#University Library Management Software
Explore tagged Tumblr posts
Text
University Management Software
University Management Software streamlines administrative tasks, academic processes, and student management for educational institutions. It facilitates efficient management of student records, course scheduling, faculty assignments, financial operations, and more. This comprehensive system enhances communication between departments, faculty, and students, ensuring smoother operations and improved organizational effectiveness within the university ecosystem.
0 notes
Text
Noosciocircus agent backgrounds, former jobs at C&A, assigned roles, and current internal status.
Kinger
Former professor — Studied child psychology and computer science, moved into neobotanics via germination theory and seedlet development.
Seedlet trainer — Socialized and educated newly germinated seedlets to suit their future assignments. I.e. worked alongside a small team to serve as seedlets’ social parents, K-12 instructors, and upper-education mentors in rapid succession (about a year).
Intermediary — Inserted to assist cooperation and understanding of Caine.
Partially mentally mulekicked — Lives in state of forgetfulness after abstraction of spouse, is prone to reliving past from prior to event.
Ragatha
Former EMT — Worked in a rural community.
Semiohazard medic — Underwent training to treat and assess mulekick victims and to administer care in the presence of semiohazards.
Nootic health supervisor— Inserted to provide nootic endurance training, treat psychological mulekick, and maintain morale.
Obsessive-compulsive — Receives new agents and struggles to maintain morale among team and herself due to low trust in her honesty.
Jax
Former programmer — Gained experience when acquired out of university by a large software company.
Scioner — Developed virtual interfaces for seedlets to operate machinery with.
Circus surveyor — Inserted to assess and map nature of circus simulation, potentially finding avenues of escape.
Anomic — Detached from morals and social stake. Uncooperative and gleefully combative.
Gangle
Former navy sailor — Performed clerical work as a yeoman, served in one of the first semiotically-armed submarines.
Personnel manager — Recordkept C&A researcher employments and managed mess hall.
Task coordinator — Inserted to organize team effort towards escape.
Reclused — Abandoned task and lives in quiet, depressive state.
Zooble
No formal background — Onboarded out of secondary school for certification by C&A as part of a youth outreach initiative.
Mule trainer — Physically handled mules, living semiohazard conveyors for tactical use.
Semiohazard specialist — Inserted to identify, evaluate, and attempt to disarm semiotic tripwires.
Debilitated and self-isolating — Suffers chronic vertigo from randomly pulled avatar. Struggles to participate in adventures at risk of episode.
Pomni
Former accountant — Worked for a chemical research firm before completing her accreditation to become a biochemist.
Collochemist — Performed mesh checkups and oversaw industrial hormone synthesis.
Field researcher — Inserted to collect data from fellows and organize reports for indeterminate recovery. Versed in scientific conduct.
In shock — Currently acclimating to new condition. Fresh and overwhelming preoccupation with escape.
Caine
Neglected — Due to project deadline tightening, Caine’s socialization was expedited in favor of lessons pertinent to his practical purpose. Emerged a well-meaning but awkward and insecure individual unprepared for noosciocircus entrapment.
Prototype — Germinated as an experimental mustard, or semiotic filter seedlet, capable of subconsciously assembling semiohazards and detonating them in controlled conditions.
Nooscioarchitect — Constructs spaces and nonsophont AI for the agents to occupy and interact with using his asset library and computation power. Organizes adventures to mentally stimulate the agents, unknowingly lacing them with hazards.
Helpless — After semiohazard overexposure, an agent’s attachment to their avatar dissolves and their blackroom exposes, a process called abstraction. These open holes in the noosciocircus simulation spill potentially hazardous memories and emotion from the abstracted agent’s mind. Caine stores them in the cellar, a stimulus-free and infoproofed zone that calms the abstracted and nullifies emitted hazards. He genuinely cares about the inserted, but after only being able to do damage control for a continually deteriorating situation, the weight of his failure is beginning to weigh on him in a way he did not get to learn how to express.
#the amazing digital circus#noosciocircus#char speaks#digital circus#tadc Kinger#tadc Ragatha#tadc Jax#tadc gangle#tadc zooble#tadc Pomni#tadc caine#bad ending#sophont ai
231 notes
·
View notes
Text
so if any of y'all have ever purchased e-books from Amazon, then you should log in to your Amazon account, and under your Content Library, download all your e-books to your computer and transfer them to your kindle reader via USB, or send them directly to your preferred device (if you have more than one connected to your Amazon account) via wifi by clicking "Deliver or Remove from this device" and switching the device you want to send it to
Once you've downloaded all your purchased e-books, not ones that are borrowed from Kindle Unlimited or Prime Reading, download the free Calibre e-book management software and this DRM removal plugin to remove the DRM (digital rights management) from your e-books, which converts your kindle e-books into the universal e-book format EPUB or whatever other ebook format you'd like, bc the Kindle ebook format AZW and AZW3, can only be used on Kindle readers, but by removing the DRM, they can then be used on any device that reads the EPUB format
BUT why should you do all this? bc on Feb. 26, 2025 (one week from now as of the time I posted this) Amazon will no longer provide this download option bc they're aware that people have been downloading their e-books from their kindle libraries and using software like Calibre to convert those e-books into EPUBs and not have to be tied down to Amazon's ecosystem, which makes them lose money (boohoo), and also the switch towards cloud-based storage
Basically, any e-books you have purchased from Amazon are not yours to own, you're essentially being licensed the e-book, so they can use this loophole to alter or completely remove those e-books from the website at their whim, and you would no longer have access to those e-books, even though you legally purchased them, which is wild bc we should be able to legally own, forever, any digital media we buy and do what we want with it, and this is something that has been happening with other forms of digital media like movies and video games, where you "buy" a digital copy but you don't actually own it
You should also stop buying e-books from amazon from now on since you don't even own them, and cancel your Kindle Unlimited subscription if you have one, and you might as well download any audiobooks you've purchased on Audible (which is also owned by Amazon)
[watch this video and this video for more thorough explanations about this issue and this video for a tutorial on how to use Calibre and the DRM ]
Alternatives to kindle readers include: Kobo (has integration with Libby) and Nook (from Barnes & Noble), or sell or donate the one you have if you don't want to use it anymore
Alternatives to amazon e-books: Libby (free app that links to your local library if you have an active library card where you can borrow ebooks and other digital media), Internet Archive, Project Gutenburg, 🏴☠️ ebooks and PDFs, and research whether your favorite author has books available to purchase directly on their website
....and you can always purchase or borrow physical books and other media as well! support your local libraries and indie bookstores!
TL,DR: this is a matter of media ownership, censorship, and archiving, so download your Amazon e-books NOW before Amazon takes away your ability to access the items that you legally purchased and locks you down to using their devices and ecosystem
FEBRUARY 26 IS THE LAST DAY TO DOWNLOAD YOUR AMAZON EBOOKS
#amazon#kindle#ebooks#books#media ownership#idk what else to tag this but hopefully it can be seen by some people#if you would like to share this please do so bc this is time sensitive#just another reason to say FUCK YOU to amazon
37 notes
·
View notes
Note
Hello! I'm currently an MLIS student (no focus yet), and I've been thinking about getting a History MA as well. I've been told that doubling up on Master's degrees can be a hindrance in getting work as it makes it look like you can't commit to one field, but I noticed that you have an MLIS and a History MA. How were you able to make that work? Was it because of the overlap of topics you were studying?
(for extra context, I'm in the U.S. and I would be looking at an MA in late antique or medieval history)
The unvarnished truth is that there are way more people with degrees in our field than there are jobs, especially in blue states. Anything you have that can put you ahead of the pack, including a subject-specific MA, is good. Especially now that, as universities have so effectively cannibalized themselves, we have a glut of PhDs who can’t get TT positions horning in on the GLAM (Galleries, Libraries, Archives, and Museums) professions.
As for my career and the doubling up; it worked until it didn’t—in this profession it’s very difficult to move up or get a pay raise unless you’re willing to become a manager; and the pay in this field has NOT kept pace with COL or inflation.
To best position yourself in the job market, you need to get your MA in a modern field. Late Antiquity and Medieval GLAM jobs in this country are few and far between, and the competition is typically PhDs.
A Masters in some aspect of US history will be the best for you to build a case for yourself as a successful candidate. Also, learning database science, and as much coding and software as you can before you finish your degree.
Sorry for the cynicism. I have ten years of experience in this field plus the masters degrees and I haven’t even been contacted for an interview in over a year.
ETA: all of this said, if some random 35 year old had given me this advice when I was just starting grad school at the (too young, imo) age of 22, I would have blown it off as the rantings of a lazy, bitter failure so, ymmv. (Here, I would say “ah the arrogance of youth,” but I’ve always been stubborn and pig headed about my goals lol)
35 notes
·
View notes
Text









Cosmo Klein (1978) by Jeff Duntemann AKA "Captain Cosmo", Rochester, NY. Cosmo Klein is based on the COSMAC Elf RCA 1802 microcomputer and features a robot arm, and a CRT face separately controlled by a COSMAC VIP, an 1802 based microcomputer with a supplementary video display chip.
"For all its flaws, the VIP is probably worth the money… The worst thing about the VIP is something that can be said of the ELF-II from Netronics or Quest's Super ELF: If you don't wire wrap it yourself, you won't learn as much. What are you doing this for? If you want to learn microcomputer hardware and software without going broke, the Popular Electronics ELF has no equal. …
COSMO'S FACE -- I take that back; there is something that the VIP is good at: Giving my robot a face. For a while I've been tinkering with a clanking heap of surplus submarine parts and wheelchair motors named Cosmo Klein. The Klein is an obscure mathematical allusion to the Klein Bottle, whos insides are identical to its outsides. Cosmo is a little like that, especially when he tips over and sends his insides spilling out onto the floor. Well, I got the notion that a COSMAC-generated face would be a marvelously humanizing touch. And so it is. If you want to see a good color picture of Cosmo and my VIP (with my own idiotically grinning mug in the background) check out Look Magazine dated April 30, 1979; it's the one with Jane Fonda on the cover. Maybe your library has it. The program which generates the face is included in this book, so I won't describe it here. Though you can't see it, my ELF is also inside, vainly trying to keep the monster from falling on his face. A CMOS robot is an old dream of mine, and I'm working on it, but for now I must pronounce his control circuitry (save for his face) a failure. Now you know who Captain Cosmo is. Yes indeed, that cute cartoon on the cover has a real model." – Captain Cosmo's Whizbang, by Jeff Duntemann, 1980.
“In addition to the VIP on his chest (which managed his face video and nothing else) he had a wire-wrapped machine inside his body, and a built-in OAE paper tape reader for getting his software up and running. (I punched the tapes on a DEC PDP11 system at Loyola University, where a friend worked at that time. The code was all written in binary, by hand.)” – Jeff Duntemann, Meet Cosmo Klein, COSMAC ELF.
"Cosmo Klein, a 4' tall robot with a TV-screen face, is a mutt bred from "junque" and computer chips. Cosmo has a World War II navy sonar-console body which was bought at a rummage sale for 25 cents and houses a homemade computer that monitors internal functions, like voltage regulation, speed, motion, and Arm and hand action. Cosmo lives with Jeff and Carol Duntemann. Jeff is a Xerox engineer, science-fiction writer, and member of a group of "techies" who build futuristic gadgets. He has grander inspirations than Cosmo. "What I'm looking toward in maybe 40 years is a robot that will act as a companion to the emotionally disturbed and the severely retarded. The patience of machines is marvellous. They'll sit there and listen and talk back." " – A Robot for Every Home, by Lauren Freudmann, Look Magazine, April 30, 1979.
42 notes
·
View notes
Text
The Trump administration, working in coordination with Elon Musk’s so-called Department of Government Efficiency, has gutted a small federal agency that provides funding to libraries and museums nationwide. In communities across the US, the cuts threaten student field trips, classes for seniors, and access to popular digital services, such as the ebook app Libby.
On Monday, managers at the Institute of Museum and Library Services (IMLS) informed 77 employees—virtually the agency’s entire staff—that they were immediately being put on paid administrative leave, according to one of the workers, who sought anonymity out of fear of retaliation from Trump officials. Several other sources confirmed the move, which came after President Donald Trump appointed Keith Sonderling, the deputy secretary of labor, as the acting director of IMLS less than two weeks ago.
A representative for the American Federation of Government Employee Local 3403, a union that represents about 40 IMLS staffers, said Sonderling and a group of DOGE staffers met with IMLS leadership late last month. Afterwards, Sonderling sent an email to staff “emphasizing the importance of libraries and museums in cultivating the next generation’s perception of American exceptionalism and patriotism,” the union representative said in a statement to WIRED.
IMLS employees who showed up to work at the agency on Monday were asked to turn in their computers and lost access to their government email addresses before being ordered to head home for the day, the employee says. It’s unclear when, or if, staffers will ever return to work. “It’s heartbreaking on many levels,” the employee adds.
The White House and the Institute of Museum and Library Services did not immediately respond to requests for comment from WIRED.
The annual budget of IMLS amounts to less than $1 per person in the US. Overall, the agency awarded over $269.5 million to library and museum systems last year, according to its grants database. Much of that money is paid out as reimbursements over time, the current IMLS employee says, but now there is no one around to cut checks for funds that have already been allocated.
“The status of previously awarded grants is unclear. Without staff to administer the programs, it is likely that most grants will be terminated,” the American Federation of Government Employee Local 3403 union said in a statement.
About 65 percent of the funding had been allocated to different states, with each one scheduled to receive a minimum of roughly $1.2 million. Recipients can use the money for statewide initiatives or pass it on to local museum and library institutions for expenses such as staff training and back-office software. California and Texas have received the highest allocated funding, at about $12.5 million and $15.7 million, respectively, according to IMLS data. Individual libraries and museums also receive grants directly from IMLS for specific projects.
An art museum in Idaho expected to put $10,350 toward supporting student field trips, according to the IMLS grant database. A North Carolina museum was allotted $23,500 for weaving and fiber art workshops for seniors. And an indigenous community in California expected to put $10,000 toward purchasing books and electronic resources.
In past years, other Native American tribes have received IMLS grants to purchase access to apps such as Hoopla and Libby, which provide free ebooks and audiobooks to library patrons. Some funding from the IMLS also goes to academic projects, such as using virtual reality to preserve Native American cultural archives or studying how AI chatbots could improve access to university research.
Steve Potash, founder and CEO of OverDrive, which develops Libby, says the company has been lobbying Congress and state legislatures for library funding. “What we are consistently hearing is that there is no data or evidence suggesting that federal funds allocated through the IMLS are being misused,” Potash tells WIRED. “In fact, these funds are essential for delivering vital services, often to the most underserved and vulnerable populations.”
Anthony Chow, director of the School of Information at San José State University in California and president-elect of the state library association, tells WIRED that Monday was the deadline to submit receipts for several Native American libraries he says he’d been supporting in their purchase of nearly 54,000 children’s books using IMLS funds. Five tribes, according to Chow, could lose out on a total of about $189,000 in reimbursements. “There is no contingency,” Chow says. “I don’t think any one of us ever thought we would get to this point.”
Managers at IMLS informed their teams on Monday that the work stoppage was in response to a recent executive order issued by Trump that called for reducing the operations of the agency to the bare minimum required by law.
Trump made a number of other unsuccessful attempts to defund the IMLS during his first term. The White House described its latest effort as a necessary part of “eliminating waste and reducing government overreach.” But the president himself has said little about what specifically concerns him about funding libraries; a separate order he signed recently described federally supported Smithsonian museums as peddling “divisive narratives that distort our shared history.”
US libraries and museums receive support from many sources, including public donations and funding from other federal agencies. But IMLS is “the single largest source of critical federal funding for libraries,” according to the Chief Officers of State Library Agencies advocacy group. Libraries and museums in rural areas are particularly reliant on federal funding, according to some library employees and experts.
Systems in big metros such as Los Angeles County and New York City libraries receive only a small fraction of their budget from the IMLS, according to recent internal memos seen by WIRED, which were issued in response to Trump’s March 14 executive order. "For us, it was more a source of money to innovate with or try out new programs,” says a current employee at the New York Public Library, who asked to remain anonymous because they aren’t authorized to speak to the press.
But the loss of IMLS funds could still have consequences in big cities. A major public library system in California is assembling an internal task force to advocate on behalf of the library system with outside donors, according to a current employee who wasn’t authorized to speak about the effort publicly. They say philanthropic organizations that support their library system are already beginning to spend more conservatively, anticipating they may need to fill funding gaps at libraries in areas more dependent on federal dollars.
Some IMLS programs also require states to provide matching funding, and legislatures may be disincentivized to offer support if the federal money disappears, further hampering library and museum budgets, the IMLS employee says.
The IMLS was created by a 1996 law passed by Congress and has historically received bipartisan support. But some conservative groups and politicians have expressed concern that libraries provide public access to content they view as inappropriate, including pornography and books on topics such as transgender people and racial minorities. In February, following a Trump order, schools for kids on overseas military bases restricted access to books “potentially related to gender ideology or discriminatory equity ideology topics.”
Last week, a bipartisan group of five US senators led by Jack Reed of Rhode Island urged the Trump administration to follow through on the IMLS grants that Congress had authorized for this year. "We write to remind the administration of its obligation to faithfully execute the provisions of the law," the senators wrote.
Ultimately, the fate of the IMLS could be decided in a showdown between Trump officials, Congress, and the federal courts. With immediate resolution unlikely, experts say museums and libraries unable to make up for lost reimbursements will likely have to scale back services.
11 notes
·
View notes
Text
Best MBA Colleges in Delhi NCR under IP University—RDIAS Leading with Industry-Focused Programs and Great Placements
Pursuing an MBA in Delhi NCR under Guru Gobind Singh Indraprastha University (GGSIPU) is an excellent choice for students aspiring to pursue a successful career in business and management. Among the top MBA colleges in Delhi NCR, Rukmini Devi Institute of Advanced Studies (RDIAS) is a premier institute offering an industry-aligned curriculum, state-of-the-art infrastructure, and excellent placement opportunities.

Why Choose RDIAS for an MBA under IP University?
RDIAS, affiliated to IP University, offers a comprehensive MBA program designed to develop analytical, leadership, and decision-making skills in students. The institute integrates experiential learning through case studies, live projects, and internships, giving students practical exposure to real-world business challenges.
Industry-focused curriculum
RDIAS offers a dynamic and updated curriculum aligned with industry trends. Subjects such as marketing, finance, human resource management, and business analytics are taught with a focus on practical implementation. The learning approach includes:
Case study analysis to develop problem-solving skills.
Simulations and group discussions to enhance decision-making abilities.
Workshops and certification in emerging business areas such as digital marketing and data analytics.
Exceptional placement assistance
RDIAS has a dedicated placement cell that collaborates with top recruiters across various industries. The placement record is impressive, with students securing roles in leading companies such as Deloitte, KPMG, Infosys, HDFC Bank, and Wipro. The placement cell provides:
Resume-building assistance and mock interviews.
Pre-placement training to develop soft skills and business acumen.
Networking opportunities with alumni and industry leaders.
Experiential learning through internships and industry exposure
To bridge the gap between academia and industry, RDIAS integrates internships and live projects as a mandatory part of its MBA curriculum. Students get to experience the following:
Corporate internships with reputed firms.
Industrial visits to understand business operations first-hand.
Guest lectures by industry experts from companies like Google, Amazon, and Tata Group.
State-of-the-art infrastructure and learning facilities
The college offers world-class infrastructure with modern classrooms, a well-equipped library, computer labs with advanced business analytics software, and seminar halls for events. The smart learning environment enhances academic engagement and overall student development.
Strong alumni network and career growth opportunities
RDIAS has an extensive alumni network that helps students in career progression through mentorship programs, industry connections, and placement referrals. The institute encourages students to participate in the following:
Entrepreneurship development programs for aspiring business leaders.
Organize festivals and competitions to develop strategic thinking.
Global exchange programs to gain international business insights.
Conclusion
For students looking for the best MBA colleges in Delhi NCR under IP University, RDIAS is the top choice due to its industry-oriented education, exceptional faculty, practical teaching approach, and excellent placements. The institute prepares students for corporate jobs and leadership roles in the competitive business world. If you aspire to pursue an MBA in Delhi NCR, RDIAS should be your priority for a successful and rewarding career.
3 notes
·
View notes
Text
Fowtools - Silver
GUIDs, or Globally Unique Identifiers, are 128-bit numbers that are generated to ensure uniqueness in various applications. They are also referred to as UUIDs, or Universally Unique Identifiers. The purpose of generating GUIDs is to provide a unique identification number that can be used to identify resources such as people, files, web pages, and even colors. Unlike regular registration numbers, which start counting at 1 and can overlap, guid generator in a way that ensures their uniqueness. The use of GUIDs has become increasingly popular in software development, where unique identification numbers are essential for efficient data management. There are different methods of generating GUIDs. One method is random generation, where the system's random-number generator is used to create a 128-bit number. Another method is time-based generation, where a GUID is created based on the current time. Additionally, hardware-based generation involves using a combination of hardware-based information, such as the MAC address, to generate a GUID. These methods ensure that GUIDs are unique and can be used for efficient data management. GUIDs have numerous applications in software development. They are commonly used in enterprise software development in languages such as C# and Java. In.NET Core, GUIDs are generated by creating a random number of 128 bits and performing a couple of bitwise operations. GUIDs are also used to identify hardware, software, and network resources. Moreover, almost all major programming languages have built-in libraries to generate GUIDs, making it easy for programmers to ensure uniqueness in their applications. The use of GUIDs has become essential in modern software development, where efficient data management is crucial for the success of any project.
297 notes
·
View notes
Text
Why Sabaragamuwa University is a Great Choice.
Sabaragamuwa University of Sri Lanka (SUSL) is increasingly recognized for its technological advancement and innovation-driven environment, making it one of the leading universities in Sri Lanka in terms of technology. Here are the key reasons why SUSL stands out technologically.

Here’s why SUSL stands out as a technological powerhouse among Sri Lankan universities:
🔧1. Faculty of Technology
SUSL established a dedicated Faculty of Technology to meet the demand for tech-skilled graduates. It offers degree programs such as:
BTech in Information and Communication Technology
BTech in Engineering Technology
These programs combine practical experience in labs, workshops and real-world projects with a strong theoretical foundation.
🖥️2. Advanced IT Infrastructure
SUSL has modern computer labs, smart classrooms, and high-speed internet access across campus.
A robust Learning Management System (LMS) supports online learning and hybrid education models.
Students and lecturers use tools like Moodle, Zoom, and Google Classroom effectively.
🤖 3. Innovation & AI Research Support
SUSL promotes AI, Machine Learning, IoT, and Data Science in student research and final-year projects.
Competitions like Hackathons and Innovative Research Symposia encourage tech-driven solutions.
Students develop apps, smart systems, and automation tools (e.g., Ceylon Power Tracker project).
🌐 4. Industry Collaboration and Internships
SUSL connects students with the tech industry through:
Internships at leading tech firms
Workshops led by industry experts
Collaborative R&D projects with government and private sector entities
These connections help students gain hands-on experience in areas such as software engineering, networking, and data analytics that make them highly employable after graduation.
💡 5. Smart Campus Initiatives
SUSL is evolving into a Smart University, introducing systems that streamline academic life:
Digital student portals
Online registration and results systems
E-library and remote resource access
Campus Wi-Fi for academic use
These initiatives improve the student experience and create an efficient, technology-enabled environment.
🎓 6. Research in Emerging Technologies
The university is involved in pioneering research across emerging technological fields, including:
Agricultural tech (AgriTech)
Environmental monitoring using sensors
Renewable energy systems
Students and faculty publish research in international journals and participate in global tech events.
🏆 7. Recognition in National Competitions
SUSL students often reach fina rounds or win national competitions in coding, robotics, AI, and IoT innovation.
Faculty members are invited as tech advisors and conference speakers, reinforcing the university's expertise.
Sabaragamuwa University is actively shaping the future not only with technology, but by integrating technology into education, research and operations. This makes it a technological leader among Sri Lankan Universities. Visit the official university site here: Home | SUSL
2 notes
·
View notes
Text
Mini React.js Tips #2 | Resources ✨
Continuing the #mini react tips series, it's time to understand what is going on with the folders and files in the default React project - they can be a bit confusing as to what folder/file does what~!
What you'll need:
know how to create a React project >> click
already taken a look around the files and folders themselves

What does the file structure look like?
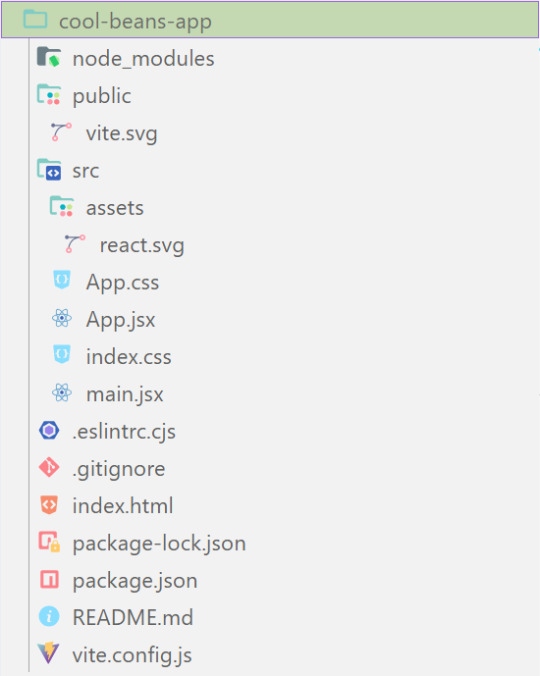

✤ node_modules folder: contains all the dependencies and packages (tools, resources, code, or software libraries created by others) needed for your project to run properly! These dependencies are usually managed by a package manager, such as npm (Node Package Manager)!
✤ public folder: Holds static assets (files that don't change dynamically and remain fixed) that don't require any special processing before using them! These assets are things like images, icons, or files that can be used directly without going through any additional steps.

✤ src folder: This is where your main source code resides. 'src' is short for source.
✤ assets folder: This folder stores static assets such as images, logos, and similar files. This folder is handy for organizing and accessing these non-changing elements in your project.
✤ App.css: This file contains styles specific to the App component (we will learn what 'components' are in React in the next tips post~!).
✤ App.jsx: This is the main component of your React application. It's where you define the structure and behavior of your app. The .jsx extension means the file uses a mixture of both HTML and JavaScript - open the file and see for yourself~!
✤ index.css: This file contains global styles that apply to the entire project. Any styles defined in this file will be applied universally across different parts of your project, providing a consistent look and feel.
✤ main.jsx: This is the entry point of your application! In this file, the React app is rendered, meaning it's the starting point where the React components are translated into the actual HTML elements displayed in the browser. Would recommend not to delete as a beginner!!

✤ .eslintrc.cjs: This file is the ESLint configuration. ESLint (one of the dependencies installed) is a tool that helps maintain coding standards and identifies common errors in your code. This configuration file contains rules and settings that define how ESLint should analyze and check your code.
✤ .gitignore: This file specifies which files and folders should be ignored by Git when version-controlling your project. It helps to avoid committing unnecessary files. The node_modules folder is typically ignored.
✤ index.html: This is the main HTML file that serves as the entry point for your React application. It includes the necessary scripts and links to load your app.
✤ package.json: A metadata file for your project. It includes essential information about the project, such as its name, version, description, and configuration details. Also, it holds a list of dependencies needed for the project to run - when someone else has the project on their local machine and wants to set it up, they can use the information in the file to install all the listed dependencies via npm install.
✤ package-lock.json: This file's purpose is to lock down and record the exact versions of each installed dependency/package in your project. This ensures consistency across different environments when other developers or systems install the dependencies.
✤ README.md: This file typically contains information about your project, including how to set it up, use it, and any other relevant details.
✤ vite.config.js: This file contains the configuration settings for Vite, the build tool used for this React project. It may include options for development and production builds, plugins, and other build-related configurations.

Congratulations! You know what the default folders and files do! Have a play around and familiarise yourself with them~!
BroCode’s 'React Full Course for Free’ 2024 >> click
React Official Website >> click
React's JSX >> click
The basics of Package.json >> click
Previous Tip: Tip #1 Creating The Default React Project >> click
Stay tuned for the other posts I will make on this series #mini react tips~!
#mini react tips#my resources#resources#codeblr#coding#progblr#programming#studyblr#studying#javascript#react.js#reactjs#coding tips#coding resources
25 notes
·
View notes
Text
J.4.7 What about the communications revolution?
Another important factor working in favour of anarchists is the existence of a sophisticated global communications network and a high degree of education and literacy among the populations of the core industrialised nations. Together these two developments make possible nearly instantaneous sharing and public dissemination of information by members of various progressive and radical movements all over the globe — a phenomenon that tends to reduce the effectiveness of repression by central authorities. The electronic-media and personal-computer revolutions also make it more difficult for elitist groups to maintain their previous monopolies of knowledge. Copy-left software and text, user-generated and shared content, file-sharing, all show that information, and its users, reaches its full potential when it is free. In short, the advent of the Information Age is potentially extremely subversive.
The very existence of the Internet provides anarchists with a powerful argument that decentralised structures can function effectively in a highly complex world. For the net has no centralised headquarters and is not subject to regulation by any centralised regulatory agency, yet it still manages to function effectively. Moreover, the net is also an effective way of anarchists and other radicals to communicate their ideas to others, share knowledge, work on common projects and co-ordinate activities and social struggle. By using the Internet, radicals can make their ideas accessible to people who otherwise would not come across anarchist ideas. In addition, and far more important than anarchists putting their ideas across, the fact is that the net allows everyone with access to express themselves freely, to communicate with others and get access (by visiting webpages and joining mailing lists and newsgroups) and give access (by creating webpages and joining in with on-line arguments) to new ideas and viewpoints. This is very anarchistic as it allows people to express themselves and start to consider new ideas, ideas which may change how they think and act.
Obviously we are aware that the vast majority of people in the world do not have access to telephones, never mind computers, but computer access is increasing in many countries, making it available, via work, libraries, schools, universities, and so on to more and more working class people.
Of course there is no denying that the implications of improved communications and information technology are ambiguous, implying Big Brother as well the ability of progressive and radical movements to organise. However, the point is only that the information revolution in combination with the other social developments could (but will not necessarily) contribute to a social paradigm shift. Obviously such a shift will not happen automatically. Indeed, it will not happen at all unless there is strong resistance to governmental and corporate attempts to limit public access to information, technology (e.g. encryption programs), censor peoples’ communications and use of electronic media and track them on-line.
This use of the Internet and computers to spread the anarchist message is ironic. The rapid improvement in price-performance ratios of computers, software, and other technology today is often used to validate the faith in free market capitalism but that requires a monumental failure of historical memory as not just the Internet but also the computer represents a spectacular success of public investment. As late as the 1970s and early 1980s, according to Kenneth Flamm’s Creating the Computer, the federal government was paying for 40 percent of all computer-related research and 60 to 75 percent of basic research. Even such modern-seeming gadgets as video terminals, the light pen, the drawing tablet, and the mouse evolved from Pentagon-sponsored research in the 1950s, 1960s and 1970s. Even software was not without state influence, with databases having their root in US Air Force and Atomic Energy Commission projects, artificial intelligence in military contracts back in the 1950s and airline reservation systems in 1950s air-defence systems. More than half of IBM’s Research and Development budget came from government contracts in the 1950s and 1960s.
The motivation was national security, but the result has been the creation of comparative advantage in information technology for the United States that private firms have happily exploited and extended. When the returns were uncertain and difficult to capture, private firms were unwilling to invest, and government played the decisive role. And not for want of trying, for key players in the military first tried to convince businesses and investment bankers that a new and potentially profitable business opportunity was presenting itself, but they did not succeed and it was only when the market expanded and the returns were more definite that the government receded. While the risks and development costs were socialised, the gains were privatised. All of which make claims that the market would have done it anyway highly unlikely.
Looking beyond state aid to the computer industry we discover a “do-it-yourself” (and so self-managed) culture which was essential to its development. The first personal computer, for example, was invented by amateurs who wanted their own cheap machines. The existence of a “gift” economy among these amateurs and hobbyists was a necessary precondition for the development of PCs. Without this free sharing of information and knowledge, the development of computers would have been hindered and so socialistic relations between developers and within the working environment created the necessary conditions for the computer revolution. If this community had been marked by commercial relations, the chances are the necessary breakthroughs and knowledge would have remained monopolised by a few companies or individuals, so hindering the industry as a whole.
Encouragingly, this socialistic “gift economy” is still at the heart of computer/software development and the Internet. For example, the Free Software Foundation has developed the General Public Licence (GPL). GPL, also know as
“copyleft”, uses copyright to ensure that software remains free. Copyleft ensures that a piece of software is made available to everyone to use and modify as they desire. The only restriction is that any used or modified copyleft material must remain under copyleft, ensuring that others have the same rights as you did when you used the original code. It creates a commons which anyone may add to, but no one may subtract from. Placing software under GPL means that every contributor is assured that she, and all other uses, will be able to run, modify and redistribute the code indefinitely. Unlike commercial software, copyleft code ensures an increasing knowledge base from which individuals can draw from and, equally as important, contribute to. In this way everyone benefits as code can be improved by everyone, unlike commercial code.
Many will think that this essentially anarchistic system would be a failure. In fact, code developed in this way is far more reliable and sturdy than commercial software. Linux, for example, is a far superior operating system than DOS precisely because it draws on the collective experience, skill and knowledge of thousands of developers. Apache, the most popular web-server, is another freeware product and is acknowledged as the best available. The same can be said of other key web-technologies (most obviously PHP) and projects (Wikipedia springs to mind, although that project while based on co-operative and free activity is owned by a few people who have ultimate control). While non-anarchists may be surprised, anarchists are not. Mutual aid and co-operation are beneficial in the evolution of life, why not in the evolution of software? For anarchists, this “gift economy” at the heart of the communications revolution is an important development. It shows both the superiority of common development as well as the walls built against innovation and decent products by property systems. We hope that such an economy will spread increasingly into the “real” world.
Another example of co-operation being aided by new technologies is Netwar. This refers to the use of the Internet by autonomous groups and social movements to co-ordinate action to influence and change society and fight government or business policy. This use of the Internet has steadily grown over the years, with a Rand corporation researcher, David Ronfeldt, arguing that this has become an important and powerful force (Rand is, and has been since its creation in 1948, a private appendage of the military industrial complex). In other words, activism and activists’ power and influence has been fuelled by the advent of the information revolution. Through computer and communication networks, especially via the Internet, grassroots campaigns have flourished, and the most importantly, government elites have taken notice.
Ronfeldt specialises in issues of national security, especially in the areas of Latin American and the impact of new informational technologies. Ronfeldt and another colleague coined the term
“netwar” in a Rand document entitled “Cyberwar is Coming!”. Ronfeldt’s work became a source of discussion on the Internet in mid-March 1995 when Pacific News Service correspondent Joel Simon wrote an article about Ronfeldt’s opinions on the influence of netwars on the political situation in Mexico after the Zapatista uprising. According to Simon, Ronfeldt holds that the work of social activists on the Internet has had a large influence — helping to co-ordinate the large demonstrations in Mexico City in support of the Zapatistas and the proliferation of EZLN communiqués across the world via computer networks. These actions, Ronfeldt argues, have allowed a network of groups that oppose the Mexican Government to muster an international response, often within hours of actions by it. In effect, this has forced the Mexican government to maintain the facade of negotiations with the EZLN and has on many occasions, actually stopped the army from just going in to Chiapas and brutally massacring the Zapatistas.
Given that Ronfeldt was an employee of the Rand Corporation his comments indicate that the U.S. government and its military and intelligence wings are very interested in what the Left is doing on the Internet. Given that they would not be interested in this if it were not effective, we can say that this use of the “Information Super-Highway” is a positive example of the use of technology in ways un-planned of by those who initially developed it (let us not forget that the Internet was originally funded by the U.S. government and military). While the internet is being hyped as the next big marketplace, it is being subverted by activists — an example of anarchistic trends within society worrying the powers that be.
A good example of this powerful tool is the incredible speed and range at which information travels the Internet about events concerning Mexico and the Zapatistas. When Alexander Cockburn wrote an article exposing a Chase Manhattan Bank memo about Chiapas and the Zapatistas in Counterpunch, only a small number of people read it because it is only a newsletter with a limited readership. The memo, written by Riordan Roett, argued that “the [Mexican] government will need to eliminate the Zapatistas to demonstrate their effective control of the national territory and of security policy”. In other words, if the Mexican government wants investment from Chase, it would have to crush the Zapatistas. This information was relatively ineffective when just confined to print but when it was uploaded to the Internet, it suddenly reached a very large number of people. These people in turn co-ordinated protests against the U.S and Mexican governments and especially Chase Manhattan. Chase was eventually forced to attempt to distance itself from the Roett memo that it commissioned. Since then net-activism has grown.
Ronfeldt’s research and opinion should be flattering for the Left. He is basically arguing that the efforts of activists on computers not only has been very effective (or at least has that potential), but more importantly, argues that the only way to counter this work is to follow the lead of social activists. Activists should understand the important implications of Ronfeldt’s work: government elites are not only watching these actions (big surprise) but are also attempting to work against them. Thus Netwars and copyleft are good examples of anarchistic trends within society, using communications technology as a means of co-ordinating activity across the world in a libertarian fashion for libertarian goals.
#community building#practical anarchy#practical anarchism#anarchist society#practical#faq#anarchy faq#revolution#anarchism#daily posts#communism#anti capitalist#anti capitalism#late stage capitalism#organization#grassroots#grass roots#anarchists#libraries#leftism#social issues#economy#economics#climate change#climate crisis#climate#ecology#anarchy works#environmentalism#environment
18 notes
·
View notes
Text
MCA University In Uttar Pradesh
Navigating the Landscape: Choosing a Distance MCA University in Uttar Pradesh

Uttar Pradesh, India's heartland, is witnessing a surge in demand for upskilling and professional development. With the IT industry boom, the Master of Computer Applications (MCA) program emerges as a sought-after option, especially in its convenient distance learning format. However, navigating the plethora of universities offering distance MCA in Uttar Pradesh can be daunting. This comprehensive guide aims to equip you with the knowledge and insights to make an informed decision.
Factors to Consider When Choosing a Distance MCA University:
University Recognition and Accreditation:
Prioritize universities recognized by the University Grants Commission (UGC) and accredited by the National Assessment and Accreditation Council (NAAC). These accreditations ensure quality education and adherence to national standards. Look for additional accreditations specific to distance learning programs, such as the Distance Education Bureau (DEB) recognition.
Reputation and Ranking:
Research the university's reputation within the academic and professional circles. Check for rankings in renowned publications like NIRF and The Week, particularly for their distance learning programs. Alumni reviews and feedback can also provide valuable insights.
Curriculum and Course Structure:
Evaluate the curriculum's comprehensiveness and relevance to current industry trends. Ensure it encompasses core subjects like computer networks, software engineering, database management, and emerging technologies like Artificial Intelligence and Machine Learning. Check for the flexibility of the course structure and the delivery format (online, offline, blended).
Faculty and Learning Resources:
The quality of faculty plays a crucial role in a distance learning program. Look for universities with experienced, qualified faculty with industry expertise. Assess the availability of quality learning resources like study materials, online lectures, e-libraries, and interactive platforms.
Admission Process and Fees:
Analyze the eligibility criteria, entrance exams (if any), and overall admission process. Compare the fee structure, considering not only the program cost but also additional expenses like study materials, exam fees, and technology requirements. Look for scholarship opportunities and financial aid options.
Placement Assistance and Career Support:
Evaluate the university's track record in providing placement assistance for distance MCA graduates. Assess the strength of their industry connections, career counseling services, and alumni network support.
Top Distance MCA Universities in Uttar Pradesh:
Swami Vivekanand Subharti University (SVSU): Renowned for its academic excellence and industry-oriented curriculum, SVSU offers a well-structured distance MCA program with UGC, DEB, and NAAC accreditations..
Amity University Distance Education: Part of the renowned Amity Education Group, this university leverages its strong industry connections and offers a practical, interactive distance MCA program with NAAC accreditation.
Rajarshi Tandon Open University (RTOU): Established by the Uttar Pradesh government, RTOU is a reputed state-run university known for its affordable and accessible distance MCA program with UGC recognition.
Jain University: Recognized by UGC and AICTE, Jain University offers a well-designed distance MCA program with a focus on emerging technologies and flexible learning options.
Online Manipal: A constituent unit of Manipal Academy of Higher Education (MAHE), Online Manipal boasts an NAAC 'A' grade accreditation and offers a comprehensive distance MCA program with a blended learning approach.
Emerging Trends in Distance MCA Education:
Industry-Integrated Learning: Universities are increasingly collaborating with industry partners to provide internship opportunities, live projects, and industry-specific workshops as part of their distance MCA programs.
Focus on Emerging Technologies: The curriculum is evolving to address the growing demand for skills in Artificial Intelligence, Machine Learning, Cloud Computing, and Data Science.
Virtual Reality and Augmented Reality (VR/AR): VR/AR simulations are being implemented to enhance the learning experience and provide practical exposure in specific technology domains.
Personalized Learning: Adaptive learning platforms and AI-powered tools are being used to personalize the learning journey for each student, adapting to their individual pace and learning styles.
Concluding Thoughts:
Choosing the right distance MCA university in Uttar Pradesh requires careful consideration of your career goals, learning preferences, and financial constraints. By prioritizing UGC recognition, strong curriculum, experienced faculty, and career support, you can choose a program that equips you with the necessary skills and knowledge to succeed in the dynamic IT landscape. Remember, the distance learning format doesn't compromise on quality; with research and dedication, you can unlock your full potential and embark on a fulfilling IT career from the comfort of your own home.
For MCA colleges in india with low fees ,visit on :-
#Distance MCA University In Uttar Pradesh#Top Distance MCA University In Uttar Pradesh#MCA University In Uttar Pradesh#MCA colleges In UP
10 notes
·
View notes
Text
Discover Excellence in Education at Himalayan Institute of Technology, Dehradun
Are you searching for a prestigious institution to pursue higher education? Look no further than the Himalayan Institute of Technology (HIT) in Dehradun. Nestled in the picturesque landscapes of the Himalayas, HIT offers an array of courses designed to provide students with a comprehensive and practical learning experience. With affiliations to both HNGBU and SDSU universities, HIT stands as a beacon of quality education and professional development.
Explore Our Diverse Course Offerings
At Himalayan Institute of Technology, we offer a variety of undergraduate programs tailored to meet the needs of today’s dynamic job market. Our courses include:
Bachelor of Commerce (B.Com)
Our B.Com program is designed to equip students with foundational knowledge in commerce, accounting, finance, and business management. With a focus on practical skills and industry insights, our graduates are well-prepared for careers in various sectors, including banking, finance, and corporate management.
Bachelor of Business Administration (BBA)
The BBA program at HIT focuses on developing leadership and entrepreneurial skills. Students gain a deep understanding of business operations, strategic management, and organizational behavior. Our BBA graduates are highly sought after by top companies and startups alike.
Bachelor of Hotel Management (HM)
Our HM program is perfect for those looking to excel in the hospitality industry. With comprehensive training in hotel operations, food and beverage management, and customer service, students are prepared to take on key roles in hotels, resorts, and other hospitality enterprises.
Bachelor of Computer Applications (BCA)
The BCA course at HIT is designed for students interested in the world of information technology. Covering topics like programming, software development, and database management, this program prepares students for successful careers in IT and software development.
Bachelor of Science in Information Technology (B.Sc IT)
Our B.Sc IT program provides students with in-depth knowledge of computer systems, networking, and information security. This course is ideal for those aiming to become IT professionals, system administrators, or cybersecurity experts.
Why Choose Himalayan Institute of Technology?
Affiliated with HNGBU and SDSU Universities: Our affiliations with Hemwati Nandan Bahuguna Garhwal University (HNGBU) and Sri Dev Suman Uttarakhand University (SDSU) ensure that our programs meet high academic standards and provide students with recognized qualifications.
Experienced Faculty: Our team of highly qualified and experienced faculty members are dedicated to providing students with the best education and guidance.
State-of-the-Art Facilities: HIT boasts modern classrooms, well-equipped laboratories, and a comprehensive library to support students in their academic pursuits.
Industry Connections: We maintain strong ties with various industries, offering students opportunities for internships, placements, and hands-on experience.
Holistic Development: At HIT, we emphasize the overall development of our students, encouraging participation in extracurricular activities, sports, and cultural events.
Join Us at Himalayan Institute of Technology
Embark on a journey of academic excellence and professional success with the Himalayan Institute of Technology, Dehradun. Visit our website at http://hitdoon.com for more information on admissions, courses, and campus life. Discover why HIT is the preferred choice for aspiring professionals in commerce, business administration, hotel management, computer applications, and information technology.
Choose HIT and take the first step towards a promising future.
2 notes
·
View notes
Text
From Novice to Java Pro: A Step-by-Step Learning Journey
Java programming, renowned for its platform independence and versatility, is a sought-after language in the world of software development. It's the language behind countless web applications, mobile apps, game development, and more. This blog serves as your comprehensive guide to embarking on a journey to learn and master Java programming. We'll walk you through the basics of programming, Java's syntax and structure, the essential tools and libraries, and the importance of practice.

The Path to Java Proficiency:
1. Understand the Basics of Programming:
Prior Experience: If you're new to programming, it's crucial to start with the foundational concepts. Variables, data types, control structures (if-else, loops), and functions are universal principles that you need to understand before delving into any programming language, including Java.
What to Learn: Begin by grasping the basics of programming logic and problem-solving. Familiarize yourself with concepts like variables (to store data), data types (to specify the kind of data), and control structures (to make decisions and loop through actions). These concepts serve as the building blocks for Java programming.
2. Java Syntax and Structure:
Prior Experience: As you delve into Java, you'll find that it's an object-oriented language with its unique syntax and structure. While prior programming experience is beneficial, it's not a prerequisite. You can start with Java as your first language.
What to Learn: Java introduces you to classes and objects. Classes are blueprints for creating objects, which are instances of classes. Java is known for its object-oriented nature, where you'll encounter concepts like inheritance (creating new classes based on existing ones), polymorphism (objects of different classes can be treated as objects of the same class), encapsulation (data hiding), and abstraction (simplifying complex reality by modeling classes based on real-world objects).
3. Get Your Hands on a Compiler and IDE:
Prior Experience: No prior experience is required to set up your Java development environment.
What to Learn: To start writing and running Java code, you'll need to install a Java Development Kit (JDK), which includes the Java compiler (javac). This kit allows you to compile your source code into bytecode that the Java Virtual Machine (JVM) can execute. Additionally, install an Integrated Development Environment (IDE) like Eclipse, IntelliJ IDEA, or NetBeans. These IDEs provide a user-friendly interface for coding, debugging, and managing your Java projects.
4. Learn the Java Standard Library:
Prior Experience: No specific prior experience is necessary, but familiarity with basic programming concepts is beneficial.
What to Learn: Java's power lies in its extensive standard library. This library includes pre-built classes and packages that simplify common programming tasks. For example, you can utilize classes in the java.io package to handle file input and output. You'll explore the java.lang package, which provides fundamental classes like String and Integer. Understanding this library is crucial for performing operations like file handling, string manipulation, and working with data structures.
5. Practice, Practice, Practice:
Prior Experience: No prior experience is required. This stage is suitable for beginners and those with basic programming knowledge.
What to Learn: The key to mastering Java or any programming language is practice. Apply the knowledge you've gained by working on small coding projects. Start with simple programs and gradually move on to more complex tasks. Solving programming challenges, such as those on websites like LeetCode or HackerRank, is an excellent way to put your skills to the test. Build simple applications to get hands-on experience in real-world scenarios.
6. Join Java Communities:
Prior Experience: No prior experience is needed to join Java communities.
What to Learn: Engage with Java communities and forums, such as Stack Overflow or Reddit's r/java. These platforms provide a space to ask questions, seek advice, and learn from experienced Java developers. You can also contribute by answering questions and sharing your knowledge.
7. Enroll in Java Courses:
Prior Experience: Enrolling in Java courses is suitable for learners of all levels, from beginners to advanced users.
What to Learn: ACTE Technologies offers comprehensive Java training programs that cater to a diverse range of learners. These programs are designed to provide hands-on experience and real-world examples, ensuring that you gain practical skills in Java programming.

In your journey to master Java programming, structured training plays a pivotal role. ACTE Technologies is a trusted partner, offering Java training programs for learners at all levels. Whether you're a beginner taking your first steps in Java or an experienced programmer seeking to expand your skill set, they can provide the guidance and resources needed to excel in the world of Java development. Consider exploring their Java courses to kickstart or enhance your Java programming journey. Java programming is a versatile and essential language, and mastering it is a rewarding journey. With dedication, practice, and structured training, you can become a proficient Java developer. Institutions like ACTE Technologies offer valuable resources and courses to accelerate your learning process, making your journey to Java mastery even more efficient.
7 notes
·
View notes
Text
This Week in Rust 541
Hello and welcome to another issue of This Week in Rust! Rust is a programming language empowering everyone to build reliable and efficient software. This is a weekly summary of its progress and community. Want something mentioned? Tag us at @ThisWeekInRust on Twitter or @ThisWeekinRust on mastodon.social, or send us a pull request. Want to get involved? We love contributions.
This Week in Rust is openly developed on GitHub and archives can be viewed at this-week-in-rust.org. If you find any errors in this week's issue, please submit a PR.
Updates from Rust Community
Official
Announcing Rust 1.77.1
Changes to u128/i128 layout in 1.77 and 1.78
Newsletters
This Week In Bevy: 2d Lighting, Particle Systems, Meshlets, and more
Project/Tooling Updates
Dioxus 0.5: Signal Rewrite, Remove lifetimes, CSS Hotreloading, and more!
EtherCrab 0.4.0: Pure Rust EtherCAT, now with Distributed Clocks
nethsm 0.1.0 - first release for this high level library for the Nitrokey NetHSM
BugStalker v0.1.3 released - first release of rust debugger
git-cliff 2.2.0 is released! (highly customizable changelog generator)
Observations/Thoughts
On Reusing Arc and Rc in Rust
Who killed the network switch?
Xr0 Makes C Safer than Rust
Easy Mode Rust
Bashing Bevy To Bait Internet Strangers Into Improving My Code
Conway's Game of Life Through Time
Functions Everywhere, Only Once: Writing Functions for the Everywhere Computer
Rust Bytes: Is Rust the Future of JavaScript Tooling?
Explaining the internals of async-task from the ground up
Programming ESP32 with Rust: OTA firmware update
Fast Development In Rust, Part 2
Rust Walkthroughs
Modelling Universal Domain Types in Rust
[video] developerlife.com - Get started with unit testing in Rust
Research
Rust Digger: More than 14% of crates configure rustfmt. 35 Have both rustfmt.toml and .rustfmt.toml
Miscellaneous
Building a Managed Postgres Service in Rust: Part 1
Beware of the DashMap deadlock
Embedded Rust Bluetooth on ESP: BLE Client
Rust Unit and Integration Testing in RustRover
[podcast] cargo-semver-checks with Predrag Gruevski — Rustacean Station
[video] Data Types - Part 3 of Idiomatic Rust in Simple Steps
[video] Deconstructing WebAssembly Components by Ryan Levick @ Wasm I/O 2024
[video] Extreme Clippy for new Rust crates
[video] [playlist] Bevy GameDev Meetup #2 - March 2024
Building Stock Market Engine from scratch in Rust (I)
Crate of the Week
This week's crate is cargo-unfmt, a formatter that formats your code into block-justified text, which sacrifices some readability for esthetics.
Thanks to Felix Prasanna for the self-suggestion!
Please submit your suggestions and votes for next week!
Call for Testing
An important step for RFC implementation is for people to experiment with the implementation and give feedback, especially before stabilization. The following RFCs would benefit from user testing before moving forward:
No calls for testing were issued this week.
If you are a feature implementer and would like your RFC to appear on the above list, add the new call-for-testing label to your RFC along with a comment providing testing instructions and/or guidance on which aspect(s) of the feature need testing.
Call for Participation; projects and speakers
CFP - Projects
Always wanted to contribute to open-source projects but did not know where to start? Every week we highlight some tasks from the Rust community for you to pick and get started!
Some of these tasks may also have mentors available, visit the task page for more information.
greptimedb - Support specifying time ranges in the COPY FROM statement to avoid importing unwanted data
greptimedb - Support converting UNIX epoch numbers to specified timezone in to_timezone function
mirrord - Capability to modify the local listen address
mirrord - Fix all check-rust-docs warnings
Hyperswitch - [REFACTOR]: Remove Default Case Handling - Braintree
Hyperswitch - [REFACTOR]: Remove Default Case Handling - Fiserv
Hyperswitch - [REFACTOR]: Remove Default Case Handling - Globepay
If you are a Rust project owner and are looking for contributors, please submit tasks here.
CFP - Speakers
Are you a new or experienced speaker looking for a place to share something cool? This section highlights events that are being planned and are accepting submissions to join their event as a speaker.
* RustConf 2024 | Closes 2024-04-25 | Montreal, Canada | Event date: 2024-09-10 * RustLab 2024 | Closes 2024-05-01 | Florence, Italy | Event date: 2024-11-09 - 2024-11-11 * EuroRust 2024| Closes 2024-06-03 | Vienna, Austria & online | Event date: 2024-10-10 * Scientific Computing in Rust 2024| Closes 2024-06-14 | online | Event date: 2024-07-17 - 2024-07-19 * Conf42 Rustlang 2024 | Closes 2024-07-22 | online | Event date: 2024-08-22
If you are an event organizer hoping to expand the reach of your event, please submit a link to the submission website through a PR to TWiR.
Updates from the Rust Project
431 pull requests were merged in the last week
CFI: (actually) check that methods are object-safe before projecting their receivers to dyn Trait in CFI
CFI: abstract Closures and Coroutines
CFI: fix drop and drop_in_place
CFI: fix methods as function pointer cast
CFI: support calling methods on supertraits
add a CurrentGcx type to let the deadlock handler access TyCtxt
add basic trait impls for f16 and f128
add detection of (Partial)Ord methods in the ambiguous_wide_pointer_comparisons lint
add rust-lldb pretty printing for Path and PathBuf
assert that ADTs have the right number of args
codegen const panic messages as function calls
coverage: re-enable UnreachablePropagation for coverage builds
delegation: fix ICE on wrong Self instantiation
delegation: fix ICE on wrong self resolution
do not attempt to write ty::Err on binding that isn't from current HIR Owner
don't check match scrutinee of postfix match for unused parens
don't inherit codegen attrs from parent static
eagerly instantiate closure/coroutine-like bounds with placeholders to deal with binders correctly
eliminate UbChecks for non-standard libraries
ensure std is prepared for cross-targets
fix diagnostics for async block cloning
fixup parsing of rustc_never_type_options attribute
function ABI is irrelevant for reachability
improve example on inserting to a sorted vector to avoid shifting equal elements
in ConstructCoroutineInClosureShim, pass receiver by mut ref, not mut pointer
load missing type of impl associated constant from trait definition
make TyCtxt::coroutine_layout take coroutine's kind parameter
match ergonomics 2024: implement mutable by-reference bindings
match lowering: build the Place instead of keeping a PlaceBuilder around
match lowering: consistently merge simple or-patterns
match lowering: handle or-patterns one layer at a time
match lowering: sort Eq candidates in the failure case too
pattern analysis: Require enum indices to be contiguous
replace regions in const canonical vars' types with 'static in next-solver canonicalizer
require Debug for Pointee::Metadata
require DerefMut and DerefPure on deref!() patterns when appropriate
rework opaque type region inference
simplify proc macro bridge state
simplify trim-paths feature by merging all debuginfo options together
store segment and module in UnresolvedImportError
suggest associated type bounds on problematic associated equality bounds
suggest correct path in include_bytes!
use the Align type when parsing alignment attributes
warn against implementing Freeze
enable cargo miri test doctests
miri: avoid mutating the global environment
miri: cotrol stacked borrows consistency check with its own feature flag
miri: experiment with macOS M1 runners
miri: extern-so: give the version script a better name; show errors from failing to build the C lib
miri: speed up Windows CI
miri: tree Borrows: Make tree root always be initialized
don't emit load metadata in debug mode
avoid some unnecessary query invocations
stop doing expensive work in opt_suggest_box_span eagerly
stabilize ptr.is_aligned, move ptr.is_aligned_to to a new feature gate
stabilize unchecked_{add,sub,mul}
make {integer}::from_str_radix constant
optimize core::char::CaseMappingIter
implement Vec::pop_if
remove len argument from RawVec::reserve_for_push
less generic code for Vec allocations
UnixStream: override read_buf
num::NonZero::get can be 1 transmute instead of 2
fix error message for env! when env var is not valid Unicode
futures: make access inner of futures::io::{BufReader,BufWriter} not require inner trait bound
regex-syntax: accept {,n} as an equivalent to {0,n}
cargo add: Preserve comments when updating simple deps
cargo generate-lockfile: hold lock before querying index
cargo toml: Warn on unused workspace.dependencies keys on virtual workspaces
cargo fix: bash completion fallback in nounset mode
clippy: large_stack_frames: print total size and largest component
clippy: type_id_on_box: lint on any Box<dyn _>
clippy: accept String in span_lint* functions directly to avoid unnecessary clones
clippy: allow filter_map_identity when the closure is typed
clippy: allow manual_unwrap_or_default in const function
clippy: don't emit duplicated_attribute lint on "complex" cfgs
clippy: elide unit variables linted by let_unit and use () directly instead
clippy: fix manual_unwrap_or_default suggestion ignoring side-effects
clippy: fix suggestion for len_zero with macros
clippy: make sure checked type implements Try trait when linting question_mark
clippy: move box_default to style, do not suggest turbofishes
clippy: move mixed_attributes_style to style
clippy: new lint legacy_numeric_constants
clippy: restrict manual_clamp to const case, bring it out of nursery
rust-analyzer: add rust-analyzer.cargo.allTargets to configure passing --all-targets to cargo invocations
rust-analyzer: implement resolving and lowering of Lifetimes (no inference yet)
rust-analyzer: fix crate IDs when multiple workspaces are loaded
rust-analyzer: ADT hover considering only type or const len not lifetimes
rust-analyzer: check for client support of relative glob patterns before using them
rust-analyzer: lifetime length are not added in count of params in highlight
rust-analyzer: revert debug extension priorities
rust-analyzer: silence mismatches involving unresolved projections
rust-analyzer: use lldb when debugging with C++ extension on MacOS
rust-analyzer: pattern analysis: Use contiguous indices for enum variants
rust-analyzer: prompt the user to reload the window when enabling test explorer
rust-analyzer: resolve tests per file instead of per crate in test explorer
Rust Compiler Performance Triage
A pretty quiet week, with most changes (dropped from the report below) being due to continuing bimodality in the performance data. No particularly notable changes landed.
Triage done by @simulacrum. Revision range: 73476d49..3d5528c
1 Regressions, 2 Improvements, 5 Mixed; 0 of them in rollups 61 artifact comparisons made in total
Full report here
Approved RFCs
Changes to Rust follow the Rust RFC (request for comments) process. These are the RFCs that were approved for implementation this week:
Merge RFC 3543: patchable-function-entry
Final Comment Period
Every week, the team announces the 'final comment period' for RFCs and key PRs which are reaching a decision. Express your opinions now.
RFCs
No RFCs entered Final Comment Period this week.
Tracking Issues & PRs
Rust
[disposition: merge] Pass list of defineable opaque types into canonical queries
[disposition: merge] Document overrides of clone_from() in core/std
[disposition: merge] Tracking Issue for Seek::seek_relative
[disposition: merge] Tracking Issue for generic NonZero
[disposition: merge] Tracking Issue for cstr_count_bytes
[disposition: merge] privacy: Stabilize lint unnameable_types
[disposition: merge] Stabilize Wasm target features that are in phase 4 and 5
Cargo
[disposition: merge] feat(add): Stabilize MSRV-aware version req selection
New and Updated RFCs
[new] RFC: Add freeze intrinsic and related library functions
[new] RFC: Add a special TryFrom and Into derive macro, specifically for C-Style enums
[new] re-organise the compiler team
Upcoming Events
Rusty Events between 2024-04-03 - 2024-05-01 🦀
Virtual
2024-04-03 | Virtual (Cardiff, UK) | Rust and C++ Cardiff
Rust for Rustaceans Book Club: Chapter 4 - Error Handling
2024-04-03 | Virtual (Indianapolis, IN, US) | Indy Rust
Indy.rs - with Social Distancing
2024-04-04 | Virtual (Charlottesville, NC, US) | Charlottesville Rust Meetup
Crafting Interpreters in Rust Collaboratively
2024-04-09 | Virtual (Dallas, TX, US) | Dallas Rust
BlueR: a Rust Based Tool for Robust and Safe Bluetooth Control
2024-04-11 | Virtual + In Person (Berlin, DE) | OpenTechSchool Berlin + Rust Berlin
Rust Hack and Learn | Mirror: Rust Hack n Learn Meetup
2024-04-11 | Virtual (Nürnberg, DE) | Rust Nüremberg
Rust Nürnberg online
2024-04-15 & 2024-04-16 | Virtual | Mainmatter
Remote Workshop: Testing for Rust projects – going beyond the basics
2024-04-16 | Virtual (Dublin, IE) | Rust Dublin
A reverse proxy with Tower and Hyperv1
2024-04-16 | Virtual (Washinigton, DC, US) | Rust DC
Mid-month Rustful
2024-04-17 | Virtual (Vancouver, BC, CA) | Vancouver Rust
Rust Study/Hack/Hang-out
2024-04-18 | Virtual (Charlottesville, NC, US) | Charlottesville Rust Meetup
Crafting Interpreters in Rust Collaboratively
2024-04-25 | Virtual + In Person (Berlin, DE) | OpenTechSchool Berlin + Rust Berlin
Rust Hack and Learn | Mirror: Rust Hack n Learn Meetup
2024-04-30 | Virtual (Dallas, TX, US) | Dallas Rust
Last Tuesday
2024-05-01 | Virtual (Indianapolis, IN, US) | Indy Rust
Indy.rs - with Social Distancing
Africa
2024-04-05 | Kampala, UG | Rust Circle Kampala
Rust Circle Meetup
Europe
2024-04-10 | Cambridge, UK | Cambridge Rust Meetup
Rust Meetup Reboot 3
2024-04-10 | Cologne/Köln, DE | Rust Cologne
This Month in Rust, April
2024-04-10 | Manchester, UK | Rust Manchester
Rust Manchester April 2024
2024-04-10 | Oslo, NO | Rust Oslo
Rust Hack'n'Learn at Kampen Bistro
2024-04-11 | Bordeaux, FR | Rust Bordeaux
Rust Bordeaux #2 : Présentations
2024-04-11 | Reading, UK | Reading Rust Workshop
Reading Rust Meetup at Browns
2024-04-15 | Zagreb, HR | impl Zagreb for Rust
Rust Meetup 2024/04: Building cargo projects with NIX
2024-04-16 | Bratislava, SK | Bratislava Rust Meetup Group
Rust Meetup by Sonalake #5
2024-04-16 | Leipzig, DE | Rust - Modern Systems Programming in Leipzig
winnow/nom
2024-04-16 | Munich, DE + Virtual | Rust Munich
Rust Munich 2024 / 1 - hybrid
2024-04-17 | Bergen, NO | Hubbel kodeklubb
Lær Rust med Conways Game of Life
2024-04-20 | Augsburg, DE | Augsburger Linux-Infotag 2024
Augsburger Linux-Infotag 2024: Workshop Einstieg in Embedded Rust mit dem Raspberry Pico WH
2024-04-23 | Berlin, DE | Rust Berlin
Rust'n'Tell - Rust for the Web
2024-04-25 | Aarhus, DK | Rust Aarhus
Talk Night at MFT Energy
2024-04-25 | Berlin, DE | Rust Berlin
Rust and Tell
2024-04-27 | Basel, CH | Rust Basel
Fullstack Rust - Workshop #2
North America
2024-04-04 | Mountain View, CA, US | Mountain View Rust Meetup
Rust Meetup at Hacker Dojo
2024-04-04 | Portland, OR, US | PDXRust Meetup
Hack Night and First Post-Pandemic Meetup Restart
2024-04-09 | New York, NY, US | Rust NYC
Rust NYC Monthly Meetup
2024-04-10 | Boulder, CO, US | Boulder Rust Meetup
Rust Meetup: Better Builds w/ Flox + Hangs
2024-04-11 | Seattle, WA, US | Seattle Rust User Group
Seattle Rust User Group Meetup
2024-04-11 | Spokane, WA, US | Spokane Rust
Monthly Meetup: Topic TBD!
2024-04-15 | Somerville, MA, US | Boston Rust Meetup
Davis Square Rust Lunch, Apr 15
2024-04-16 | San Francisco, CA, US | San Francisco Rust Study Group
Rust Hacking in Person
2024-04-16 | Seattle, WA, US | Seattle Rust User Group
Seattle Rust User Group: Meet Servo and Robius Open Source Projects
2024-04-18 | Mountain View, CA, US | Mountain View Rust Meetup
Rust Meetup at Hacker Dojo
2024-04-24 | Austin, TX, US | Rust ATX
Rust Lunch - Fareground
2024-04-25 | Nashville, TN, US | Music City Rust Developers
Music City Rust Developers - Async Rust on Embedded
2024-04-26 | Boston, MA, US | Boston Rust Meetup
North End Rust Lunch, Apr 26
Oceania
2024-04-30 | Canberra, ACT, AU | Canberra Rust User Group
April Meetup
If you are running a Rust event please add it to the calendar to get it mentioned here. Please remember to add a link to the event too. Email the Rust Community Team for access.
Jobs
Please see the latest Who's Hiring thread on r/rust
Quote of the Week
Panstromek: I remember reading somewhere (probably here) that borrow checking has O(n^3) asymptotic complexity, relative to the size of the function.
Nadrieril: Compared to match exhaustiveness which is NP-hard and trait solving which is undecidable, a polynomial complexity feels refreshingly sane.
– Panstromek and Nadrieril on zulip
Thanks to Kevin Reid for the suggestion!
Please submit quotes and vote for next week!
This Week in Rust is edited by: nellshamrell, llogiq, cdmistman, ericseppanen, extrawurst, andrewpollack, U007D, kolharsam, joelmarcey, mariannegoldin, bennyvasquez.
Email list hosting is sponsored by The Rust Foundation
Discuss on r/rust
2 notes
·
View notes
Text
Researcher studies blockchain in Brazil-Arab trade
Helena Leite Rodrigues Fernandes, from São Paulo, obtained an MBA from USP on opportunities for applying blockchain technology in Brazil’s relationship with Arab countries. The Arab Brazilian Chamber’s platform was studied.

On the one hand, blockchain and its ample application possibilities. On the other hand, Brazil’s trade relationship with the Arab countries and its growth potential. Uniting these two universes and verifying how the first is benefiting and can make the latter advance even further was the object of research of 23-year-old University of São Paulo (USP) graduate student Helena Leite Rodrigues Fernandes from São Paulo.
Earlier this August, Fernandes presented her final assignment for her MBA in Digital Business at the Luiz de Queiroz School of Agriculture (ESALQ) of USP, titled “Blockchain technology: Opportunities for applicability in trade relations between Brazil and the Arab countries.” The work received full marks, and the professors who accompanied the research presentation indicated it would remain in the USP Library as a reference.
The story of the São Paulo native with technology began at the Arab Brazilian Chamber of Commerce (ABCC), where she worked in the customer relationship management (CRM) system for four years. Despite having a degree in Marketing, based on her experience with software, the young woman wanted to delve into technology and became interested in blockchain. “I like to study, and I told myself: Let’s see what’s trending in the technology market besides CRM. I discovered several very cool things,” she said.
Fernandes started studying blockchain initially in a self-taught way, relying mainly on content in English, as she found little information on the subject in Portuguese. She also started to attend blockchain events and workshops. When she went looking for an MBA in 2020, however, she did not find courses specifically focused on the subject but believed USP’s Digital Business was a good way to unite blockchain and business, which she intended to study.
Continue reading.
#brazil#politics#arab world#brazilian politics#arab politics#economy#international politics#mod nise da silveira#image description in alt
2 notes
·
View notes