#Veracrypt
Explore tagged Tumblr posts
Text
Upgrading to Xubuntu Noble -- 24.04 from 22.02 -- and a review
I have upgraded my desktop but not my laptop. Note: Xneo is an alias for neofetch --ascii_distro xubuntu. In general, the switch to mostly snaps could be smoother, and I still need to play with the system more to discover all the changes. Note: the upgrade to Noble 24.04 was delayed several days after initial release. Disabling third-party PPAs For any upgrade, third-party PPAs are disabled…
#AppImage apps#Chromium#Cryptomator#emacs#FireFox#insync#itsfoss#LibreOffice#Opera#Org-mode#Parole#pdftk#snap apps#Task Manager#Thunar#Thunderbird#ubuntuhandbook.org#Veracrypt#Vivaldi#xsane
0 notes
Text
A gadget writer's minor equivalent of nuclear waste
What happens when privacy anxiety meets hardware meltdowns meets procrastination meets what might be a slight hoarding habit.
My home office always needs cleaning, but there’s one part of it that stays especially resistant to tidying up–the small collection of old and inoperative hardware that might have my data in a condition that might be accessible. I think of these probably-defunct devices as my own rough equivalent of nuclear waste, but instead of radioactive isotopes they may hold old personal data that I don’t…

View On WordPress
#device encryption#encryption#erase device#factory reset#half-life#HP Spectre x360#Pixel 1#Pixel 5a#reset device#Schrödinger#secure delete#VeraCrypt#wipe device
0 notes
Text
VeraCrypt
Security on your device is crucial, especially if others frequently use your machine. VeraCrypt is an application designed to secure and encrypt partitions, ensuring sensitive files remain protected. The program is highly customizable, offering a variety of options. When you open VeraCrypt, you’ll find a simple interface, which some may consider outdated, guiding you through the available…
#Data Privacy#data security#disk encryption#disk encryption software#encryption#full disk encryption#password protection#secure data#VeraCrypt#volume encryption
0 notes
Text
Some People Using ZuluCrypt?
File:VeraCrypt screenshot.png I had more dreams, but I did not record them. Now, all that I can remember is barely part of my last dream. This dream involved ZuluCrypt and / or one or more other encryption programs / software / applications / apps like VeraCrypt et cetera. In this dream, some groups of people & individuals were on computers using the operating system, Linux, probably the…
View On WordPress
#Computer#Container#Container File#Container Format#Dismount#Encryption#Favorite#Linux#Mount#opensource#Program#Software#Ubuntu#VeraCrypt#ZuluCrypt
0 notes
Text

Mit Zwang in die Cloud
1Password zwingt Nutzer in die Cloud
Weil viele Menschen sich weigern ihre Daten irgendwelchen Clouds anzuvertrauen, kommt nun die Zwangsdigitaliserung. Die neue iPhone- und Android-Version 8 der Passwortverwaltung macht ein Cloud-Abo erforerlich. Alles soll mit 1Password 8 für iOS und Android schneller und besser werden.
Man muss dafür aber einen 1Password-Account in der Cloud haben. Lokale Tresore oder alternative Synchronisationmechanismen sind nicht mehr erlaubt. Schon in der Version 7 war es nicht mehr möglich lokale Tresore neu anzulegen. Für die neue Version gibt es auch keine Möglichkeit mehr die App zu kaufen, es gibt nur noch Abos.
Da können wir nur an die freien und kostenlosen Alternativen wie KeePassX als Passworttresor und VeraCrypt für die Datenscherschlüsselung erinnern. Niemand muss beim Cloud-Wahnsinn mitspielen!
Mehr dazu bei https://www.heise.de/news/Passwortmanager-1Password-8-unterstuetzt-keine-lokalen-Tresore-mehr-7216560.html
Kategorie[21]: Unsere Themen in der Presse Short-Link dieser Seite: a-fsa.de/d/3wV Link zu dieser Seite: https://www.aktion-freiheitstattangst.org/de/articles/8564-20231024-mit-zwang-in-die-cloud.htm
#Cloud#1Password#App#Android#iOS#IPhone#VeraCrypt#KeePassX#OpenSource#Verbraucherdatenschutz#Datenschutz#Datensicherheit#Vertrauen#Verhaltensänderung#Smartphone#Handy#Zwangsdigitaliserung
1 note
·
View note
Text
VeraCrypt 1.26.7: viene con más Seguridad y Compatibilidad en Linux
VeraCrypt es una herramienta esencial para el cifrado de disco, empleando una variedad de algoritmos como AES, Serpent y Twofish, o combinaciones de los mismos. Después de un largo período de desarrollo, VeraCrypt 1.26 ha llegado con una serie de mejoras y correcciones de errores significativas, especialmente en el ámbito de Linux. Principales novedades de VeraCrypt 1.26.7 Esta nueva versión de…

View On WordPress
0 notes
Text
btw, if you see resources online that could potentially save your life or a friend's life in the future, i.e. info on access to potentially life-saving care for vulnerable groups- SCREENSHOT, print the webpage if you can or back up the file, keep it somewhere safe. slapping a "#saving for future reference" tag on there isn't enough
tumblr staff can and likely WILL delete it.
websites can always be taken down.
i'm genuinely not trying to sound like a doomer, data is sooo easy to lose forever with no way to get back.
honestly it's good to get into the habit of saving and backing up almost ANYTHING you wouldn't want to lose on the internet, such as music/videos/art/tutorials, because data can easily be lost forever when you least expect it. but it's especially important at a time like this when people's rights and access to care are in question.
save everything. set up a system that works for you to make saving things easier so you're more likely to do it. flash drives are pretty cheap. veracrypt is a fairly reputable source for password protecting folders if you share a computer or a space with people you don't trust. be mindful of your surroundings and safety. do your own research into sources to make sure they are not coming from people with ill-intentions. if this feels out of your scope, seek out communities that can help you parse it out. the most important tool at our disposal is each other.
this is the only post i'll make like this but if you have any other suggestions or corrections you're more than welcome to add on.
231 notes
·
View notes
Note
what is the best way to get safer/more anonymous online
Ok, security and anonymity are not the same thing, but when you combine them you can enhance your online privacy.
My question is: how tech literate are you and what is your aim? As in do you live in a country where your government would benefit from monitoring private (political) conversations or do you just want to degoogle? Because the latter is much easier for the average user.
Some general advice:
Leave Windows and Mac operating systems and switch to Linux distributions like Fedora and Ubuntu (both very user friendly). Switch from Microsoft Office or Pages/Numbers/Keynote (Mac) to LibreOffice.
You want to go more hardcore with a very privacy-focused operating system? There are Whonix and Tails (portable operating system).
Try to replace all your closed source apps with open source ones.
Now, when it comes to browsers, leave Chrome behind. Switch to Firefox (or Firefox Focus if you're on mobile). Want to go a step further? Use LibreWolf (a modified version of Firefox that increases protection against tracking), Brave (good for beginners but it has its controversies), DuckDuckGo or Bromite. You like ecofriendly alternatives? Check Ecosia out.
Are you, like, a journalist or political activist? Then you probably know Tor and other anonymous networks like i2p, freenet, Lokinet, Retroshare, IPFS and GNUnet.
For whistleblowers there are tools like SecureDrop (requires Tor), GlobaLeaks (alternative to SecureDrop), Haven (Android) and OnionShare.
Search engines?
There are Startpage (obtains Google's results but with more privacy), MetaGer (open source), DuckDuckGo (partially open source), Searx (open source). You can see the comparisons here.
Check libRedirect out. It redirects requests from popular socmed websites to privacy friendly frontends.
Alternatives to YouTube that value your privacy? Odysee, PeerTube and DTube.
Decentralized apps and social media? Mastodon (Twitter alternative), Friendica (Facebook alternative), diaspora* (Google+ RIP), PixelFed (Insta alternative), Aether (Reddit alternative).
Messaging?
I know we all use shit like Viber, Messenger, Telegram, Whatsup, Discord etc. but there are:
Signal (feels like Whatsup but it's secure and has end-to-end encryption)
Session (doesn't even require a phone or e-mail address to sign up)
Status (no phone or e-mail address again)
Threema (for mobile)
Delta Chat (you can chat with people if you know their e-mail without them having to use the app)
Team chatting?
Open source options:
Element (an alternative to Discord)
Rocket.chat (good for companies)
Revolt.chat (good for gamers and a good alternative to Discord)
Video/voice messaging?
Brave Talk (the one who creates the talk needs to use the browser but the others can join from any browser)
Jami
Linphone
Jitsi (no account required, video conferencing)
Then for Tor there are various options like Briar (good for activists), Speek! and Cwtch (user friendly).
Georestrictions? You don't want your Internet Provider to see what exactly what you're doing online?
As long as it's legal in your country, then you need to hide your IP with a VPN (authoritarian regimes tend to make them illegal for a reason), preferably one that has a no log policy, RAM servers, does not operate in one of the 14 eyes, supports OpenVPN (protocol), accepts cash payment and uses a strong encryption.
NordVPN (based in Panama)
ProtonVPN (Switzerland)
Cyberghost
Mullvad (Sweden)
Surfshark (Netherlands)
Private e-mails?
ProtonMail
StartMail
Tutamail
Mailbox (ecofriendly option)
Want to hide your real e-mail address to avoid spam etc.? SimpleLogin (open source)
E-mail clients?
Thunderbird
Canary Mail (for Android and iOS)
K-9 Mail (Android)
Too many complex passwords that you can't remember?
NordPass
BitWarden
LessPass
KeePassXC
Two Factor Authenticators?
2FAS
ente Authenticator
Aegis Authenticator
andOTP
Tofu (for iOS)
Want to encrypt your files? VeraCrypt (for your disk), GNU Privacy Guard (for your e-mail), Hat.sh (encryption in your browser), Picocrypt (Desktop encryption).
Want to encrypt your Dropbox, Google Drive etc.? Cryptomator.
Encrypted cloud storage?
NordLocker
MEGA
Proton Drive
Nextcloud
Filen
Encrypted photography storage?
ente
Cryptee
Piwigo
Want to remove metadata from your images and videos? ExifCleaner. For Android? ExifEraser. For iOS? Metapho.
Cloak your images to counter facial recognition? Fawkes.
Encrypted file sharing? Send.
Do you menstruate? Do you want an app that tracks your menstrual cycle but doesn't collect your data? drip.
What about your sexual health? Euki.
Want a fitness tracker without a closed source app and the need to transmit your personal data to the company's servers? Gadgetbridge.
34 notes
·
View notes
Text
hi. since i have something that could very generously be called a platform, your local dumb horny dog is here with another unfortunate public service announcement for people currently living under the legal jurisdiction of the united states of america:
this would be a good time to start investigating privacy and data security tools (and, as ever, to not panic and/or doompost because those are not useful things to do). such things include:
using (more) secure messaging apps over sms for private correspondence such signal.
using (more) private email services rather than gmail such as protonmail
password protect your shit. this is just basic data security but like. please. password protect your shit. use strong passwords and/or passphrases. don't reuse passwords. use a password manager (i recommend bitwarden).
building off the previous one, encrypt your shit if you're able to. for pc users there are plenty of open source options, such as veracrypt, and probably native os stuff too.
like. y'all are gonna roll your eyes, and i get it, but: stop using windows and try out linux. seriously. windows 11 is a fucking privacy nightmare and it's only getting worse as microsoft pushes their ai shit which is planned to have access to everything you do on it.
tumblr can't do nested lists, consider this a sub-point: mint linux is designed to be incredibly familiar to people coming from windows and is very user friendly. a huge amount of windows software can run on linux using stuff like wine. the linux version of steam comes pre-packaged with it. it's fine. please try linux it won't bite.
sadly i am, as mentioned, a dog on the internet and i cannot provide an actual comprehensive guide to keeping your privacy intact and yourself safe.
however, there are plenty of good guides for this sort of thing on the internet and despite how degraded modern search engines are they are not hard to find. i heartily suggest doing so and familiarizing yourself with them-- and not just because of the times we live in, because a lot of this shit is the same shit that will help keep you safe from a lot of forms of identity theft and the like. it's just good opsec.
22 notes
·
View notes
Photo
Also don't make backups on the same physical media (i.e. on your hard drive) backing up your desktop to your documents folder does not help you if your hard drive ever becomes unusable. Normal spinning disc hard drives (ones that are not SSDs or M.2/NVME) DO have a lifespan. You can use SMART tests to see if there are any signs of failure ahead of time.
Ideally, you would back up your personal data in a separate, secure physical location. On an individual level, this could be a bank deposit box with an external hard drive in it. For most people, that may seem a bit overboard, but if something happens that completely destroys everything in your home, you still have a backup.
A more realistic and reasonable approach would be to have an external hard drive you back up to at regular intervals (this is up to you and how much data you're willing to lose. A week/month is a reasonable amount of time between backups, and more frequently if you're constantly creating and changing data you don't want to lose). After the backup, you can store the drive in a water proof and fire proof safe and keep it somewhere safe in your home
You can also back files up to the cloud if you're comfortable with it being hosted by an outside company. Bigger companies will have several backup sites with data on them to prevent data loss in the event of a disaster at one of their data centers. The downside is you may have to pay a monthly fee to have enough storage, and also you're trusting your data with a third party company.
As far as external hard drives are concerned, I tend to shy away from USB sticks and external drives that connect via USB. I've seen way too many of their ports get broken off or worn out and become unusable without some complex data recovery methods you probably can't do on your own, and would cost a lot of money through a professional. For a cheap solution, you can buy a hard drive bay and an internal (3.5 inch) HDD to copy your data to. HDDs are cheap and can hold a ton of data (since you're just backing up data and rarely accessing it, the slower speed compared to an SSD isn't really worth paying extra for an SSD imo). These bays look like toasters, and you should get one that has removable and replaceable cables

They'll look something like this ^
The smaller drive in the front is a 2.5 inch SSD and the one in the back is a 3.5 inch HDD ("internal" hard drive). You may also find smaller 2.5 inch HDDs. These typically go in laptops and don't really provide extra benefit (and I believe they're normally a bit more expensive) so I still recommend a 3.5 inch drive.
Your station will also need an external power supply as USB will not have enough power to get the HDD spinning (most come with power, just don't use one of those SATA to USB adapters for anything that's not a 2.5 inch drive)
Set a reminder for your backups, you will forget. It's human error. Don't leave your backup drive constantly plugged in, it's vulnerable in the event of a disaster (spill, tornado, ceiling collapse) and will most likely be destroyed alongside your internal drive. Take it out. Do a backup. Lock it somewhere safe.
If you're worried about your data security on the external drive, you can encrypt the whole disk using a tool like VeraCrypt (I recommend using an AES encryption method, typically AES-256 or AES-128). This will make it so your drive cannot be accessed without using VeraCrypt and also without a password. DO NOT lose this password as you will almost certainly not be able to access your information without it! (AES encryption is too strong to brute force without an insanely long amount of time. We're talking literally hundreds of thousands of years with current computing power)
You don't need to back up everything, just the stuff you'll miss. And you can also keep multiple copies of backups at once. It's. A good idea to keep a few (maybe four backups at a time) and delete the oldest one whenever you make a new one. This gives you a few to pick from in case you purposely delete a file, but later want it back. It may be in one of your older backups, saving you a loss.
This is a pretty basic startup guide on proper backup techniques, and you're more than welcome to message me with questions.

beastly reminder
74K notes
·
View notes
Text
🛡️ Tu privacidad importa: herramientas esenciales para protegerte online 🔒
En un mundo digital lleno de rastreadores y filtraciones de datos, proteger tu información personal ya no es opcional. Aquí tienes herramientas clave para navegar de forma más segura:
✨ Navegación privada:
Brave (bloquea anuncios + trackers)
Tor (para anonimato extremo)
📡 VPNs confiables:
ProtonVPN
Mullvad
📨 Comunicaciones seguras:
Signal (mensajería encriptada)
ProtonMail (email privado)
🔎 Búsquedas que no te espían:
DuckDuckGo
Startpage
💾 Almacenamiento cifrado:
Cryptomator (para la nube)
VeraCrypt (discos locales)
¿Por qué conformarte con lo básico cuando puedes tomar el control de tu huella digital? Descubre más herramientas y consejos en la guía completa de Privancer: 👉 https://privancer.com/herramientas-de-privacidad/
0 notes
Text
Create a Secure File Encryption Tool in a Weekend
Introduction Data breaches often come from lost or stolen devices. Encrypting your files ensures that even if someone gets their hands on them, they can’t access the content without your password. Let’s build a secure file encryption routine you can complete in a weekend.
1. Choose and Install a Tool Good options include:
VeraCrypt (full-disk or volume encryption)
AxCrypt (file-by-file, simpler interface)
7-Zip with AES-256 (lightweight, widely used)
Let’s use VeraCrypt as an example. Download and install it from https://www.veracrypt.fr.
2. Encrypt Files With VeraCrypt:
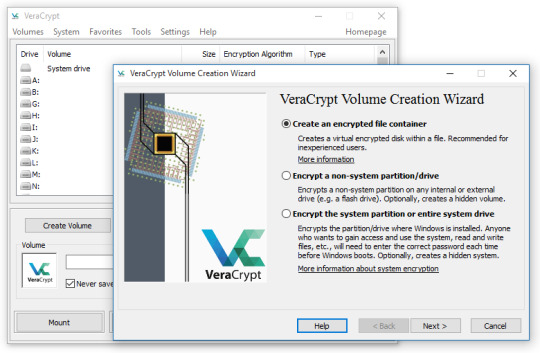
Create a new volume.
Select "Create an encrypted file container".
Choose AES (Advanced Encryption Standard).
Set the size and mount the volume.
Move sensitive files into the container.
3. Save and Secure the Password Never store passwords in plain text or reuse them across services. Use a password manager like:
Bitwarden
1Password
KeePassXC
Set a password that meets strong criteria. Example using a generator:
plaintext
CopyEdit
T#dL!r8$zP1&ExQv
Conclusion Encrypting files is a must-do for anyone handling sensitive data. Whether it’s client documents, tax forms, or personal records — this project is quick, practical, and immediately useful.
1 note
·
View note
Text
The Ultimate Guide to Secure and Efficient Submissions
Submitting documents, applications, or data is a ubiquitous task in the modern world. From applying for jobs and university programs to filing taxes and submitting research papers, the ability to securely and efficiently transmit information is crucial. However, navigating the landscape of submission processes can be complex, demanding careful consideration of security protocols, format requirements, and efficient workflow management. This guide provides a comprehensive overview of best practices for secure and efficient submissions, ensuring your information reaches its intended destination accurately and without compromise.
Understanding the Security Landscape of Submissions
Before initiating any submission, it is paramount to understand the potential security risks involved. Data breaches, phishing scams, and malware attacks are constant threats, and submitting sensitive information without proper precautions can lead to identity theft, financial loss, and compromised privacy. Identify the sensitivity of the data you are submit. Does it contain personally identifiable information (PII), financial records, or proprietary business data? Knowing the value of the information helps determine the level of security measures required. Always verify the authenticity of the submission portal. Scrutinize the URL, looking for "https" to ensure encryption. Be wary of suspicious emails or websites asking for personal information, and avoid clicking on links from unknown sources. Implement strong passwords and enable two-factor authentication whenever possible to protect your accounts from unauthorized access.

Data Encryption and Secure Transmission Protocols
Encryption is the cornerstone of secure submissions, transforming readable data into an unreadable format that can only be deciphered with a decryption key. When submitting online, always ensure the website uses HTTPS protocol, indicated by a padlock icon in the address bar. This signifies that the data transmitted between your browser and the server is encrypted using Transport Layer Security (TLS) or Secure Sockets Layer (SSL). For sensitive documents, consider encrypting the files themselves before uploading them. Utilize encryption software like VeraCrypt or 7-Zip to create password-protected archives. When sending information via email, which is inherently less secure, consider using email encryption tools like ProtonMail or Virtru. These services encrypt the email message end-to-end, ensuring that only the intended recipient can read it.
File Format and Submission Requirements
Ignoring file format and submission requirements is a common cause of delays and rejections. Before starting the submission process, carefully review the guidelines provided by the recipient. Pay attention to accepted file types (e.g., PDF, DOCX, JPEG), file size limits, and naming conventions. Failing to adhere to these specifications can result in your submission being automatically rejected or requiring manual intervention, which can significantly slow down the process. Convert documents to PDF format whenever possible. PDF is a widely accepted standard that preserves formatting and ensures compatibility across different operating systems and devices. Optimize images and documents to reduce file size without compromising quality. This can be achieved using image compression tools or PDF optimizers.
Streamlining the Submission Workflow
Efficiency is just as important as security when it comes to submissions. A streamlined workflow can save time and reduce the likelihood of errors. Begin by gathering all the necessary information and documents before starting the submission process. Organize files into folders and name them clearly and consistently. Prepare a checklist to ensure you have completed all the required steps and provided all the necessary information. For online submissions, use autofill features to automatically populate forms with your information. However, double-check the accuracy of the information before submitting. Consider using a password manager to securely store and manage your usernames and passwords for different online accounts. This can save time and prevent you from forgetting important credentials.
Utilizing Submission Management Tools
Numerous submission management tools are available to help streamline the process and enhance security. These tools can automate tasks, track progress, and ensure compliance with submission requirements. Some tools offer features like version control, file sharing, and collaboration, making them particularly useful for teams working on complex submissions. Cloud storage services like Google Drive and Dropbox can be used to store and share files securely. However, be sure to enable two-factor authentication and configure appropriate permissions to control access to your files. Project management software like Trello or Asana can be used to track the progress of your submission and assign tasks to team members.

Post-Submission Verification and Follow-Up
The submission process doesn't end when you click "submit." It's crucial to verify that your submission was received successfully and to follow up if necessary. Check for confirmation emails or notifications to ensure your submission has been acknowledged. If you don't receive a confirmation within a reasonable timeframe, contact the recipient to inquire about the status of your submission. Keep a record of your submission, including the date, time, and any confirmation numbers. This will be helpful if you need to track down your submission or provide proof of submission. If you receive feedback or requests for additional information, respond promptly and professionally.
Staying Informed and Adapting to Changing Security Landscapes
The digital landscape is constantly evolving, and new security threats and submission requirements emerge regularly. It is essential to stay informed about the latest security best practices and to adapt your submission processes accordingly. Subscribe to security newsletters and follow reputable security blogs to stay up-to-date on the latest threats and vulnerabilities. Regularly review your security practices and update your passwords and software. Be aware of new submission requirements and guidelines, and adjust your workflow accordingly. By staying informed and proactive, you can ensure that your submissions remain secure and efficient in the face of evolving threats. By implementing these strategies, you can significantly enhance the security and efficiency of your submission processes, safeguarding your information and ensuring that it reaches its intended destination promptly and securely. Remember that a proactive approach to security and efficiency is paramount in the digital age.
0 notes
Link
0 notes
Text
Dans notre vie de tous les jours, on se balade souvent avec une petite clé USB dans notre poche ou notre sac. C’est super pratique pour garder tout ce qui est important pour nous. Mais imagine un peu si tu perds cette petite clé ou si quelqu'un te la pique ! Tout d'un coup, ça devient un gros problème. Heureusement, il existe une méthode simple pour protéger ta clé USB par un mot de passe. Dans cet article, nous allons te montrer comment crypter le contenu de ta clé USB avec un mot de passe. Loin des scènes de science-fiction où les clés USB s'autodétruisent, chiffrer tes fichiers est néanmoins crucial. Comment utiliser Veracrypt pour chiffrer une clé USB Nous avons déjà vu dans les articles précédents comment chiffrer une clé USB avec BitLocker. Cependant, aujourd'hui, nous allons explorer un outil encore plus puissant pou... https://www.funinformatique.com/comment-utiliser-veracrypt-pour-crypter-facilement-une-cle-usb/?_unique_id=67bb3b88bd060
0 notes
Text

It's time to expand the geographical footprint and leave the neighbors spoofed SSIDs. The opsec needs to be completely flawless going forward. First grab a $200 used ThinkPad with cash from a street vendor with no receipts, no trace, and a USB kill switch. Wipe it clean with DBAN, then hit a library PC to download Tails OS onto a 16GB SanDisk USB, enabling encrypted persistent storage with a 32-character passphrase stored on my X-seed. Boot it at a McDonald’s, USB in, Tor up, and route through a cash-bought VPN. Tweak Tor’s exit nodes with Germany, Netherlands avoiding Five Eyes in the simplest ways. Wi-Fi’s via a $10 dongle in my backpack, MAC spoofed to a random hex via macchanger. My IP’s a ghost. The 20 wallets private keys are offline and handwritten. load five keys into Exodus (checked for no telemetry) on Tails’ persistent storage. Liquidity’s tight for ETH-Monero atomic swaps—Uniswap’s XMR pair is thin, so I spread $10M ETH across 50 Monero wallets, $200K each, using THORChain and Haveno too. I test $500 swaps first, confirm they clear, then ramp up—$50K/hour across five swaps, pausing 2-3 hours between, over 10 days. I would script on Tails with web3.py, generating 500 ETH wallets, private keys dumped to an encrypted VeraCrypt container in persistent storage. I bake in Wireshark, Nmap, tcpdump, Snort, Nikto, Burp Suite, and Kismet.. precompiled binaries from GitLab, verified SHA256 hashes to monitor Tor traffic, scan for honeypots, and sniff Wi-Fi threats. The script drips $10M, $20K per wallet, over 72 hours via Tor bridges (obfs4), randomized delays (5-15 minutes). I send $100 ETH from 50 wallets to noisy sinks like Binance deposit addresses (scraped from Etherscan), OpenSea contracts, and a Ukraine BTC donation wallets with the atomic swapped-fresh ETH adresses, while cross-transacting between my wallets: wallet A to B, B to C, 0.05 ETH each, 200 times. I burn $100K including gas ($20/tx at 50 gwei) over two weeks. Chainalysis drowns in noise. The botnet’s quiet side swaps ETH to Monero $5K-$10K chunks, targeting $1M/month, matching Monero’s $30M daily OI I use Haveno’s escrow, rotate Tor circuits, and pause 2-5 days between bursts. Locations shifts from McDonald’s, Starbucks to co-working spaces in nomad hubs like Bali, cayman, Jersey, Malta, Bermuda, Isle of Man, Cyprus, Bahamas, and Chiang Mai. I spoof the dongle’s MAC daily, monitor with Kismet for IMSI catchers, and never stay longer than 45 minutes. If a network’s crowded, I ping with Nmap.. too many devices, I bounce. Cashout’s the long game… With somewhere around $10M in Monero across 50 wallets annually, I hit OTC via Telegram groups, swapping $10K-$50K for USD or EUR, cash or tether. remain blended in with nomad towns where cash flows. Could even pose as a trust-fund drifter, living off “clean” Solana and BTC wallets funded by Monero swaps, tumbled through Wasabi’s CoinJoin for extra cover. Laptops die after 10 uses and moves quarterly. The other $1.49 billion? It’s staying cold for the long run. Split across 20 32GB USBs, each with 1/20th of the keys in encrypted 7z archives. AES-256 stays locked in safes through various deposit boxes. I clean $20M max annually mby even far lower depending on the OI. Scaling will remain low, otherwise botnets spike bandwidth, swaps dry up, feds get wise n sniff Tor exits. One slip, either be reused bridge, same Wi-Fi SSID twice. I settle in Podgorica, Montenegro: or any country with no US/EU extradition treaties, $500K buys a villa, and $10K/month keeps me invisible. $20m annually is enough to manipulate local surroundings.
1 note
·
View note