#Ethical Hacker Course
Explore tagged Tumblr posts
Text
#Ethical Hacker course#Certified Ethical Hacker v12#Certified Ethical Hacker course#cyber security courses#CEH#HPA#High Performance Academy
0 notes
Text
How Hackers Crack Any Software
youtube
Educational Purposes Only.
Ever wondered how hackers manage to crack software? This video explains the step-by-step techniques hackers use to bypass software activation, from reverse engineering and key generation to online and offline activation exploits. We also cover how developers can protect their creations with secure coding practices, encryption, and obfuscation. While YouTube restricts in-depth demonstrations, Cyberflow’s Academy offers unfiltered, step-by-step guides and expert support to help you master these skills responsibly. Use code "HACKER30" for a 30% discount on membership for the next 48 hours.
#education#educate yourselves#educate yourself#ethical hacking full course#mind hacking#technology#free education#youtube#tips and tricks#ethical hacking#cybersecurity#hacking software#How Hackers Crack Any Software#step by step#hacking tips#hacking#Youtube
3 notes
·
View notes
Text
I will be unstoppable after I learn cybersecurity in an official capacity potentially preventing me from being a black hat hacker
but first I have to get an email to let me know when I start training
#the “ethical hacker” thing is so funny#I would not consider hacking on behalf of a company or government to be ethical/white hat work#unless it aligns with my ideology of course
1 note
·
View note
Text
Why 2025 Is The Perfect Time To Start Your Ethical Hacking Journey

The technological environment is growing at an alarming rate, and, as businesses move further into the digital age, they must rely on technology to store so much data. This growth brings with it the ever so looming risk of cyber attacks and this is why ethical hacking is so valued. For anyone considering cyber security as a profession, it cannot be any better time than 2025 to begin your ethical hacking.
#cyber security ethical hacking certification#ethical hacking course with certificate#certified ethical hacker certification training#certified ethical hacker#certified ethical hacker certification#ethical hacking course#certified ethical hacker course#best ethical hacking course
0 notes
Text
Inside the Mind of a Hacker: How Ethical Hackers Outsmart Cybercriminals

In today’s digital age, the threat posed by cybercriminals is more pronounced than ever. As organizations increasingly rely on technology, the need for robust cyber security measures has become paramount. This is where ethical hackers step in, using their skills to protect systems from malicious attacks. For those interested in pursuing a career in this critical field, a cyber security course in Thane can provide the foundational knowledge and practical skills needed to succeed. Let’s delve into the mind of a hacker and explore how ethical hackers outsmart their adversaries.
Understanding the Hacker Mindset
To effectively combat cybercrime, it’s essential to understand the mindset of hackers. Cybercriminals are often driven by financial gain, political motivations, or even the thrill of the challenge. They continuously evolve their strategies, using sophisticated techniques to exploit vulnerabilities in systems. Ethical hackers, on the other hand, adopt a similar mindset but with the intention of safeguarding information rather than compromising it.
By enrolling in a cyber security course in Thane, aspiring ethical hackers can learn to think like cybercriminals. This includes understanding various hacking techniques, such as phishing, malware deployment, and social engineering. Equipped with this knowledge, they can develop more effective defense mechanisms against these threats.
The Role of Ethical Hackers
Ethical hackers play a crucial role in the realm of cyber security. Their primary objective is to identify and rectify vulnerabilities in systems before they can be exploited by malicious hackers. They employ a variety of tools and techniques to conduct penetration testing, vulnerability assessments, and security audits.
One of the significant benefits of taking a cyber security course in Thane is gaining hands-on experience with these tools. Students learn how to use software such as Wireshark for network analysis, Metasploit for penetration testing, and various programming languages for writing scripts and automating tasks. This practical knowledge is invaluable, as it allows ethical hackers to replicate the tactics used by cybercriminals and anticipate their next move.
Strategies Used by Ethical Hackers
Ethical hackers employ several strategies to outsmart cybercriminals. Here are a few key approaches they utilize:
Continuous Learning: The cyber security landscape is always changing, with new threats emerging regularly. Ethical hackers stay updated with the latest trends by participating in workshops, webinars, and, most importantly, taking comprehensive courses like a cyber security course in Thane. This continuous education allows them to adapt their strategies and tools to counteract evolving threats.
Red Team vs. Blue Team Exercises: In many training programs, ethical hackers participate in simulated attacks, often referred to as Red Team exercises. In these scenarios, they play the role of attackers, while a Blue Team defends against them. This collaborative environment helps them understand both sides of the equation, sharpening their skills in a practical context.
Threat Intelligence: Ethical hackers also rely on threat intelligence to predict potential attacks. By analyzing data from previous cyber incidents, they can identify patterns and trends, helping organizations prepare for future threats. Many cyber security courses in Thane cover this vital area, ensuring students can gather and analyze intelligence effectively.
Importance of Ethics in Hacking
A critical aspect of being an ethical hacker is adhering to a strict code of ethics. Unlike cybercriminals, ethical hackers operate with integrity and transparency. They obtain proper authorization before testing any system and report vulnerabilities to the appropriate stakeholders without exploiting them.
This ethical framework is often emphasized in cyber security courses in Thane. Students learn not only the technical skills needed for hacking but also the legal and ethical implications of their work. Understanding these principles is essential for fostering trust and accountability in the cyber security field.
Career Opportunities for Ethical Hackers
The demand for ethical hackers continues to grow as organizations prioritize cyber security. A cyber security course in Thane can open various career paths, including roles as penetration testers, security analysts, and security consultants. With businesses of all sizes seeking to bolster their defenses, skilled ethical hackers are becoming increasingly valuable assets.
In addition to traditional employment, ethical hackers can also explore freelance opportunities or consultancy roles, providing their expertise to organizations on a contract basis. The versatility of this career path makes it an attractive option for those passionate about technology and security.
Conclusion
As cyber threats continue to evolve, the importance of ethical hackers cannot be overstated. Their ability to think like cybercriminals while maintaining a commitment to ethical standards is what sets them apart. For those considering a career in this dynamic field, a cyber security course in Thane provides the essential skills and knowledge required to excel.
By understanding the hacker mindset, mastering essential tools, and adhering to ethical principles, ethical hackers play a pivotal role in safeguarding digital assets. As we look to the future, the demand for these professionals will only increase, making now the perfect time to embark on a journey into the world of cyber security.
#cyber security course#cyber security#cyber attack#cyber security threats#technology#data security#ethical hacking#ethical hacker#network security#dataprotection#hacking#security#network securiy#cybercrime#cyber security course in thane#ethical hacking course
1 note
·
View note
Text
Ethical Hacker Course: Key Skills You Will Learn
With the increasing number of cyber threats and data breaches worldwide, the demand for skilled ethical hackers is higher than ever since the past two decades. An ethical hacker course equips professionals with the knowledge and hands-on experience needed to identify, exploit, and fix the security vulnerabilities in networks & systems. If you are looking for career in cyber security, here’s a very depth analysis at the important skills you will learn in an ethical hacking course.
Core Modules in an Ethical Hacker Course
An ethical hacking course covers various modules designed to provide a solid foundation in cybersecurity. Some of the core modules include:
1. Introduction to Basics of Ethical Hacking
Understanding the role & responsibilities of an ethical hacker
Legal & ethical considerations in cybersecurity
Different types of cyber threats and attack methodologies
2. Footprinting and Reconnaissance
Gathering information about a target system using open-source intelligence (OSINT)
Using tools like Nmap, Maltego, and Google Dorking to identify vulnerabilities
Techniques such as passive and active reconnaissance
3. Scanning Networks and System Hacking
Identifying open ports, services, and vulnerabilities
Exploiting security loopholes using vulnerability scanners
Password cracking techniques, privilege escalation, and maintaining access
4. Malware Threats & Attack Vectors
Understanding types of malware: viruses, worms, ransomware, and trojans
Analyzing malware behavior & prevention strategies
Using sandboxing & endpoint protection tools
5. Web Application Security
Detecting common web vulnerabilities like SQL injection, cross-site scripting (XSS), and cross-site request forgery (CSRF)
Security testing methodologies for web applications
Understanding Secure Software Development Life Cycle (SDLC)
6. Wireless Network Security
Understanding Wi-Fi encryption standards (WEP, WPA, WPA2, WPA3)
Conducting wireless penetration testing
Preventing wireless network intrusions
7. Cryptography and Network Security
Basics of encryption, hashing, and digital signatures
Implementing secure communication channels
Understanding of VPNs, firewalls and Intrusion Detection Systems (IDS)
Hands-On Learning: Practical Exercises and Real-World Scenarios
Ethical hacking courses emphasize hands-on learning to prepare professionals for real-world cybersecurity challenges. Some key practical aspects include:
Penetration Testing Labs: Simulated environments where students can practice exploiting vulnerabilities.
Capture The Flag (CTF) Challenges: Gamified cybersecurity competitions to test hacking skills.
Incident Response Simulations: Handling real-world cybersecurity incidents, including data breaches and denial-of-service (DoS) attacks.
Reverse Engineering and Exploit Development: Analyzing malicious code and writing exploits for vulnerabilities.
By working on real-world cybersecurity scenarios, ethical hackers develop real time problem solving skills and learn to think like attackers to defend systems very effectively.
Important Tools & Tactics Used by Ethical Hackers
Ethical hackers used the various tools and techniques to perform security assessments. Some of the essential tools include:
Kali Linux: A penetration testing operating system with a wide range of security tools.
Metasploit Framework: A very powerful tools for developing and executing exploit any code.
Burp Suite: A web vulnerability scanner used for security testing of web applications.
Wireshark: A network protocol analyzer for capturing & analyzing network traffic in the systems.
John the Ripper and Hashcat: Password cracking tools.
Nmap and Zenmap: Network scanning tools for identifying vulnerabilities.
SQLmap: A tool that used for detecting & exploiting My SQL injection vulnerabilities.
Using these tools, ethical hackers perform penetration testing, vulnerability assessments, and forensic analysis to strengthen an organization’s security posture.
Complement Certifications CEH for Career & Growth:
While the Certified Ethical Hacker certification is a highly demanding credential, comparing it with other certifications can further improve your career opportunities. Some of the complementary certifications include:
1. Offensive Security Certified Professional (OSCP)
Focuses & Improve on hands-on penetration testing skills.
Requires candidates to complete a challenging 24-hour practical exam.
Those who are looking to specialize in offensive security.
2. GIAC Penetration Tester (GPEN)
Covers advanced penetration testing techniques.
Recognized by government and enterprise cybersecurity teams.
Focuses on exploit development, privilege escalation, and password attacks.
3. Certified Information Systems Security Professional (CISSP)
Covers broad cybersecurity domains, including risk management and governance.
Ideal for those aspiring to take on security management roles.
Highly valued by employers worldwide.
4. CompTIA PenTest+
Covers penetration testing methodologies, tools, and reporting.
A good alternative for those starting in ethical hacking.
5. EC-Council Certified Security Analyst (ECSA)
Advanced ethical hacking certification that builds on CEH.
Covers in-depth penetration testing methodologies.
Ideal for professionals looking to specialize in vulnerability assessment and red teaming.
Conclusion
An ethical hacker course provides professionals with in-depth knowledge and hands-on experience in cyber security programs. From network scanning and malware analysis to penetration testing and web security, ethical hackers develop a very powerful skill set to protect organizations from cyber threats. With the right combination of certifications and in depth practice, ethical hackers can advance their careers and contribute to strengthening global cyber security defenses. Are you ready to take on your ethical hacking journey? Start learning today and build a rewarding career in cybersecurity!
#ceh certification requirements#ethical hacking course#hacking course#ethical hacking courses#ethical hacker course
0 notes
Text

“To beat a hacker, think like one” Ethical hacker Not leaves behind any evidence that they were there. Ethical hackers earn ₹3,18,370 and above per month. We prepare for (CEH), (OSCP), (and CPT) Certification for newbies to professionals. Get hold of us today.
Contact us: +91 9315519124 / +91 8287266809 Email: [email protected] Website: https://www.eduvatech.com/
#learningopportunity#studynoida#learning #learningindias
#online cyber security in noida#online ethical hacker training#eduvatech#ethicalhacking#online courses#online training#ethical hacking certification#ethical hacking course#ethical hacking training#online study adcademy#online study
0 notes
Text
Introduction To Cyber Security- Aisect Learn

Aisect Learn presents a comprehensive opportunity to become an expert in cyber security through our highly regarded ethical hacker training. Our program encompasses a wide array of topics, including Cyber Security Basics, Hacking Methodologies, and the indispensable role of Security professionals within organizations.
In today's digital landscape, where threats are constantly evolving, selecting the best course for cyber security is pivotal. Aisect Learn stands out as a premier choice, offering a cutting-edge cyber security course online. This program equips you with the skills and knowledge needed to combat cyber threats effectively. Our curriculum is designed to empower you as a Certified Ethical Hacker, arming you with the ethical hacking techniques required to secure digital environments. Visit now to Enroll Today!
#ethical hacker training#best course for cyber security#cyber security course online#certified ethical hacker
0 notes
Text






December 03, 2024
338/366 Days of Growth
I restarted my dawn walks, as Rio de Janeiro is hot as hell, and the only way to walk without fainting is very (very) early in the morning.
I am also making doodles for my habit tracker (my drawing needs to me improved 😝 but it is cute enough for me).
I delivered my MBA essay and got a 9.0/10.0... I am pissed off due to this 1.0 point, as the reason to take it off was not on the task description 🙄 And yes, I am a nerd 🤓 I wanted that 1.0.
I am in the finale module now, and there's just the final project to deliver, do I will be able to enjoy the holidays in peace ✌🏾
This year was wild and tough, but I feel like recording everything here helped me understand that I did a lot, giving my best. So, I am grateful for it, and I hope my planting provides me with good things for 2025.
I must finish my network fundamentals book and start Cisco's Ethical Hacker course!
PS: Saw this orange cat while I was walking, so cute!
#studyblr#study#study blog#daily life#dailymotivation#study motivation#studying#study space#productivity#study desk#cyber security#cybersecurity#stemblr
97 notes
·
View notes
Text
I currently have two AUs that I don't exactly know what to do with or what to properly call them LMFAO- I'll probably write something on Ao3 for it eventually since there's a ton of BillFord and FiddStan in there but yeah-
1st AU: Timelord Stanford (Dr Who what if)
This case was inspired by an RP I had with someone's Bill Cipher on @gftimelord where the triangle starts to be on the mend with Stanford after their ruined past. This to me makes sense because the Doctor is inherently very lonely despite the savior god complex. In that AU where Ford is functionally immortal and Stan and Fidds both at some point die due to his complacency and arrogance— he searches for a companion that can actually keep up with him.
So when Bill visits him during one of those window hours set by the Theraprism, they talk about the triangle's impending demise with their plans to essentially erase him from existence. It's not an outlandish idea given that any inpatient seen as a lost cause would or could be disposed of when it comes to cosmic entities. It's simply the easier option.
The doctor(Ford) is more impulsive, nonchalant, and egoistic compared to his counterparts because he does have the walk to back his talk(this man has been broken by the nightmares and guilt he carries from the deaths he caused; also time war) problem being he doesn't fear death as much as he fears being alone. He's had a fair share of close calls with the grim reaper, but always like some horrible twist he survives. After all, it is a saying that we covet the most what we don't have.
So yeah, he jailbreaks Bill essentially and whatever power limiter is stuck on the triangle get tied to his sonic screwdriver instead and they simply go around the multiverse doing whatever. Most of the reason why Ford isn't caught yet largely has to do with how scared most entities are of him. The doctor is never armed, but it doesn't mean he won't kill.
2nd AU: Modern Era AU (Set in 2024)
This one is more of a shitpost thanks to the young trio I drew a little while back, I'll draw more of them for this at some point while I also try and figure out a decent human Bill design that I like in my artstyle.
But this AU heavily features these four idiots as Undergrad students fucking about college life as they would. This AU is supposed to feature like a more cultivated genius Stanley based around my own dynamic with my brother since I do like me some happy Stan twins.
It just so happens that Ford is also a very much EQ negative idiot and falls for an upperclassman(one year his senior) in BSSE[Software Engineering] who is a close friend to Fidds. He goes by 'Cipher' as an alias since he's a prodigy for his age and very young ethical hacker.
So yes, that's where Bill comes in. Haven't figured out what I want his full name to be yet shoot me some ideas! Ford is very shy when it comes down to talking with Bill whereas Stan is completely chill.
Both Stan and Bill get along very well in this AU because they're similarly chaotic the same way that Fidds and Ford get along because they're the ones holding the other two back from doing something undeniably stupid for shits and giggles.
All of them share some fundamental subjects together(i.e. Math, Biology, Chemistry, Physics, Statistics, Research, History, etc.) or take elective courses just so they could chill together. Stan is typically the one who adjusts to the schedule of the other three since he takes BSBA[Business Administration] and is the odd one out when Ford does BSCMB[Cellular Molecular Biology] and Fidds does BSEE[Electrical Engineering].
The FiddleStan in this AU is gonna be c r a z y mostly due to Fidds in this AU is the heir to his family's computer company, so lowkey spoiled nepo baby but also on a very tight leash with his parents. Stan is the kid where 90% of his childhood was parents either forgot him or straight up did not give a flying fuck. So these two kinda work as complements and it's why I decided to pair them together after chatting with a friend about the group dynamics.
So yeah, simpy and adoring Ford and silently aware but shy Bill + rebellious Fidds and supportive Stan. All the more when I actually plan for this AU to have some typical gravity falls shenanigans anyway thanks to a place on earth called the Oregon Vortex.
[I'll likely make fics and comics of these AUs, reply to this post if you want to be tagged for whenever I post something]
Yeah I need to properly name these AUs.
#gravity falls#gravity falls stanford#stanford pines#gravity falls ford#grunkle ford#ford pines#gf stanford#stanford#gravity falls au#gf stanley#stanely pines#standford pines#stan#gravity falls stanley#stan pines#grunkle stan#stan and ford#stan twins#stanley pines#bill x ford#bill x stanford#gf bill cipher#gravity falls bill cipher#bill cipher#gravity falls bill#billford#bill cipher gravity falls#fiddlestan#fiddleford mcgucket#fiddleford hadron mcgucket
30 notes
·
View notes
Text
𝐀𝐧𝐢𝐦𝐚𝐥𝐬
cw: gender neutral reader, camfecting, hacking, spying, not consented voyeurism, nonconsensual, mutual masturbation, poor research into hacking, mutual pining, you read the tags and decided to read this - don't come at me.
Jake Donfort was a pervert.
Gods, he hated himself. Freak, pervert, degenerate, disgusting.
What went wrong? He used to be a white hat hacker. Now he is on the run from the government. And to top it off, now Jake does this.
Jake got distracted. And the culprit? It was you. The victim? Was also you.
Of course he could do the work he gave to you on his own. It was nothing for him. One of the reasons why he involved you was because it divides the workload. He could focus on more important things that you couldn't do. It was teamwork. And he honestly loved it. He loves working with you. He loves talking to you. He loved knowing you. He hated how life turned out but he loved that it made him meet you.
He also loved you. Though he was still in the initial stages of acceptance, the severity of his feelings didn't escape him. Jake wasn't stupid. Jake, was very, very, very smart.
But you see, he has not had the best upbringing. It was complicated, at times toxic and traumatic. Jake grew up to be smarter than his parents, more nuanced thinking and more logical mindset. He was independent, and had been for a long time. Jake could take care of himself. In every way of the words imaginable. One of things he prided himself on was that he was resourceful.
He could take care of his needs too. On his own. He didn't need to go out and find people to satisfy his needs and take care of him. He wasn't a sex addict by any means, he has only ever had it once. Didn't like it; cause he had no feelings for the girl.
But porn. Jake has a very specific, niche genre of porn that can get him off with a good climax.
He doesn't masterbate a lot. Jake is a busy man, especially now. The stress doesn't help much either. When he does, his collection of porn helps him jack off nicely. Though nowadays… there is someone who is enough to make him to bust in his jeans. Someone, who can single handedly destroy him without even knowing of the power they hold. So now he had started imagining that someone when he watched porn and he swears that's gonna be the death of him.
Because it was. just. so. painful! For the first time in a very long time he himself wanted someone carnally. Romantically and sexually. He had started masterbating every night now. That's unlike Jake Donfort. But he couldn't. You lived somewhere else, far away from him. And even if you didn't, he can't risk yours or his safety. Plus the circumstances won't allow it, there is something new everyday. Jake was frustrated.
Baby, I'm preying on you tonight
Hunt you down eat you alive
Especially tonight. He doesn't know what happened all of a sudden. But he just couldn't control it anymore. He was like an animal. He felt like a rabid dog; drooling from the mouth, barking incessantly, dying for a prey of his own tonight. But not just any prey, you.
Just like animals
Animals
Like animals
Jake did what he used to despise. Jake did what he was against. Jake did what was morally, ethically and legally wrong. Though he had said fuck you to legality a long time ago.
When Jake asked you to keep searching Hannah’s phone this time, he had embedded a trojan in it. And when you downloaded that file, all happy and elated to find something new to share to Jake, unbeknownst to you that malware infected your own device.
Camfecting, in the field of computer security, is the process of attempting to hack into a person's webcam and activate it without the webcam owner's permission. The remotely activated webcam can be used to watch anything within the webcam's field of vision, sometimes including the webcam owner themselves.
Blackshades, after a good amount of research, seemed like a good enough trojan horse to infect your webcam. He was glad he never advised you to cover your computer’s camera. Your profile picture and the few you uploaded used to be enough for his jerking off session every night. But not anymore. He needed to be inside you. In your warm hole, with your muscular walls clinging onto him as the rings sucked him in. The way you’d moan for him, because of him, with him.
Maybe you think that you can hide
I can smell your scent for miles
Jake couldn't believe it. His luck was shit usually. He had given up on fate, deciding to trust himself only now. Well, now you too. But maybe he can lax that decision… because there you were, standing in front of your computer in your room. And you were about to take off your t-shirt.
Jake sucked in a harsh breath. At first his eyes couldn't leave the screen and everything felt like it was going in slow motion. It felt like you were teasing him, slowly pulling your t-shirt up and up and showing off the smooth expanse of your skin. From your hips to your waist, to your torso, to your stomach, to your- Jake closed his eyes and looked away. It felt too wrong. Way too wrong. His conscience wouldn't let him. This was wrong, so wrong.
But then his eyes flitted towards the screen accidentally and his breath got caught in his chest. As if that wasn't enough for you, you bent down to take off your lowers. Then your underwears.
There you were, in all your glory, bare chest and nipples pebbled by the cold air of your room. His eyes roamed over your body; naked, bare, all for him to see as much as he wanted.
Holy. Fucking. Shit.
You were gorgeous.
Jake felt like a pathetic wet mouse the way his heart raced at the sight of the person he had fallen for naked in front his eyes.
Before he could a good look down there you turned around and walked towards your bed. Your ass swayed as you moved to your bed which was conveniently right in front of your computer. An awful choice for you, a blessing in disguise for him. It was hypnotic.
Jake felt something stir in his gut as it travelled lower to his cock and he could feel it harden as blood rushed till the tip slowly. His heart pounded in his chest. Because you didn't change into comfier clothes. You laid on your bed and spread your legs open. Wide open.
Jake’s cock stood erected. Confined in his jeans and he hastily pushed it down once he caught his bearings. It slapped against his all black hoodie. Red and hard.
You winced as your touched yourself down your chest and in between your legs. You let out a soft moan as your hands made contact with your genitalia.
So what you trying to do to me
It's like we can't stop, we're enemies
“Ah-” Your eyebrows knitted and lips parted as you touched the spot which gets you turned on always. In the confines and solitude of your room you didn't feel the need to silence your pleasure and so Jake got to hear and watch live porn and pornographic moans as well.
While your hand played with your sex, Jake took care of his. His large, veiny hands stroked his cock up and down. He rubbed his tip then stroked his cock, rinse and repeat. He wants to throw his head back in pleasure but doesn't want to take his eyes off of the spectacle happening just for his eyes.
So if I run it's not enough
You're still in my head forever stuck
So you can do what you wanna do
You stroked your own privates slowly at first, playing with it with your fingers, teasing yourself. You touched your nipples with the other hand, pinching and twisting them till they became darker, perkier. A particularly good hand movement at your actions made him wince but it was nothing compared to when your legs quivered, your back arched, your moans grew louder and filthier. You looked so god damn hot to him. And then…
“Jake.”
Jake felt like time stopped. His hand stopped, the air conditioning in his room sounded distant, he felt like his brain stopped functioning. Did he hear it right?
“Oh Jake, Jake… ah!” He did, in fact, hear it right.
You were moaning his name while you touched yourself.
You were moaning his name.
You were moaning his name.
Jake couldn't believe his ears – MC was moaning his name, they were imagining him, they wanted his touch down there.
This was enough of a catalyst to spur him on, to tighten his hands around the base of his cock as he gave it a good squeeze and resumed stroking it. His other hand played with his balls. Jake’s moans filled his apartment. He grunted and barred his teeth all while exhaling air aggressively from his nostrils. He was trying to hold it in. It didn't work. A pathetic mewl later he came. All over his hands, dirtying his pants and his screens. That would have irked him, because he hated anything on his precious screen, but the way it looked as if he came on you? He was a goner.
“Oh God- Ah- Ah- Just like that- yes- Oh my God!” Your head dug into your pillow as you came. You came hard. It must have been a particularly good imagination with the way you came so much.
But the fact that you came together was enough to soothe Jake’s heart. Even if he couldn't have you, he still came with you. As your heaving chest slowed into a rhythm, you got up. And when you did your eyes landed on your computer. It felt like you were looking at him, right into his soul.
Jake, despite being a seasoned hacker, who knew that there was no way you could see him or know what he was doing, felt his heart skip a beat. He stared wide eyed. You moved towards your computer and instead of being scared his lustful eyes raked your naked body. From beside the computer you picked up your water bottle and gulped it down in one go.
“Why did I keep it here?” You asked yourself and Jake felt himself breathe again and then a thought crossed his mind. Jake let out a low chuckle.
…You can't stay away from me
I can still hear you making that sound
Taking me down rolling on the ground
I hope you are doing good, MC.
Remember, I am always with you ;)
You picked up your phone at the familiar sound of the ring. He saw your eyes widen. He relished in it.
#duskwood#duskwood jake#jake#jake x reader#jake x mc#duskwood jake x reader#duskwood jake x mc#jake smut
7 notes
·
View notes
Text



## What’s a Cyber Forensic Investigator?
Master post - part 1 • part 2
You must have heard bout forensics yk investigating bout dead people who might have been killed and all
You must have seen shows on those topics too.Cyber forensic investigator is just of same kind but investigating through all types of modern gadgets.
Catching hackers and all but cooler



### The Money Talk: How Much Do They Make?
- **Cash Money**: Expect to rake in about $60k to $120k a year. If you are very much experienced and skilled then you can expect about 150k+ a year.(obv different countries and companies may have different wages)
### Companies That Want You
- **Tech Titans**: Google, Amazon, Facebook—they all have requirement for such heroes
- **Gov Jobs**: FBI, CIA—basically every spy agency wants you.
- **Cybersecurity Firms**: CrowdStrike, McAfee—so every gateway you go you gonna have opportunities everywhere.
### What Other Forensic Investigators Are There?
- **Forensic Pathologists**: Real-life detectives who figure out how someone died. Less tech, more science.
- **DNA Analysts**: The ones matching DNA samples
- **Forensic Accountants**: Following the money to catch fraudsters and scammers
- **Toxicologists**: Poison experts, figuring out if someone’s been covertly poisoned. (Yeaa yk snow white story)
### What’s the Work Environment Like?
- **The Lab**: Imagine a room filled with more screens than your gaming setup. Gadgets galore, maybe even a Red Bull or two
- **On the Move**: Sometimes you’re out in the field, collecting evidence. Think of it like collecting rare items in a game.
- **Remote Vibes**: You could be solving cybercrimes from your bed in your PJs .
### How Long Does It Take to Become One?
- **Time Investment**: About 4 years for a bachelor’s, and then 1-2 more years for a master’s if you’re going all-in. So, 5-6 years total. But hey, good things take time, right?
### What Do You Study?
- **Cybersecurity/Computer Science**: Your main jams. Think of them as the ultimate cheat codes for this career.
- **Digital Forensics**: Specialized courses where you learn to be a digital ninja.
- **Law and Ethics**: Learning how to catch the bad guys without breaking the law yourself. (You yourself don't want to be troubled obviously)
### Subjects You Need to Get Into It
- **Math**: Yep, but not the boring kind—more like coding and algorithms.
- **Computer Science**: Your go-to for everything techy.
- **Optional Nerd Points**: Chemistry/Physics if you’re into hardware forensics or just want to flex those brain muscles.
### Work Hours: What to Expect?
- **9 to 5-ish**: Standard hours if you’re working for a company, but expect some late nights or weekend shifts when big cases pop up.
- **On-Call Madness**: Sometimes you’re on-call like a digital firefighter. Cyber-attack at 3 AM? Time to suit up (or log in) and handle it.
- **Flexible/Remote**: If you’re lucky, you can work from home. Just remember, no solving crimes in your underwear during Zoom meetings!
### Interview with a Cyber Forensic Investigator
**Interviewer**: What’s a day in the life of a cyber forensic investigator?
**Cyber Sleuth**: Imagine rolling out of bed, grabbing your coffee, and diving into cases. I’m talking analyzing hard drives, sifting through emails, or tracking down cyberattack origins. Some days it’s all data, other days I’m working with law enforcement or testifying in court. Never a dull moment!
**Interviewer**: What’s the coolest case you’ve worked on?
**Cyber Sleuth**: Helping bust a phishing ring that was scamming millions. Tracked their digital footprints, caught the culprits, and recovered their loot. Felt like a total legend.
**Interviewer**: Ever seen some dark stuff, like murders?
*Cyber Sleuth**: Yeah, I’ve stumbled across some pretty grim stuff. It’s not all memes and malware—sometimes it’s serious business. But catching those bad guys makes it all worth it.
**Interviewer**: Have you ever been on the dark web?
**Cyber Sleuth**: Oh, for sure. It’s like the sketchy underbelly of the internet. Lots of shady deals. I go there when I need to, but it’s not a fun hangout spot.
**Interviewer**: How dark can a case get?
**Cyber Sleuth**: It can get really intense. I’ve worked on cases involving human trafficking and other serious crimes. It’s tough, but making a difference makes it worth it.
**Interviewer**: Any advice for someone who wants to get into this field?
**Cyber Sleuth**: Stay curious and keep learning. Tech evolves fast, so you’ve gotta keep up. And don’t be afraid to dig deep—sometimes the answers are buried in tons of data, but finding them is like hitting gold.


So if you’re into tech and have subjects like mathematics , chemistry and physics then you are all set to start your journey.i have seen ppl running for a common a job and all and they are not even specified about what they want. So just research and find out what you want.

#masterpost#career#self development#light academia#study blog#academic validation#academic weapon#student life#study#study motivation#study with me#studyblr#studyblr community#forensics#computer#codeblr#masterpostjam
20 notes
·
View notes
Text
The Complete Manual for Understanding Ethical Hacking
In order to evaluate an organization's defenses, ethical hacking—also referred to as penetration testing or white-hat hacking—involves breaking into computers and other devices lawfully. You've come to the correct spot if you're interested in finding out more about ethical hacking. Here's a quick start tutorial to get you going.

1. "Getting Started with the Basics"
Networking and computer science principles must be thoroughly understood before getting into ethical hacking. Here are some crucial aspects to pay attention to: Operating Systems: Acquire knowledge of several operating systems, with a focus on Linux and Windows. Learning Linux is essential because a lot of hacking tools are made to run on it. Networking: It's essential to comprehend how networks operate. Find out more about
protocols include HTTP, HTTPS, DNS, TCP/IP, and others. Understanding data flow across networks facilitates vulnerability detection. Programming: It's crucial to know at least a little bit of a language like Python, JavaScript, or C++. Writing scripts and deciphering the code of pre-existing tools are made possible by having programming expertise.
2. Making Use of Internet Resources To learn more about ethical hacking, there are a ton of internet resources available. Here are a few of the top ones: Online Education: Online learning environments such as Pluralsight, Coursera, and Udemy provide in-depth instruction in ethical hacking. "Penetration Testing and Ethical Hacking" on Pluralsight and "The Complete Ethical Hacking Course: Beginner to Advanced" on Udemy are two recommended courses. Channels on YouTube: HackerSploit, The Cyber Mentor, and LiveOverflow are just a few of the channels that offer helpful tutorials and walkthroughs on a variety of hacking tactics.
3. Exercising and Acquiring Knowledge The secret to being a skilled ethical hacker is experience. Here are some strategies to obtain practical experience:
Capture the Flag (CTF) Tournaments: Applying your abilities in CTF tournaments is a great idea. CTF challenges are available on websites like CTFtime and OverTheWire, with difficulty levels ranging from novice to expert. Virtual Labs: It is essential to set up your virtual lab environment. You can construct isolated environments to practice hacking without worrying about the law thanks to programs like VMware and VirtualBox. Bug Bounty Programs: Websites such as HackerOne and Bugcrowd link corporations seeking to find and address security holes in their systems with ethical hackers. Engaging in these initiatives can yield practical experience and financial benefits.

Dedication and ongoing education are necessary to learn ethical hacking. You can become a skilled ethical hacker by learning the fundamentals, using internet resources, and acquiring real-world experience. Always remember to hack wisely and ethically. Cheers to your hacking! I appreciate your precious time, and I hope you have an amazing day.
9 notes
·
View notes
Text
Doug's first appearance in New Mutants 13 was, fun what with accidentally blowing up a Sentinel, but his second appearance is also worth mentioning.
X-Men 180 is perhaps better known for A) the scene where Kitty and Storm discuss Kitty's issues with Storm adopting a new appearance and attitude (Her leather jacket and mohawk punk phase) and B) The lead in to the X-Men going to be part of the Secret Wars maxi series, but there's
This scene is before Doug was revealed to be a mutant. He was just the kid from Salem Centre Kitty was spending a LOT of her free time with, and what would these two computer nerds be doing in the mid 80's? Yup, going to the mall!
Specifcially, the arcade!!
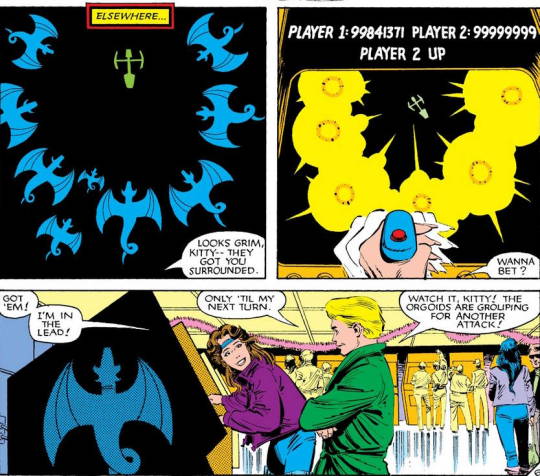
That is THE most spaciously laid out arcade I have ever seen, but that's not really the important bit here.

Though I'm pretty sure you can't actually DO that with arcade games just by scoring too high, I can easily believe these two being the bane of anyone trying to crank out a buck from video game addled teenagers with rolls of quarters!
And this is a slightly earlier version of Doug, since he doesn't know he or Kitty are mutants, he's cockier than we would see him once his inferiority complex kicks into high gear as Cypher. Here, he's Doug Ramsey, computer software genius, nerd and video game ace who is out having fun with the most amazing girl he's ever met before.

...but first and foremost, he's a good friend. (He'd have to be to deal with this level of emotional baggage infodumping. Good grief Kitty!)

Awww! These two are so sweet together!
Meanwhile, someone else is brooding, this time over Kitty and Doug... and not in an especially wholesome way

I should point out that at this point in time, Kitty is fourteen (confirmed in the previous issue where Storm specifically notes that Kitty was not yet fifteen), and Piotr is somewhere in that vague are of late teens/early twenties.
I believe, at the time that it was possible for 14 year olds to marry in the USSR, but it was far from the norm.
I should also add, in the interest of fairness, that during the slightly earlier BroodWar arc, thinking they were both going to die, Kitty asked if Piotr would become her first sexual partner, and Piotr gently turned her down (I know that's a very, VERY low bar to clear, but it should be mentioned)

This is setting the scene for Piotr falling for someone else during Secret Wars, an alien woman named Zsaji, who is a sort of walking, healing, plot device rather than a character with any agency, who is regretably fridged to give Piotr some angst, and also to confirm the breaking up of Piotr and Kitty as a possible couple and being anything other than team-mates for a great many years. There's an interesting article on Zsaji's story here, if you're interested.
So Piotr does seem to have some resentment towards Doug for taking HIS Katya (Even Wolverine, rarely the world's best agony uncle, tell's him that if that's how he views the situation, he's already lost Kitty and that's definitely for the best)
Later, as Doug has recently been invited to become a student of the Massachussetts Academy, a school the X-Men know is run by Emma Frost of the Hellfire Club, even if she is currently believed to be comatose (long story), the X-Men consider a course of action, and Chuck Xavier once against shows us that to him, "Ethics" is something for other people...

Now look, if Chuck knows that Doug is a mutant, that's one thing, he has a mutant detecting machine in the basement after all. But to casually "out" someone else was a mutant, without having any intent of ever telling the person themselves, that's just... not cool.

And yes, it may be a "quiet" power, but I don't think a Sentinel will give a rats ass about that, Doug has just as large a target on his back as anyone else.
Also, this is some years before the World Wide Web was a thing, though Doug was already established as a superbly skilled hacker on the still new and shiny thing called "The internet", thanks to his powers, so you'd have thought SOMEONE on the X-Men would have considered that a viable talent to develop, even if only as a support operative.
Kitty's comment does reference the precsse situation when Doug actually WAS inducted into the wild and wacky world of mutant-dom... When Warlock crashed on Earth, Xavier was out of town and the New Mutants REALLY needed someone to be able to talk to the confused and desperate alien (and ironically, as it turns out, Xavier would have done no good, as Warlock is telepath-proof)
But it does allow me to post these amazing bits from New Mutants #21, as Sam rockets off to break the news to Doug about, well... his entire life... whilst wearing only a towel.

Whilst allows for Doug's gloriously snarky introduction to X-plots.


He DOES have a point!
Oh, and as for the resentment towards Doug from Piotr I mentioned earlier? You might be asking if that lingers?
Well, one has to wonder, as in a much later story, Uncanny X-Men Annual #10, where the X-Men are de-aged by Mojo, and the New Mutants have to step up as temporary X-Men, the first time they meet in combat, what's the first thing mini-Colossus does?

Yup, punches Doug right in the crotch!
Methinks the Russian lad has some unresolved issues about our little omniglot.... LOTS of issues!
25 notes
·
View notes
Note
Honestly, the slight crumbs of worldbuilding are all the more frustrating because of how interesting they are.
Quirkless discrimination: it exists, given how okay the teachers are towards Aldera's bullying of Izuku. Sir Nighteye also thinks Izuku being Quirkless won't make him a good hero, using it as an insult towards him.
The Business Course and Support Course: WHAT DO THEY LEARN? I'd imagine some engineering and management classes/hands on labs in addition to the regular classes. Maybe internships with agencies/compnaies on a manigerial or engineering aspect?
Exactly! What’s the use of worldbuilding if you stay in the same spots the entire time? Keeping it safe is keeping it boring, and honestly that’s the biggest injustice for such an interesting and multifaceted world.
Like, we’ve seen people discriminate against Izuku because he doesn’t have a Quirk (even if the majority were literal children, and kids can be very cruel) - but is that just a him thing? We hardly ever (IF ever) see it elsewhere in BnHA. We hear about it it we don’t recognize its impact outside of being a traumatizing experience for our main. We don’t grasp just how widespread this issue is, and the fact that so many see it as an allegory for real-life disability in an ableist world makes it even more disappointing. We see no aids for those with destructive or harmful quirks, we see nothing for those who’ve lost their Quirks in some way (be it old age or losing it via accident), we see nothing to aid those who ARE disabled - we see none of that. I’m not expecting a Japanese man writing a Japanese-centric story to see it the same way other countries or cultures would, but it would be a genuinely interesting issue to showcase and get people discussing.
And let’s be honest, the other courses at Yuuei essentially don’t exist (save for the designers of the Support Course). What I wouldn’t give to see Business Course students debating the ethics of the hero world, or how to run agencies, or studying to get into law schools with Yuuei’s clout backing them up, or even getting government jobs! I would even take a Business Course kid being disillusioned with how corrupt and greedy the hero world is and having to confide in other students about their anxieties and frustrations. We could’ve had a legitimately interesting arc about 1-A or 1-B kids (or even Shinsou) getting to see other perspectives besides just “heroism is great and nothing is wrong!”
And the Support Course! Where’s the sidekicks, the rescue teams, the spies, or ANYTHING besides weaponsmiths? Where’s the tech kids who got into Yuuei to exercise their abilities in those branches? The hackers? The security experts? All of it would be so interesting to explore but we never see any of it!
I dunno. I really do love BnHA but the insistent refusal to explore any themes besides “let’s throw these inexperienced kids into an adult war” is severely frustrating and disappointing. I know Horikoshi isn’t (and shouldn’t be) expected to talk about everything, but even a little variety would be nice.
#she speaks#she answers#bnha critical#mha critical#horikoshi critical#honestly the worst part is how so many people ignore it too#i fully believe quirklessness is an allegory for being disabled. there’s no way it’s not#whether it’s mental disability or physical disability#either way the refusal to acknowledge it in YOUR WORLD when it directly affects YOUR MAIN is frustrating#not only that but now that we’ve SEEN afo stealing quirks it’s even more unacceptable#just once i’d like to see the pussycats having to experience quirkless discrimination due to that#idk it just severely pisses me off when i think about it#mutuals#i’m gonna say it: sometimes it feels like this show is propaganda#maybe i’m a little paranoid on that front though
37 notes
·
View notes
Text
The Wives Watch: Supernatural S2 E14-16
E14 - 🎶 My Daddy Shot Your Daddy in the HEAADDD 🎶
Amnesia my favourite of all the nesias
Demon Sam time babbyyy
Sam for the entire first half of the episode:

We will refer to Demon Sam as Evil Sammy as long as we can
Seeing the begins of new hair!Sam. We apologise for mocking the bowl cut, bring it back
Dean being more concerned by Sam's terrible choices than the actual murder
Evil Sammy lives like a 16 year old drunk girl. Cheap beer and menthol cigarettes
Do demons canonically prefer menthols?
Dean has actually murdered a couple people so it makes sense that he doesn't care
Evil Sammy is a number one hacker and has no respect for the fine china
(We were also more concerned about the china than the murder so we don't have a leg to stand on criticising Dean)
Bro got Goblin Stanced on the CCTV
Sam: "Dad says it's my turn to have the trauma this week"

Good for Evil Sammy for getting the fun one liner
Evil Sammy's real crime is racking up additional charges for Dean
Justin Timberlake! He's not just a triple threat, he's also a threat to the roads!
Rip to Jo. Girlie gonna get ceilinged
Evil Sammy being creepy as hell (with scenes like this can only think about how awkward it is to film)
MY DADDY SHOT YOUR DADDY IN THE HEAD (new vocal stim unlocked)
HOW CAN THIS DAD GET WORSE??? HATE HIM HATE HIM HATE HIM
Murder!

(Cue unsynced duet of the entirety of Betrayed)
BOBBY!!
Honestly sick plan for spotting demons. Bro's getting drunk with the Lord
Meg! In Sam!
Dadchester is in hell. Good.
Imagine John saying Howdy. Really imagine it.

In return for getting possessed and murdering a guy, you get some funky jewellery and an apology tour to do

E15 - The Boys are Fighting
Poor Bobby has to put up with these people now
Cold Open - Academic misconduct nooo (YEET)
Prank war time?
Bobby returns!
Of course it was the ethics teacher who was cheating on his wife
Dean needs to stop flirting with college students bro's like 27
Unreliable Narrator: The Episode
Poor Bobby is about to regret caring about these kids

Is ganked an American word??
We have now been given both brothers sexual preferences. We aren't sure how we feel about that
Bobby is forcing the narrative back on track if it kills him
ALIENS!
Dean buddy thats not how to respond when someone says theyve been assaulted
Forgot that fraternities are a thing. They sound terrifying and bad
Bobby is a better dad than John could ever be but he deserves some better kids

Dean got a hard line stance on animal testing but not men being assaulted and uncomfortable age gaps
Honestly, this is on this guy for falling for a SAW trap. Get a stick it aint hard
Sam buddy. You have like a head of height over Dean you dont have to paw at him like a cat
Going from Sam begging Dean to kill him to Dean getting seduced by imaginary college girls in a lecture room is giving us a headache
NGL this isnt the worst of the ghosts so far
Real siblings don't let siblings say sorry
This whole episode has Merlin goblin episode vibes. Superwholockin? Why was merlin never included in this mess, it had the vibes. Sherlock is yet to have a good episode tie in like dr who and merlin
E16 - Really just a depressing sandwich
Seriously how can you go from Brother Trauma to Gremlin Cryptozoology Trickster to The Pain of Letting Go
Our vibe this whole episode

PDA and driving is arguably worse than texting and driving. PSA BE SAFE
Ngl if a door is unlocked when I go to knock on it Im turning around
Girlie is doing all this running in heels. Good for her!
At least once every 5 episodes we get the following exchange: Victim: "You'll think I'm crazy!" The Boys: "Hah you'll be suprised" * pulls out weapon to get the ghost * Victim: "OMG You guys are FREAKS"
Dean really doesn't mind some casual manslaughter
RIP to the Impala once again
Molly stop running away into the woods by yourself. You're playing the horror movie stereotype and losing
The camerawork in this show is lowkey sick as hell
Sam once again gets existential about ghosts
These boys are going to die from black mould before they get got by a ghost
Molly getting existential about ghosts
The boys got secrets!
Its very fun seeing how insane they look from an outside perspective
"Walking encyclopaedia of weirdness" both of us: MOOD
Girlie getting ✨Tortured ✨
Sam is very quick at digging graves
Once again been reminded of Sam having telekinesis powers and never using them again
Time check! 2007!
The switcharoo double dead ghost! (called it as a joke 5 minutes before the reveal)
Telling someone to just let go of their husband and the fact that their dead like its easy
Somehow managed to land the worst possible sandwiching of episodes in terms of vibes. Damn the last ep was existential and unmemeable
{{12% though the series}}

#supernatural#supernatural spoilers#the wives they watch#john winchester hate club#supernatural series 2#dean winchester#sam winchester#john winchester
3 notes
·
View notes