say overlapping records are definitely present. In other words, it’s impossible to tell how many people or accounts were actually exposed.
However, the information that the team managed to gather revealed that most of the information followed a clear structure: URL, followed by login details and a password. Most modern infostealers – malicious software stealing sensitive information – collect data in exactly this way.
Information in the leaked datasets opens the doors to pretty much any online service imaginable, from Apple, Facebook, and Google, to GitHub, Telegram, and various government services. It’s hard to miss something when 16 billion records are on the table.
According to the researchers, credential leaks at this scale are fuel for phishing campaigns, account takeovers, ransomware intrusions, and business email compromise (BEC) attacks.
“The inclusion of both old and recent infostealer logs – often with tokens, cookies, and metadata – makes this data particularly dangerous for organizations lacking multi-factor authentication or credential hygiene practices,” the team said.
What dataset exposed billions of credentials?
The datasets that the team uncovered differ widely. For example, the smallest, named after malicious software, had over 16 million records. Meanwhile, the largest one, most likely related to the Portuguese-speaking population, had over 3.5 billion records. On average, one dataset with exposed credentials had 550 million records.
Some of the datasets were named generically, such as “logins,” “credentials,” and similar terms, preventing the team from getting a better understanding of what’s inside. Others, however, hinted at the services they’re related to.
For example, one dataset with over 455 million records was named to indicate its origins in the Russian Federation. Another dataset, with over 60 million records, was named after Telegram, a cloud-based instant messaging platform.
“The inclusion of both old and recent infostealer logs – often with tokens, cookies, and metadata – makes this data particularly dangerous for organizations lacking multi-factor authentication or credential hygiene practices,”
While naming is not the best way to deduce where the data comes from, it seems some of the information relates to cloud services, business-oriented data, and even locked files. Some dataset names likely point to a form of malware that was used to collect the data.
It is unclear who owns the leaked data. While it could be security researchers that compile data to check and monitor data leaks, it’s virtually guaranteed that some of the leaked datasets were owned by cybercriminals. Cybercriminals love massive datasets as aggregated collections allow them to scale up various types of attacks, such as identity theft, phishing schemes, and unauthorized access.
A success rate of less than a percent can open doors to millions of individuals, who can be tricked into revealing more sensitive details, such as financial accounts. Worryingly, since it's unclear who owns the exposed datasets, there’s little impact users can do to protect themselves.
However, basic cyber hygiene is essential. Using a password manager to generate strong, unique passwords, and updating them regularly, can be the difference between a safe account and stolen details. Users should also review their systems for infostealers, to avoid losing their data to attackers.
No, Facebook, Google, and Apple passwords weren’t leaked. Or were they?
With a dataset containing 16 billion passwords, that’s equivalent to two leaked accounts for every person on the planet.
We don’t really know how many duplicate records there are, as the leak comes from multiple datasets. However, some reporting by other media outlets can be quite misleading. Some claim that Facebook, Google, and Apple credentials were leaked. While we can’t completely dismiss such claims, we feel this is somewhat inaccurate.
Bob Diachenko, a Cybernews contributor, cybersecurity researcher, and owner of SecurityDiscovery.com, is behind this recent major discovery.
16-billion-record data breach signals a shift in the underground world
According to Cybernews researcher Aras Nazarovas, this discovery might signal that criminals are abandoning previously popular methods of obtaining stolen data.
"The increased number of exposed infostealer datasets in the form of centralized, traditional databases, like the ones found be the Cybernews research team, may be a sign, that cybercriminals are actively shifting from previously popular alternatives such as Telegram groups, which were previously the go-to place for obtaining data collected by infostealer malware," Nazarovas said.
He regularly works with exposed datasets, ensuring that defenders secure them before threat actors can access them.
Here’s what Nazarovas suggests you should do to protect yourself.
"Some of the exposed datasets included information such as cookies and session tokens, which makes the mitigation of such exposure more difficult. These cookies can often be used to bypass 2FA methods, and not all services reset these cookies after changing the account password. Best bet in this case is to change your passwords, enable 2FA, if it is not yet enabled, closely monitor your accounts, and contact customer support if suspicious activity is detected."
Billions of records exposed online: recent leaks involve WeChat, Alipay
Major data leaks, with billions of exposed records, have become nearly ubiquitous. Last week, Cybernews wrote about what is likely the biggest data leak to ever hit China, billions of documents with financial data, WeChat and Alipay details, as well as other sensitive personal data.
Last summer, the largest password compilation with nearly ten billion unique passwords, RockYou2024, was leaked on a popular hacking forum. In 2021, a similar compilation with over 8 billion records was leaked online.
In early 2024, the Cybernews research team discovered what is likely still the largest data leak ever: the Mother of All Breaches (MOAB), with a mind-boggling 26 billion records.
16 billion passwords exposed: how to protect yourself
Huge datasets of passwords spill onto the dark web all the time, highlighting the need to change them regularly. This also demonstrates just how weak our passwords still are.
Last year, someone leaked the largest password compilation ever, with nearly ten billion unique passwords published online. Such leaks pose severe threats to people who are prone to reusing passwords.
Even if you think you are immune to this or other leaks, go and reset your passwords just in case.
Select strong, unique passwords that are not reused across multiple platforms
Enable multi-factor authentication (MFA) wherever possible
Closely monitor your accounts
Contact customer support in case of any suspicious activity
4 notes
·
View notes
Note
Aurora how is your search going? Surely you found out something by now.
The overweight bunny leaned back on her chair, her belly now resting against the desk, her newly resized belt already unbuckled. She rubbed her glutted middle, trying her hardest not to pass out from a food coma.
"I have -bwaaaaaaarp- made some process" She said, struggling to lean forward to click on her computer.
"There have been some -uuuuuurp- extra donations from a private account towards many companies around the HQ. Normally this wouldn't be weird, but I noticed this started happening around the -bwaaaaarp- time Sarah first started getting fat, at least according to the records on the system"
Despite clearly being stuffed, Aurora couldn't help but munch one more donut, her belly growling and groaning in sign of complaint, but the bunny girl simply had to have more.
"I then -uuuuurp- uhh... 'borrowed' Captain Fortune's credentials to access the main system, there I also found an anonymous donation being done every month towards the squad."
"It's no wonder the higher-ups don't cancel the project, despite not getting attacks from the primodrians for years, they get more money keeping the project alive than shutting it down. Someone out there is funding this entire place, paying the higher-ups so much that they don't care what happens here anymore, and paying every single food chain around to deliver absurd amounts of food here."
The bunny girl took a sip of her soda, feeling her belly pushing even further out, tight like a balloon, completely packed with food "Someone -UUUUUUUUUUURRRP- if fattening up the entire squad. It's not -buuuuuuuurp- just Jinx and Vayne, someone is using them as pawns, fattening them up as well for their own amusement... I just need to figure out who made these donations... -uuuuuuuurp- but first, I think I need to go lie down first.... so -BWAAAAAAAAARP- full..."
3 notes
·
View notes
Text
Winners
Bomb sniffers - One day in and we are back to bomber, even jihad bomber, attacks. This is immediately after the drones in New Jersey that many suspected were sniffing for radioactive material.
Conspiracy Theorists - Particle fog, bombers, drones that vanished from the news, and bird flu cases. A steady flow of crazy news items.
Trump cabinet nominees - Calmed down a bit. The narratives that were rolling along have stopped.
Losers
Vivek - Can he bounce back after the H1B debate? Stick to DOGE.
Spam Email Producers - AI gave them a new tool, and spam is flooding not just your personal inbox but corporate systems.
British Media and Politicians - After a decade of being a suppressed story, the Pakistani rape gangs issue is mushrooming in the public sphere.
Links
Chinese digital espionage is pretty impressive. This Salt Typhoon op will have long term effects.
When I wrote about Rhodes’ ambitious program to sell the Iran deal, I advanced the term “echo chambers” to describe the process by which the White House and its wider penumbra of think tanks and NGOs generated an entirely new class of experts who credentialed each other on social media in order to advance assertions that would formerly have been seen as marginal or not credible, thereby overwhelming the efforts of traditional subject-area gatekeepers and reporters to keep government spokespeople honest.
An explainer on H1B "shenanigans" but the section on EB5 visas might make for a better dig into our sick union of immigration visa scams and bailing out businesses.
Biden administration stuffing all they cant into green boondoggles before the curtain falls.
2 notes
·
View notes
Text
Okta warns of "unprecedented" credential stuffing attacks on customers

Source: https://www.bleepingcomputer.com/news/security/okta-warns-of-unprecedented-credential-stuffing-attacks-on-customers/
More info: https://sec.okta.com/blockanonymizers
5 notes
·
View notes
Text
The Threat of Offensive AI and How to Protect From It
New Post has been published on https://thedigitalinsider.com/the-threat-of-offensive-ai-and-how-to-protect-from-it/
The Threat of Offensive AI and How to Protect From It
Artificial Intelligence (AI) swiftly transforms our digital space, exposing the potential for misuse by threat actors. Offensive or adversarial AI, a subfield of AI, seeks to exploit vulnerabilities in AI systems. Imagine a cyberattack so smart that it can bypass defense faster than we can stop it! Offensive AI can autonomously execute cyberattacks, penetrate defenses, and manipulate data.
MIT Technology Review has shared that 96% of IT and security leaders are now factoring in AI-powered cyber-attacks in their threat matrix. As AI technology keeps advancing, the dangers posed by malicious individuals are also becoming more dynamic.
This article aims to help you understand the potential risks associated with offensive AI and the necessary strategies to effectively counter these threats.
Understanding Offensive AI
Offensive AI is a growing concern for global stability. Offensive AI refers to systems tailored to assist or execute harmful activities. A study by DarkTrace reveals a concerning trend: nearly 74% of cybersecurity experts believe that AI threats are now significant issues. These attacks aren’t just faster and stealthier; they’re capable of strategies beyond human capabilities and transforming the cybersecurity battlefield. The usage of offensive AI can spread disinformation, disrupt political processes, and manipulate public opinion. Additionally, the increasing desire for AI-powered autonomous weapons is worrying because it could result in human rights violations. Establishing guidelines for their responsible use is essential for maintaining global stability and upholding humanitarian values.
Examples of AI-powered Cyberattacks
AI can be used in various cyberattacks to enhance effectiveness and exploit vulnerabilities. Let’s explore offensive AI with some real examples. This will show how AI is used in cyberattacks.
Deep Fake Voice Scams: In a recent scam, cybercriminals used AI to mimic a CEO’s voice and successfully requested urgent wire transfers from unsuspecting employees.
AI-Enhanced Phishing Emails: Attackers use AI to target businesses and individuals by creating personalized phishing emails that appear genuine and legitimate. This enables them to manipulate unsuspecting individuals into revealing confidential information. This has raised concerns about the speed and variations of social engineering attacks with increased chances of success.
Financial Crime: Generative AI, with its democratized access, has become a go-to tool for fraudsters to carry out phishing attacks, credential stuffing, and AI-powered BEC (Business Email Compromise) and ATO (Account Takeover) attacks. This has increased behavioral-driven attacks in the US financial sector by 43%, resulting in $3.8 million in losses in 2023.
These examples reveal the complexity of AI-driven threats that need robust mitigation measures.
Impact and Implications
Offensive AI poses significant challenges to current security measures, which struggle to keep up with the swift and intelligent nature of AI threats. Companies are at a higher risk of data breaches, operational interruptions, and serious reputation damage. It’s critical now more than ever to develop advanced defensive strategies to effectively counter these risks. Let’s take a closer and more detailed look at how offensive AI can affect organizations.
Challenges for Human-Controlled Detection Systems: Offensive AI creates difficulties for human-controlled detection systems. It can quickly generate and adapt attack strategies, overwhelming traditional security measures that rely on human analysts. This puts organizations at risk and increases the risk of successful attacks.
Limitations of Traditional Detection Tools: Offensive AI can evade traditional rule or signature-based detection tools. These tools rely on predefined patterns or rules to identify malicious activities. However, offensive AI can dynamically generate attack patterns that don’t match known signatures, making them difficult to detect. Security professionals can adopt techniques like anomaly detection to detect abnormal activities to effectively counter offensive AI threats.
Social Engineering Attacks: Offensive AI can enhance social engineering attacks, manipulating individuals into revealing sensitive information or compromising security. AI-powered chatbots and voice synthesis can mimic human behavior, making distinguishing between real and fake interactions harder.
This exposes organizations to higher risks of data breaches, unauthorized access, and financial losses.
Implications of Offensive AI
While offensive AI poses a severe threat to organizations, its implications extend beyond technical hurdles. Here are some critical areas where offensive AI demands our immediate attention:
Urgent Need for Regulations: The rise of offensive AI calls for developing stringent regulations and legal frameworks to govern its use. Having clear rules for responsible AI development can stop bad actors from using it for harm. Clear regulations for responsible AI development will prevent misuse and protect individuals and organizations from potential dangers. This will allow everyone to safely benefit from the advancements AI offers.
Ethical Considerations: Offensive AI raises a multitude of ethical and privacy concerns, threatening the spread of surveillance and data breaches. Moreover, it can contribute to global instability with the malicious development and deployment of autonomous weapons systems. Organizations can limit these risks by prioritizing ethical considerations like transparency, accountability, and fairness throughout the design and use of AI.
Paradigm Shift in Security Strategies: Adversarial AI disrupts traditional security paradigms. Conventional defense mechanisms are struggling to keep pace with the speed and sophistication of AI-driven attacks. With AI threats constantly evolving, organizations must step up their defenses by investing in more robust security tools. Organizations must leverage AI and machine learning to build robust systems that can automatically detect and stop attacks as they happen. But it’s not just about the tools. Organizations also need to invest in training their security professionals to work effectively with these new systems.
Defensive AI
Defensive AI is a powerful tool in the fight against cybercrime. By using AI-powered advanced data analytics to spot system vulnerabilities and raise alerts, organizations can neutralize threats and build a robust security cover. Although still in development, defensive AI offers a promising way to build responsible and ethical mitigation technology.
Defensive AI is a potent tool in the battle against cybercrime. The AI-powered defensive system uses advanced data analytics methods to detect system vulnerabilities and raise alerts. This helps organizations to neutralize threats and construct strong security protection against cyber attacks. Although still an emerging technology, defensive AI offers a promising approach to developing responsible and ethical mitigation solutions.
Strategic Approaches to Mitigating Offensive AI Risks
In the battle against offensive AI, a dynamic defense strategy is required. Here’s how organizations can effectively counter the rising tide of offensive AI:
Rapid Response Capabilities: To counter AI-driven attacks, companies must enhance their ability to quickly detect and respond to threats. Businesses should upgrade security protocols with incident response plans and threat intelligence sharing. Moreover companies should utilize cutting edge real-time analysis tools like threat detection systems and AI driven solutions.
Leveraging Defensive AI: Integrate an updated cybersecurity system that automatically detects anomalies and identifies potential threats before they materialize. By continuously adapting to new tactics without human intervention, defensive AI systems can stay one step ahead of offensive AI.
Human Oversight: AI is a powerful tool in cybersecurity, but it is not a silver bullet. Human-in-the-loop (HITL) ensures AI’s explainable, responsible, and ethical use. Humans and AI association is actually important for making a defense plan more effective.
Continuous Evolution: The battle against offensive AI isn’t static; it’s a continuous arms race. Regular updates of defensive systems are compulsory for tackling new threats. Staying informed, flexible, and adaptable is the best defense against the rapidly advancing offensive AI.
Defensive AI is a significant step forward in ensuring resilient security coverage against evolving cyber threats. Because offensive AI constantly changes, organizations must adopt a perpetual vigilant posture by staying informed on emerging trends.
Visit Unite.AI to learn more about the latest developments in AI security.
#2023#account takeover#ai#ai security#AI systems#AI threat#AI-powered#alerts#Analysis#Analytics#anomalies#approach#Article#artificial#Artificial Intelligence#attackers#attention#BEC#Behavior#Business#business email compromise#CEO#chatbots#Companies#complexity#compromise#continuous#credential#credential stuffing#crime
0 notes
Note
Maybe I should wait for the PDF, but I’ve been thinking about password managers lately and might forget to check for that. My problem is that if there’s one thing I want to never ever put on the cloud to potentially get compromised, it’s my password information. But if there’s one thing I don’t want to lose access to, it’s also my password information. This seems to rule out both local options like KeePassXC and remote ones like Bitwarden.
I've started to become somewhat annoyed by the "there is no cloud, there is only someone else's computer" thing (this is a general thing, not specifically directed at you but you reminded me of it).
The risks of putting things on the cloud are that the internet or the provider will go down and you'll lose access to your data OR that the data will be compromised because the information is essentially public because it's on someone else's device.
Losing access because the provider crashes and burns or because there is a global internet outage is a distinct possibility, however with most password managers it is very very easy to download a copy of your data, which you can then store as an encrypted file on your desktop.
With companies like Bitwarden and Proton, which have open source encrypted cloud storage, your risk of compromise from being on someone else's computer is essentially zero. It IS important to make sure that you're finding a provider who is actually encrypting your shit and is not holding onto your password, which is why Bitwarden and Proton are the providers I keep recommending (privacyguides.org has recommendations here; bitwarden, protonpass, and keepassxc are all on the list, all of these are extremely safe options).
And that's where I have the problem with the "other people's computer" thing. I would have zero problems with storing a properly encrypted file in the comments of a facebook page. If a document had good encryption I would post it on livejournal and not worry about people getting into it. If you are working with good encryption, there is zero risk of compromise when keeping your shit on someone else's computer.
So I actually think the solution for either side of this conundrum is the same: If you're worried about losing access to your password manager because a service shuts down or the internet blows up, download a copy of your data to your desktop and store it in an encrypted folder on your computer. If you're worried about losing access to your password manager if your physical hardware is damaged in a disaster, export a copy of your data, save it as an encrypted file, and upload your encrypted file to gmail for all it matters - they will straight up not be able to get into it.
But that's also all kind of beside the point because a major feather in Bitwarden's cap is that you can self-host. It doesn't need to go on someone else's cloud, you can put it on your own server and never worry that someone else is going to tinker with your password manager.
Either way, you are sort of worrying beyond your means because if you're not using a password manager right now you are almost certainly at greater risk of credential stuffing attacks than anything else and need to put out that fire.
Anyway if you're at Harvey Mudd have you tried Dr. Grubbs across from where Rhino used to be? Everything on the menu is great but there is this jalapeño garlic sauce they've got to go with their mains that is so good that I want like two gallons of it.
326 notes
·
View notes
Text
Forged Identities
Summary
*WARNING: May contain spoilers for Chapters 1 & 2 of the Imperial Agent story* Darth Jaedus has been defeated and the Eradicators stopped, yet an operative’s work is never done. Kahl’ryn ends his R&R short after word reaches him that his Sith father is not only missing but also a traitor to the Empire. To ensure the safety of his family from Sith retaliation, Kahl’ryn infiltrates the Imperial Census Bureau on Dromund Kaas in order to doctor his family’s history, unaware that he is already a pawn in someone’s schemes.

The light drizzle grew heavier as Kahl’ryn passed through the atrium towards the Census Bureau. A day rarely went by without rain in Kaas City, but today he welcomed the incoming storm. It would be useful for covering his tracks.
He padded down the crowded halls towards the records office. The weight of the data spike in his pocket felt heavier with each step. He wore dark gray technician coveralls and carried a small tool bag slung over his shoulder. A facial prosthetic covered his cybernetics and burn scars, which were blended in to match the rest of his skin with makeup.
He entered the Census offices and checked in with the front desk. No concerns were raised. No questions asked. The single raised eye brow and half hidden sneer didn’t escape Kahl’ryn’s notice but the receptionist didn’t question his credentials nor his work order.
He joined a group waiting at the elevators. When the doors opened, he stepped inside. A young woman stood near the control panel. She wore a light gray Census Bureau uniform, and her dark brown hair was pulled back into a bun. She cast a glance his way. “Where to?” Her hand hovered over the control panel.
“Records please.” The Lower Kaas City accent rolled off his tongue with ease. It wasn’t that much different then the accent he grew up listening too, but it wasn’t his natural accent either. It took several days of practicing to get the nuances of it just right.
She nodded and keyed in his floor. He caught her sneaking glances his way, but she made no further move to engage him in small talk. The other occupants were too absorbed in their own thoughts.
He absently tapped the edge of the data pad stuffed into his right thigh pocket. He felt another headache creeping up on him. He’d been struggling with them for a few days now due to the stress and long hours he’d been keeping. He fished a migraine tablet from his pocket and let it dissolve beneath his tongue, ignoring the bitter chalkiness that now coated his mouth.
He exited the elevator into a short hallway the led to the records rooms. Dim ambient light filtered in from overhead. Droids patrolled the narrow corridors between the stacks and their clicks and whirring added a tenor note the otherwise low hum. It would have been an oddly comforting mix of white noise, if not for the claustrophobic placement of the data stacks. He entered his forged credentials into the waiting keypad. A welcoming chime sounded as the force field dropped. It felt too easy and doubt nagged at the back of his mind, he didn’t have time to contemplate that thought; he had a schedule to follow.
He checked the time and counted down the last few seconds. 1….2….3…. The lights went dark and the soft hum of electricity went silent. He hit the stealth generator hidden under his belt, and stepped past the threshold. The back up generators kicked in and the droids switched to attack mode. Security cameras would be out for 60 seconds while the system rerouted power. Kahl’ryn made a bee line for the back terminal, the only blind spot in the droids patrol. He took the data spike from his pocket, connected it to the terminal, and entered the start command.
He didn’t have enough time to clean all the data. Half truths, misleads, and random data corruption were the best he could scrap together on short notice. Enough to throw people off the trail, he hoped, but not enough to raise suspicions. It helped that most records had him and his siblings growing up in an orphanage on Rhelg, with few records directly connecting his Mother and Father, but they did fight in the war together. Without interference, it wouldn’t take much to put two and two together, that put all the children that grew up under their care at risk of retaliation.
New adoption papers, orphanages that no longer operated, forged relationships, it all helped to hide who they were. In less then 45 seconds the family of Lord Xhai’tan, former apprentice to Darth Malgus and a traitor to the Empire, became strangers.
The program finished and Kahl’ryn disconnected the data spike. He left the room, and once back across the threshold he deactivated the stealth generator. The power came back on a few seconds later.
With the force field back in place and the droids no longer hostile, he entered his credentials a second time. The chime welcomed him again. This time he walked over to the nearest terminal and connected his data pad to it. He started a simple diagnostic program, then knelt down to open a maintenance hatch. The plan called for two minutes of playing technician after which he packed up his gear, secured the maintenance hatch, and returned to the elevators.
His foot tapped in time to his heartbeat until the elevator doors opened. The woman from earlier waited inside. Relief flickered across her face before her expression returned to neutral. “Good. You’re not dead.”
Kahl’ryn nodded. “I got lucky. Power went out before I was even inside.”
“Were you able to fix the problem?” She hadn’t moved from her spot and there wasn’t enough space to squeeze past her onto the elevator.
“Nope. The problem must have resolved itself with the power outage.” He made a point of checking the time. “You know how it is, turning it off and back on solves most things.”
A smile twitched at the corner of her mouth. “So, I’ve heard.” She stepped aside so he could enter the elevator. Kahl’ryn punched in the code for the main level then pulled the data pad from its pocket, feigning work. They rode together in awkward silence until he bid her farewell at the floor to her office.
No one bade Kahl’ryn any mind as he hurried through the heavy rain towards the safe house. He wasn’t the only one in a hurry to escape the storm. He soon reached the apartment and tapped his code into the lock. The smell of stale alcohol and cigarettes assaulted his nose as he entered through the open door. He took a measured and thorough look around the studio, taking note of the threadbare rugs and stained bed covers. A mustiness hung like a sour note in the air. The place was empty.
He grabbed his gear from the hallway closet, pulled out his neatly folded uniform and laid it out onto the bed. He gabbed the face cleanser he packed and hopped into the small shower.
The makeup and prosthetic covering his face took longer to remove then he calculated, but he scrubbed until the burn scar once more marred his face.
By the time he’d finished in the shower he needed a stim to calm his shaking hands. He pulled one out from his pack, injected it in one swift motion, then tossed the spent cartridge in the trash.
Kahl’ryn took a little extra time putting on his uniform and made sure to brush out the wrinkles. Then he re-connected his cybernetic attachments, which included a visual scanner and ear piece. He took one more look in the mirror. The twi’lek that looked back at him seemed out of place in the Imperial Intelligence uniform. His pale yellow skin appeared sallow in the unflattering light, and dark circles had formed under the dull eyes that starred back at him. Satisfied with his appearance, Kahl’ryn pulled on his great coat and stepped back into the pouring rain.
He checked the news while on the taxi ride to the Citadel. Between the propaganda and general reports on the conflicts across the galaxy, he didn’t find any mention of his Father. He wondered if the Dark Council would keep that close to their chest or turn the Empire against the rogue lord. Either could spell disaster. Next he checked the intelligence channels, still nothing.
An encrypted message blinked onto the screen; he entered his encryption key and opened it. Code Green. He huffed out a breath, he was in the clear. The plan worked, for now at least, with no one the wiser about the tampered data. The relief did little for the headache that started to return with a lot more fight then before. He pulled a bottle of pain killers from his pocket and swallowed two.
He arrived at Keeper’s office with no time to spare and walked right in. Watcher Two greeted him. “Cipher 9, come in.”
Kahl’ryn came to attention. “Outside operations are complete. Reporting for duty.”
“Then you’ll be reporting to me.” She stood up. “The Dark Council decided to make changes. My predecessor was elevated to Minister of Intelligence. That makes me the new Keeper of Operations Division.” She kept her tone clipped and professional.
He bowed. “You have my full support, Sir.”
He settled into at ease as she proceeded to fill him in on the next mission. He’d be working as a double agent, infiltrating the Republic SIS as an Imperial Defector to locate and eliminate the spymaster Ardun Kothe. Kahl’ryn followed along the best he could but the meds he’d taken were doing little to keep the headache at bay and the world around him lost focus.
Kahl’ryn woke later on his ship confused and in pain. He didn’t remember much from the briefing other then his main objectives. Returning to the ship felt like a fevered dream. He stumbled to the basin and splashed cold water on his face. His entire body ached and the headache pounded the inside of his skull. He sagged against the basin. His haggard visage starring back at him from the mirror.
As he contemplated dragging himself to the med bay, he glanced over at the bed side table. An orange light flashed on his data pad. He shuffled over and picked it up. It was another encrypted message. Kahl’ryn entered his code. Caution. Sith Interference. That wasn’t surprising, but he didn’t know what to do about it. Not until he had more information.
The light from the message made his vision swim and he swayed. He tried to set the data pad down before his knees gave out, but it landed on the edge of the night stand and tumbled to the floor with him. He sat there reeling for a few minutes, before pulling himself back into bed and dragging the covers over his head.
He woke to the sounds of his team returning. Kahl’ryn groaned as he sat up. His body felt like a punching bag. He must have pushed himself too far, or perhaps the stim interacted badly with the other meds he’d taken for the headaches. Regardless, the headache was gone for now.
Once done in the refresher he dressed in his usual black pants and light gray shirt. He pulled on the shoulder holster for his small holdout blaster, secured a concealed vibro knife in his boot, and then he buckled his primarily blaster’s holster around his waist. Next he took a few minutes to clean the connectors on his cybernetics before clicking the scanner and ear piece into place.
Before leaving his cabin he picked up the data pad from where it had fallen and scanned the intelligence channels quickly. No new messages, and still no word about his Father.
Hearing Kaliyo and Vector arguing from the other room, he slung his favorite red jacket over his shoulder, set the data pad back on the bed side table, and left to inform them of the next mission.
#Star Wars: The Old Republic#SWTOR#fanfic#Dromund Kaas#Twi’lek#Imperial Agent#Cipher 9#Kahl’ryn#Valyr Legacy#Zhak’s Stories#my obsession with this fictional family is unreal#it’s nice to be writing stories again#not perfect but it has been 10 years since I wrote fanficion
4 notes
·
View notes
Text
[Image Description: A tweet from Matt Johansen. It reads 'Breaking: Genetics firm 23andMe confirms user data theft in a credential stuffing attack. The hackers released 1 million lines of data targeting Ashkenazi Jews. End ID]
requested by anonymous:
RATING: 🟢 RELIABLE 🟢
User data was stolen from 23andMe in October 2023.
From a Wired article on the theft: 'The genetic testing company 23andMe confirmed on Friday that data from a subset of its users has been compromised.'
The data was stolen by a method known as credential stuffing, meaning that the company itself was not hacked, only user accounts.
From OWASP article on Credential Stuffing: 'Credential stuffing is the automated injection of stolen username and password pairs (“credentials”) in to website login forms, in order to fraudulently gain access to user accounts.'
From BBC article on a resulting investigation into 23andMe: 'The company was not hacked itself - but rather criminals logged into about 14,000 individual accounts, or 0.1% of customers, by using email and password details previously exposed in other hacks.'
The hackers posted a sample of the data on a forum, claiming it contained 1 million data points from Ashkenazi Jewish people. It was later found that people of Chinese decent were also impacted.
From a Wired article on the theft: 'Hackers posted an initial data sample on the platform BreachForums earlier this week, claiming that it contained 1 million data points exclusively about Ashkenazi Jews. There also seem to be hundreds of thousands of users of Chinese descent impacted by the leak.'
From a BBC article on the theft: 'One batch of data was advertised on a hacking forum as a list of people with Jewish ancestry, sparking concerns of targeted attacks.'
For clarification, no actual DNA data was stolen.
From a BBC article on the theft: 'The stolen data does not include DNA records.'
Jesus fucking Christ. Do not trust any of these fucking ancestry companies with your data.
18K notes
·
View notes
Text
The Accidental Unlocking: 6 Most Common Causes of Data Leaks

In the ongoing battle for digital security, we often hear about "data breaches" – images of malicious hackers breaking through firewalls. But there's a more subtle, yet equally damaging, threat lurking: data leaks.
While a data breach typically implies unauthorized access by a malicious actor (think someone kicking down the door), a data leak is the accidental or unintentional exposure of sensitive information to an unauthorized environment (more like leaving the door unlocked or a window open). Both lead to compromised data, but their causes and, sometimes, their detection and prevention strategies can differ.
Understanding the root causes of data leaks is the first critical step toward building a more robust defense. Here are the 6 most common culprits:
1. Cloud Misconfigurations
The rapid adoption of cloud services (AWS, Azure, GCP, SaaS platforms) has brought immense flexibility but also a significant security challenge. Misconfigured cloud settings are a leading cause of data leaks.
How it leads to a leak: Leaving storage buckets (like Amazon S3 buckets) publicly accessible, overly permissive access control lists (ACLs), misconfigured firewalls, or default settings that expose services to the internet can inadvertently expose vast amounts of sensitive data. Developers or administrators might not fully understand the implications of certain settings.
Example: A company's customer database stored in a cloud bucket is accidentally set to "public read" access, allowing anyone on the internet to view customer names, addresses, and even financial details.
Prevention Tip: Implement robust Cloud Security Posture Management (CSPM) tools and enforce Infrastructure as Code (IaC) to ensure secure baselines and continuous monitoring for misconfigurations.
2. Human Error / Accidental Exposure
Even with the best technology, people make mistakes. Human error is consistently cited as a top factor in data leaks.
How it leads to a leak: This can range from sending an email containing sensitive customer data to the wrong recipient, uploading confidential files to a public file-sharing service, losing an unencrypted laptop or USB drive, or simply discussing sensitive information in an insecure environment.
Example: An employee emails a spreadsheet with salary information to the entire company instead of just the HR department. Or, a developer accidentally pastes internal API keys into a public forum like Stack Overflow.
Prevention Tip: Implement comprehensive, ongoing security awareness training for all employees. Enforce strong data handling policies, promote the use of secure communication channels, and ensure devices are encrypted.
3. Weak or Stolen Credentials
Compromised login credentials are a golden ticket for attackers, leading directly to data access.
How it leads to a leak: This isn't always about a direct "hack." It could be due to:
Phishing: Employees falling for phishing emails that trick them into revealing usernames and passwords.
Weak Passwords: Easily guessable passwords or reusing passwords across multiple services, making them vulnerable to "credential stuffing" attacks if one service is breached.
Lack of MFA: Even if a password is stolen, Multi-Factor Authentication (MFA) adds a critical second layer of defense. Without it, stolen credentials lead directly to access.
Example: An attacker obtains an employee's reused password from a previous data breach and uses it to log into the company's internal file sharing system, exposing sensitive documents.
Prevention Tip: Enforce strong, unique passwords, mandate MFA for all accounts (especially privileged ones), and conduct regular phishing simulations to train employees.
4. Insider Threats (Negligent or Malicious)
Sometimes, the threat comes from within. Insider threats can be accidental or intentional, but both lead to data exposure.
How it leads to a leak:
Negligent Insiders: Employees who are careless with data (e.g., leaving a workstation unlocked, storing sensitive files on personal devices, bypassing security protocols for convenience).
Malicious Insiders: Disgruntled employees or those motivated by financial gain or espionage who intentionally steal, leak, or destroy data they have legitimate access to.
Example: A disgruntled employee downloads the company's entire customer list before resigning, or an employee stores client financial data on an unsecured personal cloud drive.
Prevention Tip: Implement robust access controls (least privilege), conduct regular audits of user activity, establish strong data loss prevention (DLP) policies, and foster a positive work environment to mitigate malicious intent.
5. Software Vulnerabilities & Unpatched Systems
Software is complex, and bugs happen. When these bugs are security vulnerabilities, they can be exploited to expose data.
How it leads to a leak: Unpatched software (operating systems, applications, network devices) contains known flaws that attackers can exploit to gain unauthorized access to systems, where they can then access and exfiltrate sensitive data. "Zero-day" vulnerabilities (unknown flaws) also pose a significant risk until they are discovered and patched.
Example: A critical vulnerability in a web server application allows an attacker to bypass authentication and access files stored on the server, leading to a leak of customer information.
Prevention Tip: Implement a rigorous patch management program, automate updates where possible, and regularly conduct vulnerability assessments and penetration tests to identify and remediate flaws before attackers can exploit them.
6. Third-Party / Supply Chain Risks
In today's interconnected business world, you're only as secure as your weakest link, which is often a third-party vendor or partner.
How it leads to a leak: Organizations share data with numerous vendors (SaaS providers, IT support, marketing agencies, payment processors). If a third-party vendor suffers a data leak due to their own vulnerabilities or misconfigurations, your data that they hold can be exposed.
Example: A marketing agency storing your customer contact list on their internal server gets breached, leading to the leak of your customer data.
Prevention Tip: Conduct thorough vendor risk assessments, ensure strong data protection clauses in contracts, and continuously monitor third-party access to your data. Consider implementing secure data sharing practices that minimize the amount of data shared.
The common thread among these causes is that many data leaks are preventable. By understanding these vulnerabilities and proactively implementing a multi-layered security strategy encompassing technology, processes, and people, organizations can significantly reduce their risk of becoming the next data leak headline.
0 notes
Text
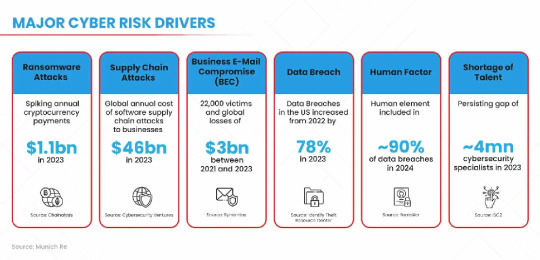
Are You Prepared for 2025's Top Cyber Threats?
Cybercriminals are getting smarter—and no business is too small to be targeted. From phishing emails and ransomware attacks to insider threats and credential stuffing, understanding today’s most dangerous cyber risks is the first step to securing your systems and data.
0 notes
Text
How Insurtechs Are Strengthening Core Software with Advanced Cybersecurity Measures
As cyber threats continue to evolve in complexity, securing sensitive customer information has become a top priority, particularly within the core software systems that drive the insurance industry. Insurers are enhancing their cybersecurity efforts, and it’s fascinating to see how they are approaching this critical challenge.
Many insurtech companies are leading this transformation by incorporating state-of-the-art technologies, such as AI-powered threat detection systems soc security operations center, into their platforms. Instead of merely reacting to cyberattacks, these companies are taking proactive steps to identify and mitigate risks before they escalate into significant issues.
The Growing Need for Cybersecurity in Insurance
Property & Casualty (P&C) insurance companies are sitting on a wealth of sensitive personal and financial data, making them prime targets for cybercriminals. As insurers embrace technologies like cloud computing, artificial intelligence (AI), and the Internet of Things (IoT) to streamline operations, they gain substantial efficiencies—but also open themselves to new vulnerabilities.
For insurers, investing in cybersecurity isn’t just about avoiding regulatory penalties. In today's increasingly hostile digital environment, robust cybersecurity is essential for long-term survival.
To underscore this point, let’s take a look at a real-world example that rattled the insurance sector: the 2020 data breach at Folksam, one of Sweden’s largest insurance providers. This incident served as a major wake-up call for the industry. Folksam unintentionally leaked sensitive data for around one million customers, not due to an external cyberattack, but because of an internal oversight. In an attempt to analyze customer behavior and provide more personalized services, the company shared private customer information with tech giants such as Facebook, Google, Microsoft, LinkedIn, and Adobe.
While Folksam stated there was no evidence of misuse by these third parties, the breach raised serious concerns among customers and regulators alike. It demonstrated that even well-intentioned actions could lead to significant security failures if proper safeguards are not in place.
Core Platform Security: A Critical Priority
Your core platform—the system responsible for policy management, claims processing, billing, and customer relations—is the backbone of your insurance business. But it also becomes a prime target for cyberattacks if not adequately protected.
AI: The Ultimate Security Co-Pilot
Leading insurers are increasingly integrating AI-powered soc security operations center “co-pilots” into their core platforms. These AI-driven systems analyze vast amounts of data to:
Detect Anomalies: Machine learning algorithms can identify unusual patterns in claims, underwriting, or policy modifications that may indicate fraudulent activity or a security breach. For instance, an unexpected increase in claims from a particular region or a sudden surge in requests to modify policy details could signal potential fraud.
Automate Incident Response: Once a threat is detected, AI can automatically isolate compromised systems, preventing the breach from spreading. This might involve shutting down affected servers or disabling user accounts to contain the damage.
Predict Attack Vectors: By analyzing data from threat intelligence feeds and the dark web, AI can help insurers anticipate and defend against future attacks. This might include identifying emerging malware strains or pinpointing vulnerabilities in third-party software.
Take Zurich Insurance, for example. Their AI models soc security operations center successfully identified and stopped a credential-stuffing attack targeting their Asian SME clients, blocking thousands of fraudulent login attempts within hours. This kind of rapid response is only achievable when AI is deeply embedded in the core platform.
0 notes