#Security and Authentication
Explore tagged Tumblr posts
Text
Unlocking the Power of APIs: Becoming an API Intermediate
The world of software development is driven by connectivity and integration. APIs, or Application Programming Interfaces, lie at the heart of this digital ecosystem. They enable different software systems to communicate and share data seamlessly. As you delve deeper into the world of APIs, you’ll embark on a journey from novice to API Intermediate, acquiring a formidable skill set that empowers…

View On WordPress
0 notes
Text
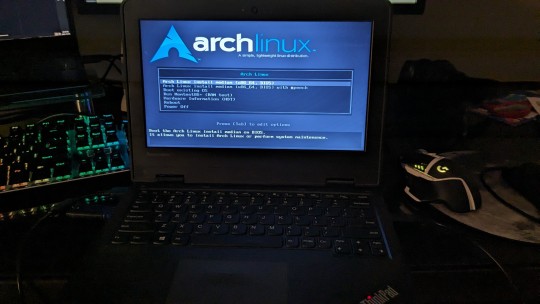
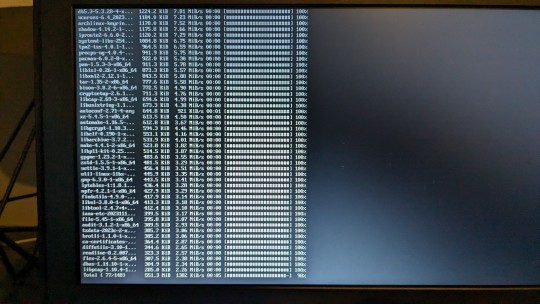
that time i, with zero prior linux experience, managed to install arch on an old-ass laptop and get the wifi to work :3
#linux#arch#I'd do it again on my main pc but I'm in uni so there's programs i need that flat-out won't work on linux#office shit and secure browsers for exams‚ and windows hello authentication#so sad.
59 notes
·
View notes
Text

#memes#meme#lol#funny#lol memes#funny memes#funny meme haha#funny stuff#cybersecurity#cyber security#2fa#mfa#multi factor authentication#riddles#throwback#data security#security#information technology
57 notes
·
View notes
Text
To answer everyone on my inbox and messages, yes I've been hacked. Again. I've changed my passwords. Again.... Really sorry about that
#ive set up the two factor authentication for extra security this time#fucking frustrating#only found out now cuz ive been at work and phones aren't allowed in my job
89 notes
·
View notes
Text
1. How to setup 2FA on your accounts
As some of you may know, my friend @why-its-kai's Discord account was taken over this morning by a scammer.
The scam they used was this one, or close enough; but anyway, the exact specifics don't matter.
What matters is, it can happen to you. It can happen to anyone.
The good news is, you can learn how to protect yourself. Making some small changes can already improve your online security by leaps and bounds.
I made a series of 3 posts covering the basics:
How to setup 2FA on your accounts (you are here!)
How to spot a scam
How to set up a password manager.
Protect yourself with 2FA
Two-factor authentication, or 2FA, isn't a silver bullet -- but it exponentially increases your online safety by adding an extra step to the login process that a hacker/scammer does not have access to.
Every account that you care about (and even those you don't) should have some form of 2FA enabled.
Especially email -- should your email become compromised, this can become a catastrophe.
(For websites that don't support 2FA, use a burner email!)
What 2FA should I use?
2FA can take many forms, from the highly convenient (SMS, email) to the highly secure (security keys), but one thing is certain:
Any form of 2FA is better than nothing.
The simplest forms of 2FA are phone number or email. While these are very easy to use, they are unfortunately not very secure.
Still, I repeat: despite their flaws, these forms of 2FA are absolutely, 100% better than not having any 2FA at all.
On the other end of the spectrum, security keys (like for example a Yubikey) are extremely secure, but they cost money and are a bit of a hassle at time. I use them, but for most people, it's overkill.
What you want is an authenticator app.
Important
A note, before we go on…
If you enable multiple forms of 2FA, how secure your account is will depend on your weakest link.
For example, if you enable SMS authentication AND register a security key, your account will only be as safe as the SMS authentication. The security key is essentially useless.
In other words, the least secure form of 2FA you add determines the overall security of your account.
Sometimes, less is more!
Authenticator Apps
First, choose a free, reputable authenticator. Google Authenticator is a good choice. So are Aegis Authenticator or Microsoft Authenticator.
For simplicity, we'll go with Google Authenticator; the process is rather similar for most authenticators.
First, download the app from your app store and install it on your phone.
Enrolling Gmail into GA
Securing your email should be your number 1 priority, so let's enroll a Google account to Google Authenticator.
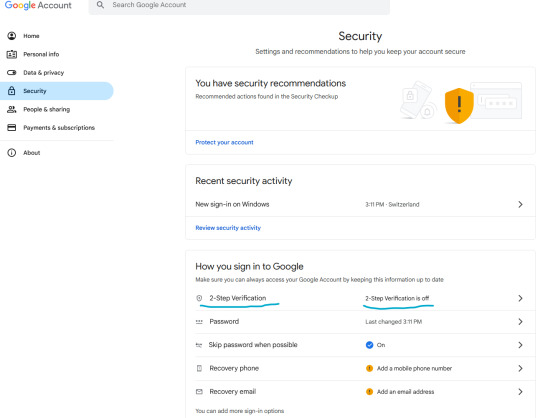
Let's enable two-step verification first.
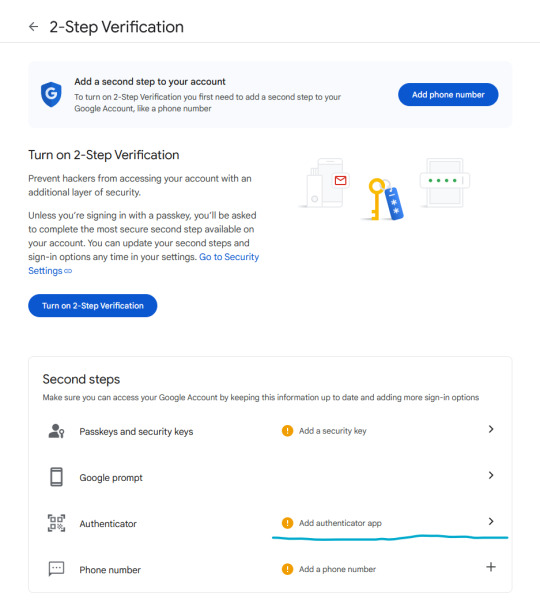
Phone number is better than nothing, but not very safe (SMS verification can be spoofed), so let's click on "Add authenticator app".
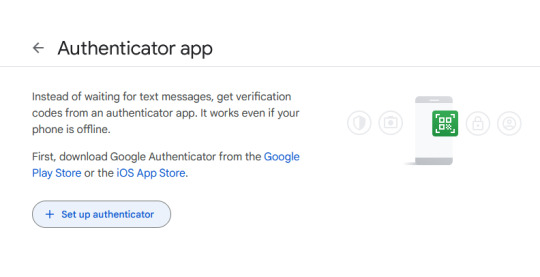
Click on "Set up authenticator". Google will generate a QR-code.
Next, go back to your phone and click on the little multicolored cross. It will bring up a menu; click on "scan a QR code".
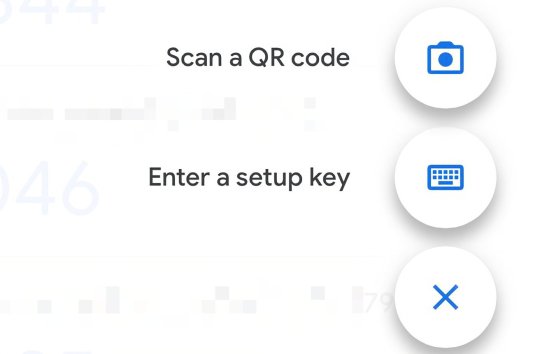
Go ahead and scan the QR code.
Congratulations, you have enrolled your Google account!
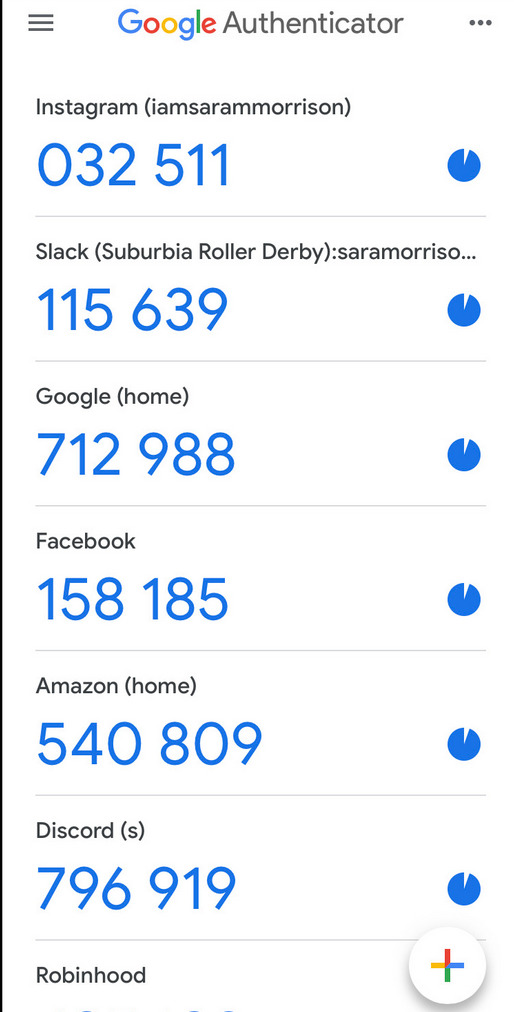
Now, whenever you are asked for a 2FA code, just open the app and copy/paste it.
Note: the codes are stored locally on your phone.
Enabling 2FA on Discord
The process is fairly similar. Go to Settings > My Account:
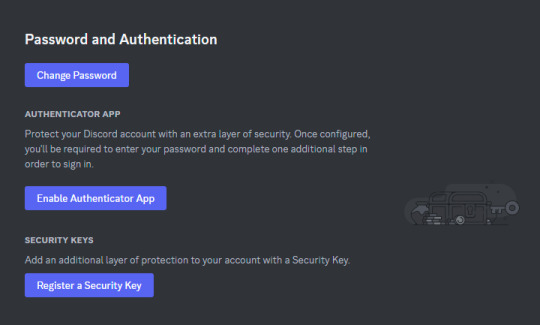
Click on "Enable Authenticator App". You will be prompted for your password. Enter it.
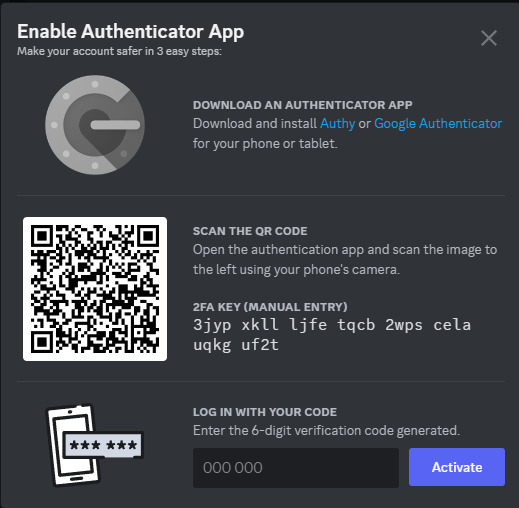
Download Google Authenticator if you haven't already. Scan the QR code as described above.
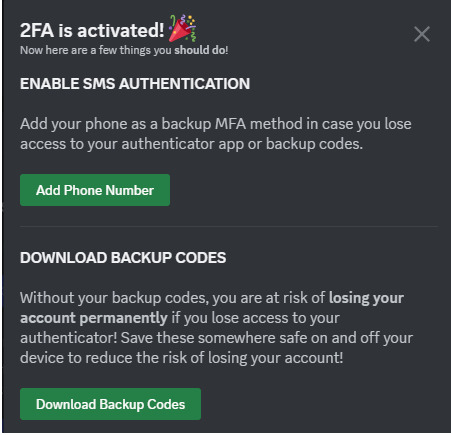
Do take the time to download your backup codes as well!
As explained above, I personally do not recommend setting up SMS authentication here, since authenticator apps are supported, as this weakens the overall security of your account for little benefit.
Stay tuned for parts 2 and 3!
If you have any questions, feel free to PM me.
17 notes
·
View notes
Text
Lilith works very much on the principle of Ask and you shall receive.
Since she doesn't impose her will on anyone because she respects the authentic integrity of each individual (even in the direst of situations), she desires to have each person authentically call for what they want in their life & she will provide it within her capabilities. The breaking of chains comes from the inner roar of your innermost thoughts. Wanting freedom, security and belonging are basic needs that should get met, and that means that you have to forego the nature of the sins themselves. Indulging in what comes easy is the gateway to selling your soul to unsavory individuals. But working hard for what you want, being patient and resilient is what will ultimately take you on a path of discernment.
She, too, has given up on the abundance of Eden for the price of freedom where life challenged her to provide for herself in a different way. Sure, the wilderness outside of the garden was tough, but at least her soul belonged to herself. Her life was hers. Her mistakes, wins and failures were hers too. Lilith belongs to herself first and foremost and that is exactly the type of life she wants her denizens to have.
Her songs always carry a message for hope, freedom and authenticity. Her hope is that the constant repeat of her melodies and hymns will eventually worm their ways into the most broken denizens and tug at their authentic desires to be free of their master, and eventually seek her help.
#ooc : the mortal#This is what I perceive as true empowerment for this interpretation of Lilith#Not in the abundance and you being the best#Like fuck that. That's just an ego stroke#True empowerment comes from feeling authentically secure enough within yourself to create a life you look forward to#Rather than dreading the next day and self soothing by numbing your brain#This is also a reason why I see Lilith being called a 'night specter' aside from her inability to be in the sun#Because she put the basis of shadow work and the dark night of the soul#She is the mother of psychology and seeking your subconscious mind for answers#The black moon Lilith is all about the unseen aspects of oneself in the zodiac and I intend to use that as inspiration
7 notes
·
View notes
Text
.
#I know why there's a real push for two-factor authentication#I get that it's better security#I really do get it#but I also loathe it so so so so intensely#and it honestly only adds insult to injury#when sites require me to enter texted codes in addition to my login information#and they actually have an option!#a nice little check box that says 'don't ask me again on this device'!#so in theory you can just confirm it and you're good to go#except#THEY STILL INSIST ON DOING THE SAME THING EVERY TIME#no matter how many times you click the little box#it means absolutely nothing
5 notes
·
View notes
Text
Convert PuTTY PPK SSH keys to OpenSSH format for seamless use on Ubuntu systems. This step-by-step guide ensures your existing SSH keys work perfectly across different operating systems.
#Convert PPK Key for SSH#cross-platform SSH#key conversion#Linux security#OpenSSH#PPK format#PuTTY#SSH authentication#SSH client#SSH keys#Ubuntu
2 notes
·
View notes
Text

#Gary Zukav#power#authentic power#security#inner security#consciousness#spirituality#spiritual#awareness#psychology#wisdom#The Seat of the Soul#Seat of the Soul
4 notes
·
View notes
Text




POLAND -> banknote look-a-like CERTIFICATE of authenticity of a coin or medal issued by SKARBIEC MENNICY POLSKIEJ. It is added to metal products as below:

>>> with security features as described below:

>>> and samples of the reverse look like this:


with uv light effects / security features like this:


#skarbiec mennicy#Poland#uv light effects#security features#certyfikat#Polonaise#certificate#authenticity#note look-a-like#Polska#Polonia#note#walor
2 notes
·
View notes
Text
Facial Recognition Application - Future of Work
Are you feeling irritated waiting in long lines for check-ins? Don't worry, we are here with an interesting application called Face Recognition. Say goodbye to the stone age. Welcome effortless check-ins with Face Recognition. Upgrade now and step into the future!
👉🌐 https://www.pranathiss.com 👉📧 [email protected] 👉📲 +1 732 333 3037
#futureofwork#SecureCheckIns#security#techinnovation#biometric security#authentication#Digitaltransformation#godigital#Facialrecognitionsoftware#FacialRecognitionTech#Facialrecognitionsystem#fraudprevention#ai security#aiinnovation#advancedsecurity#techrevolution#smartsecurity#FacialRecognitionAI#frauddetection#nextgensecurity#securetech#face recognition#futuretech#EffortlessCheckIns
10 notes
·
View notes
Note
"can benefit from male privilege" but this only applies to trans men who pass as cis and look like men. and yet, somehow, it also DOESN'T apply to trans women who are closeted, haven't realised they're trans, or don't want to transition and look like gender-conforming men..... wut....
this is only confusing to you if you think of trans women as men and trans men as women. try thinking about it again but this time consider that trans men are men and trans women are women.
#1. passing trans men exist and aren't an extreme rarity#2. being closeted and confused is different from feeling secure and authentic in your identity
6 notes
·
View notes
Text
Aadhaar Grievance: Fraudulent Authentication Attempts
Grievance Status for registration number : UIDAI/E/2025/0000070Grievance Concerns ToName Of ComplainantYogi M. P. SinghDate of Receipt02/01/2025Received By Ministry/DepartmentUnique Identification Authority of IndiaGrievance DescriptionUnique Identification Authority of India >> Helpdesk related issues >> Issue related to help desk email Email : [email protected] EID with date and…
#finance#Fraudulent Aadhar authentication attempt#Fraudulent activity#india#news#security#technology#UDAI#Unique identification authority of India
5 notes
·
View notes
Text
So this is the second time my Twitter account’s been stolen/compromised and Twitter support has been absolutely dogshit at getting it back
Has anyone else had this happen before? I don’t wanna be paranoid but the fact that this happened twice in the span of a few months is freaking me out a lil
11 notes
·
View notes
Text
#Tags:Advanced AI Systems#Apple Vision Pro#Biometric Authentication#Biometric Innovations#Civil Liberties and Technology#Consumer Technology#Corporate Control#Data Security Risks#facts#Iris Recognition Technology#life#New World Order#Optic ID#Podcast#Privacy Concerns#serious#straight forward#Surveillance Technology#truth#upfront#Post navigation#Previous
2 notes
·
View notes