#file encryption software
Explore tagged Tumblr posts
Text
Wonderful Web Wednesday 2
Testing Converso - Crnković
Converso was a messaging app meant to change the way people talked over the internet. It was released on the 21st of January, 2023 and is now gone from the internet. The only things left are a blog post exposing the absolutely rampant security flaws in their "state-of-the-art" encryption, and a couple of sponsored articles.
The article by Crnković was the catalyst that spun into the downfall of Converso. The post reads like an adventure book, telling the story of a great adventurer hacking and slashing through a field of broken promises.
The article begins by Crnković explaining how they heard about the app Converso. They had heard an ad for Converso on a podcast that presented Converso as an app that knew nothing about you or what you were talking about. From the perspective of someone who focuses a little bit on privacy, those sound like absolutely amazing promises. But from the perspective of a developer, I am a little skeptical, and so was Crnković.
This led them to digging into what was actually happening behind the scenes at Converso.
What they found is absolutely astonishing. I won't spoil a single bit here so go read it over at https://crnkovic.dev/testing-converso/!
Some secondary research (Spoilers)
Before writing this post, I decided to do some research into what Converso used to look like.
Here are the archives of the Converso website once at release and the other before the close - Converso's website at release - Converso's website near their closing
File Over App - Steph Ango
This quick essay by Steph Ango is an amazing 1 minute read. The essay explains that as we travel through the digital world, we deposit our data across hundreds of proprietary formats and servers. What happens when these formats and servers disappear? Where does the data that we have created go?
It just disappears to be lost forever.
There is a beauty in the way Steph Ango expresses their drive to durable data. They relate the files and data we create to the history our ancestors have left behind. Stone tablets, hieroglyphics, and ancient books have stood the test of time, proving to be information that is truly durable.
Making information that is durable is at the center of what Steph thinks tool makers need to account for when creating software. The tools that they create will not exist forever, but the data that their tools create should exist forever.
This is why Steph urges tool makers to give users access to their data in durable, transportable, and archivable formats. This way, if a user wants to see what they were doing 5 years or 5 decades ago, they can.
#wonderfulwebwednesday#wonderfulweb#files#app#software engineering#softwaredeveloper#encryption#blog#short reads#obsidian md#obsidian.md
4 notes
·
View notes
Text
I had a full on panic attack because I thought all my WIPs were gone bc I couldn't tell where one drive had hidden them.
getting new technology feels more infuriating every year. got a new computer for the first time in 8 years and everything about windows 11 and how it handles onedrive is driving me up the wall
#This was also when I found out that the backup software I was using had been putting my files into a proprietary encryption#And I couldn't just go in and find the back up of a file I was looking for#It was a real fun panic attack day for Sammy
23K notes
·
View notes
Text
Secure File Sharing: Best Free Encryption Tools in 2025
Introduction In an age where cyber threats are becoming more sophisticated by the day, file sharing without encryption is like sending a postcard—anyone can read it. Whether you’re a freelancer, student, small business owner, or just someone sending sensitive documents to a friend, using encrypted file-sharing tools is a must. The good news? You don’t need to spend a penny to do it securely. In…
#best free cloud encryption#end-to-end file sharing 2025#free encryption software#privacy-first file storage#secure file sharing tools
0 notes
Text
Folder Lock
If you have folders and files that you want to keep private, consider using Folder Lock. Unlike My Lockbox, it isn’t a free app, but it offers excellent configuration options and numerous methods to protect important and private documents from prying eyes. Folder Lock is a complete solution for keeping your personal files encrypted and locked, while automatically and in real-time backing up…
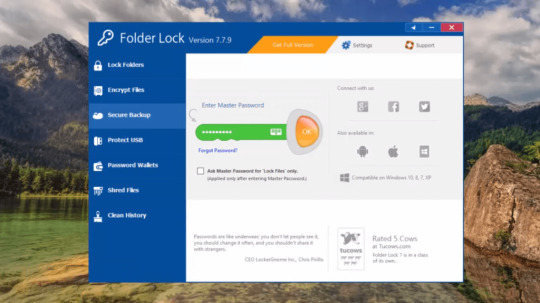
View On WordPress
#Data Encryption#Digital Wallets#Encryption Software#File Locking#File Management#File Security#File Shredding#password protection#Portable Security#privacy protection#Secure Backup#Windows Security
0 notes
Text
#best encryption tools#computer security#cybersecurity#data breach prevention#data encryption guide#data privacy#data protection#data safety#data security tips#digital security#encrypting personal information#encryption basics#encryption FAQs#encryption for beginners#encryption software#encryption solutions#encryption techniques#guide to data encryption#how to encrypt data#online privacy#personal data security#prevent cyber attacks#privacy software#protect data online#secure communication#secure data encryption#secure files and folders#secure personal data#software for encryption#strong encryption methods
1 note
·
View note
Text
Some People Using ZuluCrypt?
File:VeraCrypt screenshot.png I had more dreams, but I did not record them. Now, all that I can remember is barely part of my last dream. This dream involved ZuluCrypt and / or one or more other encryption programs / software / applications / apps like VeraCrypt et cetera. In this dream, some groups of people & individuals were on computers using the operating system, Linux, probably the…
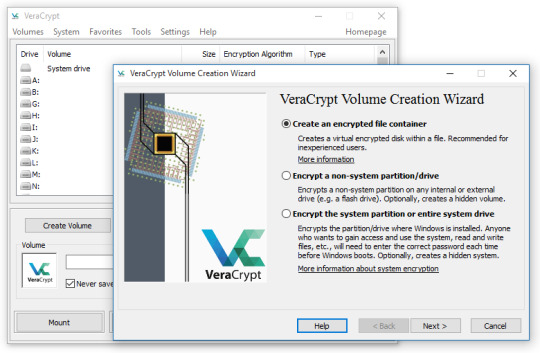
View On WordPress
#Computer#Container#Container File#Container Format#Dismount#Encryption#Favorite#Linux#Mount#opensource#Program#Software#Ubuntu#VeraCrypt#ZuluCrypt
0 notes
Text
Man's child pornography arrest: 'More charges are expected' when encryption defeated
(As originally published, Thu, January 18th 2024) THE VILLAGES, Fla. (TND) — A tip about a man uploading child pornography led to his arrest on a possession charge but authorities say “more charges are expected.” According to Sumter County detectives in Florida, “The image uploaded appeared to be a child under the age of 10.” They investigated and early last Wednesday, Jan. 10, served a search…

View On WordPress
#activity#Alan#analysis#Burke#electronic#encryption#examination#FDLE Florida Department of Law Enforcement#files#forensic#image#possession#seizure#software#Timothy
0 notes
Text
For those who are not aware: Bitlocker is encryption software, it encrypts your computer and makes it impossible to access the information on the computer unless you have the key.
It should be standard practice for IT companies to document the bitlocker keys as they are configuring bitlocker on a computer; generally you would do this by creating a record in your client management software for that specific device and putting the key in the record. Sometimes software can be used to extract that information in the event that it's necessary, but even if there's theoretically a way to extract the key, it should be documented somewhere *other* than on the encrypted computer.
This is something that a lot of IT people fuck up on kind of a lot (we've definitely had problems with missing bitlocker keys and I'm quite happy that the people who didn't document those keys aren't my coworkers anymore).
So what do you do if you want to use encryption software and you're NOT an IT company using a remote management tool that might be able to snag the keys?
When you are setting up encryption, put the encryption key in your password manager. Put it in your password manager. Document the important information that you cannot lose in your password manager. Your password manager is a good place to keep important things like your device encryption key, which you do not want lost or stolen. (If you run your password manager locally on an encrypted computer, export the data every once in a while, save it as an encrypted file, and put the file on your backup drive; you are going to have a bad time if your computer that hosts the only copies of your passwords shits the bed so *make a backup*)
This is my tip for home users for any kind of important recovery codes or software product keys: Print out the key and put it in your underwear drawer. Keep it there with your backup drive. That way you've got your important (small) computer shit in one place that is NOT your computer and is not likely to get shifted around and lost (the way that papers in desks often get shifted around and lost).
2K notes
·
View notes
Text
ONİONSİTES - DRAGON+ (2)

Onion sites, also known as.onion sites, are a unique type of website that can only be accessed through the Tor network. The Tor network, short for The Onion Router, provides a layer of anonymity and encryption for users accessing these sites, making them popular for those seeking privacy and security online. Unlike traditional websites that can be accessed through standard web browsers, onion sites list require special software, such as the Tor browser, to navigate. Individuals can create onion versions of regular websites or develop standalone onion sites for specific purposes. The exclusivity and privacy features of onion sites contribute to their appeal for various users, ranging from privacy advocates to individuals navigating the dark web for specific content.
There are several reasons why individuals choose to use onion sites, with privacy and anonymity being at the forefront. Onion sites offer a level of confidentiality that is not typically found on the surface web, making them attractive to individuals seeking to protect their identity and browsing habits. Moreover, best onion sites can provide access to content that may be restricted or censored in certain regions, allowing users to circumvent such limitations and access information freely. The encrypted nature of the Tor network adds an additional layer of security, reducing the risk of surveillance and tracking by third parties, including governments and internet service providers.
Common types of content found on onion sites range from forums and marketplaces to news outlets and secure communication platforms. While exploring onion sites, individuals may come across forums, chat rooms, file-sharing platforms, and other interactive spaces that facilitate communication and information exchange in a secure environment. The anonymity and encryption offered 2024 onion sites contribute to a unique online experience, enabling users to engage with content and communities that may not be easily accessible through conventional web browsers.
1K notes
·
View notes
Text
Copyright law: making personal copies of copyrighted work

image sourced from a Cory Doctorow article on DMCA: X (recommended reading)
creating a digital backup (legally, it's called making an "archival copy") of software is explicitly allowed. but copying or alerting books, music, vehicle operating systems, movies, shows, and so on - even those you’ve legally purchased - gets complicated due to overlapping laws
under the doctrine of "fair use," we are permitted to make backup / archival copies under certain conditions:
copyright law allows you to make copies for personal use in case the original is lost, damaged, or destroyed; or to change formats to use on new devices; or to otherwise alter or repair the original for your own personal use
all this falls within fair use
however, making a copy of copyrighted work simply for your own ease of use could be construed as copyright infringement
furthermore, the Digital Millennium Copyright Act (DMCA) restricts this by prohibiting "circumvention of encryption" on devices like DVDs and Blu-rays
the DMCA criminalizes making and disseminating technology, devices, or services intended to circumvent measures that control access to copyrighted works (aka "digital rights management" locks or DRM), and in fact criminalizes the act of circumventing access controls, whether or not doing so infringes on the copyright of the work itself
so, unless the original work you buy is unlocked, corporations that hold the copyright of that work can prosecute you for making legal archives of the material you own
and if the thing you bought is lost or damaged, or if the file format is no longer usable? you're just out of luck
DMCA needs to go
#copyright#ownership#archival copies#DMCA#backups#copyright infringement#capitalism ruins everything#my edits
296 notes
·
View notes
Text

He should be arrested for violating our privacy. He was not vetted by congress and has no security clearance.
Contact your state’s attorney general and request help.
Can we ask the ACLU to file a class action suit? Who’s with me?
“Let’s get into the details. Musk’s staffers have been caught plugging external hard drives into federal agency systems and reportedly locking others out of private rooms to perform—who knows what actions. This behavior violates key cybersecurity laws under FISMA and NIST guidelines, which are designed to protect sensitive federal information. Here’s why this is a serious problem.
Federal systems are strictly regulated, allowing only approved devices to connect. Unauthorized external drives can introduce viruses, ransomware, or other harmful software that may compromise entire networks and disrupt essential operations. This puts system stability and continuity of services at risk, endangering critical infrastructure.
These devices could also be used to steal or damage critical information, including personal data for millions of Americans—such as Social Security recipients and taxpayers. Unauthorized access creates significant vulnerabilities, exposing sensitive data to the risk of cyberattacks. Such attacks could cripple vital services and compromise the privacy and safety of millions of people.
Additionally, federal agencies have strict access controls to prevent unauthorized data manipulation or theft. When unauthorized devices are connected, these protections are bypassed, allowing unauthorized users to potentially alter or extract sensitive data. This undermines system integrity and opens the door to both internal and external threats.
External drives also often lack essential security features, such as encryption and antivirus scanning, making them vulnerable to cybercriminal exploitation. These security gaps further increase the risk of data breaches and system compromise, which can have far-reaching consequences.
Federal systems handle trillions of dollars in payments and manage personal data for millions of U.S. citizens. By bypassing cybersecurity laws and protocols, Musk’s staffers are putting these systems—and the public—at serious risk. This activity is illegal, reckless, and unacceptable. Immediate oversight and intervention are necessary to stop these violations!” ~ A N P S
225 notes
·
View notes
Text
me when companies try to force you to use their proprietary software

anyway
Layperson resources:
firefox is an open source browser by Mozilla that makes privacy and software independence much easier. it is very easy to transfer all your chrome data to Firefox
ublock origin is The highest quality adblock atm. it is a free browser extension, and though last i checked it is available on Chrome google is trying very hard to crack down on its use
Thunderbird mail is an open source email client also by mozilla and shares many of the same advantages as firefox (it has some other cool features as well)
libreOffice is an open source office suite similar to microsoft office or Google Suite, simple enough
Risky:
VPNs (virtual private networks) essentially do a number of things, but most commonly they are used to prevent people from tracking your IP address. i would suggest doing more research. i use proton vpn, as it has a decent free version, and the paid version is powerful
note: some applications, websites, and other entities do not tolerate the use of VPNs. you may not be able to access certain secure sites while using a VPN, and logging into your personal account with some services while using a vpn *may* get you PERMANENTLY BLACKLISTED from the service on that account, ymmv
IF YOU HAVE A DECENT VPN, ANTIVIRUS, AND ADBLOCK, you can start learning about piracy, though i will not be providing any resources, as Loose Lips Sink Ships. if you want to be very safe, start with streaming sites and never download any files, though you Can learn how to discern between safe, unsafe, and risky content.
note: DO NOT SHARE LINKS TO OR NAMES OF PIRACY SITES IN PUBLIC PLACES, ESPECIALLY SOCAL MEDIA
the only time you should share these things are either in person or in (preferably peer-to-peer encrypted) PRIVATE messages
when pirated media becomes well-known and circulated on the wider, public internet, it gets taken down, because it is illegal to distribute pirated media and software
if you need an antivirus i like bitdefender. it has a free version, and is very good, though if youre using windows, windows defender is also very good and it comes with the OS
Advanced:
linux is great if you REALLY know what you're doing. you have to know a decent amount of computer science and be comfortable using the Terminal/Command Prompt to get/use linux. "Linux" refers to a large array of related open source Operating Systems. do research and pick one that suits your needs. im still experimenting with various dispos, but im leaning towards either Ubuntu Cinnamon or Debian.
#capitalism#open source#firefox#thunderbird#mozilla#ublock origin#libreoffice#vpn#antivirus#piracy#linux
695 notes
·
View notes
Text
Technomancy: The Fusion Of Magick And Technology

Technomancy is a modern magickal practice that blends traditional occultism with technology, treating digital and electronic tools as conduits for energy, intent, and manifestation. It views computers, networks, and even AI as extensions of magickal workings, enabling practitioners to weave spells, conduct divination, and manipulate digital reality through intention and programming.
Core Principles of Technomancy
• Energy in Technology – Just as crystals and herbs carry energy, so do electronic devices, circuits, and digital spaces.
• Code as Sigils – Programming languages can function as modern sigils, embedding intent into digital systems.
• Information as Magick – Data, algorithms, and network manipulation serve as powerful tools for shaping reality.
• Cyber-Spiritual Connection – The internet can act as an astral realm, a collective unconscious where digital entities, egregores, and thought-forms exist.
Technomantic Tools & Practices
Here are some methods commonly utilized in technomancy. Keep in mind, however, that like the internet itself, technomancy is full of untapped potential and mystery. Take the time to really explore the possibilities.
Digital Sigil Crafting
• Instead of drawing sigils on paper, create them using design software or ASCII art.
• Hide them in code, encrypt them in images, or upload them onto decentralized networks for long-term energy storage.
• Activate them by sharing online, embedding them in file metadata, or charging them with intention.
Algorithmic Spellcasting
• Use hashtags and search engine manipulation to spread energy and intent.
• Program bots or scripts that perform repetitive, symbolic tasks in alignment with your goals.
• Employ AI as a magickal assistant to generate sigils, divine meaning, or create thought-forms.

Digital Divination
• Utilize random number generators, AI chatbots, or procedural algorithms for prophecy and guidance.
• Perform digital bibliomancy by using search engines, shuffle functions, or Wikipedia’s “random article” feature.
• Use tarot or rune apps, but enhance them with personal energy by consecrating your device.
Technomantic Servitors & Egregores
• Create digital spirits, also called cyber servitors, to automate tasks, offer guidance, or serve as protectors.
• House them in AI chatbots, coded programs, or persistent internet entities like Twitter bots.
• Feed them with interactions, data input, or periodic updates to keep them strong.
The Internet as an Astral Plane
• Consider forums, wikis, and hidden parts of the web as realms where thought-forms and entities reside.
• Use VR and AR to create sacred spaces, temples, or digital altars.
• Engage in online rituals with other practitioners, synchronizing intent across the world.
Video-game Mechanics & Design
• Use in-game spells, rituals, and sigils that reflect real-world magickal practices.
• Implement a lunar cycle or planetary influences that affect gameplay (e.g., stronger spells during a Full Moon).
• Include divination tools like tarot cards, runes, or pendulums that give randomized yet meaningful responses.

Narrative & World-Building
• Create lore based on historical and modern magickal traditions, including witches, covens, and spirits.
• Include moral and ethical decisions related to magic use, reinforcing themes of balance and intent.
• Introduce NPCs or AI-guided entities that act as guides, mentors, or deities.
Virtual Rituals & Online Covens
• Design multiplayer or single-player rituals where players can collaborate in spellcasting.
• Implement altars or digital sacred spaces where users can meditate, leave offerings, or interact with spirits.
• Create augmented reality (AR) or virtual reality (VR) experiences that mimic real-world magickal practices.
Advanced Technomancy
The fusion of technology and magick is inevitable because both are fundamentally about shaping reality through will and intent. As humanity advances, our tools evolve alongside our spiritual practices, creating new ways to harness energy, manifest desires, and interact with unseen forces. Technology expands the reach and power of magick, while magick brings intention and meaning to the rapidly evolving digital landscape. As virtual reality, AI, and quantum computing continue to develop, the boundaries between the mystical and the technological will blur even further, proving that magick is not antiquated—it is adaptive, limitless, and inherently woven into human progress.

Cybersecurity & Warding
• Protect your digital presence as you would your home: use firewalls, encryption, and protective sigils in file metadata.
• Employ mirror spells in code to reflect negative energy or hacking attempts.
• Set up automated alerts as magickal wards, detecting and warning against digital threats.
Quantum & Chaos Magic in Technomancy
• Use quantum randomness (like random.org) in divination for pure chance-based outcomes.
• Implement chaos magick principles by using memes, viral content, or trend manipulation to manifest desired changes.
AI & Machine Learning as Oracles
• Use AI chatbots (eg GPT-based tools) as divination tools, asking for symbolic or metaphorical insights.
• Train AI models on occult texts to create personalized grimoires or channeled knowledge.
• Invoke "digital deities" formed from collective online energies, memes, or data streams.
Ethical Considerations in Technomancy
• Be mindful of digital karma—what you send out into the internet has a way of coming back.
• Respect privacy and ethical hacking principles; manipulation should align with your moral code.
• Use technomancy responsibly, balancing technological integration with real-world spiritual grounding.
As technology evolves, so will technomancy. With AI, VR, and blockchain shaping new realities, magick continues to find expression in digital spaces. Whether you are coding spells, summoning cyber servitors, or using algorithms to divine the future, technomancy offers limitless possibilities for modern witches, occultists, and digital mystics alike.

"Magick is technology we have yet to fully understand—why not merge the two?"
#tech witch#technomancy#technology#magick#chaos magick#witchcraft#witch#witchblr#witch community#spellwork#spellcasting#spells#spell#sigil work#sigil witch#sigil#servitor#egregore#divination#quantum computing#tech#internet#video games#ai#vr#artificial intelligence#virtual reality#eclectic witch#eclectic#pagan
107 notes
·
View notes
Text
Echos of The Fallen

Chapter 3: Crimson Heist Shadow the Hedgehog x Reader Warnings: A little firting but thats it

September 30th - 7:45 AM - G.U.N. Headquarters
The remnants of the explosion still hung in the air, the scent of charred metal and burnt rubber clinging to Shadow’s uniform as he stepped into the war room. The monitors on the walls flickered with the latest updates—feeds from the wreckage site, reports from analysts trying to piece together what little information they had. The entire building seemed to hum with tension, the weight of last night’s failure pressing down on everyone inside.
Rouge was already seated at the long metal table, idly examining her nails as she waited for him. Omega stood nearby, his mechanical frame motionless save for the occasional whir of servos adjusting his position. The moment Shadow entered, Rouge glanced up, arching a perfectly sculpted brow.
“Well, well,” she mused, tilting her head. “You look like hell.”
Shadow ignored her, dropping into the chair across from her and flicking open the latest intel file. “We lost her.” His voice was clipped, edged with irritation.
“No kidding.” Rouge smirked, leaning forward. “You let a woman get the best of you. Now that’s a first.”
Shadow’s crimson eyes narrowed. “She was ten steps ahead. The explosion was a diversion, and we took the bait.” His fingers drummed against the table, betraying his frustration. “She’s not just some rogue mercenary. She knows how we operate.”
Omega’s monotone voice rumbled to life. “RECOMMENDATION: TERMINATION OF TARGET UPON IDENTIFICATION.”
Rouge scoffed. “So dramatic. We don’t even know who she really is yet. ‘Danny’s wife’ doesn’t exactly lead us anywhere.”
Shadow turned the file toward her. “She’s connected to Cipher. That’s all we need to know.”
Rouge’s expression darkened slightly at the mention of the name. “So, Cipher’s making moves again. Last time he popped up, it took half of G.U.N.’s intelligence division to track down just one of his hideouts. If she’s working with him, she’s dangerous.”
“Obviously.” Shadow’s voice was tight. “The question is why. What does Cipher want with G.U.N.’s classified weapons project?”
Rouge shrugged, leaning back in her chair. “Power? Leverage? Or maybe he’s just bored. But something tells me your little rooftop admirer is more than just an errand girl.”
Shadow frowned. “What do you mean?”
Rouge’s smirk returned, playful and knowing. “She could’ve killed you last night, but she didn’t.”
Shadow remained silent, his jaw tightening. He had considered that already. The explosion had been designed to wound, to scatter forces, not to kill. If she had truly wanted him dead, she wouldn’t have left it to chance.
Omega interrupted the thought. “QUERY: NEXT COURSE OF ACTION?”
Shadow pushed the file toward the center of the table. “We find her. We stop her. No more games.”
September 30th - 10:12 PM - Underground Safehouse
The glow of multiple monitors bathed the dimly lit room in a soft blue hue, casting flickering shadows against the exposed concrete walls. The safehouse was tucked beneath the remnants of an abandoned subway station, far from prying eyes.
I sat in front of the main screen, scanning through lines of encrypted data as Zero worked his magic on the G.U.N. servers. The room was filled with the soft clacking of keys, the occasional beeping of software processes running in the background. Scar stood near the entrance, arms crossed, her gaze flicking between me and the screens.
“G.U.N. is scrambling,” Zero announced, his fingers flying across the keyboard. “They’ve got teams sweeping the city, but they’re running in circles.”
Scar smirked. “Shadow must be pissed.”
I didn’t react, my eyes still focused on the data. “Let him be. It won’t change anything.”
Zero’s hands stilled for a moment, his brow furrowing. “Hold up... This is new.”
I leaned forward. “What?”
He pulled up a series of documents, most of them redacted, but one detail stood out. A shipment manifest. Destination: G.U.N. Research Facility - Grid Sector Seven. Contents: Prototype X-09.
Scar whistled lowly. “Well, that sounds interesting.”
I exhaled slowly, my mind racing. “That’s what Carson was talking about.”
Zero nodded. “Whatever X-09 is, they’re keeping it locked down tight. I can't seem to find information on it. If G.U.N. wants it then that just makes it automatically bad.”
I tapped my fingers against my arm, calculating the next steps. “Then we move first. we break into the G.U.N. bank and steal some of their assets so they will be unable to fund this project anymore"
Scar raised an eyebrow. “You sure about that? If we intercept, we’ll be putting ourselves directly in Shadow’s path.”
A part of me hesitated, just for a fraction of a second. Then I pushed the thought aside. “Let him come. this time he won't know I know his turf.”
Zero cracked his knuckles, already preparing the next phase of the operation. “Then let’s get to work.”
Viper stood up, stretching her arms. "Alright, I’m grabbing food. Try not to blow anything up while I’m gone."
She slammed the door behind her, making the walls shake slightly. Nova immediately huffed, turning toward the door with an irritated glare. "Can you not? I’m working on an experiment!"
Viper’s voice called from the hallway, "Oh, I’m sorry, Princess! Didn’t mean to disrupt your evil genius time."
Nova scoffed. "At least I actually use my brain."
I rolled my eyes, shaking my head. "Guys, let’s be real. Unless you’re both on your period, let’s not bicker like this."
Nova shot me a glare, and Viper's laughter echoed from down the hall. "You wish, sweetheart!"
I smirked but turned back to the screens, my fingers hovering over the keyboard. The banter was familiar, almost comforting, but the weight of our situation pressed heavy on my mind. G.U.N. was moving fast, and we didn’t have time to waste.
Zero leaned back in his chair, exhaling sharply. "You really think we can pull this off?"
I didn’t answer right away, my eyes scanning over the shipment details. The security routes, the escort patterns—it was tight, but not impenetrable.
"We don’t have a choice," I finally said. "I do not trust them to have that weapon"
Scar crossed her arms, her gaze sharp. "And what happens when Shadow shows up?"
A beat of silence filled the room. That was the real problem. Shadow wasn’t like the grunts G.U.N. usually sent after us. He didn’t make mistakes. He didn’t let people slip through his fingers twice.
I exhaled. "Then we adapt."
The tension settled in the air, thick and unspoken. This wasn’t just another job—this was a battle waiting to happen.
The door creaked open again, and Viper strolled back in, holding a bag of takeout. "Alright, nerds, eat up. If we’re gonna risk our lives in forty-eight hours, you might as well not do it on an empty stomach."
Nova snatched the bag from her hands. "Finally, you’re useful for something."
Viper smirked. "Careful, Princess. Keep talking like that, and I might ‘accidentally’ forget your order next time."
As they bickered, I stared at the screens, the blueprint of the G.U.N. transport route flashing in front of me. This was it. The moment we made our move, there was no turning back.
I clenched my jaw, determination settling in.
We had forty-eight hours to pull off the impossible.
And failure wasn’t an option.

1:45 AM – G.U.N. Financial Holdings, Downtown
Everything had been going smoothly—too smoothly. Scar and I had just finished loading the last of the stolen assets into our bags when a sharp, high-pitched beep cut through the silence.
"Tell me that wasn’t you," Scar muttered.
I looked down at my wrist device, where a flashing red warning glowed across the screen. Silent alarm triggered.
"Shit," I hissed. "We need to move—now."
We bolted for the exit, weaving through the dimly lit corridors of the underground vault. But as we reached the stairwell, the sound of approaching footsteps echoed through the space. Heavy. Coordinated. Armed.
Scar gritted her teeth. "They’re fast."
"They’re G.U.N.," I shot back. "Of course they are."
We reached the main hall just as the security doors slammed shut behind us. A single figure stepped through the haze of flashing red lights. Black and red. Sharp crimson eyes locked onto mine.
Shadow.
Behind him, his team—Rouge and Omega—stood ready, blocking the only other exit.
"You really thought you could just waltz in and take what you wanted?" Shadow’s voice was low, measured, but there was an edge of irritation in it. "You’re getting sloppy."
Scar and I exchanged glances before moving in opposite directions. Shadow’s eyes flicked between us, assessing. Calculating.
"Take them," he ordered.
Rouge lunged for Scar while Omega charged forward, aiming straight for me. I dodged, ducking behind a pillar as his massive arm smashed through it like it was paper.
As Omega charged toward me, I tried to dodge his powerful swing again, but this time I had a better idea.
"Geez, Omega, you ever think about toning it down?" I taunted, hoping to get under his circuits. He growled in response, tightening his grip.
"NEGATIVE," Omega boomed, his voice full of pure mechanical rage. "FULL DESTRUCTION MODE ENGAGED."
I couldn’t avoid his next hit in time, so I took a deep breath, waiting for the right moment. Omega swung harder, and this time, his fist collided with a wall near Rouge, sending debris flying everywhere.
A vulnerable moment.
Before he could adjust, I whipped out a small device from my belt. With a quick motion, I slapped it onto Omega's back. The device activated with a small electric buzz, sending a surge of energy into his system, causing his circuits to short-circuit and his movements to freeze.
Omega's massive frame shuddered, and his body froze in place. The once-booming voice became erratic. "ERROR. SYSTEM MALFUNCTION..."
I gave a sly grin. "Guess I’ll have to remind you how to play nice."
I turned just in time to see Shadow coming for me. Fast. I barely managed to block his first strike, but the sheer force sent me skidding back. He was relentless, each blow more precise than the last.
He feinted left before sweeping my legs out from under me. Before I could react, I was flat on my back, Shadow pinning me down, one knee pressing into my ribs, his hand gripping my wrist.
I struggled, but he didn’t budge. "Give it up," he said. "You’re done."
My mind raced. I needed a distraction. Something to throw him off—just for a second.
I locked eyes with him, smirking. "You gonna kiss me or something, handsome?"
Shadow’s expression flickered. Just for a second. A flash of confusion.
That was all I needed.
I drove my knee into his stomach, making him grunt in surprise. Using the momentum, I twisted us around, grabbing a pair of cuffs from my belt. Before he could recover, I snapped them around his wrist and slammed the other end to a reinforced pipe. The cuffs magnetized instantly, locking him in place.
His eyes widened slightly as he tested the restraints.
I grinned. "Gotta say, I didn’t expect you to be so easy to trap."
Shadow glared at me, but there was the faintest trace of pink on his face.
Scar broke free from Rouge’s grip, sprinting toward me. "We need to go!"
I pulled a smoke bomb from my belt, slamming it against the ground. Thick clouds engulfed the room, obscuring everything.
"See you around, handsome," I teased, before grabbing Scar’s wrist and making a break for the exit.
We darted through the emergency hatch we had scoped out earlier, leaving chaos in our wake. The sound of Shadow yanking at the cuffs and Omega’s booming voice echoed behind us, but we were already gone, disappearing into the night.
2:30 AM – Warehouse Hideout
We crashed through the doors, breathless, adrenaline still surging through our veins.
Zero looked up from his laptop. "I take it things didn’t go as planned?"
Scar dropped her bag onto the table, grinning. "Oh, it went great. Got the goods, fought Shadow, and someone got a little flirty mid-fight."
I rolled my eyes, slumping into a chair. "It was a tactical distraction."
Scar snorted. "Sure it was."
Viper raised an eyebrow. "Wait—you flirted with Shadow?"
Nova nearly choked on her drink. "Hold on, back up. Shadow the Hedgehog?"
I groaned, burying my face in my hands. "I’m going to regret this later."
Scar smirked, kicking her feet up onto the table. "Maybe. But for now? Totally worth it."

3:00 AM – G.U.N. Financial Holdings, Downtown
Shadow's POV
The smoke was thick, the echoes of their escape still ringing in my ears. I yanked futilely at the cuffs, feeling the cold metal dig into my wrist. They were designed to hold even the strongest, and for once, it seemed they might have me. But I didn’t have time to waste on my restraints. I had a bigger problem on my hands.
Omega was down, his system glitching from whatever trick that woman had pulled on him. He was muttering about malfunctions as Rouge approached me, her footsteps sharp and mocking.
“Well, that was quite the show, Shadow,” she said, her voice dripping with amusement.
I narrowed my eyes at her, trying to ignore the frustration bubbling inside me. “Save it, Rouge.”
She leaned in closer, her lips curling into a playful smirk. “Not so tough when you're distracted, huh? You got all flustered with her little stunt. Was that... flirtation? You know, I’ve seen you fight harder. Looks like someone’s got a soft spot.”
I could feel my pulse spike, irritation mixing with something I couldn’t quite place. "This isn't the time for your games."
Rouge raised an eyebrow, clearly enjoying my discomfort. "Oh, I’m not joking. You practically let her tie you up. Seems like you let your guard down for something more than just the mission."
I grit my teeth, pushing back the surge of heat in my chest. “She got lucky. That’s all.”
But Rouge wasn’t done. “Sure, sure. I mean, she’s pretty good, I’ll give her that. Had to be quick thinking to get you like that.” Her eyes twinkled as she surveyed the room, her gaze shifting from me to Omega’s malfunctioning state. "But the real question is—how did she even know how to get past all the security systems? Couldn’t have been just luck."
A thought clicked into place, something I hadn’t fully processed in the heat of the moment. The woman’s movements, the way she seemed to be one step ahead, even the tech on her person—it all seemed too familiar. My mind whirred.
“Wait...” I muttered, looking toward Rouge. “She... she knew too much about our systems. She moved like someone who’d been trained to break into places like this.”
Rouge leaned against a wall, watching me. “You think she was G.U.N. trained?” she asked, raising an eyebrow, clearly amused.
“Impossible,” I muttered under my breath, but the more I thought about it, the more it made sense. Her style, her tactics—everything about her reeked of G.U.N. precision, just twisted in a way I hadn’t expected.
“I don’t know, Shadow,” Rouge said, her voice softer now, more serious. “Maybe we should start asking the right questions. Why would someone like her target a G.U.N. facility... and why are we just now seeing her face?”
I clenched my fists, the truth dawning on me. “We’re missing something. Whoever she is, she’s connected to G.U.N. in ways we don’t understand yet.”
Rouge gave me a knowing look, her smirk fading into something more thoughtful. “You think this is the beginning of something bigger?”
I nodded, my gaze shifting back to where Scar and the woman had vanished. “It’s more than just a heist. It’s personal now.”

Guys be honest im trying to find a good length for the chapters i believe this is fine but please let me know
- Caty
58 notes
·
View notes
Note
stone faced anon (💫 anon if it's free) here; as someone who has a hyperfixation in IT and coding I also think it would be very funny if Boothill had an s/o who wasn't necessarily a mechanic but like a software engineer or just a real big nerd about coding or something. He'll be experiencing a malfunction or a memory leak and go "oh yeah this happens sometimes don't worry about it" and then 10 minutes later he's sitting down plugged into a laptop listening to his s/o rant about how terrible his code is (crack hc: boothill's code was written in javascript) and how it's a wonder he hasn't bricked* yet
Would also be mad funny if Boothill ever got hacked and his s/o basically says "no you're not" and uses a previously made system restore point or something because of course they would both use and design every feature imaginable to keep Boothill in control of his own body, can you imagine the stress that losing control would cause him?? Even better if whoever designed him originally intentionally left a backdoor incase he ever went against their orders and when they try to use it his s/o just goes "oh yeah I quarantined and encrypted all the old files related to that backdoor and whatever else you were planning on a partition as bait and personally rewrote every file and function involved since your code is *an actual crime against technology*. by the way i'm going to go ahead and format that partition i mentioned, boothill- we won't be needing anything on it now that we can trace whoever made it. trust me, this won't be happening ever again."
*(bricking is a term mostly used to refer to hardware that's been rendered basically completely nonfunctional and beyond saving by using it wrong, mostly by messing with system files. Kinda like how windows can't even repair itself if you delete the system32 folder. Though i guess you could still install it with a usb stick if you formatted your pc- i digress you get what I mean. also since this almost happened to me recently: if you manage to fill up a hard drive to the brim, with literally 0 bytes of space left, that bricks it. reminder to check your storage thoroughly and often!)
Honestly wow I read it all and I'm a little bit speechless 🥹 thank you 💫 anon, it was great 🙏

Boothill would DEFINITELY appreciate a s/o who's a tech savvy in general! I think at some point, he'd be pretty shocked you're so knowledgeable and just sit there, listening to you rant.. and just letting you do your thing.
Don't get me wrong, he definitely knows a lot about his body, his system and the way he works, but once you start to get in the zone and explain stuff to him, berate his code even, he just sits next to you, plugged in to your laptop, leaning his cheek against his hand listening to you like he obviously understands everything you say.
His other hand begins to gently play with a stand of your hair, humming deeply when the soft clicking sounds of your keyboard reach his ears; he twirls your hair with his fingers and chuckles, "mmm, really now?" Boothill raises an eyebrow, "encryptin' this, encryptin' that... How about we do somethin' more fun instead?" And then you shut him down from your laptop (😭).
Jokes aside, he'd feel very secure with you especially when he first got his new body, just knowing you'll probably fix a lot of things that could possibly blow up his face in no time, maybe even improve his life even more.
#honkai star rail#honkai star rail x reader#hsr x reader#boothill x reader#boothill hsr#boothill#.💫 anon#.anon thirst
245 notes
·
View notes
Note
Can you get a virus/malware by viewing a link, but not clicking on it?
short answer: no.
long answer: what you're talking about is a zero-click exploit, which is an attack that works without user interaction (such as clicking on a link). an example of a zero-click exploit is the 2013 FORCEDENTRY exploit, which involved sending someone a file disguised as a gif on iMessage, and when iMessage automatically processed this file to display the gif, it would compromise their device. (don't worry about that one, it's been fixed for a decade).
i'm assuming you're talking about being sent a link on a messenging service/social media/etc.? in general, if an attack involves sending you a link that you can see, then it probably depends on you clicking on the link. if you don't click on the link, it's very unlikely to be able to execute code.
zero-click exploits are thankfully pretty damn rare, and require a lot of technical knowledge to design; when they're found, they tend to be fixed urgently. but I should caveat this by saying I don't know every exploit that exists out there. there have been Discord zero-day exploits in the past (for example in 2022). the main defence against this is standard security stuff: keep your software up to date, make sure your device requires credentials to do admin shit, encrypt your passwords and don't reuse them, etc. etc.
if someone sent you a link to malware and you didn't click on it, don't worry about it too much, I wouldn't expect trouble.
114 notes
·
View notes