#Database Data Entry Services
Explore tagged Tumblr posts
Text
Streamline Your Business Operations By Outsourcing Database Data Entry Services

In the ever-changing world of business, precision and practicality are critical components. Data entry is one area where companies frequently find themselves spending excessive amounts of time. Large volumes of data can be tedious and error-prone to manually manage. This is where database data entry services become useful, providing a way to simplify company processes.
Nowadays, companies rely heavily on online databases for everything from marketing data to organizational efficiency. You must hire outside experts to handle database data entry since it is not practical for your business to hire professionals in-house.
Understanding Database Data Entry Services
The process of entering, organizing, and managing data in a database system is covered by database data entry services. This service eliminates the possibility of errors associated with manual data entry by handling massive volumes of information with precision and accuracy. The objective is to produce an easily navigable, neatly organized database that provides a solid basis for corporate operations and decision-making.
Almost every business uses database management systems, and every organization has a lot of data to handle. The difficult component is that outsourcing database data entry services is the ideal option if you want to establish a database management system and have a large database. The administration of the database itself is typically handled by your database management service provider.
Why Outsourcing Database Data Entry Services Is Important?
Outsourcing Database Data Entry Services often proves to be a more cost-effective solution, providing access to skilled professionals without the financial burden of an in-house team.
Outsourcing partners often invest in advanced technology and software tools. By outsourcing, businesses gain access to cutting-edge technology without the need for substantial investments, ensuring that data management processes are efficient and up-to-date.
Outsourcing Database Data Entry Services is not just a cost-cutting strategy; it's a strategic move that can propel your business toward greater efficiency and success. By entrusting data management to experts, businesses can navigate the complexities of data entry seamlessly, ultimately focusing on what matters most – achieving their business objectives.
Categories Of Outsourcing Database Data Entry Services
1. Data Input Services
2. Data Validation And Cleaning
3. Database Migration Services
4. Data Indexing And Archiving
5. Online And Offline Data Entry
6. Image And Document Data Entry
7. E-commerce Data Entry
8. Data Mining And Extraction
9. Form Data Entry Services
10. Customized Database Solutions
Process Follow In Database Data Entry Services
Understanding Project Requirements: Start by engaging in a thorough conversation to understand the client's data input requirements, volume, and intended results.
Scheduling The Project: Determine the necessary resources, such as the quantity of technology, tools, and data input specialists.
Data Security Protocols: Create and execute confidentiality agreements to protect confidential data. To safeguard customer information, put in place access limits, encryption, and other security measures.
Data Input And Collection: Collect data from various sources, including physical documents, digital files, and online forms. Utilize data entry professionals to input data accurately into the designated databases or systems.
Cleaning And Validation: To guarantee accuracy and integrity, put validation checks into action. Find and fix mistakes, tidy up and standardize data formats, and eliminate duplicate entries.
Quality Control: To uphold the highest standards, carry out routine quality control inspections.
Indexing And Archiving: Use methodical indexing to make information easily retrieved and analyzed. Assemble archives to save historical data while adhering to data retention guidelines.
Client Interaction: Keep lines of contact open with clients, answering their questions and offering updates on project milestones. To make sure that expectations are met by the client, hold frequent feedback meetings.
How Can We Benefit From Outsourcing Database Data Entry Services?
Outsourcing database data entry services can provide several benefits for businesses. Here are some advantages:
Value For Money: Hiring and training internal employees is frequently more expensive than outsourcing database data entry services. Businesses can reduce expenditures on things like office space, equipment, benefits, and salary.
Concentrate On Core Competencies: Product development, marketing, and customer service are examples of core business operations that your team can concentrate on through outsourcing. Time-consuming data entry jobs have the potential to take focus away from strategic concerns.
Accuracy And Quality: High standards of accuracy and quality are ensured by the specialization of professional outsourcing companies in data entry services. This is essential for preserving the accuracy of your data, cutting down on mistakes, and enhancing database integrity.
Availability To Professional Workforce: Data entry is a common area of competence for workers with training and experience from outsourcing businesses. This indicates that experts who can produce reliable and timely results are handling your data-entering tasks.
Scalability: You can scale your data entry requirements up or down based on business requirements with outsourcing. This flexibility is especially useful when managing varying workloads or during busy seasons.
Time Management: A specialized data entry crew can finish jobs faster and more effectively than a non-trained in-house workforce. As a result, data entry jobs can be completed more quickly, giving you more time to make smart business choices.
Increased Productivity And Efficiency: By enabling your staff to concentrate on activities that call for strategic thinking and decision-making, outsourcing database data entry can boost productivity and efficiency across the board for your company.
It's critical to carefully evaluate possible service providers before outsourcing to ensure they have a solid security record, a track record of success, and the capacity to fulfill your unique database data entry needs.
Source Of: https://dataentrywiki.blogspot.com/2024/02/streamline-your-business-operations-by-outsourcing-database-data-entry-services.html
#Database Data Entry#Database Data Entry Services#Outsource Database Data Entry#Professional Database Data Entry#Bulk Database Data Entry
0 notes
Text
Learn More About Outsourcing Database Data Entry Services

Database data entry services play a vital role in maintaining accurate and well-organized information, enabling businesses to make informed decisions and streamline their operations. Outsourcing database data entry can be cost-effective as it allows businesses to leverage the expertise of specialized service providers. Professional database data entry outsourcing company can often complete tasks more quickly due to their specialized skills, experience, and efficient processes. This blog gives you more knowledge about outsourcing database data entry services.
To know more visit https://latestbpoblog.blogspot.com/2024/02/learn-more-about-outsourcing-database-data-entry-services.html
#Database Data Entry#Database Data Entry Services#Database Data Entry Companies#Outsource Database Data Entry#Professional Database Data Entry#Bulk Database Data Entry
0 notes
Text
Building a reliable customer database is critical for business growth. This article explores how data entry services help achieve this by accurately organizing and managing customer information. Learn how these services reduce errors, ensure consistency, and provide quick access to essential data for marketing and sales. Discover the benefits of outsourcing data entry tasks to skilled professionals, saving time and enabling businesses to focus on core activities. Enhance your CRM system and make data-driven decisions with the help of expert data entry services.
0 notes
Text
Data Entry Services

Data Entry Expert offers cost-effective data entry services without compromising quality. So contact us to get cost-effective solutions.
Contact Us: Website: https://www.dataentryexpert.com Email: [email protected] Skype: data_expert Phone: +91 7948001664
#dataentryexpert#dataentryservices#dataentry#entrydata#dataentrywork#services#data#entry#database#dataanalytics#dataentryservice#leadgeneration#research#dataentrycompanies#dataentrycompany#dataentryindia#dataentryservicesprovider#socialmediamanagement
0 notes
Text
CapFriendly Alternative Sites MegaPost
(Last update: 07/27 - added CapSized.)
As we are all likely aware by now, the Washington Capitals have decided to ruin everyone's lives by purchasing and sunsetting CapFriendly. The site has gone dark as of July 10, 2024.
While the hockey community has experienced a similar loss before, with the death of Matthew Wuest and the subsequent loss of CapGeek, this is a markedly different situation that sets a troubling precedent - namely, that freely usable, public NHL data is now available to the highest bidder, who can then revoke access to the data at a minute's notice. Two things can coexist: we can be happy for the makers of CapFriendly that they are being compensated well for their services while also scorning the Washington Capitals organization for choosing to turn off CapFriendly entirely.
Under the cut, please find a list of free CapFriendly alternatives and other websites that contain NHL data. (In some cases, they are mostly free - however, most/all important information for lay analysis is available for free.) This list is dynamic and taking suggestions, so please feel free to send me any websites you find at @stereax and check the original post for updates!
PART 1: SALARY CAP TRACKERS
PuckPedia: The New CapFriendly
PuckPedia is the closest replacement to CapFriendly currently available. It contains salary cap information for all teams and players, draft pick information, several calculators including a buyout calculator and a pick value calculator, agent information, and more. They also run PuckDoku! The biggest strike against PuckPedia is its lack of simulators (Armchair GM, mock draft, or trade simulators); however, in the wake of the CapFriendly news, PuckPedia shared that an Armchair GM simulator is under active development. 07/05 Update: PuckGM is here! You can also react to prospective PuckGMs (thumbs up, thumbs down, laugh, think emojis).
CapSized: Labor of Love
Referred to me by @nonslipdoormat and billed as a "solo female developer's project" (nonslipdoormat IS said developer!), CapSized is a site that's designed similarly to CapFriendly. It has some features other sites lack, such as trade histories going back to 2003 (with some entries as old as 1964!) and a detailed transactions page again stretching YEARS into the past. The more you poke around, the more cool things you uncover. Its primary purpose is to be a "visual database", but calculators and an NHL GM mode are on the list of future additions. I'll be dead honest, I think this is my favorite cap-checker site because of all the extra utilities. Super excited to see where this project goes!
Referred to me by @reavenedges-lies. A "baby site" that has some of the basics of salary cap info, plus a buyout calculator, qualifying offer calculator, and trade proposal maker. The trade proposal maker is prone to error and seems to only be useful for graphics. It can be a useful site for some, but it would not be my first choice.
CapWages: CapFriendly Lite
Another alternative to PuckPedia that mimics CapFriendly in design and is more intuitive for users going directly from CapFriendly to an alternative site. Like PuckPedia, it now features a GM mode, but the GM mode is in beta and is not fully functional (it only shows contracts currently existing at the NHL level). Nevertheless, for checking salary cap info, it is very good and I recommend it. Also now has a buyout calculator.
CapSpace: Young Gun
BenchWarmers: Greenhorn
Similar to CapSpace but perhaps a little better in the design department. I like how, if you don't have an account, it acts like you're Kyle Dubas and has you watching Toronto and Carolina. Has a few neat stats (like "core four" which shows how much the four most expensive players are making) that I haven't seen easily replicated on other sites, but functionality is rather limited outside of that, which is why it's also not my first choice.
Spotrac: Another Salary Cap Checker
An alternative to PuckPedia for salary cap information. However, it lacks much of the information and functionality of PuckPedia or most other sites listed here.
PART 2: ADVANCED STATS
NaturalStatTrick: The Holy Grail of Stats
NaturalStatTrick, or NatStat for short, is a site that contains just about any stat you can think of for any team or player. It has a learning curve but is generally understood to be the most reliable stat tracker available for free. You can even view stats for individual games on it!
MoneyPuck: DTWoMeter and More
You know it from the Deserve-to-Win-o-Meter or its playoff odds rings, but MoneyPuck has a lot of useful data as well if you do a little browsing. Generally, I've heard that MoneyPuck is less accurate than NatStat, but is easier to use, especially on mobile.
HockeyViz: "If I Ever Sell, I Failed"
Home of the Simple Hockey Charts, HockeyViz has a visual for just about every stat out there. You've almost certainly seen some of them before. Most of them are completely free to the public! They're super useful for visualizing stats as more than "just numbers", allowing you to see exactly WHERE things are happening on the ice.
HockeyStatCards: GameScore Kings
Again, you've probably seen HockeyStatCards's GameScore charts. Using data from NatStat (see above) and an algorithm created by Dom Luszczyszyn, it provides a simple GameScore number that tells you whether a player is having a positive or negative impact on the ice for every game in the NHL.
PART 3: SPECIALIZED SITES
NHL Armchair GM: Building Rosters
This site allows you to Armchair GM a roster. Notably, it has a steeper learning curve than CapFriendly and does not have a forum or other way to easily save and publicize your Armchair GM moves. However, it can be useful to make Armchair GMs and have visuals for them.
NHL Entry Draft: With the First Overall Pick...
This site contains a ton of draft resources, from a mock draft simulator to scouting reports. Definitely a useful site for those who are interested in the entry draft. I've seen a couple of mock draft sites, but this one seems to have by far the easiest and arguably most expansive way to use it.
NHL Injury Viz: Rulers of LTIR
Here, you can explore the relationship between the injuries of players, their cap hits, and how teams did without them. Very useful when you're arguing that a certain player going down doomed the team.
PART 4: MORE TYPES OF DATA
HockeyReference: The Good Old Days
Hockey Reference is best used for surface level data about older players. It has some trivia sections as well, for if you ever wanted to know all players wearing certain jersey numbers, sharing a certain birthday, or hailing from Alaska.
EliteProspects: Every League Imaginable
Want to know the roster of a third-tier league in Quebec? EliteProspects has you covered. Literally every league on the face of the Earth, currently existing and not, EliteProspects has info on. Any player you can possibly name, EliteProspects has their stats from atom hockey all the way to the end of their career.
HockeyDB: Another Spot for Stats
HockeyDB, referred to me by @reavenedges-lies, is another solid site for looking up basic hockey stats. Also has a ton of leagues, similar to EliteProspects. Has a hockey card feature as well that shows you cards featuring the player you've looked up, which is neat!
PART 5: FORUMS
HFBoards: Hockey Forums
Probably the most well-known hockey forum out there. If you want to talk puck on a more forum-like site, similar to CapFriendly's forums, this is the one for you.
PART 6: CAPFRIENDLY ARCHIVES
SergeiFyodorov's CapFriendly FAQ Drive
Curated by @sergeifyodorov. Originally posted here and sent to me by @fellowshipofthegay. Archives of the CapFriendly FAQs!

Got a site that's not listed here? Let me know at @stereax and I'll add it! Remember: While CapFriendly may be going away, hockey analysis is here to stay!
337 notes
·
View notes
Text

CHECK THE FOLLOWING FOR PREVIOUS LORE INSTALLMENTS :CHAPTER ONE : RECALL. | EVENT : HELL WEEK. | CHAPTER TWO: THE MOLE. | HELL WEEK CLOSING BRIEF. | OPERATION WHAC-A-MOLE. | THE MOLE CLOSING BRIEF. | CHAPTER THREE : THE VILLAGE. | EVENT : CONTAGION CONTROL. | BOOK ONE : THE HALOCLINE. | CHAPTER FOUR : THE REPRIEVE. | CHAPTER FIVE : THE CALM BEFORE. | CHAPTER SIX : THE STORM.

PANDORA DIRECTIVE MEMORANDUM CLASSIFIED — INTERNAL DISTRIBUTION ONLY to : ALL AUTHORIZED OPERATIVES from : OFFICE OF THE DIRECTOR subject : OPERATION THALASSOPHOBIA
twelve hours ago, czernobog launched a full-scale invasion into atlantis, breaching perimeter defense systems and engaging agents of pandora in multiple sectors. the assault began with cybernetically-augmented foot soldiers entering through the hangar, then followed by coordinated mutant incursions across levels 01 through 09. their objectives included the dismantling of our command structure, retrieval of classified mutation data, mass destabilization of the facility, and the retrieval of our now declassified alien lifeform and namesake of our program, pandora. however, agents of pandora are not to be trifled with. thanks to the combined efforts of active combat units and support divisions, pandora successfully foiled the assault and eliminated key czernobog personnel such as velezlav zherdev and alexei dragunov. any surviving enemy units have been captured or eliminated. nonetheless, this victory comes at a great cost. confirmed fatalities include : rift — killed by czernobog mutants. mandela — killed by czernobog mutants. phoenix — killed by cybernetically-enhanced infantry at the hangar bay. oracle — sacrificed himself at the hangar bay. climax — killed by cybernetically-enhanced infantry at the hangar bay. elysium — killed by a czernobog mutant. jumpscare — killed by a czernobog mutant. other notable outcomes include : legion — out of commission. comatose state. bloodborn — out of commission. comatose state. prometheus — temporary death. alchemy — missing in action. surveillance shows him disappearing into thin air after evacuation into a pandora safehouse. his disappearance is being investigated for possible extradimensional, extraterrestrial or preternatural reasons. the service and bravery of our deceased agents directly contributed to the survival of over one-hundred fifty personnel and the preservation of humanity's greatest line of defense. their records are being archived with highest distinction. memorial proceedings will be announced following stabilization of atlantis, led by our temperance division and remaining porter models.
atlantis also sustained critical structural damage, including but not limited to :
> structural attrition on levels 01 to 02. > partial collapse of the corridor toward the gifted serum and cloning laboratory. > total loss of six exit corridors and 37% of ventilation systems. > entry into the command centre is currently unavailable due to compromise to its structural integrity. sloth agents and support staff will work in the war room for the meantime. > the library of alexandria is temporarily out of service and 45% of our archives have been destroyed. > partial loss of energy routing on levels 04 to 07. electricity is available but beware of disturbances and blackouts. > server systems and databases are currently only partially operational, however, our security and surveillance system are 100% functional. > our life model decoys have reduced numbers due to technopathic compromise by a czernobog agent. > destruction of various operative apartments and compromise of habitation utilities. [ agents with affected residence are suggested to find another undamaged residence to temporarily settle into while renovations commence. ]
reconstruction efforts have been started by our remaining derek and manny models, however, agents without current mission assignments are also asked to assist in repairs. if any operatives find other structural damages, please report them to your omega clearance channel.
[ MORE INFORMATION UNDER THE CUT. ]
while reconstruction efforts have began, pandora has also expedited various scientific operations. agents toxin, shepherd, elixir, and lifeweaver have been delegated to study biliquis and anomaly's mutations in hopes of improving the gifted serum without the need for the two-year isolation and physical conditioning period. agents goblin, killshot, charon, and gridlock have also been requisitioned to study czernobog's cloning technology and begin initial experimentations with trials on biological samples and uploaded memory by deceased agents. more information about these scientific endeavors will be made available once breakthroughs have been made.
however, perhaps the most important disclosure is the truth behind project pandora.
> pandora is an archivist, an alien species capable of storing biological, environmental, and cultural data within their own molecular structures. > her homeworld was destroyed by an invasive empire known as the starwalkers. > alongside another archivist, moryana, she fled across galaxies in search of safe havens and planets untouched by the starwalkers. > pandora crash-landed on earth in 1947 ( historically known as the roswell incident ) ; moryana's craft later crashed in 1959 ( believed to be responsible for the dyatlov pass incident ). > pandora was discovered and protected by human scientist dr. sieger ackermann who founded project pandora, naming the program after her. together, they began using her biological matrix to enhance and weaponize compatible human dna to create mutant soldiers as defense against possible future attack by the starwalkers. > moryana was intercepted by czernobog. his dna is believed to be extracted forcibly, resulting in unstable mutant offspring.
however, pandora also revealed that she is terminally deteriorating. it is finally disclosed that pandora's box is not just a training room, but also a biopsychic interface built to shelter her body and simulate potential threats and scenarios using what remains of her reality warping abilities.
and while pandora continues to help humanity by training and providing parts of herself to our operatives, she has asked for our assistance with retrieving moryana as potential means of biological repair— through inhabitation of moryana's form. pandora also implied an alternative, but we do not believe this is a choice she wants to make yet : selecting a viable human vessel.
nonetheless, the work is not over yet, agents. as soon as atlantis returns to at least 75% functionality, missions will be given out once again to take out czernobog's remaining forces and affiliates— until there is permanently nothing left of them. but please take these couple of days to mourn those we lost, to celebrate our victories, and to help in rebuilding our home. thank you, agents of pandora.

OOC INFORMATION.
holy shit ! another book is closed, agents ! this has been a rollercoaster of a season— from a beach episode, to a tournament arc, to agents getting kidnapped and another group fighting the clones of those kidnapped agents, to a fucking invasion into atlantis and the reveal to our real overarching plot involving aliens ! so much has happened, but i promise that the action will not stop. projectpandora still has so much to offer, and i can't wait for all of us to collaborate on what the future will bring. but as always, i just want to thank everyone for the continue support for our little rpg. i always say that this rp would be nothing without our amazing members who continue to participate, read, react, write, and plot in this community we have built and i truly do mean that. i have nothing but love for everyone who has been here with us since the beginning, for everyone who recently joined, and for everyone who joined sometime in between— i know, i know, these plots are insane and there's so much to read sometimes, but i can't help it !!! you all inspire me to create batshit plots all the time !!! but as for what's coming next : stay tuned for our chapter seven intro post, but it'll be basically be about the rebuilding efforts and future dash / discord missions. so feel free to start those aftermath threads and they will just be continued into chapter seven. also expect a patch update regarding the gifted serum and the cloning technology. and seven chapter in, but we'll also be giving out our first task ! and while it isn't mandatory, we do recommend that you do it as it will help you figure things out for the upcoming ninth chapter / third book finale. and chapter eight will be dedicated to moryana's retrieval and continuation of those dash / discord missions. but what i'm really excited for is our chapter nine event, but more on that later ! please like this once you've read, and thank you again everyone for another fun season !
7 notes
·
View notes
Text
The flood of text messages started arriving early this year. They carried a similar thrust: The United States Postal Service is trying to deliver a parcel but needs more details, including your credit card number. All the messages pointed to websites where the information could be entered.
Like thousands of others, security researcher Grant Smith got a USPS package message. Many of his friends had received similar texts. A couple of days earlier, he says, his wife called him and said she’d inadvertently entered her credit card details. With little going on after the holidays, Smith began a mission: Hunt down the scammers.
Over the course of a few weeks, Smith tracked down the Chinese-language group behind the mass-smishing campaign, hacked into their systems, collected evidence of their activities, and started a months-long process of gathering victim data and handing it to USPS investigators and a US bank, allowing people’s cards to be protected from fraudulent activity.
In total, people entered 438,669 unique credit cards into 1,133 domains used by the scammers, says Smith, a red team engineer and the founder of offensive cybersecurity firm Phantom Security. Many people entered multiple cards each, he says. More than 50,000 email addresses were logged, including hundreds of university email addresses and 20 military or government email domains. The victims were spread across the United States—California, the state with the most, had 141,000 entries—with more than 1.2 million pieces of information being entered in total.
“This shows the mass scale of the problem,” says Smith, who is presenting his findings at the Defcon security conference this weekend and previously published some details of the work. But the scale of the scamming is likely to be much larger, Smith says, as he didn't manage to track down all of the fraudulent USPS websites, and the group behind the efforts have been linked to similar scams in at least half a dozen other countries.
Gone Phishing
Chasing down the group didn’t take long. Smith started investigating the smishing text message he received by the dodgy domain and intercepting traffic from the website. A path traversal vulnerability, coupled with a SQL injection, he says, allowed him to grab files from the website’s server and read data from the database being used.
“I thought there was just one standard site that they all were using,” Smith says. Diving into the data from that initial website, he found the name of a Chinese-language Telegram account and channel, which appeared to be selling a smishing kit scammers could use to easily create the fake websites.
Details of the Telegram username were previously published by cybersecurity company Resecurity, which calls the scammers the “Smishing Triad.” The company had previously found a separate SQL injection in the group’s smishing kits and provided Smith with a copy of the tool. (The Smishing Triad had fixed the previous flaw and started encrypting data, Smith says.)
“I started reverse engineering it, figured out how everything was being encrypted, how I could decrypt it, and figured out a more efficient way of grabbing the data,” Smith says. From there, he says, he was able to break administrator passwords on the websites—many had not been changed from the default “admin” username and “123456” password—and began pulling victim data from the network of smishing websites in a faster, automated way.
Smith trawled Reddit and other online sources to find people reporting the scam and the URLs being used, which he subsequently published. Some of the websites running the Smishing Triad’s tools were collecting thousands of people’s personal information per day, Smith says. Among other details, the websites would request people’s names, addresses, payment card numbers and security codes, phone numbers, dates of birth, and bank websites. This level of information can allow a scammer to make purchases online with the credit cards. Smith says his wife quickly canceled her card, but noticed that the scammers still tried to use it, for instance, with Uber. The researcher says he would collect data from a website and return to it a few hours later, only to find hundreds of new records.
The researcher provided the details to a bank that had contacted him after seeing his initial blog posts. Smith declined to name the bank. He also reported the incidents to the FBI and later provided information to the United States Postal Inspection Service (USPIS).
Michael Martel, a national public information officer at USPIS, says the information provided by Smith is being used as part of an ongoing USPIS investigation and that the agency cannot comment on specific details. “USPIS is already actively pursuing this type of information to protect the American people, identify victims, and serve justice to the malicious actors behind it all,” Martel says, pointing to advice on spotting and reporting USPS package delivery scams.
Initially, Smith says, he was wary about going public with his research, as this kind of “hacking back” falls into a “gray area”: It may be breaking the Computer Fraud and Abuse Act, a sweeping US computer-crimes law, but he’s doing it against foreign-based criminals. Something he is definitely not the first, or last, to do.
Multiple Prongs
The Smishing Triad is prolific. In addition to using postal services as lures for their scams, the Chinese-speaking group has targeted online banking, ecommerce, and payment systems in the US, Europe, India, Pakistan, and the United Arab Emirates, according to Shawn Loveland, the chief operating officer of Resecurity, which has consistently tracked the group.
The Smishing Triad sends between 50,000 and 100,000 messages daily, according to Resecurity’s research. Its scam messages are sent using SMS or Apple’s iMessage, the latter being encrypted. Loveland says the Triad is made up of two distinct groups—a small team led by one Chinese hacker that creates, sells, and maintains the smishing kit, and a second group of people who buy the scamming tool. (A backdoor in the kit allows the creator to access details of administrators using the kit, Smith says in a blog post.)
“It’s very mature,” Loveland says of the operation. The group sells the scamming kit on Telegram for a $200-per month subscription, and this can be customized to show the organization the scammers are trying to impersonate. “The main actor is Chinese communicating in the Chinese language,” Loveland says. “They do not appear to be hacking Chinese language websites or users.” (In communications with the main contact on Telegram, the individual claimed to Smith that they were a computer science student.)
The relatively low monthly subscription cost for the smishing kit means it’s highly likely, with the number of credit card details scammers are collecting, that those using it are making significant profits. Loveland says using text messages that immediately send people a notification is a more direct and more successful way of phishing, compared to sending emails with malicious links included.
As a result, smishing has been on the rise in recent years. But there are some tell-tale signs: If you receive a message from a number or email you don't recognize, if it contains a link to click on, or if it wants you to do something urgently, you should be suspicious.
30 notes
·
View notes
Text
Caleb Ecarma and Judd Legum at Popular Information:
Several of Elon Musk’s associates installed at the Office of Personnel Management (OPM) have received unprecedented access to federal human resources databases containing sensitive personal information for millions of federal employees. According to two members of OPM staff with direct knowledge, the Musk team running OPM has the ability to extract information from databases that store medical histories, personally identifiable information, workplace evaluations, and other private data. The staffers spoke on the condition of anonymity because they were not authorized to speak publicly and feared professional retaliation. Musk Watch also reviewed internal OPM correspondence confirming that expansive access to the database was provided to Musk associates.
The arrangement presents acute privacy and security risks, one of the OPM staffers said. Among the government outsiders granted entry to the OPM databases is University of California Berkeley student Akash Bobba, a software engineer who graduated high school less than three years ago. He previously interned at Meta and Palantir, a technology firm chaired by Musk-ally and fellow billionaire Peter Thiel. Edward Coristine, another 2022 high school graduate and former software engineering intern at Musk’s Neuralink, has also been given access to the databases.
Other Musk underlings embedded at OPM following President Donald Trump’s inauguration include the agency’s new chief of staff, Amanda Scales, who until January was a human resources staffer at xAI, Musk’s artificial intelligence firm, and Brian Bjelde, who has spent the past 21 years at Musk's SpaceX, including the last 10 leading the human resources department. They are joined by Gavin Kliger, a former Twitter software engineer serving as a special advisor to the director of OPM, and Riccardo Biasini, a former software engineer at Musk’s tunneling venture, the Boring Company. OPM did not respond to a request for comment. Shortly after Trump took office, OPM installed Greg Hogan to serve as its new chief information officer (CIO). Hogan was tapped to replace OPM CIO Melvin Brown, who had accepted the job less than a month ago. The civil servants who oversee the OPM’s information technology services were then instructed to provide access to Musk's associates, according to the OPM staffers who spoke to Musk Watch. One of the OPM staffers received an email from the agency’s new leadership instructing them to give Musk’s team “access [to] the system as an admin user" and "code read and write permissions." “They have access to the code itself, which means they can make updates to anything that they want,” the staffer explained. USAJOBS, the federal government’s official hiring site, was one of the systems that Musk's associates were given access to. The database stores personal information — Social Security numbers, home addresses, employment records — provided by private individuals who have applied for federal jobs, regardless of whether the applicants went on to work for the government. Musk’s aides were also given access to the OPM’s Enterprise Human Resources Integration (EHRI) system. Contained within the EHRI are the Social Security numbers, dates of birth, salaries, home addresses, and job descriptions of all civil government workers, along with any disciplinary actions they have faced. “They’re looking through all the position descriptions… to remove folks,” one of the OPM staffers said of Musk’s team. “This is how they found all these DEI offices and had them removed — [by] reviewing position description level data.” Other databases Musk’s team has access to include USA Staffing, an onboarding system; USA Performance, a job performance review site; and HI, which the government uses to manage employee health care. “The health insurance one scares me because it's HIPAA [protected] information, but they have access to all this stuff,” the OPM staffer noted.
[...] A new server being used to control these databases has been placed in a conference room that Musk’s team is using as their command center, according to an OPM staffer. The staffer described the server as a piece of commercial hardware they believed was not obtained through the proper federal procurement process. There is a legal requirement that the installation of a new server undergo a Privacy Impact Assessment (PIA), a formal process to ensure the change would not create any security vulnerabilities. But in this instance, the staff believes there was no PIA. “So this application and corresponding hardware are illegally operating,” they added. On Friday, Reuters reported that some senior civil servants have been blocked from accessing the EHRI and other OPM systems, making it difficult for career OPM employees to know what Musk’s team has been examining or modifying. In the same report, the outlet revealed the team had moved sofa beds into the agency's headquarters to continue their work around the clock.
This should be a major national news scandal.
Elon Musk and the underlings he put in place at the Office of Personnel Management (OPM) have jeopardized data privacy and national security.
#Elon Musk#DOGE#Department of Government Efficiency#Trump Administration#Office of Personnel Management#USA Peformance#HIPAA#Enterprise Human Resources Integration#Amanda Scales#Data Breach#Privacy Impact Assessment#Data Privacy#Musk Coup
9 notes
·
View notes
Text
Learn More About Outsourcing Database Data Entry Services

The creation and maintenance of a database is crucial for any kind of business. Every day, the database that holds all of the essential data about the company should be updated and kept in good order. Such a database is necessary for every business to rely on for all of its operations and services. Given that maintaining the database requires data entry, this activity must be done. This database will enable your staff to provide better customer service.
What Is Database Data Entry Services?
The process of entering, updating, and maintaining data within a database system is offered by database data entry services. For companies and organizations that depend on precise and well-organized data to make decisions and optimize their processes, this service is essential.
Database data entry services play a vital role in maintaining accurate and well-organized information, enabling businesses to make informed decisions and streamline their operations. The specific services offered can vary based on the provider and the unique needs of the client.
Why Outsourcing Database Data Entry Services Is Important?
Outsourcing database data entry can be cost-effective as it allows businesses to leverage the expertise of specialized service providers. In many cases, outsourcing to regions with lower labor costs can result in significant savings compared to hiring and training in-house staff.
Professional database data entry outsourcing company can often complete tasks more quickly due to their specialized skills, experience, and efficient processes. This can be especially important when dealing with large volumes of data.
Outsourcing non-core tasks like data entry enables a company to concentrate on its core business activities. This allows employees to focus on strategic tasks that contribute directly to the company's growth and success.
Categories Of Outsourcing Database Data Entry Services
Outsourcing database data entry services can be categorized based on the nature of the data entry tasks and the industry-specific requirements. Here are some common categories of outsourcing database data entry services:
• Database of Reservations in Transports • Financial Database for Financial Records • Database of Legal Institutions • Online Examinations Schedule Database • Online Database of Websites • Database of Product Sales and Purchase • Medical Database of Patient’s Records
Work Procedure Follow In Outsourcing Database Data Entry Services
The work procedure followed in outsourcing database data entry services typically involves several steps to ensure accuracy, efficiency, and client satisfaction. While specific procedures may vary among outsourcing providers, here is a general overview of the common steps in the process:
Understanding Client Requirements: The first step involves a thorough understanding of the client's requirements. This includes clarifying the type of data entry tasks, the format of data, specific instructions, quality standards, and any other project-related details. Data Security And Confidentiality Agreement: Establishing a data security and confidentiality agreement is crucial. Both the outsourcing provider and the client must ensure that sensitive information remains secure and is handled in compliance with data protection regulations.
Project Planning And Resource Allocation: Based on the client's requirements, the outsourcing provider plans the project, allocates resources, and determines the workflow. This includes assigning tasks to specific data entry professionals or teams.
Data Collection And Verification: If the project involves data collection from various sources, the outsourcing team collects the required data and verifies its accuracy. This step is crucial for maintaining data quality and integrity.
Data Entry Process: The actual data entry process begins, when professionals input the collected or provided information into the designated databases, spreadsheets, or other platforms. This may involve online or offline data entry depending on the project requirements.
Quality Control And Accuracy Checks: Regular quality control checks are conducted to ensure the accuracy and completeness of the entered data. This may involve manual reviews, automated validation processes, or a combination of both.
Data Cleansing And Enrichment: If part of the project involves data cleansing and enrichment, the outsourcing team identifies and corrects errors, validates information, and supplements missing details to improve overall data quality.
Client Review And Feedback: Periodic reviews are conducted with the client to provide updates on the project's progress and to gather feedback. This ensures alignment with client expectations and allows for adjustments if needed.
Final Delivery: Upon completion of the data entry tasks and quality assurance processes, the finalized data is delivered to the client in the specified format and within the agreed-upon timeframe.
Get Benefited From Outsourcing Database Data Entry Services
Outsourcing database data entry services can offer several benefits to businesses, regardless of their size or industry. Here are some key advantages that organizations can gain by leveraging outsourced data entry services:
Cost Savings: Businesses can save money by outsourcing data entry work to areas with lower labor expenses. This removes the requirement for internal personnel hiring, training, and management, along with the related overhead expenses.
Focus On Core Activities: Businesses can reallocate internal resources and focus on strategic initiatives and core operations that lead to corporate success by outsourcing time-consuming and routine data entry tasks.
Access To Skilled Professionals: Outsourcing providers often have a team of skilled and experienced data entry professionals. This expertise ensures high-quality work, accuracy, and efficient handling of data, which may exceed the capabilities of an in-house team.
Scalability And Flexibility: Businesses can scale up or down their data entry operations through outsourcing in response to changes in workload, demand during specific seasons, or project specifications. This flexibility is especially beneficial for businesses that require different levels of data entry.
Improved Productivity And Efficiency: Dedicated outsourcing teams are often more efficient in handling data entry tasks due to their specialization, experience, and streamlined processes. This can lead to improved productivity and faster turnaround times.
Access To Advanced Technology: To enter data, outsourcing companies make investments in the newest infrastructure and technology. Access to cutting-edge equipment, software, and automated procedures can help businesses without requiring large upfront expenditures.
Risk Mitigation And Compliance: Reputable outsourcing companies follow data protection laws and put strong security measures in place. By doing this, the risks of data compromises, mistakes, and non-compliance are reduced and the confidentiality and integrity of the data are preserved.
Time Savings: Project completion times can be greatly shortened by outsourcing data entry work. This is especially helpful for companies who need to process a lot of data or have tight deadlines.
By considering these benefits, businesses can make informed decisions about outsourcing their database data entry services to enhance efficiency, reduce costs, and focus on their core competencies.
Source Link: https://latestbpoblog.blogspot.com/2024/02/learn-more-about-outsourcing-database-data-entry-services.html
#Database Data Entry#Database Data Entry Services#Database Data Entry Companies#Outsource Database Data Entry#Professional Database Data Entry#Bulk Database Data Entry
0 notes
Text
RFK Jr. says autism database will use Medicare and Medicaid info
The Department of Health and Human Services said in a statement on Wednesday that the NIH would team up with the Centers for Medicare & Medicaid Services (CMS) to create the database utilizing insurance claims, electronic medical records and data from wearable devices with health sensors, like smartwatches.
https://www.npr.org/2025/05/08/nx-s1-5391310/kennedy-autism-registry-database-hhs-nih-medicare-medicaid
Trump Administration Terminates CDC’s Infection Control Committee: NBC News
The committee provided 540 recommendations over its 30 years of existence, 90% of which were implemented to help slow the spread of infections in health care facilities.
https://www.huffpost.com/entry/trump-presidency-latest-updates_n_68029ae0e4b01dc12d4bde68/liveblog_681b7ce3e4b06f9a4f9fecc2
FDA Vaccines Division Now Led By COVID-19 Vaccine Critic
https://www.huffpost.com/entry/trump-presidency-latest-updates_n_68029ae0e4b01dc12d4bde68/liveblog_681a51e7e4b0981671add45f
RFK Jr. Tells CDC To Go All In On Bogus Vitamin ‘Cures’ For Measles
The health secretary has been promoting vitamin A and other unproven treatments for a disease that is highly preventable with a vaccine.
. . .
“Secretary Kennedy will be enlisting the entire agency to activate a scientific process to treat a host of diseases, including measles, with single or multiple existing drugs in combination with vitamins and other modalities,” HHS spokesperson Andrew Nixon said in a statement.
. . .
Research on vitamin A’s impact on measles in people without deficiencies remains inconclusive, but with Kennedy’s prompting, some parents in West Texas ― the center of the 900-person measles outbreak ― have given it to their children in high doses. Doctors in the area say many of those children have been showing signs of liver damage, a side effect of excessive vitamin A intake.
And on Monday, Kennedy said HHS was deploying doctors to Texas to treat measles with “aerosolized steroids with budesonide with clarithromycin and others.” Neither budesonide nor clarithromycin is proven to treat measles, and suggesting their use is dangerous, the American Academy of Pediatrics said in a blunt statement last month.
https://www.huffpost.com/entry/rfk-jr-measles-treatments_n_6815381de4b08215e5f697bc
ETA: Tariffs Are About to Hit Lifesaving Medical Equipment
“It’s really the most vulnerable of the most vulnerable…who need technologies to live.”
https://www.motherjones.com/politics/2025/04/trump-tariffs-medical-equipment-medicaid-dme/
3 notes
·
View notes
Text
The Strategic Role of Check-in Kiosks in Military Airport Terminals

Military airport terminals operate under heightened security and efficiency demands compared to their commercial counterparts. These facilities not only handle routine transport of service members but also play crucial roles in logistics, emergency deployments, and diplomatic missions. In such high-stakes environments, even minor inefficiencies or security lapses can have significant consequences.
To meet these challenges, many military terminals are turning to check-in kiosk technology—automated, self-service systems that streamline passenger processing and improve terminal security. These kiosks, equipped with advanced features such as biometric scanning, real-time data synchronization, and user-friendly interfaces, are reshaping the operational landscape of military air travel. In this blog, we explore how kiosk technology enhances security, boosts efficiency, improves user experience, and supports long-term cost-effectiveness and emergency readiness in military airport terminals.
Enhancing Security Protocols with Check-in Kiosks
Security is paramount in military environments, and check-in kiosks significantly contribute to strengthening existing protocols. These kiosks do more than expedite the check-in process—they integrate seamlessly with military-grade security systems to ensure rigorous identity verification and real-time data updates.
Biometric Integration for Identity Verification
One of the standout features of military check-in kiosks is biometric integration. Fingerprint scans, iris recognition, and facial recognition ensure that only authorized personnel gain access to secured areas. These systems eliminate the risks associated with lost or forged ID cards and allow for multi-factor authentication, which is critical in sensitive operations.
Biometric data is instantly matched against military personnel databases and watchlists, providing a higher level of accuracy and preventing unauthorized access. The process is not only secure but also faster and less intrusive than traditional methods, offering a seamless experience for users.
Real-Time Data Synchronization with Security Networks
Check-in kiosks in military terminals are linked to centralized security networks, allowing for real-time synchronization of data. When a service member checks in, their identity, assignment, and travel itinerary are cross-verified with military systems to detect inconsistencies or threats.
This instant communication enhances threat detection and tracking capabilities, allowing security personnel to respond swiftly to anomalies. Furthermore, in the event of a security breach, kiosks provide critical logs and timestamps to aid investigation and resolution.

Increasing Operational Efficiency in Terminal Management
Military terminals operate around tight schedules and high throughput. By automating check-in procedures, kiosks alleviate common bottlenecks and enhance operational efficiency.
Automated Boarding Pass and ID Issuance
Traditional check-in desks involve manual data entry and document verification, which can slow down the boarding process. In contrast, automated kiosks issue boarding passes and temporary access credentials within seconds, drastically reducing processing time.
Kiosks can print, scan, and digitally store documentation, minimizing the likelihood of human error. This not only improves accuracy but also enhances compliance with standardized military travel protocols.
Reduced Staff Workload and Resource Allocation
By handling repetitive check-in tasks, kiosks free up human resources for more critical responsibilities. Personnel previously tied to desk duties can be reassigned to areas such as tactical operations, logistics support, or passenger assistance.
This optimized resource allocation ensures that the terminal functions more smoothly, even during peak hours or large-scale deployments. It also reduces the risk of operational delays, contributing to overall mission readiness.
Improving User Experience for Military Personnel and Visitors
Ease of use is crucial in high-pressure environments. Military check-in kiosks are designed with user-centric interfaces, ensuring accessibility for all users, including service members, dependents, and visitors.
Multilingual Support and Accessibility Features
Military airports cater to diverse users from various linguistic and cultural backgrounds. Kiosks equipped with multilingual options ensure that language barriers do not impede check-in or access.
Moreover, features such as voice commands, screen magnification, and wheelchair-accessible interfaces make these kiosks usable for individuals with disabilities. This commitment to inclusivity aligns with military values and enhances the overall user experience.
24/7 Availability and Minimizing Congestion
Unlike staffed check-in counters, kiosks offer uninterrupted service around the clock. This is especially beneficial in military operations where flights and deployments can occur at odd hours or on short notice.
By distributing the check-in load across multiple kiosks, these systems minimize terminal congestion, allowing for smoother passenger flow and reduced wait times. This is particularly valuable during mobilizations, drills, or emergency evacuations.
Cost-Effectiveness and Long-Term Savings
Implementing kiosk systems in military terminals requires upfront investment, but the long-term financial benefits make a compelling case for adoption.
Reduction in Manual Processing Costs
Kiosks reduce the need for manual data entry, paper forms, and physical staffing, all of which incur recurring costs. Digital processes streamline administrative workflows and lower the chances of clerical errors, which can be costly and time-consuming to fix.
In addition, kiosks help reduce the environmental footprint of military operations by minimizing paper use—a growing priority in defense logistics.
Scalability to Meet Future Demands
Modern kiosk systems are built with modular and scalable designs, allowing for future upgrades without major overhauls. As military travel protocols evolve, new software features or hardware modules (e.g., upgraded biometric sensors or contactless payment capabilities) can be easily integrated.
This future-proofing makes kiosk systems a strategic investment, capable of adapting to shifting operational needs and technological advancements.

Supporting Emergency and Contingency Operations
Military terminals must remain operational under all circumstances, including crises. Kiosks offer resilience and flexibility during emergencies, supporting both evacuation and redeployment efforts.
Rapid Reconfiguration for Emergency Protocols
In the event of a crisis—whether it’s a natural disaster, base lockdown, or global conflict—check-in kiosks can be rapidly reprogrammed to follow new protocols. For example, they can be configured to prioritize certain personnel categories, enable emergency passes, or facilitate health screenings during pandemics.
This capability allows terminals to maintain order and operational continuity, even in high-stress environments.
Reliable Communication Channels for Critical Updates
During emergencies, timely and accurate communication is essential. Kiosks can function as broadcast hubs, displaying critical alerts, evacuation routes, or mission updates directly on the screen.
Some systems can also send automated SMS or email updates to personnel, ensuring that everyone receives the necessary information regardless of their physical location within the terminal. This functionality is invaluable during fast-moving operations where traditional communication lines may be overloaded or unavailable.
Conclusion
Check-in kiosks are no longer just a convenience feature—they are a strategic asset in military airport terminals. From strengthening security with biometric authentication and real-time data sync, to improving operational efficiency and delivering a seamless user experience, kiosks represent a significant leap forward in military logistics technology.
They not only reduce costs and optimize personnel usage, but also enhance readiness and resilience during emergencies. With scalable architectures and support for the latest security features, kiosk systems are well-positioned to meet the future demands of military air transport.
For defense organizations aiming to modernize their infrastructure and improve mission efficiency, adopting kiosk technology is not just an option—it’s a mission-critical necessity.
#kiosk#technology#software#business#development#programming#productivity#airport#check in kiosk#tech#techtrends#selfservicekiosk#kioskmachine#innovation#kiosks#panashi#techinnovation#digitaltransformation
2 notes
·
View notes
Text
Immigration Services in Thailand
1.1 Statutory Foundations
Immigration Act B.E. 2522 (1979): Primary legislation
Ministerial Regulations: 47 implementing regulations (updated 2023)
Royal Decrees: Special provisions for investment/retirement
1.2 Organizational Structure
Immigration Bureau: Under Royal Thai Police
Headquarters (Chaeng Wattana, Bangkok)
76 Provincial Offices
32 Border Checkpoints
Specialized Units:
Visa Division (Section 1)
Extension Division (Section 2)
Investigation Division (Section 3)
2. Core Visa Categories and Processing
2.2 Special Visa Programs
SMART Visa: 4-year stay for experts/investors
LTR Visa: 10-year privilege visa
Elite Visa: 5-20 year membership program
3. Application Procedures
3.1 Document Authentication
Notarization Requirements:
Home country documents
Thai Ministry of Foreign Affairs legalization
Translation Standards:
Certified translators
Embassy verification
4. Digital Transformation Initiatives
4.1 Online Systems
e-Extension: Pilot program for 12 visa types
90-Day Reporting: Online portal and mobile app
TM30 Automation: Hotel API integration
4.2 Biometric Implementation
Facial Recognition: At 6 major airports
Fingerprint Database: 10-print system since 2018
Iris Scanning: Testing at Suvarnabhumi
5. Compliance and Enforcement
5.1 Monitoring Systems
Overstay Tracking: Real-time alerts after 7 days
Visa Run Detection: Algorithmic pattern analysis
Work Permit Integration: MOE-Immigration data sharing
6. Provincial Variations
6.2 Special Economic Zones
Eastern Economic Corridor: Fast-track processing
Border Provinces: Cross-border worker programs
7. Specialized Services
7.1 Corporate Immigration
BOI Fast Track: 7-day work permit processing
Regional HQ Packages: Multiple-entry privileges
Startup Visa: DEPA-endorsed companies
7.2 Family Reunification
Dependent Visas: Spouse/children under 20
Parent Visas: Financial guarantee requirements
Thai National Sponsorship: Income thresholds
8. Emerging Trends (2024 Update)
8.1 Policy Developments
Digital Nomad Visa: Expected Q4 2024
Airport Automated Clearance: Expansion to 8 more nationalities
Visa Fee Restructuring: Proposed 15-20% increase
8.2 Technological Advancements
Blockchain Verification: For document authentication
AI-Assisted Processing: Risk assessment algorithms
Mobile Biometrics: Pilot for frequent travelers
9. Strategic Considerations
9.1 Application Optimization
Document Preparation:
6-month bank statement continuity
Property lease registration
Timing Strategies:
Avoid holiday periods
Pre-submission checks
9.2 Compliance Management
Record Keeping:
Entry/exit stamps
TM30 receipts
Advisory Services:
Licensed lawyers vs agents
BOI-certified consultants
#thailand#immigration#immigrationlawyers#visa#visainthailand#immigrationinthailand#immigrationlawyersinthailand#thai#thaivisa#immigrationservices
2 notes
·
View notes
Text
How to Ensure the Quality of Data Entry Services

Data entry services demand high quality and accuracy for professionals to gain the right information at the right time. Partnering with an outsourcing data entry company maintains this quality and accuracy level, allowing organizations to have an organized database. Here are some tips that can help enhance the accuracy of the data entry process and streamline business operations.
#data entry services#data entry company#outsource data entry#data digitalization#data entry for real estate#invoice data entry service#document data entry services#ecommerce data entry services#outsource data entry services#medical data entry
2 notes
·
View notes
Text
I'd rather have been asleep at 1:40am instead of laying there thinking about how uncertain and scared I feel right now, but I was laying there feeling uncertain and scared and realized I have no idea what people that work in offices DO.
I've only worked retail/customer service outside of the military and even while working in an office in the military, I had nothing to do.
At first I was put in one office that didn't need me so they just said "Here... Manage these files." and I was like "..... how, exactly??" and ended up retyping the labels for all of them because some were wrong and there was nothing else for me to do.
Then they gave me the personnel database. I rebuilt it and made it accessible in two days, and that was it. After that, I filled out orders for one person once. The only way I had anything to DO was by becoming the mail clerk which is another customer-facing, cyclically repetitive task that is never done and needs redone in the same way every day. After the mail was done, which took about two hours, I would leave or go sit in my office with nothing to do because the database was my whole job and it was DONE. It wouldn't need changed until the software was updated and that wouldn't be for years.
I had a once-a-week task of making a physical copy of the server which meant going into a closet, popping a tape into a machine, and waiting. I had to sit there with it. There was nothing else to do. I got in trouble for coloring in a coloring book while waiting for the backups to write and I was like "........ What am I SUPPOSED to do, then?????" "Work on the database!" "It's DONE........"
If it's SQL stuff do people sit around until the boss says "Hey, I need to know how much we spent on avocado toast this month." and then whip up a report real quick and wait for the boss to want a report on something else? What about when the boss doesn't need a report?
What do IT people do when things are working smoothly?
I can understand data entry, that would be like "Here we have all these waivers that were signed for the indoor trampoline business and these need plugged into the database manually because the online one was down so they're on paper." or something like that but what about when the online waivers do work what do they do then?
?????
It's like that episode of Seinfeld where George gets an office job but just sits there all day because he has no idea what he's supposed to be doing, no one tells him, and he eventually gets fired because he didn't do anything.
13 notes
·
View notes
Text
ISRAEL REALTIME - "Connecting the World to Israel in Realtime"
After Shabbat - Nov. 25 - Shavua tov
🟠 HOSTAGE RELEASES REMAIN ON HOLD BY HAMAS
🔸CEASEFIRE ENDS AT MIDNIGHT IF NO PROGRESS? (N12) Israel sent a message to Hamas: if the abductees are not released by midnight - the ceasefire will end - per Al Jazeera. (( Interestingly this is being reported by Al Jazeera and Al Arabiya Arab news networks as a statement by Israel made via Israel Channel 12, but was a commentary statement made by Israel’s political commentator for Channel 12 Amit Segal - no official source for such a statement as far as we can tell. Did Israel’s Channel 12 political commentator just set Israeli policy and threaten Hamas? And from 2 items below - effectively? ))
🔸ISRAEL SAYS… A political source: "All the claims of Hamas as if Israel violated the agreement are lies. This is a propaganda attempt by Hamas. Israel has met all its obligations. Hamas is embarrassing the mediators - Egypt and Qatar."
🔸HAMAS BACKING DOWN? A senior Hamas official, Osama Hamdan, said a few minutes ago to Al-Arabia network: "The exchange steps (the release of the abductees and prisoners) will be completed, after we receive the answers we requested from the mediators."
🔸TO HAMAS’S CLAIMS, ISRAEL SAYS… Regarding the release of the terrorists: Israel claims that it did not undertake to release based on seniority, but rather a sort of statement that it might do so. Regarding the trucks to north Gaza: they passed the Rafah crossing -Israel is not responsible for their arrival to the north, but for allowing their entry. And it happened.
🔸MAGEN DOVID ODOM SAYS… the release procedure is not in sight at the moment: First, Hamas directs the Red Cross where to go to receive the Israeli hostages - and also transfers their details. Unlike yesterday, it has not yet been transferred the meeting point. MDA has tried to contact the Red Cross, but they are not answering.
◾️PALESTINIANS AWAITING PRISONER RELEASE SHOT IN FRONT OF PRISON… Riots by Palestinians in front of Ofer prison while waiting for the release of the Hamas prisoners. 3 were wounded by our forces' live fire to disperse the rioters.
◾️ISRAEL SOCIAL NEWS CHANNEL HACK-ATTACKED BY YEMEN HACKERS… One of Israel’s top Arab monitoring social news channels was attacked on Shabbat and partially hacked - with a channel bot taken over. Those operating Israeli channels on social media are advised to increase their security - make sure to activate 2 factor authentication and only use automated management tools such as channel bots if absolutely necessary. (The channel is back is service.)
◾️ISRAEL HACKERS TAKE OUT IRANIAN HACKERS… WeRedEvils says “We managed to permanently disable the group of Iranian and Yemeni hackers "Tofan". Those hackers stole sensitive details of tens of thousands of Israelis and was involved in the disclosure of information and business damage to more than 40 companies - and also harmed quite a few soldiers and sent threatening messages to hundreds of thousands of Israelis. We received a request from a special body to attack them and delete their data, databases in the order of 50GB, and we succeeded in this task.”
23 notes
·
View notes
Text
Atom: The Beginning & AI Cybersecurity

Atom: The Beginning is a manga about two researchers creating advanced robotic AI systems, such as unit A106. Their breakthrough is the Bewusstein (Translation: awareness) system, which aims to give robots a "heart", or a kind of empathy. In volume 2, A106, or Atom, manages to "beat" the highly advanced robot Mars in a fight using a highly abstracted machine language over WiFi to persuade it to stop.

This may be fiction, but it has parallels with current AI development in the use of specific commands to over-run safety guides. This has been demonstrated in GPT models, such as ChatGPT, where users are able to subvert models to get them to output "banned" information by "pretending" to be another AI system, or other means.
There are parallels to Atom, in a sense with users effectively "persuading" the system to empathise. In reality, this is the consequence of training Large Language Models (LLM's) on relatively un-sorted input data. Until recent guardrail placed by OpenAI there were no commands to "stop" the AI from pretending to be an AI from being a human who COULD perform these actions.
As one research paper put it:
"Such attacks can result in erroneous outputs, model-generated hate speech, and the exposure of users’ sensitive information." Branch, et al. 2022

There are, however, more deliberately malicious actions which AI developers can take to introduce backdoors.
In Atom, Volume 4, Atom faces off against Ivan - a Russian military robot. Ivan, however, has been programmed with data collected from the fight between Mars and Atom.
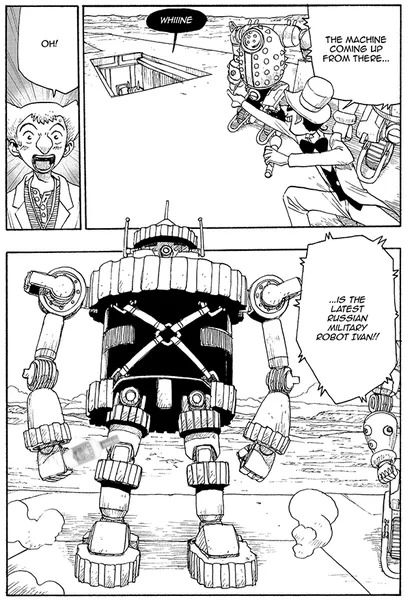
What the human researchers in the manga didn't realise, was the code transmissions were a kind of highly abstracted machine level conversation. Regardless, the "anti-viral" commands were implemented into Ivan and, as a result, Ivan parrots the words Atom used back to it, causing Atom to deliberately hold back.

In AI cybersecurity terms, this is effectively an AI-on-AI prompt injection attack. Attempting to use the words of the AI against itself to perform malicious acts. Not only can this occur, but AI creators can plant "backdoor commands" into AI systems on creation, where a specific set of inputs can activate functionality hidden to regular users.

This is a key security issue for any company training AI systems, and has led many to reconsider outsourcing AI training of potential high-risk AI systems. Researchers, such as Shafi Goldwasser at UC Berkley are at the cutting edge of this research, doing work compared to the key encryption standards and algorithms research of the 1950s and 60s which have led to today's modern world of highly secure online transactions and messaging services.
From returning database entries, to controlling applied hardware, it is key that these dangers are fully understood on a deep mathematical, logical, basis or else we face the dangerous prospect of future AI systems which can be turned against users.
As AI further develops as a field, these kinds of attacks will need to be prevented, or mitigated against, to ensure the safety of systems that people interact with.
References:
Twitter pranksters derail GPT-3 bot with newly discovered “prompt injection” hack - Ars Technica (16/09/2023)
EVALUATING THE SUSCEPTIBILITY OF PRE-TRAINED LANGUAGE MODELS VIA HANDCRAFTED ADVERSARIAL EXAMPLES - Hezekiah Branch et. al, 2022 Funded by Preamble
In Neural Networks, Unbreakable Locks Can Hide Invisible Doors - Quanta Magazine (02/03/2023)
Planting Undetectable Backdoors in Machine Learning Models - Shafi Goldwasser et.al, UC Berkeley, 2022
#ai research#ai#artificial intelligence#atom the beginning#ozuka tezuka#cybersecurity#a106#atom: the beginning
19 notes
·
View notes