#Transfer Fundamentals
Explore tagged Tumblr posts
Text
Been mulling over the idea of cisgirl!Sam&Dean, and my opinion is any attempt at critically examining and exploring how gender would affect them and their dynamic through fanwork wouldn’t work unless John was also a ciswoman
#i’ve been wondering for a while why cisgirl au doesn’t really hit with me (despite enjoying some interpretations)#and i think this is why—john tends to be still be male#which i think places him in an odd role#when i think much if sam and dean’s gender#when i think much of how gender works for sam and dean is related to john#i think i mainly see two types of aus; 1) where sam and dean#are transferred with the same characterisation and aesthetics but without further inspection on how context-specific their characters are#and 2) trying to critically examine how gender would affect them but altering fundamental characteristics to the point they really aren’t#those characters#i mean it’s literally fine i have engaged with both of those before in fanwork#and i don’t think like. it’s possible to have a perfect interpretation. like this is all for fun#i do agree with alius though that transgender readings are more interesting to consider
8 notes
·
View notes
Note
The je Sci fi au always gets me. Fellas is it gay to intimately repair your boss and they make satisifed little noises that you try very very hard not to think about what they remind you of. I am sexualizing the machine today. Jon handling all of the most fragile pieces of elias..hnghg
-skiesandcandy
Oh yes.
Jon trying so hard to keep plausible deniability, no he’s just doing his job. Look it means nothing that he’s the only one the computer allows to crawl amongst their wires. All computers make those noises, he is very professional thank you very much.
Yeah no one buys this, and honestly the fatality rate has gonna way down now that the slightly murderous ship AI seems to be distracted. So everyone just turns a blind eye to anything going on.
Jon secretly, okay not secretly at all everyone can tell, loving Elias’s attention, the cameras all turning to follow him. Jon constantly talking to him, confessing all his secrets, and his insecurities, look maybe a machine is the only one who actually understands him.
Jon touching himself in his bunk carefully in view of Elias’s mechanical eyes. He’s so embarrassed but Elias telling him it’s only fair. After all Jon gets to handle his delicate circuitry, and while he can’t physically touch Jon he can guide him verbally. Jon squirming as Elias calls him a good boy, so precious to him, how he almost wishes he still had a body just so he could take Jon apart properly. Jon comes harder than he ever has before at the thought.
#yes we are sexualizing the machine#it’s fine the AI hasn’t murdered anyone in almost a month#everyone on the ship just being like I do not see#that’s a record#Sure it keeps overheating at times but Jon fixes it#God I am never normal about them#Elias secretly working on a body to transfer Jon to#because he can’t lose him#Elias forcing Jon into an amalgamation of human and machine#look is it really JE of Jon isn’t fundamentally changed by Elias?#No he does not ask if Jon wants this of course he does#Jon is his#JE#i’m normal im so normal#answered asks
6 notes
·
View notes
Text
Today I went through my "grown up folders" to clear out junk mail / old bills / mortage and tax stuff for the previous house / etc and I had a pretty big pile of confidential esque papers, so I gathered them up and was like, "I'm gonna burn these, I don't really want to just throw them away. Is that insane?"
And my brother said, "No. [Maternal uncle] shoots his old phone when he gets a new one, I think burning your paper is a perfectly logical thing to do."
BRO HE WHAT 😭😭😭
HE OLD YELLERS HIS PHONE
#my shit: personal#he puts a BULLET HOLE#IN HIS PHONE#i know hes a paranoid conspiracy theorists but oh my goddddd#the fundamental misunderstanding of how the phone even works#babe how do you think the info is transferring from the new phone to the old one#you don't even block ads or turn off your location#somehow i am related to this man by blood
4 notes
·
View notes
Note
*taps your shoulder*
*pecks your lips with a kiss when you turn around*
*flee and run into a pole*

LETS FUCKING GOOOOOOOOOOOOO
#YEAAAAAAHHHHHHHHHH GET SMOOCHIED IDIOT /POS /LOVING 🩷🩷🩷🩷🩷🩷🩷🩷🩷🩷🩷🩷🩷🩷🩷🩷🩷🩷🩷🩷🩷🩷🩷🩷🩷#also quick unrelated anecdote#i havent ridden a bike in a long ass time. and they say you never forget how to ride one#however. about 6 years ago i got a bike for the first time since i was like 10 or so#and i managed to ride it like 30 meters before i ran into a tree#so you don't forget how to ride a bike. unless youre fundamentally a Dumb Bitch at heart 🩷#elkkie lore of the day godbless america or smth#sorry i have had far too mucb tequila tonight and i am nowhere near done loooool#thank u for the smooches beloved. i put on my cute shimnery lip gloss for you (as to transfer the sparkles to you!!! :3)#askkiel#klausinamarink.ask#im so fucking proud i was abke tk type that lool oofie
4 notes
·
View notes
Text
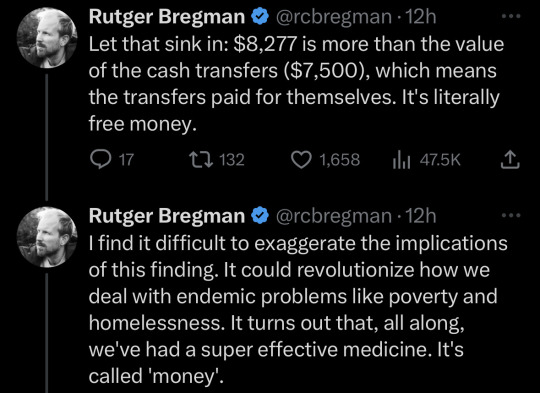
Unfortunately it's really easy to exaggerate the implications of the finding. I went down a pretty massive rabbit hole reading the study being referenced here (“Unconditional cash transfers reduce homelessness” (Ryan Dwyer, Anita Palepu, Claire Williams, and Jiaying Zhao 2023)). and looking at where the numbers came from, and that $8277 per person cost savings shows up in the discussion of the results but directly contradicts the findings. When they directly estimated the cost of services provided to the people in the study by counting the days the people used those services, they found a savings of around $2400 per person over the year - meaning with the $7500 lump sum payment, it was $5100 more expensive to give people a lump sum rather than $777 cheaper.
So where did the $8277 value come from? Why was it brought up in discussion? As far as I can tell, it comes from
Saying the participants who received cash spent 89 fewer days homeless and assuming, contrary to what they measured, that ALL days homeless were spent in shelters (as opposed to on the streets, in cars, couch surfing)
Assuming a cost of $94 per night for shelter
... based on a different study
... which had ranges of $14 to $144 per night for different kinds of housing
... which includes the MARKET VALUE PRICE OF THE BUILDING AMORTIZED AS A CAPITAL EXPENSE
which you would find if you dug through that study's appendix.
And if you pick that value you see a "cost savings", even though you measured a loss in the work at hand.
Now, this study has some other major problems, but that one seems glaring. Come on. You calculated the cost based on the actual number of days spent in the shelter, found that it was only $2400ish lower, and then made a worse estimate based on other people's approximations and intentionally misrepresented how long people spent in the shelters?
Here's their actual data.
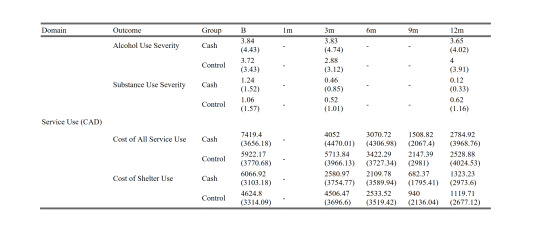
Values without parentheses are means, values in parens are standard deviations. "B" is the baseline survey and it covers the 12 month period before the study. Each 3-month survey captures 3 months' worth of spending. You can see that neither the cash nor control group used more than $7500 worth of housing in the prior year. Here's my little table showing the sums, for convenience:
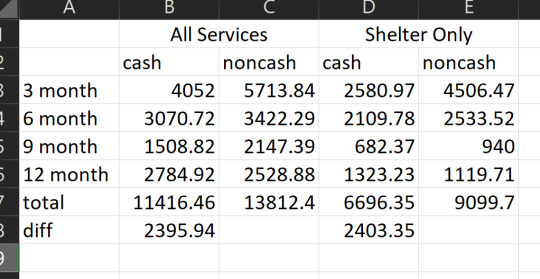
so. their own data really seem to contradict the conclusion they draw by estimating with other people's approximations.
anyway. there are a dozen other glaring issues but I think the main point is well-summarized by figures they left in the appendix. These figures show the standardized outcomes for a bunch of things they measured at the 1, 3, 6, 9, and 12-month surveys:
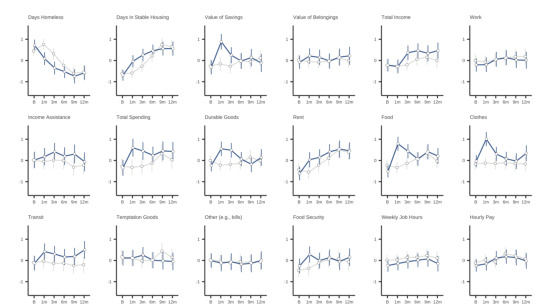

Blue lines got cash, grey lines didn't.
By the end of the study period - really, after the first three months - there was virtually no difference on any metric between the cash and non-cash groups. None.
This study was pre-registered. It stated its hypotheses ahead of time as well as the way it was going to do its power analysis, and
EVERY SINGLE HYPOTHESIS IT PREREGISTERED FAILED. Not significant.
Even in the exploratory findings, they found short-term benefits but "The cash transfer did not have overall impacts on employment, cognitive function, subjective well-being, alcohol use severity, education, or food security."
Like, yes! Giving people money increased the time they spent in stable housing by about 55 days over the year. That's valuable! That's good! But it didn't have any meaningful effect on whether they ended the year in stable housing, or whether they got a job, or even the value of their savings.
There's a whole nother rabbit hole, which I'll spare you, about the sampling bias they have here (only people 19-65 years old, homeless LESS THAN 2 YEARS, citizen or permanent resident, with nonsevere levels of substance use, alcohol use, and mental health symptoms, which excluded 69% of the shelter population) (and who agreed to participate, and stuck with the study - down to just 35 people in the sample group, <5% of the shelter population) - and two more rabbit holes about their "people don't want to give homeless people cash transfers because they think they'll spend it on drugs" studies. The news story screenshotted in the tweet kinda misrepresents that aspect too - if you explicitly exclude people with substance use and alcohol use issues from your study, the people you study don't spend money on drugs and alcohol! and water is wet. But that's a post for another day.
but in short:
the program did not save money. and the study sucks.
**** for the record! I think that society should absolutely ensure housing for everyone, especially the people with highest support needs. that's the point of society! and in general I think cash transfers can be far more effective at getting people fed and housed for many of the same reasons the study authors do. I really, really wanted this study to hold water because it would be a great piece of evidence in favor of faster and easier and cheaper ways to house people. But because I wanted it to be true so badly, I knew I ought to give it extra scrutiny. which I think was solidly warranted. ****
Source

Source
#sorry for coming onto your reblog and spilling trash everywhere#it's#I got curious about the study and was not pleased with what I found when I looked closer#fact checking#long post#for the record i believe in the value of cash transfers and donate money for cash transfers in poorer countries.#and i think housing and shelter are fundamental human rights#and like the function of a society is in large part to care for the people least able to care for themselves#and sobriety shouldn't be a prerequisite for housing and people with substance use problems should have safe and comfortable housing
55K notes
·
View notes
Text
Master CUDA: For Machine Learning Engineers
New Post has been published on https://thedigitalinsider.com/master-cuda-for-machine-learning-engineers/
Master CUDA: For Machine Learning Engineers
CUDA for Machine Learning: Practical Applications
Structure of a CUDA C/C++ application, where the host (CPU) code manages the execution of parallel code on the device (GPU).
Now that we’ve covered the basics, let’s explore how CUDA can be applied to common machine learning tasks.
Matrix Multiplication
Matrix multiplication is a fundamental operation in many machine learning algorithms, particularly in neural networks. CUDA can significantly accelerate this operation. Here’s a simple implementation:
__global__ void matrixMulKernel(float *A, float *B, float *C, int N) int row = blockIdx.y * blockDim.y + threadIdx.y; int col = blockIdx.x * blockDim.x + threadIdx.x; float sum = 0.0f; if (row < N && col < N) for (int i = 0; i < N; i++) sum += A[row * N + i] * B[i * N + col]; C[row * N + col] = sum; // Host function to set up and launch the kernel void matrixMul(float *A, float *B, float *C, int N) dim3 threadsPerBlock(16, 16); dim3 numBlocks((N + threadsPerBlock.x - 1) / threadsPerBlock.x, (N + threadsPerBlock.y - 1) / threadsPerBlock.y); matrixMulKernelnumBlocks, threadsPerBlock(A, B, C, N);
This implementation divides the output matrix into blocks, with each thread computing one element of the result. While this basic version is already faster than a CPU implementation for large matrices, there’s room for optimization using shared memory and other techniques.
Convolution Operations
Convolutional Neural Networks (CNNs) rely heavily on convolution operations. CUDA can dramatically speed up these computations. Here’s a simplified 2D convolution kernel:
__global__ void convolution2DKernel(float *input, float *kernel, float *output, int inputWidth, int inputHeight, int kernelWidth, int kernelHeight) int x = blockIdx.x * blockDim.x + threadIdx.x; int y = blockIdx.y * blockDim.y + threadIdx.y; if (x < inputWidth && y < inputHeight) float sum = 0.0f; for (int ky = 0; ky < kernelHeight; ky++) for (int kx = 0; kx < kernelWidth; kx++) int inputX = x + kx - kernelWidth / 2; int inputY = y + ky - kernelHeight / 2; if (inputX >= 0 && inputX < inputWidth && inputY >= 0 && inputY < inputHeight) sum += input[inputY * inputWidth + inputX] * kernel[ky * kernelWidth + kx]; output[y * inputWidth + x] = sum;
This kernel performs a 2D convolution, with each thread computing one output pixel. In practice, more sophisticated implementations would use shared memory to reduce global memory accesses and optimize for various kernel sizes.
Stochastic Gradient Descent (SGD)
SGD is a cornerstone optimization algorithm in machine learning. CUDA can parallelize the computation of gradients across multiple data points. Here’s a simplified example for linear regression:
__global__ void sgdKernel(float *X, float *y, float *weights, float learningRate, int n, int d) int i = blockIdx.x * blockDim.x + threadIdx.x; if (i < n) float prediction = 0.0f; for (int j = 0; j < d; j++) prediction += X[i * d + j] * weights[j]; float error = prediction - y[i]; for (int j = 0; j < d; j++) atomicAdd(&weights[j], -learningRate * error * X[i * d + j]); void sgd(float *X, float *y, float *weights, float learningRate, int n, int d, int iterations) int threadsPerBlock = 256; int numBlocks = (n + threadsPerBlock - 1) / threadsPerBlock; for (int iter = 0; iter < iterations; iter++) sgdKernel<<<numBlocks, threadsPerBlock>>>(X, y, weights, learningRate, n, d);
This implementation updates the weights in parallel for each data point. The atomicAdd function is used to handle concurrent updates to the weights safely.
Optimizing CUDA for Machine Learning
While the above examples demonstrate the basics of using CUDA for machine learning tasks, there are several optimization techniques that can further enhance performance:
Coalesced Memory Access
GPUs achieve peak performance when threads in a warp access contiguous memory locations. Ensure your data structures and access patterns promote coalesced memory access.
Shared Memory Usage
Shared memory is much faster than global memory. Use it to cache frequently accessed data within a thread block.
Understanding the memory hierarchy with CUDA
This diagram illustrates the architecture of a multi-processor system with shared memory. Each processor has its own cache, allowing for fast access to frequently used data. The processors communicate via a shared bus, which connects them to a larger shared memory space.
For example, in matrix multiplication:
__global__ void matrixMulSharedKernel(float *A, float *B, float *C, int N) __shared__ float sharedA[TILE_SIZE][TILE_SIZE]; __shared__ float sharedB[TILE_SIZE][TILE_SIZE]; int bx = blockIdx.x; int by = blockIdx.y; int tx = threadIdx.x; int ty = threadIdx.y; int row = by * TILE_SIZE + ty; int col = bx * TILE_SIZE + tx; float sum = 0.0f; for (int tile = 0; tile < (N + TILE_SIZE - 1) / TILE_SIZE; tile++) if (row < N && tile * TILE_SIZE + tx < N) sharedA[ty][tx] = A[row * N + tile * TILE_SIZE + tx]; else sharedA[ty][tx] = 0.0f; if (col < N && tile * TILE_SIZE + ty < N) sharedB[ty][tx] = B[(tile * TILE_SIZE + ty) * N + col]; else sharedB[ty][tx] = 0.0f; __syncthreads(); for (int k = 0; k < TILE_SIZE; k++) sum += sharedA[ty][k] * sharedB[k][tx]; __syncthreads(); if (row < N && col < N) C[row * N + col] = sum;
This optimized version uses shared memory to reduce global memory accesses, significantly improving performance for large matrices.
Asynchronous Operations
CUDA supports asynchronous operations, allowing you to overlap computation with data transfer. This is particularly useful in machine learning pipelines where you can prepare the next batch of data while the current batch is being processed.
cudaStream_t stream1, stream2; cudaStreamCreate(&stream1); cudaStreamCreate(&stream2); // Asynchronous memory transfers and kernel launches cudaMemcpyAsync(d_data1, h_data1, size, cudaMemcpyHostToDevice, stream1); myKernel<<<grid, block, 0, stream1>>>(d_data1, ...); cudaMemcpyAsync(d_data2, h_data2, size, cudaMemcpyHostToDevice, stream2); myKernel<<<grid, block, 0, stream2>>>(d_data2, ...); cudaStreamSynchronize(stream1); cudaStreamSynchronize(stream2);
Tensor Cores
For machine learning workloads, NVIDIA’s Tensor Cores (available in newer GPU architectures) can provide significant speedups for matrix multiply and convolution operations. Libraries like cuDNN and cuBLAS automatically leverage Tensor Cores when available.
Challenges and Considerations
While CUDA offers tremendous benefits for machine learning, it’s important to be aware of potential challenges:
Memory Management: GPU memory is limited compared to system memory. Efficient memory management is crucial, especially when working with large datasets or models.
Data Transfer Overhead: Transferring data between CPU and GPU can be a bottleneck. Minimize transfers and use asynchronous operations when possible.
Precision: GPUs traditionally excel at single-precision (FP32) computations. While support for double-precision (FP64) has improved, it’s often slower. Many machine learning tasks can work well with lower precision (e.g., FP16), which modern GPUs handle very efficiently.
Code Complexity: Writing efficient CUDA code can be more complex than CPU code. Leveraging libraries like cuDNN, cuBLAS, and frameworks like TensorFlow or PyTorch can help abstract away some of this complexity.
As machine learning models grow in size and complexity, a single GPU may no longer be sufficient to handle the workload. CUDA makes it possible to scale your application across multiple GPUs, either within a single node or across a cluster.
CUDA Programming Structure
To effectively utilize CUDA, it’s essential to understand its programming structure, which involves writing kernels (functions that run on the GPU) and managing memory between the host (CPU) and device (GPU).
Host vs. Device Memory
In CUDA, memory is managed separately for the host and device. The following are the primary functions used for memory management:
cudaMalloc: Allocates memory on the device.
cudaMemcpy: Copies data between host and device.
cudaFree: Frees memory on the device.
Example: Summing Two Arrays
Let’s look at an example that sums two arrays using CUDA:
__global__ void sumArraysOnGPU(float *A, float *B, float *C, int N) int idx = threadIdx.x + blockIdx.x * blockDim.x; if (idx < N) C[idx] = A[idx] + B[idx]; int main() int N = 1024; size_t bytes = N * sizeof(float); float *h_A, *h_B, *h_C; h_A = (float*)malloc(bytes); h_B = (float*)malloc(bytes); h_C = (float*)malloc(bytes); float *d_A, *d_B, *d_C; cudaMalloc(&d_A, bytes); cudaMalloc(&d_B, bytes); cudaMalloc(&d_C, bytes); cudaMemcpy(d_A, h_A, bytes, cudaMemcpyHostToDevice); cudaMemcpy(d_B, h_B, bytes, cudaMemcpyHostToDevice); int blockSize = 256; int gridSize = (N + blockSize - 1) / blockSize; sumArraysOnGPU<<<gridSize, blockSize>>>(d_A, d_B, d_C, N); cudaMemcpy(h_C, d_C, bytes, cudaMemcpyDeviceToHost); cudaFree(d_A); cudaFree(d_B); cudaFree(d_C); free(h_A); free(h_B); free(h_C); return 0;
In this example, memory is allocated on both the host and device, data is transferred to the device, and the kernel is launched to perform the computation.
Conclusion
CUDA is a powerful tool for machine learning engineers looking to accelerate their models and handle larger datasets. By understanding the CUDA memory model, optimizing memory access, and leveraging multiple GPUs, you can significantly enhance the performance of your machine learning applications.
#AI Tools 101#algorithm#Algorithms#amp#applications#architecture#Arrays#cache#cluster#code#col#complexity#computation#computing#cpu#CUDA#CUDA for ML#CUDA memory model#CUDA programming#data#Data Structures#data transfer#datasets#double#engineers#excel#factor#functions#Fundamental#Global
0 notes
Text
Yall dont even know just how well-behaved i am DAILY at work! its like having two jobs at once! like im an undercover person who is put in a room with intolerable people very opposite of me in every way & is forced to play pretend & be niceys or else i dont get my prize at the end (clocking out & getting a paycheck)
#lets put a queer autist whos hyperfixation is su has no religion likes quiet & can only calm down with isolation & my music in a room with#another autist (unaware) whos fixation is yugioh/power rangers (uninteresting to me) who does voice impersonation stims & clings to you#who also thinks people like you (queer) are wrong & loves to talk to you about your ex-faith#& ALSO WITH ANOTHER autist (unaware) whos fixation/faith is stones & a youtube alien cult & also LOVES to talk abt how unhealthy food is#& shes a helicopter person who wont leave stuff alone even if she knows you want to be left alone & also looks down on minorities#once theyre all in that room together we'll shake it around to make them anxious & agitated & see what happens!!! doesnt that sound fun???#im being such a good nice patient person i stg#also the security guard & my coworker cant stand each other lately so GUESS WHO GETS TO HEAR ABOUT IT ALL THE TIME!?!? me their ''friend''#killingkillingkilling#im not saying people cant come from different walks of life or people with different believes cant get along but GOD DAMN#its literally my worst nightmare EVERY TIME i drive to work. i literally dread what kind of conversations theyll have with me for the night#this is what i mean when i say i hate being palatable#people who are against me in almost every way fundamentally consider me their close friend & it fucking sickens me that i let it happen#aint no way im quitting my job though because its a near-perfect fit for me management loves me & the money is good for the work i do#plus if i work here i can easily transfer to another location out of the country which is ultimately my goal#sorry. woke up from my sleep & chose violence ig#no more ranting tonight prommy#emma rants#emma rambles#work tag
1 note
·
View note
Text
Securing Your Website: Best Practices for Web Developers
As the digital landscape continues to evolve, website security has become a paramount concern for businesses and individuals alike. With cyber threats becoming increasingly sophisticated, it is crucial for web developers to adopt robust security measures to safeguard their websites and the sensitive data they handle. In this article, we'll delve into the best practices that web developers can implement to enhance the security of their websites and protect against potential threats.
Introduction
In today's interconnected world, websites serve as the digital storefront for businesses, making them vulnerable targets for cyber attacks. From data breaches to malware infections, the consequences of a security breach can be severe, ranging from financial loss to damage to reputation. Therefore, prioritizing website security is essential for maintaining the trust and confidence of users.
Understanding Website Security
Before diving into best practices, it's crucial to understand the importance of website security and the common threats faced by websites. Website security encompasses measures taken to protect websites from cyber threats and unauthorized access. Common threats include malware infections, phishing attacks, SQL injection, cross-site scripting (XSS), and brute force attacks.
Best Practices for Web Developers
Keeping Software Updated
One of the most fundamental steps in website security is keeping all software, including the content management system (CMS), plugins, and server software, updated with the latest security patches and fixes. Outdated software is often targeted by attackers due to known vulnerabilities that can be exploited.
Implementing HTTPS
Implementing HTTPS (Hypertext Transfer Protocol Secure) encrypts the data transmitted between the website and its users, ensuring confidentiality and integrity. HTTPS not only protects sensitive information but also boosts trust among visitors, as indicated by the padlock icon in the browser's address bar.
Using Strong Authentication Methods
Implementing strong authentication methods, such as multi-factor authentication (MFA) and CAPTCHA, adds an extra layer of security to user accounts. MFA requires users to provide multiple forms of verification, such as a password and a one-time code sent to their mobile device, reducing the risk of unauthorized access.
Securing Against SQL Injection Attacks
SQL injection attacks occur when malicious actors exploit vulnerabilities in web applications to execute arbitrary SQL commands. Web developers can prevent SQL injection attacks by using parameterized queries and input validation to sanitize user inputs effectively.
Protecting Sensitive Data
It's essential to employ encryption techniques to protect sensitive data, such as passwords, credit card information, and personal details, stored on the website's servers. Encrypting data at rest and in transit mitigates the risk of data breaches and unauthorized access.
Regular Security Audits
Conducting regular security audits helps identify vulnerabilities and weaknesses in the website's infrastructure and codebase. Penetration testing, vulnerability scanning, and code reviews enable web developers to proactively address security issues before they are exploited by attackers.
Choosing a Secure Hosting Provider
Selecting a reputable and secure hosting provider is critical for ensuring the overall security of your website. When evaluating hosting providers, consider factors such as security features, reliability, scalability, and customer support.
Evaluating Security Features
Choose a hosting provider that offers robust security features, such as firewalls, intrusion detection systems (IDS), malware scanning, and DDoS protection. These features help protect your website from various cyber threats and ensure continuous uptime.
Ensuring Regular Backups
Regularly backing up your website's data is essential for mitigating the impact of security incidents, such as data breaches or website compromises. Choose a hosting provider that offers automated backup solutions and store backups securely offsite.
Customer Support and Response to Security Incidents
Opt for a hosting provider that provides responsive customer support and has established protocols for handling security incidents. In the event of a security breach or downtime, prompt assistance from the hosting provider can minimize the impact on your website and business operations.
Implementing Firewall Protection
Firewalls act as a barrier between your website and external threats, filtering incoming and outgoing network traffic based on predefined security rules. There are several types of firewalls, including network firewalls, web application firewalls (WAF), and host-based firewalls.
Configuring and Maintaining Firewalls
Properly configuring and maintaining firewalls is crucial for effective security. Define firewall rules based on the principle of least privilege, regularly update firewall configurations to reflect changes in the website's infrastructure, and monitor firewall logs for suspicious activity.
Educating Users about Security
In addition to implementing technical measures, educating users about security best practices is essential for enhancing overall website security. Provide users with resources, such as security guidelines, tips for creating strong passwords, and information about common phishing scams.
Importance of User Awareness
Users play a significant role in maintaining website security, as they are often the targets of social engineering attacks. By raising awareness about potential threats and providing guidance on how to recognize and respond to them, web developers can empower users to stay vigilant online.
Providing Training and Resources
Offer training sessions and educational materials to help users understand the importance of security and how to protect themselves while using the website. Regularly communicate updates and reminders about security practices to reinforce good habits.
Monitoring and Responding to Security Incidents
Despite taking preventive measures, security incidents may still occur. Establishing robust monitoring systems and incident response protocols enables web developers to detect and respond to security threats in a timely manner.
Setting Up Monitoring Tools
Utilize monitoring tools, such as intrusion detection systems (IDS), security information and event management (SIEM) systems, and website monitoring services, to detect abnormal behavior and potential security breaches. Configure alerts to notify you of suspicious activity promptly.
Establishing Incident Response Protocols
Develop comprehensive incident response plans that outline roles, responsibilities, and procedures for responding to security incidents. Establish clear communication channels and escalation paths to coordinate responses effectively and minimize the impact of security breaches.
Securing your website requires a proactive approach that involves implementing a combination of technical measures, choosing a secure hosting provider, educating users about security best practices, and establishing robust monitoring and incident response protocols. By following these best practices, web developers can mitigate the risk of security breaches and safeguard their websites and the sensitive data they handle.
#website security has become a paramount concern for businesses and individuals alike. With cyber threats becoming increasingly sophisticated#it is crucial for web developers to adopt robust security measures to safeguard their websites and the sensitive data they handle. In this#we'll delve into the best practices that web developers can implement to enhance the security of their websites and protect against potenti#Introduction#In today's interconnected world#websites serve as the digital storefront for businesses#making them vulnerable targets for cyber attacks. From data breaches to malware infections#the consequences of a security breach can be severe#ranging from financial loss to damage to reputation. Therefore#prioritizing website security is essential for maintaining the trust and confidence of users.#Understanding Website Security#Before diving into best practices#it's crucial to understand the importance of website security and the common threats faced by websites. Website security encompasses measur#phishing attacks#SQL injection#cross-site scripting (XSS)#and brute force attacks.#Best Practices for Web Developers#Keeping Software Updated#One of the most fundamental steps in website security is keeping all software#including the content management system (CMS)#plugins#and server software#updated with the latest security patches and fixes. Outdated software is often targeted by attackers due to known vulnerabilities that can#Implementing HTTPS#Implementing HTTPS (Hypertext Transfer Protocol Secure) encrypts the data transmitted between the website and its users#ensuring confidentiality and integrity. HTTPS not only protects sensitive information but also boosts trust among visitors#as indicated by the padlock icon in the browser's address bar.#Using Strong Authentication Methods#Implementing strong authentication methods
0 notes
Text
"What emerged in two interviews with Trump, and conversations with more than a dozen of his closest advisers and confidants, were the outlines of an imperial presidency that would reshape America and its role in the world. To carry out a deportation operation designed to remove more than 11 millions people from the country, Trump told me, he would be willing to build migrant detention camps and deploy the U.S. military, both at the border and inland. He would let red states monitor women's pregnancies and prosecute those who violate abortion bans. He would, at his personal discretion, withhold funds appropriated by Congress, according to top advisers. He would be willing to fire a U.S. Attorney who doesn't carry out his order to prosecute someone, breaking with a tradition of independent law enforcement that dates from America's founding. He is weighing pardons for every one of his supporters accused of attacking the U.S. Capitol on Jan. 6, 2021, more than 800 of whom have pleaded guilty or been convicted by a jury. He might not come to the aid of an attacked ally in Europe or Asia if he felt that country wasn't paying enough for its own defense. He would gut the U.S. civil service, deploy the National Guard to American cities as he sees fit, close the White House pandemic-preparedness office, and staff his Administration with acolytes who back his false assertion that the 2020 election was stolen."
-- "How Far Would He Go", TIME Magazine's interviews with Donald Trump, April 30, 2024.
I know we're saturated in coverage of Trump and it's easy (and probably better for our mental health) to usually ignore most of the articles when we see them, especially since he's so full of shit and infuriating. But it's also important to recognize that he is going to be the Republican nominee for President and he could absolutely be elected in November, and if you thought his first term was scary and dangerous, you need to understand that in a second term he's going to have people around him that are better prepared and VERY willing to do the crazy shit that he wants to do to this country. They aren't even hiding the fact that they are seeking vengeance against political opponents whom they feel have wronged them, and are ready to fundamentally dismantle the democratic foundations that are barely holding this country together after nearly 250 years.
Just look at what Trump says about the people who he incited to attack the United States Capitol in an attempt to overturn the results of the 2020 election and halt the peaceful transfer of power that has happened every four years since 1789:
"Trump has sought to recast an insurrectionist riot as an act of patriotism. 'I call them the J-6 patriots,' he say. When I ask whether he would consider pardoning every one of them, he says, 'Yes, absolutely.' As Trump faces dozens of felony charges, including for election interference, conspiracy to defraud the United States, willful retention of national-security secrets, and falsifying business records to conceal hush-money payments, he has tried to turn legal peril into a badge of honor."
Oh, and please note that Trump -- a former President of the United States and possible future President of the United States -- said on the record in these interviews with TIME: "There is a definite antiwhite feeling in the country and that can't be allowed either." We are at a point where political leaders are outright saying that in this country again, and it's because of Donald Trump.
So, take the time to recognize that Trump is straight-up telling us the country we're going to be living in if he wins again in November. And understand that your vote matters -- and WHO you vote for matters -- because, as I've been saying for years now, ELECTIONS HAVE FUCKING CONSEQUENCES.
#2024 Election#Politics#Donald Trump#President Trump#Trump Administration#Vote#ELECTIONS HAVE CONSEQUENCES#TIME Magazine
10K notes
·
View notes
Note
Can you please elaborate on the original FFXIV getting blown up?
yeah so, in summary, when FF14 was first released it was helmed by an entirely different team of producers who were very much not interested in learning from developments in the MMO genre up to that point and kinda created a mess of a game. it wasn’t really due to one thing in particular that the game failed though, the entire production was highly mismanaged. people knew in beta that it was going to be a mess but they pushed it out anyway and it was a major flop critically and a big hit to square’s reputation. the producers were then removed from the project and another producer named Naoki Yoshida who had a lot of experience working on the Dragon Quest MMO was brought on to replace them and hopefully improve the state of the game.
when realizing just how fucked FF14 1.0 was at the time, yoshida gave square a bit of a hail mary option and was like “we can improve this game, but it will never be great in this form. let me continue making updates to the game… while also in the background secretly rebuild the entire game almost from scratch”. fucking miraculously square was like “yeah sure” and actually gave that idea the greenlight, with a 2-year window to release.
so that became the plan. improve the game in incremental amounts for players currently sticking with it, and then wipe the whole slate clean and release a FF14 2.0 that was a fundamentally remade experience, actually taking more design inspiration from other successful MMOs and other final fantasy games. they didn’t just decide to wipe the original game on a meta level though, they actually worked the destruction of FF14 1.0 into the plot of both games. and so, famously, the day that the servers for 1.0 were shut down was a day where IN GAME players fought a horde of deadly monsters spawning around the world until inevitably a giant moon crashed into the world and took the servers offline for good. and then when you play 2.0, they frequently reference this calamity in the early MSQ and players who stuck with 1.0 until the end actually got their entire character transferred over with a special tattoo, opening cutscenes, and special dialogue throughout the MSQ that connects them to the game that was deleted.
there’s a 3-part noclip documentary that goes into more detail, it is FASCINATING stuff.
youtube
5K notes
·
View notes
Text
@amedetoiles’s great tags per usual

Lotta takes that are like "Jiang Cheng didn't change his behaviour at all in 13 years, that proves that he doesn't want to grow as a person" and it's like, sorry but why would he change his behaviour when the information that would recontextualise Wei Wuxian's actions and thus lead him to rethink his own reactions was deliberately kept hidden from him? From his perspective, his brother broke all his promises for no goddamn reason, picked a different family over him, lost control of the evil energy he swore he could control, and in doing so caused such a catastrophe that both of Jin Ling's parents were killed. We know that there's more to that story, but he doesn't, and it would be impossible for him to find out on his own because again, everyone involved was lying to him and hiding the relevant information on purpose.
He's told about the golden core transfer like three hours before the book ends, and frankly processes it faster than most people could reasonably be expected to after 13 years of grief and loneliness! "He had chances to improve his behaviour and didn't" HE LITERALLY DIDN'T HAVE ANY CHANCES BECAUSE WWX LIED TO HIM!! His behaviour was completely justified from his perspective and when his perspective is changed, and he realises that what he did was wrong, he's like, SUPER upset about it!
#the untamed#Yunmeng bros#once again I am banging the drum that the bad communication is not because they’re incapable#it’s willful#the silence arounf the golden core transfer poisoned their relationship#it gave WWX a secret to hide#and a loss that emotionally festered within him probably moreso BECAUSE he couldn’t admit to it#much deal with with all the horrible feelings he had about living with the loss#(we know how this man deals with the bad feelings!)#now arguably you could put some of that on JC and his own silence about how he lost his core#I cannot imagine any version of WWX taking that news well#but I do think knowing what had happened would probably result in there being no core transfer#like if he could made to understand that JC absolutely would not want his cultivation back at WWX’s expense#he REALLY had to work himself up to that decision! it was monumental! he needed very badly to believe#that this sacrifice was worth it to save JC’s life#knowing that JC would die for him would probably give him a lil pause on that huge self-sacrifice#if nothing else I think WN and WQ would be like#mmm. maybe let’s wake up the patient and ask him before we commit to this on WWX’s analysis of JC’s character alone#anyway the problem with JC needing to be up front about his own self-sacrifice#is that he barely has the chance to process what happened to him before they sent him to Lalaland for being such a downer#it’s not like WWX asked him what happened and he lied#WWX made assumptions and did not bother to confirm them#and post-core transfer JC thinks BSSR gave him a new core at the eminently bearable cost of WWX missing out on the chance to ask her a favor#and therefore that the circumstances under which he lost his core in the first place are not relevant and do not need to be shared#this is the part where they’re ships passing in the night#this is the fundamental root of the relationship/communication breakdown#not wanting to deal with the consequences of the other one knowing what they sacrified for them#and so staying silent about it when it desperately needed to be dealt with on both sides#THAT’S the gift of the magi baby#WWX is worse in general but JC is just as much a part of THIS communication fuckup. and he’s still withholding the truth at the end…
567 notes
·
View notes
Quote
Scientists at UC Riverside have demonstrated a new, RNA-based vaccine strategy that is effective against any strain of a virus and can be used safely even by babies or the immunocompromised. Their flu vaccine will also likely be delivered in the form of a spray, as many people have an aversion to needles. “Respiratory infections move through the nose, so a spray might be an easier delivery system,” Hai said. Additionally, the researchers say there is little chance of a virus mutating to avoid this vaccination strategy. “Viruses may mutate in regions not targeted by traditional vaccines. However, we are targeting their whole genome with thousands of small RNAs. They cannot escape this,” Hai said. Ultimately, the researchers believe they can ‘cut and paste’ this strategy to make a one-and-done vaccine for any number of viruses. “There are several well-known human pathogens; dengue, SARS, COVID. They all have similar viral functions,” Ding said. “This should be applicable to these viruses in an easy transfer of knowledge.”
Vaccine breakthrough means no more chasing strains
This is HUGE. This will fundamentally change how we get inoculated.
5K notes
·
View notes
Text
When someone from europe or a peripheral capitalist state does the whole 'oh police violence and repression aren't a problem here that's just a USA thing' song and dance, it's obviously bullshit - the oppositional nature between the enforcers of the ruling class and the classes they rule over is fairly fundamental to the existence of any state - but it would be a lot easier to countermand if usamericans weren't so utterly provincial.
The character of the bourgeois police in, for example, Kazakhstan, is genuinely different than that of the US police, and cannot be neatly understood through just seeing it as a variation on the latter. A more broad, theoretical understanding of policing in general applies to both, but an empiricist understanding of a federal security apparatus descended from British-imperial slave patrols just plainly will not transfer to a unitary state's police force made to replace a workers' militia.
This applies to everything, really - the racial and ethnic dynamics of a given place outside the USA are going to be fundamentally and qualitatively different than those of the USA, and the refusal, of usamericans who have learned, empirically, about the nature of anglo settler-colonial white supremacy, to then develop a deeper and broader theoretical understanding of how systems of racial and ethnic oppression are developed - rather than saying 'its crazy that serbs and croats could hate each other when they're both White, shrimp racism lol' and the like - makes it more difficult, not less, to meaningfully oppose it when someone says 'racism isn't a problem in my country, just the USA', especially when the only response given is regarding supposed oppression of racial categories that may well not exist in that context.
This is, incidentally, why the whole 'I don't need theory, I have lived experience' tripe is wholly insufficient for the real world. You do not have enough experience, and you are going to encounter novel scenarios where mindlessly applying learned dynamics by rote will lead to entirely confident wrong answers. It's not good enough. The world is a lot bigger than you.
#read my sentence boy#my abuse of the english language continues unabated and I will make no concessions - only connectives
2K notes
·
View notes
Text
Tesla's Dieselgate

Elon Musk lies a lot. He lies about being a “utopian socialist.” He lies about being a “free speech absolutist.” He lies about which companies he founded:
https://www.businessinsider.com/tesla-cofounder-martin-eberhard-interview-history-elon-musk-ev-market-2023-2 He lies about being the “chief engineer” of those companies:
https://www.quora.com/Was-Elon-Musk-the-actual-engineer-behind-SpaceX-and-Tesla
He lies about really stupid stuff, like claiming that comsats that share the same spectrum will deliver steady broadband speeds as they add more users who each get a narrower slice of that spectrum:
https://www.eff.org/wp/case-fiber-home-today-why-fiber-superior-medium-21st-century-broadband
The fundamental laws of physics don’t care about this bullshit, but people do. The comsat lie convinced a bunch of people that pulling fiber to all our homes is literally impossible��— as though the electrical and phone lines that come to our homes now were installed by an ancient, lost civilization. Pulling new cabling isn’t a mysterious art, like embalming pharaohs. We do it all the time. One of the poorest places in America installed universal fiber with a mule named “Ole Bub”:
https://www.newyorker.com/tech/annals-of-technology/the-one-traffic-light-town-with-some-of-the-fastest-internet-in-the-us
Previous tech barons had “reality distortion fields,” but Musk just blithely contradicts himself and pretends he isn’t doing so, like a budget Steve Jobs. There’s an entire site devoted to cataloging Musk’s public lies:
https://elonmusk.today/
But while Musk lacks the charm of earlier Silicon Valley grifters, he’s much better than they ever were at running a long con. For years, he’s been promising “full self driving…next year.”
https://pluralistic.net/2022/10/09/herbies-revenge/#100-billion-here-100-billion-there-pretty-soon-youre-talking-real-money
He’s hasn’t delivered, but he keeps claiming he has, making Teslas some of the deadliest cars on the road:
https://www.washingtonpost.com/technology/2023/06/10/tesla-autopilot-crashes-elon-musk/
Tesla is a giant shell-game masquerading as a car company. The important thing about Tesla isn’t its cars, it’s Tesla’s business arrangement, the Tesla-Financial Complex:
https://pluralistic.net/2021/11/24/no-puedo-pagar-no-pagara/#Rat
Once you start unpacking Tesla’s balance sheets, you start to realize how much the company depends on government subsidies and tax-breaks, combined with selling carbon credits that make huge, planet-destroying SUVs possible, under the pretense that this is somehow good for the environment:
https://pluralistic.net/2021/04/14/for-sale-green-indulgences/#killer-analogy
But even with all those financial shenanigans, Tesla’s got an absurdly high valuation, soaring at times to 1600x its profitability:
https://pluralistic.net/2021/01/15/hoover-calling/#intangibles
That valuation represents a bet on Tesla’s ability to extract ever-higher rents from its customers. Take Tesla’s batteries: you pay for the battery when you buy your car, but you don’t own that battery. You have to rent the right to use its full capacity, with Tesla reserving the right to reduce how far you go on a charge based on your willingness to pay:
https://memex.craphound.com/2017/09/10/teslas-demon-haunted-cars-in-irmas-path-get-a-temporary-battery-life-boost/
That’s just one of the many rent-a-features that Tesla drivers have to shell out for. You don’t own your car at all: when you sell it as a used vehicle, Tesla strips out these features you paid for and makes the next driver pay again, reducing the value of your used car and transfering it to Tesla’s shareholders:
https://www.theverge.com/2020/2/6/21127243/tesla-model-s-autopilot-disabled-remotely-used-car-update
To maintain this rent-extraction racket, Tesla uses DRM that makes it a felony to alter your own car’s software without Tesla’s permission. This is the root of all autoenshittification:
https://pluralistic.net/2023/07/24/rent-to-pwn/#kitt-is-a-demon
This is technofeudalism. Whereas capitalists seek profits (income from selling things), feudalists seek rents (income from owning the things other people use). If Telsa were a capitalist enterprise, then entrepreneurs could enter the market and sell mods that let you unlock the functionality in your own car:
https://pluralistic.net/2020/06/11/1-in-3/#boost-50
But because Tesla is a feudal enterprise, capitalists must first secure permission from the fief, Elon Musk, who decides which companies are allowed to compete with him, and how.
Once a company owns the right to decide which software you can run, there’s no limit to the ways it can extract rent from you. Blocking you from changing your device’s software lets a company run overt scams on you. For example, they can block you from getting your car independently repaired with third-party parts.
But they can also screw you in sneaky ways. Once a device has DRM on it, Section 1201 of the DMCA makes it a felony to bypass that DRM, even for legitimate purposes. That means that your DRM-locked device can spy on you, and because no one is allowed to explore how that surveillance works, the manufacturer can be incredibly sloppy with all the personal info they gather:
https://www.cnbc.com/2019/03/29/tesla-model-3-keeps-data-like-crash-videos-location-phone-contacts.html
All kinds of hidden anti-features can lurk in your DRM-locked car, protected from discovery, analysis and criticism by the illegality of bypassing the DRM. For example, Teslas have a hidden feature that lets them lock out their owners and summon a repo man to drive them away if you have a dispute about a late payment:
https://tiremeetsroad.com/2021/03/18/tesla-allegedly-remotely-unlocks-model-3-owners-car-uses-smart-summon-to-help-repo-agent/
DRM is a gun on the mantlepiece in Act I, and by Act III, it goes off, revealing some kind of ugly and often dangerous scam. Remember Dieselgate? Volkswagen created a line of demon-haunted cars: if they thought they were being scrutinized (by regulators measuring their emissions), they switched into a mode that traded performance for low emissions. But when they believed themselves to be unobserved, they reversed this, emitting deadly levels of NOX but delivering superior mileage.
The conversion of the VW diesel fleet into mobile gas-chambers wouldn’t have been possible without DRM. DRM adds a layer of serious criminal jeopardy to anyone attempting to reverse-engineer and study any device, from a phone to a car. DRM let Apple claim to be a champion of its users’ privacy even as it spied on them from asshole to appetite:
https://pluralistic.net/2022/11/14/luxury-surveillance/#liar-liar
Now, Tesla is having its own Dieselgate scandal. A stunning investigation by Steve Stecklow and Norihiko Shirouzu for Reuters reveals how Tesla was able to create its own demon-haunted car, which systematically deceived drivers about its driving range, and the increasingly desperate measures the company turned to as customers discovered the ruse:
https://www.reuters.com/investigates/special-report/tesla-batteries-range/
The root of the deception is very simple: Tesla mis-sells its cars by falsely claiming ranges that those cars can’t attain. Every person who ever bought a Tesla was defrauded.
But this fraud would be easy to detect. If you bought a Tesla rated for 353 miles on a charge, but the dashboard range predictor told you that your fully charged car could only go 150 miles, you’d immediately figure something was up. So your Telsa tells another lie: the range predictor tells you that you can go 353 miles.
But again, if the car continued to tell you it has 203 miles of range when it was about to run out of charge, you’d figure something was up pretty quick — like, the first time your car ran out of battery while the dashboard cheerily informed you that you had 203 miles of range left.
So Teslas tell a third lie: when the battery charge reached about 50%, the fake range is replaced with the real one. That way, drivers aren’t getting mass-stranded by the roadside, and the scam can continue.
But there’s a new problem: drivers whose cars are rated for 353 miles but can’t go anything like that far on a full charge naturally assume that something is wrong with their cars, so they start calling Tesla service and asking to have the car checked over.
This creates a problem for Tesla: those service calls can cost the company $1,000, and of course, there’s nothing wrong with the car. It’s performing exactly as designed. So Tesla created its boldest fraud yet: a boiler-room full of anti-salespeople charged with convincing people that their cars weren’t broken.
This new unit — the “diversion team” — was headquartered in a Nevada satellite office, which was equipped with a metal xylophone that would be rung in triumph every time a Tesla owner was successfully conned into thinking that their car wasn’t defrauding them.
When a Tesla owner called this boiler room, the diverter would run remote diagnostics on their car, then pronounce it fine, and chide the driver for having energy-hungry driving habits (shades of Steve Jobs’s “You’re holding it wrong”):
https://www.wired.com/2010/06/iphone-4-holding-it-wrong/
The drivers who called the Diversion Team weren’t just lied to, they were also punished. The Tesla app was silently altered so that anyone who filed a complaint about their car’s range was no longer able to book a service appointment for any reason. If their car malfunctioned, they’d have to request a callback, which could take several days.
Meanwhile, the diverters on the diversion team were instructed not to inform drivers if the remote diagnostics they performed detected any other defects in the cars.
The diversion team had a 750 complaint/week quota: to juke this stat, diverters would close the case for any driver who failed to answer the phone when they were eventually called back. The center received 2,000+ calls every week. Diverters were ordered to keep calls to five minutes or less.
Eventually, diverters were ordered to cease performing any remote diagnostics on drivers’ cars: a source told Reuters that “Thousands of customers were told there is nothing wrong with their car” without any diagnostics being performed.
Predicting EV range is an inexact science as many factors can affect battery life, notably whether a journey is uphill or downhill. Every EV automaker has to come up with a figure that represents some kind of best guess under a mix of conditions. But while other manufacturers err on the side of caution, Tesla has the most inaccurate mileage estimates in the industry, double the industry average.
Other countries’ regulators have taken note. In Korea, Tesla was fined millions and Elon Musk was personally required to state that he had deceived Tesla buyers. The Korean regulator found that the true range of Teslas under normal winter conditions was less than half of the claimed range.
Now, many companies have been run by malignant narcissists who lied compulsively — think of Thomas Edison, archnemesis of Nikola Tesla himself. The difference here isn’t merely that Musk is a deeply unfit monster of a human being — but rather, that DRM allows him to defraud his customers behind a state-enforced opaque veil. The digital computers at the heart of a Tesla aren’t just demons haunting the car, changing its performance based on whether it believes it is being observed — they also allow Musk to invoke the power of the US government to felonize anyone who tries to peer into the black box where he commits his frauds.

If you'd like an essay-formatted version of this post to read or share, here's a link to it on pluralistic.net, my surveillance-free, ad-free, tracker-free blog:
https://pluralistic.net/2023/07/28/edison-not-tesla/#demon-haunted-world

This Sunday (July 30) at 1530h, I’m appearing on a panel at Midsummer Scream in Long Beach, CA, to discuss the wonderful, award-winning “Ghost Post” Haunted Mansion project I worked on for Disney Imagineering.

Image ID [A scene out of an 11th century tome on demon-summoning called 'Compendium rarissimum totius Artis Magicae sistematisatae per celeberrimos Artis hujus Magistros. Anno 1057. Noli me tangere.' It depicts a demon tormenting two unlucky would-be demon-summoners who have dug up a grave in a graveyard. One summoner is held aloft by his hair, screaming; the other screams from inside the grave he is digging up. The scene has been altered to remove the demon's prominent, urinating penis, to add in a Tesla supercharger, and a red Tesla Model S nosing into the scene.]

Image: Steve Jurvetson (modified) https://commons.wikimedia.org/wiki/File:Tesla_Model_S_Indoors.jpg
CC BY 2.0 https://creativecommons.org/licenses/by/2.0/deed.en
#pluralistic#steve stecklow#autoenshittification#norihiko shirouzu#reuters#you're holding it wrong#r2r#right to repair#range rage#range anxiety#grifters#demon-haunted world#drm#tpms#1201#dmca 1201#tesla#evs#electric vehicles#ftc act section 5#unfair and deceptive practices#automotive#enshittification#elon musk
8K notes
·
View notes
Text
NASA’s Space Station Laser Comm Terminal Achieves First Link - Technology Org
New Post has been published on https://thedigitalinsider.com/nasas-space-station-laser-comm-terminal-achieves-first-link-technology-org/
NASA’s Space Station Laser Comm Terminal Achieves First Link - Technology Org
A NASA technology experiment on the International Space Station completed its first laser link with an in-orbit laser relay system on Dec. 5, 2023. Together, they complete NASA’s first two-way, end-to-end laser relay system.
NASA’s ILLUMA-T payload communicating with LCRD over laser signals. Image credit: NASA / Dave Ryan
NASA’s LCRD (Laser Communications Relay Demonstration) and the new space station demonstration, ILLUMA-T (Integrated LCRD Low Earth Orbit User Modem and Amplifier Terminal), successfully exchanged data for the first time.
LCRD and ILLUMA-T are demonstrating how a user mission, in this case the space station, can benefit from a laser communications relay located in geosynchronous orbit.
The benefits of laser communications: more efficient, lighter systems, increased security, and more flexible ground systems. Image credit: NASA / Dave Ryan
Laser communications, also known known as optical communications, uses infrared light rather than traditional radio waves to send and receive signals. The tighter wavelength of infrared light allows spacecraft to pack more data into each transmission. Using laser communications greatly increases the efficiency of data transfer and can lead to a faster pace of scientific discoveries.
NASA’s SpaceX 29th commercial resupply services mission launched cargo and new science experiments, including ILLUMA-T, to the space station. Following its arrival, the payload was installed onto the station’s Japanese Experiment Module-Exposed Facility.
ILLUMA-T and LCRD are a part of the NASA Space Communications and Navigation (SCaN) program’s effort to demonstrate how laser communications technologies can significantly benefit science and exploration missions.
“ILLUMA-T’s first link with LCRD – known as first light – is the latest demonstration proving that laser communications is the future.” said Dr. Jason Mitchell, director of SCaN’s Advanced Communications and Navigation Technology division.
“Laser communications will not only return more data from science missions, but could serve as NASA’s critical, two-way link to keep astronauts connected to Earth as they explore the Moon, Mars, and beyond.”
Shortly after space station installation, operation engineers began conducting on-orbit testing to ensure the ILLUMA-T payload operated nominally. Now, it is communicating with LCRD, a relay launched in 2021 that has conducted over 300 experiment configurations to help NASA refine laser communications technologies. LCRD and ILLUMA-T are exchanging data at 1.2 gigabits-per-second.
“We have demonstrated that we can overcome the technical challenges for successful space communications using laser communications. We are now performing operational demonstrations and experiments that will allow us to optimize our infusion of proven technology into our missions to maximize our exploration and science,” said David Israel, a NASA space communications and navigation architect.
NASA’s Laser Communications Roadmap: Demonstrating laser communications capabilities on multiple missions in a variety of space regimes. Image credit: NASA/Dave Ryan
The LCRD experiments are conducted with industry, academia, and other government agencies. ILLUMA-T is now LCRD’s first in-space user experiment. NASA is still accepting experiments to work with LCRD. Interested parties should contact [email protected] for more information.
Source: National Aeronautics and Space Administration
You can offer your link to a page which is relevant to the topic of this post.
#2023#Administration#aeronautics#astronauts#communications#data#data transfer#Discoveries#earth#efficiency#email#engineers#Featured Space news#Fundamental physics news#Future#Government#how#Industry#International Space Station#Israel#it#laser#lasers#Light#Link#mars#module#Moon#NASA#National Aeronautics and Space Administration
0 notes
Text
i used codecademy to learn python, but i already had a bit of a background with js. i'm not entirely sure how good it is for cpp (i think i just kind of learned it through like. osmosis). anyway it'll be kind of difficult at first but it (for me at least) ends up being really freeing
If anyone has any c++ tutorials please send them to me. It's my first language and it's so hard to understand because of the way it's bring presented in class.
It's literally a problem solving class now with no help or input from other students or professors so you don't know it's wrong until you get a 0 for it for turning it in
I need major help like bad
#cpp is currently my top programming language#although js is a fairly close second#it'd probably be better to start with something higher level (ie python)#but once you grok the fundamentals of programming a lot of the skills transfer between languages
85 notes
·
View notes