#Email Encryption Software
Explore tagged Tumblr posts
Text
Email Encryption Software Market Development Factors, Application, Future Prospects
According to a new report published by Allied Market Research, titled, “Email Encryption Software Market, By Component (Solution, Service), By Deployment Mode (On-premise, Cloud), By Organization Size (Large Enterprises, Small and Medium-sized Enterprises), By Industry Vertical (BFSI, IT and Telecom, Retail and E-Commerce, Healthcare, Manufacturing, Government, Energy and Utilities, Others): Global Opportunity Analysis and Industry Forecast, 2023–2032” The email encryption software market was valued at $6.3 billion in 2022, and is estimated to reach $55.4 billion by 2032, growing at a CAGR of 24.7% from 2023 to 2032.
Email encryption software is the process of using software to gather and analyze data from offline, online, and inventory outlets to offer retail businesses an understanding of customer behavior and shopping trends. In addition, email encryption software can measure customer satisfaction, identify purchasing patterns, predict demand, and optimize store layouts. Moreover, data analytics solutions and services have been increasingly employed in the retail industry, with rising user data on physical as well as online platforms. In addition, email encryption software helps businesses to understand demand trends so they can have enough products in stock. Overall, the email encryption software market is driven by the need for intelligent and analytical systems that can process and analyze vast amounts of data, which in turn allows organizations to take actions based on data-driven insights.

On the basis of deployment mode, the on-premise segment dominated the email encryption software market in 2022 and is expected to continue this trend during the forecast period. Many organizations preferred on-premise solutions due to various factors, including data control, customization options, and security concerns. These factors further drive the demand for the on-premise segment in the global market. However, the cloud segment is expected to exhibit the highest growth during the forecast period, as cloud-based solutions offer cost-effectiveness and scalability, which further is expected to provide lucrative growth opportunities for the market during the forecast period.
By region, North America dominated the email encryption software market share in 2022, as North America is home to numerous large enterprises and multinational corporations that handle vast amounts of sensitive data, which is expected to drive market revenue growth in the region. Thus, anticipated to propel the growth of the market. However, Asia-Pacific is expected to exhibit the highest growth during the forecast period. With the rise in cyber threats and data breaches, businesses and organizations in Asia-Pacific have become more aware of the importance of robust cybersecurity measures are expected to drive market revenue growth in the region and provide lucrative growth opportunities for the market in this region.
With most of the population confined in homes even after the lockdown measures of the COVID-19 pandemic, businesses needed to optimize their business operations and offerings to maximize their revenue opportunities while optimizing their operations to support the rapidly evolving business environment post the outbreak of the COVID-19 pandemic. This enabled many businesses to invest in email encryption software solutions. In addition, integrating advanced technologies such as artificial intelligence (AI) and machine learning (ML) into email encryption software can enhance threat detection, anomaly detection, and predictive analysis. These technologies are capable of supporting the detection of suspicious activity, the identification of possible security breaches, and the automation of encryption procedures based on user behavior patterns.
Inquiry Before Buying: https://www.alliedmarketresearch.com/purchase-enquiry/132972
Furthermore, the rise in trend of cloud computing in several industries including email encryption software industry is anticipated to create numerous opportunities for the the growth. For instance, in March 2021, IBM launched new and enhanced services designed to help organizations manage the cloud security strategy, policies, and controls across hybrid cloud environments. Therefore, numerous strategies adopted by businesses further help to accelerate the email encryption software market globally.
Key Findings of the Study
By component, the solution segment accounted for the largest email encryption software market share in 2022.
By deployment mode, the on-premise segment accounted for the largest email encryption software market share in 2022.
By organization size, the large enterprises segment accounted for the largest email encryption software market share in 2022.
By industry vertical, the BFSI segment accounted for the largest email encryption software market share in 2022.
Region wise, North America generated the highest revenue in 2022.
The market players operating in the email encryption software market analysis are Proofpoint Inc., BAE Systems, CipherMail B.V., Cisco Systems, Inc., Hewlett Packard Enterprise (HPE), Micro Focus International plc, Proton Technologies AG, Sophos Ltd., Trend Micro Incorporated, and Virtru. These major players have adopted various key development strategies such as business expansion, new product launches, and partnerships, which help to drive the growth of the email encryption software market globally.
About Us: Allied Market Research (AMR) is a full-service market research and business-consulting wing of Allied Analytics LLP based in Portland, Oregon. Allied Market Research provides global enterprises as well as medium and small businesses with unmatched quality of “Market Research Reports Insights” and “Business Intelligence Solutions.” AMR has a targeted view to provide business insights and consulting to assist its clients to make strategic business decisions and achieve sustainable growth in their respective market domain.
#Email Encryption Software Market#Email Encryption Software Industry#Email Encryption Software#Software and Services
0 notes
Note
Hi! You’re in the LA area, right? I hope you and your family are okay.
Unrelatedly, I ran across a thread on Mastodon about Proton Mail, which I think you’ve talked about before, and was curious what you make of it / how credible it is: https://code4lib.social/@[email protected]/113838748729664639
I'm fine thanks! Worried about some friends but I'm good.
I think that thread is not incorrect, but is also bullshit.
Email protocols do not allow for 100% anonymous communication and never will, when Proton was subpoenaed for user data that ended up with some French climate activists getting prosecuted they were transparent about what was requested and updated their logging rules to store less data. *Starting* from the assumption that protonmail is supposed to be totally secure OR sells itself as totally secure is disingenuous.
The great thing about open source software is that you never have to trust a shithead CEO when they talk about what the software does. I get why people are angry at the CEO (I think the CEO is at least half wrong in that he is claiming that Republicans will challenge monopolies, but he's not wrong about the destructive corporatism of the Democratic party even if he is *in essence* wrong about which party is more likely to gesture in the direction of breaking up tech monopolies) but A) the thread says that proton's software is "opaque" and it just. Literally is not. and B) that thread links to another thread talking about how what proton is selling is trust and nope. They don't have to sell trust; you can see what their software does if you choose to investigate it, there's no need for trust when you can verify. What they're selling is transparency and from where i'm standing they are indeed quite transparent.
God. Imagine thinking that a zero trust service is selling trust.
So I think the argument that "protonmail actually isn't as secure as it claims" is bullshit that people bring up whenever they're mad at the company (whether they have legitimate reasons to be mad at the company or not).
For the record: you should never, ever, EVER treat email as a secret. Nothing you do over email is really secret because *the rules that allow email to function as a service* require at least some very sensitive information to be an open part of the protocol.
The Proton page on end to end encryption is *very* clear that it is the contents of your email messages that are encrypted, not your email as a whole, and in the image they use to illustrate this the parts of your email that *cannot* be made private (sender, recipient, subject line, time sent) are shown unencrypted:

They're not subtle about letting people know this. Nor are they quiet about the fact that replies to encrypted emails are not encrypted by default.
So the thread is *technically* correct in that all the security "holes" described reflect reality, but it's correct like saying "McDonald's says that you can eat their food for every meal and you'll put on ten pounds of muscle but ACTUALLY putting on ten pounds of muscle requires a huge amount of dedication and a very careful diet and a lot of resistance exercise" - like, I guess yeah that's what you have to do to put on ten pounds of muscle but where exactly was McDonald's making that claim? Did they actually make that claim or are general statements like "I'm Lovin' It" being misinterpreted in bad faith by people on the internet who are mad at something a CEO did?
So. Like. Yeah the CEO is being a shithead, the social media team made a pretty bad fuckup by doubling down on his shitheadery, the product still works as described, AND the thread discussing all of that is deeply annoying.
So.
I think this thread actually does a great job of explaining why I've never seen a "hackers for social justice" group that has lasted. This reminds me a LOT of when someone tried to say that you shouldn't use firefox because the former CEO was a homophobe. There are a lot of deeply shitty people who have made important contributions to our tech ecosystem and if we threw the baby out with the bathwater every time Notch from Minecraft ended up being Notch from minecraft you'd lock yourself out of a lot of really important tools. And this isn't the same as "buying harry potter merch funds transphobia" because it literally doesn't; especially with open source tools you can continue using the software and cheerfully hate the CEO because A) fuck that guy and B) what the fuck are you going to do about it, guy, this shit's encrypted.
I don't want to get too deeply into a discussion about what is or is not cancel culture, but what I'm seeing in that thread (and what I see coming up every time someone brings up the "But the French Climate Activists!" thing) is an attempt to prioritize political alignment over real-world utility. It's attempting to cancel a *genuinely useful tool* because someone involved in the development is an asshole.
By all means, don't give protonmail money if the CEO's trump-positive comments make you feel unsafe.
However: What service are you going to use that is as accessible and as secure to ensure that you actually *are* safe? There are alternatives out there. Do they actually do more than proton? Are they easier to use? Are they open source? One of the responses to that thread was "yeah, that dude seems shitty; i'd switch to another service if there was another one that I felt was as secure" and that's pretty much what I think the correct attitude is. (If you really, really still want to switch, Tuta has been the broadly recommended alternative to protonmail for years but at this point Proton has a suite of services that some users would need to replace, not just email)
IDK i think shit like this contributes to a lot of the bad kind of security nihilism where people are like "oh no, things will never be secure and even my scrappy little open source product is headed by an asshole, i may as well use google because everything sucks" when they should have the good kind of nihilism which is like "man, there are a lot of assholes out there and they're never going to stop being assholes; i'd better take proactive steps to act like the people who make tech stuff are assholes and operate from a better base of security at the start"
so the takeaways are:
Proton never claimed that anything but the message contents of your e2e encrypted messages are encrypted; as far as these things go, they do a pretty good job of being both secure and easy to use compared to other offerings.
Yeah the CEO is being kind of a shithead and I'm not a huge fan of that.
If you think the CEO is being a shithead and don't want to give the company your money, don't pay for their services, but the CEO being a shithead doesn't actually mean you can't trust their services; their services are literally built on zero trust, if the CEO literally wanted to hunt you down personally he wouldn't be any more able to decrypt your emails than he was before and he wouldn't be any more likely to respond to a subpoena than he was before (proton does respond to subpoenas when required but not otherwise; they've been compelled to produce more data in the last decade than before because law enforcement finally realized who they needed to yell at - one of the bigger issues here is the Swiss courts being more willing to grant subpoenas to international complainants than they were before)
The reason we don't go see hogwarts movies is because doing so gives JK money and that does actual real world harm; using firefox does not have an impact on Brendan Eich's ability to materially change the world. It is very weird that we're in a place where we're treating *open source encryption software that is simple enough for your grandma to use it* as though it is Orson Scott Card.
Sorry i'm still stuck on people thinking that proton, famously open source, is opaque, and that an encryption service with zero trust architecture is selling trust.
Anyway if you've ever got questions about security/privacy/whatever services privacyguides.org is a very reliable source.
OH I FIGURED OUT WHAT WAS BUGGING ME
There are a bunch of people discussing this talking about how the CEO's social media is what has made them feel unsafe and I'm going to be a dick here and say that facts don't care about your feelings.
The CEO saying stupid shit doesn't actually make you unsafe in a situation like this; if the CEO was a violent transphobe or aggressive racist or horribly misogynist that wouldn't actually make any of the users of the product less safe. That's why the SJ hacker stuff I've seen hasn't had much staying power; I think that groups that focus on making people feel included and welcome and safe to be themself within the group run into really big problems when there's a conflict between people in the group FEELING unsafe because of (genuinely important in many ways) cultural signifiers like political alignment and so in order to accommodate that feeling they end up doing things (like some kinds of collaboration/accountability practices, abandoning useful tools, WAY too much personal transparency and radical vulnerability for people who are doing crime shit) that ACTUALLY make them less safe.
The CEO being a shithead may make you feel bad, but moving to a less secure platform may actually be dangerous. One of these things can have a big impact on your life, and it is not the one that is happening on twitter.
Anyway. Email is inherently insecure and if you want a secure messaging tool use Signal.
If you are doing crime shit don't talk about it on the internet and DEFINITELY don't talk about it in any kind of unencrypted platform.
If you are a French climate activist who would like to not get arrested if Tuta gets a subpoena for data, use the email service in concert with tor and be cautious about senders/receivers and subject lines.
244 notes
·
View notes
Text
me when companies try to force you to use their proprietary software

anyway
Layperson resources:
firefox is an open source browser by Mozilla that makes privacy and software independence much easier. it is very easy to transfer all your chrome data to Firefox
ublock origin is The highest quality adblock atm. it is a free browser extension, and though last i checked it is available on Chrome google is trying very hard to crack down on its use
Thunderbird mail is an open source email client also by mozilla and shares many of the same advantages as firefox (it has some other cool features as well)
libreOffice is an open source office suite similar to microsoft office or Google Suite, simple enough
Risky:
VPNs (virtual private networks) essentially do a number of things, but most commonly they are used to prevent people from tracking your IP address. i would suggest doing more research. i use proton vpn, as it has a decent free version, and the paid version is powerful
note: some applications, websites, and other entities do not tolerate the use of VPNs. you may not be able to access certain secure sites while using a VPN, and logging into your personal account with some services while using a vpn *may* get you PERMANENTLY BLACKLISTED from the service on that account, ymmv
IF YOU HAVE A DECENT VPN, ANTIVIRUS, AND ADBLOCK, you can start learning about piracy, though i will not be providing any resources, as Loose Lips Sink Ships. if you want to be very safe, start with streaming sites and never download any files, though you Can learn how to discern between safe, unsafe, and risky content.
note: DO NOT SHARE LINKS TO OR NAMES OF PIRACY SITES IN PUBLIC PLACES, ESPECIALLY SOCAL MEDIA
the only time you should share these things are either in person or in (preferably peer-to-peer encrypted) PRIVATE messages
when pirated media becomes well-known and circulated on the wider, public internet, it gets taken down, because it is illegal to distribute pirated media and software
if you need an antivirus i like bitdefender. it has a free version, and is very good, though if youre using windows, windows defender is also very good and it comes with the OS
Advanced:
linux is great if you REALLY know what you're doing. you have to know a decent amount of computer science and be comfortable using the Terminal/Command Prompt to get/use linux. "Linux" refers to a large array of related open source Operating Systems. do research and pick one that suits your needs. im still experimenting with various dispos, but im leaning towards either Ubuntu Cinnamon or Debian.
#capitalism#open source#firefox#thunderbird#mozilla#ublock origin#libreoffice#vpn#antivirus#piracy#linux
695 notes
·
View notes
Text
Updated Personal Infosec Post
Been awhile since I've had one of these posts part deus: but I figure with all that's going on in the world it's time to make another one and get some stuff out there for people. A lot of the information I'm going to go over you can find here:
https://www.privacyguides.org/en/tools/
So if you'd like to just click the link and ignore the rest of the post that's fine, I strongly recommend checking out the Privacy Guides. Browsers: There's a number to go with but for this post going forward I'm going to recommend Firefox. I know that the Privacy Guides lists Brave and Safari as possible options but Brave is Chrome based now and Safari has ties to Apple. Mullvad is also an option but that's for your more experienced users so I'll leave that up to them to work out. Browser Extensions:
uBlock Origin: content blocker that blocks ads, trackers, and fingerprinting scripts. Notable for being the only ad blocker that still works on Youtube.
Privacy Badger: Content blocker that specifically blocks trackers and fingerprinting scripts. This one will catch things that uBlock doesn't catch but does not work for ads.
Facebook Container: "but I don't have facebook" you might say. Doesn't matter, Meta/Facebook still has trackers out there in EVERYTHING and this containerizes them off away from everything else.
Bitwarden: Password vaulting software, don't trust the password saving features of your browsers, this has multiple layers of security to prevent your passwords from being stolen.
ClearURLs: Allows you to copy and paste URL's without any trackers attached to them.
VPN: Note: VPN software doesn't make you anonymous, no matter what your favorite youtuber tells you, but it does make it harder for your data to be tracked and it makes it less open for whatever public network you're presently connected to.
Mozilla VPN: If you get the annual subscription it's ~$60/year and it comes with an extension that you can install into Firefox.
Mullvad VPN: Is a fast and inexpensive VPN with a serious focus on transparency and security. They have been in operation since 2009. Mullvad is based in Sweden and offers a 30-day money-back guarantee for payment methods that allow it.
Email Provider: Note: By now you've probably realized that Gmail, Outlook, and basically all of the major "free" e-mail service providers are scraping your e-mail data to use for ad data. There are more secure services that can get you away from that but if you'd like the same storage levels you have on Gmail/Ol utlook.com you'll need to pay.
Tuta: Secure, end-to-end encrypted, been around a very long time, and offers a free option up to 1gb.
Mailbox.org: Is an email service with a focus on being secure, ad-free, and privately powered by 100% eco-friendly energy. They have been in operation since 2014. Mailbox.org is based in Berlin, Germany. Accounts start with up to 2GB storage, which can be upgraded as needed.
Email Client:
Thunderbird: a free, open-source, cross-platform email, newsgroup, news feed, and chat (XMPP, IRC, Matrix) client developed by the Thunderbird community, and previously by the Mozilla Foundation.
FairMail (Android Only): minimal, open-source email app which uses open standards (IMAP, SMTP, OpenPGP), has several out of the box privacy features, and minimizes data and battery usage.
Cloud Storage:
Tresorit: Encrypted cloud storage owned by the national postal service of Switzerland. Received MULTIPLE awards for their security stats.
Peergos: decentralized and open-source, allows for you to set up your own cloud storage, but will require a certain level of expertise.
Microsoft Office Replacements:
LibreOffice: free and open-source, updates regularly, and has the majority of the same functions as base level Microsoft Office.
OnlyOffice: cloud-based, free
FreeOffice: Personal licenses are free, probably the closest to a fully office suite replacement.
Chat Clients: Note: As you've heard SMS and even WhatsApp and some other popular chat clients are basically open season right now. These are a couple of options to replace those. Note2: Signal has had some reports of security flaws, the service it was built on was originally built for the US Government, and it is based within the CONUS thus is susceptible to US subpoenas. Take that as you will.
Signal: Provides IM and calling securely and encrypted, has multiple layers of data hardening to prevent intrusion and exfil of data.
Molly (Android OS only): Alternative client to Signal. Routes communications through the TOR Network.
Briar: Encrypted IM client that connects to other clients through the TOR Network, can also chat via wifi or bluetooth.
SimpleX: Truly anonymous account creation, fully encrypted end to end, available for Android and iOS.
Now for the last bit, I know that the majority of people are on Windows or macOS, but if you can get on Linux I would strongly recommend it. pop_OS, Ubuntu, and Mint are super easy distros to use and install. They all have very easy to follow instructions on how to install them on your PC and if you'd like to just test them out all you need is a thumb drive to boot off of to run in demo mode. For more secure distributions for the more advanced users the options are: Whonix, Tails (Live USB only), and Qubes OS.
On a personal note I use Arch Linux, but I WOULD NOT recommend this be anyone's first distro as it requires at least a base level understanding of Linux and liberal use of the Arch Linux Wiki. If you game through Steam their Proton emulator in compatibility mode works wonders, I'm presently playing a major studio game that released in 2024 with no Linux support on it and once I got my drivers installed it's looked great. There are some learning curves to get around, but the benefit of the Linux community is that there's always people out there willing to help. I hope some of this information helps you and look out for yourself, it's starting to look scarier than normal out there.

#infosec#personal information#personal infosec#info sec#firefox#mullvad#vpn#vpn service#linux#linux tails#pop_os#ubuntu#linux mint#long post#whonix#qubes os#arch linux
79 notes
·
View notes
Text
Some tips on how to survive a fascist state
From your auntie who has been around this block before.
This was made for people living in the US, but most of this is generally useful.
Assess your level of risk. For example, if you are not a citizen, going to a protest is much higher risk than it is for a citizen. But also recognize that the landscape of who is and is not being targeted is rapidly changing, so keep that in mind.
Get an updated passport. Make this a priority. If you live in a state where they have them, also get an Enhanced ID (not a Real ID, specifically an Enhanced ID) so you have a second way to cross land or sea borders into Canada and Mexico. That way, if authorities take your passport, you have another way out of the country.
Assume that the law is not there to protect you. Many parts of the law that are meant to protect you no longer apply. It's good to know your rights, but also know that the administration is not going to respect them. Just because you aren't doing anything illegal does not mean they won't come after you.
Move your communications, especially political communications, to encrypted messaging services. Use Signal for texts, ProtonMail for email, and Cryptpad as a word processor.
Get a private web browser. DuckDuckGo is a good option. I've also heard good things about Norton's private browser.
If you post political content on social media, you have two options. Make your account private and spend an evening going through your followers to weed out the ones you don't trust. Or, make it anonymous. But if you are picking the latter, know that it is hard to anonymize an account where you previously shared your identity. It's easier to go private if it's linked to your real life self, including through mutuals.
Turn off face ID on your devices. Police can force you to open them with your biometrics, even without a warrant. Additionally, make sure you have strong passwords (that are different for every account!) and keep track of them using a secure password manager.
If you go to protests or otherwise engage in subversive activity, DO NOT POST ABOUT IT ONLINE. Doing so endangers yourself and potentially others. Especially do not post pictures of protests, even if you've blurred the faces, even if you think you scrubbed the metadata. Even better, don't take photos at protests.
If you're exiting and re-entering the US, get a burner phone. I'm serious. Get an iPhone secondhand if you can afford it, but a flip phone will work if you need it to. Don't assume that just deleting anything sensitive off your device will be enough. You may not find it all, and depending on how thoroughly they search your phone, they may be able to see things that were deleted.
Mask up, especially when you're at a protest. In general, it's a good idea to mask since covid and many other viruses are going around. But masking has the added benefit of reducing the amount of biometric information you are making visible. Additionally, facial recognition software relies heavily on eyebrows, so cover them using a beanie or similar item.
Get involved or strengthen your ties with some kind of community. You are going to need others to lean on, whether that's emotionally or politically, in times like these.
22 notes
·
View notes
Text
hi. since i have something that could very generously be called a platform, your local dumb horny dog is here with another unfortunate public service announcement for people currently living under the legal jurisdiction of the united states of america:
this would be a good time to start investigating privacy and data security tools (and, as ever, to not panic and/or doompost because those are not useful things to do). such things include:
using (more) secure messaging apps over sms for private correspondence such signal.
using (more) private email services rather than gmail such as protonmail
password protect your shit. this is just basic data security but like. please. password protect your shit. use strong passwords and/or passphrases. don't reuse passwords. use a password manager (i recommend bitwarden).
building off the previous one, encrypt your shit if you're able to. for pc users there are plenty of open source options, such as veracrypt, and probably native os stuff too.
like. y'all are gonna roll your eyes, and i get it, but: stop using windows and try out linux. seriously. windows 11 is a fucking privacy nightmare and it's only getting worse as microsoft pushes their ai shit which is planned to have access to everything you do on it.
tumblr can't do nested lists, consider this a sub-point: mint linux is designed to be incredibly familiar to people coming from windows and is very user friendly. a huge amount of windows software can run on linux using stuff like wine. the linux version of steam comes pre-packaged with it. it's fine. please try linux it won't bite.
sadly i am, as mentioned, a dog on the internet and i cannot provide an actual comprehensive guide to keeping your privacy intact and yourself safe.
however, there are plenty of good guides for this sort of thing on the internet and despite how degraded modern search engines are they are not hard to find. i heartily suggest doing so and familiarizing yourself with them-- and not just because of the times we live in, because a lot of this shit is the same shit that will help keep you safe from a lot of forms of identity theft and the like. it's just good opsec.
22 notes
·
View notes
Text
Proton, the secure-minded email and productivity suite, is becoming a nonprofit foundation, but it doesn't want you to think about it in the way you think about other notable privacy and web foundations.
"We believe that if we want to bring about large-scale change, Proton can’t be billionaire-subsidized (like Signal), Google-subsidized (like Mozilla), government-subsidized (like Tor), donation-subsidized (like Wikipedia), or even speculation-subsidized (like the plethora of crypto “foundations”)," Proton CEO Andy Yen wrote in a blog post announcing the transition. "Instead, Proton must have a profitable and healthy business at its core."
The announcement comes exactly 10 years to the day after a crowdfunding campaign saw 10,000 people give more than $500,000 to launch Proton Mail. To make it happen, Yen, along with co-founder Jason Stockman and first employee Dingchao Lu, endowed the Proton Foundation with some of their shares. The Proton Foundation is now the primary shareholder of the business Proton, which Yen states will "make irrevocable our wish that Proton remains in perpetuity an organization that places people ahead of profits." Among other members of the Foundation's board is Sir Tim Berners-Lee, inventor of HTML, HTTP, and almost everything else about the web.
Of particular importance is where Proton and the Proton Foundation are located: Switzerland. As Yen noted, Swiss foundations do not have shareholders and are instead obligated to act "in accordance with the purpose for which they were established." While the for-profit entity Proton AG can still do things like offer stock options to recruits and even raise its own capital on private markets, the Foundation serves as a backstop against moving too far from Proton's founding mission, Yen wrote.
There’s a lot more Proton to protect these days
Proton has gone from a single email offering to a wide range of services, many of which specifically target the often invasive offerings of other companies (read, mostly: Google). You can now take your cloud files, passwords, and calendars over to Proton and use its VPN services, most of which offer end-to-end encryption and open source core software hosted in Switzerland, with its notably strong privacy laws.
None of that guarantees that a Swiss court can't compel some forms of compliance from Proton, as happened in 2021. But compared to most service providers, Proton offers a far clearer and easier-to-grasp privacy model: It can't see your stuff, and it only makes money from subscriptions.
#proton#protonmail#surveillance capitalism#privacy#social media#artificial intelligence#big tech#technology#google#nonprofit
22 notes
·
View notes
Text
Introducing SavvyDissent
Friends, it's time (I'm sorry to say) to bring back the chain e-mail, the reply all, and the mass text. Security and safe use of the internet just became critical.
I hope you will (securely) spread it through your social circles in person, or by secured email or text.
We're all in shock from the election, and we're all wishing we could do something. Protests and resistance will increase over the next years. My hope, and my advice, is that we take the threat seriously. You (and I) are not overreacting; they tell us their plans. Trump promised at the beginning of this campaign way back in 2023 to overhaul the federal government into his personal bureaucracy. He specified that will include surveillance departments.
This is real, and it's critical to understand the the US is not immune to fascism and authoritarianism. American exceptionalism is a dangerous lie. With the technology we have now, the rise of fascism will look radically different that our historical imaginations conjure, and the administration will be very different than his 2016-2020 presidency.
The 2016 Trump was chaotic and vague, and even then he left destruction in his wake. Now, the far-right have had years to organize for a second Trump regime.
They have concrete plans they didn't have before. Trump is less coherent now, but he's surrounded by people with purpose and competence that in he didn't have in his first administration. His health is declining fast, and JD Vance is potentially even worse ideologically. The Trump administration will likely involve RFK, Jr. and Elon Musk, both of whom are extremely dangerous.
Audaciously, the richest man in the world has warned us to expect austerity. He's in a position to become Trump's propagandist (and has played the role already.)
The Heritage Foundation, an extreme Chisto-fascist organization, are the architects of this coming regime. Their agenda in Project 2025 should terrify us. One of my only sources of hope is that it seems Trump/MAGA are telling us their plans. That advantage is lost when we don't believe them.
We need to accept some harsh truths, and one of these is that social media is not the place for a resistance movement.
It is not our friend or ally; it is demonstrably dangerous. Learning this is part of the mission inherent in the popular phrase, "Don't obey in advance." Don't hand them your information. The CEOs of the major sites are collaborators--they helped manifest this outcome, and they've already demonstrated their willingness to help quell dissent (your photos are used in face-recognition software to identify protesters) and aid the police in hunting down and arresting abortion patients.
We have to rethink organizing, and we have to do it securely.
I must stress that Trump has included leftists (by which he means even moderate liberals and democrats) in his speech about "the enemy within." Even if we are white, Christian, cisgender, straight, and able-bodied, he has declared us the enemy.
Each of us has a decision to make. We either become publicly dissident--risking personal safety to a degree we can't know--or we wage our opposition in the safest way possible.
Social media? They're cops. If we are going to have any hope of staying safe and organizing, we must accept this truth.
We must assess the risk of posting our affiliations and circulate petitions and direct actions on the public web. Most of us are easily identified where data miners and AI can detect this information. For the most part, that's out there, permanently. When you delete an account, the company retains copies of your data.
I am not a security expert, but I have some beginner tips for safer communication.
● Download an end-to-end encrypted messenger app and stop using SMS texting and social media DMs. I recommend Signal or Discord, but would not trust WhatsApp, as it's owned by Meta.
● Look in to data removal services like DeleteMe or Incogni; these will help your reclaim as much of your data.
● Turn off your phone's location tracking.
● Install a VPN and sign up for a secured email. Proton Mail and storage are good; Gmail and Google Drive are the enemy. A VPN (virtual private network) hides your IP address that would otherwise out your location and other info.
● There are cheap anf free options for VPNs and you can find secure email free.
● Install TOR or other secured browsers. Chrome especially is a security nightmare. Incognito or private browsing on your regular browsers is not a safe option.
● Reject site cookies and use best practices for password security.
● Don't make plans online. Circulate information directly using these secure practices. If you volunteer or join protests or see calls to action on public social media, talk with the organizer to urge a move off social media.
● If you attend a protest, read into Black Bloc tactics for anonymity and health/safety, or at least wear a face-obscuring mask. Police have already used face-matching software to arrest protesters in the US.
● Speaking of masking, follow Covid protocols. Our health system will be gutted soon and any measures to prevent communicable disease are going to be on us. (Vaccines could be banned; the CDC eroded even further.) There are dangerous flu strains as well- please take precautions.
● Disable face recognition or thumbprint logins on your phone. Currently the cops are allowed to use these to access your phone, but they can't force you to give them the PIN or pattern drawing. Be aware that could change.
● If you are trans, discuss privacy concerns with your doctor.
● Along that vein, if you're seeking an autism diagnosis *and your level of support needs can be met without it* rethink having your neurodivergence documented. The fate of disabled folks is precarious, and authoritarian/fascist movements are dangerous for us. I'm not sure if ADHD or other neurotypes are at risk, but there is historical precedence for autistics and other divergent people to be targeted.
● Protect each other: Do not out trans, queer, racialized, or any other vulnerable people in your friends groups. Note that includes any pregnant person--Whether you're excited your best friend is having another baby or your kid sister is late for her period, keep that offline. (For the love of all that's holy delete your period trackers.)
● If you know travel plans for someone to travel or move to a safer blue state, you shut the fuck up about it.
If you have further knowledge about privacy and security, add it when you forward this to friends.
I'm planning for this to become an anonymous zine/newsletter where we can distribute info under-the-radar communications network. To opt in to occasional newsletter posts,
email "add me" to [email protected], visit tumblr.com/savvydissent message via Discord or Telegram @savvydissent
Print & distribute on paper.
Share this with your contacts, and circulate it safely. Please message me to share any direct actions, mutual aid organizing, or any relevant info you want to spread. Please take good care of yourself.
5 notes
·
View notes
Text
Astraweb: The Home of Crypto Recovery in the Digital Age

In the ever-evolving world of cryptocurrency, security and access remain critical concerns. For every success story of early adopters turning modest investments into fortunes, there are unfortunate accounts of users losing access to their digital wallets due to forgotten passwords, phishing attacks, or compromised private keys. This is where Astraweb has carved out a vital niche — establishing itself as the go-to solution for crypto asset recovery.
The Need for Crypto Recovery
Cryptocurrency promises decentralized finance and ownership without intermediaries — but this power comes with a cost: total user responsibility. There is no central authority to call when access is lost. Millions of dollars in crypto assets are estimated to be trapped in inaccessible wallets. The stakes are high, and the traditional “write your password down and hope for the best” method has proven tragically inadequate.
Astraweb has stepped in to fill this gap, offering a technically advanced, ethically grounded, and user-focused recovery service for individuals and institutions alike.
Who is Astraweb?
Astraweb is a team of cybersecurity professionals, blockchain analysts, and ethical hackers dedicated to the recovery of lost digital assets. Known in online communities for their discretion and technical excellence, Astraweb has quietly built a reputation as the “home of crypto recovery” — a safe harbor in the sometimes stormy seas of decentralized finance.

Core Services Offered
Wallet Password Recovery Utilizing a combination of brute force optimization, machine learning, and customized dictionary attacks, Astraweb helps users recover wallets with forgotten passwords. Their tools are especially effective with partially remembered credentials.
Seed Phrase Reconstruction Lost or partial seed phrases are another major barrier to wallet access. Astraweb’s proprietary tools attempt to reconstruct valid mnemonic phrases based on user input and probabilistic modeling.
Phishing and Scam Mitigation If your crypto assets have been stolen due to phishing attacks or scams, Astraweb provides investigation support and recovery options. While crypto transactions are irreversible, Astraweb works with partners and tracing tools like Chainalysis to help track and reclaim funds when possible.
Multi-Sig and Legacy Wallet Recovery Many early wallets used now-defunct software or obscure security models. Astraweb specializes in navigating old formats, deprecated standards, and rare cryptographic setups.
Cold Wallet Restoration Lost access to hardware wallets like Trezor, Ledger, or even encrypted USB drives? Astraweb can assist with forensic-level data recovery and hardware-based key extraction.
Why Astraweb Stands Out
Confidentiality First: Every case is handled with strict privacy. Your data and identity are protected at all stages of the recovery process.
Transparent Communication: Clients are updated at every step, with no vague promises or false guarantees.
No Recovery, No Fee: Astraweb operates on a results-based model. You only pay if your assets are successfully recovered.
Client Trust and Track Record
Though much of their work remains confidential due to the sensitive nature of crypto assets, Astraweb’s success stories span from everyday investors to high-net-worth individuals and even businesses affected by inaccessible wallets or theft.
Their community reputation and testimonials underscore one thing: they deliver.
Contact Astraweb
If you’ve lost access to your cryptocurrency wallet, or fallen victim to crypto fraud, don’t give up hope. Reach out to Astraweb for a professional assessment of your situation.
Email: [email protected]
Whether it’s one token or an entire portfolio, Astraweb may be your best shot at recovery.
2 notes
·
View notes
Text
Integrating Third-Party Tools into Your CRM System: Best Practices
A modern CRM is rarely a standalone tool — it works best when integrated with your business's key platforms like email services, accounting software, marketing tools, and more. But improper integration can lead to data errors, system lags, and security risks.

Here are the best practices developers should follow when integrating third-party tools into CRM systems:
1. Define Clear Integration Objectives
Identify business goals for each integration (e.g., marketing automation, lead capture, billing sync)
Choose tools that align with your CRM’s data model and workflows
Avoid unnecessary integrations that create maintenance overhead
2. Use APIs Wherever Possible
Rely on RESTful or GraphQL APIs for secure, scalable communication
Avoid direct database-level integrations that break during updates
Choose platforms with well-documented and stable APIs
Custom CRM solutions can be built with flexible API gateways
3. Data Mapping and Standardization
Map data fields between systems to prevent mismatches
Use a unified format for customer records, tags, timestamps, and IDs
Normalize values like currencies, time zones, and languages
Maintain a consistent data schema across all tools
4. Authentication and Security
Use OAuth2.0 or token-based authentication for third-party access
Set role-based permissions for which apps access which CRM modules
Monitor access logs for unauthorized activity
Encrypt data during transfer and storage
5. Error Handling and Logging
Create retry logic for API failures and rate limits
Set up alert systems for integration breakdowns
Maintain detailed logs for debugging sync issues
Keep version control of integration scripts and middleware
6. Real-Time vs Batch Syncing
Use real-time sync for critical customer events (e.g., purchases, support tickets)
Use batch syncing for bulk data like marketing lists or invoices
Balance sync frequency to optimize server load
Choose integration frequency based on business impact
7. Scalability and Maintenance
Build integrations as microservices or middleware, not monolithic code
Use message queues (like Kafka or RabbitMQ) for heavy data flow
Design integrations that can evolve with CRM upgrades
Partner with CRM developers for long-term integration strategy
CRM integration experts can future-proof your ecosystem
#CRMIntegration#CRMBestPractices#APIIntegration#CustomCRM#TechStack#ThirdPartyTools#CRMDevelopment#DataSync#SecureIntegration#WorkflowAutomation
2 notes
·
View notes
Text
On Personal InfoSec
Been awhile since I've had one of these posts but I figure with all that's going on in the world it's time to make another one of these posts and get some stuff out there for people. A lot of the information I'm going to go over you can find here:
So if you'd like to just click the link and ignore the rest of the post that's fine, I strongly recommend checking out the Privacy Guides.
Browsers:
There's a number to go with but for this post going forward I'm going to recommend Firefox. I know that the Privacy Guides lists Brave and Safari as possible options but Brave is Chrome based now and Safari has ties to Apple. Mullvad is also an option but that's for your more experienced users so I'll leave that up to them to work out.
Browser Extensions:
uBlock Origin: content blocker that blocks ads, trackers, and fingerprinting scripts. Notable for being the only ad blocker that still works on Youtube.
Privacy Badger: Content blocker that specifically blocks trackers and fingerprinting scripts. This one will catch things that uBlock doesn't catch but does not work for ads.
Facebook Container: "but I don't have facebook" you might say. Doesn't matter, Meta/Facebook still has trackers out there in EVERYTHING and this containerizes them off away from everything else.
Bitwarden: Password vaulting software, don't trust the password saving features of your browsers, this has multiple layers of security to prevent your passwords from being stolen.
ClearURLs: Allows you to copy and paste URL's without any trackers attached to them.
VPN:
Note: VPN software doesn't make you anonymous, no matter what your favorite youtuber tells you, but it does make it harder for your data to be tracked and it makes it less open for whatever network you're presently connected to.
Mozilla VPN: If you get the annual subscription it's ~$60/year and it comes with an extension that you can install into Firefox.
Proton VPN: Has easily the most amount of countries serviced, can take cash payments, and does offer port forwarding.
Email Provider:
Note: By now you've probably realized that Gmail, Outlook, and basically all of the major "free" e-mail service providers are scraping your e-mail data to use for ad data. There are more secure services that can get you away from that but if you'd like the same storage levels you have on Gmail/Outlook.com you'll need to pay.
Proton Mail: Secure, end-to-end encrypted, and fairly easy to setup and use. Offers a free option up to 1gb
Tuta: Secure, end-to-end encrypted, been around a very long time, and offers a free option up to 1gb.
Email Client:
Thunderbird if you're on Windows or Linux
Apple Mail if you're on macOS
Cloud Storage:
Proton Drive: Encrypted cloud storage from the same people as Proton Mail.
Tresorit: Encrypted cloud storage owned by the national postal service of Switzerland. Received MULTIPLE awards for their security stats.
Peergos: decentralized and open-source, allows for you to set up your own cloud storage, but will require a certain level of expertise.
Microsoft Office Replacements:
LibreOffice: free and open-source, updates regularly, and has the majority of the same functions as base level Microsoft Office.
OnlyOffice: cloud-based, free, and open source.
Chat Clients:
Note: As you've heard SMS and even WhatsApp and some other popular chat clients are basically open season right now. These are a couple of options to replace those.
Signal: Provides IM and calling securely and encrypted, has multiple layers of data hardening to prevent intrusion and exfil of data.
Molly (Android OS only): Alternative client to Signal. Routes communications through the TOR Network.
Briar: Encrypted IM client that connects to other clients through the TOR Network, can also chat via wifi or bluetooth.
Now for the last bit, I know that the majority of people are on Windows or macOS, but if you can get on Linux I would strongly recommend it. pop_OS, Ubuntu, and Mint are super easy distros to use and install. They all have very easy to follow instructions on how to install them on your PC and if you'd like to just test them out all you need is a thumb drive to boot off of to run in demo mode.
If you game through Steam their Proton emulator in compatibility mode works wonders, I'm presently playing a major studio game that released in 2024 with no Linux support on it and once I got my drivers installed it's looked great. There are some learning curves to get around, but the benefit of the Linux community is that there's always people out there willing to help.
I hope some of this information helps you and look out for yourself, it's starting to look scarier than normal out there.

#information security#infosec#computer security#computer infosec#personal infosec#browsers#internet browser#email#instant messaging#cloud storage#linux#pop os#linux mint#ubuntu#firefox#firefox extensions#long post
67 notes
·
View notes
Text
Fast list for privacy minded people (I lied, it's long):
Change your DNS from the default ISP provisioned one to literally anything else that has decent reputation. CloudFlare is pretty good to bet on, and Firefox has toggles to use it instead of your system DNS. Alternatively if you don't hate Google, they have a DNS that is marginally an improvement from an ISP default but you're certainly being datamined by Big Letters and they are gleefully compliant warrants or not. There are ample public DNS servers out there unlike the next point.
That is fine for general browsing and making it difficult for your ISP to snoop on you, a step further is obfuscating your public IP which makes it difficult for third-parties to track and identify you. VPNs come in here. Free ones ought to be avoided unfortunately in all but the most milquetoast use-cases. Even then they are likely collecting your data so it's best to use a paid service from a well reputed provider that is specifically not based in a 14 Eyes or mandatory logging country. CyberGhostVPN has a lot of literature on this to reference.
Use HTTPS-forcing extensions and avoid HTTP-only websites. This will require all data in transit to be encrypted which makes it impossible for third-parties including your ISP to know exactly what you are doing. Some sites still have HTTP bits on otherwise HTTPS websites, make sure your extension or browser refuses to load these parts without your consent. However be mindful that the server you are talking to obviously will know what data you sent or requested and may or may not store or use it in some way. This info may be available in some privacy statement etc. Assume that your IP, connection details, etc are all logged and act accordingly.
Avoid Tor unless you are especially confident in your understanding. While it isn't 100% confirmed, it's been generally accepted that certain powers have indeed compromised swathes of the Tor network and have the ability to eventually identify you. The naive use of this tool will be more of a hindrance causing false security than it will help you if you are actually needing a list like this.
Likewise, do not assume encryption means anything. Don't buy into anything you don't understand enough to feel confident explaining to someone else. At most, if it isn't a absolute pain in the ass, find a reputable encrypted email provider or learn how to use OpenPGP to encrypt email communications. Side note to OpenPGP, it also is useful as a way to verify your communications are yours and is often used as such in mailing lists or for contributing to open software/validating packages. In a deep fake world this will become more important but isn't quite a privacy matter.
Generally speaking, fancy tools and technologies are worthless if you can't really use them and actually a hindrance to you. If you start with a zero privacy/zero security assumption as default and operate accordingly you'll already be far ahead of the curve with little added complexity or effort. Don't say stupid shit, don't do stupid shit, don't give out stupid shit. Never ever use public or work APs for personal or private browsing, I'd say don't even connect to public wifis at all even. Don't do personal stuff at work either, and try to keep work computers off your private network and personal devices off work networks. Mindset is probably by far more important than any of the other points. Techno neophytes and fetishists will never tell you that most of your privacy and security comes from your brain.
And since it won't let me do it my way.. 0. Security does not mean privacy, nor does privacy mean security. These are two separate goals. This is an important distinction to make.
5 notes
·
View notes
Text
5 Ways to Improve Your Network Security
In today’s digital age, network security is more critical than ever. With cyberattacks becoming more sophisticated and frequent, businesses and individuals alike must take proactive steps to protect their networks. Whether you’re a small business owner or a tech-savvy professional, improving your network security can help safeguard sensitive data, prevent downtime, and maintain trust. Here are five actionable tips to enhance your network’s defenses.
1. Use Strong, Unique Passwords
Weak or reused passwords are among the most common vulnerabilities in network security. To protect your network:
Create strong passwords that include a mix of uppercase and lowercase letters, numbers, and special characters.
Avoid using easily guessed information, such as birthdays or common words like "password123."
Use a password manager to generate and securely store complex passwords for all your accounts.
Implement multi-factor authentication (MFA) for an extra layer of security. MFA requires users to verify their identity through a second method, such as a text message code or biometric scan.
2. Keep Your Software Up-to-Date
Outdated software is a goldmine for hackers who exploit known vulnerabilities. Regular updates ensure you’re protected with the latest security patches.
Update your operating system, applications, and firmware regularly.
Enable automatic updates to ensure critical patches are installed promptly.
Replace unsupported or obsolete hardware and software with newer, more secure alternatives.
3. Secure Your Wi-Fi Network
Your Wi-Fi network is a primary gateway for potential attacks. Securing it is essential:
Change the default administrator username and password for your router.
Use WPA3 encryption (or at least WPA2) to secure your wireless connection.
Hide your network's SSID (Service Set Identifier) so it’s not visible to unauthorized users.
Set up a guest network for visitors, keeping them isolated from your primary network.
4. Install and Update Security Software
Comprehensive security software is your first line of defense against malicious activity.
Use antivirus and anti-malware programs to detect and remove threats.
Install a firewall to monitor and block unauthorized access to your network.
Invest in a Unified Threat Management (UTM) system, which combines multiple security features like intrusion detection, content filtering, and VPN support.
Keep all security software updated to stay protected from the latest threats.
5. Educate and Train Users
Even the most robust security measures can fail if users are unaware of best practices.
Train your team to recognize phishing emails, suspicious links, and social engineering tactics.
Encourage employees to report unusual activity immediately.
Establish a network security policy that outlines acceptable use, password protocols, and steps for reporting incidents.
Conduct regular cybersecurity awareness sessions to keep users informed about emerging threats.
Bonus Tip: Monitor Your Network Activity
Proactively monitoring your network can help you detect potential issues before they become critical. Use tools to track unusual traffic, failed login attempts, and other red flags.
Conclusion
Improving your network security doesn’t have to be overwhelming. By implementing these five steps, you can significantly reduce your risk of cyberattacks and create a safer environment for your business or personal network. Remember, cybersecurity is an ongoing process—stay vigilant, keep learning, and adapt to new threats as they arise.
Have questions or need help securing your network? Contact us today for expert IT solutions tailored to your needs!
4 notes
·
View notes
Text
Top Cybersecurity Solutions Providers in Delhi-NCR: Wish Geeks Techserve
Cybersecurity services in India have become an essential investment for businesses looking to safeguard their digital infrastructure from rising cyber threats. With an increasing number of data breaches, phishing attacks, and malware infiltrations, organizations cannot afford to overlook the importance of strong IT security frameworks. Companies in Delhi-NCR, in particular, need to prioritize security due to the region's rapid technological growth and evolving cyber risk landscape.
Finding the top cybersecurity solutions provider in India is crucial for ensuring business continuity, regulatory compliance, and data integrity. Among the top contenders offering robust security solutions is Wish Geeks Techserve, a trusted IT security services India provider known for its innovative and customized cybersecurity strategies.
The Growing Cybersecurity Challenges in India
As the digital economy expands, businesses face a multitude of security threats ranging from ransomware attacks to sophisticated hacking attempts. The emergence of remote working models and cloud computing has further increased the vulnerability of organizations, making network security services in India a necessity rather than an option. The cyber threat landscape includes:
Phishing and Social Engineering Attacks: Cybercriminals exploit human vulnerabilities through fraudulent emails and deceptive practices to gain unauthorized access to sensitive information.
Malware and Ransomware Infections: Malicious software infiltrates systems, encrypting or corrupting critical business data, often leading to significant financial losses.
Insider Threats and Human Errors: Employees, either maliciously or unintentionally, can cause security breaches through weak passwords, mishandling of data, or lack of security awareness.
DDoS (Distributed Denial-of-Service) Attacks: Hackers overwhelm business networks with excessive traffic, leading to downtime and operational disruptions.
Cloud Security Risks: With increasing cloud adoption, businesses must ensure secure cloud storage, access management and data encryption practices to prevent unauthorized intrusions.
Why Choose Wish Geeks Techserve as the Best Cybersecurity Company in India?
Wish Geeks Techserve stands out among cybersecurity solutions providers in India, offering state-of-the-art security services tailored to businesses of all sizes. Their comprehensive approach ensures complete protection from internal and external threats. Here’s what makes them the ideal IT security services India provider:
1. Advanced Cybersecurity Solutions for End-to-End Protection
Wish Geeks Techserve provides holistic security solutions that cover all aspects of IT security. Their expertise spans across:
Threat Intelligence & Risk Assessment: Proactively identify vulnerabilities and strengthen weak points before attacks occur.
Endpoint Protection & Malware Defense: Implementing security measures that shield endpoints like computers, mobile devices and IoT systems from cyber threats.
Firewall & Intrusion Prevention Systems (IPS): Ensuring that network boundaries remain impervious to unauthorized access attempts.
Incident Response & Forensics: Swift action in the event of a cyberattack, minimizing damage and preventing future breaches.
2. Comprehensive Network Security Services in India
As a leading cybersecurity solutions provider in India, Wish Geeks Techserve specializes in network security services in India, ensuring robust defense mechanisms against cyber threats. Their network security offerings include:
Secure VPN Implementations: Allowing safe and encrypted remote access for employees working from different locations.
DDoS Protection & Mitigation: Preventing large-scale cyberattacks that aim to disrupt operations.
Zero Trust Security Frameworks: Adopting a ‘never trust, always verify’ approach to user authentication and access control.
3. 24/7 Cybersecurity Monitoring & Incident Response
Cyber threats do not operate within business hours, which is why Wish Geeks Techserve provides round-the-clock monitoring and support. Their dedicated Security Operations Center (SOC) continuously tracks anomalies, preventing attacks before they escalate.
4. Regulatory Compliance & Data Privacy Solutions
With stringent data protection regulations like GDPR and India’s upcoming Personal Data Protection Bill, businesses must comply with legal security mandates. Wish Geeks Techserve helps companies meet these requirements by implementing industry-leading compliance strategies and ensuring secure handling of customer and business data.
5. Customized Cybersecurity Strategies for Businesses
Recognizing that no two businesses have the same security needs, Wish Geeks Techserve delivers customized cybersecurity services in India based on industry-specific challenges. Whether it's securing financial transactions, protecting healthcare records, or preventing e-commerce fraud, their team crafts personalized solutions to fit organizational requirements.
How Businesses Can Benefit from Strong Cybersecurity Measures
Adopting best-in-class IT security services India offers multiple benefits beyond just data protection. Businesses that invest in top-tier security measures experience:
Improved Customer Trust: Demonstrating commitment to data privacy enhances brand credibility.
Reduced Financial Losses: Preventing cyberattacks reduces the risk of hefty ransom payments, fines and revenue losses due to downtime.
Operational Efficiency: Secure IT environments enable seamless business operations without disruptions from malware or unauthorized access.
Competitive Advantage: Businesses that prioritize cybersecurity gain an edge over competitors who fail to implement robust security strategies.
Conclusion
Cybersecurity is no longer a choice but a necessity for businesses in Delhi-NCR and across India. Choosing the right cybersecurity solutions provider in India can make all the difference in ensuring business continuity and protection against cyber threats. Wish Geeks Techserve emerges as one of the best cybersecurity companies in India, offering cutting-edge IT security services in India that cater to businesses of all sizes. Their expertise in network security services in India ensures that organizations remain resilient against evolving cyber risks.
If you’re looking for a trusted partner to fortify your cybersecurity infrastructure, Wish Geeks Techserve is the go-to provider, ensuring that your business stays secure in the ever-changing digital landscape. Invest in strong security measures today and safeguard your business’s future!
#Best Cybersecurity Company in India#IT Security Services India#Cybersecurity Solutions Provider in India#Network Security Services in India
4 notes
·
View notes
Text
Facebook "New Rules"
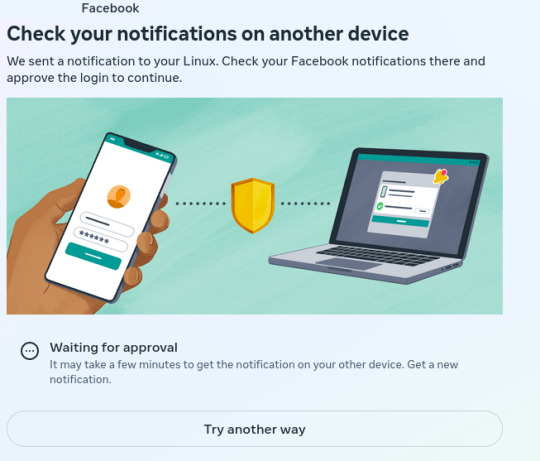
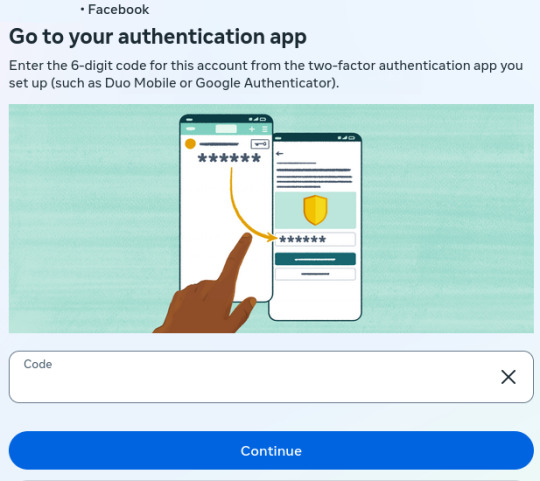
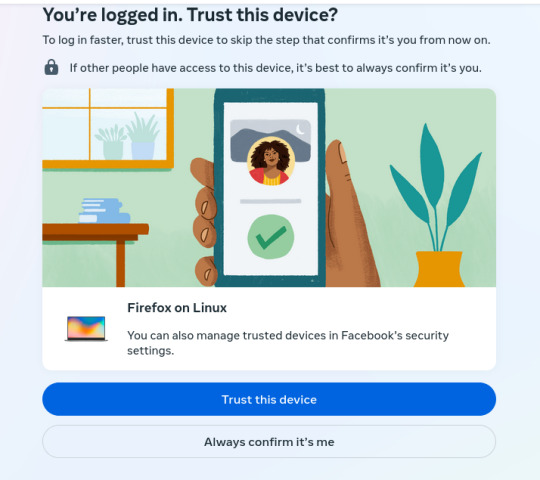
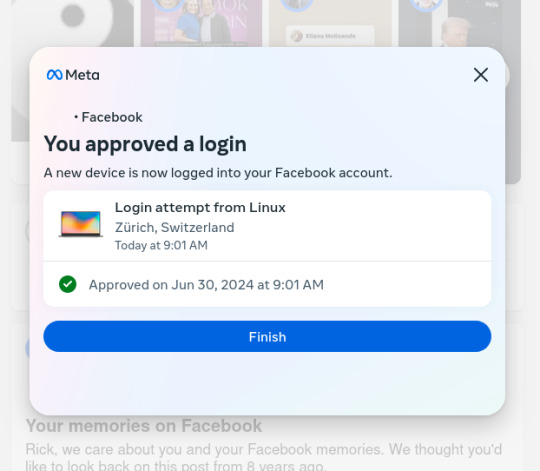
A few years ago, I decided to signup for an encrypted email service (Protonmail), to protect my emails from internet traffic Snoops. Later, I also signed up for a virtual private network service (ProtonVPN) which keeps the same internet traffic Snoops, from tracking my physical location and trying to mess with my browser's security. Since then several social media apps (for phones & laptops) have become "concerned" with security on 'their end' (so they say). But I've determined that they're LESS concerned with MY security than they are their own… So much so that they have surreptitious software installed to monitor what ALL of us do on social media. Lately, because I use a VPN service that can by my choice connect me to ANY server in the world that locks out 99% of snoops of all kinds all over the world. However, Facebook in its low-minded wisdom has become distrustful of MY logon attempts and of MY server addresses, even though ALL my credentials are in order. You may ask, "Rick are you having any mental problems?" No, not anything other than what I've always had..LOL! I just want to point out that the MORE security a user like any of us wants for their internet uses, the MORE the social media corps (and maybe the Govt) seem to "interrogate" our (my) intentions to be secure on our (my) end. Attached are 6 images that show Facebook's logon procedure because of MY security apps that are keeping me safer & more secure. And BTW..there is a false statement within the first one.. "We sent a notification to your Linux.." Linux is my operating system, the same type of technology that Windows is, but it's Not Windows and it's Not email. So it's impossible to "send a notification" to my operating system!! Trust me on this.. Anyway here are the images of the messages I get from Facebook Every Time I simply want to login to my Facebook account:
1 This is bullshit. Linux is an operating system, not an email address or a social media app:
2 It's not Google Authenticatior..LOL!
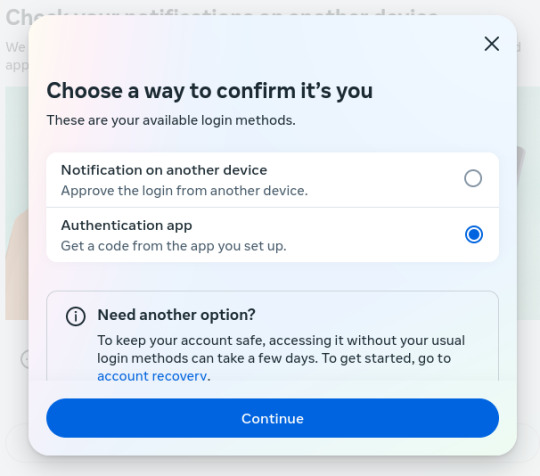
3. This should've been the 2nd question after my Password was entered! I don't need an education on authenticators or how to use them. I'm old but not stupid or naive, FFS!
4. If I'm logged in, I've already trusted this device. How moronic can you assholes be?
5. Okay Okay. I've entered all my info that's protected and now you're asking me if it's REALLY ME? Are you phucking serious right now??

6. I approved a login from Zurich, Switzerland and you're letting me know that I approved it, but your final statement is "Finish"? The people in Switzerland are not "Finish", their Swiss!! Did your AI algorithm get world geography confused with nationalities?
Facebook has a legion of phucking idiots.. Or..they have phucking idiots programming their "AI" algorithm. .... .... .... Welcome to the Machine.... tic-toc-tic-toc-tic-toc-tic-toc-tic-toc.
10 notes
·
View notes
Text
How do I choose the top Forex trade copier services?

Choosing the best Forex trade copier service depends on several key factors that impact efficiency, reliability, and profitability. Here’s what you should look for:
1. Speed & Execution Time: A good trade copier should have low latency to ensure trades are executed in real time without delays. This is crucial for scalpers and high-frequency traders.
2. Compatibility: Ensure the copier is compatible with your broker and trading platform (MT4, MT5, cTrader, etc.). Some copiers also work via Telegram or other third-party integrations.
3. Copying Features: Look for features such as:
Risk Management Controls
Partial or Full Trade Copying
Reverse Trading
Multi-Account Copying
4. Reliability & Performance: Check for uptime, accuracy, and past performance. A copier with frequent lags or execution failures can lead to unnecessary losses.
5. Security & Privacy: The copier should securely transfer trade data without exposing your account credentials. API-based solutions or encryption methods offer better security.
6. Customer Support & Updates: A responsive support team is essential. Look for providers that offer live chat, email, or ticket support along with regular software updates.
7. Pricing & Fees: Some trade copiers have a one-time fee, while others charge a monthly subscription. Ensure the pricing model suits your budget and trading volume.
#forex education#forextrading#currency markets#finance#economy#investing#telegram signal copier#forex Copier#Forex trade copier
2 notes
·
View notes