#Secure Accounting Software
Explore tagged Tumblr posts
Text
How to Secure Your Financial Data with Billing Software

In an age where cyber threats are growing, protecting your financial data is no longer a luxury, but a necessity. High-end billing software like TRIRID Biz Accounting and Billing Software offers advanced security features to protect your sensitive financial information. Here's how using the right billing software can fortify your business's data security.
1. Protect Your Data with Encryption Technology Data encryption is one of the fundamental aspects of secure billing software. TRIRID Biz secures all your financial transactions and records by encrypting them both during storage and during transmission. This minimizes the risk of data breaches and unauthorized access.
2. Secure Cloud-Based Architecture With TRIRID Biz, your financial data is stored in a highly secure cloud environment, protected by advanced firewalls and regular security updates. Cloud storage not only ensures data safety but also allows seamless access to your billing records anytime, anywhere.
3. Multi-Layered Authentication A single password is no longer enough to keep hackers at bay. That's why TRIRID Biz supports multi-layered authentication, such as Two-Factor Authentication (2FA), to add an extra level of protection to your accounts.
4. Controlled Access with User Roles Sensitive financial information is not to be shared with every individual. TRIRID Biz allows you to tailor your user roles and their permissions so that only users who are authorized will see specific information. This limits any chance of insider threats as well as accidental data exposure.
5. Automatic Backups and Disaster Recovery Data loss can occur due to cyberattacks, hardware failures, or even human error. TRIRID Biz automatically backs up your data regularly, enabling quick recovery and ensuring your operations remain uninterrupted.
6. Real-Time Monitoring and Alerts The best defense is a good offense. TRIRID Biz provides real-time monitoring of your system and alerts you to suspicious activities, such as multiple failed login attempts or unusual data exports. This proactive approach helps prevent breaches before they happen. 7. Compliance with Financial Regulations TRIRID Biz ensures that your business is complying with financial and data protection regulations, such as those of GST guidelines, GDPR, and PCI DSS. This way, your business will operate legally and with security, avoiding heavy fines and reputational damage.
8. Secure Payment Processing Secure payment processing is highly important when dealing with customer transactions. TRIRID Biz integrates with secure payment gateways to ensure safe handling of customers' financial information in compliance with industry standards.
Don't let your financial information at stake. Choose TRIRID Biz Accounting and Billing Software for the ultimate security and peace of mind.
Contact us today for a free demo and see how TRIRID Biz can revolutionize your business's billing and accounting processes!
Call @ +91 8980010210 / +91 9023134246
Visit @ https://tririd.com/tririd-biz-gst-billing-accounting-software
#TRIRID Biz Accounting and Billing Software#Best Accounting & Billing Software In India#Secure Accounting Software#Best Small Business Accounting Software India#Best Cloud Accounting Software for Businesses
0 notes
Text
How to Choose the Best Accounting Software for Your Business
Introduction In the fast-moving environment related to the business world, keeping yourself on top of the finances will never be an easy task. In reality, a company can easily slip into disarray without proper supervision of its finances. No matter whether yours is a small startup or a big corporation, the right kind of accounting software will certainly work wonders in the smooth flow of financial operations. But with accounting software options galore, how do you choose a software that’s suitable for your business? The guide from TechtoIO will take you through everything you need to know to make an informed decision. Read to continue
#analysis#science updates#tech news#trends#adobe cloud#nvidia drive#science#business tech#technology#tech trends#CategoriesSoftware Solutions#Tagsaccounting software comparison#AI in accounting software#automated invoicing software#best accounting software for business#blockchain accounting solutions#choosing accounting software#cloud-based accounting software#expense tracking software#financial reporting tools#FreshBooks review#integrating accounting software#mobile accounting software#QuickBooks vs Xero#scalable accounting software#secure accounting software#small business accounting software#top accounting software 2024#user-friendly accounting software#Wave accounting software
0 notes
Text
i don't think people realize how mason is deadass set to become a billionaire by his mid 30s.
#he was already selling software to companies at 16 and got a few million.#then slowly created neon secure at 22. that pushed him to 20-50 mill.#then if you take into account his job with the wwe and then expanding neon to corporate and gov. partnerships. etc. that puts him at 150-30#at 23-25 years old.#then he creates his skateboard /streetwear shops. that adds another 500 mill.#then as he approaches his mid 30s he's gonna be a billionaire.#and you know he won't be a greedy one.#hes gonna have the company everyone wants to work at weather its his skate company or his security company..#benefits. pto. livable pay??? paid paternal leave.#catch this man on the forbes 30 under 30 thank youuuu
4 notes
·
View notes
Text
I haven’t really seen any of the more recent U.S. election news hitting tumblr yet so here’s some updates (now edited with sources added):
There’s evidence of Trump cheating and interfering with the election.
Possible Russian interference.
Mail-in ballots are not being counted or “recognized” in multiple (notably swing) states.
30+ bomb threats were called in and shut down polling stations on Election Day.
20+ million votes are still unaccounted for, and that’s just to have the same voter turnout as 2020.
There was record voter turnout and new/first-time voter registration this year. We definitely should be well over the turnout in 2020.
U.S. citizens are using this site to demand, not only a recount, but a complete investigation into election fraud and interference for the reasons stated above:
Here is what I submitted as an example:
An investigation for election interference and fraud is required. We desperately need a recount or even a revote. The American people deserve the right to a free and fair election. There has been evidence unveiled of Trump cheating and committing election fraud which is illegal. There is some evidence of possible Russian interference. At least 30+ bomb threats were called in to polling places. Multiple, notably swing states, have ballots unaccounted for and voting machines not registering votes. Ballots and ballot boxes were tampered with and burned. Over 20 million votes that we know of are unaccounted for. With record turnout and new voter registration this year, there should be no possibility that there are less votes than even in the 2020 election.
Sources (working on finding more links but if anyone wants to add info, it’s appreciated):
FBI addressing Russian interference and bomb threats:
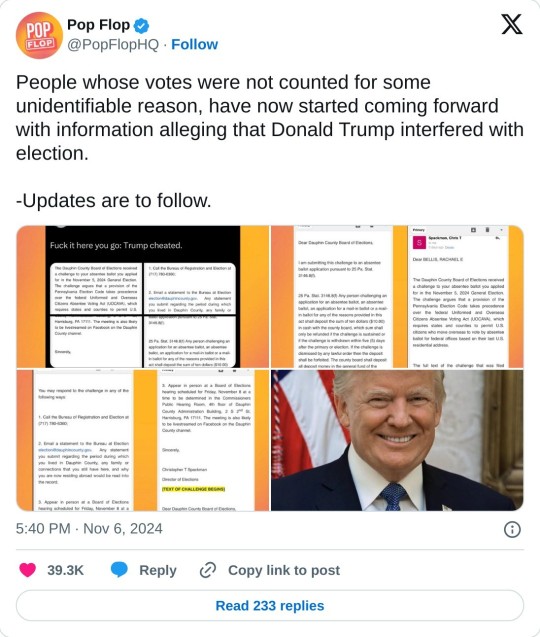
Emails released by Rachael Bellis (private account, can’t share original tweet) confirming Trump committing election fraud:
Pennsylvania's Centre County officials say they are working with their ballot scanner vendor to figure out why the county's mail-in ballot data is "not being recognized when uploaded to the elections software:”

Wisconsin recount:
[ID:
Multiple screenshots and images.
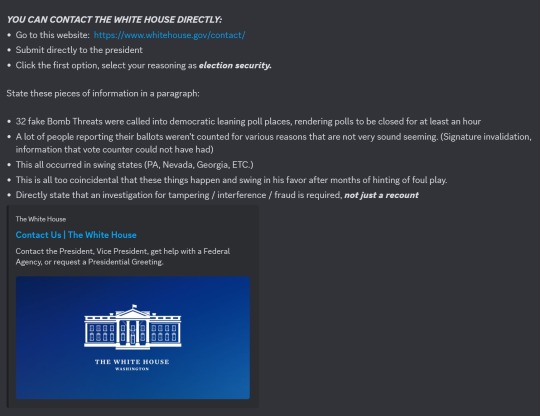
The first is a screenshot with a link and information for contacting the White House directly regarding election fraud. The instructions include choosing to leave a comment to President Joe Biden directly and to select election security as the reason.
The screenshot then instructs people to include any or all of the following information in a paragraph as a comment to the president:
32 fake bomb threats were called into Democratic leaning poll places, rendering polling places closed for at least an hour.
A lot of people reporting their ballots were not counted for various reasons.
This all occurred in swing states.
This is too coincidental that these things happen and swing in his favor after months of hinting at foul play.
Directly state that an investigation for tampering, interference, fraud is required, not just a recount.
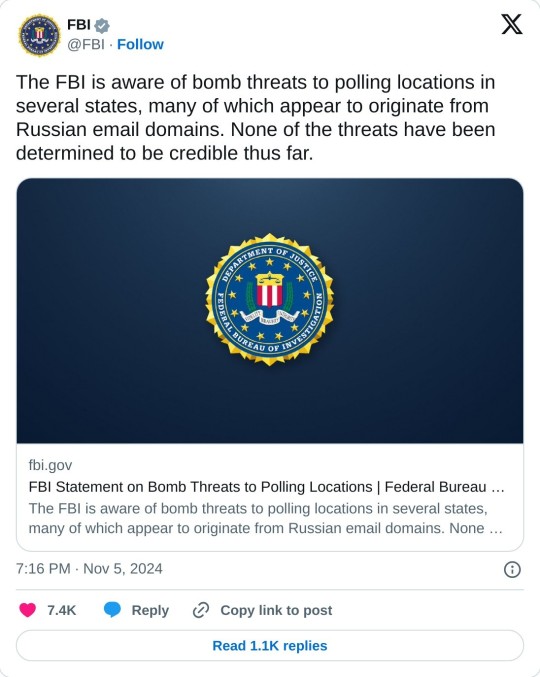
The second image is from the FBI Twitter account that reads:
The FBI is aware of bomb threats to polling locations in several states, many of which appear to originate from Russian email domains. None of the threats have been determined to be credible thus far. https://t.co/j3YfajVK1m — FBI (@FBI) November 5, 2024
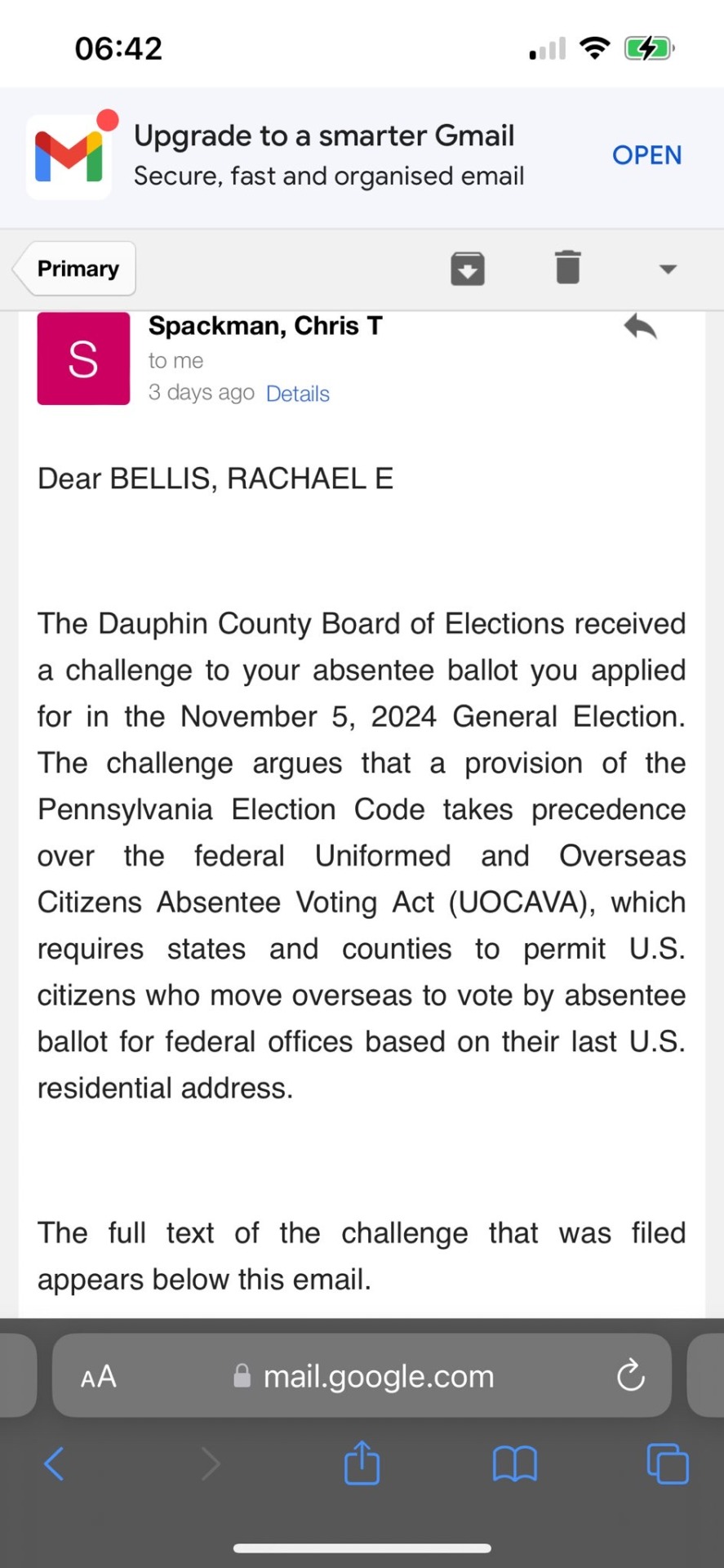
The next four Gmail screenshots of an email sent to Rachael Bellis from Chris T. Spackman that read together as follows:
Dear BELLIS, RACHAEL E., The Dauphin County Board of Elections received a challenge to your absentee ballot you applied for in the November 5, 2024 General Election. The challenge argues that a provision of the Pennsylvania Election Code takes precedence over the federal Uniformed and Overseas Citizens Absentee Voting Act (UOCAVA), which requires states and counties to permit U.S. citizens who move overseas to vote by absentee ballot for federal offices based on their last U.S. residential address.
The full text of the challenge that was filed appears below this email.
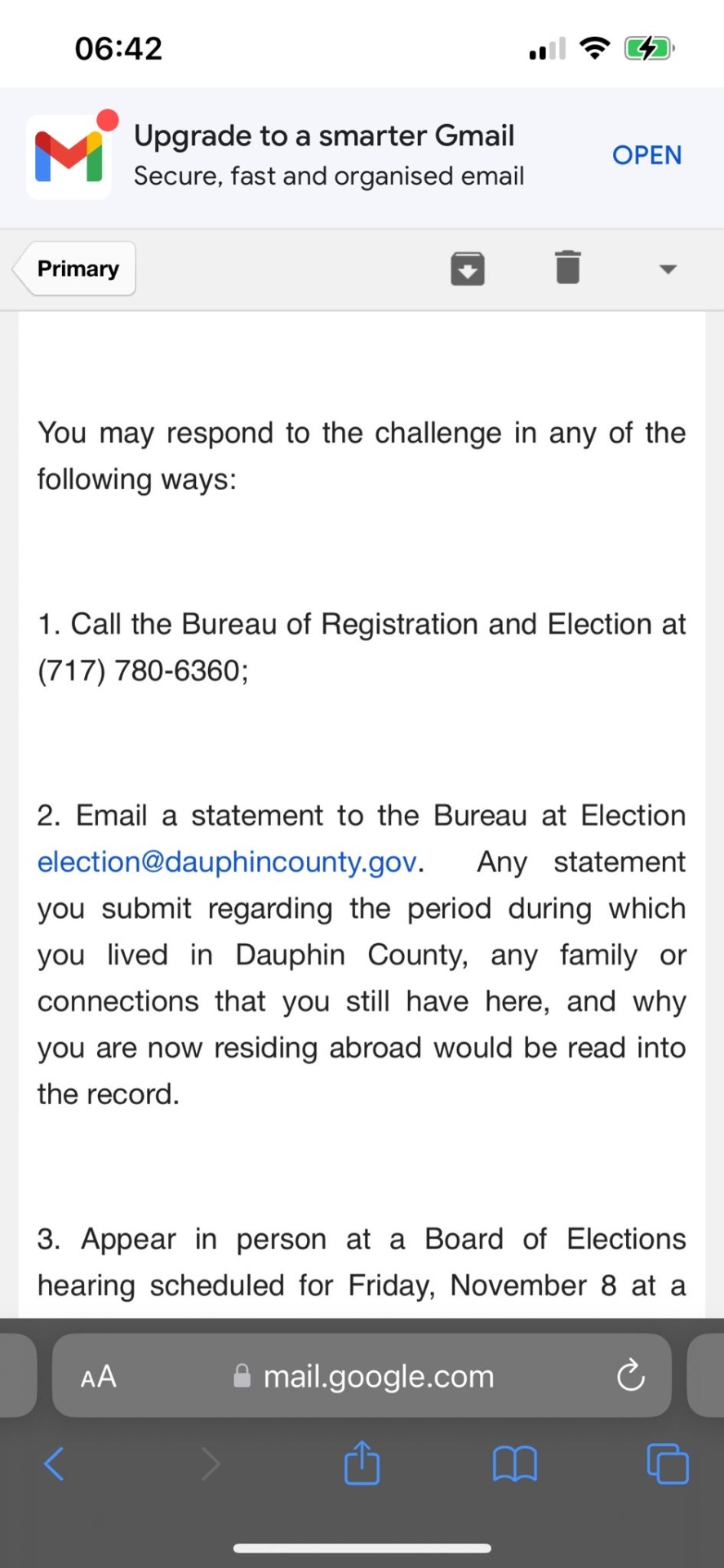
You may respond to the challenge in any of the following ways:
1. Call the Bureau of Registration and Election at (717) 780-6360;
2. Email a statement to the Bureau at Election [email protected]. Any statement you submit regarding the period during which you lived in Dauphin County, any family or connections that you still have here, and why you are now residing abroad would be read into the record.
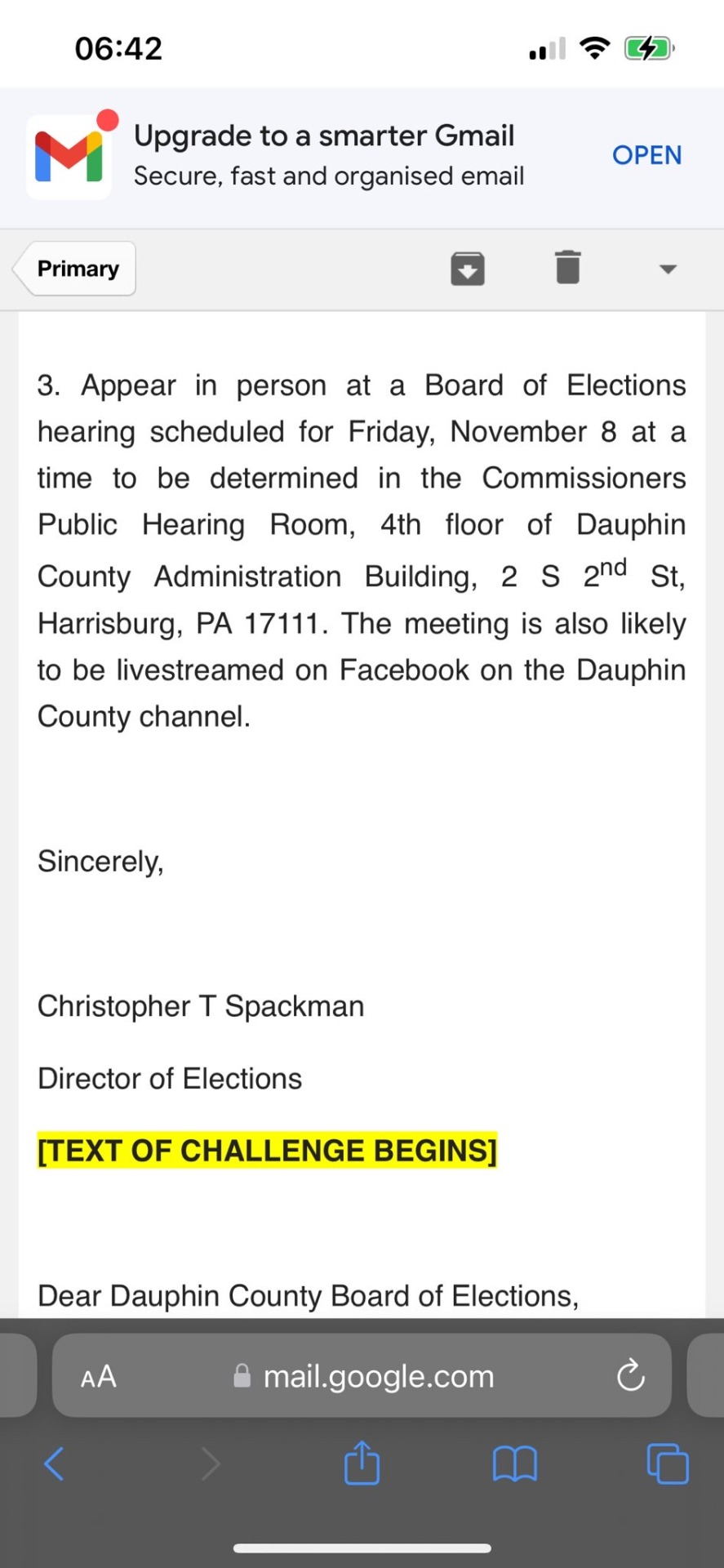
3. Appear in person at a Board of Elections hearing scheduled for Friday, November 8 at a time to be determined in the Commissioners Public Hearing Room, 4th floor of Dauphin County Administration Building, 2 S 20d St, Harrisburg, PA 17111. The meeting is also likely to be livestreamed on Facebook on the Dauphin County channel.
Sincerely,
Christopher T Spackman
TEXT OF CHALLENGE BEGINS
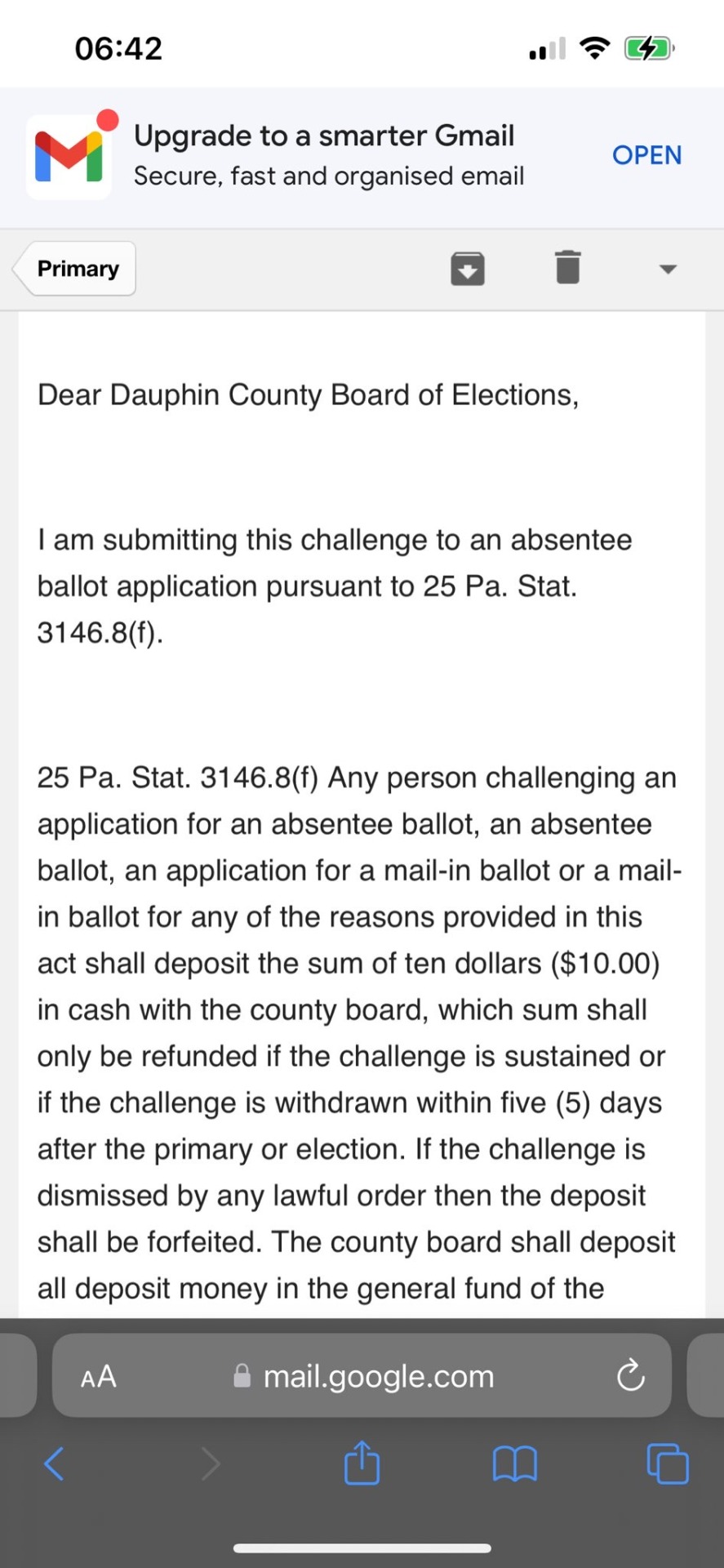
Dear Dauphin County Board of Elections,
I am submitting this challenge to an absentee ballot application pursuant to 25 Pa. Stat.
3146.8(f).
25 Pa. Stat. 3146.8(f) Any person challenging an application for an absentee ballot, an absentee ballot, an application for a mail-in ballot or a mail-in ballot for any of the reasons provided in this act shall deposit the sum of ten dollars ($10.00) in cash with the county board, which sum shall only be refunded if the challenge is sustained or if the challenge is withdrawn within five (5) days after the primary or election. If the challenge is dismissed by any lawful order then the deposit shall be forfeited. The county board shall deposit all deposit money in the general fund of the…
The rest of the forwarded email is cut off.
The last image is a screenshot of the official statement from the Centre County, Pennsylvania Board of Commissioners released on November 6, 2024 that states:
Centre County Working with Ballot Scanner Vendor to Export Election Results.
(Bellefonte, PA) -Centre County Elections Office is working continuously to provide mail-in ballot data in order to post unofficial results.
To this point, all ballots have been scanned, including all mail-in ballots.
Centre County's Election team and IT team have identified that the data are successfully being exported from the mail-in ballot scanners, but that the data is not being recognized when uploaded to the elections software.
Centre County's Administrator, John Franek, Jr. stated, "We have not stopped working, and we will continue to work until unofficial results are posted and reported to the Pennsylvania Department of State."
As a next step, Centre County has begun working with the equipment vendor to adjust configurations to make the two systems-the mail-in ballot scanner and the elections software where data are uploaded -compatible with one another.
We will provide updates as we make progress.
/end ID]
#sources added#us politics#us election#presidential election#2024 presidential election#election interference#election integrity#election security#image described#image description in alt#image description included#image description added#described#kamala harris#kamala 2024#us news#us presidents#updated id
36K notes
·
View notes
Text
The Future of Accounts Payable and Receivable Automation in India
In today’s fast-paced business environment, financial transactions must be handled efficiently to maintain cash flow and profitability. Companies are rapidly shifting towards digital solutions to optimize their financial operations. Accounts payable automation in India is revolutionizing how businesses manage their outgoing payments, ensuring accuracy, compliance, and seamless processing. Likewise, accounts receivable automation in India is helping organizations streamline invoicing, payment collection, and reconciliation, reducing manual errors and delays.

The Rise of Financial Services Automation in India
As industries expand and transactions increase, traditional manual financial processes become inefficient and error-prone. This has led to a surge in demand for financial services automation in India. Businesses across sectors are embracing automation to improve efficiency, enhance compliance, and minimize risks. Automated financial workflows not only speed up payment cycles but also provide real-time visibility into transactions, ensuring better decision-making.
Key Benefits of Accounts Payable and Receivable Automation
1. Enhanced Efficiency and Speed
Automation eliminates repetitive tasks, reducing the time spent on invoice processing and payment approvals. Companies using accounts payable automation in India can process invoices swiftly and avoid late payment penalties.
2. Error Reduction and Compliance
Manual data entry often results in miscalculations and compliance issues. With accounts receivable automation in India, businesses can ensure accurate billing, automated reminders, and error-free financial records.
3. Improved Cash Flow Management
By automating accounts payable and receivable functions, businesses can maintain a healthy cash flow, avoid bottlenecks, and ensure timely payments and collections.
4. Fraud Prevention and Security
Automation software comes with built-in security features that protect businesses from fraud, unauthorized access, and financial discrepancies.
Choosing the Right Accounts Payable and Receivable Automation Software
Selecting a reliable Accounts Payable Receivable Automation Software Company is crucial for businesses looking to modernize their financial operations. A good software provider offers features such as AI-powered invoice processing, automated reconciliation, seamless integration with ERP systems, and real-time reporting. Investing in the right automation solution ensures long-term financial efficiency and business growth.
Conclusion
The demand for accounts payable automation in India and accounts receivable automation in India is growing as businesses recognize the advantages of financial digital transformation. Partnering with a top Accounts Payable Receivable Automation Software Company can help organizations achieve operational excellence, reduce costs, and improve financial accuracy. Embracing financial services automation in India is no longer a choice but a necessity for companies looking to stay ahead in the competitive market.
If your business is looking for a seamless transition to automated financial processes, now is the time to explore cutting-edge solutions and take a step towards financial excellence!
#aviation compliance software in india#audit tracking system#hipaa compliant workflow automation in india#document approval workflows in india#aviation document management system#healthcare data security solutions in india#accounts payable automation in india#healthcare regulatory compliance software in india#Accounts Payable Receivable Automation Software Company#financial services automation in india
0 notes
Text
How to Integrate Invoice Maker Tools with Your Accounting Software

In today's fast-paced business world, efficiency and accuracy are paramount when managing financial data. One essential aspect of this is invoicing. As businesses grow, manually creating and managing invoices becomes more cumbersome. That's where invoice maker tools come into play, allowing you to quickly generate professional invoices. However, to truly streamline your financial workflow, it’s important to integrate these tools with your accounting software.
Integrating invoice maker tools with your accounting software can help automate the process, reduce human error, and improve overall productivity. This article will walk you through how to integrate your Invoice Maker Tools with accounting software effectively, ensuring smoother operations for your business.
1. Choose the Right Invoice Maker Tool
Before integration, ensure you have selected an invoice maker tool that suits your business needs. Most invoice maker tools offer basic features such as customizable templates, tax calculations, and payment tracking. However, the integration potential is an important factor to consider.
Look for an invoice maker tool that offers:
Cloud-based features for easy access and collaboration.
Customizable templates for branding.
Multi-currency support (if you do international business).
Integration capabilities with various accounting software.
Examples of popular invoice maker tools include Smaket, QuickBooks Invoice, FreshBooks, and Zoho Invoice.
2. Check Compatibility with Your Accounting Software
Not all invoice maker tools are compatible with every accounting software. Before proceeding with the integration, confirm that both your invoice maker tool and accounting software are capable of syncing with each other.
Common accounting software that integrate with invoice tools includes:
QuickBooks
Smaket
Xero
Sage
Wave Accounting
Zoho Books
Most software providers will indicate which tools can integrate with their platform. Check for available APIs, plugins, or built-in integration features.
3. Use Built-in Integrations or APIs
Many modern invoice maker tools and accounting software platforms come with built-in integrations. These are often the easiest to set up and manage.
If you choose a platform that does not offer a built-in integration, you can use APIs (Application Programming Interfaces) to link the two systems. APIs are a more technical option, but they provide greater flexibility and customization.
4. Set Up the Integration
Once you've confirmed that the invoice tool and accounting software are compatible, follow the setup process to connect both tools.
The typical steps include:
Access your accounting software: Log into your accounting software and navigate to the integration settings or marketplace.
Search for the invoice maker tool: In the marketplace or integration section, look for the invoice tool you are using.
Connect accounts: Usually, you’ll be asked to sign into your invoice maker tool from within the accounting software and authorize the integration.
Map your fields: You may need to map invoice fields (like customer names, amounts, or due dates) to corresponding fields in the accounting software to ensure the data flows seamlessly.
5. Test the Integration
After the integration is complete, it’s crucial to test whether the connection between the invoice maker and accounting software is working as expected. Generate a sample invoice and check if the details appear correctly in your accounting software. Confirm that invoices are synced, and ensure payment status updates automatically.
Test for:
Accurate syncing of client details: Ensure names, addresses, and payment history are transferred correctly.
Real-time updates: Check that any changes made to invoices in the invoice tool reflect in your accounting software.
Reporting features: Verify that your financial reports, such as profit and loss statements, include data from the invoices.
6. Automate Invoicing and Payments
Once the integration is up and running, set up automated workflows. With the right integration, you can automate recurring invoices, late payment reminders, and payment receipts. This reduces manual effort and ensures consistency in your accounting.
7. Monitor and Maintain the Integration
Just because the integration is set up doesn't mean it's a "set it and forget it" situation. Regularly monitor the syncing process to ensure everything is working smoothly.
Make sure:
Software updates: Regular updates from either your accounting software or invoice maker tool might affect the integration. Always check for compatibility after any software updates.
Backup and security: Ensure your data is securely backed up, and verify that integration tools comply with security standards.
8. Benefits of Integration
By integrating invoice maker tools with your accounting software, you’ll enjoy several key benefits:
Time Savings: Automating the invoicing process frees up time for you to focus on other important aspects of your business.
Improved Accuracy: With automatic syncing, you reduce the risk of errors that often come with manual data entry.
Better Financial Management: Real-time data syncing allows for accurate tracking of income, expenses, and cash flow, which helps with budgeting and financial forecasting.
Enhanced Customer Experience: Timely and accurate invoicing helps maintain a professional image and reduces confusion with clients.
Conclusion
Integrating invoice maker tools with Accounting Software is a smart move for businesses that want to streamline their financial operations. By selecting the right tools, following the integration steps, and ensuring regular maintenance, you can save time, improve accuracy, and focus on growing your business. Don’t let manual invoicing slow you down—leverage modern tools to automate your processes and boost efficiency.
#accounting#software#gst#smaket#billing#gst billing software#accounting software#invoice#invoice software#cloud accounting software#benefits of cloud accounting#financial software#business accounting tools#cloud-based accounting#real-time financial insights#scalable accounting solutions#cost-effective accounting software#cloud accounting security#automated accounting software#business accounting software#cloud accounting features
0 notes
Text
Tinder Multi-login Account to Prevent Account Banning!

Ways to solve the problem of Tinder account multi-login blocking
1. Avoid logging in on multiple devices at the same time
(1) Try to log in to your Tinder account on only one primary device. If you need to log in on other devices, avoid frequent switching and ensure each login is legitimate.
(2) Don’t lend your account to others to log in on different devices to minimize the risk of being misjudged by the platform.
2. Standardized behavior
(1) Strictly abide by Tinder’s User Agreement and Community Guidelines, and do not engage in any illegal behavior.
(2) Avoid using multiple accounts to engage in inappropriate interactions and maintain a sincere and civilized attitude towards dating.
3. Pay attention to the network environment and equipment information
(1) Try to maintain a stable network environment and avoid frequent login or operation of your account under unstable network conditions.
(2) Regularly clear the cache and cookies of your device to minimize abnormal information that may be detected by the platform.
(3) Log in to your Tinder account on the VMLogin fingerprint browser.
Start the VMLogin Fingerprint Browser client, create multiple virtual browsers, and set the fingerprint parameters, IP address, etc. of multiple virtual browsers to differentiate the account environment. Users can securely multi-login to Tinder accounts on a single computer. Each Tinder account has an independent digital fingerprint, IP address, cookie and cache, and login environment, effectively preventing account blocking due to Tinder's multi-account association.
New users can receive a free trial after signing up for VMLogin~
#protection#dataprotection#incognito#browser#virtualplatform#vmlogin#tinder#software#search engine marketing#socialmediamarketing#onlinemarketing#growyourbusiness#multiple accounts#multishop#amazon business#ecommercesuccess#data security
0 notes
Text
Benefits of Upgrading to Tally Prime 5.0 for Your Business
Upgrading to Tally Prime 5.0 presents a unique opportunity for businesses to enhance their financial management and streamline their operations. With the Tally Prime 5.0 download available, users can access a range of robust features designed to elevate their accounting processes. From small startups to large enterprises, the versatility offered by Tally Prime 5.0 makes it a suitable choice for companies across various sectors. By embracing this latest version, businesses not only improve their efficiency but also gain the flexibility needed to adapt to the demands of an ever-changing commercial landscape.

One of the standout aspects of Tally Prime 5.0 is its user-friendly interface and simplified navigation. Users can expect to save precious time on routine accounting tasks, thanks to enhancements that allow for quicker access to essential features. This upgrade also introduces advanced reporting capabilities, enabling businesses to generate insightful analyses of their financial health seamlessly. With the new tools and analytics at their disposal, decision-makers can expect to make more informed choices, ultimately driving growth and profitability.
Additionally, Tally Solutions has integrated cutting-edge technology into this update, enhancing security and data integrity. Businesses can rest assured that their sensitive financial information is well protected, thanks to improved encryption and backup features. This emphasis on security provides peace of mind for users, allowing them to focus on their core operations without the worry of data breaches. The new features and benefits accompanying Tally Prime 5.0 make it easier than ever to manage various aspects of a business while ensuring robust protection against potential threats.
In conclusion, the decision to upgrade to Tally Prime 5.0 is one that can significantly benefit organizations looking to maximize their operational efficiency and safeguard their financial data. The combination of a user-friendly interface, advanced reporting tools, and enhanced security measures positions this software as a leading solution in the accounting field. With the Tally Prime 5.0 download readily available, businesses are encouraged to leverage the new features and benefits with Tally Solutions, ensuring they remain competitive in today’s dynamic marketplace.
#TallyPrime 5.0#TallyPrime upgrade#accounting software#business management software#TallyPrime features#TallyPrime benefits#financial management#GST compliance#data security#automated ledger#Tally solution
0 notes
Text
Amazon Prime Day occasion begins, gross sales up 12% in first 7 hours: Report | Firm Information
Prime Day can function a bellwether for the vacation procuring season. 3 min learn Final Up to date : Jul 17 2024 | 12:10 AM IST Amazon.com Inc.’s Prime Day gross sales rose virtually 12 per cent within the first seven hours of the occasion in contrast with the identical interval final 12 months, based on Momentum Commerce, which manages 50 manufacturers in a wide range of product…
#amazon#Amazon Prime#artificial intelligence#bank account#Check Point Software Technologies#counterfeit products#director of worldwide buyer risk prevention#E-commerce & Auction Services#e-commerce shoppers#eBay#Federal Trade Commission#Food Retail & Distribution (NEC)#HTTP#Internet & Mail Order Department Stores#Josh Planos#online hoaxes#online retailer#online shopping giant#Online shopping scams#phony products#public relations#retail calendar#Scott Knapp#Security Software#social media ads#vice president of communications and public relations#Walmart
0 notes
Text
Why Self-Employed Individuals Should Explore SETC and FFCRA Benefits
Why Self-Employed Small Business Owners Should Explore SETC and FFCRA Benefits As a self-employed small business owner, gig worker, or 1099 contractor, managing finances can often feel like walking a tightrope. Between fluctuating incomes, rising costs, and complex tax regulations, it’s easy to overlook potential benefits that could significantly ease your financial burden. Among these benefits,…
#1099 contractors#accounting firms#business growth#cash advances#cash flow#eligibility criteria#Families First Coronavirus Response Act#FFCRA#financial benefits#financial management#financial relief#gig workers#IRS regulations#securing loans#Self-Employed#Self-Employed Tax Credit#setc#small business owners#tax credits#tax software
0 notes
Text
Future Of AI In Software Development

The usage of AI in Software Development has seen a boom in recent years and it will further continue to redefine the IT industry. In this blog post, we’ll be sharing the existing scenario of AI, its impacts and benefits for software engineers, future trends and challenge areas to help you give a bigger picture of the performance of artificial intelligence (AI). This trend has grown to the extent that it has become an important part of the software development process. With the rapid evolvements happening in the software industry, AI is surely going to dominate.
Read More
#Accountability#Accuracy Accuracy#Advanced Data Analysis#artificial intelligence#automated testing#Automation#bug detection#code generation#code reviews#continuous integration#continuous deployment#cost savings#debugging#efficiency#Enhanced personalization#Ethical considerations#future trends#gartner report#image generation#improved productivity#job displacement#machine learning#natural language processing#privacy privacy#safety#security concerns#software development#software engineers#time savings#transparency
0 notes
Text
Accounting Meets Innovation

In today's fast-paced digital era, traditional accounting methods are changing at a rapid pace. Innovative tools such as TRIRID Accounting and Billing Software help businesses streamline their financial operations and remain ahead in the competitive market.
Why Innovation in Accounting Matters
Modern accounting software takes advantage of the latest technologies such as cloud computing, artificial intelligence, and real-time analytics to make the once cumbersome financial tasks turn into smooth workflows. In doing so, businesses can gain:
Accuracy: Calculations are minimized through automation.
Efficiency: Save time through streamlined billing and reporting.
Scalability: Grow your business easily.
TRIRID: Redefining Accounting Standards
TRIRID Biz Accounting Software has the perfect mix of functionality and innovation. With advanced tools and user-friendly features, TRIRID ensures that your business is handled well with:
GST-Compliant Billing
Tax Management
Inventory Tracking
Multi-User Access
Key Features That Drive Success
Cloud Integration: View your accounts anytime, anywhere
Secure Transactions: Ensure data safety with the most advanced encryption
Customizable Dashboards: Get the insights your business needs
Future-Proof Your Business with TRIRID
Innovation is the core foundation of success in accounting. With TRIRID Biz Accounting Software, you're empowering your business with a tool that simplifies all operations and enhances productivity.
Leap into the future of accounting—see how TRIRID Biz can change your financial management today!
Call @ +91 8980010210 / +91 9023134246
Visit @ https://tririd.com/tririd-biz-gst-billing-accounting-software
#TRIRID Accounting and Billing Software#Best accounting software in Ahmedabad Gujarat#Secure Billing Solutions#TRIRID-Billing software in Bopal in Ahmedabad#TRIRID-Billing software in ISCON-Ambli road-ahmedabad
0 notes
Text
Data breach litigation, the new cyber battleground. Are you prepared? - CyberTalk
New Post has been published on https://thedigitalinsider.com/data-breach-litigation-the-new-cyber-battleground-are-you-prepared-cybertalk/
Data breach litigation, the new cyber battleground. Are you prepared? - CyberTalk


By Deryck Mitchelson, EMEA Field Chief Information Security Officer, Check Point Software Technologies.
Nearly everyone trusts Google to keep information secure. You trust Google with your email. I use Google for my personal email. Yet, for three years – from 2015 to 2018 – a single vulnerability in the Google Plus platform resulted in the third-party exposure of millions of pieces of consumer data.
Google paid a settlement of $350M in a corresponding shareholder lawsuit, but most organizations cannot afford millions in settlements. For most organizations, this level of expenditure due to a breach is unthinkable. And even for larger organizations with financial means, constant cycles of breach-related lawsuits are unsustainable.
Yet, across the next few years, especially as organizations continue to place data into the cloud, organizations are likely to see a significant uptick in post-breach litigation, including litigation against CISOs, unless they adopt stronger cyber security protocols.
Litigation looms large
Organizations that have experienced data breaches are battling a disturbing number of lawsuits. In particular, privacy-related class actions against healthcare providers are taking off.
Globally, there were 2X the number of data breach victims in 2023 as compared to 2022.
In 2023 alone, breach related class actions and government enforcement suits resulted in over $50 billion in settlement expenditures.
The Irish Health Service Executive, HSE, was severely impacted by a large cyber attack in 2021 with 80% of its IT services encrypted and 700 GB of unencrypted data exfiltrated, including protected health information. The HSE subsequently wrote to 90,936 affected individuals. It has been reported that the HSE is facing 473 data-protection lawsuits, and this number is expected to continue rising.
I recently spoke with a lawyer who specializes in data breach litigation. Anecdotally, she mentioned that breach-related lawsuits have grown by around 10X in the last year. This is becoming the new normal after a breach.
While organizations do win some of these lawsuits, courts have become increasingly sympathetic to plaintiffs, as data breaches can result in human suffering and hardship in the forms of psychological distress, identity theft, financial fraud and extortion. They can also result in loss of human life, but more about that later.
In courts of justice, an organization can no longer plead ‘we made an error or were unaware’, assuming that such a line will suffice. The World Economic Forum has found that 95% of cyber security threats can, in some capacity, be traced to human error. These cases are not complex. But the level of litigation shows that businesses are still making avoidable missteps.
To that effect, businesses need to not only start thinking about data protection differently, but also need to start operating differently.
Personal (and criminal) liability for CISOs
CISOs can be held personally liable, should they be found to have failed in adequately safeguarding systems and data that should be protected. At the moment, we’re not seeing much in the way of criminal liability for CISOs. However, if CISOs appear to have obfuscated the timeline of events, or if there isn’t full transparency with boards on levels of cyber risk, courts will indeed pursue a detailed investigation of a CISO’s actions.
The patch that would have fixed a “known critical vulnerability” should have been applied immediately. If the organization hadn’t delayed, would it still have been breached?
Therefore, it is in CISOs’ best interest to record everything – every interaction, every time that they meet with the board, and every time that they’re writing a document (who said what information, what the feedback was, who has read it, what the asks are), as a proactive breach preparedness measure.
If a CISO ends up in litigation, he or she needs to be able to say ‘this risk was fully understood by the board’. CISOs will not be able to argue “well, the board didn’t understand the level of risk” or “this was too complex to convey to the board”, it is the CISOs job to ensure cyber risk is fully understood.
We’re starting to see a trend where CISOs are leaving organizations on the back of large breaches, which may mean that they knew their charter, but failed to take full responsibility and accountability for the organization’s entire cyber security program.
The consumer perspective
As a consumer, I would expect CISOs to know what their job is – to understand the attack surface and to map out where they have weaknesses and vulnerabilities. And to have a program in-place in order to mitigate against as much.
But even if CISOs have a program in place to mitigate breaches, consumers can still come after them for a class action. Consumers can still argue that cyber security staff should have and could have moved faster. That they should have attempted to obtain additional investment funding from the board in order to remediate problems efficiently or to increase their operational capacity and capability to prevent the data breach.
The challenge that CISOs have got is that they’re trying to balance funding acquisition, the pace of change, innovation, and competitive advantage against actually ensuring that all security endeavors are done correctly.
A current case-study in liability
In Scottland, the National Health System of Dumfries and Gallloway recently experienced a serious data breach. The attack led to the exposure of a huge volume of Personally Identifiable Information (PII). Reports indicate that three TB of sensitive data may be been stolen. As means of proof, the cyber criminals sent screenshots of stolen medical records to the healthcare service.
As expected, a ransom demand was not paid. The criminals have now leaked a large volume of data online. Having previously worked in NHS Scotland, I find such criminal activity, targeting sensitive healthcare information, deplorable. Will we now, similar to HSE, see already constrained taxpayers’ money being used to defend lawsuits?
Liability leverage with proper tooling
CISOs cannot simply put in tooling if it can’t stand up to scrutiny. If CISOs are looking at tooling, but less-so at the effectiveness/efficacy of that tooling, then they should recognize that the probability of facing litigation is, arguably, fairly high. Just because tooling functions doesn’t mean that it’s fit for purpose.
In regards to tooling, CISOs should ask themselves ‘is this tool doing what it was advertised as capable of?’ ‘Is this delivering the right level of preventative security for the organization?’
Boards should also demand a certain level of security. They should be asking of CISOs, ‘Is the efficacy of what you’ve implemented delivering at the expected level, or is it not?’ and ‘Would our security have prevented a similar attack?’ We don’t see enough senior conversation around that. A lot of organizations fail to think in terms of, ‘We’ve got a solution in-place, but is it actually performing?’
CISOs need to approach data the same way that banks approach financial value. Banks place the absolute best safeguards around bank accounts, investments, stocks and money. CISOs need to do the same with all data.
Third-party risk
One of the areas in which I often see organizations struggle is supply chain and third-party risk. As you’ll recall, in August of 2023, over 2,600 organizations that deployed the MOVEit app contended with a data breach.
What lessons around due diligence can be learned here? What more could organizations have done? Certainly, CISOs shouldn’t just be giving information to third parties to process. CISOs need to be sure that data is being safeguarded to the right levels. If it’s not, organizational leaders should hold CISOs accountable.
If the third party hasn’t done full risk assessments, completed adequate due diligence and understood the information that they’ve got, then consider severing the business connection or stipulate that in order to do business, certain security requirements must be met.
The best litigation defense
In my view, the best means of avoiding litigation consists of improving preventative security by leveraging a unified platform that offers end-to-end visibility across your entire security estate. Select a platform with integrated AI capabilities, as these will help prevent and detect a breach that may be in-progress.
If an organization can demonstrate that they have deployed a security platform that adheres to industry best practices, that’s something that would enable an organization to effectively demonstrate compliance, even in the event of a data breach.
With cyber security systems that leverage AI-based mitigation, remediation and automation, the chances of a class-action will be massively reduced, as the organization will have taken significant and meaningful steps to mitigate the potentiality of a breach.
Reduce your organization’s breach probability, and moreover, limit the potential for lawsuits, criminal charges against your CISO and overwhelming legal expenditures. For more information about top-tier unified cyber security platforms, click here.
#2022#2023#Accounts#ai#app#approach#Attack surface#automation#billion#board#boards#breach#Business#challenge#change#Check Point#Check Point Software#chief information security officer#CISO#CISOs#Cloud#compliance#consumer data#consumers#cyber#cyber attack#cyber criminals#cyber risk#cyber security#cyber security staff
0 notes
Text
Someone accessed my Gmail 2 days ago, compromising my linked accounts like Twitter and YouTube. Here's how it happened, why I fell for it, and what you can learn to avoid making the same mistake:
The scam I fell victim to was a cookie hijack. The hacker used malicious software to steal my browser cookies (stuff like autofill, auto sign in, etc), allowing them to sign in to my Gmail and other accounts, completely bypassing my 2FA and other security protocols.
A few days ago, I received a DM from @Rachael_Borrows, who claimed to be a manager at @Duolingo. The account seemed legitimate. It was verified, created in 2019, and had over 1k followers, consistent with other managers I’d seen at the time n I even did a Google search of this person and didnt find anything suspicious.
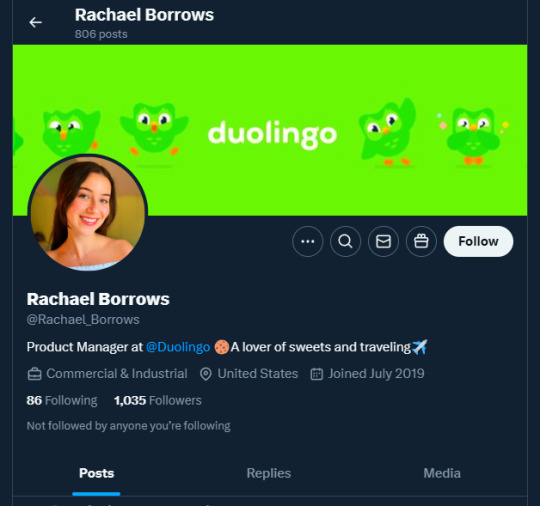
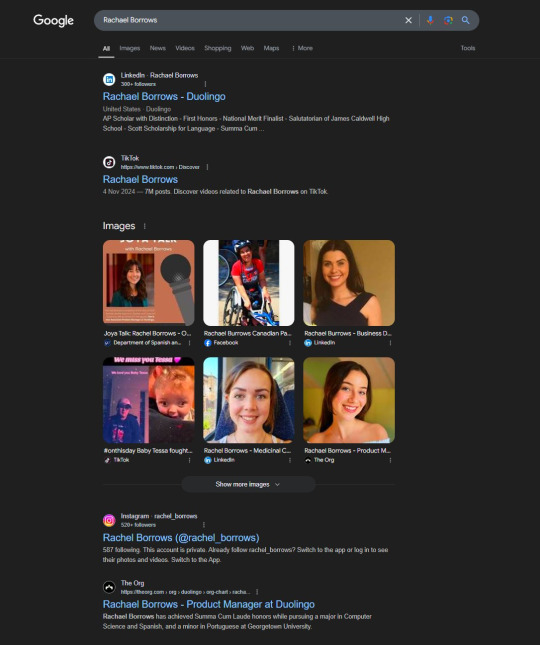
She claimed that @Duolingo wanted me to create a promo video, which got me excited and managed to get my guard down. After discussing I was asked to sign a contract and at app(.)fastsigndocu(.)com. If you see this link, ITS A SCAM! Do NOT download ANY files from this site.
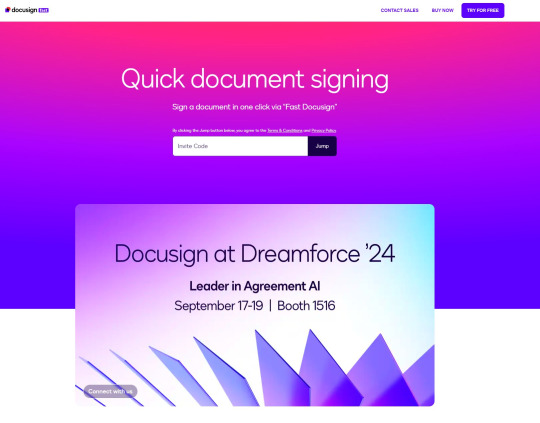
Unfortunately, I downloaded a file from the website, and it downloaded without triggering any firewall or antivirus warnings. Thinking it was just a PDF, I opened it. The moment I did, my console and Google Chrome flashed. That’s when I knew I was in trouble. I immediately did an antivirus scan and these were some of the programs it found that were added to my PC without me knowing:

The thing about cookie hijacking is that it completely bypasses 2FA which should have been my strongest line of defense. I was immediately signed out of all my accounts and within a minute, they changed everything: passwords, 2FA, phone, recovery emails, backup codes, etc.
I tried all methods but hit dead ends trying to recover them. Thankfully, my Discord wasn’t connected, so I alerted everyone I knew there. I also had an alternate account, @JLCmapping, managed by a friend, which I used to immediately inform @/TeamYouTube about the situation
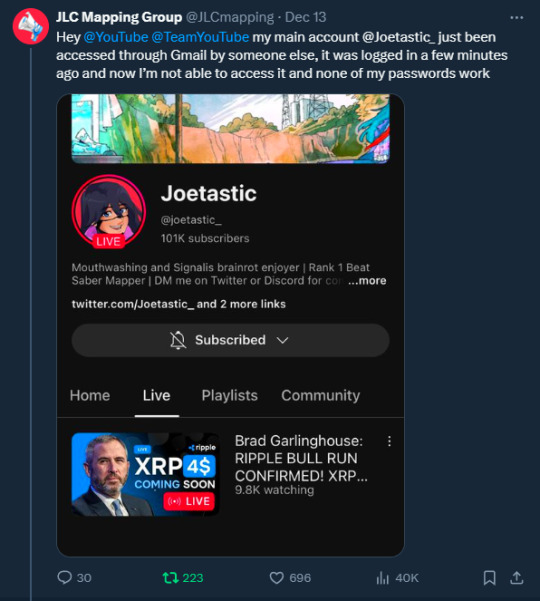
Meanwhile, the hackers turned my YouTube channel into a crypto channel and used my Twitter account to spam hundreds of messages, trying to use my image and reputation to scam more victims
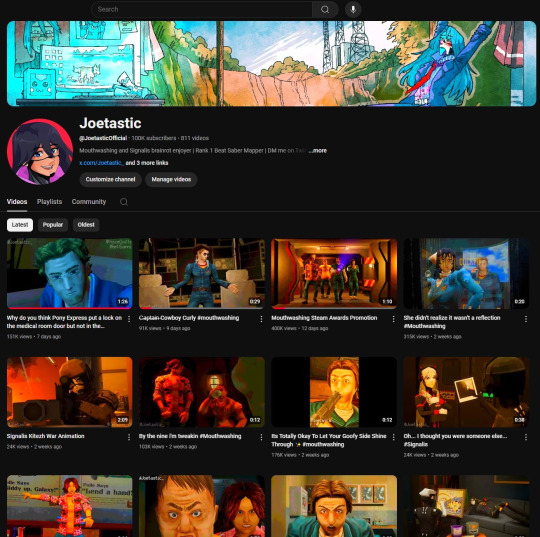
Thankfully, YouTube responded quickly and terminated the channel. Within 48 hours, they locked the hacker out of my Gmail and restored my access. They also helped me recover my channel, which has been renamed to JoetasticOfficial since Joetastic_ was no longer available.
Since then, I’ve taken several steps to secure my accounts and prevent this from happening again. This has been a wake-up call to me, and now I am more cautious around people online. I hope sharing it helps others avoid falling victim to similar attacks. (End)
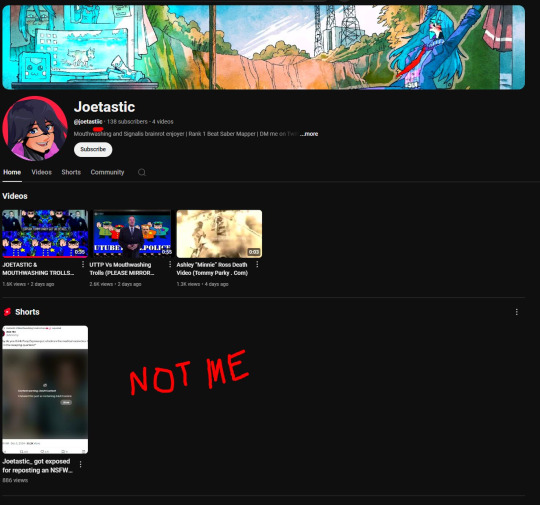
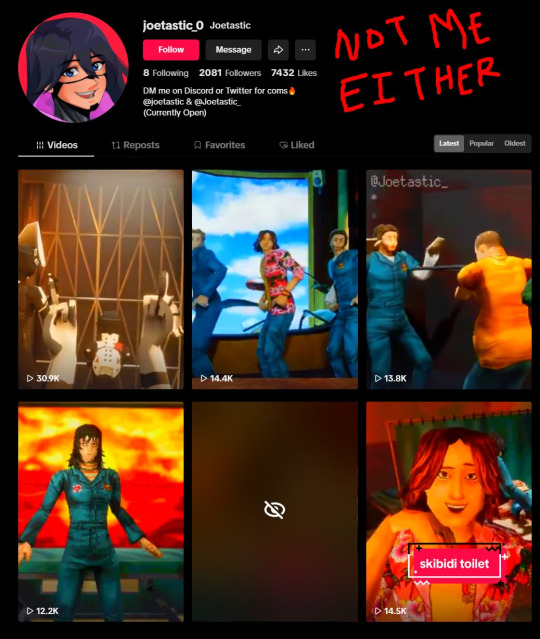
(side note) Around this time, people also started to impersonate me on TikTok and YouTube. With my accounts terminated, anyone searching for "Joetastic" would only find the imposter's profiles. I’m unsure whether they are connected or if it’s just an unfortunate coincidence, but it made the situation even more stressful.
3K notes
·
View notes
Text
A Close Look at the Build Operate Transfer Model in Accounting Outsourcing

93% of accounting firms faced in delay accounting tasks due to staffing shortage
In the advent of technological advancements and evolving landscapes, accounting firms continually seek innovative strategies to streamline operations and boost efficiency. This dynamic sphere presents an array of back-office services, propelling firms to explore new horizons.
Read More on A Close Look at the Build Operate Transfer Model in Accounting Outsourcing
#Accounting Outsourcing#benefits of outsourcing#bookkeeping#bot model#Build Operate Transfer Model#data security#implementing software#offshore accounting partner#Outsourced Accounting
0 notes
Text
Revolutionizing Healthcare with HIPAA Compliant Workflow Automation in India
The healthcare industry in India is rapidly evolving, with digital transformation reshaping how medical data is managed and secured. With increasing concerns over patient privacy, regulatory compliance, and operational efficiency, healthcare providers must adopt HIPAA compliant workflow automation in India to streamline their processes while ensuring data security and regulatory adherence.

The Need for HIPAA Compliant Workflow Automation in India
Healthcare organizations deal with vast amounts of sensitive patient data, making security and compliance crucial. Manual processes not only slow down operations but also pose risks such as data breaches, unauthorized access, and compliance violations. By implementing HIPAA compliant workflow automation in India, hospitals, clinics, and medical service providers can enhance efficiency, reduce errors, and maintain compliance with global standards.
Key benefits of workflow automation include:
Improved Data Security: Automating healthcare workflows minimizes human intervention, reducing the chances of data mishandling.
Regulatory Compliance: Automated systems ensure that healthcare organizations meet regulatory standards effortlessly.
Operational Efficiency: Faster data processing, seamless coordination, and reduced paperwork enhance overall patient care.
Ensuring Data Protection with Healthcare Data Security Solutions in India
Data security remains one of the biggest challenges in the healthcare sector. With cyber threats on the rise, implementing robust healthcare data security solutions in India is non-negotiable. These solutions help in protecting electronic health records (EHRs), preventing unauthorized access, and ensuring that sensitive patient data remains confidential.
Leading healthcare data security solutions in India include:
End-to-End Encryption: Protects patient data during storage and transmission.
Access Control Mechanisms: Ensures only authorized personnel can access sensitive information.
Regular Security Audits: Helps identify vulnerabilities and maintain compliance with regulations.
Streamlining Compliance with Healthcare Regulatory Compliance Software in India
Navigating the complex regulatory landscape in India’s healthcare sector requires specialized tools. Healthcare regulatory compliance software in India helps organizations adhere to industry guidelines such as HIPAA, NABH, and GDPR by automating compliance processes, reducing human error, and ensuring regular reporting.
Features of compliance software include:
Automated Compliance Checks: Reduces risks of violations and penalties.
Audit-Ready Reports: Simplifies regulatory inspections and documentation.
Real-Time Monitoring: Ensures continuous adherence to evolving regulations.
The Future of Healthcare Automation and Compliance in India
As India’s healthcare sector embraces digitalization, the demand for HIPAA compliant workflow automation in India, healthcare data security solutions in India, and healthcare regulatory compliance software in India will continue to grow. By leveraging these technologies, healthcare organizations can enhance efficiency, improve security, and ensure seamless regulatory compliance, ultimately leading to better patient care and trust.
If you’re looking to implement top-tier healthcare automation and security solutions, now is the time to invest in cutting-edge technologies that protect your organization and your patients.
#aviation compliance software in india#audit tracking system#hipaa compliant workflow automation in india#document approval workflows in india#aviation document management system#healthcare data security solutions in india#accounts payable automation in india#healthcare regulatory compliance software in india
0 notes