#CryptoLocking
Explore tagged Tumblr posts
Text
Healthcare's Ransomware Attackers Are Addicted to Encryption
Fraud Management & Cybercrime , Healthcare , Industry Specific Extortionist Crypto-Locking Hackers Keep Hitting Healthcare Sector, Experts Report Marianne Kolbasuk McGee (HealthInfoSec) • November 1, 2023 Image: Shutterstock Once ransomware hackers get inside a healthcare sector organization’s systems, 3 in 4 attackers will also maliciously encrypt data, says security firm Sophos. See…

View On WordPress
0 notes
Text
Mesh it Up Monday: Ransomware - The Real-Life Villain in the Cyber World
Welcome to Mesh it Up Monday! 🎉 Today, we’re delving into the captivating realm of ransomware, the real-life villain of the cyber world. But fear not, we won’t let this digital menace intimidate us. Instead, we’ll tackle the topic with a humorous twist and analogies that even a novice can relate to. So, fasten your virtual seatbelts, put on your cybersecurity capes, and let’s dive into the…

View On WordPress
#CryptoLocker#cyber world#cybersecurity heroes#data security#Locky#Petya#ransomware#ransomware protection#ransomware threats#WannaCry
0 notes
Text
Chapter 1: Ghost In the Machine

The hum of the fluorescent lights in "Byte Me" IT Solutions was a monotonous drone against the backdrop of Gotham's usual cacophony. Rain lashed against the grimy window, each drop a tiny percussionist drumming out a rhythm of misery. Inside, however, misery was a bit more… organized.
I sighed, wrestling with a particularly stubborn strain of ransomware. "CryptoLocker v. 7.3," the diagnostic screen read. A digital venereal disease, if you asked me. Another day, another infected grandma's laptop filled with pictures of her grandkids and a crippling fear that hackers were going to steal her identity.
"Still at it?" My coworker, Mark, sidled over, clutching a lukewarm mug of something vaguely resembling coffee. Mark was a good guy, perpetually optimistic despite working in one of Gotham's less-than-glamorous neighborhoods. Bless his heart.
"You know it," I replied, jabbing at the keyboard. "Think I've finally managed to corner the bastard. Just gotta… there!" The screen flashed a success message. "One less victim of the digital plague."
Mark nodded, then his eyes drifted to the hulking metal beast in the corner, a Frankensteinian creation of salvaged parts and mismatched wiring. "How's the behemoth coming along?"
I followed his gaze. My pet project. My escape. "Slowly but surely. Got the cooling system optimized today. Almost ready to fire it up."
"Planning anything special with it?" Mark asked, his brow furrowed in curiosity. "You've been collecting scraps for months. It's gotta be more than just a souped-up gaming rig."
I shrugged, a deliberately vague gesture. "You could say I'm planning something… big. Something Byte Me isn't equipped to handle."
Mark chuckled. "Well, whatever it is, I'm sure you'll make it sing. You've got a knack for that sort of thing." He wandered off, whistling a jaunty tune that died a slow, agonizing death against the backdrop of the Gotham rain.
He had no idea just how much of a knack.
Mark bid me one final goodbye before pulling out an umbrella and disappearing into the night. No doubt he stops at Nero’s pizzeria before going home to his wife and kids. You watched through the shop window before he disappeared around the corner. Then, you locked the door and reached for the light switch. The fluorescent lights flickered a final, dying gasp before plunging the shop into darkness. I waited a beat, the city's distant sirens a mournful choir. Then, I flipped the hidden switch behind the breaker box, illuminating a small, secluded corner of the shop.
Rain hammered against the grimy windowpanes of my "office," a repurposed storage room tucked away in the forgotten bowels of the shop. The rhythmic drumming was almost hypnotic, a bleak lullaby for a city perpetually on the verge of collapse. I ignored it, fingers flying across the keyboard, the green glow of the monitor painting my face in an unsettling light. Outside, the city's distant sirens formed a mournful choir. Here, the air crackled with a different kind of energy.
"Almost there," I muttered, the words barely audible above the whirring of the ancient server rack humming in the corner. It was a Frankensteinian creation, cobbled together from spare parts and salvaged tech, but it packed enough processing power to crack even the most stubborn encryption algorithms. Laptops with custom OSes, encrypted hard drives, and a tangle of wires snaked across the desk. This was Ghostwire Solutions, my little side hustle. My… outlet.
Tonight's victim, or client – depending on how you looked at it – was a low-level goon. One was a two-bit thug named "Knuckles" Malone; the other, a twitchy character smelling of desperation, Frankie "Fingers" Falcone. Malone's burner phone, or Falcone's data chip containing an encrypted message, was now on the screen in front of me, a jumble of characters that would make most people's eyes glaze over. For me, it was a puzzle. A challenging, if morally questionable, puzzle.
My service, "Ghostwire Solutions," was discreet, to say the least. No flashy neon signs, no online presence, just word-of-mouth referrals whispered in dimly lit back alleys. I was a ghost, a digital shadow flitting through the city's underbelly, connecting people. That's how I liked to justify it anyway. I cracked my knuckles and went to work. My fingers danced across the keyboard, feeding the encrypted text into a series of custom-built algorithms, each designed to exploit a specific vulnerability. Hours melted away, marked only by the rhythmic tapping of keys and the soft hum of the custom-built rig in the corner, its processing power gnawing away at the digital lock.
The encryption finally buckled. A cascade of decrypted data flooded the screen. I scanned through it, a jumbled mess of texts, voicemails, location data, or a simple message detailing a meeting point and time. Mostly dull stuff about late payments and turf wars, the mundane reality of Gotham's criminal element. I extracted the relevant information.
"Alright, Frankie," I muttered to myself, copying the decrypted message onto a clean file. "Just connecting people. That's all I'm doing."
I packaged the data into a neat little file, added a hefty markup to my initial quote, and sent it off via an encrypted channel. Within minutes, the agreed-upon sum, a few hundred cold, hard dollars, landed in my untraceable digital wallet. I saved the file to a new data chip and packaged it up. Another job done. Another night closer to sanity's breaking point.
"Just connecting people," I repeated, the phrase tasting like ash in my mouth. The lie tasted even worse. I knew what I was doing. I was enabling crime. I was greasing the wheels of Gotham's underbelly. But bills had to be paid. It was a convenient lie, a way to sleep at night knowing I was profiting from the chaos. But tonight, it felt particularly hollow. And honestly, did it really matter? Gotham was already drowning in darkness. What was one more drop?
Gotham was a broken city, a machine grinding down its inhabitants. The system was rigged, the rich got richer, and the poor fought over scraps. I wasn't exactly helping to fix things. But I wasn't making it worse, right? I was just a cog in the machine, a necessary evil. I was good at what I did, damn good. I could see patterns where others saw chaos. I could exploit vulnerabilities, both in code and in the systems of power that held Gotham hostage. It was a skill, a talent, and in this city, unique talents were currency. I was efficient and discreet. But every decrypted message, every bypassed firewall, chipped away at something inside me. It hollowed me out, leaving me a ghost in my own life, a wire connecting the darkness.
I leaned back in my creaky chair, the rain still pounding against the window. The air was thick with the scent of ozone and melancholy. Another night, another decryption, another small victory against the futility of existence in Gotham. The flicker of conscience, that annoying little spark that refused to be extinguished, flared again. Was I really making a difference? Or was I just another parasite feeding off the city's decay?
I closed my eyes, trying to silence the questions. Tomorrow, there would be another encryption to crack, another connection to make. And I would be ready, Ghostwire ready to disappear into the digital ether, another ghost in the machine, until the next signal came. As I waited for the morning, for the return of the fluorescent lights and the mundane reality of "Byte Me" IT Solutions, I wondered if one day, the darkness I trafficked in would finally claim me completely. Because in Gotham, survival was a code all its own, and I was fluent in its language. And frankly, some days, that didn't seem like such a bad deal. For now, that was enough.
#gotham knights#gotham knights fanfic#gotham knights jason todd#gk jason todd#jason todd#jason todd x reader#jason todd x you#red hood#red hood x reader#hacker!reader#dc
40 notes
·
View notes
Text
Understanding Ransomware: A Guide for Small Businesses
Ransomware is a malicious software that restricts access to your device or data until a ransom is paid. In this article, we explore how ransomware enters your system, how it works, and how to prevent attacks. A ransomware attack occurs when malware prevents access to your device or data until a ransom is paid. Attackers may threaten to publish data if the ransom is not paid. Ransomware can be locker ransomware, which locks access, or crypto ransomware, which encrypts files. Ransomware usually enters a device, assesses critical data, encrypts files, and demands a ransom. Paying the ransom doesn't guarantee recovery, so it's not recommended. Historical ransomware attacks include CryptoLocker, CryptoWall, Locky, WannaCry, NotPetya, and more. To prevent ransomware, you can have good network policies, secure servers, backup data offline and online, and encourage safe online behavior. Installing security software like antivirus, firewall, and email filtering can also help. Advanced strategies include ATP, email filtering, and security audits. In case of a ransomware infection, isolate the device, assess damage, check for a decryption key, and restore from backups. Seek professional help for recovery. Immediate actions post-infection include isolation, incident response activation, legal compliance, and stakeholder communication. Ransomware can get on your device through spam emails, phishing, pop-ups, pirated software, weak passwords, and more. Attackers prefer cryptocurrency payments for anonymity. Ransomware can spread through Wi-Fi, infecting all connected devices. Protect yourself from ransomware by following the prevention strategies mentioned above. Stay safe online and be cautious of suspicious emails, links, and downloads. And remember, it's crucial to have backups and a plan in case of a ransomware attack. #StartupBusiness #Businesses #Guide #howdoesransomwarework #Ransomware #ransomwareattack #Small #Understanding #whatisaransomware #whatisaransomwareattack #whatisransomware https://tinyurl.com/228z9vpf
#Businesses#Guide#how does ransomware work#Ransomware#ransomware attack#Small#Understanding#what is a ransomware#what is a ransomware attack#what is ransomware
1 note
·
View note
Text
What are The Types of Ransomware and Ransomware History

Cyberattacks like ransomware are serious. Among the most dangerous malware, they can affect any company. Within four days of network access, attackers deploy ransomware, leaving little time for detection and prevention. Stopping operations, losing money, reputation, and data.
According to the IBM Cost of a Data Breach report, ransomware breaches average USD 5.68 million, excluding ransom payments. Not all ransoms reach $80 million.
Better threat detection and prevention reduced ransomware attacks 11.5% between 2022 and 2023.
The Ransomware Types
Varying ransomware strains exploit vulnerabilities.
Crypto ransomware: Locks important files until a ransom is paid. WannaCry, Locky, CryptoLocker. Ransomware encrypts.
Without payment, this ransomware blocks the victim's device or system from accessing files or apps. Screen-locking ransomware isn't encrypted.
Scareware: Fake software that diagnoses system issues and recommends dangerous fixes. Scareware can restrict system access or bombard users with pop-ups to install malware or pay. Scareware can provide or be ransomware.
Leakware, or doxware, steals confidential data and threatens disclosure without payment. The attacks pressure victims with reputational danger. Modern variants steal and encrypt data.
Mobile ransomware: Spreads via malicious apps or drive-by downloads. Most mobile ransomware involves screen-lockers since cloud backups make encryption attacks easier to reverse.
If unpaid, ransomware wipes data. Ransomware by cybercriminals and nation-states erases data after payment.
Modern ransomware uses double- and triple-extortion. Unpaid double-extortion threatens to steal and publish vulnerable data online. Consumers or business partners with stolen data face triple extortion. Even with data backups, these methods raise the stakes. Since 2019, the IBM Security X-Force incident Response team has seen double extortion in most ransomware events.
Infection via Ransomware
Ransomware can attack systems via multiple channels. Well-known methods:
Phishing uses emails with phoney attachments or malicious websites to get people to download and run hazardous programs.
Zero-day vulnerabilities in operating systems and applications allow cybercriminals to inject malware. The 2017 WannaCry assault used fixed vulnerabilities.
Stolen, bought, or cracked user credentials are used to log in and deploy ransomware via Remote Desktop Protocol (RDP).
Malware like Trickbot Trojan (which seeks banking details) can spread ransomware.
Drive-by downloads: Ransomware can infiltrate devices without user awareness via exploit kits or malvertising.
In legitimate online interactions, cybercriminals utilise thread hijacking to spread malware.
RaaS: Ransomware as Service
Cybercriminals distribute ransomware via RaaS. Malware developers share code with “affiliates” who split the ransom. Developers and affiliates can benefit without releasing new attacks or malware. RaaS distributors can sell dark web access or recruit affiliates. Major ransomware gangs have recruited affiliates.
Staged Ransomware Attack
Typical ransomware attacks include many phases:
Initial access: Phishing, vulnerability exploitation, or hacked RDP protocols give attackers access.
After initial access, attackers may utilise RATs to consolidate.
After acquiring access to a system or network, attackers may lateral migrate to other systems and domains.
Ransomware thieves steal credentials, customer data, and IP. Double-extortion uses data theft.
File encryption, system restoration disablement, and backup deletion/encryption increase pressure with crypto ransomware. Unencrypting ransomware locks or spams the device. The ransomware then delivers a text file or pop-up window with instructions on how to pay the ransom (usually in cryptocurrency) to decrypt or regain access.
History of ransomware
Thousands of ransomware variants exist. Some prominent ones:
The AIDS Trojan was the first floppy-disk ransomware in 1989. It concealed file directories but was easily reversed.
CryptoLocker, introduced in 2013, allowed cryptocurrency ransomware.
An unpatched Microsoft Windows vulnerability attacked 200,000 devices in 150 countries with WannaCry. The ransom threatens file deletion if not paid.
File system table encryption by Petya and NotPetya affects PC booting. A 2017 Ukraine attack utilised a modified NotPetya wiper that could not restore systems after payment.
Ryuk, a 2018 ransomware attack, popularised large-scale attacks on high-value targets with high demands. It finds and disables backups.
A purported Russian gang, DarkSide, assaulted the Colonial Pipeline in 2021, briefly halting petroleum supplies. The group licenses ransomware using RaaS.
Encrypting malware Locky hides hazardous macros in email attachments, usually bills.
IN 2021, REvil (Sodinokibi) popularised RaaS for big-game hunting and double-extortion attacks against JBS USA and Kaseya Limited.
Since 2020, the Conti gang's large RaaS scam paid hackers. In a unique double-extortion scheme, Conti threatened to sell network access to hackers. After 2022 internal communication dumps, the gang separated, however former members are tied to BlackBasta, Royal, and Zeon.
A popular 2023 ransomware version is LockBit. The company is known for businesslike conduct and malware acquisition. LockBit assaults victims despite police efforts.
Paying Ransom
An average ransom is hard to quantify, however estimates range from six to seven figures. Ransom payments dropped from 70% in 2020 to 37% in 2023, perhaps owing to better planning.
Agents from the FBI and NCIJTF aggressively discourage ransom payments. Payment may not retrieve data, strengthen attackers, support criminal conduct, or promote more attacks.
Strong backup systems provide negotiation-free recovery. Authorities recommend reporting attacks before paying. Payment of ransom to attackers from US economic sanctions or state governments in particular US regions is illegal.
Ransomware prevention
Ransomware prevention requires technology and user behaviour. Main strategies:
Regular OS, app, and firmware upgrades fix ransomware security holes.
Detect and eliminate threats using real-time scanning, behavioural detection, and automated updates from contemporary antivirus and anti-malware software.
A good firewall blocks unauthorised network access.
Phishing prevention: Email filtering and scanning detects suspicious links and attachments.
Regular backups speed recovery without ransom. Secure, immutable backups can restore data if systems fail. Data should be replicated three times on two media types, one offsite. Seagate Lyve Cloud backups offer geographic redundancy, encryption, and immutability.
Firewalls, intrusion detection systems, network segmentation, and secure VPNs help thwart attacks. Least privilege access and endpoint security harden networks.
AI can predict and stop assaults by studying behaviour, detecting anomalies, and stopping attacks before they start. AI-powered systems can monitor users and endpoints, detect zero-day attacks, and respond faster using playbooks.
Policies and procedures: Ready crisis response requires a detailed strategy with responsibilities, timetables, and communication channels.
Teams require regular security awareness training to spot phishing and suspicious emails because human error is a huge risk.
Ransomware Response Plan
Every system is vulnerable, hence a detailed response strategy is needed. Actions include:
Disconnect compromised systems immediately to stop ransomware.
Report to authorities: Request FBI or CISA law enforcement assistance. Legal duties may require reporting.
Damage assessment: Identify affected systems, assess data compromise, and contain with IT/security teams.
Use the latest clean backup to restore data. Immutable solutions like Seagate Lyve Cloud are needed for reliable recovery. Inform employees, partners, and consumers to build trust and reputation.
Don't pay the ransom: Experts say it may not retrieve data and may encourage more attacks.
#Ransomware#Runningransomwareasaservice#ransomwareattacks#PayingRansom#preventRansomware#Attackersdeployransomware#technology#TechNews#technologynews#news#govindhtech
0 notes
Text
Cyber Security Market Scope, Size, Share, Trends, Forecast By 2031
The cybersecurity landscape is witnessing a significant transformation with the growing adoption of the cybersecurity mesh. This innovative approach is redefining security architectures by enabling distributed enterprises to deploy and extend security precisely where it is needed the most. By decentralizing security measures and focusing on individual users and access points, the cybersecurity mesh is emerging as a rapidly growing strategy in the realm of IT security.

For Full Industry Insights: https://www.fairfieldmarketresearch.com/report/cybersecurity-market
The Concept of Cybersecurity Mesh
The cybersecurity mesh acknowledges that traditional network boundaries are becoming obsolete in today's interconnected world. Organizations are now required to create security perimeters around each user, allowing secure access to assets from any location or device. This model shifts policy enforcement to cloud services, focusing on assets rather than devices. By establishing smaller, individual perimeters around each access point, the cybersecurity mesh offers a robust framework to protect identities and restrict network access to authorized users or systems, whether on-premises or in the cloud.
IoT Security Adoption and Market Demand
The surge in IoT traffic is expected to drive cybersecurity market demand significantly. As enterprises across various industries adopt IoT devices to enhance operational efficiency and communication, the scope of cybercriminals' attacks broadens. The increasing adoption of these devices necessitates a cybersecurity model that provides greater visibility into network access points, user activities, and application usage. Businesses are turning to advanced cybersecurity solutions to inspect all network traffic, detect malicious activities, and address visibility issues arising from the large volume of IoT queries.
Types of Computer Viruses
In the evolving threat landscape, various types of computer viruses pose significant risks to organizations:
Malware: Including worms, Trojans, adware, and ransomware, malware is designed to damage computer systems, gain unauthorized access, or steal information.
Ransomware: This type of malware encrypts data, demanding payment or other actions to restore access. Even large enterprises and city governments have fallen victim to ransomware attacks.
Trojans: Requiring user action, Trojans often deceive users into running malicious programs or accessing harmful websites.
Top Destructive Cyber Viruses
Some of the most destructive cyber viruses include CryptoLocker Ransomware, Plug X malware, Zeus (Gameover) virus, Stuxnet worm, MyDoom worm, Sasser and Netsky worms, Code Red worm, Nimda virus, ILOVEYOU virus, Melissa virus, Cyborg Ransomware, GoBrut virus, Jokeroo malware, CryptoMix Clop Ransomware, Trojan Glupteba virus, Fake Windows Updates (Hidden Ransomware), and News Malware Attacks.
Hot Technologies in Cybersecurity
To combat evolving cyber threats, several hot technologies are gaining traction:
Context-Aware Behavioral Analytics: By using sophisticated behavioral analytics, companies can monitor and identify suspicious behavior or transactions, addressing the issue of overwhelming security alerts.
Next Generation Breach Detection: Combining machine learning and behavioral analytics, these technologies detect breaches and trace them to their source, tackling "zero-day" exploits.
Virtual Dispersive Networking (VDN): VDN splits messages into multiple parts, encrypts them, and routes them over different protocols on independent paths, enhancing encryption security.
Challenges in Cybersecurity
Despite the advancements, several challenges persist in the cybersecurity domain:
Low Cybersecurity Budget and High Installation Costs: Emerging startups often lack sufficient budgets to implement Next-Generation Firewalls (NGFWs) and Advanced Threat Protection (ATP) solutions. This limits the adoption of cybersecurity solutions, particularly in small businesses within developing economies.
Designing and Deploying Cybersecurity Solutions: Transitioning from a network perimeter-based approach to a user-based and application-based security model presents design and implementation challenges. This transition requires a thorough network analysis and a deep understanding of each user, device, application, and resource.
Regional Analysis
The North American region is at the forefront of cybersecurity advancements, with several prominent market players delivering cutting-edge solutions across various industries. Strategic investments, partnerships, and significant R&D activities contribute to the widespread deployment of cybersecurity solutions. Key players such as IBM, Oracle, Fortinet, Microsoft, and Trend Micro, along with several startups, are offering enhanced cybersecurity software solutions and services to meet customer needs, driving market growth in North America.
0 notes
Text
Unlocking Data Recovery Excellence with Tech4Service
At Tech4Service, we understand the heartache that can accompany the loss of precious data. Whether it’s family photos, critical business documents, or important project files, we know that data loss can be distressing and costly. That’s why we’re here to offer you top-tier data recovery services in Edmonton, with a specialization in handling mechanical failures.Computer Repair Shop Near Me
Mechanical Failure Recovery
Our team of skilled engineers operates in a specially sanitized clean room environment, minimizing risks and optimizing recovery outcomes for mechanical failures. When your hard drive experiences a mechanical failure, it requires delicate handling, and that’s precisely what we provide. Our goal is simple: to recover your valuable data safely and efficiently.
Drive Imaging for Thorough Recovery
To ensure comprehensive data recovery, all hard drives entrusted to us undergo imaging in a full working environment. This step allows us to create a complete copy of your drive, ensuring that no data is left behind. Our drive imaging process is a vital part of our success in delivering efficient data recovery solutions.
Specialist Tools for Complex Cases
Tech4Service utilizes proprietary tools that set us apart in the industry. We can recover data from damaged drives by reading around the affected areas, effectively retrieving the entire drive’s contents. When faced with challenging cases, our specialist tools and expertise enable us to recover data that others might consider lost.
Ransomware Recovery Expertise
In addition to mechanical failures, we specialize in ransomware recovery. Over the years, we’ve successfully restored data from various ransomware infections, including notorious variants like Cryptolocker, Arrow, JAVA, UHV, DMA, XTBL, Kyra, Thor, Lucky, CrytpoMIX, Microsoft Crypto, Arena, Nuclear, Aleta, NuroRing, NM4, Gryphon, BTC, Zepto, and many more. Our experience in dealing with ransomware infections is unrivaled.
Hard Drive Recovery Solutions
Our data recovery services extend to a wide range of hard drive issues, such as faulty read/write heads, spindle motor seizure, faulty controller PCBs, deleted, lost, or formatted data, bad sectors, firmware failure, and corrupt file systems. No matter the nature of the problem, we have the expertise to handle it.
Apple Mac Recovery Expertise
Tech4Service offers free evaluations at competitive prices for Apple Mac data recovery. We understand that data loss can be particularly distressing for Mac users, and we’re here to provide reassurance and efficient solutions for Mac-related data recovery.
Leave Data Recovery to the Experts
Attempting DIY data recovery from a compromised drive can worsen the situation and result in more data loss. When you choose Tech4Service, you’re opting for years of experience, cutting-edge research, and unwavering dedication to data recovery. Leave the process to our experts, and rest assured that your data will be handled professionally and securely.
Conclusion
Tech4Service is your trusted partner when it comes to data recovery services in Edmonton. Equipped with a state-of-the-art clean room, drive imaging capabilities, and specialist tools, we’re ready to tackle any data recovery challenge. Our expertise extends to ransomware recovery, hard drive recovery, and Apple Mac data restoration. Don’t risk further complications by attempting DIY recovery. Trust the experts at Tech4Service to regain your valuable data with confidence. Your data is worth it, and so are you.Laptop Repair Shop Near Me
0 notes
Text
Lo scorso 13 febbraio scrissi un post in cui, senza avere le adeguate competenze, provai a immaginare le conseguenze geopolitiche ed economiche della guerra di invasione russa.
Ora, leggendo dell'attacco informatico alla nostra rete ferroviaria, comincio a pensare che forse sono stato un facile indovino quando ho parlato dei rischi a cui ci espone l'insicurezza dei nostri sistemi telematici.
"Questa volta, poi, temo che quella verrà (e voglia il cielo che non venga) sarà anche una cyberguerra. La Russia oltre a chiuderci la canna del gas, penetrerà anche nei nostri deboli sistemi di sicurezza digitale, provocando problemi a catena che potrebbero essere perfino più gravi della crisi energetica."
Questo scrissi, più di un mese fa. E vorrei ancora essermi sbagliato.
Magari quelli di ieri erano semplici hacker, cybercriminali interessati solo a chiedere un riscatto per consegnarci le chiavi del cryptolocker che è stato introdotto nella rete del sistema di vendita dei biglietti di Trenitalia.
Ma questo non fa che confermare la facilità con cui sia possibile penetrare nei nostri dati per decriptare, criptare, bloccare o oscurare i nostri dati e mettere in crisi interi sistemi su cui ormai si reggono le nostre vite.
#cyberguerra#sicurezza digitale#cittadinanza digitale#aitan#cryptolocker#virus#aitanblog#guerra#hacker
3 notes
·
View notes
Text
Le ransomware Crypt0L0cker
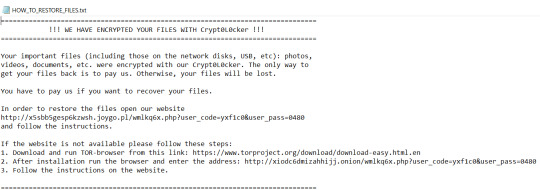
Ce ransomware Crypt0L0cker (les O sont remplacés par des ZERO) est apparu en 2015 en descendant direct de la famille TorrentLocker. Il a souvent été propagé par une pièce-jointe infectée via des campagnes de courrier électronique. Une fois que les fichiers sont cryptés, Crypt0L0cker rajoute une extension à chaque fichier et laisse une ou plusieurs notes de demande de rançon. Les extensions des fichiers cryptés les plus courantes de ce ransomware sont : - .enc - .encrypted - .asdgfd, .udezum, .smejux, .etc... soit une série de 6 lettres aléatoires - .vendeta La demande de rançon est souvent laissée sous deux formats, le premier en texte et le deuxième en html, soit en anglais, soit dans la langue de la victime : HOW_TO_RESTORE_FILES.txt HOW_TO_RESTORE_FILES.html DECRYPT_INSTRUCTIONS.html DECRYPT_INSTRUCTIONS.txt
COME_RIPRISTINARE_I_FILE.txt COME_RIPRISTINARE_I_FILE.html ISTRUZIONI_DECRITTAZIONE.txt ISTRUZIONI_DECRITTAZIONE.html
COMO_RESTAURAR_ARCHIVOS.html COMO_RESTAURAR_ARCHIVOS.txt
INSTRUCCIONES_DESCIFRADO.txt INSTRUCCIONES_DESCIFRADO.html wie_zum_Wiederherstellen_von_Dateien.txt wie_zum_Wiederherstellen_von_Dateien.html COMMENT_RESTAURER_DES_FICHIERS.txt COMMENT_RESTAURER_DES_FICHIERS.html SIFRE_COZME_TALIMATI.txt SIFRE_COZME_TALIMATI.html Contenu type de la demande de rançon : ------------------------------------------------------- ============================================================= !!! WE HAVE ENCRYPTED YOUR FILES WITH Crypt0L0cker !!! =============================================================Your important files (including those on the network disks, USB, etc): photos, videos, documents, etc. were encrypted with our Crypt0L0cker. The only way to get your files back is to pay us. Otherwise, your files will be lost.You have to pay us if you want to recover your files.If you want your files to be decrypted write us: [email protected] ============================================================= ou ============================================================= !!! WE HAVE ENCRYPTED YOUR FILES WITH Crypt0L0cker !!! =============================================================
Your important files (including those on the network disks, USB, etc): photos, videos, documents, etc. were encrypted with our Crypt0L0cker. The only way to get your files back is to pay us. Otherwise, your files will be lost.
You have to pay us if you want to recover your files.
In order to restore the files open our website http://e3tdxhll5fa6rirn.micronit.tw/c5aykzm0.php?user_code=5l2nyi9&user_pass=1037 and follow the instructions.
If the website is not available please follow these steps: 1. Download and run TOR-browser from this link: https://www.torproject.org/download/download-easy.html.en 2. After installation run the browser and enter the address: http://vhx6kpgibjohmvox.onion/c5aykzm0.php?user_code=5l2nyi9&user_pass=1037 3. Follow the instructions on the website.
=============================================================
Ce ransomware a été longuement analysé par notre laboratoire de décryptage et nous avons un excellent taux de récupération des fichiers cryptés. Pour toutes demandes à ce sujet, veuillez nous envoyer avec www.wetransfer.com à l’adresse [email protected] la demande de rançon et 4 fichiers cryptés avec vos coordonnées. Après analyse de vos fichiers et seulement si nous arrivons à concevoir un décrypteur pour récupérer vos fichiers cryptés, nous vous proposerons le kit de récupération pour 150 euros hors taxe.
1 note
·
View note
Text
Attacco Virus CryptoLocker: tecniche per difendere i nostri dati

In questo articolo vi parliamo del CryptoLocker si tratta di un noto Ransomware. Ossia è un virus che una volta che è penetrato all'interno del vostro PC blocca i vostri file di sistema Criptandoli, da qui il nome, ed impedendo che possano essere aperti. Quindi si tratta come vi dicevamo di un virus che agisce sui sistemi operativi in particolare Windows. La prima volta che si è sentito parlare di questo virus era l'anno 2013 e in appena 2 mesi è riuscito a estorcere ai malcapitati la cifra di 27 milioni di dollari. Purtroppo con il passare degli anni questo virus ha continuato a costituire una minaccia reale, dato che è sempre stato aggiornato alle nuove versioni del SO.
Cos'è CryptoLocker?
Si tratta fondamentalmente di un Trojan, ossia un virus che entra nel vostro sistema operativo con un sotterfugio ed è quindi in grado di modificare i vostri dati, nel caso specifico appunto Criptandoli. Se volete rientrare in possesso dei vostri dati dovrete letteralmente pagare un riscatto tipicamente in bitcoin . Dopo l'avvenuto pagamento dovreste ricevere una chiave di decodifica. Ma di fatto non c'è nessuna garanzia reale che queto avvenga veramente.
Il funzionamento del virus nel vostro sistema operativo.
Il troiano viene inviato al Computer che vuole infettare tipicamente tramite email, oppure una botnet, ossia una rete che è formata da PC che sono stati infettati da malware , controllati da un solo dispositivo. La vittima ignara di quello che sta per succedergli apre il file , tipicamente gli viene chiesto di inserire una password contenuta all'interno del Messaggio. Questa PSW gli permetterà per esempio di aprire un ipotetico file PDF ricevuto in allegato. Di fatto attiverete un file exe che andrà a crittografare con la chiave pubblica i file dati e di sistema presenti nel vostro Computer. Ovviamente la chiave privata rimarrà nella disponibilità unicamente dell'hacker che fisicamente ha predisposto l'attacco. Per recuperare questi file ci sono purtroppo unicamente due modi Pagamento del riscatto e speranza di ottendere la chiave privata dall'estorsore avere fatto un backup del vostro Computer e quindi ripristinare la versione hackerata.
Come difendersi dai RansomWare
Beh diciamola così se seguirete tutti i consigli che adesso vi daremo le probabilità di essere infettati. - Vi potrà sembrare una banalità, ma tenete il vostro Sistema Operativo sempre aggiornato. - Programmati back periodico, vi consiglio una a settimana nel fine settimana. - Massima attenzione ai messaggi di posta elettronica che contengano allegati provenienti da mittenti conosciuti ma che generalmente non li inviano. Se provengono da mittenti sconosciuti prima di aprirlo pensateci bene 100 volte. - Disattivate le estensioni di file nascosti al fine di riconoscere immediatamente un file dannoso. - Utilizzate un Antivirus professionale, non soluzioni free. - Anche se sono riusciti a bloccare il vostro PC e non ne avete una copia di back up, onestamente vi sconsiglio di pagare il riscatto per due semplici motivi. Il primo perchè alimentate delle pratiche illegali. La seconda è che difficilmente vi verrà consegnata la chiave privata. Il consiglio è sempre quello di contattare la Polizia Postale a prescindere. Read the full article
0 notes
Text
Ferrovie sotto attacco informatico, modus operandi riconducibile ad hacker russi
Ferrovie sotto attacco informatico, modus operandi riconducibile ad hacker russi Fs: "Per ora impossibile risalire a origine"
ATTUALITA’ – 23 marzo 2022 Attacco informatico a Ferrovie, riconducibile ad hacker russi. Fs: “Per ora impossibile risalire a origine” E’ ipotizzabile che l’attacco informatico alle Ferrovie che ha bloccato alcuni sistemi della società sia riconducibile alla Russia. La tipologia dell’attacco informatico e il modus operandi, secondo fonti qualificate della sicurezza italiana, sarebbero infatti…

View On WordPress
#attacco hacker#attacco hacker a FS#Cryptolocker#ferrovie#ferrovie di stato#guerra russia-ucraina#hacker russi attacco a FS#infezione#internet#Italia#russia#ucraina#virus informatico
0 notes
Text
What The Hell Is Ransomware? Simple Explanation..
What The Hell Is Ransomware? Simple Explanation..
Ransomware is a strong threat to you and your computer devices , but what make this malware so dangerous? Ransomware is extortion software that can lock your computer and then demand a ransom for it release. In most case, ransomware infection occurs as follows . If you want to reduce the risk of a ransomware attack, you should rely on high-quality ransomware protection software and some computer…

View On WordPress
0 notes
Text
GridinSoft Anti-ransomware Software For PC
GridinSoft Anti-ransomware Software For PC
GridinSoft Anti-Ransomware works as a vaccine for PC! When protection is enabled, the ransomware bypasses your Windows computer! This is a free ransomware protection software that allows you to protect your computer against file-encrypting in a few simple clicks! Just run the program and be sure that your computer protected from any cryptovirus 24/7. You will never know how much it cost to…

View On WordPress
#Block Cryptolocker#Block Ransomware#file encryption software#Free Ransomware Protection#Free Ransomware Protection Software#Prevent Ransomware#protect your pc#Ransomware Cryptolocker#Ransomware Protection Software
0 notes
Link

Atempo professional services guide organizations and help put in place a rock-solid disaster recovery plan, so, not if but when the plan needs to be carried out, it will be a simple checklist to get your business back on track in minimum time.
0 notes
Text
WEBROOT

Just about every antivirus tool claims to be ‘lightweight’, but Webroot SecureAnywhere AntiVirus really delivers on this front. Installation takes seconds, and it only uses 15MB (yes, megabytes) of hard drive space – plus the app’s memory footprint is just as tiny, with virus definitions stored in the cloud. Considering this, there’s no compromise on features, which makes Webroot all the more impressive. SecureAnywhere AntiVirus gives you solid malware protection – although it isn’t ranked by the big-name testing labs – and extremely quick virus scans, along with a smart ‘firewall’ monitoring system, accurate real-time anti-phishing, identity theft protection and much more. Further up the Webroot range, SecureAnywhere Internet Security Plus expands coverage from Windows and Mac PCs to mobile devices, also providing a password manager (courtesy of LastPass) and covering up to five devices (rather than three). And at the top of the tree is Internet Security Complete which introduces an automatic backup tool (with 25GB of cloud storage) and additional online privacy features. SecureAnywhere AntiVirus gives you everything you need, really, although Internet Security Plus is the top pick for the most rounded package. Another boon worth bearing in mind here is Webroot’s confidence-instilling lengthy 70-day 100% money-back guarantee. Techradar.com No, this post is in no way sponsored by Webroot, even though it'd be cool to have a sponsor. Anyway. Read the full article
#antivirus#Avast#AVG#computers#CryptoLocker#free#geek#Kaspersky#Malwarebytes#McAfee#nerd#nerdcore#Norton#paid#software#tech#technology#webroot
0 notes
Photo

18 – “Cryptolocker teleport”
1 note
·
View note