#Firewall Tutorial
Explore tagged Tumblr posts
Text
How to Allow IP Addresses through Firewall Linux?
Configuring IP Access with iptables
Verifying iptables Installation
Listing Current Firewall Rules
Allowing Specific IP Addresses
Saving iptables Rules
Creating a Secure IP Whitelist
Defining Your IP Whitelist
Configuring iptables Rules
Testing Connectivity
Streamlining Firewall Management with BeStarHost
Introducing BeStarHost
Using BeStarHost for IP Whitelisting
Best Practices for Linux Firewall Management
Regularly Review and Update Whitelist
Implement Fail2Ban for Additional Security
Conclusion:
Effectively managing your Linux firewall is an integral part of maintaining a secure server environment. By mastering iptables and understanding how to allow specific IP addresses, you fortify your defenses against potential threats. Whether you opt for manual configuration or utilize tools like BeStarHost, the key is to stay vigilant, update your rules regularly, and adapt your security measures to evolving threats. Implementing these practices will empower you to keep your Linux server secure and resilient.
To Learn More, Click this Link:
#Linux Firewall Configuration#IP Address Whitelisting#Linux Firewall Rules#Network Security on Linux#Firewall Tutorial
0 notes
Video
youtube
Linux Firewall Control with iptables and Firewall-cmd | Linux Security |...
#youtube#🔥 Master Linux Firewall Control with this comprehensive tutorial! Whether you're a beginner or looking to refine your skills this video div
0 notes
Text
#hostnextra#linux#technology#linuxserver#ubuntu#linux tutorial#programming#almalinuxserver#selinux#security#firewall
0 notes
Text
youtube
SOPHOS XGS SW-19.5.3 MR-3 Firewall | First Time Configuration | Step by Step in Hindi | By Sachin
#firewall#sophos xg firewall#network security tutorial#sophos xg firewall complete overview in hindi#how to setup sophos firewall in hindi#how to create rule in the sophos xg firewall#how to install sophos firewall#how to install sophos firewall on vmware#sophos xg v19#sophos xg firewall v19#xg firewall#setup sophos xg v19#configure sophos xg v19#configuring sophos xg v19#v19#xg firewall v19#sophos firewall#what is firewall#firewall explained#network firewall#Youtube
0 notes
Text
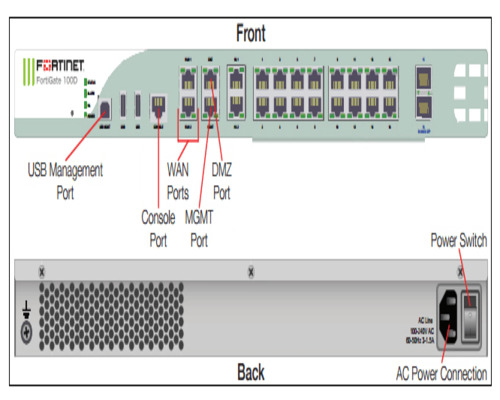
Unleash the power of DNA Center with our comprehensive courses. Dive into network automation, assurance, and security. Master the art of intent-based networking with #DNAC. https://www.dclessons.com/category/courses/fortigate
#CiscoDNA#NetworkAutomation#fortigate#firewall#security#networking#cybersecurity#it#training#certification#labs#practice#tutorials#videos#fortinet#learnfortigate#fortinettraining#fortinetcertification#fortinetlabs#fortinetvideos#networksecurity#networkfirewall#firewallsecurity#cybersecuritytraining#ittraining#itsecurity#cybersecuritycertification#learnnetworking#learnfirewall#learncybersecurity
0 notes
Text
Albert Gonzalez (born 1981) is an American computer hacker, computer criminal and police informer, who is accused of masterminding the combined credit card theft and subsequent reselling of more than 170 million card and ATMnumbers from 2005 to 2007, the biggest such fraud in history. Gonzalez and his accomplices used SQL injection to deploy backdoors on several corporate systems in order to launch packet sniffing (specifically, ARP spoofing) attacks which allowed him to steal computer data from internal corporate networks.
Gonzalez bought his first computer when he was 12, and by the time he was 14 managed to hack into NASA. He attended South Miami High School in Miami, Florida, where he was described as the "troubled" pack leader of computer nerds. In 2000, he moved to New York City, where he lived for three months before moving to Kearny, New Jersey.


While in Kearny, he was accused of being the mastermind of a group of hackers called the ShadowCrew group, which trafficked in 1.5 million stolen credit and ATM card numbers. Although considered the mastermind of the scheme (operating on the site under the screen name of "CumbaJohnny"), he was not indicted. According to the indictment, there were 4,000 people who registered with the Shadowcrew.com website. Once registered, they could buy stolen account numbers or counterfeit documents at auction, or read "Tutorials and How-To's" describing the use of cryptography in magnetic strips on credit cards, debit cards and ATM cards so that the numbers could be used. Moderators of the website punished members who did not abide by the site's rules, including providing refunds to buyers if the stolen card numbers proved invalid.
In addition to the card numbers, numerous other objects of identity theft were sold at auction, including counterfeit passports, drivers' licenses, Social Security cards, credit cards, debit cards, birth certificates, college student identification cards, and health insurance cards. One member sold 18 million e-mail accounts with associated usernames, passwords, dates of birth, and other personally identifying information. Most of those indicted were members who actually sold illicit items. Members who maintained or moderated the website itself were also indicted, including one who attempted to register the .cc domain name Shadowcrew.cc.
The Secret Service dubbed their investigation "Operation Firewall" and believed that up to $4.3 million was stolen, as ShadowCrew shared its information with other groups called Carderplanet and Darkprofits. The investigation involved units from the United States, Bulgaria, Belarus, Canada, Poland, Sweden, the Netherlands and Ukraine. Gonzalez was initially charged with possession of 15 fake credit and debit cards in Newark, New Jersey, though he avoided jail time by providing evidence to the United States Secret Service against his cohorts. 19 ShadowCrew members were indicted. Gonzalez then returned to Miami.
While cooperating with authorities, he was said to have masterminded the hacking of TJX Companies, in which 45.6 million credit and debit card numbers were stolen over an 18-month period ending in 2007, topping the 2005 breach of 40 million records at CardSystems Solutions. Gonzalez and 10 others sought targets while wardriving and seeking vulnerabilities in wireless networks along U.S. Route 1 in Miami. They compromised cards at BJ's Wholesale Club, DSW, Office Max, Boston Market, Barnes & Noble, Sports Authority and T.J. Maxx. The indictment referred to Gonzalez by the screen names "cumbajohny", "201679996", "soupnazi", "segvec", "kingchilli" and "stanozlolz." The hacking was an embarrassment to TJ Maxx, which discovered the breach in December 2006. The company initially believed the intrusion began in May 2006, but further investigation revealed breaches dating back to July 2005.
Gonzalez had multiple US co-defendants for the Dave & Buster's and TJX thefts. The main ones were charged and sentenced as follows:
Stephen Watt (Unix Terrorist, Jim Jones) was charged with providing a data theft tool in an identity theft case. He was sentenced to two years in prison and 3 years of supervised release. He was also ordered by the court to pay back $250,000 in restitution.
Damon Patrick Toey pleaded guilty to wire fraud, credit card fraud, and aggravated identity theft and received a five-year sentence.
Christopher Scott pleaded guilty to conspiracy, unauthorized access to computer systems, access device fraud and identity theft. He was sentenced to seven years.
Gonzalez was arrested on May 7, 2008, on charges stemming from hacking into the Dave & Buster's corporate network from a point of sale location at a restaurant in Islandia, New York. The incident occurred in September 2007. About 5,000 card numbers were stolen. Fraudulent transactions totaling $600,000 were reported on 675 of the cards.
Authorities became suspicious after the conspirators kept returning to the restaurant to reintroduce their hack, because it would not restart after the company computers shut down.
Gonzalez was arrested in room 1508 at the National Hotel in Miami Beach, Florida. In various related raids, authorities seized $1.6 million in cash (including $1.1 million buried in plastic bags in a three-foot drum in his parents' backyard), his laptops and a compact Glock pistol. Officials said that, at the time of his arrest, Gonzalez lived in a nondescript house in Miami. He was taken to the Metropolitan Detention Center in Brooklyn, where he was indicted in the Heartland attacks.
In August 2009, Gonzalez was indicted in Newark, New Jersey on charges dealing with hacking into the Heartland Payment Systems, Citibank-branded 7-Eleven ATM's and Hannaford Brothers computer systems. Heartland bore the brunt of the attack, in which 130 million card numbers were stolen. Hannaford had 4.6 million numbers stolen. Two other retailers were not disclosed in the indictment; however, Gonzalez's attorney told StorefrontBacktalk that two of the retailers were J.C. Penney and Target Corporation. Heartland reported that it had lost $12.6 million in the attack including legal fees. Gonzalez allegedly called the scheme "Operation Get Rich or Die Tryin."
According to the indictment, the attacks by Gonzalez and two unidentified hackers "in or near Russia" along with unindicted conspirator "P.T." from Miami, began on December 26, 2007, at Heartland Payment Systems, August 2007 against 7-Eleven, and in November 2007 against Hannaford Brothers and two other unidentified companies.
Gonzalez and his cohorts targeted large companies and studied their check out terminals and then attacked the companies from internet-connected computers in New Jersey, Illinois, Latvia, the Netherlands and Ukraine.
They covered their attacks over the Internet using more than one messaging screen name, storing data related to their attacks on multiple Hacking Platforms, disabling programs that logged inbound and outbound traffic over the Hacking Platforms, and disguising, through the use of proxies, the Internet Protocol addresses from which their attacks originated. The indictment said the hackers tested their program against 20 anti virus programs.
Rene Palomino Jr., attorney for Gonzalez, charged in a blog on The New York Times website that the indictment arose out of squabbling among U.S. Attorney offices in New York, Massachusetts and New Jersey. Palomino said that Gonzalez was in negotiations with New York and Massachusetts for a plea deal in connection with the T.J. Maxx case when New Jersey made its indictment. Palomino identified the unindicted conspirator "P.T." as Damon Patrick Toey, who had pleaded guilty in the T.J. Maxx case. Palomino said Toey, rather than Gonzalez, was the ring leader of the Heartland case. Palomino further said, "Mr. Toey has been cooperating since Day One. He was staying at (Gonzalez's) apartment. This whole creation was Mr. Toey's idea... It was his baby. This was not Albert Gonzalez. I know for a fact that he wasn't involved in all of the chains that were hacked from New Jersey."
Palomino said one of the unnamed Russian hackers in the Heartland case was Maksym Yastremskiy, who was also indicted in the T.J. Maxx incident but is now serving 30 years in a Turkish prison on a charge of hacking Turkish banks in a separate matter. Investigators said Yastremskiy and Gonzalez exchanged 600 messages and that Gonzalez paid him $400,000 through e-gold.
Yastremskiy was arrested in July 2007 in Turkey on charges of hacking into 12 banks in Turkey. The Secret Service investigation into him was used to build the case against Gonzalez including a sneak and peek covert review of Yastremskiy's laptop in Dubai in 2006 and a review of the disk image of the Latvia computer leased from Cronos IT and alleged to have been used in the attacks.
After the indictment, Heartland issued a statement saying that it does not know how many card numbers were stolen from the company nor how the U.S. government reached the 130 million number.
Gonzalez (inmate number: 25702-050) served his 20-year sentence at the FMC Lexington, a medical facility. He was released on September 19, 2023.
22 notes
·
View notes
Text

Now let's see miss China's makeup routine
(Her everyday look is a little less extreme tho)
(Reference: me my friends and my library of makeup tutorials from firewall hopping chinese youtubers and douyin)
43 notes
·
View notes
Text
Ah fuck I've done it again
Amalgam AI AU
I've seen some AUs about the humans being AI instead of Caine and I thought that might be the simplest way to get this monstrosity to happen with a massive glitch without abstraction playing a part.
I think I just really like horror AUs and doing stuff like that is just so fun so I made another one with a better title than "Horror House" cuz c'mon what the hell does that mean lol
The only characters I don't have designed currently are Zooble, Caine, and Bubble but I'll add them soon. Caine will be a human, Bubble could be something to help him out and what not.
Inspired by AUs like Sm-baby's and The Horror Circus AU, but like, different ofc.
Think this: the game wasn't originally supposed to be a horror game, just a game you go through for fun. Like Undertale, I guess? But not quite
[WARNINGS: LOTS OF EYES/ARACHNID IMAGERY, BODY HORROR, EYESTRAIN]
So first and foremost, I think people would wanna see Pomni, though Jax was the first to be designed.

Pomni is supposed to be some sort of anti-virus or some sort of protecting thing. Supposed to fix bugs and glitches and prevent viruses from getting into the game. Like a firewall, I guess? I tried to make her look like "right/wrong" esc thing. She was the last to be designed and it was like 1 am when I designed her. I had no clue what to do with her, I'll be completely honest.
Story wise, she'd be trying to find a way to undo this massive glitch and get the game back to normal before she can even rest. Once Caine pops up to try and fix the game from inside, as a dev himself, she does her best to protect him and help him fix the game.
No there is no shipping in this AU, they're just helping each other basically survive. They might become friends over time but nothing more. :V
Next up: Ragatha and Gangle! I actually really like Gangle's design but Ragatha definitely needs a few tweaks I think.

Ragatha, before this massive glitch, would have been an NPC that would help a player out at the start but end up getting lost after a certain point, like a tutorial. She was the most caring character in the game before everything went down.
Gangle used to be someone who ran a little theatre thing in the game, as I've seen from other AUs and took inspiration from, but she's usually nice no matter what mask she has on. More arms means she can help more people at once, right? Game mechanics wise she was like a little shop keeper for costumes if they're needed and she can help with newer mechanics on stage if something new is added. Friendly NPC, you know? Love her design, too!
Now for the first two to be designed, Jax and Kinger!!

So Jax was like a reoccurring villain, I guess. Always trying to make the player quit the game or just scare the shit out of them, despite him not being very scary himself. He's more played off to be a joke character, if I'm honest, always failing with his antics and what not. It's part of the code! I actually like his design, small lil paws and just so shapey over all.
Kinger was like a final boss, I guess? The scariest of all of them at that time. He was a king, ruling over his pawns and such, all of which were also bug themed! I love making Kinger bug related it's so fun. He's a big softie in reality but hits like a train if you ever went against him. He had terrible vision despite all of his eyes and was very slow despite the amount of legs.
Now for what everyone has been waiting for.
The reason for the AU title.
The MASSIVE glitch that caused everything to go downhill.
The Amalgam.

I still think it needs a few tweaks here and there but this is one of four concepts I've had for it.
One time all four of these characters were together, which was relatively rare but possible, a glitch happened in the game. Pomni doesn't know where it started from and none of the game devs understand how it happened, but it did. Some devs think there's a hacker. A massive glitch pulled those four characters together into one terrifying being, always hostile and destructive. All the code of the characters were merged into this thing and somewhat scrambled. The game has now been broken to where once you're in, you can't escape until it's fixed, yet no one knows it, which is why Caine went in.
So much has happened and it's still being fixed, but a hostile blob of characters constantly attacking whenever it's near? It will be hard to fix.
It seems to be guarding something.
Concepts for the amalgam:




You can see in the first one I was going to put Zooble there but I still need a good design for Zooble. Let's see what they'll be.
#the amazing digital circus#tadc#tadc caine#tadc kinger#tadc pomni#tadc jax#tadc ragatha#tadc gangle#tadc zooble#tadc au#amalgam ai tadc au#aatadc au#tw body horror#tw spiders#tw eyestrain#tw eye horror#don't tag as ship
22 notes
·
View notes
Text
Progress Update #6
It’s been a little over two weeks since my last post, and I have quite a lot to say about what I’ve been doing.
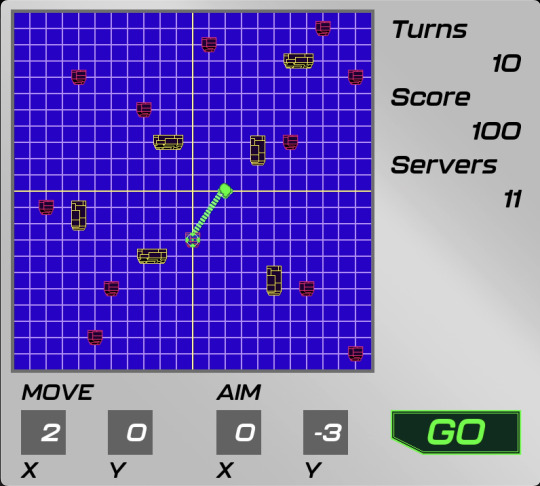
First of all, I finished creating the revised sprites. They now have a bit more detail, and the servers and firewalls are drawn in perspective (I don’t know if that’s the right term, but if you look at the picture, you’ll get it). I’m actually proud that I managed to pull this off, especially the shading in Sasha’s hair. Here's just some of the sprites I made (I don't want to put too many pictures in this post:




I also got a lot of coding done. The biggest accomplishment (at least in my opinion) is finally making it where you put in the aim coordinates after Sasha finishes moving. I feel like this will make the game a bit easier. That being said, getting it done wasn’t easy. It all had to do with the states I was using. When I first made the states, they were all in Sasha’s object code. However, since they would have to be referenced by other objects for this mechanic to work, I wanted to move the states to a new control object. Put simply, this didn’t work. The code that was supposed to make Sasha move just made the control object move instead. So, I just kept the states in Sasha’s code, which actually works fine.
(Note: I fixed up some more stuff after I recorded this, such as changing the direction of the ray and making only one marker visible at a time.)
Besides revising the coordinate input mechanic, I also changed the controls. Before, I had the player press buttons to change the coordinates. However, I got feedback from someone saying that this was confusing. Their main issue was that moving on the x-axis was being associated with up and down arrows; they felt it would be more fitting for it to be linked to left and right arrows. At first, I was reluctant to do this (that might be putting it too softly) because I thought adding left and right arrow buttons would ruin the UI. But then, I thought of a better solution: use the arrow keys instead. So, the game is now controlled primarily with a keyboard (I also made it where you press enter to make Sasha move and shoot instead of pressing the Go Button). I honestly think that this control system is better than the previous one, and I have to admit that the feedback was helpful in this case.
Of course, not everything turned out well. The biggest frustration these past two weeks is that I can’t get a certain animation to work. When Sasha went from moving to aiming, I wanted her to have a brief transition animation. However, when I tried to put it in, the animation either looped indefinitely or didn’t play at all (instead going straight to the normal aim sprite). I have no idea how to fix this, and considering how little time I have left, I may just have to scrap the animation…
On a more lighthearted note, I also tried to make it where Sasha didn’t immediately switch back to her idle state right after shooting. When I tried to do it, though, I ended up with this:
It’s a little amusing, but it’s not what I want. So, I just settled with what Sasha currently does.
I did some more stuff, such as making sure that a ray wouldn’t hit a server multiple times. This wasn’t an issue until I added the disintegrating server animation. The video above actually shows it in action (take a good look at the number of servers and score).
Still, I have even more to do, such as:
Fixing the shock SFX
Making a new background
Adding a “grade” system at the end
Adding the tutorial (this is the one I’m most anxious about)
Adding some fade-in/out transitions (this is probably the easiest task in my to-do list)
I have a little over a week left to get this all done. I’ll try to get most of this out of the way by this week so I can focus on the tutorial next week. After that, I’ll be done. Let’s see how things go…
2 notes
·
View notes
Text
BETA 1.1.0
Updated FIREWALL with a few new features:
>Added bodies >Added setting to disable bodies >Added speed consumable >Changed enemy speed leveling to have no max speed but upgrades slower >Enemy health upgrades faster >Consumables will not appear in selection list or ITEMs if their equipped >Added Xbox based gamepad controller glyphs to tutorial >Added HoldToShoot tutorial >Changed style of settings toggle buttons >Enemy bullets now add their owners velocity to their own
SMASHING BUGS
>Fixed a problem where Lore and Credit Earning SKILLs won't save >Fixed areas where the gamepad won't respond >Fixed WALL health being set to an incredibly low value at the end of a Cycle



Somewhat morbid but that's why we have a setting to get rid of the bodies if your too bothered by them. Or if they cause the game to lag.
#cyberninjax-3648 studios#indie games#firewall: cyber defense#programming#godot engine#coding#cyberspace
2 notes
·
View notes
Text
Discover the Unique Fusion of Action and Puzzle-Solving in NULLPTR

NULLPTR a new action puzzle game is coming to Linux and Windows PC, but offers a native Demo. Thanks to Jeferson Silva's creative skills bring an experience to the digital world. Available to try now on Steam. Let's dive into a fresh experience called NULLPTR by Jeferson Silva, a brilliant mind from the indie scene. Imagine being a master hacker, infiltrating high-security server grids, all under the unyielding tick-tock of a 20 second timer. This isn't just a challenge; it's also a fusion of action and puzzle-solving where each second could be the difference between digital glory and cyber demise. Taking place deep in a digital landscape, where mega corporations hold the keys to valuable data. Your mission? To swipe this data right under their noses. But here’s the twist - it's all about strategy and swiftness. You've got a mere 20 seconds to breach security, dodge sentinel programs, and download the precious data. NULLPTR is a pulse-pounding race against time. Choosing your entry point is also crucial. Each server offers various ports to connect to, each color-coded and leading to different segments of the server and unique security systems. Similar to picking the right door in a maze; the choice is due to set the tone for your entire mission. And if you're clever, you can install backdoors to open up new pathways and strategize your attack even further.
NULLPTR - Official Trailer
youtube
The real meat of NULLPTR is plotting your course. You’ve got to link up your entry point to the database. The shorter your route, the quicker the download. But it's not just about finding the shortest path. You need to be a step ahead of firewalls and other security hurdles. It's a delicate dance of strategy and quick thinking. And then there are the sentinel programs – digital guardians each megacorp has deployed to hunt down intruders like you. Each one has its quirks and weaknesses, and figuring these out is key to turning a complex level into an achievable puzzle. NULLPTR is about outsmarting the system, and shaping it to your advantage. The Linux demo alone is a treasure trove of learning and challenge. Since you get 17 tutorial levels to sharpen your skills, a story that shows you to the world’s mega corporations, and over 25 servers to test your mettle. Plus, you get to face off against those sentinel programs and discover your own ways to outwit them. And for the idealists out there, revisiting completed stages to improve your times adds an extra layer of replayability. The whole experience is kind of brilliant. NULLPTR is an action puzzle game in a thrilling blend of rapid-fire action and brain-teasing. Doing so in a high-stakes cyber world. It's an indie game that's sure to challenge your reflexes and your mind in equal measure. So, get ready to hack, outsmart, and claim your place in the digital hall of fame. Coming to Linux and Windows PC, with a release date of Q3 2024 on Steam. Try the Demo!!
2 notes
·
View notes
Text
Reseller Royalty Crown Yourself with the Best in Reseller Hosting
Unveiling Excellence in Reseller Hosting Solutions
At L3WebHosting.com, we redefine the reseller hosting experience, offering unparalleled services that go beyond conventional standards. Our commitment to excellence sets us apart, allowing you to crown yourself with the best in reseller hosting. Discover why partnering with us ensures reseller royalty in the dynamic digital landscape.
Tailored Reseller Packages
L3WebHosting.com prides itself on tailoring reseller hosting packages to meet diverse needs. Our comprehensive packages empower resellers with the flexibility to customize hosting solutions for their clients. From bandwidth to storage, we provide the building blocks for resellers to create unique and scalable hosting experiences.
Cutting-Edge Technology for Optimal Performance
In the fast-paced online world, performance is non-negotiable. Our reseller hosting solutions leverage cutting-edge technology, ensuring optimal website speed and reliability. With state-of-the-art servers and advanced infrastructure, your clients' websites will thrive, enhancing user experience and satisfaction.
Unmatched Customer Support
24/7 Dedicated Support
We understand that your success is our success. That's why our dedicated support team is available 24/7 to assist you and your clients. Whether it's technical troubleshooting or general inquiries, our experts are ready to provide prompt and efficient solutions.
Comprehensive Knowledge Base
Empower yourself with our extensive knowledge base. We offer a wealth of resources, including tutorials, guides, and FAQs, equipping you with the knowledge to navigate and optimize your reseller hosting experience. Our commitment to transparency ensures you are always in control.
Robust Security Measures
Fortifying Your Digital Kingdom
Security is paramount in the online realm. At L3WebHosting.com, we prioritize the safeguarding of your digital assets. Our reseller hosting solutions come with robust security measures, including firewalls, malware detection, and regular security audits. Rest easy knowing your clients' data is shielded against cyber threats.
Seamless Integration and White Label Solutions
Your Brand, Your Identity
We understand the importance of brand identity. Our reseller hosting solutions offer seamless integration and white label options, allowing you to establish and promote your brand effortlessly. Provide hosting services under your label while we handle the technical intricacies behind the scenes.
Cost-Efficiency for Maximum Profitability
Unlocking Profit Potential
Our reseller hosting packages are not only feature-rich but also cost-efficient. Maximize your profitability with competitive pricing and flexible billing options. We believe in empowering resellers to achieve financial success while delivering top-notch hosting services.
Conclusion: Elevate Your Reseller Hosting Experience with L3WebHosting.com
In the competitive landscape of reseller hosting, L3WebHosting.com stands as a beacon of excellence. Our commitment to tailored solutions, cutting-edge technology, unmatched support, robust security, seamless integration, and cost-efficiency makes us the optimal choice for those aspiring for reseller royalty.
If you are ready to elevate your reseller hosting experience and crown yourself with success, partner with L3WebHosting.com today.
2 notes
·
View notes
Video
youtube
Raspberry Pi 5 Firewall Setup Guide: Easy GUFW GUI Tutorial for Secure
🔐 Secure Your Raspberry Pi 5 with GUFW Firewall - Step-by-Step Tutorial Welcome to our comprehensive guide on setting up a firewall on your Raspberry Pi 5 using GUFW GUI. Whether you're a beginner or an experienced Pi user, this tutorial is designed to help you enhance your device's security with ease. What You'll Learn: ✅ Introduction to Firewalls and their importance ✅ Step-by-step instructions on installing GUFW on Raspberry Pi OS ✅ How to configure basic firewall rules ✅ Tips for maintaining firewall security Equipment Used: Raspberry Pi 5 Model B Raspberry Pi OS (Latest Version) Internet Connection Additional resources and links can be found below Useful Links: Official Raspberry Pi Website @raspberrypi @cybersecurityclub @Microsoft @YouTube https://www.raspberrypi.com/ 👍 Like this video if you found it helpful and subscribe to our channel for more Raspberry Pi tutorials and tips. Don't forget to hit the bell icon to get notified about our latest uploads! #RaspberryPi5 #FirewallSetup #GUFW #Cybersecurity #RaspberryPiTutorial #DIYNetworking
2 notes
·
View notes
Text
A game idea I had in the shower:
Old Skizzlewick's Encyclopedic Tome of Knowledge
A game based on a fantasy Wikipedia. Your tutorial guide is the Install Wizard, who helps you get going (but then has to leave to help somebody install McAferty's Firewall). Through clicking links, you learn about lore & story... all the while, certain pages will start encounters where you have to do magic that you learn on other pages. The back button would serve as a way to run away from a battle you can't do - for example, in the tutorial, the Install Wizard will have you click on the link for Dragons and then IMMEDIATELY tell you to press the back button... with him getting burned right as you leave
2 notes
·
View notes
Video
youtube
How To Enable or Disable Windows Defender Firewall in Windows 11 : Step-...
In this easy-to-follow tutorial, you'll learn how to enable or disable the Windows Defender Firewall in Windows 11. Whether you're troubleshooting network issues, installing specific software, or adjusting your system’s security settings, this video walks you through the process clearly and safely.
Simple Steps 1. In the search box located in the taskbar, type "control panel" and click on "Control Panel" to open it. 2. In the dialog box that opens, click on the "System and Security". 3. Click on "Windows Defender Firewall". 4. On the left side pane, click on "Turn Windows Defender Firewall On Or Off. 5. Toggle on or off Windows Defender Firewall.
0 notes
Text
CroxyProxy YouTube: Unlocking Unrestricted Access to Your Favorite Videos

In today’s digital age, video content is king. YouTube, being the largest video-sharing platform, is the go-to source for tutorials, music, entertainment, news, and more. However, many users face restrictions when trying to access YouTube videos—whether it's due to school, workplace firewalls, or regional blocks. That’s where CroxyProxy YouTube steps in as a game-changer.
What is CroxyProxy?
CroxyProxy is a free and secure web proxy service that allows users to access blocked websites, including YouTube. Unlike traditional VPNs or complicated software, CroxyProxy is simple to use. Just head to the official CroxyProxy website, enter the URL of the video you want to watch, and you’re good to go—no downloads, no installations.
Why Use CroxyProxy for YouTube?
The biggest advantage of using CroxyProxy is its ability to bypass restrictions without compromising your privacy. It masks your IP address, keeps your browsing anonymous, and works seamlessly on almost any device or browser. Whether you're trying to watch a documentary at school, a music video at work, or a region-blocked vlog, CroxyProxy provides a smooth and secure streaming experience.
Final Thoughts
Don’t let internet restrictions limit your access to information and entertainment. CroxyProxy YouTube opens the doors to a free internet, giving you the ability to enjoy your favorite videos anytime, anywhere. It’s fast, reliable, and totally free—making it the perfect tool for uninterrupted YouTube streaming.
0 notes