#and running code on the vpn
Explore tagged Tumblr posts
Text
I have to replace my laptop (I'm overdue tbh) but it truly goes against my nature to replace something before it literally stops working
#like i understand why it's way better and easier to do so#and im also hoping to get at least a bit of trade in value out of my old laptop#though it does have questionable battery#and occasionally the screen peaces out#but my brain is like#what r we doing?#i can probably make it last another few months#that said it's actually become somewhat problematic with TAing#and running code on the vpn#so i kinda can't wait#even tho i could make it work for pretty much everything else#mercy speaks#phd tag#phd year one tag
4 notes
·
View notes
Text
.
#playing a risky game with the work vpn#i have to wait ~30 mins for code to run then change something then go again etc#and i want to write a thing in between but i CANNOT log into fandom stuff while connected to the work vpn#so have to disconnect and reconnect every time#pray 4 me#personal
0 notes
Text
there's a lot of fear mongering around the new firefox terms of service and privacy policy and most of all of it is bullshit and, just fear mongering. One thing that is concerning however is the following:
Your use of Firefox must follow Mozilla’s Acceptable Use Policy, and you agree that you will not use Firefox to infringe anyone’s rights or violate any applicable laws or regulations.
Before this would only apply to mozilla services such as the matrix chat, firefox send (rip), the vpn, or whatever, but now they are saying it is applied to the browser as well.
And one of the things you shouldn't do according to the policy is, you guessed it:
Upload, download, transmit, display, or grant access to content that includes graphic depictions of sexuality or violence
So mozilla (perhaps accidentally, companies love to do this but also mozilla is kind of stupid), just said you cannot use firefox to browse porn. If it is intentional and they double down on this (which I'm really not sure if they even can, firefox is a program running locally on your computer, it's not a service they can just ban you from or anything like that, again, mozilla is a bit stupid), it's not a reason to use chromium. In the terms of service they also write:
These Terms only apply to the Executable Code version of Firefox, not the Firefox source code.
"the Executable Code" is vague, like does it count if you build it locally on your computer, or is it just the mozilla packaged versions of it downloaded from official sources or whatever idk.
But i think it would make sense forks don't count as the terms apply to "Firefox" and not anything else. So here's some alternative browsers which aren't firefox, but are firefox based:
Librewolf: just firefox, all the crap removed, and lots of privacy features turned on as well. Google is disabled in the search bar, but you can enable it again with a bit of a hack, and by default, history and cookies is cleared when you close it. You can turn that off easily. Basically identical to regular firefox otherwise, it's what i'm currently using.
Zen: Very new but gaining popularity quickly. kind of buggy due to it's recency, but people seem to love it. Main focus is customization, but with improvements in privacy, and speed. Pretty different from other browsers, but that might be what you want.
thats. basically the main two rn. i dont think anything else really would be good for most people and even as someone who really likes to get into things deep with privacy and security and shit i think librewolf is just fine. there's lot of other options but they're kinda all in the categories that these two cover.
While nowhere near in a state to be used as a regular browser, i would keep your eyes on Ladybird which is undergoing the insane challenge of making a web browser from scratch; it's not based on chromium or firefox. The first alpha version is projected to come out next year and it seems very promising.
284 notes
·
View notes
Text
Barbara Gordon's Coding & Computer Cram School is a popular YouTube series. Tucker Foley is a star student.
Barbara Gordon's Cram School posts free online courses for both coding and computer engineering. Think Crash Course in terms of entertainment, but college lecture in terms of depth. Hundreds of thousands of viewers flock to it— students who missed a class, people looking to add new skills to a resume, even simple hobbyists. It’s a project Barbara’s proud of.
Sometimes, when she wants to relax, she’ll even hop in the comments and spend an afternoon troubleshooting a viewer’s project with them.
User “Fryer-Tuck” has especially interesting ones. Barbara finds herself seeking out his comments, checking in on whatever this crazy kid is making next. An app for collecting GPS pings and assembling them on a map in real-time, an algorithm that connects geographic points to predict something’s movement taking a hundred other variables into account, simplified versions of incredibly complex homemade programs so they can run on incredibly limited CPU’s.
(Barbara wants to buy the kid a PC. It seems he’s got natural talent, but he keeps making reference to a PDA. Talk about 90’s! This guy’s hardware probably predates his birth.)
She chats with him more and more, switching to less public PM threads, and eventually, he opens up. His latest project, though, is not something Barbara has personal experience with.
FT: so if you found, hypothetically, a mysterious glowing substance that affects tech in weird and wacky ways that could totally have potential but might be vaguely sentient/otherworldly…. what would you do and how would you experiment with it. safely, of course. and hypothetically
BG: I’d make sure all my tests were in disposable devices and quarantined programs to keep it from infecting my important stuff. Dare I ask… how weird and wacky is it?
FT: uhhh. theoretically, a person composed of this substance once used it to enter a video game. like physical body, into the computer, onto the screen? moving around and talking and fighting enemies within the game?
FT: its been experimented with before, but not on any tech with a brain. just basic shields and blasters and stuff, its an energy source. also was put in a car once
FT: i wanna see how it affects software, yk? bc i already know it can. mess around and see how far i can push it
BG: […]
FT: … barbara?
BG: Sorry, thinking. Would you mind sharing more details? You said “blasters?”
Honestly. Kid genius with access to some truly wacky materials and even wackier weapons, she needs to start a file on him before he full sends to either hero or villain.
[OR: Tucker is a self-taught hacker, but if he were to credit a teacher, he'd name Barbara Gordon's Coding & Computer Cram School! He's even caught the attention of Dr. Gordon herself. She's full of sage advice, and with how she preaches the value of a good VPN, he's sure she's not pro-government. Maybe she'll help him as he studies the many applications of ecto-tech!]
#she does end up sending tucker a PC lol#and after she learns he has experience supporting a superhero team maybe pushes his name forward to WEs outreach program for r&d potentials#picks him up by the scruff and says MY coding buddy#also fun fact she had a phd in library science at one point. i like that about her i think we should talk about it a little more#also tucker was making a ghost reporting & tracking app for amity parkers#dpxdc#dcxdp#barbara gordon#tucker foley#prompt#kipwrite
600 notes
·
View notes
Text
VPNs aren't just for pirates and company data anymore
A friend complained to me that they couldn't access pr0n anymore because the government is now requiring ID to verify age where they are, and due to data leaks and privacy issues, didn't want to share their ID even though they're of legal age.
Shit like this doesn't work on the intended target. It only frustrates people who are aren't tech savvy while a lot of kids have already found their way around it because that's what kids do ¯\_(ツ)_/¯
When I talk about VPNs (virtual private networks), non-tech savvy people's eyes glaze over 😂
It sounds like complicated, unknowable magic. It's not! And you don't even have to understand it to use it!
With the government and ISPs (internet service providers) invading privacy more and more and hackers breaking in and stealing user data from companies, VPNs are becoming necessary.
Some Things a VPN Does for You:
hides your data from others
can make your internet speeds faster if your ISP does speed throttling (purposely making your speed slower)
hides what you're doing from your ISP
keeps you safer from some malware, viruses, hackers, and trackers
allows you to access things that are either restricted in your area or not available in your area (such as content in other countries)
keeps you safer when you're out in public connected to wifi
Below is a basic infographic on how VPNs work. When you access the internet, a VPN encrypts your data - making it into a secret code that can't be read by anyone else including your ISP.
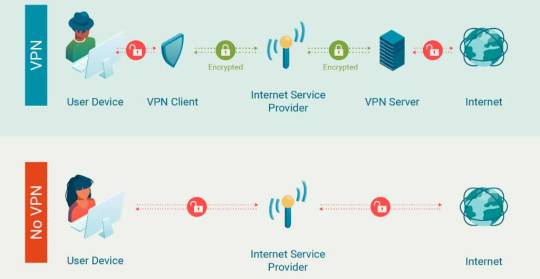
Tech companies, ISPs, etc. want you to think VPNs are complicated so that you won't use them.
When searching for a free VPN, please be aware that a lot of the free VPN services out there are malware or full of viruses and trackers.
Either do some research into which one to choose or use a paid VPN service. You can either pay monthly or yearly - the yearly is always cheaper in the long run.
Some of the Top Rated VPN Services:
ExpressVPN $7 - $13/month
NordVPN $3 - $13/month
Surfshark $2 - $14/month
PrivateInternetAccess $2 - $12/month
ProtonVPN (some sites block this one) $4 - $10/month
CyberGhost $2 - $13/month
I use ExpressVPN, so for the purposes of this post, I'm going to use screenshots from ExpressVPN.
Once you have an account, download the program from the website to your desktop/laptop or find the app on Android or iOS app stores.
Signing in requires a code that the VPN will email to you that unlocks all the features. Pay attention when the program installs because it'll ask you about preferences, and you can easily check yes on blocking pr0n when that's the reason you wanted a VPN in the first place 😂
When the program is open, you'll see this:

As you can see in the screenshot, not only do I have the program, but I have an ExpressVPN icon on my browser. The program installs this automatically, and when the program is running, the icon will have a green checkmark on it so you know it's working in your browser.
You'll notice I've recently connected using Japan. I did this so I could watch a series that isn't available outside of Japan.
The program automatically chooses a location near you, but if you want to access things that are restricted to you, make sure you click on the three dots to the right of the selected location (see screenshot below) and search for a state/country/place that your content will be available in.

Once your location is selected, click on the start/power button, and you'll get a popup notification from your computer that ExpressVPN is connected.
Go to the site you want to use and use it like you normally would.
Here's what it should look like when it's running correctly:

Keep in mind that if you leave a VPN running all the time (which is perfectly fine to do), search engines like Google will assume you live wherever ExpressVPN tells it you live, so searching for "stores near me" will give you results that aren't close to you.
When you're done using the VPN, just hit the power button again and it shuts off.
I use this on all my handheld devices, my desktop, and my laptop for business and personal reasons. I'm a pirate, and I've been using VPNs for a long time, yet none of the ISPs I've used have ever given me a warning about torrenting.
Good luck, and enjoy all the new things you can access!
BTW for anybody wondering, my desktop wallpaper is a map of the world's time zones. So pretty!! 😍
75 notes
·
View notes
Text
ios users: did you know safari has extensions? id just switched from it to firefox thinking itd be more secure, but Now... im very 💪 with mobile security!!
just a heads up, you do need to go into settings > safari > exrensions and manually enable everything.
heres what i use:
adguard: pretty standard ad/tracker blocker. comes with a dns protector and vpn i havent tested, as I've outsourced mine.
hyperweb: another ad blocker, but also advances search results so your first hits are more credible or preferable. can also add custom scripts.
baking soda: replaces custom video players (aside from youtube) with a minimal html video tag.
vinegar: companion of baking soda that works solely on youtube!! it removes ads, allows picture-in-picture playing, and continues playing in the background.
pipifier: i use this in case the fizzy bundles (name of baling soda + vinegar) pip function goes down.
noir: defaults to dark mode on webpages.
honey: automatically checks for and runs coupon codes when online shopping so you always get the best deal.
happy & safe browsing everyone!! consider sending a kofi 🧿❣️
122 notes
·
View notes
Note
Your list of ride or die couples is iconic and has so many of my faves, flower of evil bad buddy it's okay that's love lighter and princess one spring night like yes give me a show where the entire story is two individuals willing to take on the world together and for each other, it's my favorite dynamic and we don't get a lot of it especially in heterosexual couples. You have amazing taste and I would take any other suggestions you have of the same dynamic.
Hi anon! Thank you for the kind words, I do agree that I have amazing taste. :) The Ride or Die list is specifically about drama couples who we get to see be in a confirmed romantic relationship for at least half of the drama's run, with their relationship development the primary focus of the plot. I think of them as battle couples; they face challenges together and stay loyal even when they struggle. There actually are not that many of these in dramaland, which is why they are so precious to me and why I hold them close.
That said, since I wrote that post I do think we have gotten a few more entries for the list, so here are some additional recs for you:
Won and Sarang, King the Land
(S Korea, Netflix)

It was getting salty about fan reaction to this show that inspired the Ride or Die list in the first place, and I am happy to report that when it finished its run, these two were still a rock solid couple. This drama is entirely about their relationship and we get lots of time with them as an established couple getting to know each other and settling into a great relationship. I love it and will stab anyone who says it's boring.
Ten and Prem, Cooking Crush
(Thailand, YouTube)

Ten and Prem, my beloveds! These two meet, start liking each other, and move into dating in relatively short order, and the back half of the show has them navigating a slew of external conflicts that would normally result in a lot of breakups and false starts. But not for them! They slay every relationship demon via the power of communication.
Maki and Haruta, Ossan's Love Returns
(Japan, Gagaoolala)

This one comes with a caveat that this is technically a sequel season, and the first one would very much not qualify them for this list. But you don't have to watch that first season if you don't want to, and in this return they are a couple the entire time and there is just so much time spent on them navigating their relationship and facing every day life challenges. They're an extremely charming pair.
Yuanzhou and Ruyi, A Journey to Love
(China, iQIYI)
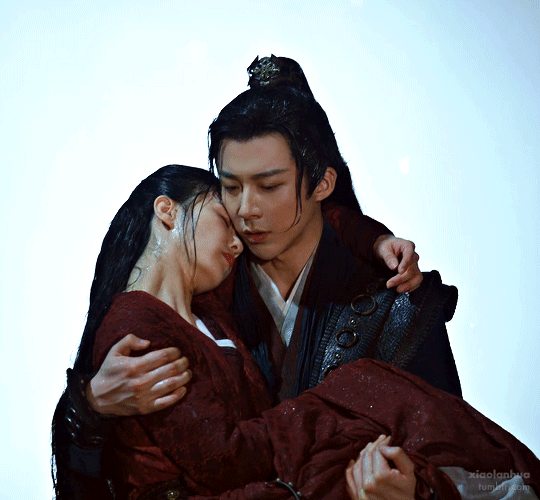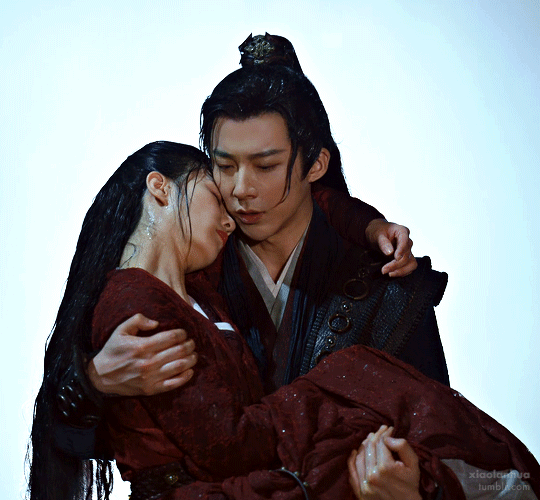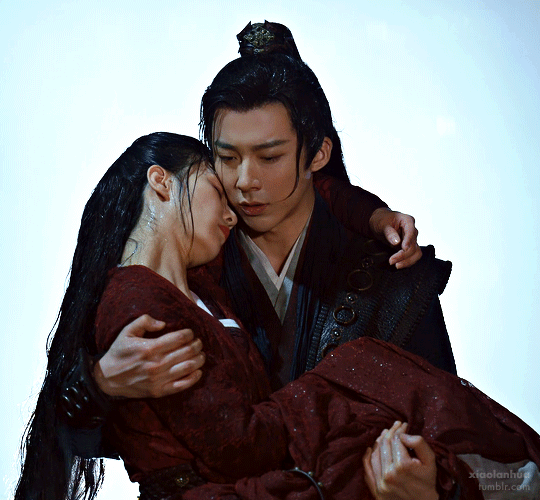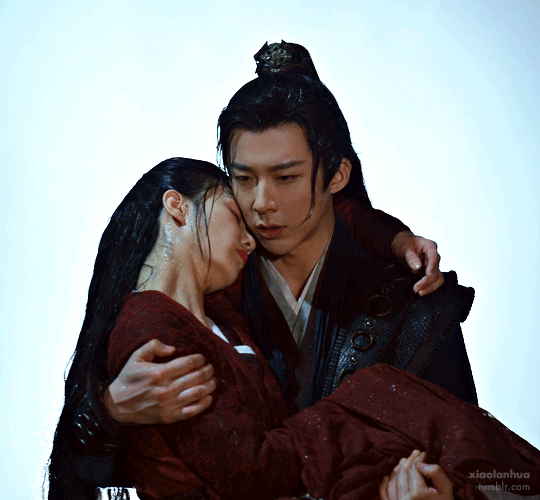
The most literal battle couple on this list, we have ourselves an assassin and spy master pair here. They meet, she decides he's the perfect baby daddy specimen, and a hilarious pursuit begins. These two get together remarkably early for a cdrama and face just so many trials and tribulations, phew. But they face them together in their color coded costumes and look amazing doing it. CW: the plot is basically about them and a band of buds leading a suicide mission so, uh, there will be many deaths, and their ending can be read as ambiguous but IMO is actually quite a happily ever after in context.
Achi and Karan, Cherry Magic Thailand
(Thailand, Viu)
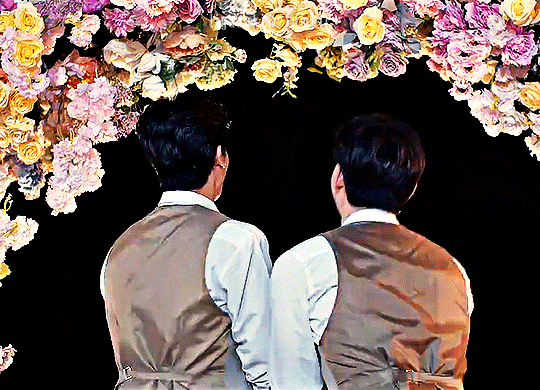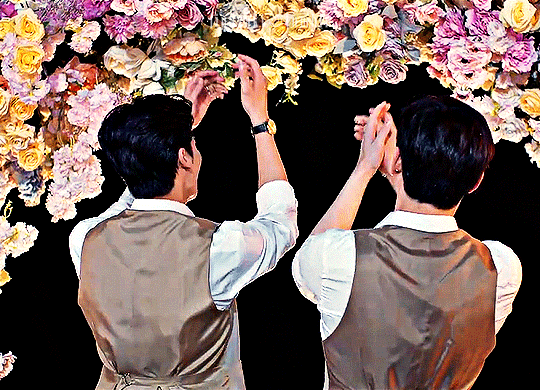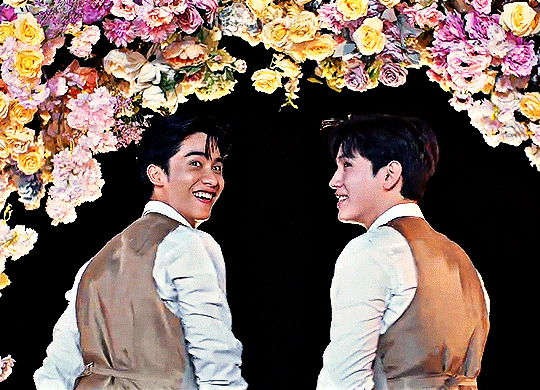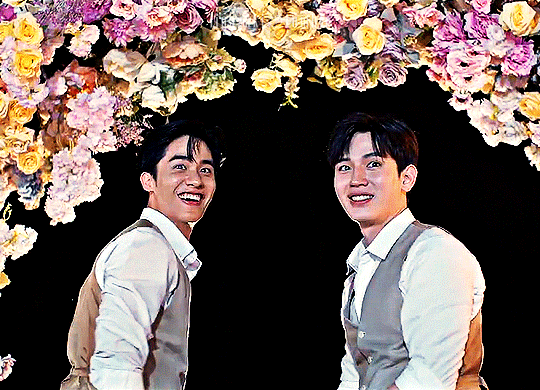
Karan and Achi are so into each other it's embarrassing, and we get to see them build and deepen and maintain their relationship every step of the way. This one is a little harder to watch--you will need a VPN if you're not in Thailand--but so worth the effort, trust me. And you may recognize this actor pair from the main list, because they are in fact the same beautiful faces behind Pete and Kao of Dark Blue Kiss. Congratulations to Tay Tawan and New Thitipoom for being the only actors who have achieved the honor of making the coveted Ride or Die list twice.
#king the land#cooking crush#ossan's love returns#a journey to love#cherry magic th#shan recommends#shan answers
34 notes
·
View notes
Text
one interesting thing in programming is the prevalence of scripting languages, which refer to programming languages that are built around "scripts" which are interpreted at run-time rather than other types of programs which are compiled into machine code and then executed. The important distinction here is that with scripting languages, you write your code and run it, with no in-between compilation step (which often can take a while).
as the name implies, scripting languages are really good for "scripting" things! so if you have a certain set of steps you want to execute every time you log in to your computer (i.e. turn on my vpn, adjust my timezone, deactivate my webcam) you'll use something like Bash to write that script, rather than an ahead-of-time compiled language like C.
The most common (by far, like it's not even close) scripting language is javascript, which you may know from the internet. But another popular scripting language, especially for videogames, is Lua.
There's a few cool things about Lua, but one of my favorites is that it's Brazilian! Nearly every programming language in widespread use was developed in the USA, but Lua was developed at the Pontifical Catholic University of Rio de Janeiro, which is where it is still developed to this day!
While made famous by roblox, which uses Lua for scripting the games you can make within it, manh other games also use Lua, such as:
Garry's Mod
BeamNG.Drive
Civilization V & VI
Don't Starve
The Elder Scrolls Online
Factorio
Grim Fandango
Payday: The Heist & 2
Powder Toy
S.T.A.L.K.E.R.
Saints Row 2, The Third, and IV
SimCity 4
Star Wars: Battlefront I & II (the originals)
Tap Tap Revenge
The Witcher
World of Warcraft
and more!
52 notes
·
View notes
Text
Privacy Concerns: How Gen Z is Protecting Their Data?
What’s the first thing you do when a pop-up asks, “Do you accept cookies?”—immediately click “Accept” or hesitate as if pondering the secrets of the universe?
If you’re Gen Z, the answer might surprise you. While they’re often labelled as the oversharing Snapchat generation, they’re also becoming the poster children for digital privacy warriors. Want to know how? Stick around. By the end of this blog, you’ll not only uncover Gen Z’s surprising strategies for safeguarding their data but also pick up a few tips to reclaim control of your own.

The Paradox of Gen Z: Masters of Oversharing, Yet Privacy-Conscious
On the surface, Gen Z seems like the generation that lives for Instagram reels, TikTok challenges, and viral tweets. But underneath the filters and hashtags lies a surprising truth: they care—deeply—about their digital footprints. They may post a dance video on TikTok but won’t hesitate to use pseudonyms on Facebook or create private Instagram accounts (finstas) to keep their personal lives personal.

How Did Gen Z Get So Privacy-Savvy?
Growing Up With Data Breaches
From hearing about massive breaches (remember the infamous Cambridge Analytica scandal?) to watching documentaries like The Social Dilemma, Gen Z grew up knowing that even their memes could fuel someone’s data-mining empire. Lesson learned? Share strategically.

Cybersecurity 101 Is Their Second Nature
For this generation, two-factor authentication isn’t optional—it’s a lifestyle. “123456” as a password? Please, that’s so 2010. Gen Z knows their passwords should look like they smashed their keyboard in frustration.

Tech Education in Schools
Unlike older generations, who stumbled their way through the internet’s dark corners, Gen Z often received digital literacy education. They know the difference between a phishing scam and an actual email from their bank. (Pro tip: If it starts with “Dear Customer,” run.)

Privacy Tips We Can All Steal (Ethically, of Course)
Gen Z is showing us the way, and here are some of their best practices:
Think Before You Link
Clicking on that shady “You’ve Won a Free iPhone!” ad is the digital equivalent of walking into a trap. Gen Z gets it—they avoid suspicious links like the plague.

Limit Permissions
Why should a weather app need access to your contacts? Gen Z regularly audits app permissions, keeping unnecessary snoopers at bay.

Use Burners for Fun
They know that creating a “throwaway” email address for subscriptions keeps spam out of their primary inbox.

The Ironic Humor of Gen Z’s Privacy Stance
Isn’t it ironic that the generation branded as addicted to screens is leading the charge for digital privacy? They’ll meme about data breaches but won’t let companies snoop on their Spotify playlists.

Conclusion: A Balancing Act
Gen Z proves you can live your best digital life and protect your data. Whether it’s using VPNs, switching to encrypted messaging apps, or simply saying no to invasive permissions, they’re rewriting the rules for online privacy.
The takeaway? Protecting your data doesn’t mean going off the grid; it means being intentional with your digital choices.
Do you think Gen Z has cracked the code on balancing online presence and privacy, or are they just lucky digital natives? Drop your thoughts in the comments below!

6 notes
·
View notes
Note
What do you do when you are at work but for whatever reason you have to wait to keep working (development breaking bug that is being fixed by other people, code compiling, waiting on person working on X thing you need so you can start work on Y, etc)
You're talking about downtime. Whenever I have downtime I try to be productive if I can, but the type of downtime determines what I can do. There's two main types of downtime - when my workstation is still usable and when it isn't.

If my workstation is still usable (e.g. the build is broken but I can still look at code/script/assets/etc.) then I notify my team that I've got some bandwidth and downtime to help out as a second set of eyes on any tasks my team might need help with. I can do code, design, or asset reviews for teammates and I can look over the various Slack discussions on other in-progress bug fixes and features to comment if I feel like I can contribute something helpful. I might not be able to run the game to test or validate anything, but I can still contribute my skill and knowledge to others who aren't having downtime.

If my workstation is unusable (e.g. all system resources are dedicated to building the game, building assets, compiling a level/lighting/etc., network or VPN down, etc.) then I really can't do much. I can't do reviews or join those conversations. In those situations I've traditionally done things to pass the time like listen to music or a podcast, scroll through social media, or think about what to write next on the blog. More recently, I've been focusing on leaning away from the social media scrolling and being more mindful so I have been taking the opportunity for mental and emotional "digestion" by not focusing on anything external and allowing my mind to process the normal emotional experiences in my life. It was difficult to start, but has definitely helped with my focus and my attention since I've started doing it.
[Join us on Discord] and/or [Support us on Patreon]
Got a burning question you want answered?
Short questions: Ask a Game Dev on Twitter
Long questions: Ask a Game Dev on Tumblr
Frequent Questions: The FAQ
25 notes
·
View notes
Note
...<ENCRYPTING MESSAGE>
...
...<ENCRYPTION COMPLETE>
...
Hello? Um... Wow. Verily, this is strange. Um... I am Lord Raymond Hurst VI of the House of Remembrance. That is... probably quite strange for thee as well... Rest assured, this is not a matter of animosity between Karrakins and those of the Armory, and I mean thee no harm, I- well I suppose I should simply explain.
I do contact thee on behalf of mine dearest sister in inquiry of this "echo.exe" thou doth use. We know not its exact nature, but it seems to be a powerful method of encryption. We... would do well to invest in an upgrade to what we do use at present.
I assure thee, I assure thee! This is not a Karrakin plot of any nature that might bring the ire of the Armory. This is a... well I do suppose it is a humanitarian crisis of sorts. Mine sister doth believe that the both of the clones which do run this account would be... sympathetic.
So I pray thee will explain more of this "echo.exe" and whether thou believest it may help us as it doth help thee.
Mine deepest thanks!
Sincerely,
Raymond
[ECHO.EXE RUNNING]
◂▸ T-E passed me back the datapad for this one, said it was some of that "coding witchcraft" that's more my speed. They can be so dramatic sometimes :P
◂▸ Please don't stress yourself too much about our respective allegiances your Lordship; it's a bit strange aye, I won't deny you that but I understand completely. The reason I cobbled ECHO together in the first place was... well, not dissimilar to the reason I think you're asking about it.
◂▸ First off- I know it's probably not my place to say this, but I'm proud you're reaching out despite the fear. Trust me when I say I know how difficult that is. I promise you, if anyone you don't want hearing about this asks me? I've never heard of you o7 I've seen some of what's been happening, from a distance. It's not fair what's happening to your sister, and it's not fair how much weight's been put on her shoulders. Hoping your mother's too busy with that upcoming duel to blame her for the sudden hostility toward your house. Take care of yourselves alright?
◂▸ Now, onto your actual question: I'm happy to tell you more about ECHO, might even be able to talk you through how to tailor the code to what you need it for. What exactly ECHO does is disguise any messages we send out from this account, cloaking the code to any IP addresses originating from Purview space. I've got it keyed in to cloak us from the devices of any tech guys I know personally too, wouldn't be much of a tool if all it took was a VPN to get around it. Since it's embedded into the posts themselves, you can't get around it by sending the link through from non-Purview space. I've got it coded to block any screengrabs too, so it's about as good as I was able to manage. There's a standard encryption there too, for good measure :]
◂▸ Essentially? With a bit of tweaking, nobody you don't want to see your messages would get to, and nobody monitering your mail would see anything amiss since it cloaks itself in outgoing data. Unless everyone on the planet stopped posting altogether, you should be safe. I made it with secrecy in mind, on top of security- sometimes... sometimes higher powers knowing you're keeping secrets is as dangerous as them knowing what those secrets are. I feel like we might be in the same boat there.
◂▸ I'm attaching the skeleton file here, with some blanks where the specific locations should be: if you need me to walk you through what needs filling out where and how to do that? I'm keeping a channel open for you o7 FILE: [echo_draft04.exe]
◂▸ ...hm? Oh, T-E wants to say something too, here-
XIII▸ Thank you Helios. Lord Raymond, correct? Please tell Lady Rosceline from me, that- ...that whatever her mother says, the collective punishment is no fault of hers. There wasn't a way for her to save them. She had no choice in any of this. It was just... cruelty. It was done because Lady Violet could, because she holds power and wanted to remind her of it. That was the only lesson involved.
XIII▸ Keep your heads down until you think you're clear. It's safer to blend in than shout defiance. Whispering it gets you further, anyway.
//
11 notes
·
View notes
Note
Speaking of advertising in 2015 I worked at a tech startup advertising startup that used cookies (digital ones) to track individuals (doesn’t matter if you used a VPN) and they had a way to “inject” ads right into videos bypassing adblockers. It was very creepy tbh. The company was bought by Google and we all got two years of pay before being let go. I honestly hate it. So yes. Advertising executives are scum.
It has changed a lot over the past decade, but there used to be a perception that tech companies were generally progressive and for the benefit of their users. Google used to have “don’t be evil” as the core of their employee code of conduct but they officially dropped that in 2018 (which coincidentally was the same year that GDPR became enforceable and gave people in EU countries some decent rights for privacy).
In the United States we just don’t have equivalent federal legislation to protect citizens (California, Virginia, and Colorado do have some state-level protections).
the bottom line is that tech companies are owned and operated by extremely wealthy individuals who have a vested interest in being able to profit though digital tracking and advertising.
We’re entering the 4th era of digital surveillance:
1st era was IP address tracking (VPNs provided protection for this)
2nd era was cookies and ‘super cookies’ (a range of techniques that serve the same purpose as cookies but are harder to clear from your browser)
3rd era is fingerprinting - possible since 2005 but I think became common in practice only since ~2015 and is a method which uses a bunch of metadata and pinpoints you as an individual based on your unique set of attributes.
I think that a lot of people are still under the misconception that using Chrome incognito mode gives you some privacy
Google's Chrome browser does not provide protection against trackers or fingerprinters in Incognito Mode.
4th era is coming soon and enabled by similar technology that enable LLM and will be able to identify you by the unique way you interact with technology (e.g. the style/tone of my writing in this post has characteristics that are unique to me, and also very hard for me to avoid!).
the 4th era for me is horrifying- imagine your employer being able to take a sample of your writing (from emails or company chat) and be able to identify content you’ve posted online that you thought you were posting anonymously?
—
btw, if anyone is curious about seeing where you stand in terms of digital fingerprinting here are some online tools you can use to get an idea - both are free, no login/signup and take just a few seconds to run:
15 notes
·
View notes
Text
For years, it's been an inconvenient truth within the cybersecurity industry that the network security devices sold to protect customers from spies and cybercriminals are, themselves, often the machines those intruders hack to gain access to their targets. Again and again, vulnerabilities in “perimeter” devices like firewalls and VPN appliances have become footholds for sophisticated hackers trying to break into the very systems those appliances were designed to safeguard.
Now one cybersecurity vendor is revealing how intensely—and for how long—it has battled with one group of hackers that have sought to exploit its products to their own advantage. For more than five years, the UK cybersecurity firm Sophos engaged in a cat-and-mouse game with one loosely connected team of adversaries who targeted its firewalls. The company went so far as to track down and monitor the specific devices on which the hackers were testing their intrusion techniques, surveil the hackers at work, and ultimately trace that focused, years-long exploitation effort to a single network of vulnerability researchers in Chengdu, China.
On Thursday, Sophos chronicled that half-decade-long war with those Chinese hackers in a report that details its escalating tit-for-tat. The company went as far as discreetly installing its own “implants” on the Chinese hackers' Sophos devices to monitor and preempt their attempts at exploiting its firewalls. Sophos researchers even eventually obtained from the hackers' test machines a specimen of “bootkit” malware designed to hide undetectably in the firewalls' low-level code used to boot up the devices, a trick that has never been seen in the wild.
In the process, Sophos analysts identified a series of hacking campaigns that had started with indiscriminate mass exploitation of its products but eventually became more stealthy and targeted, hitting nuclear energy suppliers and regulators, military targets including a military hospital, telecoms, government and intelligence agencies, and the airport of one national capital. While most of the targets—which Sophos declined to identify in greater detail—were in South and Southeast Asia, a smaller number were in Europe, the Middle East, and the United States.
Sophos' report ties those multiple hacking campaigns—with varying levels of confidence—to Chinese state-sponsored hacking groups including those known as APT41, APT31, and Volt Typhoon, the latter of which is a particularly aggressive team that has sought the ability to disrupt critical infrastructure in the US, including power grids. But the common thread throughout those efforts to hack Sophos' devices, the company says, is not one of those previously identified hackers groups but instead a broader network of researchers that appears to have developed hacking techniques and supplied them to the Chinese government. Sophos' analysts tie that exploit development to an academic institute and a contractor, both around Chengdu: Sichuan Silence Information Technology—a firm previously tied by Meta to Chinese state-run disinformation efforts—and the University of Electronic Science and Technology of China.
Sophos says it’s telling that story now not just to share a glimpse of China's pipeline of hacking research and development, but also to break the cybersecurity industry's awkward silence around the larger issue of vulnerabilities in security appliances serving as entry points for hackers. In just the past year, for instance, flaws in security products from other vendors including Ivanti, Fortinet, Cisco, and Palo Alto have all been exploited in mass hacking or targeted intrusion campaigns. “This is becoming a bit of an open secret. People understand this is happening, but unfortunately everyone is zip,” says Sophos chief information security officer Ross McKerchar, miming pulling a zipper across his lips. “We're taking a different approach, trying to be very transparent, to address this head-on and meet our adversary on the battlefield.”
From One Hacked Display to Waves of Mass Intrusion
As Sophos tells it, the company's long-running battle with the Chinese hackers began in 2018 with a breach of Sophos itself. The company discovered a malware infection on a computer running a display screen in the Ahmedabad office of its India-based subsidiary Cyberoam. The malware had gotten Sophos' attention due to its noisy scanning of the network. But when the company's analysts looked more closely, they found that the hackers behind it had already compromised other machines on the Cyberoam network with a more sophisticated rootkit they identified as CloudSnooper. In retrospect, the company believes that initial intrusion was designed to gain intelligence about Sophos products that would enable follow-on attacks on its customers.
Then in the spring of 2020, Sophos began to learn about a broad campaign of indiscriminate infections of tens of thousands of firewalls around the world in an apparent attempt to install a trojan called Asnarök and create what it calls “operational relay boxes” or ORBs—essentially a botnet of compromised machines the hackers could use as launching points for other operations. The campaign was surprisingly well resourced, exploiting multiple zero-day vulnerabilities the hackers appeared to have discovered in Sophos appliances. Only a bug in the malware's cleanup attempts on a small fraction of the affected machines allowed Sophos to analyze the intrusions and begin to study the hackers targeting its products.
As Sophos pushed out patches to its firewalls, its team responsible for threat intelligence and incident response, which it calls X-Ops, also began an effort to track its adversary: Sophos included in its “hotfix" for the hackers' intrusions additional code that would collect more data from customers' devices. That new data collection revealed that a single Sophos device registered in February of 2020 in Chengdu showed signs of early alterations similar to the Asnarök malware. “We started to find tiny little indicators of the attack that predated any other activity,” McKerchar says.
Using registration data and records of downloads of code Sophos made available to its customers, the X-Ops team eventually identified a handful of machines it believed were being used as guinea pig devices for Chinese hackers as they sought to find vulnerabilities and test their intrusion techniques prior to deployment. Some of them seemed to have been obtained by a Chengdu-based company called Sichuan Silence Information Technology. Others were tied to an individual who used the handle TStark, whom X-Ops analysts then found had held a position at the University of Electronic Science and Technology of China, also in Chengdu.
X-Ops analysts could even observe individuals using computers and IP addresses tied to the test devices reading Sophos' online materials that detailed the firewalls' architecture. “We could see them researching us,” McKerchar says.
In late April of 2020, Dutch police worked with Sophos to seize a Netherlands-based server that Sophos had identified as being used in the Asnarök infection wave. In June of that year, however, the hackers launched another round of their mass intrusions, and Sophos found they had significantly reduced the complexity and “noise” of their malware in an attempt to evade detection. Yet through the increased data collection from its devices and the intelligence it had assembled on the Chengdu exploit development group, Sophos was able to spot the malware and push out patches for the vulnerabilities the hackers had used within a week, and even identify a “patient zero” machine where the new malware had first been tested two months earlier.
The next month, X-Ops took its most aggressive step yet in countering the effort to exploit its devices, deploying its own spy implants to the Sophos devices in Chengdu they were testing on—essentially hacking the hackers, albeit only through code added to a few installations of its own products the hackers had obtained. Sophos says that preemptive surveillance allowed the company to obtain key portions of the hackers' code and head off a third wave of their intrusions, catching it after only two customers had been compromised and pushing out a patch designed to block the attacks, while obfuscating that fix to avoid tipping off the hackers to Sophos' full knowledge of their techniques.
“In the first wave, we were on the back foot. In the second wave, it was an even match,” says McKerchar. “The third attack, we preempted.”
A New Phase of the Game
Starting in 2021, Sophos says it began to see far more targeted attacks from Chinese hacker groups exploiting its products, many of which it was able to uncover due to its efforts to surveil the research of the Chengdu-based exploit development network. Over the next two years, the hackers continued hijack vulnerabilities in Sophos appliances in a wide variety of targeted attacks hitting dozens of targets in Asia and the West.
In September of 2022, for instance, Sophos found a campaign exploiting a vulnerability in its products that had breached military and intelligence agencies in a Southeast Asian country, as well as other targets including water utilities and electric generation facilities in the same region. Later, Sophos says, a different Chinese state-sponsored group appears to have exploited a bypass for its patch for that vulnerability to target government agencies outside of Asia, in one instance hacking an embassy shortly before it was set to host officials from China's ruling Communist Party. It also found intrusions at another country's nuclear energy regulatory agency, then a military facility in the same country and the airport of the country's capital city, as well as other hacking incidents that targeted Tibetan exiles.
“We just opened the door on a huge amount of high-end targeted activity, a Pandora's Box of threat intelligence," McKerchar says.
As the hackers' tooling continued to evolve in response to Sophos' attempts to head them off, the company's X-Ops researchers at one point pulled from a test device they were surveilling a unique new specimen of malware: The hackers had built a “bootkit,” an early attempt at malware designed to infect a Sophos firewall's low-level code that's used to boot up the device before its operating system is loaded, which would make the malware far harder to detect—the first time Sophos believes that sort of firewall bootkit has ever been seen.
X-Ops never found that bootkit deployed on an actual victim's machine, but Sophos CISO McKerchar says he can't rule out that it was in fact used somewhere and evaded detection. “We certainly tried to hunt for it, and we have some capability to do that,” says McKerchar. “But I would be brash to say it's never been used in the wild.”
As Sophos has tried to understand the motives of the Chengdu-based network of hackers digging up vulnerabilities and providing them to the Chinese state, that picture has been complicated by the strange fact that the researchers finding those flaws may have on two occasions also reported them to Sophos itself through its “bug bounty” program. On one occasion, for instance, the exact vulnerability used in a hacking campaign was reported to Sophos by a researcher with a Chinese IP address just after it was first used in an exploitation campaign—Sophos paid the researcher $20,000 for their findings.
That bizarre incongruity with the Chengdu-based researchers' apparent role as suppliers of intrusion techniques for Chinese state hacking groups and its bug bounty reports to Sophos, McKerchar argues, show perhaps how loose the connections are between the researchers finding these vulnerabilities and the state hackers exploiting those bugs. “I think this is a security research community which is patriotically aligned with PRC objectives,” he says, referencing the People's Republic of China. “But they're not averse to making a bit of money on the side.”
Contacts at the University of Electronic Science and Technology China didn't respond to WIRED's request for comment on Sophos' report. Sichuan Silence Information Technology couldn't be reached for comment, and appears to have no working website.
Sophos' timeline of its struggle against a highly adaptive adversaries sussing out its products' hackable flaws points to the success of China's efforts to corral its security research community and funnel its discoveries of vulnerabilities to the government, says Dakota Cary, a researcher at the Atlantic Council, a nonpartisan think tank, who has focused on that Chinese exploit development pipeline. He points to China's efforts, for instance, to foster hacking competitions as a source of intrusion techniques for its offensive hacking efforts, as well as 2021 legislation that requires researchers and companies based in China to report to the government any hackable bug they find in a product.
“In Sophos' document, you see the interconnectedness of that system kind of shine through,” says Cary. “The culture of these organizations working together or competing for work, and the way that the government is trying to centralize collection of vulnerabilities and then distribute those tools to offensive teams—you see all of that reflected.”
Sophos' report also warns, however, that in the most recent phase of its long-running conflict with the Chinese hackers, they appear more than ever before to have shifted from finding new vulnerabilities in firewalls to exploiting outdated, years-old installations of its products that are no longer receiving updates. That means, company CEO Joe Levy writes in an accompanying document, that device owners need to get rid of unsupported “end-of-life” devices, and security vendors need to be clear with customers about the end-of-life dates of those machines to avoid letting them become unpatched points of entry onto their network. Sophos says it's seen more than a thousand end-of-life devices targeted in just the past 18 months.
“The only problem now isn't the zero-day vulnerability,” says Levy, using the term “zero-day” to mean a newly discovered hackable flaw in software that has no patch. “The problem is the 365-day vulnerability, or the 1,500-day vulnerability, where you've got devices that are on the internet that have lapsed into a state of neglect.”
That warning was echoed by Cybersecurity and Infrastructure Security Agency assistant director for cybersecurity Jeff Greene, who stresses the risk of Chinese hackers exploiting older, unpatched systems, as well as the broader, ironic threat of network perimeter appliances serving as entry points for hackers. “These edge devices often have inherent insecurities, they’re often not managed once they’re put out, they're not patched," says Greene. “We’ll leave a trail of these devices for a long time that attackers will be looking to compromise.”
Sophos CISO McKerchar says the company is revealing its five-year fight with the Chengdu-based hacking network to amplify those warnings, but also to end a kind of cybersecurity industry omertà around the growing issue of security companies' own products creating vulnerabilities for their customers. “Trust in the industry has been massively eroded in the past few years. There's a huge amount of skepticism across about the way that vendors are handling these risks, but we've relied on silence instead,” says McKerchar. “We want to show a bit of vulnerability ourselves, recognize that we've had problems, then tell the story about how we stepped up.”
8 notes
·
View notes
Text

(MICHAEL CIMINO, CISMALE, HE/HIM) They say the city never forgets a name and MIGUEL RIVERA is no testament to that. The TWENTY-FIVE-year-old has carved out their place in NYC’s underbelly. On the surface, they’re all QUIRKY, smooth moves and sharp eyes. But dig a little deeper and you’ll find something far more dangerous , STUBBORN, with no hesitation and even less remorse. They move through the streets like they own them, wearing the colors of the THE ASSEMBLY and running the game as a HACKER. Some say they’ve always been here. Others swear something’s changed. Either way, they’re not just part of the story.
“I can hack a city grid blindfolded, but sure, let’s pretend your six-digit password is impressive.”
Affiliation: The Assembly Occupation: Hacker | Surveillance Tech | Digital Mischief Coordinator™ Face Claim: Michael Cimino Age: 25 Sexual Orientation: Bisexual Vibe: Golden retriever energy + keyboard gremlin Alignment: Chaotic good with a morally gray badge
OVERVIEW
Miguel Rivera is the reason the darkest ops team in New York hasn't murdered each other yet. While the rest of The Assembly moves in silence and shadows, Miguel moves in memes, caffeine, and absurd commentary. He’s the sunshine in a room full of storm clouds—cracking jokes while cracking encrypted files.
Yes, he can break into government servers like it's a game of Sudoku. Yes, he knows everyone's dirty secrets. But somehow, Miguel manages to hold it all with a light touch. He’s funny, warm, loud when he shouldn't be—and too smart for his own good. While others push agendas, Miguel keeps the heart of The Assembly somewhat human.
Don’t mistake the sunshine for softness though—he’ll fry your hard drive mid-sentence and eat your lunch while he does it.
SKILLS
Elite Hacker Energy: Breaks into encrypted systems while dancing to '90s playlists.
Surveillance Expert: Runs the screens, drones, wiretaps—sometimes with glitter stickers on the gear.
Distraction Master: Talks his way out of almost anything, including getting caught in places he shouldn’t be.
Creative Sabotage: Think: replacing a corrupt politician’s files with cat videos and crashing a mobster's crypto wallet with confetti code.
People Person™: The one Assembly agent who can talk to a barista and a senator and make them both laugh.
BACKSTORY
Miguel Rivera believes in light. Even when it’s dim, even when it flickers, even when no one else can see it—he does. Because when you lose everything and still wake up smiling, what else can you be but hope in a hoodie?
Raised in the Bronx by his grandmother after his parents were killed in a crossfire, Miguel learned early that grief doesn’t ask for permission. He also learned that grief doesn’t win—not if you don’t let it. His abuela filled their tiny apartment with prayer candles and laughter, cooking lessons and telenovelas, and a constant refrain: “Find joy, even in the ruins.” So Miguel did. First in machines. Then in people.
He was a self-taught prodigy—building computers before he hit puberty, hacking school firewalls for fun, setting up VPNs for his neighborhood to stream movies for free. He had the mind of a genius and the heart of a class clown. Teachers adored him, classmates gravitated to him, but behind all that light was a quiet knowledge of loss. He didn’t let it define him—but he never forgot it, either.
When his grandmother passed during his sophomore year of college, something in him cracked—but it didn’t break. Instead, he turned pain into purpose. He got louder. Brighter. Smarter. He started exposing corruption in quiet, clever ways. And when he hacked a NYPD database as a prank, turning their annual gala slideshow into SpongeBob GIFs, The Assembly came calling.
They expected a jaded, sharp-tongued hacker. What they got was someone who talks too fast, wears headphones like a crown, and calls his surveillance drones “my babies.” He doesn’t just track targets—he watches over people. The team calls him "the kid" but listens when he speaks, because his heart? It’s as dangerous as his code.
Miguel jokes so he doesn’t fall apart. He smiles so others don’t have to fake it. And when it really counts—when things are falling apart and no one knows what comes next—he’s the one still holding onto the idea that maybe, just maybe, there’s still something worth saving.
TRAITS
Sunshine with Bite: Always smiling, always joking—but fiercely loyal and deeply protective.
Empathic Tech Nerd: Understands people as much as he understands code.
Morally Awake in a Corrupt World: He jokes to cope, but he’s here to make a difference—even if it’s behind the curtain.
Talks Fast, Thinks Faster: Words spill out like a stream of consciousness. Often ridiculous. Always on brand.
Unintentional Charmer: Doesn’t know how hot or smart he is. It’s infuriating.
CONNECTION
The Grumpy to His Sunshine: Someone in The Assembly who finds him very annoying… until they don’t.
The One He Accidentally Hacked: Oops. That virus was meant for someone else. Now they’re in his DMs.
The Crush He Can’t Shut Up About: A rival? A cop? A morally-questionable crush he keeps gushing about while the team rolls their eyes.
The Bestie with Matching Chaos: Another upbeat character who causes joint mischief with Miguel. Trouble, but make it adorable.
The One He Secretly Protects: Maybe a civilian or someone who he wants to protect. He monitors them like a silent guardian.
4 notes
·
View notes
Text
Cyberchase: How to Hack the Motherboard
So, when I was writing my episode discussion post on Cyberchase Season 1 Episode 1 "Lost My Marbles", I mentioned that I might make another post about the security breach that allowed The Hacker to infect Motherboard with the virus. What did The Hacker do to set this up? How did the kids accidentally open the breach? And other questions like that. I have a bit of background in software engineering. I will try to keep things as simple as possible.
Much of this is head-canon built on top of what we see in the episode. Of course, the show plays it fast and loose with computer terminology. Don't try to hack things in real life. You will go to prison.
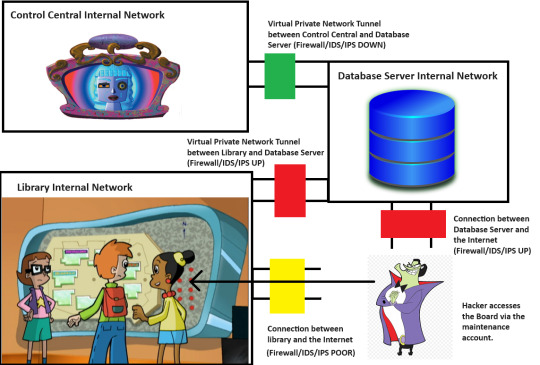
So, here's an MSPaint diagram of a tiny piece of Motherboard's setup. Keep in mind that she is the god of the Internet, and her Internet may even stretch beyond Earth into other galaxies.
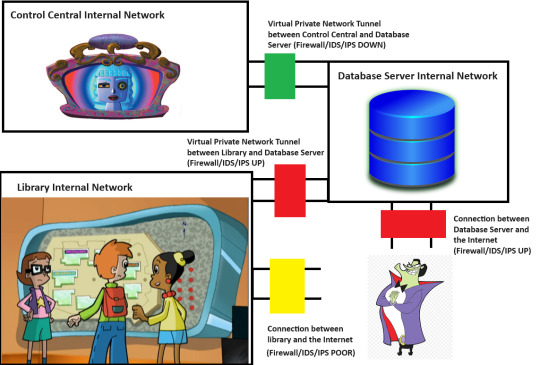
So, there are three separate network segments here. We have the library's internal network, which has the big board on it. We have Control Central's internal network, which has Motherboard on it. And then we have a Database Server internal network, which has a Database Server running on it.
The Database Server is something that I invented here. Remember that this whole diagram is head-canon. However, it's not too far-fetched to think that Motherboard must reach across Cyberspace to a separate Database Server, maybe at the Cybrary.
Now, we know that Motherboard is not directly reachable, even with her Firewall down. Otherwise, The Hacker wouldn't have needed a separate security breach to get to her. He would have just pushed the virus once she took down her firewall for maintenance.
However, Motherboard has a Virtual Private Network (VPN) tunnel to the Database Server. If The Hacker can compromise the Database Server and get his virus in there, it might be able to ride the tunnel into Control Central.
The purpose of any Firewall is to apply a set of rules to any network traffic going into or out of a network, device or application. A good Firewall configuration allows on the traffic that is needed and denies everything else. Motherboard's firewall between herself and the Database Server is currently down. The Database Server itself has connection points to the larger Internet without using a VPN tunnel. However, the Database Server's own Firewall for that access point is UP. If The Hacker tried to throw his virus at that access point, it wouldn't work.
However, there is another connection point into the Database Server. This is another VPN tunnel from the library network. Let's say that the board retrieves the data on the locations of different objects on the map and the icons for those objects by reading one of the Databases. Maybe the board also writes data to the Database to log what directions people requested.
The point here is that some traffic from the Board is authorized to pass through the Firewall on that VPN tunnel. Now, is there a way for The Hacker to get the Board to send authorized traffic over the VPN tunnel to tell the Database Server to open a breach in the Firewall for that public access point? Maybe. It is an Internet-of-Things (ioT) device. Alot of people get these devices, and then they either leave passwords set to their defaults or they forget to keep the sofware patches up to date.
There is a public access point to the Board with a poorly-configured firewall. Maybe there's a way for him to get inside. It may be possible for him to dump the virus code into the board, but there's no guarantee that it would be able to go any further, since the Firewall between the Board and the Database Server is working.
So, let's think about the Board as its own thing.

Suppose that we have two user accounts associated with the board. There is a Principle of Least Privilege that states that a given user account or system process should only be given the minimum amount of permissions required to perform its tasking. That way, if the user account or system process attempts to do something out of line with its permissions, it won't be allowed to perform the operation.
However, if you leave other unnecessary permissions open, and the user account or system process attempts to do something outside of its original intended operations, then the operation may succeed and have unintended consequences.
This also links up with the software development concept of the Minimum Viable Product. You build your software to perform only the exact tasking that it needs it perform. You don't put any additional, undocumented functions in there. Otherwise, those functions could activate and have unexpected consequences.
The board's purpose it to display the different locations. It allows for users to input two points, and it will draw a line between them to assist in navigation. We also established earlier that it reads its information from the Database and writes other information out to the Database.
However, suppose there was some undocumented functionality here. Suppose the developers had a special feature installed in the board that ran a cleanup command against the Database if you pressed three buttons in quick succession. Suppose that the cleanup command in question could be any arbitrary command. Therefore, the developers put the command into a configuration file to be read and executed by the software at runtime.
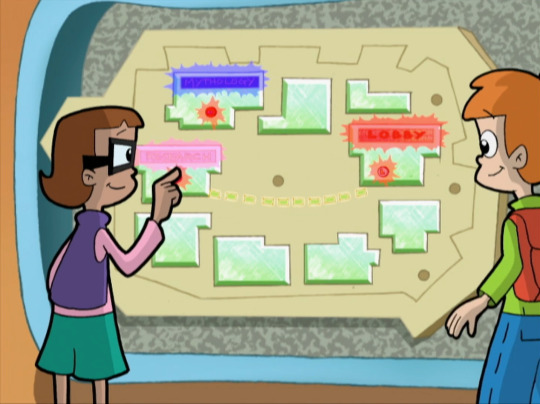
However, the developers knew that if some kids turned up and started poking the map, they could accidentally kick off the Database Cleanup command. They removed the Database Cleanup command from the configuration file. That way, if someone did poke three buttons in quick succession, the software would check the configuration file, see that there was no command defined, and then do nothing.
The trouble is that they left the part of the software that read the configuration file and ran the arbitrary command in place. So, if the command was somehow added back to that part of the configuration file, then there would be a command for the software to run. Then, if someone else pushed the three buttons, that command would be run. So, yeah, someone could put a command in there to write a bunch of junk into the Database until it filled up and crashed. Again, these are commands being sent to the Database from the Board. The Firewall would let them through just fine.
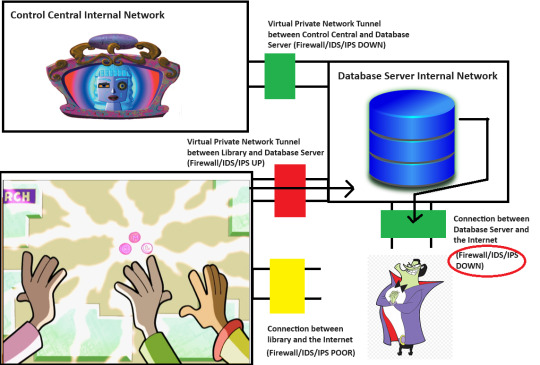
That's pretty bad, but that only lets them modify the Database, right? It's not like they can just tell the Database to open the Firewall on the server that it is sitting on, right?
Well, what if one of the things that the Database could do, upon request, was to open a command shell on the server and run a command. And what if, that command shell was able to run commands that impacted things on the server beyond the Database itself.
What if we called it "xp_cmdshell" and called the Database Server "Microsoft SQL Server 2000". Windows XP and Microsoft SQL Server 2000 would have been around at the time of "Lost My Marbles" after all. Those were also the key players in the real-world Heartland Payment Systems data breach of 2008, which inspired this post.
But hey, just because the Database could open a command shell on the Database Server doesn't mean that The Hacker could use it to bust the Database Server's external Firewall, right? He still needs a way to execute "xp_cmdshell". So, he needs an account with the correct permissions to tell the Database to execute "xp_cmdshell", and he needs the Database itself to have high-enough permissions to run a command via "xp_cmdshell" that can bust the Database Server's external firewall and open a path to Motherboard. Thankfully, the Database only run the "xp_cmdshell" for the top-level Database Administrator account.
This is where we get back to the Principle of Least Privilege. The Board should connect to the Database with a fairly low-power account. It only needs to read-from and write-to a few Database tables after all. Likewise, the Database itself should have been started on the Database Server by a fairly low-power account, as it only needs to handle reading and writing its own set of tables.
But then some moron decided to hook up the Board to the Database Server on the top-level Database Administrator Account. So, if the Board was configured to send an "xp_cmdshell" command, the Database would run it. Oh, and another moron decided to have the Database Server start the Database with the "root" account for that server. So, if the Board was configured to send in an "xp_cmdshell" command to nuke the external Firewall, then the Database would be able to nuke the external Firewall.

There is a principle called Defense-in-Depth, where you build multiple layers of defense around your critical item. That way, if a layer fails, you may be okay. We're running out of layers.
We only have one or two layers left. We know that the Board doesn't run "xp_cmdshell" for its regular operations today. Sure it has an undocumented debug mode that allows someone to execute any command in its configuration file (including "xp_cmdshell") against the Database. But someone would need to get to that file.
The board's main account doesn't give you a filesystem to play with, as they wouldn't want kids running up, poking things, and deleting the filesystem. No, you only get the interfaces that you get. You can pick two items and see a path between them. Or you can pick three items and see the undocumented debug mode run whatever command is in the configuration file.
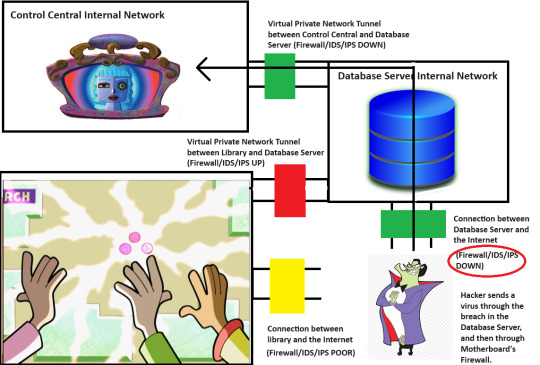
But what if there was some sort of maintenance account accessible through the Internet that didn't enable someone to send commands to the Database, but would enable someone to get into the filesystem and mess around with it? And what if that maintenance account was still using a weak or default password because people just don't check that for IoT devices?

So, he's in the Board's filesystem now. That's concerning. And wouldn't you know it, yet another moron left that critical configuration file in a state where the maintenance account can make changes to it. So, of course, he found the empty configuration item for the cleanup command. Remember, this was setup to run any arbitrary command. Of course, he put in an "xp_cmdshell" command that tells the Database to nuke the external firewall on its own server.
While The Hacker was able to put the command in place, the maintenance account doesn't have the power to send commands to the Database on its own. That power is only enabled for the system account tied to the Board's user interface. So, he still has to rely on someone in the real world to push three buttons in quick succession.


Well...shit.
That's not good.

That's not good at all.


Seriously though, don't try this at home.
I suppose we can speculate on the nature of the virus. We know from Season 1 Episode 14 "Cool It" that Motherboard goes through more cryoxide than normal due to the virus. There are actual computer viruses out there that were designed to turn off heat safety warnings on CPUs and then cause them to run hotter. Some CPUs would eventually melt and ruin the computer.
The original infection destroyed the Encryptor Chip, and it is stated that only a replacement Encryptor Chip could cure the virus. The name suggests that it deals with data encryption, but perhaps it is also a virus cleanup tool. Perhaps it worked to weaken the existing virus until it was eventually overwhelmed and destroyed. Perhaps the virus exhausted most of its strength destroying the Encryptor Chip first.
In any case, curing the virus permanently would end the show.
#cyberchase#2000s#cartoon#nostalgia#pbs kids#2000s childhood#not for use in real life#you'll get busted
12 notes
·
View notes
Text
hi blog it's friday! ugh work is a shitshow and i am already exhausted. today is one of those days where nothing is working like it's supposed to and sadly, the person everyone comes to when shit isn't working is me.
and omg i just asked someone on my team a question and their response was to send me a piece of code that's 1500 lines long. maybe 20 years ago i would have spent the day stepping through the code to find the answers i need but lol i don't have that kind of time anymore.
on a more fun note, i am finally getting around to configuring the laptop i bought last year to do all my media stuff. i've got my vpn and my shared folder and my screen capture video player settings all updated.
yesterday i finished vol 4 of the wotakoi manga and it continues to be super cute! i just put a hold on vol 5 at my library and i'm very excited for it to come in. i'm still feeling betrayed by prime putting ads into the anime but i now have all the episodes downloaded to my computer! i just need to find some better subtitles.
this weekend i will prob take a break from running to let my calf muscle rest. it doesn't hurt anymore but i still feel a bit of soreness when i walk, so i'm not going to be dumb and ignore it. maybe i'll use my extra time for writing! i still have aspirations of finished the yuhuang interview fic!
also now that i'm back on my wotakoi bullshit i kind of want the king's avatar crossover. mostly because i think it's hilarious how yu wenzhou and hirotaka have basically the same exact look to them and i think that's funny.
i hope everyone has a nice weekend!
#random text post silliness#happy friday blog#is it happy hour yet i am so tired#the bullshit started at 8:30am and i think it's gonna go all day
6 notes
·
View notes