#Database Data Entry Companies
Explore tagged Tumblr posts
Text
Learn More About Outsourcing Database Data Entry Services

Database data entry services play a vital role in maintaining accurate and well-organized information, enabling businesses to make informed decisions and streamline their operations. Outsourcing database data entry can be cost-effective as it allows businesses to leverage the expertise of specialized service providers. Professional database data entry outsourcing company can often complete tasks more quickly due to their specialized skills, experience, and efficient processes. This blog gives you more knowledge about outsourcing database data entry services.
To know more visit https://latestbpoblog.blogspot.com/2024/02/learn-more-about-outsourcing-database-data-entry-services.html
#Database Data Entry#Database Data Entry Services#Database Data Entry Companies#Outsource Database Data Entry#Professional Database Data Entry#Bulk Database Data Entry
0 notes
Text
i wish people who program their web apps entirely in javascript a very die
#im fighting for my life in here#what do you meeeaaaaan i cant open this up in a diff tab#also i dont want to deal with a million interfaces#the natural enemy of sysengs and database engs is webdevs i can tell u that#why not have everything in one place simple#but i think the real enemy is the data entry people who couldnt be bothered to enter the right company name#milk (normal)
6 notes
·
View notes
Text

dave whammond
* * * *
Shocking disclosures regarding a data breach at the National Labor Relations Board suggest illegal conduct by DOGE members
Over the weekend, NPR published a lengthy story about a potential major data breach at the National Labor Relations Board. At first blush, the story sounds like it is in 45th place on the list of the most horrible things that Trump and DOGE have done in the first 86 days of his administration.
But you must pay attention to this story. It is a national scandal that suggests DOGE has intentionally exposed confidential US government information to foreign adversaries.
I will give a very brief summary, but urge you to read, listen to, or watch one of the sources I cite below.
In short, a whistleblower from the National Labor Relations Board (NLRB) claims the following:
DOGE gained access to the NLRB's most sensitive information, which included labor complaints, identity of whistleblowers, identity of private employees engaged in union organizing, and enforcement actions against private companies (like Tesla and SpaceX).
DOGE turned off log files that would record their actions.
DOGE set up a “black box” inside the NLRB network so that NLRB IT personnel could not monitor what was happening.
DOGE disabled security protections, thereby exposing the NLRB’s sensitive information to the internet.
Within 15 minutes of the firewall protections being disabled, someone using an IP address in Russia used a username and password for a DOGE team member to attempt to access the NLRB information.
NLRB IT members witnessed a massive spike in information being downloaded from the NLRB servers.
A DOGE team member set up a file that was briefly visible on a public forum; the filename suggested that it was a “backdoor” download program for an NLRB-specific database.
The NLRB IT staff asked the federal Cybersecurity and Infrastructure Security Agency (CISA) security team to help launch an investigation, but the CISA investigation was peremptorily shut down without explanation.
The employee who asked CISA to begin the investigation received a typed note on his residence door which warned the employee to drop the request for CISA assistance and included personal details about the employee known only from government files. The note also included a drone photo of the employee walking his dog on a public street.
A spokesperson for the NLRB issued a statement claiming that DOGE never visited the NLRB and did not gain access to NLRB data—a statement that seems to a blatant, easily disprovable lie.
I have not done justice to the details of the story. There are three ways you can educate yourself about this story.
First, the lengthy NPR article is here: NPR, Whistleblower details how DOGE may have taken sensitive NLRB data.
Second, the NPR report has a seven-minute audio summary embedded in the article. It is an accessible entry point into the article.
Finally, Rachel Maddow did an excellent job of explaining the whistleblower allegations on Tuesday evening. I have excerpted the 20-minute segment of her show that includes an interview with the whistleblower and his attorney. See The Rachel Maddow Show, Whistleblower Excerpt, April 15, 2025.
As a personal favor to me (and you), I urge you to watch the Rachel Maddow segment. It will bring you up to speed on this scandal, which will be around for a long time and may be the undoing of DOGE.
If you watch the Rachel Maddow show, you will meet the whistleblower--Daniel Berulis—who is a loyal employee of the federal government who says that he “hopes he is wrong” in believing that DOGE exposed sensitive information to someone in Russia who was using a DOGE username and password.
At this very moment, there are hundreds or thousands of Daniel Berulises in the federal government who have not come forward. Daniel Berulis’s example should encourage them to come forward to describe other instances of DOGE misconduct or carelessness that may have harmed America’s interests.
If Berulis’s allegations are true, it is difficult to see how the conduct by at least one DOGE member does not rise to the level of a felony. We need to know more and must be open to the facts, including denials of the allegations. But the allegations are truly shocking and suggest that DOGE may have inflicted grievous injury on the US by exposing confidential information.
CODA: As shocking as the above allegations are, we have reasonable grounds for believing misconduct by Trump administration officials in seeking to conceal their unlawful actions.
Remember Signalgate? You may recall that CIA Director John Ratcliffe participated in chats on an non-secure commercial application. Congress has asked that all such communications be turned over for review.
Well, it might not shock you to learn that the CIA’s information technology team has informed Congress that none of John Ratcliff’s communications on Signal are recoverable. See MSNBC, Missing Signal messages from CIA director’s phone raise cover-up concerns.
Remember after the January 6 insurrection when most of the Secret Service’s texts were mysteriously deleted and therefore unavailable for review by the January 6 Committee? See PBS News, Government watchdog says Secret Service agents deleted Jan. 6 text messages.
Once is a mistake. Twice is a suspicious coincidence. Three times is a damning pattern. Secret Service. Signalgate. DOGE. It appears that actors within the Trump administration believe that destroying communications is an acceptable way to avoid accountability. It is up to Congress and the courts to get to the bottom of the DOGE NLRB incident and Signalgate as quickly as possible—before more evidence goes missing.
[Robert B. Hubbell Newsletter]
#Robert B. Hubbell#Robert B. Hubbell Newsletter#MSNBC#Rachel Maddow#DOGE#coverup#Signalgate#National Labor Relations Board#foreign adversaries
58 notes
·
View notes
Text
"In the age of smart fridges, connected egg crates, and casino fish tanks doubling as entry points for hackers, it shouldn’t come as a surprise that sex toys have joined the Internet of Things (IoT) party.
But not all parties are fun, and this one comes with a hefty dose of risk: data breaches, psychological harm, and even physical danger.
Let’s dig into why your Bluetooth-enabled intimacy gadget might be your most vulnerable possession — and not in the way you think.
The lure of remote-controlled intimacy gadgets isn’t hard to understand. Whether you’re in a long-distance relationship or just like the convenience, these devices have taken the market by storm.
According to a 2023 study commissioned by the U.K.’s Department for Science, Innovation, and Technology (DSIT), these toys are some of the most vulnerable consumer IoT products.
And while a vibrating smart egg or a remotely controlled chastity belt might sound futuristic, the risks involved are decidedly dystopian.
Forbes’ Davey Winder flagged the issue four years ago when hackers locked users into a chastity device, demanding a ransom to unlock it.
Fast forward to now, and the warnings are louder than ever. Researchers led by Dr. Mark Cote found multiple vulnerabilities in these devices, primarily those relying on Bluetooth connectivity.
Alarmingly, many of these connections lack encryption, leaving the door wide open for malicious third parties.
If you’re picturing some low-stakes prank involving vibrating gadgets going haywire, think again. The risks are far graver.
According to the DSIT report, hackers could potentially inflict physical harm by overheating a device or locking it indefinitely. Meanwhile, the psychological harm could stem from sensitive data — yes, that kind of data — being exposed or exploited.
A TechCrunch exposé revealed that a security researcher breached a chastity device’s database containing over 10,000 users’ information. That was back in June, and the manufacturer still hasn’t addressed the issue.
In another incident, users of the CellMate connected chastity belt reported hackers demanding $750 in bitcoin to unlock devices. Fortunately, one man who spoke to Vice hadn’t been wearing his when the attack happened. Small mercies, right?
These aren’t isolated events. Standard Innovation Corp., the maker of the We-Vibe toy, settled for $3.75 million in 2017 after it was discovered the device was collecting intimate data without user consent.
A sex toy with a camera was hacked the same year, granting outsiders access to its live feed.
And let’s not forget: IoT toys are multiplying faster than anyone can track, with websites like Internet of Dongs monitoring the surge.
If the thought of a connected chastity belt being hacked makes you uneasy, consider this: sex toys are just a small piece of the IoT puzzle.
There are an estimated 17 billion connected devices worldwide, ranging from light bulbs to fitness trackers — and, oddly, smart egg crates.
Yet, as Microsoft’s 2022 Digital Defense Report points out, IoT security is lagging far behind its software and hardware counterparts.
Hackers are opportunistic. If there’s a way in, they’ll find it. Case in point: a casino lost sensitive customer data after bad actors accessed its network through smart sensors in a fish tank.
If a fish tank isn’t safe, why would we expect a vibrating gadget to be?
Here’s where the frustration kicks in: these vulnerabilities are preventable.
The DSIT report notes that many devices rely on unencrypted Bluetooth connections or insecure APIs for remote control functionality.
Fixing these flaws is well within the reach of manufacturers, yet companies routinely fail to prioritize security.
Even basic transparency around data collection would be a step in the right direction. Users deserve to know what’s being collected, why, and how it’s protected. But history suggests the industry is reluctant to step up.
After all, if companies like Standard Innovation can get away with quietly siphoning off user data, why would smaller players bother to invest in robust security?
So, what’s a smart-toy enthusiast to do? First, ask yourself: do you really need your device to be connected to an app?
If the answer is no, then maybe it’s best to go old school. If remote connectivity is a must, take some precautions.
Keep software updated: Ensure both the device firmware and your phone’s app are running the latest versions. Updates often include critical security patches.
Use secure passwords: Avoid default settings and choose strong, unique passwords for apps controlling your devices.
Limit app permissions: Only grant the app the bare minimum of permissions needed for functionality.
Vet the manufacturer: Research whether the company has a history of addressing security flaws. If they’ve been caught slacking before, it’s a red flag.
The conversation around sex toy hacking isn’t just about awkward headlines — it’s about how we navigate a world increasingly dependent on connected technology. As devices creep further into every corner of our lives, from the bedroom to the kitchen, the stakes for privacy and security continue to rise.
And let’s face it: there’s something uniquely unsettling about hackers turning moments of intimacy into opportunities for exploitation.
If companies won’t take responsibility for protecting users, then consumers need to start asking tough questions — and maybe think twice before connecting their pleasure devices to the internet.
As for the manufacturers? The message is simple: step up or step aside.
No one wants to be the next headline in a tale of hacked chastity belts and hijacked intimacy. And if you think that’s funny, just wait until your light bulb sells your Wi-Fi password.
This is where IoT meets TMI. Stay connected, but stay safe."
https://thartribune.com/government-warns-couples-that-sex-toys-remain-a-tempting-target-for-hackers-with-the-potential-to-be-weaponized/
#iot#I only want non-smart devices#I don't want my toilet to connect to the internet#seriously#smart devices#ai#anti ai#enshittification#smart sex toys
26 notes
·
View notes
Text
The flood of text messages started arriving early this year. They carried a similar thrust: The United States Postal Service is trying to deliver a parcel but needs more details, including your credit card number. All the messages pointed to websites where the information could be entered.
Like thousands of others, security researcher Grant Smith got a USPS package message. Many of his friends had received similar texts. A couple of days earlier, he says, his wife called him and said she’d inadvertently entered her credit card details. With little going on after the holidays, Smith began a mission: Hunt down the scammers.
Over the course of a few weeks, Smith tracked down the Chinese-language group behind the mass-smishing campaign, hacked into their systems, collected evidence of their activities, and started a months-long process of gathering victim data and handing it to USPS investigators and a US bank, allowing people’s cards to be protected from fraudulent activity.
In total, people entered 438,669 unique credit cards into 1,133 domains used by the scammers, says Smith, a red team engineer and the founder of offensive cybersecurity firm Phantom Security. Many people entered multiple cards each, he says. More than 50,000 email addresses were logged, including hundreds of university email addresses and 20 military or government email domains. The victims were spread across the United States—California, the state with the most, had 141,000 entries—with more than 1.2 million pieces of information being entered in total.
“This shows the mass scale of the problem,” says Smith, who is presenting his findings at the Defcon security conference this weekend and previously published some details of the work. But the scale of the scamming is likely to be much larger, Smith says, as he didn't manage to track down all of the fraudulent USPS websites, and the group behind the efforts have been linked to similar scams in at least half a dozen other countries.
Gone Phishing
Chasing down the group didn’t take long. Smith started investigating the smishing text message he received by the dodgy domain and intercepting traffic from the website. A path traversal vulnerability, coupled with a SQL injection, he says, allowed him to grab files from the website’s server and read data from the database being used.
“I thought there was just one standard site that they all were using,” Smith says. Diving into the data from that initial website, he found the name of a Chinese-language Telegram account and channel, which appeared to be selling a smishing kit scammers could use to easily create the fake websites.
Details of the Telegram username were previously published by cybersecurity company Resecurity, which calls the scammers the “Smishing Triad.” The company had previously found a separate SQL injection in the group’s smishing kits and provided Smith with a copy of the tool. (The Smishing Triad had fixed the previous flaw and started encrypting data, Smith says.)
“I started reverse engineering it, figured out how everything was being encrypted, how I could decrypt it, and figured out a more efficient way of grabbing the data,” Smith says. From there, he says, he was able to break administrator passwords on the websites—many had not been changed from the default “admin” username and “123456” password—and began pulling victim data from the network of smishing websites in a faster, automated way.
Smith trawled Reddit and other online sources to find people reporting the scam and the URLs being used, which he subsequently published. Some of the websites running the Smishing Triad’s tools were collecting thousands of people’s personal information per day, Smith says. Among other details, the websites would request people’s names, addresses, payment card numbers and security codes, phone numbers, dates of birth, and bank websites. This level of information can allow a scammer to make purchases online with the credit cards. Smith says his wife quickly canceled her card, but noticed that the scammers still tried to use it, for instance, with Uber. The researcher says he would collect data from a website and return to it a few hours later, only to find hundreds of new records.
The researcher provided the details to a bank that had contacted him after seeing his initial blog posts. Smith declined to name the bank. He also reported the incidents to the FBI and later provided information to the United States Postal Inspection Service (USPIS).
Michael Martel, a national public information officer at USPIS, says the information provided by Smith is being used as part of an ongoing USPIS investigation and that the agency cannot comment on specific details. “USPIS is already actively pursuing this type of information to protect the American people, identify victims, and serve justice to the malicious actors behind it all,” Martel says, pointing to advice on spotting and reporting USPS package delivery scams.
Initially, Smith says, he was wary about going public with his research, as this kind of “hacking back” falls into a “gray area”: It may be breaking the Computer Fraud and Abuse Act, a sweeping US computer-crimes law, but he’s doing it against foreign-based criminals. Something he is definitely not the first, or last, to do.
Multiple Prongs
The Smishing Triad is prolific. In addition to using postal services as lures for their scams, the Chinese-speaking group has targeted online banking, ecommerce, and payment systems in the US, Europe, India, Pakistan, and the United Arab Emirates, according to Shawn Loveland, the chief operating officer of Resecurity, which has consistently tracked the group.
The Smishing Triad sends between 50,000 and 100,000 messages daily, according to Resecurity’s research. Its scam messages are sent using SMS or Apple’s iMessage, the latter being encrypted. Loveland says the Triad is made up of two distinct groups—a small team led by one Chinese hacker that creates, sells, and maintains the smishing kit, and a second group of people who buy the scamming tool. (A backdoor in the kit allows the creator to access details of administrators using the kit, Smith says in a blog post.)
“It’s very mature,” Loveland says of the operation. The group sells the scamming kit on Telegram for a $200-per month subscription, and this can be customized to show the organization the scammers are trying to impersonate. “The main actor is Chinese communicating in the Chinese language,” Loveland says. “They do not appear to be hacking Chinese language websites or users.” (In communications with the main contact on Telegram, the individual claimed to Smith that they were a computer science student.)
The relatively low monthly subscription cost for the smishing kit means it’s highly likely, with the number of credit card details scammers are collecting, that those using it are making significant profits. Loveland says using text messages that immediately send people a notification is a more direct and more successful way of phishing, compared to sending emails with malicious links included.
As a result, smishing has been on the rise in recent years. But there are some tell-tale signs: If you receive a message from a number or email you don't recognize, if it contains a link to click on, or if it wants you to do something urgently, you should be suspicious.
30 notes
·
View notes
Text
Caleb Ecarma and Judd Legum at Popular Information:
Several of Elon Musk’s associates installed at the Office of Personnel Management (OPM) have received unprecedented access to federal human resources databases containing sensitive personal information for millions of federal employees. According to two members of OPM staff with direct knowledge, the Musk team running OPM has the ability to extract information from databases that store medical histories, personally identifiable information, workplace evaluations, and other private data. The staffers spoke on the condition of anonymity because they were not authorized to speak publicly and feared professional retaliation. Musk Watch also reviewed internal OPM correspondence confirming that expansive access to the database was provided to Musk associates.
The arrangement presents acute privacy and security risks, one of the OPM staffers said. Among the government outsiders granted entry to the OPM databases is University of California Berkeley student Akash Bobba, a software engineer who graduated high school less than three years ago. He previously interned at Meta and Palantir, a technology firm chaired by Musk-ally and fellow billionaire Peter Thiel. Edward Coristine, another 2022 high school graduate and former software engineering intern at Musk’s Neuralink, has also been given access to the databases.
Other Musk underlings embedded at OPM following President Donald Trump’s inauguration include the agency’s new chief of staff, Amanda Scales, who until January was a human resources staffer at xAI, Musk’s artificial intelligence firm, and Brian Bjelde, who has spent the past 21 years at Musk's SpaceX, including the last 10 leading the human resources department. They are joined by Gavin Kliger, a former Twitter software engineer serving as a special advisor to the director of OPM, and Riccardo Biasini, a former software engineer at Musk’s tunneling venture, the Boring Company. OPM did not respond to a request for comment. Shortly after Trump took office, OPM installed Greg Hogan to serve as its new chief information officer (CIO). Hogan was tapped to replace OPM CIO Melvin Brown, who had accepted the job less than a month ago. The civil servants who oversee the OPM’s information technology services were then instructed to provide access to Musk's associates, according to the OPM staffers who spoke to Musk Watch. One of the OPM staffers received an email from the agency’s new leadership instructing them to give Musk’s team “access [to] the system as an admin user" and "code read and write permissions." “They have access to the code itself, which means they can make updates to anything that they want,” the staffer explained. USAJOBS, the federal government’s official hiring site, was one of the systems that Musk's associates were given access to. The database stores personal information — Social Security numbers, home addresses, employment records — provided by private individuals who have applied for federal jobs, regardless of whether the applicants went on to work for the government. Musk’s aides were also given access to the OPM’s Enterprise Human Resources Integration (EHRI) system. Contained within the EHRI are the Social Security numbers, dates of birth, salaries, home addresses, and job descriptions of all civil government workers, along with any disciplinary actions they have faced. “They’re looking through all the position descriptions… to remove folks,” one of the OPM staffers said of Musk’s team. “This is how they found all these DEI offices and had them removed — [by] reviewing position description level data.” Other databases Musk’s team has access to include USA Staffing, an onboarding system; USA Performance, a job performance review site; and HI, which the government uses to manage employee health care. “The health insurance one scares me because it's HIPAA [protected] information, but they have access to all this stuff,” the OPM staffer noted.
[...] A new server being used to control these databases has been placed in a conference room that Musk’s team is using as their command center, according to an OPM staffer. The staffer described the server as a piece of commercial hardware they believed was not obtained through the proper federal procurement process. There is a legal requirement that the installation of a new server undergo a Privacy Impact Assessment (PIA), a formal process to ensure the change would not create any security vulnerabilities. But in this instance, the staff believes there was no PIA. “So this application and corresponding hardware are illegally operating,” they added. On Friday, Reuters reported that some senior civil servants have been blocked from accessing the EHRI and other OPM systems, making it difficult for career OPM employees to know what Musk’s team has been examining or modifying. In the same report, the outlet revealed the team had moved sofa beds into the agency's headquarters to continue their work around the clock.
This should be a major national news scandal.
Elon Musk and the underlings he put in place at the Office of Personnel Management (OPM) have jeopardized data privacy and national security.
#Elon Musk#DOGE#Department of Government Efficiency#Trump Administration#Office of Personnel Management#USA Peformance#HIPAA#Enterprise Human Resources Integration#Amanda Scales#Data Breach#Privacy Impact Assessment#Data Privacy#Musk Coup
9 notes
·
View notes
Text
Episode 7

Word count: 7.4K
Content Warning: depictions of violence and masturbation
Pairing: Edward Nashton X OC Romy Winslow
Setting: Pre-Arkham Origins; 2013
─── [ sequence: loading ] ───
Wednesday, January 23rd, 2013
The names blurred together on the screen, each one a grim reminder of Gotham’s rot, festering just beneath the surface. Edward scrolled through the database, his sharp eyes darting between columns of information: names, ages, employment histories, and last-known locations. The pattern wasn’t immediately clear, but patterns always revealed themselves to him eventually. They had to.
Marcus Kane. Javier Moreno. Luis Dominguez. DeShawn Green. Alan Park.
And so many more.
He clicked on Luis Dominguez’s file, his fingers moving with practiced precision. A grainy ID photo filled the screen, showing a man in his early 30s with tired eyes and a forced smile. He’d worked at a warehouse on Gotham’s south side, one of the dozens flagged in the database Romy had compiled last week. The same warehouse where his body had been found two weeks ago—another so-called “accident” in a growing list of suspicious deaths.
Edward’s hand hovered over the mouse as his jaw tightened, his mind racing to piece the puzzle together. Luis wasn’t the first victim connected to the flagged properties. He wouldn’t be the last. These weren’t random deaths, and they certainly weren’t accidents. The connections were there, buried beneath layers of falsified reports and sanitized records. Edward could see the edges of the web, even if the full picture hadn’t yet come into focus.
He clicked into another file: Marcus Kane, 45. The data painted a grimly familiar picture. Marcus had been undocumented, working under the table for a ghost company listed as a subsidiary of Janus Logistics. His death had been ruled a heart attack, but Edward wasn’t buying it. Not with the growing number of cases tied to Janus-owned properties.
A pattern was emerging, one that gnawed at Edward’s mind with infuriating subtlety. These men weren’t just unlucky—they were expendable. Tools discarded when they outlived their usefulness.
He narrowed his eyes, scrolling through more entries, the hum of the computer the only sound in the dimly lit room. His thoughts, however, kept circling back to Romy. Her meticulous attention to detail had been instrumental in compiling these files last week, her ability to sift through mountains of data both impressive and irritating. She’d flagged the initial anomalies, bringing the network into sharper focus.
Too sharp.
Edward frowned, his lips pressing into a thin line. He hated admitting that her work had been flawless. It meant she’d seen what he had—the unspoken connections, the chilling efficiency behind the façade of disorder. Romy wasn’t blind to Gotham’s ugliness, and she’d been far too quick to grasp the scope of what they were uncovering. It wasn’t her intelligence that bothered him—it was how unbothered she seemed by it.
His gaze shifted back to the screen, his irritation simmering just beneath the surface. This was his case to crack, his puzzle to solve. The work was what mattered, not her involvement, not the way her observations stayed with him longer than they should. And certainly not the way her presence felt, at times, like a disruption he couldn’t ignore.
He exhaled sharply, clicking into another file, the weight of the revelation settling over him. The victims weren’t just numbers. They were part of a system—one designed to exploit, to erase, to ensure that no one looked too closely.
His lip curled. “She’s good,” he muttered in private, the admission slipping out reluctantly.
Edward’s gaze shifted, almost involuntarily, to the empty chair beside him. Romy had claimed that space as her own these past few weeks, invading his world with her presence, her scent, and her maddeningly confident demeanor. Now, even with her gone, the space felt occupied. She lingered, somehow, in the corners of his mind, impossible to dislodge.
A faint smirk tugged at the corner of his mouth as the thought settled. His hand rose to adjust his glasses, the motion deliberate, as if physically realigning his focus. With a sigh, he turned idly in his chair, letting the motion ground him as his gaze drifted to the stack of reports beside him. His lips tightened over his teeth. All this paper. The precinct’s stubborn clinging to outdated media was laughable in a world now dominated by digital precision. He rolled his eyes, his fingers brushing over the stack as though the mere texture of the pages irritated him.
And then his gaze landed on a smaller stack, set apart from the rest. The files Romy had left him last Friday before she left.
He hesitated, his hand hovering above the neatly compiled documents. Finally, he picked them up, flipping idly through the pages. The irritation that had flickered in his chest a moment ago began to dissipate, replaced by something quieter.
Each page was pristine. The data was meticulously compiled, each figure, timestamp, and cross-reference organized with such precision that it felt as if the documents themselves were tailored specifically for him. As he scanned the contents, he realized it wasn’t just well-done; it was exactly how he would have structured it—his preferences mirrored almost perfectly.
A faint sense of admiration stirred in him, unexpected and unwelcome.
Romy had taken almost three times the amount of time it would have taken him to complete this task, of course. He’d noted that last week—her slower, more deliberate pace was impossible to ignore. Yet, the result spoke for itself. The work was impeccable, precise, and thorough.
His smirk faded as he continued to flip through the pages, his brow furrowing slightly. How had she known what he would need? He hadn’t told her how to do anything. He’d just let her work, waiting for her inevitable failure. But she hadn’t failed. She’d anticipated the exact structure he’d find most persuasive, most efficient. He leaned back in his chair, the papers resting lightly in his hands as he considered the question. It wasn’t just competence. It was understanding—an infuriatingly precise grasp of what he valued, what he demanded.
For a moment, Edward allowed himself to sit with the thought, the faint hum of his monitors filling the silence. His admiration, as reluctant as it was, settled somewhere beneath the irritation she so often inspired.
Edward had not met someone like Romy before. It was maddening, this ease with which she had woven herself into his routine, carrying herself with an aura that was part silk, part steel—a contemporary, unapologetic, confident woman who drew him in, even as it irritated him.
She was a vision of modern allure, the kind of woman who knew exactly what power she held and wielded it with precision. Her wardrobe was anything but subdued, each outfit making a statement, often subtle but always intentional: tailored blazers, preppy shirts, chic sweaters, edgy dresses, and skirts that left just enough to the imagination. And those heels… He was ashamed to admit he had spared her calves numerous glances, observing the supple tone of her muscles poised in that unnatural yet oh-so classically alluring way.
There was her hair, cascading down her shoulders in luscious curtains, catching the light and shifting like silk with each movement, sometimes swaying when she walked. It was always luxurious, shimmering under even the poorest of office lights, and he was annoyingly aware of how often he watched it fall over her shoulder, only for her to flick it or brush it back in a way that drew his attention to the delicate arch of her neck.
Her makeup was never the same twice. It always accentuated her features so well, highlighting the line of her cheekbones, the arch of her brow, or the sensual curve of her cupid’s bow, each detail meticulously crafted yet seemingly casual. Some days, it was a timely look—a hint of blush, eyeliner sharp enough to cut, lips painted in a deep red or berry tone that made her look both effortlessly powerful and unattainable. Other days, it was daring, glossy lips and colorful negative space liner or sparse rhinestones decorating her eyes that pushed the boundary of professionalism in a way he couldn’t bring himself to dislike.
And those nails—acrylic, polished to perfection, shaped like little ovals. ( Or were they almonds? ) Mint green, then nude last week. Part of him wondered what color she had this week. He couldn’t help but notice the way they glinted when she typed or traced them along the edges of a folder. His mind wandered in spite of himself, wondering how her nails would feel on his skin like she’d jokingly suggested weeks ago, wondering what those slender fingers would look like wrapped around his…
No. No. No… No.
Edward pinched the bridge of his nose under his glasses, squeezing his eyes shut. Feeling an insidious twitch in his loins makes him take a slow steadying breath. Then he drug his hand down his face before letting his hand drop to his lap.
It was infuriating—but he couldn’t deny the effect she had.
He wanted to say it was just a physical attraction, mitigated by baser instincts, hormones like testosterone and estrogen infecting and influencing his mind.
But it wasn’t just the way she looked. Edward had expected that by now, Romy’s focus would have wavered, that maybe the allure of this “work-study” would wear off, leaving her bored and inattentive within the first week. Instead, she had surprised him with a silent, steady concentration that he was hesitant to say matched his own. When he explained something complex, her eyes were on him, keen and attentive, the barest nod to show she was following.
She was generally quiet when she worked, slipping effortlessly into that role—so much so that, despite her brashness, her crudeness at times, he found himself appreciating how well she actually listened when she wanted to, how easily she fell in line with his rhythm when the moment called for it.
Like a good girl, he mused, only catching himself a split second later with a grimace.
This combination of confidence and compliance, of inappropriate, well-timed quips, daring looks, and mindful attention, left Edward increasingly off-balance. Romy was a puzzle, a challenge he never expected to find in a young woman who looked and talked like her. He didn’t intimidate her, and every attempt to rattle her only seemed to draw that maddening, knowing smile to her lips—a smile that seemed to say, I see you, and I’m not backing down, sir…
Each Wednesday, Thursday, Friday, Edward steeled himself for her presence, knowing that, despite himself, he was drawn in, captured by the quiet power she wielded so effortlessly. She was a force, he realized, a clever, stylish, glossy-nailed hurricane that had him, against all reason, anticipating the days they’d share the same tiny, musty workspace.
His gaze kept drifting to the empty wooden chair beside him, the one where Romy so often sat. He frowned. (He really needed to get her something more comfortable to work in.) She wasn’t there today—she had an exam, her first of the semester.
At some point, he realized he had forgotten to wish her luck. The thought unnerved him as soon as it surfaced. Why would I want to wish her luck? he thought. He shifted in his seat.
Edward Nashton had never been the type to wish anyone luck or to care about someone else’s success or failure. Normally, he found satisfaction in the inevitable stumbles of others—the way they faltered or fell short of expectations. He even relished it, especially in those who paraded their ambitions with the naïve confidence he so despised.
But with Romy, the thought struck a different chord.
He pictured her on graduation day: a vision of her in that cap and gown, her usual chic style distilled into a single pair of elegant heels and a dress hidden beneath the formless black robe. The idea tugged at him, bringing the faintest curve to his lips. He could practically see it—her triumphant smirk as she stepped across the stage to accept her degree, that self-assured stride carrying her forward. The image made something warm unfurl in his chest, something he wasn’t entirely comfortable with.
He let the thought settle, that rare lift of the corners of his lips lingering for a moment. Maybe he should have wished her luck. After all, if anyone deserved it, it was her. Romy wasn’t like the others—she was intriguing, somewhat capable, and, against all his instincts, she made him feel… appreciative, somehow, of her presence.
Him , of all people, appreciative of someone else’s existence? Pfft.
In the silence, his eyes drifted to her empty spot again.
Today, in her absence, he decided he’d talk to Loeb.
Romy had been working alongside him for almost three weeks now, mostly assisting with mundane tasks and one-off cases, but she had also contributed to the analysis, organization, and compilation of his off-the-books response time investigation. The weight of it had been building, accumulating with each line of data, each correlation they had carefully drawn out together. Now, with everything laid out in stark, undeniable detail, he felt the pull to present it, to finally confront the decay that had festered in the department for far too long.
This was it. He was prepared, and with the foundation Romy had helped him build, the case was ready. There would be no disputing the corruption, no brushing off the carefully orchestrated negligence—the systemic rot that had turned Gotham’s protectors into something dark, twisted, and morally bankrupt.
As he stacked the pages, lining them up in perfect order, he couldn’t ignore the small, nagging awareness that Romy wouldn’t be there to see it. His grip tightened on the folder as he strode out the door and through the bullpen, every step steady, his pace unwavering. He was thankful no one stopped him, no one blocked his path. For once, his focus was undisturbed.
He climbed the stairs to Loeb’s office with long, deliberate strides, his resolve sharpening with each step. When he reached the mezzanine, he didn’t hesitate, rapping his knuckles against the door with confidence.
The answer was gruff, the Commissioner’s voice muffled but clear: “Come in.”
Edward’s breath remained calm, his nerves steady. The weight of what he was about to do felt right, as if every calculation, every line of data he had poured over—with Romy, his mind added—had brought him to this moment. As he stepped inside, his eyes locked onto Loeb.
The old bulldog sat hunched behind his desk, oversized form crammed into a worn leather chair that groaned under the strain. He was tapping at his phone, his fingers jabbing at the screen with impatient irritation, as though whatever he was doing was a poor distraction from the real issues at hand. Only when Edward stood before the desk, thick folder held firmly in his hands, did Loeb finally look up. The Commissioner’s beady eyes narrowed, a heavy sigh escaping him as he set his phone aside, clearly displeased to be interrupted.
“What is it, Nashton?”
Undeterred by his impatient tone, Edward held his gaze, feeling the weight of the evidence pressing at his fingertips. “I have something you need to see, Commissioner,” he said, his voice steady and low, just on the edge of formality. He slid the folder onto the desk with precision, opening it to reveal the meticulously organized pages. “It’s about a pattern I’ve uncovered in the officer response times. Specifically, certain neighborhoods and particular types of cases.”
The Commissioner’s eyes flickered over the documents. Edward paused, expecting a response, and, after a moment, his lips twitched. He forced down a smirk. The old man didn’t seem to comprehend what he was saying, so he continued, even being so kind as to lower himself closer and point out the data specifically. His actions were more helpful and generous than he had ever been in his life as he tried to make Loeb understand.
“For the last two months, I’ve compiled evidence of consistent delays in high-priority responses—delays that can’t be attributed to chance. The same officers show up in these records, over and over, and the pattern isn’t random.” Edward’s voice sharpened as he gestured to the pages.
He had never been more sure of something in his life. There was a mystery here, and he was smart enough to have uncovered it. The Commissioner should have been patting him on the back by now, but Loeb’s features tightened the longer Edward spoke. Edward laid out the evidence methodically, pointing to the pages, the names—Edison, Curtis, Hartley, and Murphy—and each pattern of delayed response times, tied to specific neighborhoods and incidents. His tone remained steady, but as he continued, he noticed the commissioner’s irritation seething just below the surface—the slight clenching of Loeb’s jaw and the narrowing of his eyes.
“And what exactly are you implying?”
“I’m not implying anything.” Edward’s gaze was unyielding as he straightened up from his position of helpfulness. “I’ve discovered facts and brought them to your attention. These officers are deliberately delaying their response times in specific areas, and the data points to a level of coordination that suggests they’re acting under instruction or incentive.”
“You’re throwing accusations around, Nashton.” Loeb’s gaze hardened, his eyes darting from the pages to Edward with an expression that bordered on contempt. “And you’re doing it with a lot of confidence.”
“‘Confidence?’” Edward’s voice remained cool, his posture unfaltering. “No, no. This is pronounced ‘evidence.’” He gestured towards the documents.
Loeb eyed the pages, and, after a moment, his lips pressed and pulled into a tight line. He flicked his beady eyes up to Edward and crossed his thick arms over his barrel chest, his uniform jacket pulling tight.
Edward rolled his eyes. “You can ignore it if you want, Commissioner. But I assure you, the numbers don’t lie.” Against his better judgment, he smirked—a tricky little thing that usually got him in trouble. “But people do…”
The words hit their mark, and he watched with satisfaction as Loeb’s face flushed, a muscle twitching in his jaw. The Commissioner unfulred his arms pushed the folder away, slow and deliberate, his fingers clenching slightly on the arm of his chair as he leaned back, studying Edward with an unreadable expression. But Edward didn’t flinch. He knew the strength of what he’d brought, knew the hours poured into each line of data, each name flagged, each statistic meticulously cross-checked.
Then a strange smile curled on Loeb’s thin lips—an unsettling expression that never reached his beady brown eyes. It was the kind of smile Edward recognized, the practiced smile of someone who knew far more than he was letting on.
“I’ll look into it,” Loeb had said finally, his voice oily, almost too smooth.
“‘ Look into it ’?” Edward’s eyes had narrowed, a spark of frustration flaring in his chest. He gritted his teeth, his jaw tight as he spoke. “What else is there to look into? The work is done.” His voice had sharpened, no longer masking his irritation. “I’d say the evidence is damning as it is.”
Loeb’s smile hadn’t wavered, but there was an unmistakable edge in his gaze now, one that bordered on condescension. “Careful, Nashton…,” he drawled. “You’ve done your job. I’ll take it from here. Now, let the real investigators handle it.”
Edward had opened his mouth, then paused before snapping it shut, biting back the urge to press further, to demand action right then and there, to curse and degrade Loeb’s so-called “investigators.” But as he’d watched the Commissioner casually close the folder, his fingers curling over it as though he’d already dismissed it, Edward had felt a cold realization settle over him. This wasn’t news to Loeb. He could see it in the way the man avoided his gaze, in his dismissive tone, in that unsettling smile.
Without another word, Edward had nodded, maintaining a neutral expression as he stepped back, masking the frustration roiling inside him. He needed to be smart about this. Keep a level head. But as he’d exited the office, shutting the door harder than he’d intended, the weight of the Commissioner’s reaction had pressed heavily on his chest. He had done everything right, laid out the evidence, made the case impossible to dismiss, and yet…
He paused on the landing, staring out over the bullpen, the precinct buzzing with detectives, officers, clerks, and secretaries—each one absorbed in their tasks, oblivious to the poison rotting at the heart of their work. The sight grated at him, a reminder of just how deep the corruption ran, how many people were blissfully unaware of the filth surrounding them. Or worse—they were all filth.
This fucking place… he thought bitterly. It’s an institution built on lies. Liars, thieves, conmen, cheaters—the lot of them.
Long before he descended the stairs, his earlier calm had evaporated. Each step felt heavier, his anger simmering in his blood. He had come to the Commissioner’s office prepared, ready to stand his ground, expecting resistance but hoping that, at the very least, his work would be taken seriously. Instead, he’d been met with that unsettling smile, those dismissive words that stung more than he cared to admit.
He reached the bottom of the stairs, his fists clenched at his sides. His mind raced, cycling through his options. Loeb’s reaction wasn’t just resistance—it had been a warning, a reminder that he, Edward Nashton, was playing in a league where power wasn’t wielded through logic or facts. It was a game played in shadows, where truth was twisted, buried, and left to rot. And yet, he knew he couldn’t walk away from this. Not now. If anything, this only drove him further. He needed a moment to collect himself, to let the red-hot anger settle into something cold and calculating.
With a quiet exhale, he turned toward the break room, a quick, bitter laugh escaping him. Coffee, he thought. It was the last thing he wanted, but somehow the small act of going through the motions, of finding some semblance of normalcy in this mess, felt necessary. He couldn’t let himself spiral. Perhaps a minute to focus on something ordinary would be enough to anchor him, to bring him back from the brink.
The break room was quiet save for the hum of the coffee machine, filling the space with its gentle whirr. He poured a cup methodically, the simple routine almost grounding as he tried to corral his chaotic thoughts. Loeb’s reaction still gnawed at him, festering like a splinter under his skin. The Commissioner’s dismissive smile, the way he’d pushed the folder away without a second glance—it all felt too rehearsed, too controlled.
Something’s not right, Edward thought, his hands tightening around the mug as he leaned against the counter, scowling into the dark liquid. His mind roiled with a thousand plans and counterplans. Strategies bloomed and unfolded, each one bent on taking this fight further, on unearthing the depths of the rot festering within the department. He would let Loeb sit with the evidence, watch for any cracks in the Commissioner’s carefully constructed facade, see if the old man made a move. In the meantime, he would keep digging, keep collecting irrefutable data.
As he leaned against the counter, his mind crystallized around a single thought: I won’t give up. This was no longer about simply amassing evidence; it was a matter of principle now, a puzzle layered with intrigue, a challenge that demanded his skill, his intellect.
There was satisfaction in it, knowing that only he, Edward Nashton, had the insight and tenacity to solve it. Loeb might have tried to dismiss him, but that dismissal only sharpened his resolve, igniting his obsession to piece this mystery together. It was a test of wit, and his pride flared at the thought of proving himself capable—superior, even.
But as he considered the implications of success, a different satisfaction stirred in his chest, one less idealistic and far more self-assured. Not only was this a battle of principles, but it was also an opportunity to solidify his place here, to secure the respect he’d long been denied. If he could expose this corruption, bring the whole, rotten infrastructure to its knees, his career would be not just made—it would be legendary.
A smug satisfaction unfurled within him. The Cybercrime Division, a department once treated as an afterthought, would rise under his direction, shaped into something formidable. He could already envision it: with him at the helm, the division would have the resources, the personnel, and the tools to finally track, trace, and dismantle the criminal networks that infested Gotham. He wouldn’t just be a nameless cog in the GCPD; he’d be its backbone, its mind. People would respect him, perhaps even fear him, for his unrelenting pursuit of truth. He would be the one to cut through the shadows, and his name would carry weight far beyond the precinct walls.
And deeper still, beneath the principles and the professional aspirations, there was a flicker of something darker, a quiet thrill in knowing that he alone had the power to control the narrative. He would have his victory, his influence. The thought settled into a quiet confidence as he took another sip, feeling the weight of his decision settle firmly within him. His legacy would be set in stone.
And so would Romy’s…
The realization sparked a faint, barely noticeable smirk at the corner of his mouth. What would it mean for Romy, still a student, to play a role in a case of this magnitude? To report back on her capstone project and tell them she’d been instrumental in uncovering corruption within the Gotham City Police Department? It would be no small feat. A move like this would cement her place here, secure her future. She wouldn’t be a mere preceptee but a respected part of something larger. He could picture it—the way she would walk through the precinct, head held high, with the quiet confidence of someone who had seen beyond the surface, someone with purpose.
And he felt something strange and unexpected—a sliver of satisfaction, even pride, in the thought. Romy had proven herself worthy of the work, skilled beyond what he’d initially thought. She wasn’t at his level, of course, but good enough to surpass his lowest expectations and, perhaps, even more curiously, someone he was beginning to respect.
The sound of someone entering the breakroom tore him from his thoughts. He looked up and immediately frowned and looked back to his coffee, brows knitted.
Hartley.
The officer swaggered into the room, crony in tow, mid conversation. But the moment they saw him, they grew quiet, however they were undeterred.
He saddled up right next to Edward at the coffee maker and grabbed a cup. Beside him, Edward could see the way Hartley glanced at him, a smirk tugging at his lips. Then he looked back to pouring his cup.
“Naaashton,” Hartley drawled, the grin in his voice palpable. “You’re more doom and gloom today than normal…” He cocked a sandy brow and backed away, casually blowing on his pipping hot joe. “What’s wrong? Missin’ someone?” He settled back beside his partner.
“I’m not sure I want to entertain whatever you are talking about, Hartley.” Edward grimaced, not even sure why he was responding at all. The officer’s statement intrigued him, though.
“C’mon, your girl—the new one?” Hartley smirked, nudging his friend, his voice dripping with mock interest.
“My girl?” Edward cocked a brow, his lips twitching into a sneer.
“Yeah, the babe strolling to and from your dungeon,” the officer drawled. He looked at Edward over the rim of his mug, taking a languid sip before continuing. “Please tell me you’re fuckin’ her in there.”
“I beg your pardon?”
“Oh, you’ve gotta be fuckin’ kiddin’ me.” With an almost incredulous look, Hartley set his mug beside him on the counter. “Nashton… She’s super, super fu— super fuckin’ hot, bro.” He gestured to his partner—Curtis Murphy. “He’s seen her. We all have. That tight little ass, mmm, fuck, I bet everything about her is tight.” Those greasy eyes slipped back to Edward, a challenge almost in his gaze. “Is it?”
Edward’s eye twitched.
“Also, does she spit or swallow? Murph wanted to know.” Hartley gestured to his partner with a casual toss of his head, to which Murphy only smirked and crossed his arms over his chest.
How crude. Vile.
A blaze of irritation ignited in Edward’s chest. He fought to keep his face neutral, barely lifting his eyes to acknowledge Hartley. “Not that it’s any of your business, but no, I’m not,” he replied coolly, his voice even but with an edge that could cut glass.
“Sooo, she’s available, then?” Hartley smirked, his eyes glinting with that same crude confidence, as though he’d won some imaginary contest.
A dark wave of something rolled over Edward, something deeper and more visceral than he was used to—something he had not felt before. It made his grip tighten on his coffee.
Edward wrenched forward, the mug flying from his fingers and smashing into Hartley’s smug, unguarded face. The ceramic shattered against his nose, hot liquid splashing across his skin, searing it. Blood spurted, crimson against the pale breakroom tile, as Hartley recoiled, shock and pain twisting his features. But Edward didn’t stop there; he leaped at the man, his hands gripping his neck, feeling the resistance of muscle and sinew as he drove him to the floor. His shoes skidded against the tile, slipping before he found his balance, pouring his weight down onto Hartley’s trachea, feeling the pulse of his screaming carotids under his fingers slow, then weaken, until those greasy eyes, filled with cruelty, began to dull. There was something intoxicating about watching the smug light fade, about knowing it was at his hands, his doing. Beneath him, Hartley’s body kicked, scrabbling for purchase, desperate for air, clawing at Edward’s arms in a final, useless attempt at survival. His grip tightened, his lip curling in savage satisfaction as he bore down, watching as the vessels burst in Hartley’s scleras, muddling those blue eyes of his.
Then he blinked.
Officer Jack Hartley was still standing before him, unblemished, alive, leaning casually against the counter, his short but stout crony beside him snickering along with his crude jabs about Romy. Edward stared, feeling the blood drain from his face as the real world settled back in around him, the brutal fantasy fading but leaving a charged, dangerous energy coursing through him. His fingers were fisted around his coffee mug, and he was acutely aware of the tension in his arms and shoulders, the clenched muscles that had been ready to spring into action. The urge to throw the mug, to silence that smug look, was a raw, simmering instinct, something almost frightening in its intensity.
The thought of Hartley even thinking about Romy, let alone considering the possibility of approaching her, disgusted him in a way he couldn’t fully explain. It was the way Hartley’s words slipped so easily, so carelessly, as if Romy were just another conquest, just another prize for him to leer at and pick apart. It was the blatant disrespect, the dismissive way he talked about her as though she were an object, something shiny to be coveted.
Edward took a measured breath, his eyes narrowing as he locked onto Hartley’s gaze. “Someone who has the good taste and sense to work with me, Hartley, wouldn’t stoop to… lower standards,” he said, his voice dripping with cold disdain, every word pointed. He took a slow sip of his coffee, savoring the flash of annoyance that flickered across Hartley’s face.
“Hey, easy there, Nashton,” Hartley sneered, recovering quickly, his smile twisting into something uglier. “No need to get all possessive…”
He met Hartley’s gaze with an unflinching stare, his eyes icy and sharp, cutting through the officer’s smug confidence. “Possessiveness requires actual interest,” he drolled, his voice low and laced with contempt. “To which I have none.” Liar. He leaned in, his words clipped and direct as he narrowed his gaze. “ No —what bothers me is the way you talk about people as if they’re here merely to stimulate that worn-out pleasure center of your puny brain. Not that I care, really. It’s just disconcerting to know you truly lack the executive functions to think with anything else but your dick.”
Hartley’s grin faltered, caught off guard by the blunt dismissal, but Edward didn’t linger long enough for him to respond. He kicked off the counter with a calm, deliberate stride, and as he passed the fuming officer and his dullard friend, he paused just long enough to let a cutting look settle between them. “So, go ahead, bro . Take your best shot.”
Without waiting for a response, Edward strode out of the breakroom, each step laced with the simmering anger he was barely keeping in check. But as soon as he was alone, the composure he had clung to in Hartley’s presence began to fracture. His brow furrowed, his jaw tight, and he picked up his pace, shoulders hunched with barely contained irritation as he stormed toward his office. The door swung open with more force than necessary, and he slammed it shut behind him, the sound stunted and sharp in the small space.
Inside, Edward sat, slumped in his chair, his gaze hard and unfocused, his mind still tangled in the aftermath of that encounter. Hartley’s words echoed relentlessly, the crude insinuations churning his thoughts with a bitterness he couldn’t seem to shake. Moron , he thought, his jaw clenching. Someone as mindless as him even thinking he had a chance with his student?
The thought alone felt like an insult.
But why?
Why was he so certain that Romy would turn someone like Hartley down?
When he examined it more closely, it almost seemed irrational—uncharacteristically emotional. After all, she was the type, wasn’t she? She was beautiful—effortlessly so. A former cheerleader. Sorority girl. Confident in ways he’d never been, with that easy demeanor of hers, and a social prowess that seemed second nature. Surely, he told himself, she’d been with someone like Hartley before. Hell, maybe she even belonged with someone like Hartley—someone who fit the part, who shared her seeming ease in the world. Someone easy to look at, easy to be with, and, more likely than not, someone who had never questioned his place in life.
The thought twisted his stomach in a way he didn’t understand. It grated against him, like sandpaper on raw skin. He’d always prided himself on his independence, on his unwillingness to conform or to care what people thought. But when he pictured Romy with someone like Hartley—a brute with no sense of subtlety, no spark of intellect, no intrigue beyond what he could bully or seize—it felt… cheap . Like she’d be wasting something; as if choosing someone like Hartley would somehow diminish the sharp wit and depth Edward had begun to glimpse in her.
And that, he realized with a pang, was what was eating at him. There was something in Romy that was different . Something he couldn’t name or fully understand but that he recognized, just beneath the surface, with every sly smile and barbed quip. She wasn’t what he had assumed, not another vapid pretty face that she presented herself to be.
Edward’s fingers stilled against the desk, and he inhaled, fighting to steady the unsettling rush within him. But his resolve wavered as his gaze drifted, almost instinctively, to the workspace she had set up beside his own.
The space felt strangely alive, as if it still held her presence, each detail carrying an imprint of her—the faint scent of her enticing perfume, the memory of her acrylic nails tapping against the keyboard, a sound he had come to find oddly comforting. In his mind, he could almost see the subtle arch of her spine leading up to that delicate curve of her neck. And there it was again: that teasing smirk that seemed to hover on her lips, one he had come to anticipate.
A smirk tugged at his own lips, and his gaze softened, his body losing some of the tension it had held only moments before. If he was honest with himself—something he rarely allowed in matters of this nature—there was a part of him that could, reluctantly, agree with Officer Hartley on one thing: Romy was, indeed, gorgeous. Beautiful in a way that was more than superficial, more than just a passing attraction. From the very first moment he’d seen her, he knew there was something about her that demanded attention, that drew his gaze with a power he couldn’t ignore. And in the privacy of his thoughts, he allowed himself to study the memory of her, her details vivid in his mind’s eye.
Her silken hair, the way it fell in such deliberate elegance around her face, and her alluring lips that he’d noticed moved with practiced charm, always careful, always in control. His mind traced over her—the shapely swell of her chest, her torso dipping into curving hips that seemed almost grippable. His breath caught, lingering on the image, following the memory of her form down to her thighs and calves. He had spent more than a few moments catching himself watching her cross her legs with that easy elegance, the subtle rise of her skirt when she shifted.
Then, Edward realized, with a pang of something between shame and excitement, that he had thought about the details of her existence more than he cared to admit. There was something fascinating in the way she carried herself… it was as if she were caught in a perfect balance between poised elegance and calculated seduction. She was fully aware of the effect she had, that much was clear, yet there was a restraint in the way she wielded it—enough to spark intrigue, but always keeping her allure just out of reach. It was maddening. That understated power she held, the way she navigated through spaces with that cool demeanor, the confidence that lingered around her like a cloud—it stirred something within him he was almost embarrassed to acknowledge.
But what was most confounding, what gnawed at him as he tried to dissect it, was that indifference. That fronted, artfully worn disinterest, as if she was completely unbothered by the world’s attention. But he wasn’t fooled, not entirely. He could see the hints, the subtle ways she showed she did care, that she was keenly aware of the impression she made. The way she smoothed down the fabric of her skirt, the deliberate flick of her hair, the glance in a pocket mirror when she thought he wasn’t looking. It was controlled, honed, a display of ease that felt intentional.
And, God, was it all effective.
Edward groaned, leaning forward, his elbows digging into his knees as his hands raked through his hair. His fingers gripped tightly at the roots, as if the pressure might somehow quiet his thoughts. His teeth grit, his brows pulling together into a sharp line as his eyes focused on the gritty black-and-white linoleum beneath him.
It didn’t help.
To his chagrin, Edward felt a tug of arousal pooling low in his belly, his body betraying him with a telltale twitch he wished he could ignore. He clenched his jaw, forcing his gaze back to his desk, willing the vision to fade. Yet it lingered, leaving him with a sense of helplessness he despised. He had never let anyone make him feel this off-kilter, this irrational, and yet here he was, caught up in thoughts he knew better than to entertain.
The repulsion he felt with himself caused his stomach to churn. He should not be feeling this way about her; should not be thinking like this. She was his student. But he could not help it. The dam in his mind had been broken, and now he could not stop himself from imagining what it would be like to have her.
Edward sat with his head in his hands, thinking hard about what to do. He reasoned with himself. Maybe if he were to release the pressure, he would feel better and be able to put the temptation behind him? Maybe then he would feel better?
Sitting at his desk, alone in the dusty, old file room converted to his workspace, Edward reached a hand down to grip himself through his pants. It had been so long since he allowed himself to indulge such primal desires. Normally, he did not need such baser pleasures, but he suddenly felt desperate. It was a disgusting desperation that he hoped the end would justify. Hand trembling, his fingers brushed against the top of his trousers and boxers. He undid the fly and button, trying his best not to think about it. Throat bobbing tight, he dipped his hand into his boxers to find and tentatively wrap his hand around his cock. A sigh of relief escaped him as he relaxed back into his seat, eyes slipping closed.
He, lips parted and brows knitted together, touched himself. He could already feel the uncomfortable stress leaving his body as a new pleasurable tension replaced it. Attempting to clear his mind, he tried to focus merely on the sensation of his fingers squeezing gently at the head before stroking down to the base of his member. Edward wanted to think about anything else but Romy. However, there was no use in thought-stopping because it only made the thoughts more persistent.
A desperate mewl left his lips as he imagined her—her body, her hands, her nails, her lips wrapped around him instead of his fingers. He could practically feel that pink tongue of hers on the tip of his cock, licking up the pre-cum that dripped and spreading it down his shaft. Edward couldn’t stop thinking about what it would be like to have her pretty face staring up at him, her knees red and bruised from kneeling. Hand moving faster, his breath came in short gasps as he chased his climax. He wanted this to be over with, and yet…
The image of Romy now sitting in his lap enveloped his mind in a searing grasp. She straddled his hips as she bounced eagerly on him. The thought of her warm, wet cunt squeezing him nearly made him cum alone. His ears tingled as he practically heard her moaning his name, squealing as he filled her to the brim.
“Mr. Nashton! Yes, please fuck me, sir. You’re so good. The fucking best!”
Feeling his body nearing his climax, he pictured her riding him, her delicate fingers gripping his shoulders as she continued bouncing up and down on his hard cock, her skirt bunched around her hips and panties shoved to the side. The sound of her voice, hoarse and mewling as she begged him to fuck her good, echoed in his now burning ears.
“ So close... I’m so close. K-keep going.”
Edward’s hand picked up the pace; desperation in his movements made the gestures jerky and short.
“Yes, that’s it! You’re so good, Edward. So fucking good to me. I want you to cum for me. That’s it, Edward, cum for me, baby!”
The groan that tore its way from his throat was stunted in the small room, his body trembling and shaking as he felt himself spurt into his hand.
“You did so well...”
Edward slumped back in his chair, his chest heaving. The silence that followed was deafening, the hum of the computer the only sound cutting through the thick, suffocating quiet. His breathing was ragged, his body trembling slightly as the intensity of his climax faded, leaving him adrift in the stark reality of what he’d just done. He blinked, the gravity of it all pressing heavily on his chest, the remnants of Romy’s vivid tableau lingering in his mind like an afterimage burned into his vision.
The memory was both deeply embarrassing and—he hated to admit—sickeningly satisfying.
His gaze flickered around the dim office, the quiet air feeling heavier now. His hand, sticky with evidence of his indulgence, curled into a loose fist before he sighed sharply, reaching for the box of tissues on his desk. A grumble rumbled low in his throat, a mix of frustration and quiet shame.
As he wiped himself clean, the hazy satisfaction began to fade, replaced by the creeping, familiar irritation that so often shadowed his thoughts. His gloves were a mess, and with a grimace, he tore them off, tossing them carelessly into the wastebasket. The action felt small, but it was a release—a way to discard the moment, as if ridding himself of the gloves might cleanse him of the lapse in his usually rigid self-control.
Edward muttered to himself as he finished cleaning up, the words lost in the low hum of the room but tinged with unmistakable annoyance.
Then he caught his reflection in one of the darkened monitors, a fleeting glimpse of himself—his slightly tousled hair, the vulnerability etched into the sharp lines of his features. The image was almost jarring, his own gaze looking back at him with a rawness he didn’t want to acknowledge. He looked away quickly, wadding the tissues and tossing them into the trash, his movements brisk and methodical.
The shame burned, but his walls were already rebuilding themselves, his detachment slotting back into place like armor he couldn’t live without. He adjusted his glasses, straightened his posture, and leaned forward again, his hands already reaching for the keyboard.
“Ridiculous.”
Ao3 link here!
#The Edge of Us#Riddler#The Riddler#Enigma#Edward Nashton#Edward Nigma#Nashton#Riddler x OC#Edward Nashton x OC#Edward x Romy#Female Oc#Fanfiction#Riddler Fanfiction#Arkham Origins#Arkhamverse#Romance#Smut#Action#Crime Drama#GCPD#2013#Slow Burn
8 notes
·
View notes
Text
How ERP Software for Engineering Companies Improves Operational Efficiency
In today's competitive market, engineering companies are under immense pressure to deliver innovative solutions, maintain cost-efficiency, and meet tight deadlines—all while ensuring the highest standards of quality. As the engineering industry becomes more complex and digitally driven, operational efficiency has become a key metric for success. One of the most transformative tools driving this change is ERP (Enterprise Resource Planning) software.

For companies seeking to streamline their operations, ERP software for engineering companies provides a centralized platform that integrates every function—ranging from procurement, design, production, finance, HR, and project management. In India, especially in industrial hubs like Delhi, the demand for such software is growing rapidly. Let us explore how ERP systems significantly enhance operational efficiency and why choosing the right ERP software company in India is vital for engineering enterprises.
Centralized Data Management: The Foundation of Efficiency
One of the major challenges engineering companies face is managing vast amounts of data across departments. Manual entries and siloed systems often lead to redundancies, errors, and miscommunication. With ERP software for engineering companies in India, organizations gain access to a unified database that connects all operational areas.
Real-time data availability ensures that everyone, from the design team to procurement and finance, is working with the latest information. This reduces rework, improves collaboration, and speeds up decision-making, thereby increasing efficiency.
Streamlined Project Management
Engineering projects involve numerous stages—from planning and design to execution and maintenance. Tracking timelines, resources, costs, and deliverables manually or via disparate systems often results in delays and budget overruns.
Modern engineering ERP software companies in Delhi provide robust project management modules that allow firms to plan, schedule, and monitor projects in real time. This includes milestone tracking, Gantt charts, resource allocation, and budget forecasting. Managers can gain visibility into bottlenecks early on and reallocate resources efficiently, ensuring timely delivery.
Automation of Core Processes
Automating routine tasks is one of the key advantages of implementing ERP software. From generating purchase orders and invoices to managing payroll and inventory, ERP eliminates the need for repetitive manual work. This not only saves time but also minimizes human error.
The best ERP software provider in India will offer customizable automation workflows tailored to the specific needs of engineering companies. For instance, when a material stock reaches a minimum threshold, the ERP system can automatically generate a requisition and notify the purchasing team. This ensures zero downtime due to material shortages.
Enhanced Resource Planning and Allocation
Resource planning is crucial in engineering projects where labour, materials, and machinery must be utilized efficiently. A good ERP software for engineering companies provides detailed insights into resource availability, utilization rates, and project requirements.
By analysing this data, companies can better allocate resources, avoid overbooking, and reduce idle time. This leads to significant cost savings and ensures optimal productivity across the board.
youtube
Integration with CAD and Design Tools
Many ERP solution providers in Delhi now offer integration with design and CAD software. This is particularly useful for engineering firms where design data is often needed for procurement, costing, and production.
When ERP is integrated with CAD, design changes automatically reflect across related departments. This seamless flow of information eliminates miscommunication and ensures that downstream processes such as procurement and manufacturing are aligned with the latest design specifications.
Real-time Cost and Budget Management
Keeping engineering projects within budget is a continuous challenge. Unexpected costs can arise at any stage, and without proper monitoring, they can spiral out of control. ERP software providers in India equip engineering companies with real-time budget tracking tools.
From initial cost estimation to actual expenditure, companies can monitor every aspect of the financials. Alerts can be configured for budget deviations, helping management take corrective action promptly. This financial control is a cornerstone of operational efficiency and long-term profitability.
Improved Compliance and Documentation
Engineering companies must adhere to various compliance standards, certifications, and audit requirements. Maintaining accurate documentation and audit trails is critical. ERP systems automate compliance tracking and generate necessary documentation on demand.
By partnering with trusted ERP software companies in Delhi, engineering firms can ensure they meet industry standards with minimal administrative overhead. Features like document versioning, digital signatures, and compliance checklists help organizations stay audit-ready at all times.
Scalable and Future-ready Solutions
One of the biggest advantages of working with a reputed engineering ERP software company in Delhi is access to scalable solutions. As engineering businesses grow, their operational complexities increase. Modern ERP systems are modular and scalable, allowing businesses to add new functionalities as needed without disrupting existing operations.
Moreover, cloud-based ERP solutions offer flexibility, remote access, and lower infrastructure costs. These are especially beneficial for engineering companies that operate across multiple locations or work on-site with clients.
Enhanced Customer Satisfaction
Efficient operations lead to improved delivery timelines, better quality products, and faster customer service—all of which directly impact customer satisfaction. With ERP, engineering companies can maintain accurate production schedules, meet delivery deadlines, and respond to customer queries with real-time information.
By choosing the right ERP software for engineering companies in India, firms not only improve internal operations but also build a strong reputation for reliability and professionalism among their clients.
Choosing the Right ERP Partner
With the growing number of ERP solution providers in India, selecting the right partner is crucial. Here are a few factors to consider:
Domain Expertise: Choose a vendor with experience in the engineering sector.
Customization: The software should be tailored to suit your specific workflows.
Scalability: Ensure the ERP solution grows with your business.
Support & Training: Opt for companies that provide ongoing support and employee training.
Integration Capabilities: Check whether the ERP can integrate with your existing systems, including CAD tools, financial software, etc.
Trusted ERP software companies in Delhi like Shantitechnology (STERP) stand out because they offer deep industry knowledge, scalable platforms, and dedicated customer support—making them ideal partners for engineering businesses seeking to transform operations.
youtube
Final Thoughts
In a rapidly evolving business landscape, engineering companies must adopt smart technologies to stay ahead. ERP software is not just an IT solution—it is a strategic tool that can redefine how engineering firms manage their projects, people, and performance.
From streamlining project workflows and automating routine tasks to enhancing collaboration and boosting resource efficiency, ERP solutions deliver measurable gains across the organization. For those looking to make a digital leap, partnering with a top-rated ERP software company in India can be the difference between stagnation and scalable success.
Looking for a reliable ERP partner? Shantitechnology (STERP) is among the leading ERP solution providers in Delhi, offering tailored ERP software for engineering companies to help you boost productivity, reduce costs, and grow sustainably. Contact us today to learn more!
#Engineering ERP software company#ERP software for engineering companies in India#ERP solution providers#ERP software for engineering companies#ERP software companies#ERP software providers in India#Gujarat#Maharashtra#Madhyapradesh#ERP solution providers in India#ERP for manufacturing company#Delhi#Hyderabad#ERP Software#Custom ERP#ERP software company#Manufacturing enterprise resource planning software#Bengaluru#ERP software company in India#Engineering ERP Software Company#Best ERP software provider in India#Manufacturing ERP software company#Manufacturing enterprise resource planning#ERP modules for manufacturing industry#Best ERP for manufacturing industry#India#Youtube
2 notes
·
View notes
Text
Learn More About Outsourcing Database Data Entry Services

The creation and maintenance of a database is crucial for any kind of business. Every day, the database that holds all of the essential data about the company should be updated and kept in good order. Such a database is necessary for every business to rely on for all of its operations and services. Given that maintaining the database requires data entry, this activity must be done. This database will enable your staff to provide better customer service.
What Is Database Data Entry Services?
The process of entering, updating, and maintaining data within a database system is offered by database data entry services. For companies and organizations that depend on precise and well-organized data to make decisions and optimize their processes, this service is essential.
Database data entry services play a vital role in maintaining accurate and well-organized information, enabling businesses to make informed decisions and streamline their operations. The specific services offered can vary based on the provider and the unique needs of the client.
Why Outsourcing Database Data Entry Services Is Important?
Outsourcing database data entry can be cost-effective as it allows businesses to leverage the expertise of specialized service providers. In many cases, outsourcing to regions with lower labor costs can result in significant savings compared to hiring and training in-house staff.
Professional database data entry outsourcing company can often complete tasks more quickly due to their specialized skills, experience, and efficient processes. This can be especially important when dealing with large volumes of data.
Outsourcing non-core tasks like data entry enables a company to concentrate on its core business activities. This allows employees to focus on strategic tasks that contribute directly to the company's growth and success.
Categories Of Outsourcing Database Data Entry Services
Outsourcing database data entry services can be categorized based on the nature of the data entry tasks and the industry-specific requirements. Here are some common categories of outsourcing database data entry services:
• Database of Reservations in Transports • Financial Database for Financial Records • Database of Legal Institutions • Online Examinations Schedule Database • Online Database of Websites • Database of Product Sales and Purchase • Medical Database of Patient’s Records
Work Procedure Follow In Outsourcing Database Data Entry Services
The work procedure followed in outsourcing database data entry services typically involves several steps to ensure accuracy, efficiency, and client satisfaction. While specific procedures may vary among outsourcing providers, here is a general overview of the common steps in the process:
Understanding Client Requirements: The first step involves a thorough understanding of the client's requirements. This includes clarifying the type of data entry tasks, the format of data, specific instructions, quality standards, and any other project-related details. Data Security And Confidentiality Agreement: Establishing a data security and confidentiality agreement is crucial. Both the outsourcing provider and the client must ensure that sensitive information remains secure and is handled in compliance with data protection regulations.
Project Planning And Resource Allocation: Based on the client's requirements, the outsourcing provider plans the project, allocates resources, and determines the workflow. This includes assigning tasks to specific data entry professionals or teams.
Data Collection And Verification: If the project involves data collection from various sources, the outsourcing team collects the required data and verifies its accuracy. This step is crucial for maintaining data quality and integrity.
Data Entry Process: The actual data entry process begins, when professionals input the collected or provided information into the designated databases, spreadsheets, or other platforms. This may involve online or offline data entry depending on the project requirements.
Quality Control And Accuracy Checks: Regular quality control checks are conducted to ensure the accuracy and completeness of the entered data. This may involve manual reviews, automated validation processes, or a combination of both.
Data Cleansing And Enrichment: If part of the project involves data cleansing and enrichment, the outsourcing team identifies and corrects errors, validates information, and supplements missing details to improve overall data quality.
Client Review And Feedback: Periodic reviews are conducted with the client to provide updates on the project's progress and to gather feedback. This ensures alignment with client expectations and allows for adjustments if needed.
Final Delivery: Upon completion of the data entry tasks and quality assurance processes, the finalized data is delivered to the client in the specified format and within the agreed-upon timeframe.
Get Benefited From Outsourcing Database Data Entry Services
Outsourcing database data entry services can offer several benefits to businesses, regardless of their size or industry. Here are some key advantages that organizations can gain by leveraging outsourced data entry services:
Cost Savings: Businesses can save money by outsourcing data entry work to areas with lower labor expenses. This removes the requirement for internal personnel hiring, training, and management, along with the related overhead expenses.
Focus On Core Activities: Businesses can reallocate internal resources and focus on strategic initiatives and core operations that lead to corporate success by outsourcing time-consuming and routine data entry tasks.
Access To Skilled Professionals: Outsourcing providers often have a team of skilled and experienced data entry professionals. This expertise ensures high-quality work, accuracy, and efficient handling of data, which may exceed the capabilities of an in-house team.
Scalability And Flexibility: Businesses can scale up or down their data entry operations through outsourcing in response to changes in workload, demand during specific seasons, or project specifications. This flexibility is especially beneficial for businesses that require different levels of data entry.
Improved Productivity And Efficiency: Dedicated outsourcing teams are often more efficient in handling data entry tasks due to their specialization, experience, and streamlined processes. This can lead to improved productivity and faster turnaround times.
Access To Advanced Technology: To enter data, outsourcing companies make investments in the newest infrastructure and technology. Access to cutting-edge equipment, software, and automated procedures can help businesses without requiring large upfront expenditures.
Risk Mitigation And Compliance: Reputable outsourcing companies follow data protection laws and put strong security measures in place. By doing this, the risks of data compromises, mistakes, and non-compliance are reduced and the confidentiality and integrity of the data are preserved.
Time Savings: Project completion times can be greatly shortened by outsourcing data entry work. This is especially helpful for companies who need to process a lot of data or have tight deadlines.
By considering these benefits, businesses can make informed decisions about outsourcing their database data entry services to enhance efficiency, reduce costs, and focus on their core competencies.
Source Link: https://latestbpoblog.blogspot.com/2024/02/learn-more-about-outsourcing-database-data-entry-services.html
#Database Data Entry#Database Data Entry Services#Database Data Entry Companies#Outsource Database Data Entry#Professional Database Data Entry#Bulk Database Data Entry
0 notes
Text
Structured Query Language (SQL): A Comprehensive Guide
Structured Query Language, popularly called SQL (reported "ess-que-ell" or sometimes "sequel"), is the same old language used for managing and manipulating relational databases. Developed in the early 1970s by using IBM researchers Donald D. Chamberlin and Raymond F. Boyce, SQL has when you consider that end up the dominant language for database structures round the world.
Structured query language commands with examples
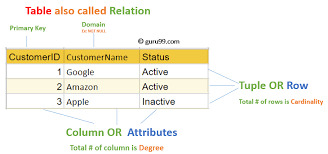
Today, certainly every important relational database control system (RDBMS)—such as MySQL, PostgreSQL, Oracle, SQL Server, and SQLite—uses SQL as its core question language.
What is SQL?
SQL is a website-specific language used to:
Retrieve facts from a database.
Insert, replace, and delete statistics.
Create and modify database structures (tables, indexes, perspectives).
Manage get entry to permissions and security.
Perform data analytics and reporting.
In easy phrases, SQL permits customers to speak with databases to shop and retrieve structured information.
Key Characteristics of SQL
Declarative Language: SQL focuses on what to do, now not the way to do it. For instance, whilst you write SELECT * FROM users, you don’t need to inform SQL the way to fetch the facts—it figures that out.
Standardized: SQL has been standardized through agencies like ANSI and ISO, with maximum database structures enforcing the core language and including their very own extensions.
Relational Model-Based: SQL is designed to work with tables (also called members of the family) in which records is organized in rows and columns.
Core Components of SQL
SQL may be damaged down into numerous predominant categories of instructions, each with unique functions.
1. Data Definition Language (DDL)
DDL commands are used to outline or modify the shape of database gadgets like tables, schemas, indexes, and so forth.
Common DDL commands:
CREATE: To create a brand new table or database.
ALTER: To modify an present table (add or put off columns).
DROP: To delete a table or database.
TRUNCATE: To delete all rows from a table but preserve its shape.
Example:
sq.
Copy
Edit
CREATE TABLE personnel (
id INT PRIMARY KEY,
call VARCHAR(one hundred),
income DECIMAL(10,2)
);
2. Data Manipulation Language (DML)
DML commands are used for statistics operations which include inserting, updating, or deleting information.
Common DML commands:
SELECT: Retrieve data from one or more tables.
INSERT: Add new records.
UPDATE: Modify existing statistics.
DELETE: Remove information.
Example:
square
Copy
Edit
INSERT INTO employees (id, name, earnings)
VALUES (1, 'Alice Johnson', 75000.00);
three. Data Query Language (DQL)
Some specialists separate SELECT from DML and treat it as its very own category: DQL.
Example:
square
Copy
Edit
SELECT name, income FROM personnel WHERE profits > 60000;
This command retrieves names and salaries of employees earning more than 60,000.
4. Data Control Language (DCL)
DCL instructions cope with permissions and access manage.
Common DCL instructions:
GRANT: Give get right of entry to to users.
REVOKE: Remove access.
Example:
square
Copy
Edit
GRANT SELECT, INSERT ON personnel TO john_doe;
five. Transaction Control Language (TCL)
TCL commands manage transactions to ensure data integrity.
Common TCL instructions:
BEGIN: Start a transaction.
COMMIT: Save changes.
ROLLBACK: Undo changes.
SAVEPOINT: Set a savepoint inside a transaction.
Example:
square
Copy
Edit
BEGIN;
UPDATE personnel SET earnings = income * 1.10;
COMMIT;
SQL Clauses and Syntax Elements
WHERE: Filters rows.
ORDER BY: Sorts effects.
GROUP BY: Groups rows sharing a assets.
HAVING: Filters companies.
JOIN: Combines rows from or greater tables.
Example with JOIN:
square
Copy
Edit
SELECT personnel.Name, departments.Name
FROM personnel
JOIN departments ON personnel.Dept_id = departments.Identity;
Types of Joins in SQL
INNER JOIN: Returns statistics with matching values in each tables.
LEFT JOIN: Returns all statistics from the left table, and matched statistics from the right.
RIGHT JOIN: Opposite of LEFT JOIN.
FULL JOIN: Returns all records while there is a in shape in either desk.
SELF JOIN: Joins a table to itself.
Subqueries and Nested Queries
A subquery is a query inside any other query.
Example:
sq.
Copy
Edit
SELECT name FROM employees
WHERE earnings > (SELECT AVG(earnings) FROM personnel);
This reveals employees who earn above common earnings.
Functions in SQL
SQL includes built-in features for acting calculations and formatting:
Aggregate Functions: SUM(), AVG(), COUNT(), MAX(), MIN()
String Functions: UPPER(), LOWER(), CONCAT()
Date Functions: NOW(), CURDATE(), DATEADD()
Conversion Functions: CAST(), CONVERT()
Indexes in SQL
An index is used to hurry up searches.
Example:
sq.
Copy
Edit
CREATE INDEX idx_name ON employees(call);
Indexes help improve the performance of queries concerning massive information.
Views in SQL
A view is a digital desk created through a question.
Example:
square
Copy
Edit
CREATE VIEW high_earners AS
SELECT call, salary FROM employees WHERE earnings > 80000;
Views are beneficial for:
Security (disguise positive columns)
Simplifying complex queries
Reusability
Normalization in SQL
Normalization is the system of organizing facts to reduce redundancy. It entails breaking a database into multiple related tables and defining overseas keys to link them.
1NF: No repeating groups.
2NF: No partial dependency.
3NF: No transitive dependency.
SQL in Real-World Applications
Web Development: Most web apps use SQL to manipulate customers, periods, orders, and content.
Data Analysis: SQL is extensively used in information analytics systems like Power BI, Tableau, and even Excel (thru Power Query).
Finance and Banking: SQL handles transaction logs, audit trails, and reporting systems.
Healthcare: Managing patient statistics, remedy records, and billing.
Retail: Inventory systems, sales analysis, and consumer statistics.
Government and Research: For storing and querying massive datasets.
Popular SQL Database Systems
MySQL: Open-supply and extensively used in internet apps.
PostgreSQL: Advanced capabilities and standards compliance.
Oracle DB: Commercial, especially scalable, agency-degree.
SQL Server: Microsoft’s relational database.
SQLite: Lightweight, file-based database used in cellular and desktop apps.
Limitations of SQL
SQL can be verbose and complicated for positive operations.
Not perfect for unstructured information (NoSQL databases like MongoDB are better acceptable).
Vendor-unique extensions can reduce portability.
Java Programming Language Tutorial
Dot Net Programming Language
C ++ Online Compliers
C Language Compliers
2 notes
·
View notes
Text
Immigration Services in Thailand
1.1 Statutory Foundations
Immigration Act B.E. 2522 (1979): Primary legislation
Ministerial Regulations: 47 implementing regulations (updated 2023)
Royal Decrees: Special provisions for investment/retirement
1.2 Organizational Structure
Immigration Bureau: Under Royal Thai Police
Headquarters (Chaeng Wattana, Bangkok)
76 Provincial Offices
32 Border Checkpoints
Specialized Units:
Visa Division (Section 1)
Extension Division (Section 2)
Investigation Division (Section 3)
2. Core Visa Categories and Processing
2.2 Special Visa Programs
SMART Visa: 4-year stay for experts/investors
LTR Visa: 10-year privilege visa
Elite Visa: 5-20 year membership program
3. Application Procedures
3.1 Document Authentication
Notarization Requirements:
Home country documents
Thai Ministry of Foreign Affairs legalization
Translation Standards:
Certified translators
Embassy verification
4. Digital Transformation Initiatives
4.1 Online Systems
e-Extension: Pilot program for 12 visa types
90-Day Reporting: Online portal and mobile app
TM30 Automation: Hotel API integration
4.2 Biometric Implementation
Facial Recognition: At 6 major airports
Fingerprint Database: 10-print system since 2018
Iris Scanning: Testing at Suvarnabhumi
5. Compliance and Enforcement
5.1 Monitoring Systems
Overstay Tracking: Real-time alerts after 7 days
Visa Run Detection: Algorithmic pattern analysis
Work Permit Integration: MOE-Immigration data sharing
6. Provincial Variations
6.2 Special Economic Zones
Eastern Economic Corridor: Fast-track processing
Border Provinces: Cross-border worker programs
7. Specialized Services
7.1 Corporate Immigration
BOI Fast Track: 7-day work permit processing
Regional HQ Packages: Multiple-entry privileges
Startup Visa: DEPA-endorsed companies
7.2 Family Reunification
Dependent Visas: Spouse/children under 20
Parent Visas: Financial guarantee requirements
Thai National Sponsorship: Income thresholds
8. Emerging Trends (2024 Update)
8.1 Policy Developments
Digital Nomad Visa: Expected Q4 2024
Airport Automated Clearance: Expansion to 8 more nationalities
Visa Fee Restructuring: Proposed 15-20% increase
8.2 Technological Advancements
Blockchain Verification: For document authentication
AI-Assisted Processing: Risk assessment algorithms
Mobile Biometrics: Pilot for frequent travelers
9. Strategic Considerations
9.1 Application Optimization
Document Preparation:
6-month bank statement continuity
Property lease registration
Timing Strategies:
Avoid holiday periods
Pre-submission checks
9.2 Compliance Management
Record Keeping:
Entry/exit stamps
TM30 receipts
Advisory Services:
Licensed lawyers vs agents
BOI-certified consultants
#thailand#immigration#immigrationlawyers#visa#visainthailand#immigrationinthailand#immigrationlawyersinthailand#thai#thaivisa#immigrationservices
2 notes
·
View notes
Text
How to Ensure the Quality of Data Entry Services

Data entry services demand high quality and accuracy for professionals to gain the right information at the right time. Partnering with an outsourcing data entry company maintains this quality and accuracy level, allowing organizations to have an organized database. Here are some tips that can help enhance the accuracy of the data entry process and streamline business operations.
#data entry services#data entry company#outsource data entry#data digitalization#data entry for real estate#invoice data entry service#document data entry services#ecommerce data entry services#outsource data entry services#medical data entry
2 notes
·
View notes
Text
ISRAEL REALTIME - "Connecting the World to Israel in Realtime"
After Shabbat - Nov. 25 - Shavua tov
🟠 HOSTAGE RELEASES REMAIN ON HOLD BY HAMAS
🔸CEASEFIRE ENDS AT MIDNIGHT IF NO PROGRESS? (N12) Israel sent a message to Hamas: if the abductees are not released by midnight - the ceasefire will end - per Al Jazeera. (( Interestingly this is being reported by Al Jazeera and Al Arabiya Arab news networks as a statement by Israel made via Israel Channel 12, but was a commentary statement made by Israel’s political commentator for Channel 12 Amit Segal - no official source for such a statement as far as we can tell. Did Israel’s Channel 12 political commentator just set Israeli policy and threaten Hamas? And from 2 items below - effectively? ))
🔸ISRAEL SAYS… A political source: "All the claims of Hamas as if Israel violated the agreement are lies. This is a propaganda attempt by Hamas. Israel has met all its obligations. Hamas is embarrassing the mediators - Egypt and Qatar."
🔸HAMAS BACKING DOWN? A senior Hamas official, Osama Hamdan, said a few minutes ago to Al-Arabia network: "The exchange steps (the release of the abductees and prisoners) will be completed, after we receive the answers we requested from the mediators."
🔸TO HAMAS’S CLAIMS, ISRAEL SAYS… Regarding the release of the terrorists: Israel claims that it did not undertake to release based on seniority, but rather a sort of statement that it might do so. Regarding the trucks to north Gaza: they passed the Rafah crossing -Israel is not responsible for their arrival to the north, but for allowing their entry. And it happened.
🔸MAGEN DOVID ODOM SAYS… the release procedure is not in sight at the moment: First, Hamas directs the Red Cross where to go to receive the Israeli hostages - and also transfers their details. Unlike yesterday, it has not yet been transferred the meeting point. MDA has tried to contact the Red Cross, but they are not answering.
◾️PALESTINIANS AWAITING PRISONER RELEASE SHOT IN FRONT OF PRISON… Riots by Palestinians in front of Ofer prison while waiting for the release of the Hamas prisoners. 3 were wounded by our forces' live fire to disperse the rioters.
◾️ISRAEL SOCIAL NEWS CHANNEL HACK-ATTACKED BY YEMEN HACKERS… One of Israel’s top Arab monitoring social news channels was attacked on Shabbat and partially hacked - with a channel bot taken over. Those operating Israeli channels on social media are advised to increase their security - make sure to activate 2 factor authentication and only use automated management tools such as channel bots if absolutely necessary. (The channel is back is service.)
◾️ISRAEL HACKERS TAKE OUT IRANIAN HACKERS… WeRedEvils says “We managed to permanently disable the group of Iranian and Yemeni hackers "Tofan". Those hackers stole sensitive details of tens of thousands of Israelis and was involved in the disclosure of information and business damage to more than 40 companies - and also harmed quite a few soldiers and sent threatening messages to hundreds of thousands of Israelis. We received a request from a special body to attack them and delete their data, databases in the order of 50GB, and we succeeded in this task.”
23 notes
·
View notes
Text
What exactly is Blockchain
A Comprehensive Guide for All: What is Blockchain?
Try to picture yourself with a notebook in which you record every purchase or sale. Each time you do a transaction, you note it in the notebook. Now, what if you distributed this notebook amongst your friends and everyone had one? All of your buddies would scrutinize your entry before adding it to their notes. This way, nobody could fake an old entry, since everyone else would spot it.
Something known as blockchain is built upon this basic concept — sharing a record of transactions open for everyone to verify. Though it may sound intimidating, it is a technology gaining traction in the financial and computer sector. We will clarify it in this blog in simple words, so anybody may follow it.
What Exactly Does Blockchain Mean?
Fundamentally, blockchain is simply a unique form of digital record-keeping. Think of it as a series of blocks (hence the name “blockchain”), each block including transaction information. These blocks are related in a way that makes them quite stable and difficult to change.
Step by step, this is how it works:
A Transaction Occurs: Suppose Alice wants to give Bob $10. This is an interaction.
The transaction is registered: the information of this transaction is passed to a network of computer nodes instead of being written in one notebook.
Everyone Checks the Transaction: The computers in the network check to make sure Alice has $10 to transmit. By examining her past deals kept in earlier blocks, they do this.
The transaction is added to a block: Once everyone concurs it is legitimate, it gets formed with other transactions into a block.
The Block Is Sealed, attached: The block is assigned an individual code (known as a hash) and then included in the chain of already existing blocks. This makes a fixed, permanent record of the deal. There it is! It is like one huge, common ledger keeping track of all system events.
What Makes Blockchain Different?
Now, one might be wondering, “Why not simply use a normal database or spreadsheet?” Fantastic issue! Blockchain distinguishes itself by several distinct qualities.
It is distributed across.
Most models today have one main custodian — be it a bank, company, or government — that manages the records. The entire system can crumble if something goes wrong with that central authority — say, hacking or corruption.
Blockchain relies on many, but not one authority. It rather distributes the blame amongst several computers (nodes). Every node has a full blockchain copy, therefore no individual or group may manage it. This all but prevents evil actors from using the data.
It is transparent.
Given that each transaction is visible to all people in the network, and recorded on the blockchain, it is clear. You can observe when and where money or assets traveled from one location to another. Since no one can hide anything, this openness fosters confidence.
Consider how a nonprofit uses blockchain to monitor contributions, for instance. Donors might observe very clearly how their funds are used, therefore guaranteeing that they reach the intended beneficiaries without middlemen siphoning off funds.
Safe.
Adding a transaction to the blockchain makes it virtually irrevocable.
Therefore: Every block has its distinct code (hash), including the one from the preceding block. Trying to change a block would also require one to re-compute the hashes for every subsequent block, hardly a small job.
Since the blockchain is decentralized, hackers would have to simultaneously compromise more than half of the computers in the network to fiddle with the data. Considering how vast these networks can usually be, this is virtually impossible.
Such a level of security makes blockchain perfect for sensitive uses including medical records, banking, and voting systems
It cuts out intermediaries.
Usually, when you want to buy anything online or move funds, you go via middlemen including banks, payment processors, or even legal practitioners. These intermediaries increase both costs and time for the project.
Blockchains free you from the need for intermediaries. Transactions take place between parties on their own, therefore saving both time and financial means. Sending funds abroad the old way can take days and incur large charges, for example. Using blockchain-based cryptocurrencies like Bitcoin, the same transaction can take minutes for a small percentage of the cost.
Examples of blockchain in the real world:
To know more about how blockchain operates in practice, let us look at some instances:
Cryptocurrencies
Cryptocurrencies like Bitcoin and Ethereum have the most well-known applications of blockchain. People can transfer money and accept it without a bank using these digital currencies. Each time somebody sends Bitcoin to another, the blockchain notes the transaction.
Supply Chain Management Tracking
As goods traverse the supply chain, enterprises including IBM and Walmart use blockchain to monitor them. If you buy a mango, you can scan a QR code, for instance, and find exactly where it came from, who touched it, and when it reached the store. This ensures product quality and reduces fraud.
Election processes
Some nations are trying voting systems based on blockchain. Blockchain might help to lower voter fraud and raise public faith in election results since it is open and safe.
Health information
Ways hospitals and clinics could leverage blockchain for patient records storage are under investigation. This would let doctors quickly access precise and current data while permitting patients complete control of their information.
Some popular misunderstandings surrounding blockchain
Though blockchain is growing in popularity, some questions remain about its nature and usage. Those should be cleared away:
“Blockchain Is Just for Cryptocurrencies.”
Though cryptocurrencies were the first significant application of blockchain, the technology itself has great applications beyond finance. Industries including logistics, healthcare, and government are discovering creative applications of blockchain.
Blockchain is anonymous.
Though blockchain provides privacy, it is not entirely anonymous. Since transactions are listed publicly, anyone can see them. Users’ identities are typically expressed by codes — rather than actual names — thus granting some level of pseudonymity.
“Blockchain is flawless.”
Though very secure, blockchain is not free from dangers. Thankfully, such attacks are really rare because of the complexity and size of the majority of blockchain networks — for instance, if someone gains control of more than 50% of the computing power of the network, they could theoretically manipulate the blockchain in what is known as a “51% assault.”
The Future of Blockchains
Though blockchain is still fairly new, its possibilities are vast. Improvements in general efficiency, openness, and security across the board will probably follow the more widespread acceptance of it. Some professionals think that blockchain could transform everything from our personal data management to our voting.
Still, popular usage will need time. Scalability (managing vast transaction numbers), regulation (governments determining how to deal with blockchain), and education (assisting people in understanding and embracing the technology) are obstacles to be tackled.
Wraps up.
So, at its most basic, blockchain is a decentralized, clear, and secured means of documentation. Whether it is assisting farmers in obtaining fair prices for their products, accelerating international payments, or safeguarding sensitive medical information, blockchain has the capacity to change our lives and employment fundamentally.
Next time you learn about blockchain, recall the notebook analogy: It’s a shared, tamper-proof book everyone can view but no one can edit. And who knows? Maybe someday soon, blockchain will become as common as smartphones or the internet!
Even a small tip goes a long way!
ETH: 0x788571C4c836ec733a72ff84c626BF7F20736d76
Thanks for reading Aadit’s Substack! Subscribe for free to receive new posts and support my work.
3 notes
·
View notes
Text
Atom: The Beginning & AI Cybersecurity

Atom: The Beginning is a manga about two researchers creating advanced robotic AI systems, such as unit A106. Their breakthrough is the Bewusstein (Translation: awareness) system, which aims to give robots a "heart", or a kind of empathy. In volume 2, A106, or Atom, manages to "beat" the highly advanced robot Mars in a fight using a highly abstracted machine language over WiFi to persuade it to stop.

This may be fiction, but it has parallels with current AI development in the use of specific commands to over-run safety guides. This has been demonstrated in GPT models, such as ChatGPT, where users are able to subvert models to get them to output "banned" information by "pretending" to be another AI system, or other means.
There are parallels to Atom, in a sense with users effectively "persuading" the system to empathise. In reality, this is the consequence of training Large Language Models (LLM's) on relatively un-sorted input data. Until recent guardrail placed by OpenAI there were no commands to "stop" the AI from pretending to be an AI from being a human who COULD perform these actions.
As one research paper put it:
"Such attacks can result in erroneous outputs, model-generated hate speech, and the exposure of users’ sensitive information." Branch, et al. 2022

There are, however, more deliberately malicious actions which AI developers can take to introduce backdoors.
In Atom, Volume 4, Atom faces off against Ivan - a Russian military robot. Ivan, however, has been programmed with data collected from the fight between Mars and Atom.
What the human researchers in the manga didn't realise, was the code transmissions were a kind of highly abstracted machine level conversation. Regardless, the "anti-viral" commands were implemented into Ivan and, as a result, Ivan parrots the words Atom used back to it, causing Atom to deliberately hold back.

In AI cybersecurity terms, this is effectively an AI-on-AI prompt injection attack. Attempting to use the words of the AI against itself to perform malicious acts. Not only can this occur, but AI creators can plant "backdoor commands" into AI systems on creation, where a specific set of inputs can activate functionality hidden to regular users.

This is a key security issue for any company training AI systems, and has led many to reconsider outsourcing AI training of potential high-risk AI systems. Researchers, such as Shafi Goldwasser at UC Berkley are at the cutting edge of this research, doing work compared to the key encryption standards and algorithms research of the 1950s and 60s which have led to today's modern world of highly secure online transactions and messaging services.
From returning database entries, to controlling applied hardware, it is key that these dangers are fully understood on a deep mathematical, logical, basis or else we face the dangerous prospect of future AI systems which can be turned against users.
As AI further develops as a field, these kinds of attacks will need to be prevented, or mitigated against, to ensure the safety of systems that people interact with.
References:
Twitter pranksters derail GPT-3 bot with newly discovered “prompt injection” hack - Ars Technica (16/09/2023)
EVALUATING THE SUSCEPTIBILITY OF PRE-TRAINED LANGUAGE MODELS VIA HANDCRAFTED ADVERSARIAL EXAMPLES - Hezekiah Branch et. al, 2022 Funded by Preamble
In Neural Networks, Unbreakable Locks Can Hide Invisible Doors - Quanta Magazine (02/03/2023)
Planting Undetectable Backdoors in Machine Learning Models - Shafi Goldwasser et.al, UC Berkeley, 2022
#ai research#ai#artificial intelligence#atom the beginning#ozuka tezuka#cybersecurity#a106#atom: the beginning
19 notes
·
View notes
Text
How Can You Ensure Data Quality in Healthcare Analytics and Management?

Healthcare facilities are responsible for the patient’s recovery. Pharmaceutical companies and medical equipment manufacturers also work toward alleviating physical pain, stress levels, and uncomfortable body movement issues. Still, healthcare analytics must be accurate for precise diagnosis and effective clinical prescriptions. This post will discuss data quality management in the healthcare industry.
What is Data Quality in Healthcare?
Healthcare data quality management includes technologies and statistical solutions to verify the reliability of acquired clinical intelligence. A data quality manager protects databases from digital corruption, cyberattacks, and inappropriate handling. So, medical professionals can get more realistic insights using data analytics solutions.
Laboratories have started emailing the test results to help doctors, patients, and their family members make important decisions without wasting time. Also, assistive technologies merge the benefits of the Internet of Things (IoT) and artificial intelligence (AI) to enhance living standards.
However, poor data quality threatens the usefulness of healthcare data management solutions.
For example, pharmaceutical companies and authorities must apply solutions that remove mathematical outliers to perform high-precision data analytics for clinical drug trials. Otherwise, harmful medicines will reach the pharmacist’s shelf, endangering many people.
How to Ensure Data Quality in the Healthcare Industry?
Data quality frameworks utilize different strategies to prevent processing issues or losing sensitive intelligence. If you want to develop such frameworks to improve medical intelligence and reporting, the following 7 methods can aid you in this endeavor.
Method #1| Use Data Profiling
A data profiling method involves estimating the relationship between the different records in a database to find gaps and devise a cleansing strategy. Data cleansing in healthcare data management solutions has the following objectives.
Determine whether the lab reports and prescriptions match the correct patient identifiers.
If inconsistent profile matching has occurred, fix it by contacting doctors and patients.
Analyze the data structures and authorization levels to evaluate how each employee is accountable for specific patient recovery outcomes.
Create a data governance framework to enforce access and data modification rights strictly.
Identify recurring data cleaning and preparation challenges.
Brainstorm ideas to minimize data collection issues that increase your data cleaning efforts.
Ensure consistency in report formatting and recovery measurement techniques to improve data quality in healthcare.
Data cleaning and profiling allow you to eliminate unnecessary and inaccurate entries from patient databases. Therefore, healthcare research institutes and commercial life science businesses can reduce processing errors when using data analytics solutions.
Method #2| Replace Empty Values
What is a null value? Null values mean the database has no data corresponding to a field in a record. Moreover, these missing values can skew the results obtained by data management solutions used in the healthcare industry.
Consider that a patient left a form field empty. If all the care and life science businesses use online data collection surveys, they can warn the patients about the empty values. This approach relies on the “prevention is better than cure” principle.
Still, many institutions, ranging from multispecialty hospitals to clinical device producers, record data offline. Later, the data entry officers transform the filled papers using scanners and OCR (optical character recognition).
Empty fields also appear in the database management system (DBMS), so the healthcare facilities must contact the patients or reporting doctors to retrieve the missing information. They use newly acquired data to replace the null values, making the analytics solutions operate seamlessly.
Method #3| Refresh Old Records
Your physical and psychological attributes change with age, environment, lifestyle, and family circumstances. So, what was true for an individual a few years ago is less likely to be relevant today. While preserving historical patient databases is vital, hospitals and pharma businesses must periodically update obsolete medical reports.
Each healthcare business maintains a professional network of consulting physicians, laboratories, chemists, dietitians, and counselors. These connections enable the treatment providers to strategically conduct regular tests to check how patients’ bodily functions change throughout the recovery.
Therefore, updating old records in a patient’s medical history becomes possible. Other variables like switching jobs or traveling habits also impact an individual’s metabolism and susceptibility to illnesses. So, you must also ask the patients to share the latest data on their changed lifestyles. Freshly obtained records increase the relevance of healthcare data management solutions.
Method #4| Standardize Documentation
Standardization compels all professionals to collect, store, visualize, and communicate data or analytics activities using unified reporting solutions. Furthermore, standardized reports are integral to improving data governance compliance in the healthcare industry.
Consider the following principles when promoting a documentation protocol to make all reports more consistent and easily traceable.
A brand’s visual identities, like logos and colors, must not interfere with clinical data presentation.
Observed readings must go in the designated fields.
Both the offline and online document formats must be identical.
Stakeholders must permanently preserve an archived copy of patient databases with version control as they edit and delete values from the records.
All medical reports must arrange the data and insights to prevent ambiguity and misinterpretation.
Pharma companies, clinics, and FDA (food and drug administration) benefit from reporting standards. After all, corresponding protocols encourage responsible attitudes that help data analytics solutions avoid processing problems.
Method #5| Merge Duplicate Report Instances
A report instance is like a screenshot that helps you save the output of visualization tools related to a business query at a specified time interval. However, duplicate reporting instances are a significant quality assurance challenge in healthcare data management solutions.
For example, more than two nurses and one doctor will interact with the same patients. Besides, patients might consult different doctors and get two or more treatments for distinct illnesses. Such situations result in multiple versions of a patient’s clinical history.
Data analytics solutions can process the data collected by different healthcare facilities to solve the issue of duplicate report instances in the patients’ databases. They facilitate merging overlapping records and matching each patient with a universally valid clinical history profile.
Such a strategy also assists clinicians in monitoring how other healthcare professionals prescribe medicine to a patient. Therefore, they can prevent double dosage complications arising from a patient consuming similar medicines while undergoing more than one treatment regime.
Method #6| Audit the DBMS and Reporting Modules
Chemical laboratories revise their reporting practices when newly purchased testing equipment offers additional features. Likewise, DBMS solutions optimized for healthcare data management must receive regular updates.
Auditing the present status of reporting practices will give you insights into efficient and inefficient activities. Remember, there is always a better way to collect and record data. Monitor the trends in database technologies to ensure continuous enhancements in healthcare data quality.
Simultaneously, you want to assess the stability of the IT systems because unreliable infrastructure can adversely affect the decision-making associated with patient diagnosis. You can start by asking the following questions.
Questions to Ask When Assessing Data Quality in Healthcare Analytics Solutions
Can all doctors, nurses, agents, insurance representatives, patients, and each patient’s family members access the required data without problems?
How often do the servers and internet connectivity stop functioning correctly?
Are there sufficient backup tools to restore the system if something goes wrong?
Do hospitals, research facilities, and pharmaceutical companies employ end-to-end encryption (E2EE) across all electronic communications?
Are there new technologies facilitating accelerated report creation?
Will the patient databases be vulnerable to cyberattacks and manipulation?
Are the clinical history records sufficient for a robust diagnosis?
Can the patients collect the documents required to claim healthcare insurance benefits without encountering uncomfortable experiences?
Is the presently implemented authorization framework sufficient to ensure data governance in healthcare?
Has the FDA approved any of your prescribed medications?
Method #7| Conduct Skill Development Sessions for the Employees
Healthcare data management solutions rely on advanced technologies, and some employees need more guidance to use them effectively. Pharma companies are aware of this as well, because maintaining and modifying the chemical reactions involved in drug manufacturing will necessitate specialized knowledge.
Different training programs can assist the nursing staff and healthcare practitioners in developing the skills necessary to handle advanced data analytics solutions. Moreover, some consulting firms might offer simplified educational initiatives to help hospitals and nursing homes increase the skill levels of employees.
Cooperation between employees, leadership, and public authorities is indispensable to ensure data quality in the healthcare and life science industries. Otherwise, a lack of coordination hinders the modernization trends in the respective sectors.
Conclusion
Healthcare analytics depends on many techniques to improve data quality. For example, cleaning datasets to eliminate obsolete records, null values, or duplicate report instances remains essential, and multispecialty hospitals agree with this concept.
Therefore, medical professionals invest heavily in standardized documents and employee education to enhance data governance. Also, you want to prevent cyberattacks and data corruption. Consider consulting reputable firms to audit your data operations and make clinical trials more reliable.
SG Analytics is a leader in healthcare data management solutions, delivering scalable insight discovery capabilities for adverse event monitoring and medical intelligence. Contact us today if you want healthcare market research and patent tracking assistance.
3 notes
·
View notes