#Personal Cybersecurity
Explore tagged Tumblr posts
Text
Executive Protection Gaps in Cybersecurity: A Candid Conversation.
Sanjay Kumar Mohindroo Sanjay Kumar Mohindroo. skm.stayingalive.in Explore executive protection gaps in cybersecurity with real-world insights, industry examples, and thoughtful discussion. The Unseen Threats at Home How Our Private Spaces Become the Weak Link in Digital Safety The world of cybersecurity is changing in ways that raise tough questions for companies and leaders alike. We face…
#CISO#Concierge Cybersecurity#Cyber Attack#Cyber Risk#Cybersecurity#Digital Safety#Executive Protection#Executive Risk#Home Network#Personal Cybersecurity#Privacy#Remote Work Security#Sanjay Kumar Mohindroo
0 notes
Text
Do NOT send pictures of your ID card to discord bots!!!!
Or, like, any online rando.
I ran into a server that wanted to make sure that members are over 18 years old. They wanted to avoid the other thing I've heard of, which is asking you to verify your age by sending pictures of your ID card to a moderator. Good! Don't do that!
However, ALSO don't do this other thing, which is using a discord bot that would "automatically verify" you from a selfie and a photo of your ID card showing your birthday. The one they used is ageifybot.com. There's a little more information on its top.gg page. Don't like that! Not using that!
Why not? It's automatic! Well, let me count the ways this service skeeves me out:
How does the verification process work? There is no information on this. Well, okay, if you had more info on what kind of algorithms etc were being used here, that might make it easier for people to cheat it. Fair enough. But we need something to count on.
Who's making it? Like, if I can't understand the mechanics, at least I'd like to know who creates it - ideally they'd be a security professional, or at least a security hobbyist, or an AI expert, or at least someone with some kind of reputation they could lose if this turns out to not be very good, or god forbid, a data-stealing operation. However, the website contains nothing about the creators.
The privacy policy says they store information sent to them, such as your selfie and photo of an ID card, for up to 90 days, or a year if they suspect you're misleading them. It sure seems like even if they're truly abiding by their privacy policy, there's nothing to stop human people from looking at your photos.
The terms of service say they can use, store, process, etc, any information you send them. And that they can't be held accountable for mistakes, misuse, etc. And that they can change the bot and the ToS at any times without telling you. The terms of service also cut off midway through a sentence, so like, that's reassuring:
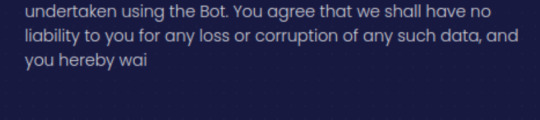
In conclusion, DO NOT SEND PICTURES OF YOUR ID CARD TO RANDOM DISCORD BOTS.
Yes, keeping minors out of (say) NSFW spaces is a difficult problem, but this "solution" sucks shit and is bad.
Your ID card is private, personal information that can be used by malicious actors to harm you. Do not trust random discord bots.
#light writes#discord#internet so strange#internet safety#personal safety#information security#cybersecurity#discord bot
171 notes
·
View notes
Text
wait kpop stans genuinely believe a random employee fired from YG has 500+ terabytes of data (200+ TBs being from JYP (???)) on a bunch of massive kpop corporations just hanging around on their computer???
#I have to laugh I’m sorry#I think my standards for the general iq level of the average kpop stan is too high#I don't think y'all understand how much 223 tbs of data is...#tbf its a little hard to visualize if you dont know tech#but like#it most definitely would NOT fit on a laptop lmao#not to mention this is (supposedly) an ex-yg employee....why would they have data on other companies???#these corporations literally spend so much money on cybersecurity#NOTHING is seeing the light of day unless they want it to#also if they actually believed this person had so much data they would most definitely be suing left and right lol#yg leaker#yg#jyp#hybe#cube#sm#sm entertainment#jyp entertainment#bighit#kpop#also holy shit this person HAD to have been an extremely high up person
23 notes
·
View notes
Text
learning to code!
When I was 9 years old, I learned enough html to code neopets pages, my own geocities websites, and I even made forums on my own sites so my friends could all roleplay together or rant together lol. And then? I forgot so much. I no longer no how to make a forum, or even a 'next page' button - so even the dream of just making a simple blog or webnovel site feels like a huge hurdle now. (9 year old me could probably figure it out in 2 hours).
So I'm relearning! I figured this would be a fun post to place resources I find for coding, since there's coding languages, and I figure maybe if you like running you're blog then you also might be interested in tools for making blogs!
First, for those of you who miss the old geocities and angelfire type of sites to make your own free site on: neocities.org
You can make free sites you can code yourself, the way 9 year old me did. A lot of people have made SUCH amazing sites, it's baffling my mind trying to figure out how they did, I definitely wish I could make an art portfolio site even a fourth as cool as some of the sites people have made on here.
And for those pressed for time, who aren't about to learn coding right now: wix.com is the place I recommend for building a site, it requires no coding skill and is fairly straightforward about adding pages or features by clicking buttons. I used it to make my art portfolio site, I am testing out using it for my webnovel - the alternative is Wordpress, but wix.com is letting me basically make a wordpress blog Inside my own site. It's very beginner friendly in terms of "how the fuck do I set up a 'sign up for updates' message and have my site actually email these people my novel updates?" and "I need a 4x20 grid of my art down the page, that lets people click the art to see it's information and make it bigger."
I did neocities.org's little html tutorial today, it's the part of html I DID remember (links, paragraphs, headers).
My next step is to go through htmldog.com's tutorials. They go from beginner, to intermediate, to CSS. Unlike many a coding tutorial I've seen, they explain what program on your computer you need to WRITE the code in and then how to save it and how to open it. (You'd think this isn't a big deal but I've been looking into how to learn Python for months and I can't find a tutorial explaining what fucking program to write my python in... notepad? do I need something else? I don't fucking know!! My dad finally gave me a printed textbook which supposedly tells you what to download to start... I learned C++ in college and for that you needed Visual Basic to code C++, so I figured I needed Something to Write the fucking python IN.)
#coding#rant#wooh my new CODING TAG#learning to code#i feel very. odd if im honest?#i genuinely knew how to build full fucking forum websites as a child including user sign ups#and i studied Computer Science Engineering in college so i did everything with C++ we were asked to and got As#and then i promptly BLOCKED IT OUT because i#HATED studying c++ SO fucking much. i hated my whole major. i did not like Engineering. i hated it. i was so mentally destroyed#by my college major that when i graduated i got a DIFFERENT job#and do NOTHING related to my major#i want to get into a more tech focused career eventually...since that is what my fucking degree is in#but i've been looking into something with less coding OR trying to teach myself#to like coding as long as its not fucking c++ again... i cant do it. too many bad memories#i think cybersecurity sounds like a fun job.#but u know me. im a person who likes knowing the BASICS#so i feel like i need to Relearn to code and learn python decently#before i try to study cybersecurity specific shit
37 notes
·
View notes
Text
One of western Canada’s largest rental property companies is warning tenants about a cyber security breach it says was discovered earlier this year. In a letter to tenants on Aug. 19, also published on its website, Mainstreet Equity Corporation says on it discovered a third party had gained access to a portion of its IT infrastructure on May 21. “Upon discovering this, we immediately undertook countermeasures to prevent any further unauthorized activity,” the company said.
Continue Reading
Tagging: @newsfromstolenland
#data breach#cybersecurity#landlords#personal information#western canada#cdnpoli#canadian politics#canadian news#canada
77 notes
·
View notes
Text
Person of Interest (2011-2016)
#person of interest#cyberpunk aesthetic#hacking#graphic design#surveillance#science fiction#surveillence state#hackers#cybersecurity#scifi#mobile hacker#code breaker#data manipulation#network security#infosecurity#10s#command line
81 notes
·
View notes
Text

#4chan#if i see one more person say omg feds glowies feds biggest cybersecurity hack evarrr im going to.well. ignore it probs#t for text post
8 notes
·
View notes
Text
youtube
Congressman Dan Goldman today lit up House Republicans for holding a committee hearing on job training for cybersecurity positions in the federal government while President Trump and his unelected billionaire patron Elon Musk systematically slash the federal government’s effectiveness and actively endanger America’s cybersecurity and national security.
#rep dan goldman#rep goldman#elongatd muskrat#personal data breach#us government#oligarchy#dictatorship#cybersecurity#national security#us politics#united states#Youtube
9 notes
·
View notes
Text
An open letter to the U.S. Congress
Stop Elon Musk from stealing our personal information!
6,399 so far! Help us get to 10,000 signers!
I am writing to urge you to stop Elon Musk from stealing our personal information.
It appears Musk has hacked into millions of Americans’ personal information and now has access to their taxes, Social Security, student debt and financial aid filings. Musk's so-called Department of Government Efficiency was not created by Congress—it is operating with zero transparency and in clear violation of federal law.
This violation of our privacy is causing American families across the country to fear for our privacy, safety and dignity. If this goes unchecked, Musk could steal our private data to help in making cuts to vital government programs that our families depend on—and to make it easier to cut taxes for himself and other billionaires.
We must have guardrails to stop this unlawful invasion of privacy.
Congress and the Trump administration must stop Elon Musk from stealing Americans' tax and other private data.
▶ Created on February 10 by Jess Craven · 6,398 signers in the past 7 days
📱 Text SIGN PUTWGR to 50409
🤯 Text FOLLOW JESSCRAVEN101 to 50409
#PUTWGR#jesscraven101#resistbot#petition#activate your activism#stop the coup#Government Accountability#Data Privacy#U.S. Congress#Legislative Action#Public Policy#Federal Oversight#Constitutional Rights#Elon Musk#Department of Government Efficiency#Privacy Violation#Cybersecurity#Personal Data Protection#Taxpayer Rights#Social Security#Student Debt#Financial Aid#Government Transparency#Corporate Overreach#Public Advocacy#Citizen Action#Stop Data Theft#Congressional Investigation#Tech Regulation#Digital Privacy
5 notes
·
View notes
Text
everyone “the ai is going to take over the world!”
Me an intellectual “brain organoid computation is a man made horror”
ANYWAY HOW’S IT GOING GUYS!!!
I for one accept the LITERAL newborn babies-
(this isn’t even a joke they are literally the equivalent of newborns or pre-term babies with the ability to interact and move in digital or real worlds… which we can grow and develop… bro why did we do this to children)
-who are being used for computer computation, I am so fucking sorry for them holy shit.
As soon as they figure out how to make a circulatory system it is OVER, these poor babies LITERAL BABIES will be basically tortured in a torture nexus being used a biological CPU’s for their entire lives..
they have sentience they are LITERALLY BABIES holy shit.
so uh, yeah artificial intelligence being the hype????
(I knew it was never gonna happen lol, it's a bit too hard and annoying)
FUCK NO BRAIN ORGANOIDS!
anyway nothing particularly fancy I’ve literally expected this to happen my entire life now, and it’s here.
like.. clones, genetics, bioengineering, all this cool stuff it's happening!!!
and uh kinda horrifying I do hope they are treating the organoids okay. the military, and other cool governmental orgs are totally using these.
and that is HORRIFYING, but you know we persist!
anyway cyberpunk is here, be nice to the children (brain organoids) and uh go about your day's guys!
#-pop#activism stuff#Hi guys welcome back to pop updates you on the latest in computers#now we have created uh cyborgs? Literal babies?? To use in computer computation???#personally the cat’s out of the bag with this one#I am so fucking sorry for these poor guys that is a fate worst than death. (NOT REALLY LITTLE BRAIN ORGANOIDS)#”oh but it’s just some brain organoids” bro that’s where they keep the living part of you#without a brain u die. The brain is the u. Tiny fucking little guys with literal eyes half the time#are being subjected to digital hell I am SO SORRY FOR THEM#cyberpunk#cybersecurity#cybercore#computers#punk community#punk#ai#artificial intelligence#technology#brain organoids#before u ask no I am not pro-life I'm pro-choice#this is just INCREDIBLY SCREWED UP#and I for one am not forgetting these are like literally human children <3#ai art#character ai
9 notes
·
View notes
Text
Multiple Users Masquerading As One
8 notes
·
View notes
Text
I'm all for security/cybersecurity, but the uni requesting a phone call with the entire main cybersecurity team and possibly needing me to come in person for another meeting to just change my phone number is fucking ridiculous.
Also, I put in the ticket for this to happen (after an IT team member had to do it for me because that system wasn't working on the regular user end of it) weeks ago and have been waiting for a reply, only for them to start that reply with 'do you still need help with this issue? We haven't heard from you'
only to then admit that yes, they knew they hadn't actually sent me anything about the ticket yet UNTIL THIS FUCKING EMAIL and that they hadn't 'had time' to read up on the actual issue on the ticket.
The IT guy that put the ticket in assured me they would just get it changed with probably nothing more than a confirmation email or me letting them know if I get a code they text to me to confirm the number is correct, bc that's usually how they do it. Don't love that suddenly I need at least one call and potentially an in person meeting just for this. What the fuck are they going to require when I bring them my name change certificate and updated docs?
#text post#and yes I already had to explain to the head of cybersecurity that they need to call my new number for this call#'why?' bc my old phone barely runs while plugged in and might not last through a call#'oh...so I really have to call the 475 number?'#like I couldn't make this shit up my fucking god#im now waiting to find out when/if they're going to do this call since I already gave them my availability for one for today and tomorrow#if I have to in person for this like. I'll do it but my god am I gonna be frustrated abt it#Im gonna need to suck off the dean or some shit to get my name change stuff put into the system and tbh? would rather do that then all this#that's one brief in person meeting versus me being grilled abt why I changed my number#bc yes I was already warned that they need to 'ascertain why I have changed my number and why I would do so now'#I think they think they're like. protecting national secrets or some shit and it's like. bro it ain't that deep I just needed a new phone#and wanted a number from the state I now live in instead of the one from my old state
3 notes
·
View notes
Text
Some day, I am going to write more eloquently about how any system with a setup for defending against data security threats eventually devolves into treating its users as the threat, and this eventually *makes* these users a threat.
Some day.
For now, I just want to put this out here.
Picture a company. Let's say, a company that relies on external contractors for all of its IT development work. And I do mean, ALL OF IT.
This company has been doing a lot to increase their data security rating. Things like blocking people from accessing Gmail or Slack, making MS Teams chat unavailable for external employees, making it so externals cannot see anyone's agenda nor book meeting rooms, preventing usage of flashdrives, making a huge "data leak" hassle because an external developer had downloaded a file they needed for their work onto their own machine's desktop and a manager spotted this during a demo of the new development... You know, just corporate things. Cyber security swag.
Anyway.
Now picture this company has decided to get Next Level with their security.
Introducing: computers that only work if a "smart badge" is inserted, containing so much intrusive spyware that employees using them had to sign a legal document stating they are ok with that. Five fiery rings of hell to connect to a "secured" virtual workspace if working from home. Recording a Teams meeting? How about you just put a bomb in the server room, you terrorist. And most importantly... If you are not an internal payroll employee of sufficiently high rank...
YOU CAN NO LONGER SEND EMAILS WITH ATTACHMENTS.
...
...
So, how do you think people would respond?
...
Let me tell you: we are making fake user stories in Agile Accelerator and dropping our files in the Files section in order to share them with each other. Our manager is serving as our external postal office because she has hierarchical attachment sending clearance. We are classifying all our documents as "public" to minimize the hurdles.
We are becoming the threat, with grit teeth as we lose hours and days just trying to do our fucking job around all these "security features".
Cybersecurity? At this point I think a good fifth of my colleagues would click a phishing link On Purpose.
#cybersecurity#data security#working in it#work woes#it jobs#dys-functional analysis#every day I fight with corporate to just let me do what I am paid for#disaster thoughts#work shit#office life#cyber security#security theater#“what if the TSA -but for computers?” is no longer a hypothesis#i like our CISO as a person but I also want to wring his neck
2 notes
·
View notes
Text
How to check if your computer is being monitored
In today's digital age, the issue of privacy and security is more pressing than ever. Whether you’re a casual user or a professional, understanding if your computer is being monitored is crucial. This guide will delve into the signs of monitoring, tools to detect it, and steps to safeguard your privacy.

Understanding Computer Monitoring
Before diving into the signs and detection methods, it’s essential to understand what computer monitoring entails. Monitoring can involve tracking your online activity, keystrokes, file access, and even webcam usage. This can be done by malicious software (malware), spyware, or legitimate monitoring software used by employers or parents.
Types of Monitoring
Malware and Spyware: These are malicious programs that can be installed without your knowledge. They can track your activities and send data back to an attacker.
Keyloggers: This type of software records keystrokes, capturing sensitive information like passwords and personal messages.
Remote Access Tools (RATs): These tools allow someone to control your computer remotely, monitoring your screen, accessing files, and even using your webcam.
Legitimate Monitoring Software: Often used in corporate environments, this software tracks employee activity for productivity or compliance reasons. While legal, it can still infringe on personal privacy.
Signs That Your Computer May Be Monitored
Recognizing the signs that your computer might be monitored is the first step in protecting yourself.
1. Unusual System Behavior
Slow Performance: If your computer suddenly becomes sluggish, it might be due to monitoring software consuming resources.
Frequent Crashes or Freezes: Unexpected system crashes can indicate underlying issues, including malware.
2. Suspicious Programs
Unknown Applications: Check your installed programs for any unfamiliar applications. Many monitoring tools disguise themselves as legitimate software.
High Resource Usage: Use the Task Manager (Windows) or Activity Monitor (Mac) to look for processes consuming excessive CPU or memory.
3. Network Activity
Unexplained Network Traffic: Use network monitoring tools to check for unusual data being sent or received. High outbound traffic could indicate that data is being transmitted without your consent.
Blocked Ports: Monitoring software often uses specific ports to communicate. If you notice blocked ports that you didn’t configure, it could be a red flag.
4. Webcam and Microphone Behavior
Indicator Light Activation: If your webcam or microphone is being accessed without your knowledge, the indicator light may be on even when you're not using it.
Unexpected Recordings: Check for unusual files that could be recordings made by your microphone or webcam.
5. Browser Behavior
Unusual Browser Extensions: Check for extensions you didn’t install. Some can track your browsing activity.
Unexpected Redirects: Frequent redirects to strange sites or altered search results can indicate tracking.
6. Security Alerts
Antivirus Notifications: If your antivirus software frequently alerts you about threats, it may indicate that monitoring software is present.
Firewall Alerts: Unusual outgoing connection attempts can suggest that an unauthorized program is trying to access the internet.
Tools to Detect Monitoring Software
If you suspect that your computer is being monitored, several tools can help you investigate further.
1. Antivirus and Anti-Malware Software
Using a reliable antivirus or anti-malware program can help detect and remove malicious software. Some popular options include:
Malwarebytes: Excellent for detecting and removing malware and spyware.
Norton: Offers comprehensive protection against various types of threats.
2. Network Monitoring Tools
Tools like Wireshark can help analyze network traffic and identify suspicious activity. You can monitor data packets to see if there are any unexpected connections.
3. Task Manager / Activity Monitor
Regularly check the Task Manager (Windows) or Activity Monitor (Mac) for processes that look unfamiliar or suspicious. Research any questionable applications before taking action.
4. System Scans
Use built-in tools to perform system scans:
Windows Defender: Run a full scan for malware and spyware.
Mac’s Built-in Security Features: Use the Malware Removal Tool for additional scanning.
5. Firewall Monitoring
Make sure your firewall is active and monitor logs for any unusual activity. A firewall can block unauthorized access attempts and alert you to potential threats.
Steps to Protect Your Privacy
If you determine that your computer is being monitored or you want to prevent it from happening, follow these steps to enhance your security.
1. Update Your Software Regularly
Keeping your operating system and all software up-to-date ensures that you have the latest security patches. This reduces vulnerabilities that can be exploited by monitoring tools.
2. Use Strong Passwords
Implement strong, unique passwords for all your accounts and devices. Consider using a password manager to generate and store complex passwords securely.
3. Enable Two-Factor Authentication
Two-factor authentication (2FA) adds an extra layer of security by requiring a second form of verification, making unauthorized access much more difficult.
4. Install a Firewall
Ensure you have a firewall activated, whether it’s built-in (like Windows Firewall) or third-party. This helps control incoming and outgoing network traffic.
5. Be Cautious with Downloads
Avoid downloading software from untrusted sources, as this can introduce malware to your system. Always verify the legitimacy of software before installing it.
6. Regularly Review Permissions
Check application permissions on your device regularly. Revoke access for any apps that do not need to access your camera, microphone, or location.
7. Use a VPN
A Virtual Private Network (VPN) encrypts your internet connection, making it difficult for anyone to monitor your online activities.
8. Educate Yourself
Stay informed about the latest cybersecurity threats and best practices. Knowledge is your best defense against monitoring.
When to Seek Professional Help
If you suspect your computer is being monitored and cannot identify or remove the software yourself, consider seeking professional help. Cybersecurity experts can perform a thorough analysis of your system and provide tailored solutions.
Conclusion
Understanding if your computer is being monitored is vital for protecting your privacy. By recognizing the signs, utilizing detection tools, and implementing security measures, you can safeguard your personal information. Remember, vigilance is key in the ever-evolving landscape of digital security. Stay informed, proactive, and secure in your online presence.
#Computer Security#Online Privacy#Cybersecurity#Monitoring Software#Malware Detection#Privacy Protection#Digital Security#Keyloggers#Network Monitoring#Antivirus#VPN#Internet Safety#Personal Data Security#Remote Access Tools#Digital Awareness
2 notes
·
View notes
Text
bbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbb
#im really thinking about like doing something with my life and going into cybersecurity like i said i would when i wasl ike 13#im so into engineering IT computers and all that shit#every trime my dad builds a computer im like I Want to do that#like i wnana build computers and do stuf with computers#i fantasize abotu doing art as a career but#i know it wont pan oput the way i want it to bc my vision is very romanticized#like i know damn well i wont be living by the beach remotely and clocking into freelance art job whenever i want#that just wont happen#we gotta be realistic#but ive lawyas been a person who cant pick betwween things#i really love computers though#the money doesnt really matter to me but i know my mom would be like#OH THATS SO COOL YOU GET PAID SO MUCH!#but like i just wnana be around computers and be in a labyrinth
3 notes
·
View notes
Text
Y'all I'm so fucking excited. Phrack is going to be coming out with a new issue in summer of this year! Hacking magazine that has literally existed since before the birth of the web is still up and running and I am so so so excited to see what winds up in the next issue.
5 notes
·
View notes