#Secure Data Storage
Explore tagged Tumblr posts
Text
Explore Timbl Cloud Services for secure data storage, seamless access, and scalable solutions. Empower your business with reliable cloud hosting and advanced technology infrastructure.
#Timbl Cloud Services#Cloud Hosting Solutions#Secure Data Storage#Scalable Cloud Plans#Business Cloud Solutions#Timbl Cloud Technology#Enterprise Cloud Services
0 notes
Text
How to Set Up a Personal Cloud Storage System
In a world dominated by online services and ever-growing data needs, setting up your personal cloud storage system is a game changer. Whether you’re tired of relying on third-party services or simply want more control over your data, a personal cloud storage setup offers the flexibility, security, and scalability you need. Here’s how to set up your own cloud storage system, step by step. 1.…
#home cloud network#personal cloud storage#remote access cloud.#secure cloud setup#secure data storage
0 notes
Text
What Are the Top Security Features to Look for When Choosing a Virtual Tax Filing Service?
In today’s digital age, virtual tax filing services offer a convenient way to handle your taxes. However, with the growing risks of cyber threats, protecting your sensitive financial and personal information is more important than ever. When choosing a virtual tax filing service, security should be at the top of your priority list. Here are the top security features to look for to ensure your data remains safe.

Data Encryption
Encryption is the backbone of secure online platforms. A trustworthy virtual tax filing service should use robust encryption protocols, such as 256-bit SSL (Secure Sockets Layer). This ensures that all information exchanged between you and the platform—like Social Security numbers and bank account details—is protected from unauthorized access.
Multi-Factor Authentication (MFA)
Passwords alone are no longer enough to safeguard accounts. Look for services that offer multi-factor authentication, which requires a second verification step, like a code sent to your phone or email. MFA adds an extra layer of protection, making it harder for hackers to breach your account even if they have your password.
Secure Storage
Your tax information is valuable, so it’s crucial to choose a service that stores your data securely. Check if the platform offers encrypted storage and uses secure servers located in data centers with advanced physical security measures.
Regular Security Audits and Updates
A reliable virtual tax filing service should perform regular security audits to identify and fix vulnerabilities. They should also stay updated with the latest cybersecurity practices, ensuring their platform remains protected against new and emerging threats.
Privacy Policy Transparency
Read the service’s privacy policy to understand how they handle your data. Ensure they don’t share your information with third parties without your consent and comply with regulations like GDPR or CCPA, depending on your location.
Fraud Detection and Alerts
Some platforms include built-in fraud detection systems that monitor for suspicious activity, like unauthorized logins or unusual transactions. Additionally, instant alerts keep you informed of any potential security breaches.
Customer Support and Backup Options
In case of a security issue, responsive customer support is essential. Choose a service that offers immediate assistance and provides options for securely backing up your data.
When selecting a virtual income tax filing service, security should be non-negotiable. By prioritizing features like encryption, MFA, secure storage, and regular updates, you can protect your sensitive information and enjoy the convenience of filing taxes online without worry.
#Virtual Tax Filing Service#Income Tax Filing#Data Encryption#Multi-Factor Authentication#Secure Data Storage#Fraud Detection and Privacy Protection
0 notes
Text
Understanding SecurePath Premium: A Comprehensive Review
Introduction
In a world of increasing cyber threats, businesses and individuals alike are seeking more robust and reliable ways to protect their data and assets. SecurePath Premium is a pioneering cybersecurity solution designed to provide comprehensive protection for businesses and individuals in today’s digital age. In this review, we will take a closer look at SecurePath Premium, its features, benefits, and how it can help you stay safe online.
What is SecurePath Premium?
SecurePath Premium is a leading cybersecurity service that provides comprehensive protection for businesses and individuals. It is designed to offer advanced security measures to keep your sensitive data and assets safe from cyber threats such as malware, ransomware, phishing attacks, and more.
Features of SecurePath Premium
Comprehensive Endpoint Protection
SecurePath Premium offers comprehensive endpoint protection, which means it protects your devices from all angles. This includes real-time threat detection and removal, advanced firewall protection, web filtering, and more. With this feature, you can rest assured that your devices are protected from the latest cyber threats.
Cloud Backup
SecurePath Premium also includes cloud backup, allowing you to securely store your important files and documents in the cloud. This feature ensures that even if your device is compromised, your data is safe and can be easily restored.
Identity Theft Protection
Identity theft is a growing concern, and SecurePath Premium addresses this by offering identity theft protection. This feature helps protect your personal and financial information from unauthorized access and misuse.
Password Manager
SecurePath Premium also includes a password manager, making it easy for you to create and manage strong, unique passwords for all your online accounts. This feature helps protect you from password-related security breaches.
Benefits of SecurePath Premium
Enhanced Security
The most obvious benefit of SecurePath Premium is enhanced security. With its advanced features, SecurePath Premium provides comprehensive protection against a wide range of cyber threats.
Peace of Mind
Knowing that your sensitive data and assets are protected can give you peace of mind. With SecurePath Premium, you can rest assured that your devices and data are safe from cyber threats.
Cost Savings
While the cost of SecurePath Premium may seem high, the benefits it provides can actually save you money in the long run. By preventing data breaches and other cyber incidents, SecurePath Premium can help you avoid costly repairs and downtime.
Conclusion
SecurePath Premium is a pioneering cybersecurity solution that offers comprehensive protection for businesses and individuals. With its advanced features and benefits, it provides enhanced security, peace of mind, and cost savings. If you are looking for a reliable and effective cybersecurity solution, SecurePath Premium is definitely worth considering.
0 notes
Text

#WordPress site deletion#Delete WordPress website#Removing WordPress site#Uninstall WordPress from cPanel#Backup WordPress website#WordPress database deletion#Website platform migration#WordPress site management#cPanel tutorial#WordPress site backup#WordPress website security#Data backup and recovery#Website content management#WordPress maintenance#WordPress database management#Website data protection#Deleting WordPress files#Secure data storage#WordPress site removal process#WordPress website best practices
0 notes
Text
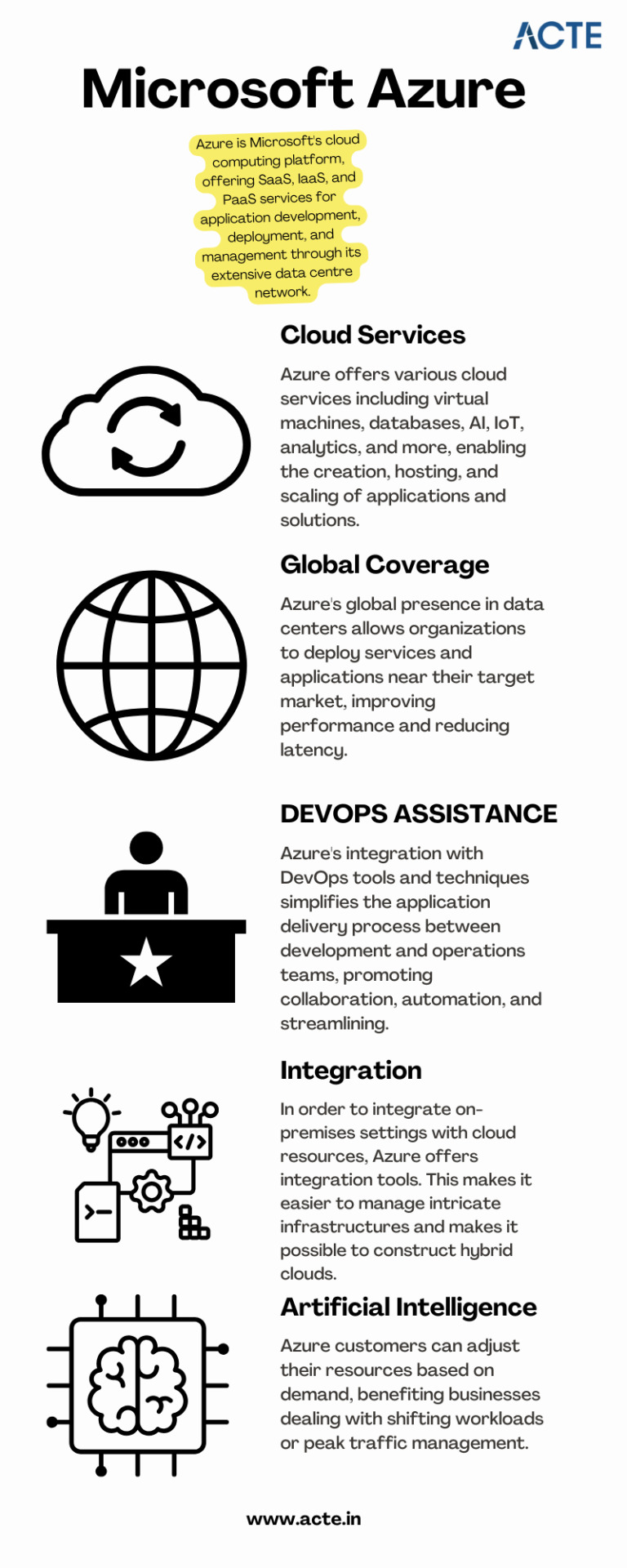
A Complete Guide to Mastering Microsoft Azure for Tech Enthusiasts
With this rapid advancement, businesses around the world are shifting towards cloud computing to enhance their operations and stay ahead of the competition. Microsoft Azure, a powerful cloud computing platform, offers a wide range of services and solutions for various industries. This comprehensive guide aims to provide tech enthusiasts with an in-depth understanding of Microsoft Azure, its features, and how to leverage its capabilities to drive innovation and success.
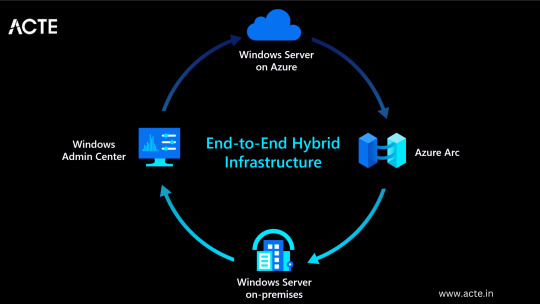
Understanding Microsoft Azure
A platform for cloud computing and service offered through Microsoft is called Azure. It provides reliable and scalable solutions for businesses to build, deploy, and manage applications and services through Microsoft-managed data centers. Azure offers a vast array of services, including virtual machines, storage, databases, networking, and more, enabling businesses to optimize their IT infrastructure and accelerate their digital transformation.
Cloud Computing and its Significance
Cloud computing has revolutionized the IT industry by providing on-demand access to a shared pool of computing resources over the internet. It eliminates the need for businesses to maintain physical hardware and infrastructure, reducing costs and improving scalability. Microsoft Azure embraces cloud computing principles to enable businesses to focus on innovation rather than infrastructure management.
Key Features and Benefits of Microsoft Azure
Scalability: Azure provides the flexibility to scale resources up or down based on workload demands, ensuring optimal performance and cost efficiency.
Vertical Scaling: Increase or decrease the size of resources (e.g., virtual machines) within Azure.
Horizontal Scaling: Expand or reduce the number of instances across Azure services to meet changing workload requirements.
Reliability and Availability: Microsoft Azure ensures high availability through its globally distributed data centers, redundant infrastructure, and automatic failover capabilities.
Service Level Agreements (SLAs): Guarantees high availability, with SLAs covering different services.
Availability Zones: Distributes resources across multiple data centers within a region to ensure fault tolerance.
Security and Compliance: Azure incorporates robust security measures, including encryption, identity and access management, threat detection, and regulatory compliance adherence.
Azure Security Center: Provides centralized security monitoring, threat detection, and compliance management.
Compliance Certifications: Azure complies with various industry-specific security standards and regulations.
Hybrid Capability: Azure seamlessly integrates with on-premises infrastructure, allowing businesses to extend their existing investments and create hybrid cloud environments.
Azure Stack: Enables organizations to build and run Azure services on their premises.
Virtual Network Connectivity: Establish secure connections between on-premises infrastructure and Azure services.
Cost Optimization: Azure provides cost-effective solutions, offering pricing models based on consumption, reserved instances, and cost management tools.
Azure Cost Management: Helps businesses track and optimize their cloud spending, providing insights and recommendations.
Azure Reserved Instances: Allows for significant cost savings by committing to long-term usage of specific Azure services.
Extensive Service Catalog: Azure offers a wide range of services and tools, including app services, AI and machine learning, Internet of Things (IoT), analytics, and more, empowering businesses to innovate and transform digitally.
Learning Path for Microsoft Azure
To master Microsoft Azure, tech enthusiasts can follow a structured learning path that covers the fundamental concepts, hands-on experience, and specialized skills required to work with Azure effectively. I advise looking at the ACTE Institute, which offers a comprehensive Microsoft Azure Course.

Foundational Knowledge
Familiarize yourself with cloud computing concepts, including Infrastructure as a Service (IaaS), Platform as a Service (PaaS), and Software as a Service (SaaS).
Understand the core components of Azure, such as Azure Resource Manager, Azure Virtual Machines, Azure Storage, and Azure Networking.
Explore Azure architecture and the various deployment models available.
Hands-on Experience
Create a free Azure account to access the Azure portal and start experimenting with the platform.
Practice creating and managing virtual machines, storage accounts, and networking resources within the Azure portal.
Deploy sample applications and services using Azure App Services, Azure Functions, and Azure Containers.
Certification and Specializations
Pursue Azure certifications to validate your expertise in Azure technologies. Microsoft offers role-based certifications, including Azure Administrator, Azure Developer, and Azure Solutions Architect.
Gain specialization in specific Azure services or domains, such as Azure AI Engineer, Azure Data Engineer, or Azure Security Engineer. These specializations demonstrate a deeper understanding of specific technologies and scenarios.
Best Practices for Azure Deployment and Management
Deploying and managing resources effectively in Microsoft Azure requires adherence to best practices to ensure optimal performance, security, and cost efficiency. Consider the following guidelines:
Resource Group and Azure Subscription Organization
Organize resources within logical resource groups to manage and govern them efficiently.
Leverage Azure Management Groups to establish hierarchical structures for managing multiple subscriptions.
Security and Compliance Considerations
Implement robust identity and access management mechanisms, such as Azure Active Directory.
Enable encryption at rest and in transit to protect data stored in Azure services.
Regularly monitor and audit Azure resources for security vulnerabilities.
Ensure compliance with industry-specific standards, such as ISO 27001, HIPAA, or GDPR.
Scalability and Performance Optimization
Design applications to take advantage of Azure’s scalability features, such as autoscaling and load balancing.
Leverage Azure CDN (Content Delivery Network) for efficient content delivery and improved performance worldwide.
Optimize resource configurations based on workload patterns and requirements.
Monitoring and Alerting
Utilize Azure Monitor and Azure Log Analytics to gain insights into the performance and health of Azure resources.
Configure alert rules to notify you about critical events or performance thresholds.
Backup and Disaster Recovery
Implement appropriate backup strategies and disaster recovery plans for essential data and applications.
Leverage Azure Site Recovery to replicate and recover workloads in case of outages.
Mastering Microsoft Azure empowers tech enthusiasts to harness the full potential of cloud computing and revolutionize their organizations. By understanding the core concepts, leveraging hands-on practice, and adopting best practices for deployment and management, individuals become equipped to drive innovation, enhance security, and optimize costs in a rapidly evolving digital landscape. Microsoft Azure’s comprehensive service catalog ensures businesses have the tools they need to stay ahead and thrive in the digital era. So, embrace the power of Azure and embark on a journey toward success in the ever-expanding world of information technology.
#microsoft azure#cloud computing#cloud services#data storage#tech#information technology#information security
6 notes
·
View notes
Video
youtube
🔐 Your Data Deserves Better
This Wednesday, we’re diving into the future of data protection with an exclusive presentation on GotBackup — the cloud backup service that secures your files and helps you earn residual income. 💻💰
🌍 100% Online & Free 🗓️ Don’t miss it — spots are limited!
👉 Reserve Your Spot Now
https://bit.ly/42JEDax
#GotBackup #DataProtection #CloudBackup #DigitalSecurity #OnlineBackup #PassiveIncome #WorkFromHome #TechTools #BackupSolutions #SecureYourFiles #ProtectYourData #TumblrEvents #CyberSecurity #CloudStorage
(via 🔒 Why You Can’t Miss This Wednesday’s GotBackup Presentation!)
#GotbackUp#data protection#cloud backup#digital security#Online Backup#passive income#work from home#tech tools#backup solution#secure your files#protect your data#tumblr event#cybersecurity#cloud storage
0 notes
Text
Is Your Data Storage Strategy AI-Ready?
New Post has been published on https://thedigitalinsider.com/is-your-data-storage-strategy-ai-ready/
Is Your Data Storage Strategy AI-Ready?


The adoption of AI has caused an increased need for proper data governance, and companies are now under pressure to ensure data maturity. Globally, many companies are either using or exploring AI, with over 82% actively leveraging or considering AI for business operations. Yet, according to Gartner only 14% of cyber leaders can balance maximizing the efficient use of their data and securing their data to hit business objectives.
As more businesses rush to utilize AI, they need to ensure they are operating at peak data maturity with a proper framework to handle the increasing amount of critical data they are managing. By leveraging a data maturity model framework, organizations can identify the most effective ways to optimize data usage, helping pinpoint gaps in security and foster greater data efficiency. As part of this framework, organizations also need a mature data management strategy.
One of the most overlooked parts of a mature data management strategy is having the proper storage requirements to backup and store critical data. Businesses face many threats when it comes to their data security, and proper storage to handle AI workloads may be the only way to prevent AI-generated data from being lost or tampered with due to ransomware or another disaster. Your business may be AI-capable, but is your storage infrastructure AI-ready?
Why Storage Has to Be Involved in the AI Conversation
There are several reasons why proper storage is essential for data created and consumed by AI— businesses need to ensure data remains easily accessible, is secure against evolving threats, can be recovered in the case of a disaster, and must be optimized for AI workloads.
Accessibility is important because developers must be able to quickly and efficiently find and leverage data to train other AI algorithms. Most of the time this type of data is considered “mission critical” and can be the most valuable to business operations. Having this type of data readily available is key to ensuring streamlined processes when it matters most.
This data also needs to have the highest level of security while it is being stored. Given that 96% of ransomware attacks now target backup data, storage needs to be ransomware-proof and able to withstand any downtime or outage an organization may face. Backups are primary targets for attackers because they render companies unable to restore their data, making it more likely that they will pay the ransom to retrieve critical data. In the meantime, businesses could be left defenseless and face extended periods of IT outages if their “mission-critical” data is not accessible. This could cause both reputational and monetary loss that would be devastating for shareholders, customers, and employees alike.
Cybersecurity attacks are not the only reason storage may be lost or manipulated. Production data, or the data used in a business’s daily operations, should always be treated as though it was destroyed or corrupted. Therefore, a golden recovery copy, or a clean, reliable, and isolated copy of critical data is mandatory. Accidental deletion, overwriting data, or any other kind of mistake caused by human error can compromise your data. Software and hardware failures such as corruption or viruses can also put your data at risk, especially if your software and hardware do not have the most recent updates. Lastly, environmental factors such as power outages, floods, and extreme weather are all good reasons to ensure your backup data can be recovered.
What’s more, AI tools can produce an excessive amount of data at an exponential rate, and traditional storage architectures may not be able to keep up with the amount of data needed to be stored. Therefore, storage for AI must be equipped to handle massive workloads efficiently. Using scalable and secure data storage, such as tiered storage solutions, will present optimal capabilities so data is being monitored and saved.
The Best Storage of AI Data (Without Breaking the Bank)
Tiered backup storage ensures that vital data is quickly accessible and is one of the most cost-effective solutions. It allows for data retention, permitting data to be accessed and reused at any time. Tiered storage and backups organize data based on its importance and frequency of access. High-priority data goes on fast, expensive storage like SSDs, while less critical data is stored on cheaper, slower media like HDDs or cloud storage. Specifically, AI data should be stored on tier 0 or tier 1 given the above requirements. Tier 0 is high-speed storage for mission-critical data with NVMe media types and all-flash storage arrays. Tier 1 is high-performance storage for frequently accessed data with SSDs and hybrid Flash storage media types.
Taking it a step further, backing up the data housed in tiered storage as often as possible will allow for quick access in the face of a disaster, such as human error or malicious alteration. Ensuring copies of backup data stored in multiple locations, with several types of encryptions, and on various media types is the only way to be sure backups are secure.
When choosing a ransomware-proof backup and storage vendor, it is important to ensure you are selecting immutable storage that can withstand any kind of disaster that could put your data at risk. It’s important to note that not all immutable storage delivers on this agreement. If ‘immutable’ data can be overwritten by a backup or storage admin, a vendor, or an attacker, then it is NOT a truly immutable storage solution. Understanding the core concept of true immutability will help separate secure backup systems from empty vendor claims.
These five requirements help define a backup storage environment that delivers immutability:
S3 Object Storage: A fully documented, open standard with native immutability that enables independent penetration testing
Zero Time to Immutability: Backup data must be immutable the moment it is written
Zero Access to Destructive Actions: No administrator—internal or external—should be able to modify, delete, or reset immutable data.
Segmentation of Backup Software and Storage: Backup software and backup storage must be physically isolated to prevent compromised credentials from being used to alter or destroy data, and to provide resilience against other disasters.
Hardware Form Factor: A dedicated appliance isolates immutable storage from virtualized attack surfaces and should remove all risks during setup, updates, and maintenance.
By meeting these requirements, organizations can assure immutability and thereby ensure that whatever happens—ransomware, insider threats, or credential breaches—backup data remains protected and recoverable.
As AI becomes a consistent tool for businesses, they need to adopt and identify better data management and infrastructure to ensure data maturity. The answer to this may lie in tiered storage and backups as the best way to secure the excessive amounts of data created and trained by AI and allow for the ability to quickly access and secure this critical and expansive data.
#Accessibility#admin#adoption#agreement#ai#AI data governance#ai tools#Algorithms#Arrays#attackers#backup#backups#bank#Business#Cloud#cloud storage#Companies#compromise#credential#credentials#cyber#cybersecurity#data#Data Governance#Data Management#data security#data storage#data usage#delete#developers
0 notes
Text
#Backup and Restore Tools#backup strategies#Cloud Storage for MSPs#Data Security#Data Transfer Solutions#managed service providers#MSP backup solutions#Multi-Location Backups#Ransomware Protection#Secure Data Backups
0 notes
Text

Revolutionizing Home Security: Why Cloud Storage Is the Future! Discover how cloud storage is transforming home security, with Arlo leading the charge. Enhanced security, remote access, and advanced features are revolutionizing the industry.
Read more
#cloud storage#home security#Arlo#cybersecurity#World Cloud Security Day#video surveillance#data privacy#remote access#AI security
0 notes
Text
AI से फोटो ट्रांसफॉर्मेशन का क्रेज: Studio Ghibli स्टाइल में मस्ती के साथ प्राइवेसी का खतरा!
Ghibli Style Privacy Threat: आजकल सोशल मीडिया पर एक नया ट्रेंड जोर पकड़ रहा है, जहां लोग अपनी तस्वीरों को AI की मदद से अलग-अलग आर्ट स्टाइल में बदल रहे हैं। इनमें सबसे ज्यादा चर्चा में है Studio Ghibli की एनीमेशन थीम, जो जापानी फिल्ममेकर हायाओ मियाज़ाकी की खूबसूरत और सपनीली दुनिया से प्रेरित है। लेकिन क्या आपने कभी सोचा कि इस मज़े के पीछे आपकी निजता को कितना बड़ा खतरा हो सकता है? आइए, इस ट्रेंड की…
#AI photo transformation#biometric data theft#data storage#Ghibli trend#image generation#machine learning#privacy risks#secure AI tools#Studio Ghibli style#third-party sharing
0 notes
Text
Best Privacy Tools to Anonymize Your Online Activity
In an era where data is the new currency, protecting your privacy online is more important than ever. From tracking your browsing habits to selling your personal information, it feels like everyone wants a piece of your digital footprint. But don’t worry, you can fight back with these top privacy tools designed to help you stay anonymous and keep your online activity secure. 1. Virtual Private…
#DIY cloud storage#home cloud network#personal cloud storage#remote access cloud.#secure data storage
0 notes
Text
Apple cedează presiunilor autorităților britanice: Criptarea end-to-end pentru iCloud, dezactivată în Marea Britanie
Apple a confirmat oficial că renunță la criptarea end-to-end oferită prin sistemul Advanced Data Protection (ADP) pentru utilizatorii iCloud cu conturi nou create în Regatul Unit, urmând ca și utilizatorii existenți să fie afectați de această decizie. Acest pas marchează un compromis semnificativ în politica de confidențialitate a companiei americane, realizat în urma presiunilor exercitate de…
#ADP#Advanced Data Protection#apple#backdoor#bam#cloud storage#Confidențialitate#criptare end-to-end#cybersecurity#data protection#diagnosis#diagnoza#end-to-end encryption#icloud#Marea Britanie#neamt#online security#privacy#Protecția datelor#Regatul Unit#roman#securitate cibernetică#securitate online#UK#United Kingdom
0 notes
Text
Moving is a very important event needing a lot of time, energy, and resources. Choosing the most apt local movers in Dubai is, therefore, essential for a successful and stress-free move. You will want to go for reliable moving services to assist you with everything from packing to transport.
What features should you look for, what to expect and what questions should you ask to ensure you get the best local movers in Dubai? Did you know that 20% of people face issues due to inadequate research on their moving company?
#Local Mover in Dubai#relocation services in Dubai#Packing Services#secure storage services#Khimji Ramdas Relocation Services#Reliable Moving Company in UAE#best movers in Dubai#Dubai relocations#Storage Services#International Moving Services#Fine Arts Shipping Services#Office Moving Services#Data Center Moves#Hospitality Logistics#Employee Relocations Services
0 notes
Text
Advanced Data Security for Businesses by IR Systems
In today’s digital age, business data protection is no longer optional—it’s a necessity. With cyber threats on the rise, companies need robust solutions to safeguard their sensitive information. This is where IR Systems steps in as your ultimate business guardian. Offering cutting-edge technology and secure data storage for businesses.
0 notes
Video
youtube
🌟 Protect Your Data with GotBackup! 🌟
Your files deserve the best care in 2025. With GotBackup, you get: ✅ 6TB of secure cloud storage ✅ 6 accounts for family or business ✅ Global access anytime, anywhere—all for just $9.97/month
🌐 Start your FREE 7-day trial now and experience peace of mind like never before!
👉 https://bit.ly/40uxWdH
Because your data is worth it. 💾✨
#GotBackup #DataSecurity #CloudStorage #SecureFiles #DigitalLife
(via The Essential Guide to Protecting Your Digital Life in 2025)
1 note
·
View note