#SensitiveData
Explore tagged Tumblr posts
Text

Keeping Sensitive Data Safe in the Age of AI
AI is powerful, but your data security should be stronger. Discover smart ways to keep sensitive information secure in the AI-driven world.
#DataSecurity#AIPrivacy#Cybersecurity#SensitiveData#AIandSecurity#AICompliance#DataProtection#ArtificialIntelligence#TechSafety
0 notes
Video
youtube
You NEED to know this
#youtube#medicaldata#starmer#starmerssecrets#technology#AI#danielthebannister#humanrights#humanrightsabuses#datasharing#NHS#research#sensitivedata#data#survalence
0 notes
Text
Self Encrypting Drives: Securing Sensitive Data With SEDs

Self Encrypting Drives
Data security is crucial in the digital era, and self-encrypting drives (SEDs) are essential. Advanced storage solutions embed encryption into the hardware, securing data from storage to retrieval. This proactive approach decreases the danger of unwanted access, data breaches, and compliance violations, giving institutions handling sensitive data peace of mind.
SEDs
Self encrypting drives automate data encryption without software, making them efficient and safe. Self Encrypting Drives automatically integrate hardware-level encryption into regular operations, unlike standard drives that may require separate encryption software. Offloading encryption processes from the CPU to the HDD simplifies data protection and improves speed.
Self Encrypting Drives basics are crucial as businesses and consumers prioritize data privacy and security. This article discusses self-encrypting disks’ features, benefits, and installation. If you’re new to data security or looking to strengthen your organization’s defenses, understanding SEDs will assist you choose data storage solutions.
Why Use Self-Encrypting Drives?
Cyber threats and sophisticated hacking have increased the need for effective data protection solutions. By embedding encryption into the hardware, self-encrypting SSDs reduce these dangers. Data is encrypted, preventing illegal access and breaches.
Increased Cyberattack Risk
Cyberattacks are becoming more sophisticated and dangerous to organizations and individuals. Malicious actors exploit data storage and transfer weaknesses with ransomware and phishing attacks. By encrypting data as it is written to the drive and limiting access to it to authorized users or applications, Self Encrypting Drives defend against these assaults. Data breaches are strongly prevented by hardware-based encryption. Even if a drive is physically compromised, encrypted data is illegible without authentication.
Trends in Data Protection
To combat new dangers and regulations, data protection evolves. To comply with GDPR, FIPS, and CCPA, organizations across industries are using encryption technologies like Self Encrypting Drives. Trends also favor encryption by default, which encrypts critical data at rest and in transit. This proactive strategy boosts security and stakeholder confidence by committing to protecting critical data from illegal access and breaches.
SED types
SED kinds have diverse characteristics and functions for different use cases and security needs. Drive encryption implementation and management are the main differences.
Self-Encrypting Drives Work How?
Self Encrypting Drives automatically encrypt all drive data using strong cryptographic techniques since they use hardware encryption. No additional software or configuration is needed to encrypt through this transparent technique. Data from the drive is decrypted on the fly if login credentials are provided. These simultaneous encryption and decryption processes safeguard data at rest and in transit, preventing illegal access.
Software and Hardware Self-Encrypting Drives
The two primary types of self-encrypting disks are hardware and software.
Hardware-based SEDs encrypt and decode at hardware speed without affecting system performance by integrating encryption directly into the disk controller. Software-based SEDs use host-system encryption software to manage encryption tasks.
Although both types offer encryption, hardware-based SEDs are chosen for their security and efficiency.
Seagate Exos X Series enterprise hard drives feature Seagate Secure hardware-based encryption, including SEDs, SED-FIPS (using FIPS-approved algorithms), and fast secure erase.
Lock/Unlock Self-Encrypting Drives?
Set up and manage passwords or PINs to lock and unlock a self-encrypting drive. This ensures that only authorized people or systems can access encrypted hard drive data. Most SEDs offer a simple interface or tool to securely initialize, update, or reset authentication credentials. Self Encrypting Drives protect critical data even if the physical drive is taken by using robust authentication.
Seagate Advantage: Safe Data Storage
Seagate leads in safe data storage with their industry-leading self encrypting drives that meet strict industry security standards. The advantages of Seagate SEDs are listed below.
Existing IT Integration
Seagate self-encrypting disks integrate well with IT infrastructures. These drives integrate into varied IT ecosystems without extensive overhauls in enterprise or small business contexts. This integration feature minimizes operational disruption and improves data security using hardware-based encryption.
Using Hardware Encryption
Seagate SEDs encrypt data with hardware. Encrypting the disk controller or drive directly protects against unwanted access and data breaches. Hardware-based encryption optimizes encryption and decryption without compromising system performance.
Compliant with Industry Rules
Trusted Computing Group (TCG) Opal 2.0 data security and privacy requirements apply to Seagate SEDs. These disks encrypt sensitive data at rest to ensure GDPR, HIPAA, and other compliance. This compliance helps firms secure sensitive data and reduce regulatory non-compliance concerns.
Easy Management and Administration
Seagate’s straightforward tools and utilities simplify self-encrypting drive management. IT managers can easily manage encryption keys, access controls, and drive health using these solutions. Seagate SEDs simplify data security operations with user-friendly interfaces and robust administration tools.
Are SEDs Safe?
The drive’s specific hardware automatically encrypts and decrypts any data written to and read from it, making Self Encrypting Drives safe.
An important feature is that encryption and decryption are transparent and do not affect system performance.
SEDs also use passwords or security keys to unlock and access data, improving security.
SED encryption keys are produced and stored on the drive, making them unavailable to software attackers. This design reduces key theft and compromise.
SEDs that meet industry standards like the Opal Storage Specification are interoperable with security management tools and offer additional capabilities like secure erase and data protection compliance. The SED method of protecting sensitive data at rest is effective and robust.
What’s SEDs’ encryption level?
AES with 128-bit or 256-bit keys is used in Self Encrypting Drives. AES encryption is known for its encryption strength and durability. This encryption keeps SED data secure and inaccessible without the encryption key, giving sensitive data handlers piece of mind.
AES-256 encryption, known for its security and efficiency, is used in Seagate Exos X corporate drives. Governments, financial organizations, and businesses employ AES-256 for critical data protection.
Which Encryption Levels Are Available?
SEDs’ encryption levels vary by model and setup. SEDs with several encryption modes, such as S3, let enterprises choose the right security level for their data. Hardware and full disk encryption (FDE) are standard. Hardware components encrypt and decrypt all FDE-encrypted data on the drive.
Backup encrypting drives
Backup SED data to provide data resilience and continuity in case of drive failure or data loss. SED backups use secure backup technologies to encrypt disk data. These encrypted backups protect data while helping enterprises recover data quickly after a disaster or hardware breakdown. Organizations can reduce data breaches and operational disruptions by backing up self-encrypting disks regularly.
Unlocking SED Power
SEDs’ full potential requires understanding and using their main features and capabilities, such as:
To manage and configure encryption settings, use tools offered by the drive manufacturer, such as Seagate Secure Toolkit. These tools usually manage passwords and authentication credentials.
Security Software: Integrate the SED with Opal Storage Specification-compliant security management software. This allows remote management, policy enforcement, and audit logging.
Enable BIOS/UEFI Management: Let your BIOS or UEFI manage the drive’s locking and unlocking. This adds security by requiring the necessary credentials on system boot to access the drive.
To get the latest security updates and bug fixes, upgrade the drive’s firmware regularly. If available, monitor and audit access logs to detect unauthorized drive access.
With these tactics, your SEDs will safeguard data while being easy to use and manage.
Considerations for SED Implementation
To ensure IT infrastructure integration and performance, SED installation must consider various criteria.
Current IT Compatibility
SEDs must be compatible with IT systems before adoption. OS, hardware, and storage integration are compatibility factors. Self Encrypting Drives have broad platform compatibility and low deployment disruption.
Effects on performance and scaling
When implementing SEDs, encryption may affect performance. SED hardware encryption reduces performance decrease compared to software encryption. To ensure SEDs suit current and future data processing needs, organizations should evaluate performance benchmarks and scalability choices.
Total Ownership Cost
Total cost of ownership (TCO) includes initial costs, ongoing maintenance, and possible savings from data security and operational overhead improvements. SEDs may cost more than non-encrypting drives, however increased security and compliance may outweigh this.
Simple Configuration and Maintenance
SEDs simplify configuration and maintenance, making deployment and management easier. IT managers may adjust encryption settings, maintain encryption keys, and monitor drive health from centralized panels. This streamlined solution reduces administrative hassles and standardizes storage infrastructure security.
Read more on Govindhtech.com
#SensitiveData#SEDs#storagesolutions#Datasecurity#SelfEncryptingDrives#datastorage#databreaches#protectdata#news#technews#technology#technologynews#technologytrends#govindhtech
0 notes
Text
Organizations collect data to improve their products and services and support their business. To use this data effectively, it must be shared with internal and external teams for various purposes. However, using this data for non-productive uses can lead to security breaches and compromised sensitive information.
#DataMasking#SensitiveData#PrivacyProtection#DataObfuscation#MaskingTechniques#DataAnonymization#DataSecurity#Compliance#GDPR#Encryption#DynamicDataMasking
0 notes
Video
youtube
Musk Has Access to DATA of Non-US Citizens Around the WorldStop The International DATA BREACH of DOGE! Even citizens of countries around the world outside of the United States are having their data breached by DOGE and do not even know it! Trump, Musk and others are breaching international treaties and privacy agreements. The international community outside of the United States MUST STAND UP TO THIS ILLEGAL ACTIVITY! #taxtreaties #internationalagreements #personaldata #businessdata #sensitivedata #databreach #DOGE #ElonMusk #Tesla #SpaceX #Neurolink #UnitedStates #USGovernment #NationalSecurity #Taxation #Taxinfo #medicalData #fraud #Grok #GrokAI #X #Twitter #DOGETeam #USSenate #UnitedNations #WorldTradeOrganization #News #Machinelearning #AI #AISystems #AIDatasets #datasets #MachineLearningSystems #AITraining #DATASecurity #ArtificialIntelligence #GenerativeAI #Deepseek #MetaAI #BreakingNews #Wired #AssociatedPress #USjudiciary #ICC #NATO #Parliament #Visas #DataTheft #Security #WorldNews #law #lawandorder #TrumpCorruption #TrumpAdministration #SignalBreach #SignalGate #PeteHegseth #Boebert #Intelligence #CSIS #FBI #CIA #RCMP #MarkCarney #JagmeetSingh #MI5 #MI6 #Interpol #Mexico #China #Japan #Australia #Denmark #Spain #Greece #Italy #Sweden #Greenland #USIntelligence #Poland #Europe #EuropeanUnion #Unitedkingdom #KingCharles
0 notes
Text
Samsung Bans Use of Generative AI Tools in the Workplace over Data Leakage Fears

South Korean tech giant Samsung has issued a blanket ban on using generative AI tools like ChatGPT, Google Bard, and Bing AI chatbot for work-related activities. The company fears that using such AI-based platforms could lead to data leakage. According to reports, Samsung discovered that staff uploaded sensitive code to one of these platforms, prompting the ban. The memo issued by the company discusses the risks associated with using these AI-based platforms.
Memo Issued to Employees, Details and Justification
Samsung reportedly notified staff at one of its biggest divisions about the new policy through a memo. The memo stated that the company has been observing an increase in interest in generative AI platforms like ChatGPT and others, both internally and externally. The memo reads, "While this interest focuses on the usefulness and efficiency of these platforms, there are also growing concerns about security risks presented by generative AI." Moreover, the memo even hinted that Samsung engineers accidentally leaked internal source code by uploading it on ChatGPT. Samsung will deploy additional security measures to create a secure environment for the safe use of generative AI to enhance employee productivity and efficiency. However, until these measures are prepared, Samsung has temporarily restricted the use of generative AI.
Reasons for the Ban
A few companies and even nations have started restricting the use of generative AI platforms like ChatGPT, Bing AI, and others, claiming they could harbor sensitive data. Samsung was not one of these companies. The company had allowed its engineers at the semiconductor division to use ChatGPT to help fix problems with source code. However, some employees reportedly entered top-secret data, which may have included source code for a new program and internal meeting notes relating to their hardware, into the platform. Samsung fears that as data accepted by these platforms is stored on external servers, it may end up in the wrong hands. The new rules ban the use of generative AI systems on computers, tablets, and phones, as well as on internal networks that Samsung owns and offers its employees. Samsung products sold to consumers, such as Android smartphones and Windows laptops, aren't restricted from accessing these platforms.
Implications of the Ban
The use of generative AI in the workplace has been on the rise, with employees using it to automate tedious tasks, such as data entry and analysis. Samsung's decision to ban the use of these platforms in the workplace will affect the company's productivity and efficiency, as well as the productivity of its employees. The ban may also prompt other companies to review their policies regarding the use of generative AI in the workplace. Read the full article
#ban#BingAI#ChatGPT#dataleakage#generativeAI#GoogleBard#internalmeetingnotes#memo#Samsung#securitymeasures#semiconductordivision#sensitivedata#servers#top-secret
0 notes
Text
Important Facts about PCI-DSS
You may hear about “PCI Compliance”, “PCI-DSS secured Apps” or "PCI” terms before. But you may not be aware of what PCI-DSS is and how it is important in today's digital world.
So, this article will clear out your gray areas about this topic quickly and easily.
What is PCI-DSS?
Payment Card Industry Data Security or PCI-DSS consists of standards that ensure the safety cardholder data across the world. These policies and procedures are defined in 2004 by the PCI Security Standards Council. They serve the organizations and people who work with cardholder data. Current standard documents can be found on the Councils website.

Who should follow these standards?
✓ Financial Institutions
✓ Merchants
✓ POS Vendors
✓ Hardware and Software Developers
✓ And whoever involving in processing, transferring, and storing cardholder data.
The Basics of PCI Compliance
Many organizations think that compliance is a one-time activity. No, it’s not. PCI Compliance is a continuous process.
Mainly, PCI compliance consists of 12 standards. These will apply to any business that employs in credit/debit card data regardless of the size of the business or location.
Below mentioned data should be protected which includes the following:
✓ Cardholder name
✓ Expiration date
✓ CAV2, CVC2, CVV2, CID (the security digits on the back of credit cards)
✓ Service code
✓ Full magnetic stripe data
✓ PINs
Levels of PCI Compliance

Four levels exist for the standard. These levels are divided based on the annual number of credit/debit card transactions a business processes.
✓ Level1: Merchants who process more than six million VISA transactions per year fall into this category.
✓ Level 2: Merchants who process transactions between 1 to 6 million VISA transactions per year fall into this level.
✓ Level 3: Merchants who process transactions between 20 000 to 1 million VISA e-commerce transactions per year is fall into this level.
✓ Level 4: Applies to merchants processing fewer than 20,000 VISA e-commerce transactions annually, or those that process up to one million real-world transactions
Each level has its requirements that are needed to fulfill by the merchants.
How do I become a PCI-DSS Compliant?
If you want to become a PCI complaint merchant or an organization, you need to follow twelve requirements.
Install and maintain a firewall configuration to protect cardholder data.
Do not use vendor-supplied defaults for system passwords and other security parameters.
Protect stored cardholder data.
Encrypt transmission of cardholder data across open, public networks.
Protect all systems against malware and regularly update anti-virus software or programs.
Develop and maintain secure systems and applications.
Restrict access to cardholder data by business justification.
Identify and authenticate access to system components.
Restrict physical access to cardholder data.
Track and monitor all access to network resources and cardholder data.
Regularly test security systems and processes.
Maintain a policy that addresses information security for all personnel.
Why Security is important?
Everybody needs to know about cardholder data security and it affects and who is in the digital payment industry.
If you are a merchant who accepts digital transactions then you need to ensure that the customers' card details are secured with your payment channels. When you are a payment app developer or financial institution who runs a payment app, then you all should protect customers’ card details when processing, storing and transmitting with other parties.
If the financial institutions or merchants do not follow the secure methods when transacting, customers will complain about the payment channels. When your application is unstable and not securing the customers' card details, then you will lose the credibility you have built through the community. Sometimes your business will fail because of your careless mistakes when joining with payment vendors and other parties involved in customer data handling.
As you know, PCI requirements are not “one-and-done” requirements. You need to maintain your data security every day.
0 notes
Photo

Tokenization is the process of replacing sensitive data with unique identification symbols that retain all the essential information about the data without compromising its security. JISA offers Vault based Tokenization and Vaultless Tokenization. For more details please contact us [email protected] OR CALL ON +919619222553 You can also visit www.jisasoftech.com
0 notes
Text
Keeping Sensitive Data Safe in the Age of AI: What You Need to Know
The rise of artificial intelligence (AI) brings unmatched efficiency, but it also opens the door to new data privacy concerns. Businesses across sectors now process vast amounts of sensitive information—from client documents to employee records—using AI tools. With this shift, data security and compliance have become non-negotiable.
To safeguard your data in an AI-driven environment:
✅ Use encrypted AI platforms: Ensure that any AI software handling data uses encryption protocols. ✅ Limit data exposure: Only share the minimum data necessary for AI processing. ✅ Conduct AI risk assessments: Regularly audit AI systems for privacy gaps. ✅ Stay compliant: Align with global standards like GDPR, HIPAA, or CCPA. ✅ Educate teams: Make cybersecurity awareness a part of your company culture.
Whether you're using AI in immigration software, HR compliance, or business automation, the focus must be on secure and ethical use of technology.
🔗 Discover AI-powered solutions that prioritize privacy
#DataSecurity#AIPrivacy#Cybersecurity#SensitiveData#AIandSecurity#AICompliance#DataProtection#ArtificialIntelligence#TechSafety
0 notes
Video
youtube
Are you one of the 106 million being targeted?
0 notes
Text
Google Cloud Computing Careers in 2024: Trends and Prospects

Cloud Computing Careers
The cloud computing business is predicted to grow rapidly, offering IT experts several Google Cloud Computing Careers opportunities. Despite companies adopting cloud infrastructures, demand for cloud experts is higher than ever. This article highlights 2024’s top cloud computing trends, job openings, and essential skills, certifications, and duties.
Important Developments in Google Cloud Computing Careers
Multi-Cloud/Hybrid Cloud Adoption
Commercial businesses are adopting multi-cloud and hybrid-cloud methods to boost flexibility, decrease risk, and minimize costs. More experts that can manage intricate cloud systems and combine services from many providers are needed as a result of this change.
Pay Attention to Security
Any organisation using cloud services must priorities security due to rising a cyberthreats. Cloud security experts are in demand to protect sensitive data and comply with rules.
The Expansion of Edge Computing
Edge computing is becoming more and more popular. It involves processing data closer to the source rather than in a central data centre. Professionals that install and manage edge computing solutions with proficiency will now have additional responsibilities.
Cloud AI and Machine Learning Growth AI, machine learning, and cloud platforms are changing several industries. For maintaining and creating intelligent apps, cloud experts with ML and AI knowledge are in demand.
Automation together with DevOps
Professionals with infrastructure as code, continuous integration, and continuous deployment skills are in great demand, as automation and DevOps are currently at the heart of every effective cloud operation. Containerization expertise is also in high demand.
Cloud Computing On-Demand Positions
Cloud Solutions Architect
At the request of a single organisation, the cloud solutions architect creates customized cloud solutions while guaranteeing scalability, dependability, and security. Additional prerequisites include proficiency with Google Cloud, Azure, or AWS.
Engineer for Cloud Security
Cloud security experts design safety measures that monitor vulnerabilities and guarantee adherence to industry standards, protecting cloud environments against security breaches.
An engineer for DevOps
With the use of tools like Docker, Kubernetes, and Jenkins for more efficient cloud operations, DevOps engineers close the gap between development and operations teams through process automation, continuous integration, and continuous deployment pipeline management.
Engineer for Cloud Data
Designing, putting into place, and maintaining data processing systems on cloud platforms is the responsibility of cloud data engineers. To ensure prompt data management, they employ ETL, various databases, and big data technologies.
Cloud Engineer AI/ML Cloud Cloud-based machine learning and artificial intelligence models are created and implemented by AI/ML engineers. To create intelligent apps, they make use of technologies like TensorFlow, PyTorch, and cloud-based ML services.
Skills Needed for Google Cloud Computing Careers
Proficiency in Cloud Platforms
Large clouds like Google Cloud, Microsoft Azure, and Amazon Web Services are crucial. The majority of cloud occupations demand knowledge of their best practices, tools, and services.
Security Proficiency
It is essential to understand the fundamentals of cloud security, IAM, encryption, compliance, etc. AWS Certified Security Specialty and Certified Cloud Security Professional (CCSP) certifications are quite beneficial.
DevOps and Automation Expertise
IaC, containerization, scripting, automation tooling, and IaC are highly desirable. To that end, it is recommended to learn about automation tools, Python, Bash, Terraform, Cloud Formation, Docker, and Kubernetes.
Analysis and Management of Data
Big data technology, data processing, and data storage are necessary for Google Cloud Computing Careers like cloud data engineers and cloud AI/ML engineers.
Database knowledge is crucial: SQL versus NoSQL, pipelines for data.
Artificial Intelligence and Machine Learning
Exposure to frameworks and methods for machine learning For the cloud AI/ML function, TensorFlow, PyTorch, together with cloud-based ML services like AWS SageMaker, Google AI Platform, would be quite significant.
Top Cloud Computing Certifications for 2024
Associate in Amazon Certified Solutions Architecture
This certification attests to your proficiency in developing and implementing scalable AWS systems. It works well for architects of cloud systems and professionals in general who want to show off their proficiency with AWS.
Expert in Microsoft Azure Solutions Architecture
Because the candidate will have experience planning and executing on Microsoft Azure, it is especially appropriate for individuals who aspire to become outstanding Azure solution architects.
The Professional Cloud Architect from Google
This certification demonstrates your ability to plan, create, and oversee Google Cloud solutions. For individuals that are passionate about GCP specialization, it’s always the best choice.
Professional with Certification in Cloud Security CCSP The CCSP is derived from (ISC)2 and is primarily concerned with cloud security principles and best practices. This implies that it is intended for experts who want to improve their knowledge of cloud security.
Professional DevOps Engineer Certified by AWS
Your proficiency with automation, monitoring, and CI/CD pipeline management on AWS is validated by this certification. For DevOps engineers working in AWS settings, it’s ideal.
Google Cloud Computing Careers many cloud technology jobs. Here are some significant Google Cloud roles:
Cloud engineers develop, manage, and scale high-performance cloud technology. Priorities are IaC, automation, and orchestration.
Experience with Terraform, Kubernetes, Docker, CI/CD pipelines, Python, Go, Java, and GCP.
Cloud architects offer business-specific, scalable, reliable, and inexpensive cloud solutions.
Coordinate cloud plans with stakeholders
Expertise in cloud services, architecture frameworks, microservices, API administration, and problem-solving. Google Cloud Computing Careers Cloud Architect certifications help.
Cloud Developer Duties: Create and manage cloud-based applications. Integrate front-end and back-end components with cloud APIs. Skills: Python, Java, Node.js, cloud-native development, and Google App Engine, Cloud Functions, and Cloud Storage experience.
Data Engineer Design: Data Engineer Design and implement Google Cloud data processing systems. Input, transform, and store analytics and machine learning data. Skills: Data warehousing, ETL, big data tools (Apache Beam, Dataflow, BigQuery), and SQL, Python, or Java programming.
DevOps Engineer Duties: Manage CI/CD pipelines, automate infrastructure provisioning, and optimize deployment on Google Cloud. Knowledge of DevOps, Kubernetes, Jenkins, GitLab, and cloud monitoring and logging tools.
Cloud Security Engineer: Ensure cloud infrastructure and application security. Implement security best practices, analyse risk, and handle events. Skills: Cloud security frameworks, encryption, IAM, network security, and security tools and technologies.
Site dependability Engineer (SRE) Duties: Ensure cloud service dependability, availability, and performance. Set up monitoring, alerting, and incident response. Skills: System administration, Python, Bash scripting, Prometheus, Grafana monitoring, and large-scale distributed system experience.
Cloud Consultant: Provide advice on cloud strategies, migrations, and implementations. Offer best practices and industry standards experience. Communicate well, comprehend cloud services, manage projects, and understand business needs.
Machine Learning Engineer Duties: Create and deploy machine learning models on Google Cloud. Develop scalable AI solutions with data scientists. Python or R expertise, TensorFlow, PyTorch, and cloud ML tools ( AI Platform, AutoML).
Read more on Govindhtech.com
#cloudcomputing#GoogleCloudComputingCareers#cyberthreats#EdgeComputing#cloudsecurity#SensitiveData#edgecomputingsolutions#machinelearning#cloudplatforms#Azure#CloudData#datamanagement#AIML#artificialintelligence#MicrosoftAzure#amazonwebservices#datastorage#devopsengineers#monitoring#DataWarehousing#dataflows#BigQuery#Python#SQL#gitlab#news#TechNews#technology#technologynews#technologytrends
1 note
·
View note
Text
Fortifying Data Masking: Strategies for Protecting Sensitive Information and Ensuring Compliance in Today's Digital Landscape
In today's data-driven world, organizations harness data to refine their offerings, enhance customer experiences, and fortify their operations. However, the strategic utilization of Data Masking its dissemination among internal and external stakeholders. While this sharing is crucial for fostering innovation and collaboration, it also introduces risks of security breaches and compromises to sensitive information. Consequently, safeguarding data integrity has become paramount in contemporary data environments.
To mitigate the peril of data breaches and uphold regulatory compliance, such as GDPR, PCI-DSS, and HIPAA, organizations must adopt robust security protocols. These measures are indispensable for curtailing the exposure of sensitive data throughout its lifecycle. By implementing stringent security practices, enterprises can fortify their defenses and uphold the trust of their customers and partners.
In adhering to security and compliance imperatives, organizations deploy a multifaceted approach encompassing various phases of their operational cycle. From data acquisition to storage, processing, and transmission, each stage demands tailored security measures to mitigate vulnerabilities and thwart potential threats. By integrating security seamlessly into their workflows, organizations can engender a culture of vigilance and resilience against evolving cybersecurity challenges.
Central to data masking is the concept of least privilege, whereby access to sensitive information is restricted only to authorized personnel and systems. By limiting access based on roles and responsibilities, organizations minimize the risk of unauthorized data exposure and inadvertent leaks. Moreover, encryption techniques are instrumental in safeguarding data integrity during transit and storage, rendering it indecipherable to unauthorized entities.
Furthermore, organizations invest in robust authentication and authorization mechanisms to validate the identity of users and govern their access privileges. Multi-factor authentication, biometric verification, and access controls are pivotal in fortifying defenses against unauthorized access attempts. Similarly, audit trails and logging mechanisms enable organizations to monitor and trace user activities, facilitating timely detection and mitigation of security incidents.
In parallel, organizations leverage advanced technologies such as artificial intelligence and machine learning to augment their threat detection capabilities. By analyzing vast troves of data in real-time, these systems can discern anomalous patterns indicative of potential security breaches. This proactive approach empowers organizations to preemptively thwart threats before they escalate into full-fledged breaches.
Moreover, robust incident response plans are indispensable for orchestrating swift and coordinated responses to security incidents. By delineating roles, responsibilities, and escalation procedures, organizations can minimize the impact of breaches and expedite recovery efforts. Regular drills and simulations enable teams to refine their response strategies and bolster their preparedness for emergent cyber threats.
Beyond technological fortifications, fostering a culture of security awareness is imperative for cultivating a vigilant workforce. Comprehensive training programs equip employees with the knowledge and skills to identify and mitigate security risks in their daily activities. By instilling a sense of collective responsibility, organizations empower their employees to serve as frontline defenders against cyber threats.
In conclusion, safeguarding sensitive data is an ongoing imperative for organizations navigating the complexities of today's Data Masking. By embracing a holistic approach to data security, encompassing technological, procedural, and cultural dimensions, enterprises can fortify their defenses and uphold the trust of their stakeholders. In a landscape fraught with evolving cyber threats, proactive measures are indispensable for preserving data integrity and fostering sustainable business growth.
#DataMasking#SensitiveData#PrivacyProtection#DataObfuscation#MaskingTechniques#DataAnonymization#DataSecurity#Compliance#GDPR#Encryption#DynamicDataMasking
0 notes
Link
If you have sensitive information that should never be access by anyone but yourself, try not to store it in the cloud – use an external hard drive instead. Keep this hard drive in a secure place in your house, like your safe or a fire proof box. Whilst cloud storage is very secure, if someone guesses your password; access my be compromised.

0 notes
Link
Office computers sometimes contain sensitive data that could be imperative to the company’s operations. But if in the wrong hands, it can prove harmful to the company’s reputation and financial standing. All this happens because sometimes employees get relaxed with their computer’s security.

#computer#security#data#sensitivedata#companyoperations#financialstanding#employees#company#operation#itsupport#computersecurity
0 notes
Photo
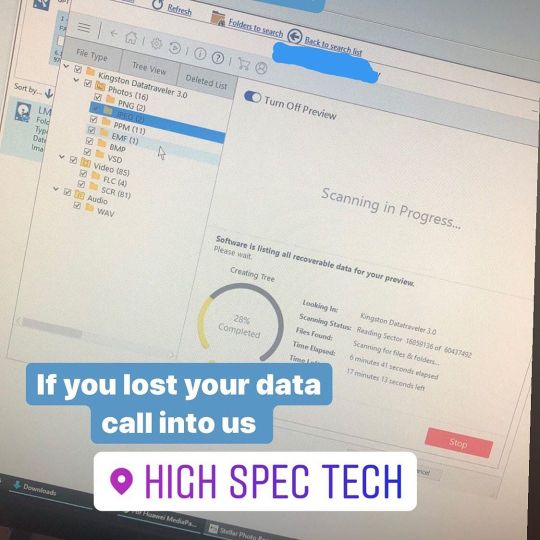
💾DATA RECOVERY💾 Today a very worried customer came into us after FORMATTING their USB key by accident thinking they were formatting another USB- the key contained very important photographs that meant a lot to them. After running this USB through our data recovery software we managed to recover all of their photographs, even photos and files that they previously deleted over time were recovered. If you find yourself in this unfortunate position, deleted or formatted your hard drive on your computer or Mac or even your your usb stick or SD card, we can help. Data and file recovery 🗂 Pictures and video recovery 📷 #datarecovery #datarecoveryservices #datarecoveryservice #recoverydata #recovermydata #datarecoveryspecialist #sensitivedata #dataprivacy #recoverydata #hddrecovery #sadrecover #ssdrecovery #usbrecovery #sdcardrecovery #filerecovery #macdatarecovery #desktopdatarecovery #laptopdatarecovery (at High Spec Tech) https://www.instagram.com/p/B7t6xZlnzl4/?igshid=njyh2z4zy8ku
#datarecovery#datarecoveryservices#datarecoveryservice#recoverydata#recovermydata#datarecoveryspecialist#sensitivedata#dataprivacy#hddrecovery#sadrecover#ssdrecovery#usbrecovery#sdcardrecovery#filerecovery#macdatarecovery#desktopdatarecovery#laptopdatarecovery
0 notes
Text
Degaussing in Westworld?
Prior to this course, Principles of Information Assurance, I never even thought of how data could be safely deleted. I assumed every time I erase the data on my hard-drive to reset my PC for better performance that the data on it was completely erased forever!
This took me on a research journey on the topic, from watching YouTube videos of a guy degaussing his old crt monitor (80s retro computers). That in fact old crt tv monitors would become extremely effected by anything that emitted electricity, even a nearby lightening bolt hit would cause the monitor screen to scatter.
https://www.youtube.com/watch?v=qEEaZ1GGl9I Here’s a link to the degaussing of the crt monitor if you’re interested!
On my continued research path, I looked into the differences between wiping vs degaussing vs shredding. I recently built my own desktop PC, which helped me under my laptop a little bit better when it came to the motherboard and ssd vs hard drives that I installed. When my SurfaceBook 2 started getting a little glitchy, I decide to do a clean install on it. The performance is just like it was out of the box. Don’t get rid of your old computers just yet! At least not with PC rigs, because they never die really you just replace the parts inside over time.
Finally, in reference to my title and why ensuring a machine has been degaussed properly. Software claiming to wipe a drive is not always a guarantee. Due to GLB-Act & HIPPA regulations, NSA requires that sensitive data has the ability to be completely unrecoverable. If not degaussed properly, your data can still be restored from a partially corrupted drive. It can be repaired so to speak and remounted onto the drive. Additionally, something I didn’t know before researching is that USB drives cannot be degaussed due to their data storage being based on a solid-state drive. Never knew why there was a difference, having both a HD & SSD installed on my PC rig, now I really know why one is quicker than the other.
If you don’t understand my Westworld reference in the title, read this explanation:
Westworld, an HBO show deals with AI being put into this simulation park that its clients pay big money to participate in. Clients can live out their wildest fantasies, kind of like when you’re playing videogames in Red Dead Redemption and be a cowboy. Well, they put in these NPCs characters, real modern AI robots that every time are either killed by a client or client’s actions, they wipe their memory and respawn them back into this simulation world. Some memory wipes aren’t successful and certain AI protagonists have PTSD and rebel. Great show if you haven’t seen it.
All in all, remember to degauss your data storage devices so people can’t access your sensitive data and/or so your computer doesn’t become self-aware and rebel against you.
CITATIONS
What is degaussing & how does it work? (2013, March 1). DataKillers. Retrieved June 17, 2021, from https://datakillers.com/what-is-degaussing-and-how-does-it-work/
Wiping vs degaussing vs shredding - what's the difference? (2019, February 18). ERI Direct. Retrieved June 17, 2021, from https://eridirect.com/blog/2019/02/wiping-vs-degaussing-vs-shredding-whats-the-difference/
#westworld#ai#degaussing#wiping#sensitivedata#databreach#datastorage#pc#pcbuild#ssd#harddriverecovery#magneticfield#red dead redemption 2#erase#robots#cybersecurity#darkweb#usb#irobot#data#erase all data#hippa
0 notes