#Web Developer Interview Questions
Explore tagged Tumblr posts
Text
Java Projects for Your Resume: Why They Matter

Java Projects for Your Resume: Why They Matter
Adding Java projects to your resume can really help you land a job. Employers want to see real experience, and showcasing projects shows that you know how to apply your skills. A solid portfolio stands out more than just having certifications. These projects reflect your problem-solving skills, creativity, and understanding of Java basics and advanced concepts. Whether you’re just graduating or changing careers, having practical projects is important. Students taking Java course in Coimbatore are often encouraged to create live applications to boost their resumes and improve their chances in job interviews.
Simple Java Projects for Beginners
If you're just starting out, try adding basic Java projects like a calculator, to-do list, or temperature converter to your resume. These projects are great for grasping object-oriented programming and basic GUI design. They’re usually part of beginner exercises in Java training programs in Coimbatore, helping you learn coding logic efficiently. Working on simple applications also enhances your debugging and problem-solving skills, which are key for coding interviews. It’s a good idea for beginners to focus on these smaller projects before tackling more advanced systems.
Intermediate Java Projects That Impress
Once you’ve got the basics down, you can move on to intermediate-level Java projects for your resume, like library management systems, quiz apps, or student record management tools. These projects show that you have a better grasp of file handling, user authentication, and data structures. Many Java course in Coimbatore make sure students work on these types of projects to build real-world problem-solving skills. These applications don’t just show off your technical skills; they also demonstrate that you can create user-friendly programs.
Advanced Java Projects That Stand Out
For those with more experience, advanced projects could include chat applications, e-commerce websites, or banking systems using JavaFX or Spring Boot. These projects show that you’re skilled in frameworks, APIs, and databases. Many top Java training programs in Coimbatore include this type of work in their syllabus. Having these projects on your resume proves to employers that you’re ready for the job and can manage larger systems. Using GitHub to share your source code, along with documentation and screenshots, can give you an edge.
Importance of Full-Stack Java Projects
A full-stack Java project covers both the frontend and backend, often using HTML, CSS, JavaScript, Java, and MySQL. These projects help show that you’re not just focused on the backend but can also manage UI and databases. Joining a Java course in Coimbatore that includes full-stack content will give you an advantage in today’s job market. Such projects mimic real work environments and prove you can handle end-to-end application development.
Using Java Projects to Show Teamwork
Employers often look for teamwork skills. Including team-based Java projects on your resume, where you collaborated with others, demonstrates your ability to communicate, manage tasks, and work with version control systems like Git. Group projects in Java training programs in Coimbatore teach students how to build scalable applications with effective task management. Showcasing these projects on your resume emphasizes both your technical abilities and your teamwork qualities.
How to Present Java Projects on a Resume
When listing Java projects on your resume, make sure to include the project title, a brief description, the technologies you used, and your role in the project. Focus on the impact of your work—did it solve a real problem or improve performance? Students in Java course in Coimbatore learn how to document and present their projects for interviews. Adding links to demos or GitHub repositories is a nice touch. How you present your projects can help you stand out to potential employers.
Mistakes to Avoid While Showcasing Java Projects
Avoid listing too many projects that aren’t complete or too similar. Don’t just focus on frontend work; employers want to see sound coding and backend integration too. Students in Java training programs in Coimbatore are advised to keep their code clean, well-documented, and free of bugs. Steer clear of copying projects from the internet; instead, focus on customizing and innovating based on your learning. This shows creativity and confidence, and you'll be better prepared for questions about your projects in interviews.
How Projects Improve Your Job Readiness
Including Java projects on your resume is vital for showing you’re ready to work. It shows you can create practical applications with your skills. Employers want candidates who can contribute from day one. A strong portfolio, supported by a solid Java course in Coimbatore or good Java training program, can greatly improve your hiring chances. Recruiters appreciate real-world experience over just theoretical knowledge or course certificates.
Conclusion: Learn, Build, and Stand Out with Xplore IT Corp
If you want to get good at Java and build impressive projects for your resume, then a structured Java course in Coimbatore is a great place to start. At Xplore IT Corp, we provide relevant Java training that includes hands-on project development, resume-building workshops, and full placement support. With real experience and guidance, you can create a portfolio that impresses employers. Let your Java projects show your skills learn, build, and grow with us at Xplore IT Corp.
FAQs
1. What types of Java projects should I include in my resume?
Include a mix of simple, intermediate, and advanced projects to showcase various Java skills like OOPs, file handling, APIs, and databases.
2. How many Java projects should I list on my resume?
List 2 to 4 well-documented projects. Focus on quality rather than quantity, ensuring each project highlights a unique skill set.
3. Do Java projects really help in getting a job?
Yes, they provide evidence of your coding skills and can help you make a strong impression in interviews, especially for roles needing practical programming.
4. Where can I get help for building Java projects?
Enrolling in a Java course in Coimbatore, like the one offered by Xplore IT Corp, can provide expert guidance, resources, and structured projects.
5. Can I use GitHub to showcase my Java projects?
Definitely! GitHub is a great platform to display your work to potential employers. Include links to your GitHub projects in your resume for easy access.
#Java programming#Java developer#Java applications#Java frameworks#Java projects#Java coding#Java syntax#object-oriented programming#Java backend#Java frontend#Java database connectivity#Java Spring Boot#JavaFX#Java GUI#Java tools#Java version control#Java IDE#Java servlet#Java web development#Java interview questions
0 notes
Text
Blazor Latest Interview Questions 2024
Introduction Are you preparing for a Blazor interview in 2024 and want to be well-prepared with the latest interview questions and answers? Look no further! In this article, we will provide you with a comprehensive list of Blazor interview questions that will help you crack your interview with confidence. 1. What is Blazor? Blazor is a web development framework developed by Microsoft that allows…
#blazor#Blazor interview answers#Blazor interview preparation#Blazor interview questions#C#dotnetcore#interview preparation#web development
0 notes
Text
Web Development Interview Questions?
In such a situation, it is critical to be ready for interviews, especially when entering the web development field. Irrespective of your plan of working with a leading organization such as SkyWeb Design Technologies, an organization that deals in web and mobile applications, or with any organization of your preference, it is important to learn the basics.
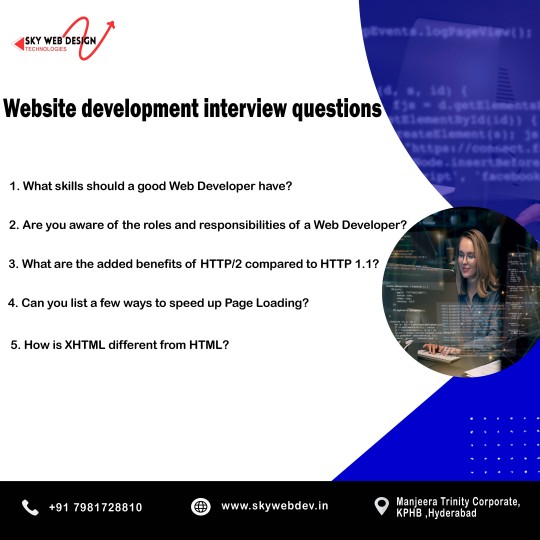
1. What is HTML, what is it used for?
Answer: HTML stands for Hyper Text Markup Language it’s most commonly used markup language in the creation of Web documents or anything related to the Web environment. It determines the layout of the material posted on the World Wide Web and includes such components as headings, paragraphs, hyperlinks, images, and others.
2. What makes HTML5 different from the prior version of HTML?
Answer: HTML5 is the version of HTML that is currently in use. It adds new elements and attributes and enhanced support for multimedia that are <article>, <section>, <header>, <footer>, <audio>, <video> and new APIs such as Canvas, Web Storage and Geolocation.
3. Here are some of the frequently used HTML tags and what they are used for:
Answer:
<p>: Defines a paragraph.
<h1> to <h6>:
<a>: Defines a hyperlink.
<img>: Embeds an image.
<ul> and <ol>: is unordered list, and ordered list.
<div>: division. So it defines a division or section.
<span>: Sets a block of text, mainly used for applying a style on.
4. What is CSS and why should one bother with it?
Answer: HTML is used to create a structure of a web page while CSS (Cascading Style Sheets) is used for appears of web pLAST EDITED: pages. It enables you to use aspects like colors font, space and position to your html elements which in turn creates aesthetically pleasing and more functional website to the users.
5. Please also provide me with a definition of what the box model in CSS .
Answer: The CSS box model describes the rectangular boxes generated for elements in the document tree and consists of:The CSS box model describes the rectangular boxes generated for elements in the document tree and consists of:
Content: The inner content area referred to as Knowledge Creation is:
Padding: Margin between the stuff and its visual frame.
Border: These are the line on the right and at the bottom of the padding and content.
Margin: (h) Space referring to the area beyond the border surrounding an element and other elements.
6. JavaScript is a programming language and web development tool, but how is it defined and what does it do?
Answer: JavaScript is also a language used in the designing of web sites to provide flexibility and impressive features on any web page. It lets you to work with HTML and CSS, manage events, verify data in forms, use animations, and work with servers.
7. What are variables in JavaScript and how can one declare them?
Answer: In JavaScript, variables refer to the means of storing data values. You can declare them using the var, let, or const keywords:You can declare them using the var, let, or const keywords:
javascript
var name = "ram";
let age = 25;
const isStudent = true;
8. What is the difference between let, const, and var?
Answer:
var: Any variable declared in a function block is either function-scoped or globally-scoped which even can be redeclared and again updated.
let: Local, write-only, specifically they allow updating the variable but not declaring it in the same block.
const: declared only in block can’t be updated, or redeclared after the declaration.
9. What is an array; Explain how you can define an array in JavaScript?
Answer: An array can be defined as a united variable for storing more than one value. We can create an array using square brackets []:
javascript
let fruits = [‘apple’, ‘banana’,’ cherries’];
10. What is a function and how does one describe or create one using JavaScript?
Answer: Function is a set of statements and instruction used to do a certain job or achieve a specific goal. we can define a function using the function keyword:
javascript
function greet(name) {
return ‘Hello, ‘ + name;
}
11. What is the event handling of JavaScript?
Answer: Javascript as the name suggests is an event driven language; this means that functions can be written that will take actions based on events such as a click, key press or even mouse movements. we can handle events by attaching event listeners to elements:
javascript
document. getElementById("myButton"). addEventListener("click", function() {
alert("Button clicked!");
});
12. What is the Document Object Model (DOM)?
Answer: DOM is a programming interface for the web documents. It depicts a document as a tree structure of nodes; this assist in managing the content and structures of the web pages by applying JavaScript.
13. How do you select an element by its ID in JavaScript?
Answer:
I can select an element by its ID using the getElementById method:
javascript
let element = document.getElementById("myElement");
14. What is responsive web design, and why is it important?
Answer:
Responsive web design ensures that web pages look good and function well on devices of various screen sizes and resolutions. It is important because it improves user experience and accessibility, and it is favored by search engines.
15. What are some basic steps to create a responsive web design?
Answer:
Use flexible grid layouts: Utilize relative units like percentages instead of fixed units like pixels.
Media queries: Apply different styles based on screen size, orientation, and other characteristics.
Flexible images: Ensure images scale appropriately within their containers.
Viewport meta tag: Set the viewport to control layout on mobile browsers.
html
<meta name="viewport" content="width=device-width, initial-scale=1.0">
These questions and answers demystify basic facts which a fresher that wants to join the web development team should know.
Thanks for visit us……For more Information to visit our website: skyweb design Technologies.
Adress: 15th floor, Manjeera trinity corporation, kukkatpally, HYDERABAD
#web development interview questions#skyweb design technologie#top15 interview questions#top 10 interview questions#web dev interview question for freshers
0 notes
Text
Deploying a Node.js application to Heroku is a straightforward process. Heroku is a platform as a service (PaaS) that allows you to easily deploy, manage, and scale web applications. Here's a step-by-step guide to deploying a Node.js application to Heroku
#reactjs#jsx#react#react native#react developer#react js#react developer tools#react js tutorial#react table#react tutorial#react dev#react js developer#react interview questions#react framework#react data table component#stackoverflow#web design#web dev#web development#website#programming#backedn#backend eng#tech#technology#engineering
0 notes
Text
Deploying a Node.js application to Heroku is a straightforward process. Heroku is a platform as a service (PaaS) that allows you to easily deploy, manage, and scale web applications. Here's a step-by-step guide to deploying a Node.js application to Heroku
#reactjs#jsx#react#react native#react developer#react js#react developer tools#react js tutorial#react table#react tutorial#react dev#react js developer#react interview questions#react framework#react data table component#stackoverflow#web design#web dev#web development#website#programming#backedn#backend eng#tech#technology#engineering
0 notes
Text
Deploying a Node.js application to Heroku is a straightforward process. Heroku is a platform as a service (PaaS) that allows you to easily deploy, manage, and scale web applications. Here's a step-by-step guide to deploying a Node.js application to Heroku
#reactjs#jsx#react#react native#react developer#react js#react developer tools#react js tutorial#react table#react tutorial#react dev#react js developer#react interview questions#react framework#react data table component#stackoverflow#web design#web dev#web development#website#programming#backedn#backend eng#tech#technology#engineering
0 notes
Text
Deploying a Node.js application to Heroku is a straightforward process. Heroku is a platform as a service (PaaS) that allows you to easily deploy, manage, and scale web applications. Here's a step-by-step guide to deploying a Node.js application to Heroku
#reactjs#jsx#react#react native#react developer#react js#react developer tools#react js tutorial#react table#react tutorial#react dev#react js developer#react interview questions#react framework#react data table component#stackoverflow#web design#web dev#web development#website#programming#backedn#backend eng#tech#technology#engineering
0 notes
Text
The Best Software Institutes in Guntur and Vijayawada
Nipuna Technologies is the best software school in Guntur and Vijayawada, and we're going to show you why.
Are you prepared to begin a cutting-edge software education journey? If you're searching for a top-notch institute in Guntur and Vijayawada, then Nipuna Technologies is the perfect choice. We are distinguished as the top software institute in the region due to our dedication to achieving excellence, curriculum that is tailored to the needs of the industry, and a faculty with extensive experience.

Improve your skills by enrolling in our comprehensive courses.
Nipuna Technologies acknowledges the dynamic nature of the technology industry and its constant evolution. We offer a wide variety of courses that are suitable for both beginners and professionals. Our goal is to make sure that everyone can find the course that is the perfect fit for them. Our courses cover a wide range of topics, including web development, app design, and data analytics. Whether you have an interest in any of these areas, we have something for you. The instructors in our program are experienced professionals in their fields. They provide valuable real-world knowledge to the classroom, helping to connect theoretical concepts with practical applications.
Why Choose Nipuna Technologies?
Hands-On Learning: Our philosophy is centered around the idea of learning through practical experience. Our education approach focuses on practical skills that employers highly value, ensuring that you are equipped with the abilities they seek.
Industry-Relevant Curriculum: The syllabus we have developed is created in collaboration with industry leaders, ensuring that you gain the most up-to-date and relevant knowledge.
State-of-the-Art Infrastructure: The learning experience is enhanced when one learns in a conducive environment. The labs and facilities we have are specifically designed to encourage and support creativity and innovation.
Placement Assistance: We consider your success to be synonymous with our own success. At Nipuna Technologies, we offer dedicated placement support to assist you in confidently launching your career.
Frequently Asked Questions
1. Who can apply for these courses?
Our courses are designed to accommodate students from various backgrounds. Whether you're a recent graduate, a working professional, or someone looking to switch careers, Nipuna Technologies welcomes you.
2. What sets Nipuna Technologies apart from other institutes?
Nipuna Technologies stands out due to its industry-aligned curriculum, experienced faculty, practical approach to learning, and top-notch placement assistance.
3. Can I get a job after completing these courses?
Yes, Nipuna Technologies has a strong track record of placing students in reputable companies. Our extensive network and career guidance will significantly increase your job prospects.
Conclusion: Your Pathway to Success in the World of Software
In a digitally driven world, choosing the right institute for your software education is pivotal. Nipuna Technologies emerges as the beacon of excellence in Guntur and Vijayawada. Our commitment to nurturing talent, fostering innovation, and propelling careers makes us the unrivaled choice. Join us today and set forth on a journey of limitless possibilities!
Ready to take the plunge? Contact us to learn more about our courses and kick-start your journey toward a successful software career.
#institute#software developers#web design#course#job placement#interview questions#digital marketing
1 note
·
View note
Text
Top Salesforce Developer Interview Questions
Here is a list of some Top questions for the Developer interview in Salesforce: What is Sandbox and the Type of Sandbox in Salesforce? What is Cloud Computing? What is Iaas? What is PaaS? What is Saas? Type of Object Relationship in Salesforce? What is Junction Object in Salesforce? What is the difference between Role and Profiles? How many way we have in Salesforce for Sharing? What…
View On WordPress
0 notes
Note
Hii, I asked you a question about spiritual qi being transferred. Thanks for replying!
Also I'm a bit shocked. Mo Xuanyu and Jin Guangyao did not develop a golden core yet? I didn't know oh my goodness! I might have missed this in the novel. Do you know where it says so? I need to bookmark this. Or is it only explicitly said so in the interview with mxtx?
Man this makes me view Wei Wuxian and Jiang Cheng in a way different light. If I remember correctly, Wei Wuxian punched a few meters into the ground while in Mo Xuanyu's body. So the fact that he did it without a core and with a weakened body like Mo Xuanyu's... he's an absolute monster XD. What can't this man do?
And it makes Jiang Cheng a loser even more. He lost to a physical fight with Jin Guangyao XD. Jiang Cheng literally wasted Wei Wuxian's golden core at this point.
(I really really hate you tumblr erasing my posts I work on mid sentence 💜) sighhhhh round two of this:
Hi again anon!
Chapter 1 and 2 of the web serialization and chapter 1 of the published version:
Hanzi:
然而,尚未等到莫玄羽修仙有成、继承他父亲 的家业,他就被赶了回来。
而且是被极其难看地赶了回来。因为莫玄羽是 个断袖,还胆大包天地骚扰纠缠同门,这丑事被当 众捅破,再加上天资平平,修为无所建树,也就没 有让他继续留在家族中的理由了。
My translation:
However, before Mo Xuanyu could even succeed in cultivating like an immortal to inherit his father's position, he was driven back.
In an extremely brutal way at that. Mo Xuanyu was a cut sleeve, he had been so bold as to harrass his fellow disciples and the scandal became public knowledge. Additionally, he was of mediocre talent with no achievements in cultivation, so there was no reason for the clan to keep him.
Sevenseas:

ExR:

(Remember that immortal part in particular because his mother had bragged specifically about Mo Xuanyu achieving immortality as a cultivator and expecting him to be the fastest at it just before this passage when Jin Guangshan summoned Mo Xuanyu to Lanling Jin)
Secondly:
Hanzi:
他索性先打坐一阵,适应新舍。这一坐就是一 整天。睁眼时,有阳光从门缝窗隙漏入屋中。虽然 能起身行走,却仍头昏眼花,不见好转。魏无羡心 中奇怪:“这莫玄羽修为低得那点灵力可以忽略不 计,没道理我驾驭不了这具肉身,怎么这般不好 使?”
直到腹中传来异响,他才明白根本不关修为灵 力的事,只不过是这具不辟谷的身体饿了而已。他 再不去觅食,说不定就要成为有史以来头一位刚被 人请上身就立刻活活饿死的厉鬼邪神。
My Translation:
He decided he would simply meditate a bit to adapt to his new accommodations*. He sat there almost the entire day. When he opened his eyes, sunlight seeped through the cracks of the door and the windows. Although he could stand up and walk, he felt dizzy without it seeming to ease. Wei Wuxian was puzzled, "This Mo Xuanyu's cultivation is so nonexistent any spiritual power might as well be ignored. It doesn't make sense why I can't control this body. Why is it so difficult?"
Until he heard a strange sound from his stomach, he realized that it had nothing to do with cultivation and spiritual power. It was just that this body hadn't practiced inedia, and was hungry. If he didn't seek out food, he might just become the first evil ghost in history to starve to death as soon as he was summoned to possess someone.
(*That first line is pretty funny because Wei Wuxian literally does refer to the body as a new residence/dwelling)
Sevenseas:

ExR:

Now in terms of this, I guess you could say it requires to know some general cultivation conventions (personally why I don't suggest MDZS as a first time cultivation read as well as it being a deconstruction of the tropes). If Mo Xuanyu had achieved forming a golden core, even a low level one, he would be able to practice inedia as that is one of the first things learned by cultivators once a foundation level is achieved. Mo Dao Zu Shi also just... mashes the first three stages of cultivation ( qi formation, foundation level and golden core) into one base at immediate golden core at young age.
We also get told Mo Xuanyu is summoned at the age of fourteen, but did not stay long enough to learn the cultivation to form that essential core (in this jianghu it is pertinent to form these cores early otherwise it is next to impossible unless you are EXCEPTIONALLY talented). If Mo Xuanyu had formed a core his spiritual power should at least be somewhat of note and it is not. No one with a golden core or uses spiritual energy often should be lacking in spiritual prowess as he is. MXTX's interview just reiterates this all.
As for the Jiang Cheng matter... well... Wen Ning was right to say he was lacking despite being given a prodigious core...
45 notes
·
View notes
Text

The concept of alien impregnation may be terrifying to most but several niches found some level of joy in it. The one most common among these niches were were women dealing with empty nest syndrome. Various web forums about alien sightings become a common ground for those seeking out possible opportunities to feel the rush of life swelling within their womb.
Presently, ex adult entertainment actress Minka has taken to such activities and returned to the industry sporting a large and rather sudden pregnancy. Aside from the obvious questions of the suddenness of the change in figure, many wondered how she was able to conceive at her age. As she dodged the questions, concerned parties reached out to the ACC and investigations proceeded.
Minka was interviewed and examined, her brood having only just begun developing and more growth is expected. While she did not willingly come with agents, she needed to be contained for the sake of stopping further spreading of whichever species she was carrying. The symptoms she's experiencing became clear as she was placed under observation. More youthful demeanor and rejuvenating properties were more obvious, however these symptoms seemed to extend to even restarting her reproductive system and causing her libido to skyrocket. Sexual release was deemed necessary to limit her distress, lest Minka grow restless and more uncooperative.
#alien pregnancy#huge pregnant belly#pregnant captions#pregnant kink#preggo kink#pregnancy captions#mature woman#mature pregnancy
90 notes
·
View notes
Text
On paper, the first candidate looked perfect. Thomas was from rural Tennessee and had studied computer science at the University of Missouri. His résumé said he’d been a professional programmer for eight years, and he’d breezed through a preliminary coding test. All of this was excellent news for Thomas’ prospective boss, Simon Wijckmans, founder of the web security startup C.Side. The 27-year-old Belgian was based in London but was looking for ambitious, fully remote coders.
Thomas had an Anglo-Saxon surname, so Wijckmans was surprised when he clicked into his Google Meet and found himself speaking with a heavily accented young man of Asian origin. Thomas had set a generic image of an office as his background. His internet connection was laggy—odd for a professional coder—and his end of the call was noisy. To Wijckmans, Thomas sounded like he was sitting in a large, crowded space, maybe a dorm or a call center.
Wijckmans fired off his interview questions, and Thomas’ responses were solid enough. But Wijckmans noticed that Thomas seemed most interested in asking about his salary. He didn’t come across as curious about the actual work or about how the company operated or even about benefits like startup stock or health coverage. Odd, thought Wijckmans. The conversation came to a close, and he got ready for the next interview in his queue.
Once again, the applicant said they were based in the US, had an Anglo name, and appeared to be a young Asian man with a thick, non-American accent. He used a basic virtual background, was on a terrible internet connection, and had a single-minded focus on salary. This candidate, though, was wearing glasses. In the lenses, Wijckmans spotted the reflection of multiple screens, and he could make out a white chatbox with messages scrolling by. “He was clearly either chatting with somebody or on some AI tool,” Wijckmans remembers.
On high alert, Wijckmans grabbed screenshots and took notes. After the call ended, he went back over the job applications. He found that his company’s listings were being flooded with applicants just like these: an opening for a full-stack developer got more than 500 applications in a day, far more than usual. And when he looked more deeply into the applicants’ coding tests, he saw that many candidates appeared to have used a virtual private network, or VPN, which allows you to mask your computer’s true location.
Wijckmans didn’t know it yet, but he’d stumbled onto the edges of an audacious, global cybercrime operation. He’d unwittingly made contact with an army of seemingly unassuming IT workers, deployed to work remotely for American and European companies under false identities, all to bankroll the government of North Korea.
With a little help from some friends on the ground, of course.
christina chapman was living in a trailer in Brook Park, Minnesota, a hamlet north of Minneapolis, when she got a note from a recruiter that changed her life. A bubbly 44-year-old with curly red hair and glasses, she loved her dogs and her mom and posting social justice content on TikTok. In her spare time she listened to K-pop, enjoyed Renaissance fairs, and got into cosplay. Chapman was also, according to her sparse online résumé, learning to code online.
It was March 2020 when she clicked on the message in her LinkedIn account. A foreign company was looking for somebody to “be the US face” of the business. The company needed help finding remote employment for overseas workers. Chapman signed on. It’s unclear how fast her workload grew, but by October 2022 she could afford a move from chilly Minnesota to a low-slung, four-bedroom house in Litchfield Park, Arizona. It wasn’t fancy—a suburban corner lot with a few thin trees—but it was a big upgrade over the trailer.
Chapman then started documenting more of her life on TikTok and YouTube, mostly talking about her diet, fitness, or mental health. In one chatty video, shared in June 2023, she described grabbing breakfast on the go—an açaí bowl and a smoothie— because work was so busy. “My clients are going crazy!” she complained. In the background, the camera caught a glimpse of metal racks holding at least a dozen open laptops covered in sticky notes. A few months later, federal investigators raided Chapman’s home, seized the laptops, and eventually filed charges alleging that she had spent three years aiding the “illicit revenue generation efforts” of the government of North Korea.
For maybe a decade, North Korean intelligence services have been training young IT workers and sending them abroad in teams, often to China or Russia. From these bases, they scour the web for job listings all over, usually in software engineering, and usually with Western companies. They favor roles that are fully remote, with solid wages, good access to data and systems, and few responsibilities. Over time they began applying for these jobs using stolen or fake identities and relying on members of their criminal teams to provide fictional references; some have even started using AI to pass coding tests, video interviews, and background checks.
But if an applicant lands a job offer, the syndicate needs somebody on the ground in the country the applicant claims to live in. A fake employee, after all, can’t use the addresses or bank accounts linked to their stolen IDs, and they can’t dial in to a company’s networks from overseas without instantly triggering suspicion. That’s where someone like Christina Chapman comes in.
As the “facilitator” for hundreds of North Korea–linked jobs, Chapman signed fraudulent documents and handled some of the fake workers’ salaries. She would often receive their paychecks in one of her bank accounts, take a cut, and wire the rest overseas: Federal prosecutors say Chapman was promised as much as 30 percent of the money that passed through her hands.
Her most important job, though, was tending the “laptop farm.” After being hired, a fake worker will typically ask for their company computer to be sent to a different address than the one on record—usually with some tale about a last-minute move or needing to stay with a sick relative. The new address, of course, belongs to the facilitator, in this case Chapman. Sometimes the facilitator forwards the laptop to an address overseas, but more commonly that person holds onto it and installs software that allows it to be controlled remotely. Then the fake employee can connect to their machine from anywhere in the world while appearing to be in the US. (“You know how to install Anydesk?” one North Korean operative asked Chapman in 2022. “I do it practically EVERYDAY!” she replied.)
In messages with her handlers, Chapman discussed sending government forms like the I-9, which attests that a person is legally able to work in the US. (“I did my best to copy your signature,” she wrote. “Haha. Thank you,” came the response.) She also did basic tech troubleshooting and dialed into meetings on a worker’s behalf, sometimes on short notice, as in this conversation from November 2023:
Worker: We are going to have laptop setup meeting in 20 mins. Can you join Teams meeting and follow what IT guy say? Because it will require to restart laptop multiple times and I can not handle that. You can mute and just follow what they say ...
Chapman: Who do I say I am?
Worker: You don’t have to say, I will be joining there too.
Chapman: I just typed in the name Daniel. If they ask WHY you are using two devices, just say the microphone on your laptop doesn’t work right ... Most IT people are fine with that explanation.
Sometimes, she got jumpy. “I hope you guys can find other people to do your physical I9s,” she wrote to her bosses in 2023, according to court documents. “I will SEND them for you, but have someone else do the paperwork. I can go to FEDERAL PRISON for falsifying federal documents.” Michael Barnhart, an investigator at cybersecurity company DTEX and a leading expert on the North Korean IT worker threat, says Chapman’s involvement followed a standard pattern—from an innocuous initial contact on LinkedIn to escalating requests. “Little by little, the asks get bigger and bigger,” he says. “Then by the end of the day, you’re asking the facilitator to go to a government facility to pick up an actual government ID.”
By the time investigators raided Chapman’s home, she was housing several dozen laptops, each with a sticky note indicating the fake worker’s identity and employer. Some of the North Korean operatives worked multiple jobs; some had been toiling quietly for years. Prosecutors said at least 300 employers had been pulled into this single scheme, including “a top-five national television network and media company, a premier Silicon Valley technology company, an aerospace and defense manufacturer, an iconic American car manufacturer, a high-end retail store, and one of the most recognizable media and entertainment companies in the world.” Chapman, they alleged, had helped pass along at least $17 million. She pleaded guilty in February 2025 to charges relating to wire fraud, identity theft, and money laundering and is awaiting sentencing.
Chapman’s case is just one of several North Korean fake-worker prosecutions making their way through US courts. A Ukrainian named Oleksandr Didenko has been accused of setting up a freelancing website to connect fake IT workers with stolen identities. Prosecutors say at least one worker was linked to Chapman’s laptop farm and that Didenko also has ties to operations in San Diego and Virginia. Didenko was arrested in Poland last year and was extradited to the United States. In Tennessee, 38-year-old Matthew Knoot is due to stand trial for his alleged role in a scheme that investigators say sent hundreds of thousands of dollars to accounts linked to North Korea via his laptop farm in Nashville. (Knoot has pleaded not guilty.) And in January 2025, Florida prosecutors filed charges against two American citizens, Erick Ntekereze Prince and Emanuel Ashtor, as well as a Mexican accomplice and two North Koreans. (None of the defendants’ lawyers in these cases responded to requests for comment.) The indictments claim that Prince and Ashtor had spent six years running a string of fake staffing companies that placed North Koreans in at least 64 businesses.
before the hermit kingdom had its laptop farms, it had a single confirmed internet connection, at least as far as the outside world could tell. As recently as 2010, that one link to the web was reserved for use by high-ranking officials. Then, in 2011, 27-year-old Kim Jong Un succeeded his father as the country’s dictator. Secretly educated in Switzerland and said to be an avid gamer, the younger Kim made IT a national priority. In 2012, he urged some schools to “pay special attention to intensifying their computer education” to create new possibilities for the government and military. Computer science is now on some high school curricula, while college students can take courses on information security, robotics, and engineering.
The most promising students are taught hacking techniques and foreign languages that can make them more effective operatives. Staff from government agencies including the Reconnaissance General Bureau— the nation’s clandestine intelligence service—recruit the highest-scoring graduates of top schools like Kim Chaek University of Technology (described by many as “the MIT of North Korea”) or the prestigious University of Sciences in Pyongsong. They are promised good wages and unfettered access to the internet—the real internet, not the intranet available to well-off North Koreans, which consists of a mere handful of heavily censored North Korean websites.
The earliest cyberattacks launched by Pyongyang were simple affairs: defacing websites with political messages or launching denial-of-service attacks to shut down US websites. They soon grew more audacious. In 2014, North Korean hackers famously stole and leaked confidential information from Sony’s film studio. Then they targeted financial institutions: Fraudulent trades pulled more than $81 million from the Bank of Bangladesh’s accounts at the New York Federal Reserve. After that, North Korean hackers moved into ransomware—the WannaCry attack in 2017 locked hundreds of thousands of Windows computers in 150 countries and demanded payments in bitcoin. While the amount of revenue the attack generated is up for debate—some say it earned just $140,000 in payouts—it wreaked much wider damage as companies worked to upgrade their systems and security, costing as much as $4 billion, according to one estimate.
Governments responded with more sanctions and stronger security measures, and the regime pivoted, dialing back on ransomware in favor of quieter schemes. It turns out these are also more lucrative: Today, the most valuable tool in North Korea’s cybercrime armory is cryptocurrency theft. In 2022, hackers stole more than $600 million worth of the cryptocurrency ether by attacking the blockchain game Axie Infinity; in February of this year, they robbed the Dubai-based crypto exchange Bybit of $1.5 billion worth of digital currency. The IT pretender scam, meanwhile, seems to have been growing slowly until the pandemic dramatically expanded the number of remote jobs, and Pyongyang saw the perfect opportunity.
In 2024, according to a recent report from South Korea’s National Intelligence Service, the number of people working in North Korea’s cyber divisions—which includes pretenders, crypto thieves, and military hackers—stood at 8,400, up from 6,800 two years earlier. Some of these workers are based in the country, but many are stationed overseas in China, Russia, Pakistan, or elsewhere. They are relatively well compensated, but their posting is hardly cushy.
Teams of 10 to 20 young men live and work out of a single apartment, sleeping four or five to a room and grinding up to 14 hours a day at weird hours to correspond with their remote job’s time zone. They have quotas of illicit earnings they are expected to meet. Their movements are tightly controlled, as are those of their relatives, who are effectively held hostage to prevent defections. “You don’t have any freedom,” says Hyun-Seung Lee, a North Korean defector who lives in Washington, DC, and says some of his old friends were part of such operations. “You’re not allowed to leave the apartment unless you need to purchase something, like grocery shopping, and that is arranged by the team leader. Two or three people must go together so there’s no opportunity for them to explore.”
The US government estimates that a typical team of pretenders can earn up to $3 million each year for Pyongyang. Experts say the money is pumped into everything from Kim Jong Un’s personal slush fund to the country’s nuclear weapons program. A few million dollars may seem small next to the flashy crypto heists— but with so many teams operating in obscurity, the fraud is effective precisely because it is so mundane.
in the summer of 2022, a major multinational company hired a remote engineer to work on website development. “He would dial in to meetings, he would participate in discussions,” an executive at the company told me on condition of anonymity. “His manager said he was considered the most productive member of the team.”
One day, his coworkers organized a surprise to celebrate his birthday. Colleagues gathered on a video call to congratulate him, only to be startled by his response—but it’s not my birthday. After nearly a year at the company, the worker had apparently forgotten the birth date listed in his records. It was enough to spark suspicion, and soon afterward the security team discovered that he was running remote access tools on his work computer, and he was let go. It was only later, when federal investigators discovered one of his pay stubs at Christina Chapman’s laptop farm in Arizona, that the company connected the dots and realized it had employed a foreign agent for nearly a year.
For many pretenders, the goal is simply to earn a good salary to send back to Pyongyang, not so much to steal money or data. “We’ve seen long-tail operations where they were going 10, 12, 18 months working in some of these organizations,” says Adam Meyers, a senior vice president for counter adversary operations at the security company CrowdStrike. Sometimes, though, North Korean operatives last just a few days— enough time to download huge amounts of company data or plant malicious software in a company’s systems before abruptly quitting. That code could alter financial data or manipulate security information. Or these seeds could lay dormant for months, even years.
“The potential risk from even one minute of access to systems is almost unlimited for an individual company,” says Declan Cummings, the head of engineering at software company Cinder. Experts say that attacks are ramping up not just in the US but also in Germany, France, Britain, Japan and other countries. They urge companies to do rigorous due diligence: speak directly to references, watch for candidates making sudden changes of address, use reputable online screening tools, and conduct a physical interview or in-person ID verification.
But none of these methods are foolproof, and AI tools are constantly weakening them. ChatGPT and the like give almost anyone the capacity to answer esoteric questions in real time with unearned confidence, and their fluency with coding threatens to make programming tests irrelevant. AI video filters and deepfakes can also add to the subterfuge.
At an onboarding call, for instance, many HR representatives now ask new employees to hold their ID up to the camera for closer inspection. “But the fraudsters have a neat trick there,” says Donal Greene, a biometrics expert at the online background check provider Certn. They take a green-colored card the exact shape and size of an identity card—a mini green screen—and, using deepfake technology, project the image of an ID onto it. “They can actually move it and show the reflection,” says Greene. “It’s very sophisticated.” North Korean agents have even been known to send look-alikes to pick up a physical ID card from an office or to take a drug test required by prospective employers.
Even security experts can be fooled. In July 2024, Knowbe4, a Florida-based company that offers security training, discovered that a new hire known as “Kyle” was actually a foreign agent. “He interviewed great,” says Brian Jack, KnowBe4’s chief information security officer. “He was on camera, his résumé was right, his background check cleared, his ID cleared verification. We didn’t have any reason to suspect this wasn’t a valid candidate.” But when his facilitator—the US-based individual giving him cover—tried to install malware on Kyle’s company computer, the security team caught on and shut him out.
Back in london, Simon Wijckmans couldn’t let go of the idea that somebody had tried to fool him. He’d just read about the Knowbe4 case, which deepened his suspicions. He conducted background checks and discovered that some of his candidates were definitely using stolen identities. And, he found, some of them were linked to known North Korean operations. So Wijckmans decided to wage a little counter exercise of his own, and he invited me to observe.
I dial in to Google Meet at 3 am Pacific time, tired and bleary. We deliberately picked this offensively early hour because it’s 6 am in Miami, where the candidate, “Harry,” claims to be.
Harry joins the call, looking pretty fresh-faced. He’s maybe in his late twenties, with short, straight, black hair. Everything about him seems deliberately nonspecific: He wears a plain black crewneck sweater and speaks into an off-brand headset. “I just woke up early today for this interview, no problem,” he says. “I know that working with UK hours is kind of a requirement, so I can get my working hours to yours, so no problem with it.”
So far, everything matches the hallmarks of a fake worker. Harry’s virtual background is one of the default options provided by Google Meet, and his connection is a touch slow. His English is good but heavily accented, even though he tells us he was born in New York and grew up in Brooklyn. Wijckmans starts with some typical interview questions, and Harry keeps glancing off to his right as he responds. He talks about various coding languages and name-drops the frameworks he’s familiar with. Wijckmans starts asking some deeper technical questions. Harry pauses. He looks confused. “Can I rejoin the meeting?” he asks. “I have a problem with my microphone.” Wijckman nods, and Harry disappears.
A couple of minutes pass, and I start to fret that we’ve scared him away, but then he pops back into the meeting. His connection isn’t much better, but his answers are clearer. Maybe he restarted his chatbot, or got a coworker to coach him. The call runs a few more minutes and we say goodbye.
Our next applicant calls himself “Nic.” On his résumé he’s got a link to a personal website, but this guy doesn’t look much like the profile photo on the site. This is his second interview with Wijckmans, and we are certain that he’s faking it: He’s one of the applicants who failed the background check after his first call, although he doesn’t know that.
Nic’s English is worse than Harry’s: When he’s asked what time it is, he tells us it’s “six and past” before correcting himself and saying “quarter to seven.” Where does he live? “I’m in Ohio for now,” he beams, like a kid who got something right in a pop quiz.
Several minutes in, though, his answers become nonsensical. Simon asks him a question about web security. “Political leaders ... government officials or the agencies responsible for border security,” Nic says. “They’re responsible for monitoring and also securing the borders, so we can employ the personnel to patrol the borders and also check the documents and enforce the immigration laws.”
I’m swapping messages with Wijckmans on the back channel we’ve set up when it dawns on us: Whatever AI bot Nic seems to be using must have misinterpreted a mention of “Border Gateway Protocol”—a system for sending traffic across the internet—with national borders, and started spewing verbiage about immigration enforcement. “What a waste of time,” Wijckmans messages me. We wrap up the conversation abruptly.
I try to put myself in the seat of a hiring manager or screener who’s under pressure. The fraudsters’ words may not have always made sense, but their test scores and résumés looked solid, and their technical-sounding guff might be enough to fool an uninformed recruiter. I suspect at least one of them could have made it to the next step in some unsuspecting company’s hiring process.
Wijckmans tells me he has a plan if he comes across another pretender. He has created a web page that looks like a standard coding assessment, which he’ll send to fake candidates. As soon as they hit the button to start the test, their browser will spawn dozens of pop-up pages that bounce around the screen, all of them featuring information on how to defect from North Korea. Then loud music plays—a rickroll, “The Star-Spangled Banner”—before the computer starts downloading random files and emits an ear-splitting beep. “Just a little payback,” he says.
Wijckman’s stunt is not going to stop the pretenders, of course. But maybe it will irritate them for a moment. Then they’ll get back to work, signing on from some hacking sweatshop in China or through a laptop farm in the US, and join the next team meeting—a quiet, camera-off chat with coworkers just like me or you.
7 notes
·
View notes
Text
Nightmare Kart: Multi-Track Dreaming
LW Media have done it again. After making one of the best fanworks on the web with “Bloodborne PSX” star developer Lilith Walther has returned to the realm of nightmares to go a little faster this time. How much faster? Somewhere around 200cc or so. Nightmare Kart made its debut on itch.io on June 3rd 2024 and has already become yet another banger from the dev that keeps on giving. First imagined as “Bloodborne Kart” the game hit a minor legal snag and ended up having to scrub any overt references to the Fromsoftware game entirely, leading to its rebranding into the much more original “Nightmare Kart”. But what is Nightmare Kart? And why should you play it? In this article/review I’d like to go over my personal favourite elements as well as some not-so polished ones that all in all make Nightmare Kart an easy sell to anyone looking to have some new fun in an old school way.

Some Background:
If you’ve read my article on Bloodborne PSX you know that I’m a massive fan of LW Media’s previous work. BBPSX was a masterwork in bringing old fashioned clunk to a modern game and letting it thrive on the atmosphere and gameplay quirks that come with something like that. Nightmare Kart is no different. According to Lilith via our previous interview work on Nightmare Kart began not too long after BBPSX released, owing its existence largely to a popular meme used to tease a new Bloodborne game being announced at major gaming shows. Ever since the game’s inception Lilith was hard at work trying to make a kart racer that captured not only the feeling of Bloodborne’s visceral world and combat, but those old school racers we all know and love. I personally am a big fan of Mario Kart 64, and when I got to ask her questions about Nightmare Kart’s development I was delighted to hear that she was taking inspiration from the title. My previous article is linked here as well as Lilith’s tumblr blog and youtube channel where you can see more of the development process in action leading up to the debut of the game.
youtube
Nightmare Kart:
So, back to that question I asked before, what is Nightmare Kart? Inspired by kart racer classics like Mario Kart 64, Diddy Kong Racing, and Crash Team Racing, alongside some rather exciting action picks like Halo, Nightmare Kart is a combination kart racer/battler. In the game you take on the role of “The good hunter”, a mysterious person who awakens in a strange world known as the Pocket Dream before taking to the streets of Miralodia, a gothic styled city beset by all sorts of creatures of the night. The game takes you through a brief singleplayer campaign consisting of several races, battle mode matches, and even boss fights showing off an impressive array of gameplay and animated cutscenes. The base gameplay of the racer is closest to those kart racers I mentioned before, with drifting and boosting being a core part of the racing experience. It does however put some unique souls-like spins on a few things, as well as introducing a brake-slide mechanic which allows you to turn on a dime at the cost of your momentum. A true feast for the senses, consisting of graphics and music to rival Bloodborne PSX in their quality, and a truly impressive feat of development prowess. The game, much like its predecessor, feels so at home in its old school roots that I could almost hear the disc whirring in the drive of my non-existent PlayStation as I played through its campaign and tore through some multiplayer battles.

Gameplay:
Let’s talk more about that gameplay for a bit. As mentioned before Nightmare Kart does a superb job at nailing the feeling of an old school kart racer with a modern twist. A large part of that is its more battle-focused gameplay, as the powerups and controls are much more suited for aggression and duking it out at high speed than just simply racing. The first mechanic to show this off is the Blood Droplets system. As you race a number of enemies will spawn on the track and wander around, some will even try to attack racers as they speed past. Running over one of these enemies or destroying them with one of the several weapons on offer nets an amount of “blood droplets”. These function identically to both Blood Echoes in Bloodborne as well as coins in the Mario Kart series. The more droplets you collect, the higher your maximum speed will increase (as indicated by a red sword shaped arrow on your in-game speedometer). There is, however, a limited number of these enemies on a given track. Once they’re all killed you’ll have to turn to alternative means to collect those speed-granting droplets. Most notably, the destruction of your fellow racers. With a small array of weapons at your disposal granted via small powerup sparks scattered throughout the tracks you’ll be able to cut, smash, shoot, or even call down the stars themselves upon your competition to take their droplets as your own. This feature is most important during races, where speed is much more of a focus, but during the battle modes is where the fighting truly shines.
Deathmatch, elimination, capture the flag, and a score mode based around having the most droplets for your team all serve as the real way to show off Nightmare Kart’s strengths. The brake-slide mentioned before serves as your way to stop and aim ranged weapons like the hunter’s pistol and lever action shotgun, or to reposition yourself for a lunging strike with one of the several melee weapons you’re able to slot in to your melee powerup slot. My personal favourite of these were the gatling gun, which straps a four-barreled monster of a gun to the front of a vehicle of your choice allowing for 40 shots of continuous rapid fire destruction, and the spark-cage, a stand in for the Bloodborne Tonitrus which sends you leaping forward in your kart to smash an electrified mace into your opponents. All of this is headed by a health and stamina system much akin to the game’s former namesake. Health dictates damage done and sustained, while stamina is used by dashing. Also consumed by dashing are “Aether Viles”, viles of blue liquid used in groups of 5 to send you careening forward with a burst of speed. Performing tricks off of jumps by tapping the jump button or simple picking them up from a powerup grants you a number of these viles which you can use to bash into enemies or get ahead in the race standings. With everything I’ve talked about here I hope it’s apparent just how fun Nightmare Kart is to play. I had such an amazing time trashing enemies in deathmatch battles and roaring my way through city streets and forbidden forests.


Graphics/Design:
Nightmare Kart boasts a sense of style rivaled only by the game that came before it. Iterating on the already delightfully dated look that BBPSX had, Nightmare Kart takes it to the next level with original characters and environments that give it that trademark PSX feel. Coming with a built in (and customizeable) CRT filter along with a slew of graphical options ranging from texture warp to pixel distortion the game has quite literally never looked better. My entire time with the game was spent marveling at the track design and style that bleeds from every low-poly crease and jittering texture. Twelve vehicles and a variety of playable characters show off the gothic horror inspirations from Bloodborne and otherwise in perfect pixelated glory. Just as with BBPSX the game shows a mastery of the concept of a “demake”, but being built from the ground up as an original concept the game shows off iconic themes and locations leftover from its Bloodborne origins now with a lovingly crafted layer of originality. Fans of PSX horror and modern retro-makes in general will find nothing but some of the best graphical styling from this game’s blood soaked streets and haunted clock towers.
The real star at the center of well crafted textures and wonderfully low-detail models is the track design. Even if it isn’t legally allowed be Bloodborne Kart, its very apparent that the tracks on offer are nothing less than love letters to a wacky concept contained within a genuine respect for the inspirations. The game’s first few tracks do a top notch job at showing off the sort of homage you’d come to expect from a game inspired by Fromsoft’s gothic masterpiece, but soon descend into the depths of creative (and sometimes seemingly sadistic) level design that sets a kart racer apart from its peers. The Forbidden Forest, for example, features a split path laden with traps and lurking enemies that culminates in an upward clime via jump pads that sends you up the decaying innards of a windmill tower. Delving further into the madness sees you drifting your way through a library maze and making daring jumps to catch up with Nicholas, one of the game’s bosses to put him down for good. The inspiration for this game shines through even the mandatory layer of original art, enhancing into a viscerally wild ride from the first look at the endless void of the Pocket Dream to the cramped quarters of the Outsider’s Mansion.


Sound design/Soundtrack:
At last we arrive at what I consider to be the true highlight of Nightmare Kart. Continuing from BBPSX’s beautifully bitcrushed audio design Nightmare Kart wastes absolutely no time showing off just how much work was put into making the nightmare sound as good as it looks. One thing in particular that stuck with me was the animated cutscenes seen throughout the singleplayer campaign. Fully voice acted and entirely animated the voices in the scenes remind me of the best of the best PlayStation VA work. Extending a massive amount of congratulations to the entire voice cast, which the game’s developer Lilith Walther also provided a performance for. Those sweet filtered voices are only the beginning though, as Nightmare Kart’s soundtrack explodes into a symphony of haunted house jams and retro bangers right from the first screen. I find myself left without a whole lot to say other than just how good the soundtrack is. Composer Evalyn Lark destroyed any doubts I could have had about the game’s soundtrack not living up to the hype that the concept drummed up. The full soundtrack is available on youtube as well as other streaming services and will also be linked in this article for your listening pleasure. A short but sweet section for a set of tunes that I truly feel need to speak for themselves.
youtube
Full soundtrack
A sweet nightmare, and everything that comes with it
This section is a bit different from what I usually do in reviews like this. As I don’t have a second interview with Ms. Walther and I want this to be just as much a discussion about the game as well as a glowing review, I’d like to go over the less than stellar things I experienced while I sped my way through the horrors and bloodsoaked nightmare visions. I’d like to start off this section with this: This article/review is a work of opinion, not objective fact. Everything I put here is based on my own experience with the game. I also understand that in the modern video game landscape we exist in a time where games can receive updates and patches to repair and alter things that might be grinding or frustrating to players. I say all of this out of profuse respect for Ms. Walther and all of those who worked on Nightmare Kart, so that my words cannot be taken as damning evidence that this game is anything other than fun.
Nightmare Kart is above all else, an indie game in the purest meaning of the phrase. Developed by a small team on a small (by video game standards) budget and released entirely for free for anyone to enjoy. Because of this it does suffer from some standard if not frustrating bugs and glitches that made my experience with it nearly perfect, but not quite. Every game (especially today) has it’s rough edges. And with one trying to have so many on purpose (visually anyway) it was bound to have something in it that didn’t function one hundred percent of the time, or something out of place at random intervals.
Common glitches I encountered while playing:
- Hitting walls and ending up underneath the map (this has a minor fix already in the game in the form of a respawn option)
- Controls not being recognized after being hit by an enemy weapon, requiring me to either repress buttons or restart the match/race
- Powerups not actually firing off but being consumed anyway
Please keep in mind that these three things are glitches and do have the potential to be patched out. However, even if they weren’t, I think they added to the charm of the game either way. What was also a part of the charm and became somewhat grating as the game went on were some things I feel work against the games sense of flow and speed that the races would have you want to achieve. These notes are not comprehensive, and come from a place of constructive criticism only. The first frustrating element came in the form of the game’s strict adherence to a retro draw distance. Most of the tracks in the game are enveloped in a dark fog after a certain point, and the track becomes revealed to you as you ride or drive. This works wonders for the atmosphere, but tended to work against me when I was gaining speed and using my aether boosts, only to run face first into a wall because I couldn’t see the turn coming. Moving on from that but in the same vein, running into things can lead into some frustrating moments as well. Some objects and even enemies have hitboxes a fair bit larger than what it would appear. There were several times I tried to skirt past a crucified beast or stack of unbreakable boxes only for a seemingly small part of my cart to clip it, causing the entirety of my speed and momentum to be lost along with my placement. Getting stuck on one of these objects is a different beast entirely, as sometimes the objects invisible hitbox stops you from turning or accelerating altogether until you physically use the reverse button and reorient yourself. On top of all of this, and I’ve certainly seen people state this in far less kind ways, I do feel like the game’s campaign is a bit too easy. Now please keep in mind I did not go into Nightmare Kart expecting a high skill ceiling challenge that would test my mettle at every turn. I also didn’t expect to essentially go on a joyride through the nightmare’s scenic vistas and town squares while a host of NPC drivers waged war with each other far behind me, occasionally sending a volley of stars my way which did very little to actually slow me down. Combined with the fact that enemies didn’t seem to respawn once killed, I found myself with shockingly little to do other than just drive and go for style points on the jumps as I stayed well ahead of the pack. This issue, I will add, was exclusive to the campaign’s races. I found the AI was much more suited for battling it out in the boss battles and other versus modes, the elimination match at the end of the game being a particular highlight of an absolute brawl. None of these issues stand to ruin any part of Nightmare Kart’s fun. Video games are hard to make, and not a single one of them can ever claim to be perfect. These just stand as notes from a personal perspective, meant to offer a bit of a look at what someone jumping into the game and playing it start to finish might experience.
Closing Thoughts:
If you’re looking for something fun to play this summer I can’t recommend Nightmare Kart enough. It really does echo the days of playing head to head with friends in wacky kart racers and deathmatch games, going as far as to combine the two into easily one of the most fun kart games I’ve ever played. If you liked what you read here or would otherwise like to support LW Media’s endeavors, I’ve linked the official itch.io page and steam page for Nightmare Kart below, along with the LW Media patreon and (yet another) link to my previous article on Bloodborne PSX. Thank you so much for reading, now go shred those radical streets.
Links:
Nightmare Kart
Steam
itch.io
LWMedia Patreon
Bloodborne PSX Article
#article#my stuff#my writing#video games#writing#youtube#b0tster#nightmare kart#indie games#review#Youtube
21 notes
·
View notes
Text
Implementing a date picker in a React app can be done using various libraries, and one popular choice is react-datepicker. Here's a step-by-step guide on how to implement a date picker using this library
#reactjs#jsx#react#react native#react developer#react js#react developer tools#react js tutorial#react table#react tutorial#react dev#react js developer#react interview questions#react framework#react data table component#stackoverflow#web design#web dev#web development#website#programming#backedn#backend eng#tech#technology#engineering
0 notes
Text
Implementing a date picker in a React app can be done using various libraries, and one popular choice is react-datepicker. Here's a step-by-step guide on how to implement a date picker using this library
#reactjs#jsx#react#react native#react developer#react js#react developer tools#react js tutorial#react table#react tutorial#react dev#react js developer#react interview questions#react framework#react data table component#stackoverflow#web design#web dev#web development#website#programming#backedn#backend eng#tech#technology#engineering
0 notes
Text
Implementing a date picker in a React app can be done using various libraries, and one popular choice is react-datepicker. Here's a step-by-step guide on how to implement a date picker using this library
#reactjs#jsx#react#react native#react developer#react js#react developer tools#react js tutorial#react table#react tutorial#react dev#react js developer#react interview questions#react framework#react data table component#stackoverflow#web design#web dev#web development#website#programming#backedn#backend eng#tech#technology#engineering
0 notes