#Cyber Security Tools
Explore tagged Tumblr posts
Text
0 notes
Text
Cyber Crime Investigation in Cyber Security: A Practical Guide
The increasing reliance on digital systems and the internet has led to a surge in cybercrime. Criminal activities that exploit digital vulnerabilities are becoming more sophisticated and widespread. From identity theft to hacking, data breaches, and cyber extortion, cybercrime poses a significant threat to individuals, organizations, and governments worldwide. To combat these crimes,…
0 notes
Text
15 Best Free Resources for Malicious URLs and Phishing Links for Cybersecurity Testing
In today’s rapidly evolving cybersecurity landscape, having access to reliable sources of malicious URLs, phishing links, and malware samples is essential for security professionals, penetration testers, and IT administrators. Whether you’re validating your security controls, conducting security awareness training, or researching new threat vectors, accessing known malicious content in a…
#cyber threats#cybersecurity#ethical hacking#malicious URLs#malware analysis#malware samples#penetration testing#phishing detection#phishing links#security controls#security testing#security tools#security validation#threat intelligence#web security
2 notes
·
View notes
Text
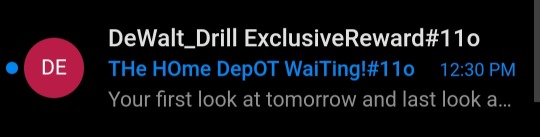
Only scam/phishing email I've received that ever perked my interest. You expect the fake malware software emails and the ones claiming to have videos of you beating your meat, but to impersonate a beloved tool company? 😭 that's low.

Honestly, I've always been more into Ryobi anyway--they may be lesser quality, but I like lime green better than Dewalt's yellow (or Milwaukee's red. Makita's odd teal is fine but they don't have as many tools.)
2 notes
·
View notes
Text
Idea for wholesome (IT) projectS for people with memory conditions (that is, everyone, since everyone is forgetful sometimes) | by Sansa Zet | Jun, 2024 | Medium
#endo safe#memory#cyber security#data security#password#creative#brainstorm#tools#diy projects#create#making#teamwork#leadership#innovation#strategy#intelligence#opportunities
2 notes
·
View notes
Text
Cybersecurity in the Age of AI: Navigating New Threats

Understanding AI-Driven Cyber Threats and Defense Strategies
Introduction: A New Cybersecurity Landscape in the Age of AI
Artificial Intelligence (AI) has revolutionized industries worldwide by enhancing efficiency, accuracy, and innovation. From automating routine tasks to enabling predictive analytics, AI continues to unlock unprecedented opportunities. However, as AI becomes deeply embedded in our digital ecosystems, it also reshapes the cybersecurity landscape bringing both powerful defenses and novel risks.
The rise of AI-driven cybersecurity tools is transforming how organizations detect, respond to, and prevent cyber threats. Machine learning algorithms can analyze massive datasets to identify unusual patterns, predict attacks, and automate defenses in real time. Yet, the same AI advancements also equip cybercriminals with sophisticated capabilities enabling automated phishing, intelligent malware, and adaptive intrusion techniques that are harder to detect and mitigate.
This dual-edged nature of AI demands a new approach to cyber threat intelligence, risk management, and security strategy. Organizations must stay vigilant and adopt innovative solutions to safeguard sensitive data and infrastructure against increasingly complex and automated cyberattacks.
For a deeper understanding of how AI is reshaping cybersecurity, check out NIST’s AI and Cybersecurity Framework.
How AI Is Changing Cybersecurity: Defense and Threat Evolution
Artificial Intelligence is revolutionizing cybersecurity by playing a dual role empowering defenders while enabling more sophisticated cyberattacks. On the defense front, AI-powered cybersecurity systems leverage machine learning and data analytics to process enormous volumes of network traffic, user activity, and threat intelligence in real time. These systems excel at detecting anomalies and predicting potential threats far faster and more accurately than traditional signature-based methods.
For example, AI-driven tools can identify subtle patterns indicative of phishing attacks, ransomware activity, or unusual network intrusions, often flagging risks before they escalate into full-blown breaches. Automated incident response capabilities enable rapid containment, minimizing damage and reducing reliance on manual intervention.
However, cybercriminals are equally quick to adopt AI technologies to enhance their offensive tactics. By using AI-generated content, hackers craft convincing phishing emails and social engineering schemes that trick users more effectively. AI can also be used to bypass biometric systems, automate vulnerability scanning, and mimic legitimate user behaviors to avoid detection by conventional security measures. This escalating “arms race” between attackers and defenders underscores the critical need for adaptive cybersecurity strategies.
To explore the evolving interplay between AI and cyber threats, consider reviewing insights from the Cybersecurity & Infrastructure Security Agency (CISA).
Emerging AI-Powered Threats: Deepfakes, Adaptive Malware, and Automated Attacks
The cybersecurity landscape faces increasingly sophisticated challenges due to the rise of AI-powered threats. Among the most alarming is the use of deepfakes hyper-realistic synthetic media generated by AI algorithms that can convincingly impersonate individuals. These deepfakes are weaponized for identity theft, social engineering schemes, or disinformation campaigns designed to manipulate public opinion or corporate decision-making. The growing prevalence of deepfakes adds a dangerous new dimension to phishing and fraud attempts.
In addition, AI-driven adaptive malware is evolving rapidly. Unlike traditional viruses, this malware can modify its code and behavior dynamically to evade signature-based antivirus software and intrusion detection systems. This makes infections more persistent and difficult to eradicate, posing a serious risk to personal, corporate, and government networks.
Furthermore, automated hacking tools powered by AI significantly accelerate cyberattacks. These intelligent systems can autonomously scan vast networks for vulnerabilities, execute targeted breaches, and learn from unsuccessful attempts to improve their strategies in real time. This capability enables hackers to conduct highly efficient, large-scale attacks that can quickly overwhelm human cybersecurity teams.
For more insights into the risks posed by AI-powered cyber threats and how to prepare, visit the National Institute of Standards and Technology (NIST).
Strengthening Cyber Defenses with AI: The Future of Cybersecurity
Despite the growing threat landscape driven by AI-powered attacks, artificial intelligence remains a crucial asset for cybersecurity defense. Cutting-edge security systems leverage AI technologies such as real-time threat intelligence, automated incident response, and predictive analytics to detect and neutralize cyber threats faster than ever before. By continuously analyzing vast amounts of data and learning from emerging attack patterns, AI enables organizations to anticipate and prevent breaches before they occur.
One of the most effective approaches is the integration of AI with human expertise, forming a hybrid defense model. In this setup, cybersecurity analysts harness AI-generated insights to make critical decisions, prioritize threats, and customize response strategies. This synergy balances the rapid detection capabilities of AI with the nuanced judgment of human operators, resulting in more accurate and adaptive cybersecurity posture.
Organizations that adopt AI-driven security platforms can significantly reduce response times, improve threat detection accuracy, and enhance overall resilience against sophisticated attacks.
For organizations seeking to implement AI-based cybersecurity solutions, resources like the Cybersecurity and Infrastructure Security Agency (CISA) offer valuable guidance and best practices.
Ethical and Privacy Considerations in AI-Driven Cybersecurity
As organizations increasingly integrate artificial intelligence in cybersecurity, important ethical and privacy concerns arise. The process of collecting and analyzing vast datasets to identify cyber threats must be carefully balanced with safeguarding user privacy rights and sensitive information. Maintaining transparency in AI decision-making processes is crucial to build trust and accountability. Clear regulatory frameworks, such as the General Data Protection Regulation (GDPR), provide guidelines that help organizations use AI responsibly while respecting individual privacy.
Additionally, organizations face risks associated with over-automation in cybersecurity. Relying solely on AI systems without sufficient human oversight can result in missed threats, false positives, or biased decision-making. These errors may lead to security vulnerabilities or negatively impact the user experience. Therefore, a balanced approach combining AI’s speed and scale with human judgment is essential for ethical, effective cybersecurity management.
By prioritizing ethical AI use and privacy protection, businesses can foster safer digital environments while complying with legal standards and maintaining customer confidence.
Preparing for the Future of AI and Cybersecurity
As artificial intelligence continues to transform the cybersecurity landscape, organizations must proactively prepare for emerging challenges and opportunities. Investing in continuous learning and regular employee cybersecurity training ensures teams stay equipped to handle evolving AI-powered threats. Developing flexible security architectures that seamlessly integrate AI-driven tools enables faster threat detection and response, improving overall resilience.
Collaboration across industries, governments, and academic researchers is critical for creating shared cybersecurity standards, real-time threat intelligence sharing, and innovative defense strategies. Initiatives like the Cybersecurity and Infrastructure Security Agency (CISA) promote such partnerships and provide valuable resources.
For individuals, maintaining strong cybersecurity hygiene using strong passwords, enabling multi-factor authentication (MFA), and practicing safe online behavior is more important than ever as attackers leverage AI to launch more sophisticated attacks.
By combining organizational preparedness with individual vigilance, we can build a safer digital future in an AI-driven world.
Conclusion: Embracing AI to Navigate the New Cybersecurity Threat Landscape
Artificial Intelligence is fundamentally reshaping the cybersecurity landscape, introducing both unprecedented opportunities and significant risks. While cybercriminals increasingly use AI-driven techniques to execute sophisticated and automated attacks, cybersecurity professionals can harness AI-powered tools to create smarter, faster, and more adaptive defense systems.
The key to success lies in adopting AI thoughtfully blending human expertise with intelligent automation, and maintaining continuous vigilance against emerging threats. Organizations that invest in AI-based threat detection, real-time incident response, and ongoing employee training will be better positioned to mitigate risks and protect sensitive data.
By staying informed about evolving AI-driven cyber threats and implementing proactive cybersecurity measures, businesses and individuals alike can confidently navigate this dynamic digital frontier.
For further insights on how AI is transforming cybersecurity, explore resources from the National Institute of Standards and Technology (NIST).
FAQs
How is AI changing the cybersecurity landscape? AI is transforming cybersecurity by enabling faster threat detection, real-time response, and predictive analytics. Traditional systems rely on static rules, but AI adapts to evolving threats using machine learning. It can scan vast datasets to identify anomalies, spot patterns, and neutralize potential attacks before they spread. However, AI is also used by hackers to automate attacks, create smarter malware, and evade detection. This dual-use nature makes cybersecurity both more effective and more complex in the AI era, demanding constant innovation from defenders and responsible governance around AI deployment.
What are the biggest AI-powered cybersecurity threats today? AI can be weaponized to launch sophisticated cyberattacks like automated phishing, deepfake impersonations, and AI-driven malware that adapts in real time. Hackers use AI to scan networks for vulnerabilities faster than humans can react. They also employ natural language models to craft realistic phishing emails that bypass traditional filters. Deepfakes and synthetic identities can fool biometric security systems. These AI-enhanced threats evolve quickly and require equally intelligent defense systems. The speed, scale, and realism enabled by AI make it one of the most significant cybersecurity challenges of this decade.
How does AI improve threat detection and response? AI boosts cybersecurity by analyzing massive volumes of network traffic, user behavior, and system logs to detect anomalies and threats in real time. It identifies unusual patterns like logins from strange locations or data spikes and flags them before they escalate into breaches. AI can also automate responses, isolating infected devices, updating firewalls, or sending alerts instantly. This proactive approach dramatically reduces reaction times and false positives. In large enterprises or cloud environments, where manual monitoring is nearly impossible, AI acts as a 24/7 digital watchdog.
Can AI prevent phishing and social engineering attacks? Yes, AI can help identify phishing attempts by scanning emails for suspicious language, links, or metadata. Natural language processing (NLP) models are trained to detect tone, urgency cues, or fake URLs often used in phishing. AI can also assess sender reputations and flag unusual communication patterns. While it can’t fully prevent human error, it significantly reduces exposure by quarantining suspicious emails and alerting users to risks. As phishing tactics evolve, so does AI constantly learning from past attacks to improve prevention accuracy.
Are AI-based cybersecurity tools available for small businesses? Absolutely. Many affordable, AI-powered security tools are now available for small and mid-sized businesses. These include smart antivirus software, behavior-based threat detection, AI-driven email filters, and endpoint protection platforms that learn from each user’s habits. Cloud-based solutions like Microsoft Defender, SentinelOne, and Sophos offer AI-powered features tailored for SMBs. They provide enterprise-grade security without the need for in-house security teams. With cyberattacks increasingly targeting smaller firms, AI-based solutions are not just accessible they’re essential for staying protected with limited resources.
Can AI replace cybersecurity professionals? AI enhances cybersecurity but won’t replace human experts. While it automates routine tasks like threat detection, data analysis, and basic response, human oversight is still crucial for judgment, strategy, and interpreting complex risks. Cybersecurity professionals work alongside AI to investigate incidents, fine-tune models, and ensure compliance. In fact, AI allows professionals to focus on high-level security architecture, incident response, and governance rather than tedious monitoring. The future lies in a human-AI partnership where AI handles scale and speed, and humans manage context and ethical oversight.
What are some ethical concerns with using AI in cybersecurity? Ethical concerns include data privacy, surveillance overreach, and algorithmic bias. AI systems require vast amounts of data, which can lead to privacy violations if not managed properly. There’s also the risk of false positives that could unjustly flag innocent users or systems. If left unchecked, AI could reinforce existing biases in threat detection or lead to disproportionate responses. Moreover, governments and companies may use AI tools for excessive surveillance. Responsible AI in cybersecurity means transparency, data governance, user consent, and fairness in decision-making.
How do hackers use AI to their advantage? Hackers use AI to create more sophisticated and scalable attacks. For instance, AI-powered bots can probe systems for weaknesses, bypass CAPTCHAs, and execute brute-force attacks faster than humans. NLP models are used to generate realistic phishing emails or impersonate voices using deepfakes. Machine learning helps malware adapt its behavior to avoid detection. These tools allow cybercriminals to attack with greater precision, volume, and deception making AI both a powerful ally and a formidable threat in the cybersecurity battlefield.
What is AI-driven threat hunting? AI-driven threat hunting involves proactively seeking out hidden cyber threats using machine learning and behavioral analytics. Instead of waiting for alerts, AI scans systems and networks for subtle anomalies that indicate intrusion attempts, dormant malware, or lateral movement. It uses predictive modeling to anticipate attack paths and simulate threat scenarios. This proactive approach reduces the risk of long-term undetected breaches. By continuously learning from new threats, AI enables security teams to shift from reactive defense to predictive offense, identifying threats before they do damage.
How can organizations prepare for AI-powered cyber threats? Organizations should invest in AI-powered defenses, regularly update their threat models, and train employees on AI-enhanced risks like deepfakes or phishing. Cybersecurity teams need to adopt adaptive, layered security strategies that include AI-based detection, behavioral monitoring, and automated response. It's also crucial to perform AI-specific risk assessments and stay informed about new threat vectors. Partnering with vendors that use explainable AI (XAI) helps ensure transparency. Finally, fostering a cyber-aware culture across the organization is key because even the smartest AI can’t protect against careless human behavior.
#AI cybersecurity threats#artificial intelligence in security#AI-driven cyber attacks#cybersecurity in AI age#AI-powered threat detection#digital security and AI#AI-based malware protection#evolving cyber threats AI#AI cyber defense tools#future of cybersecurity AI
0 notes
Text
AI and National Security: The New Battlefield
New Post has been published on https://thedigitalinsider.com/ai-and-national-security-the-new-battlefield/
AI and National Security: The New Battlefield


Artificial intelligence is changing how nations protect themselves. It has become essential for cybersecurity, weapon development, border control, and even public discourse. While it offers significant strategic benefits, it also introduces many risks. This article examines how AI is reshaping security, the current outcomes, and the challenging questions these new technologies raise.
Cybersecurity: A Fight of AI against AI
Most present‑day attacks start in cyberspace. Criminals no longer write every phishing email by hand. They use language models to draft messages that sound friendly and natural. In 2024, a gang used a deep-fake video of a chief financial officer stealing 25 million dollars from his own firm. The video looked so real that an employee followed the fake order without a doubt. Attackers now feed large language models with leaked resumes or LinkedIn data to craft personal bait. Some groups are even using generative AI to create software bugs or write malware snippets.
Defenders are also using AI to shield against these attacks. Security teams feed network logs, user clicks, and global threat reports into AI tools. The software learns “normal” activity and warns when something suspicious happens. When an intrusion is detected, AI systems disconnect a suspected computer to limit damage that would spread if humans reacted slower.
Autonomous Weapons
AI also steps onto physical battlefields. In Ukraine, drones use onboard vision to find fuel trucks or radar sites before they explode. The U.S. has used AI to help identify targets for airstrikes in places like Syria. Israel’s army recently used an AI target‑selection platform to sort thousands of aerial images to mark potential militant hideouts. China, Russia, Turkey, and the U.K. have tested “loitering munitions” that circle an area until AI spots a target. These technologies can make military operations more precise and reduce risks for soldiers. But they also bring serious concerns. Who is responsible when an algorithm chooses the wrong target? Some experts fear “flash wars” where machines react too quickly for diplomats to stop them. Many experts are calling for international rules to control autonomous weapons, but states fear falling behind if they pause.
Surveillance and Intelligence
Intelligence services once relied on teams of analysts to read reports or watch video feeds. Today they rely on AI to sift millions of images and messages each hour. In some countries, like China, AI tracks citizens’ behavior, from small things like jaywalking to what they do online. Similarly, on the U.S.–Mexico border, solar towers with cameras and thermal sensors scan empty desert. The AI spots a moving figure, labels it human or animal, then alerts patrol agents. This “virtual wall” covers wide ground that humans could never watch alone.
While these tools extend coverage, they also magnify errors. Face‑recognition systems have been shown to misidentify women and people with darker skin at higher rates than white men. A single false match may cause an innocent person to face extra checks or detention. Policymakers ask for audited algorithms, clear appeal paths, and human review before any strong action.
Information Warfare
Modern conflicts are fought not only with missiles and code but also with narratives. In March 2024 a fake video showed Ukraine’s president ordering soldiers to surrender; it spread online before fact‑checkers debunked it. During the 2023 Israel–Hamas fighting, AI‑generated fakes favoring one side’s policies flooded social streams, in order to tilt opinion.
False information spreads faster than governments can correct it. This is especially problematic during elections, where AI-generated content is often used to sway voters. Voters find it difficult to distinguish between real and AI-generated images or videos. While governments and tech firms are working on counter‑AI projects to scan the digital fingerprints of AI but the race is tight; creators improve their fakes just as fast as defenders improve their filters.
Decision Support
Armies and agencies collect vast amounts of data including hours of drone video, maintenance logs, satellite imagery, and open‑source reports. AI helps by sorting and highlighting relevant information. NATO recently adopted a system inspired by the U.S. Project Maven. It links databases from 30 member states, providing planners with a unified view. The system suggests likely enemy movements and identifies potential supply shortages. The U.S. Special Operations Command uses AI to help draft parts of its annual budget by scanning invoices and recommending reallocations. Similar AI platforms predict engine failures, schedule repairs in advance, and customize flight simulations for individual pilots’ needs.
Law Enforcement and Border Control
Police forces and immigration officers are using AI for tasks that require constant attention. At busy airports, biometric kiosks confirm identities of travelers to make the process more efficient. Pattern-analysis software picks out travel records that hint at human trafficking or drug smuggling. In 2024, one European partnership used such tools to uncover a ring moving migrants through cargo ships. These tools can make borders safer and help catch criminals. But there are concerns too. Facial recognition sometimes fails for certain classes of people with low representation, which could lead to mistakes. Privacy is another issue. The key question is whether AI should be used to monitor everyone so closely.
The Bottom Line
AI is changing national security in many ways, offering both opportunities and risks. It can protect countries from cyber threats, make military operations more precise, and improve decision-making. But it can also spread lies, invade privacy, or make deadly errors. As AI becomes more common in security, we need to find a balance between using its power for good and controlling its dangers. This means countries must work together and set clear rules for how AI can be used. In the end, AI is a tool, and how we use it will redefine the future of security. We must be careful to use it wisely, so it helps us more than it harms us.
#2023#2024#agents#ai#AI Cyber Security#AI in defense strategies#AI in national security#AI platforms#ai surveillance#AI systems#ai tools#ai-generated content#alerts#algorithm#Algorithms#Analysis#Article#artificial#Artificial Intelligence#attackers#attention#autonomous#autonomous weapons#Behavior#biometric#border#borders#bugs#Cameras#China
0 notes
Text
The Role of Generative AI in Cybersecurity: Enhancing Protection in a Threat-Filled Digital World
Generative AI in cybersecurity is transforming real-time threat detection, enhancing protection, and ensuring smarter defense for global digital systems Generative AI in cybersecurity has emerged as a powerful force, redefining how companies detect, prevent, and respond to digital threats globally. Visit more Understanding Generative AI’s Impact on Cybersecurity Generative AI in cybersecurity…
#ai#AI Security Tools#cyber-security#Cybersecurity#generative AI#security#technology#Threat Detection#USA Cybersecurity Trends
0 notes
Text
Unmasking Cyber Threats: The Power of Digital Forensics & Incident Response.
Sanjay Kumar Mohindroo Sanjay Kumar Mohindroo. skm.stayingalive.in An in-depth look at digital forensics and incident response, exploring tools, techniques, and clear strategies to tackle cyber breaches and analyze digital evidence. This post explores digital forensics and incident response with clear steps and real examples that spark discussion. We break down techniques, introduce simple yet…
#Clear Response#Cyber Breaches#Cyber Security#Data Recovery#Digital Evidence#Digital Forensics#Forensic Tools#Incident Response#IT Security#News#Sanjay Kumar Mohindroo
0 notes
Text
How to Develop a Personal Data Security Plan
In 2025, your data is more valuable than gold—and sadly, just as many people want to steal it. Whether you’re a freelancer, remote worker, business owner, or regular online user, having a personal data security plan is no longer optional—it’s essential. This guide will show you, step by step, how to take control of your digital privacy and protect yourself from identity theft, hacking, and online…
0 notes
Text
Website: https://www.turacolabs.com/
Address: 31a Charnham Street, Hungerford, Berkshire, RG17 0EJ, United Kingdom
Turaco Labs specializes in eCommerce cybersecurity, offering ThreatView, a state-of-the-art cyber threat detection and PCI DSS compliance monitoring solution. Their services focus on protecting online businesses from malware, digital skimmers, loaders, and data theft. With a free security scan, breach protection warranty, and forensic-level monitoring, they provide a proactive defense system for online stores using platforms such as Magento, WordPress, OpenCart, and Joomla. Their ThreatView solution ensures continuous monitoring, detects the latest cybersecurity threats, and helps eCommerce merchants comply with PCI DSS standards.
LinkedIn: https://www.linkedin.com/company/turaco-labs-threatview/
Keywords: eCommerce cyber security website malware scan scan website for malware PCI compliance monitoring free website security scan website security monitoring website compliance audit security services website website malware scanning tools eCommerce security solutions eCommerce fraud prevention ecommerce fraud prevention companies prevent ecommerce fraud website malware scanner PCI compliance services pci compliance service provider pci compliance consulting services cybersecurity services for small businesses Magecart protection Google Tag Manager malware hacked website recovery eCommerce security best practices website security services malware removal from weebly website website malware removal website malware removal service how do i remove malware from my website how to remove malware from website how to remove malware from wordpress website malware removal for websites malware removal website remove malware from website best website malware removal how to remove virus from website website protection services best website protection service website malware protection services ecommerce fraud protection services
#eCommerce cyber security#website malware scan#scan website for malware#PCI compliance monitoring#free website security scan#website security monitoring#website compliance audit#security services website#website malware scanning tools#eCommerce security solutions#eCommerce fraud prevention#ecommerce fraud prevention companies#prevent ecommerce fraud#website malware scanner
1 note
·
View note
Text
0 notes
Text
AI Tools in Cybersecurity: Enhancing Protection with Artificial Intelligence
In today’s rapidly evolving digital landscape, cybersecurity has become a critical priority for businesses and individuals alike. With an increase in cyber-attacks, data breaches, and sophisticated threats, traditional security systems alone are no longer sufficient to protect sensitive information and digital infrastructure. To tackle these challenges, many organizations are turning to…
#ai for threats detection#ai in cyber security#ai tools for threat intelligence#ai tools guide for cyber security#top ai tools for cyber security
0 notes
Text
Microsoft 365 Business Apps deliver versatile tools to help organizations streamline operations and improve productivity. When combined with IT managed services in Lanham, Maryland, businesses gain support for seamless Microsoft 365 integration and reliable day-to-day management. Core apps like Outlook, Word, and Excel keep essential tasks organized, while cloud services make document sharing, scheduling, and collaboration more accessible and secure.
0 notes
Text
What Are Top 3 Vulnerability Management Metrics to Measure in 2025
In today’s rapidly evolving cybersecurity landscape, staying ahead of potential threats is essential. Companies face a relentless onslaught of security vulnerabilities, and effectively managing these vulnerabilities has become critical for safeguarding data and maintaining regulatory compliance. One of the primary methods to assess the security posture of any organization is through vulnerability management and penetration testing. In 2024, certain key metrics have emerged as essential for effectively managing vulnerabilities, aiding businesses in minimizing risks while optimizing their security strategy.

This article will explore the top three vulnerability management metrics to measure in 2024, focusing on their significance in shaping a robust security program, and highlighting how penetration testing plays an integral role.
1. Vulnerability Detection Rate
The Vulnerability Detection Rate is a metric that reflects how effectively your organization identifies security vulnerabilities within its IT infrastructure. A higher detection rate indicates that the organization has robust tools and processes in place for continuous monitoring and assessment, which is crucial for early-stage vulnerability management.
Why It Matters: In 2024, the growing sophistication of cyber threats makes the Vulnerability Detection Rate a key performance indicator (KPI) for cybersecurity teams. An accurate and high detection rate allows teams to discover potential vulnerabilities before they are exploited. It also helps organizations quantify the effectiveness of their scanning tools, Vulnerability Scanning protocols, and penetration testing procedures.
How to Measure It: The Vulnerability Detection Rate is typically calculated by dividing the number of detected vulnerabilities by the total vulnerabilities present, which can be estimated based on past data and testing results. Organizations should strive for real-time detection capabilities using tools that integrate vulnerability management with penetration testing solutions. This hybrid approach allows for both automated and manual detection of weaknesses across endpoints, applications, and networks.
Penetration Testing's Role: Penetration testing acts as a simulated attack on the system, testing the detection capabilities of an organization. Conducting regular penetration tests helps verify that vulnerabilities are detected accurately and promptly, which can reveal any gaps in detection mechanisms. A comprehensive penetration test offers insights into vulnerabilities that automated tools may overlook, helping cybersecurity teams to refine their detection tools and strategies.
2. Mean Time to Remediation (MTTR)
Mean Time to Remediation (MTTR) is a crucial metric for understanding the efficiency of an organization’s response to identified vulnerabilities. MTTR calculates the average time taken to fix a vulnerability after its detection. Keeping this metric low is essential for preventing the exploitation of vulnerabilities and ensuring that identified threats do not remain in the system long enough to cause harm.
Why It Matters: The faster an organization remediates a vulnerability, the less time attackers have to exploit it. With the increasing rate of zero-day vulnerabilities in 2024, cybersecurity teams must act quickly once vulnerabilities are identified. A short MTTR not only indicates an agile response capability but also helps in meeting regulatory requirements and reducing potential financial or reputational damage.
How to Measure It: To measure MTTR, calculate the time between when a vulnerability is identified and when it is resolved. Divide the total remediation time across all vulnerabilities by the number of resolved vulnerabilities within a specific timeframe. It is best practice to track MTTR by severity level (e.g., high, medium, low), as high-risk vulnerabilities should generally have a shorter MTTR than low-risk ones.
Penetration Testing's Role: Penetration testing supports MTTR by identifying specific weaknesses in systems and applications, thereby guiding prioritized remediation efforts. It helps highlight vulnerabilities that pose the greatest risk, allowing teams to allocate resources effectively and improve response times. When Penetration Testing is conducted regularly, it can also reveal recurring vulnerabilities, helping teams streamline their remediation processes and reduce MTTR.
3. Vulnerability Reopen Rate
The Vulnerability Reopen Rate metric measures the frequency at which previously remediated vulnerabilities reappear, indicating that previous fixes may have been insufficient or temporary. A high reopen rate suggests that there are issues within the patch management or remediation processes, or that vulnerabilities have returned due to configuration changes, software updates, or inadequate fixes.
Why It Matters: In 2024, complex infrastructures and third-party dependencies mean that vulnerabilities can recur due to software updates or overlooked configurations. A high Vulnerability Reopen Rate can indicate a need for improved patching practices, better configuration management, or more thorough penetration testing to verify that vulnerabilities are completely resolved. Reducing the reopen rate not only boosts security posture but also conserves resources by minimizing repetitive work for security teams.
How to Measure It: Calculate the Vulnerability Reopen Rate by dividing the number of vulnerabilities that have reappeared after initial remediation by the total number of vulnerabilities resolved over a given period. Tracking this metric over time helps organizations understand the consistency and effectiveness of their remediation efforts.
Penetration Testing's Role: Penetration testing is critical in validating that vulnerabilities have been properly remediated. After a vulnerability is patched or mitigated, conducting a follow-up penetration test ensures that the issue has been fully addressed. This practice not only helps to keep the Vulnerability Reopen Rate low but also verifies that patches have not inadvertently created new vulnerabilities. Regular penetration tests are instrumental in keeping this metric under control by providing an extra layer of verification and reducing the chances of vulnerability reoccurrence.
The Role of Penetration Testing in Vulnerability Management Metrics
Incorporating penetration testing into vulnerability management goes beyond simply identifying security gaps; it enhances the entire vulnerability management process. Penetration testing, when conducted consistently, provides a real-world perspective on the security posture of an organization, helping cybersecurity teams to accurately assess and improve each metric. Here’s how:
Improving Detection Accuracy: Penetration testing helps assess the accuracy and coverage of detection tools, enabling organizations to fine-tune their scanning and monitoring systems.
Prioritizing Remediation Efforts: By highlighting high-risk vulnerabilities, penetration tests help in prioritizing and reducing MTTR, as they show which areas need immediate attention and streamline the remediation process.
Ensuring Lasting Remediation: Penetration testing verifies that vulnerabilities have been remediated effectively, which in turn helps in maintaining a low Vulnerability Reopen Rate.
Conclusion
In 2024, vulnerability management metrics like Vulnerability Detection Rate, Mean Time to Remediation (MTTR), and Vulnerability Reopen Rate will be pivotal in measuring and improving an organization’s cybersecurity resilience. Penetration testing plays an indispensable role in supporting these metrics, offering a comprehensive approach to identifying, prioritizing, and validating remediation efforts. By focusing on these metrics and integrating regular penetration testing, organizations can bolster their security posture and reduce their risk of cyber-attacks. Emphasizing these metrics helps companies build a proactive and effective vulnerability management strategy, making 2024 a year of fortified defenses against an evolving threat landscape.
#Vulnerability management metrics#Penetration testing#Cybersecurity resilience#Vulnerability Detection Rate#Mean Time to Remediation (MTTR)#Vulnerability Reopen Rate#Cyber threats#Vulnerability scanning tools#Security posture#IT infrastructure vulnerabilities
0 notes
Text
1 note
·
View note