#Distributed technology
Explore tagged Tumblr posts
Text
#ai#artificial intelligence#digital#evolution#technology#next evolution#distributed technology#smartchain
0 notes
Text

YES BECAUSE SHOWCASING IS SUCH AN UNFAMILIAR WORD
#I didn’t think part of being an engineer would come with the side effect of hating technology sometimes#bruh it’s a lab report on pressure distribution in supersonic nozzles#I DONT THINK ANYONE READING THAT WOULD NOT KNOW THE WORD SHOWCASING
19 notes
·
View notes
Text
5 Common Crypto Investment Mistakes and How to Avoid Them.
With its potential for high returns comes equally high risk. New investors often find themselves making critical mistakes that can impact their financial health. We'll explore five common mistakes.
Investing in cryptocurrency can be both thrilling and daunting. With its potential for high returns comes equally high risk. New investors often find themselves making critical mistakes that can impact their financial health. Here, we’ll explore five common errors and provide in-depth guidance on how to avoid them. 1. Lack of Research and Due Diligence Mistake: Jumping into investments without…

View On WordPress
#Altcoin Investment#Altcoins#Avoid FOMO#Avoiding Crypto Scams#Beginner’s Guide to Crypto#Blockchain Technology#Crypto Community#Crypto Investment#Crypto Investment Strategy#Crypto News#Crypto Portfolio#Crypto Research Tips#Crypto Scams#Crypto Whitepapers#Cryptocurrency Investing#Cryptocurrency Red Flags#Dollar-Cost Averaging#Financial Advice#How to Spot Crypto Scams#Identifying Genuine Crypto Projects#Investing in Cryptocurrency#Investing Tips#Legitimate Crypto Projects#Meme Coins#Reputable Crypto Exchanges#Risk Management#Secure Investments#Token Distribution
2 notes
·
View notes
Text








Death Stranding Distribution Centre
44 notes
·
View notes
Text
desperately need to go back to the time when the geronimo stilton/thea sisters books were peak fiction
#THEY WERE SO GOOD I LOVED THE ILLUSTRATIONS AND THE CHARACTER DESIGNS AND THE FUN AND THE MAGIC#no idea if anyone remembers the special edition hardback books where they went to fantasy worlds#just found some pdfs of the books i’m tempted to read them again for old times sakes#also the technology and fantasy elements were all chefs kiss#my fav one i think is the one where they go to russia for the dance competition i was obsessed#also geronimo stilton being a reporter kinda kickstarted my interest in journalism at the time#started reading way more of the young people’s newspapers my old school distributed so thanks ig#ugh those books were just so fun and cute and exciting and silly the illustrations were cute the different fonts used were interesting ajdh#also creepella von cacklefur. absolute queen#valeramblings
23 notes
·
View notes
Text
I don't consider rewritable CD's and rewritable DVD's to be obsolete. They are way too fucking novel and rad to be obsolete.
#2024#CD-RW#Rewritable CD#The money goes toward the novelty factor.#And limited-term indie game distribution in the apocalypse; should it come down to that.#Actually one year I made a stupid sort game and burned it onto a CD for a gift.#NEVER obsolete#older technology#CD's#DVD's
2 notes
·
View notes
Text

Amsco Systems AMTS advertisement, 1975.
15 notes
·
View notes
Text
ngl i get way more mad at reactions to Just Stop Oil activities than the actual actions they took. like stop being patronising to these ppl who are desperate for more people to actually listen and do something
#tweets like 'if they spent their time builidng wind farms they'd be more successful than if they paint stonehenge orange'#like. wtf do you think they're doing. this IS them trying to get more ppl to build wind farms. because no one was listening before#and also sidenote building windfarms will do nothing if we don't adjust how we use and distribute energy#technological solutions cannot solve climate change. capitalism NEEDS constant growth to stay stable#and constant growth is impossible in a world with finite resources and attempting it will lead further into environmental destruction#but accepting that would mean changing your way of living and world view and some ppl would rather drown in the next flood than do that#emma talks
2 notes
·
View notes
Text

#saudi arabia#petrodollar#us dollar#global economy#oil trade#currency exchange#digital currency#project mbridge#international trade#economic shift#bitcoin transactions#cross-border payments#distributed ledger technology#central banks#global finance
4 notes
·
View notes
Text
01001000 01100101 01110010 01100101 00100000 01001011 01101001 01110100 01110100 01111001
By:
instagram
#robotics#robot pets#robots#robotics technology#robotics club#distribute#robotics engineering#robot art#interactive art#Instagram#cats#cats of tumblr#cat aesthetic#cat
2 notes
·
View notes
Text
#ai#artificial intelligence#digital#evolution#technology#smartchain#distributed technology#next evolution
1 note
·
View note
Text
Optimize Your Ceramic & Faucets Business with ERPNext Solutions by Sigzen
ERPNext offers an ideal solution for businesses in the ceramics and faucets industry, delivering a tailored, robust platform designed to streamline various operational processes. This powerful ERP software facilitates seamless management of inventory, production, sales, and procurement, while also providing comprehensive financial management tools. Its ability to integrate and automate these key…
View On WordPress
#business optimization#Ceramics Industry#Digital Transformation#ERP Software#ERPNext#Faucets Business#Financial Management#Inventory Management#Production Planning#Sales Distribution#Sigzen Technologies
2 notes
·
View notes
Text
If it is inaccessible to the poor, it is neither radical nor revolutionary.
— John Herrera
#quotes#radical change is for everyone#the future is here it's just unevenly distributed william gibson#politics#technology#silicon valley
5 notes
·
View notes
Text
Cybersecurity in Power Systems: Safeguarding Transmission and Distribution Infrastructure
Introduction:
In an era dominated by technology, the power industry is undergoing a transformation, with the integration of smart grids and digital solutions becoming increasingly prevalent. However, this digital evolution brings with it a new set of challenges, particularly in the realm of cybersecurity. Power systems, including transmission and distribution infrastructure, are critical components of our modern society, making them prime targets for cyber threats. In this blog post, we will delve into the importance of cybersecurity in power systems and explore measures to safeguard transmission and distribution infrastructure.

Understanding the Landscape:
Power systems, encompassing transmission and distribution, are the backbone of any nation's infrastructure. As these systems become more interconnected and reliant on digital technologies, the vulnerability to cyber threats escalates. Transmission and distribution manufacturers in India are at the forefront of adopting innovative solutions to enhance the efficiency of power systems. However, with this increased connectivity comes the imperative need to fortify these systems against cyber attacks.
The Role of Cybersecurity in Power Systems:
Protecting Critical Infrastructure:
Cybersecurity plays a pivotal role in protecting critical infrastructure, especially in the power sector. Transmission and distribution manufacturers in India are recognizing the significance of robust cybersecurity measures to safeguard their equipment and networks.
Securing Outdoor Support Insulators:
Outdoor support insulators are crucial components in power systems, providing structural support and insulation. Cyber threats targeting these insulators could compromise the integrity of the entire power grid. Implementing cybersecurity protocols ensures the resilience of these components against potential attacks.
High Voltage Primary Bushing Outdoor Manufacturers in India:
Manufacturers producing high voltage primary bushings outdoors are well-aware of the challenges posed by cyber threats. Implementing stringent cybersecurity measures is imperative to prevent unauthorized access and manipulation of these critical components.
Addressing Vulnerabilities in Fuse Cutouts:
Fuse cutouts are essential for protecting power distribution systems from overcurrents. However, these components are susceptible to cyber threats that could disrupt their functionality. Cybersecurity measures are crucial in identifying and addressing vulnerabilities in fuse cutouts.
Cyber Threats in Power Systems:
Malware and Ransomware Attacks:
Malicious software and ransomware attacks pose a significant threat to power systems. These attacks can disrupt operations, compromise sensitive data, and demand ransom payments. Implementing robust cybersecurity measures is essential to mitigate the risk of malware and ransomware infiltrations.
Phishing and Social Engineering:
Phishing attacks and social engineering tactics target human vulnerabilities within organizations. Employees in transmission and distribution manufacturers in India must be educated on recognizing and avoiding these cyber threats to prevent unauthorized access to critical systems.
Insider Threats:
Insider threats, whether intentional or unintentional, can pose a severe risk to power systems. Establishing comprehensive access controls, monitoring systems, and conducting regular employee training can help mitigate the potential impact of insider threats.
Safeguarding Strategies:
Network Segmentation:
Implementing network segmentation is crucial to isolate and contain cyber threats. This strategy ensures that even if one part of the network is compromised, the entire system remains secure.
Regular Security Audits:
Conducting regular security audits is essential for identifying vulnerabilities and weaknesses in power systems. Transmission and distribution manufacturers in India should prioritize periodic assessments to stay ahead of evolving cyber threats.
Employee Training Programs:
Employees play a crucial role in cybersecurity. Training programs should focus on raising awareness about potential threats, recognizing phishing attempts, and promoting a security-conscious culture within the organization.
Advanced Authentication Protocols:
Implementing advanced authentication protocols, such as multi-factor authentication, adds an extra layer of security to prevent unauthorized access to critical systems.
Conclusion:
As power systems evolve with technological advancements, the need for robust cybersecurity measures becomes paramount. Transmission and distribution manufacturers in India must prioritize safeguarding their infrastructure against cyber threats to ensure the continuous and reliable delivery of power. From outdoor support insulators to high voltage primary bushings outdoors and fuse cutouts, every component plays a critical role in the functioning of power systems and requires protection from potential cyber attacks.
In the face of evolving cyber threats, a proactive approach to cybersecurity is the key to resilience. By adopting advanced cybersecurity measures and staying abreast of the latest developments in the field, Radiant Enterprises and other stakeholders in the power industry can fortify their transmission and distribution infrastructure, contributing to a secure and sustainable energy future.
#Transmission and Distribution Manufacturers in India#Outdoor Support Insulator#High Voltage Primary Bushing Outdoor Manufacturers in India#Fuse Cutouts#epoxy insulator#epoxy bushing#electricity#fuse cutouts#smart grid sensor#railway technology companies#train operating companies#locomotive#tramways#metro systems#traffic infrastructure
6 notes
·
View notes
Text
A point-to-point long-distance quantum key distribution (QKD) over a distance of 1,002 km has been achieved by scientists from the University of Science and Technology of China (USTC) of the Chinese Academy of Sciences (CAS), and their collaborators from Tsinghua University, Jinan Institute of Quantum Technology, and Shanghai Institute of Microsystem and Information Technology (SIMIT), CAS. This milestone not only sets a new world record for non-relay QKD but also provides a solution for high-speed intercity quantum communication. The results were published in Physical Review Letters on May 25th.
QKD is based on the principles of quantum mechanics and enables secure key distribution between two remote parties. When combined with the "one-time pad" encryption method, it can achieve the highest level of security for confidential communication. However, the distance of QKD has been limited by factors such as the channel loss and system noise.
The twin-field QKD (TF-QKD) using sending-or-not-sending (SNS) protocol was demonstrated in the experiment, improving the relation between the key rate and channel transmittance from a linear η to its square root η. Therefore, it can achieve a much longer secure distance than traditional QKD protocols.
To achieve long-distance QKD, the research team collaborated with Yangtze Optical Fiber and Cable Joint Stock Limited Company (YOFC) and used ultra-low-loss fiber based on pure silica core technology, which achieved a maximum attenuation of 0.16 dB/km. SIMIT developed ultra-low-noise superconducting single-photon detectors.
By implementing multiple filters at temperatures of 40 K and 2.2 K to suppress dark counts caused by thermal radiation, the noise of the single-photon detectors was reduced to around 0.02 cps. Furthermore, the team also developed a dual-band phase estimation scheme to avoid the spontaneous Raman scattering noise, reducing the system noise to below 0.01 Hz.
Based on the aforementioned technological developments, the team achieved TF-QKD over a record distance of 1,002 km, with a key rate of 0.0034 bps. This work not only verifies the feasibility of the SNS-TF-QKD scheme at extremely long distances but also demonstrates that this protocol can achieve high key rates in many practical scenarios.
The success of this study holds significant implications for the advancement of secure quantum communication. It opens up new possibilities for long-distance quantum key distribution and paves the way for the realization of high-speed intercity quantum communication networks.
4 notes
·
View notes
Text
Since people are sharing. Why not adding more :)
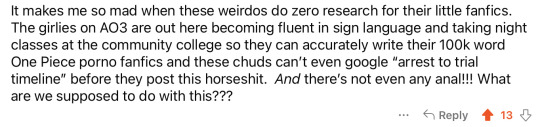
This is why I read the reddit comments
#stuff I research for one fanfic#not even smut just fanfics#stone age religion through Europe#copper age religion and cultural and societal development through Eurasia and Africa#Scandinavian and East Europe folklore#all the Celtic/ Greek/ Scandinavian/ Egyptian/ India/ China and Japan pantheon of gods from the Copper age to the first millennium#a comparative study of all the horned divine and spiritual creatures in human culture for a period of 5 millennia#the history of Ancient Roman expansionism#Babylonian and Canaan gods evolution through pre-historical period#Metallurgy technological history and its various technics through each culture#Prehistorical medicinal knowledge and herbs available at that time#shamanism and druidism because why not doing it as well#architectural and clothing fashion for a period of 6000 years focused on Celtic and also Chinese and Japanese culture#artisanal resource and art of war in Copper and Iron age#naming and languages evolution in pro-Celtic civilization#Hinduism genesis with all the exploits of Shiva#bloody Dashka story#Gaul tribes distribution#and the culture behind Xian people#All of it to simply put together the family a tree of a background character and ensure that 5 scenes in the ENTIRE story are accurate#And yes there are gays in it#but it is a 5000 years long story#it wouldn't be realistic if no gay weren't somehow involved in such a long period of time
137K notes
·
View notes