#cloud based cyber security
Text
https://www.blogbangboom.com/blog/aws-cloud-services-empowering-businesses-with-scalability-and-flexibility
AWS Cloud Services: Empowering Businesses with Scalability and Flexibility
In today's digital age, businesses are increasingly relying on cloud services to meet their computing and storage needs. Amazon Web Services (AWS) has emerged as a leading cloud service provider, offering a wide range of services to help businesses scale, innovate, and stay competitive.
#aws cloud services#aws cloud server#server hosting aws#devops consulting services#aws hosting provider#aws cloud infrastructure#devops consulting companies#aws cloud technologies#cloud based cyber security#azure cloud computing services#cloud architecture design
0 notes
Text
17 Essential Steps to Fortify Your AI Application
Master AI security with these 17 essential steps! #AISecurity #DataProtection #CyberSecurity
In today’s digital landscape, securing AI applications is crucial for maintaining trust and ensuring data integrity. Here’s a comprehensive guide to the 17 essential steps for fortifying your AI application.
1. Encrypt Data
Ensure that all data, both in transit and at rest, is encrypted. Use industry-standard encryption protocols like AES (Advanced Encryption Standard) for data at rest and TLS…

View On WordPress
#access controls#AI security#authentication mechanisms#Cloud security#cyber security#Cybersecurity#data encryption#differential privacy#encrypted communications#Incident response#input validation#model protection#Multi-factor authentication#Regulatory Compliance#role-based access control#secure coding#securing AI applications#Security#Security assessments#Security Best Practices#software patching#technology#threat monitoring
3 notes
·
View notes
Text

In 2023, the trend you need to know about is improved extended detection and response with XDR. Strengthen security while enhancing the efficiency. Read More...
#Cyber Security XDR#Unified Communications#Voiceware Platform#PBX Solution#Cloud PBX#Cloud Technology#VoIP Solutions#VoIP Services#cloud based system#Communications System#Business Telephone System#SIP Trunking#Technology#VoIP Phone#VoIP#IP telephony#mobile Phones#Telephone#cloud Computing#IP Telephone Home#VoIP technology#Modern VoIP Phone#Hotel Phone System#Voiceware#phone suite phone system#voiceware express#phonesuite support#phonesuite console#hospitality communication#Busines Phonenumber
12 notes
·
View notes
Text
How AI turbocharges your threat hunting game - CyberTalk
New Post has been published on https://thedigitalinsider.com/how-ai-turbocharges-your-threat-hunting-game-cybertalk/
How AI turbocharges your threat hunting game - CyberTalk


EXECUTIVE SUMMARY:
Over 90 percent of organizations consider threat hunting a challenge. More specifically, seventy-one percent say that both prioritizing alerts to investigate and gathering enough data to evaluate a signal’s maliciousness can be quite difficult.
Threat hunting is necessary simply because no cyber security protections are always 100% effective. An active defense is needed, as opposed to dependence on ‘set it and forget it’ types of security tools.
But, despite active threat hunting, many persistent threats often remain undiscovered — until it’s too late. Or at least, that used to be the case.
Artificial intelligence is changing the game. Threat hunting is a task “…that could be accelerated, or in some cases replaced, by AI,” says Check Point’s CTO, Dr. Dorit Dor.
Evolve your threat hunting
Many threat hunters contend with visibility blind-spots, non-interoperable tools and growing complexity due to the nature of hybrid environments. But the right tools can empower threat hunters to contain threats quickly, minimizing the potential impact and expenses associated with an attack.
1. Self-learning. AI-powered cyber security solutions that assist with threat hunting can learn from new threats and update their internal knowledge bases. In our high-risk digital environments, this level of auto-adaptability is indispensable, as it keeps security staff ahead of attacks.
2. Speed and scale. AI-driven threat hunting engines can also process extensive quantities of data in real-time. This allows for pattern and indicator of compromise identification at speed and scale – as never seen before.
3. Predictive analytics. As AI-powered engines parse through your organization’s historical data, the AI can then predict potential threat vectors and vulnerabilities. In turn, security staff can proactively implement means of mitigating associated issues.
4. Collaborative threat hunting. AI-based tools can facilitate collaboration between security analysts by correlating data from different sources. They can then suggest potential threat connections that neither party would have observed independently. This can be huge.
5. Automated response. AI security solutions can automate responses to certain types of threats after they’re identified. For instance, AI can block certain IP addresses or isolate compromised systems, reducing friction and response times.
Implicit challenges
Although AI-based tools can serve as dependable allies for threat hunters, AI cannot yet replace human analysts. Human staff members ensure a nuanced understanding and contextualization of cyber threats.
The right solution
What should you look for when it comes to AI-powered threat hunting tools? Prioritize tools that deliver rich, contextualized insights. Ensure cross-correlation across endpoints, network, mobile, email and cloud in order to identify the most deceptive and sophisticated of cyber attacks. Make sure that your entire security estate is protected.
Are you ready to leverage the power of AI for threat hunting? Get ready to hunt smarter, faster and more efficiently while leveraging the power of AI. The future of threat hunting has arrived. Get more information here.
Lastly, to receive more timely cyber security news, insights and cutting-edge analyses, please sign up for the cybertalk.org newsletter.
#ai#ai security#AI-driven solution#AI-powered#AI-powered cyber security#alerts#analyses#Analytics#artificial#Artificial Intelligence#automation#bases#behavioral analysis#challenge#Check Point#Cloud#Collaboration#collaborative#complexity#compromise#CTO#cutting#cyber#cyber attacks#cyber security#cyber security news#Cyber Threats#data#defense#Digital Transformation
0 notes
Text
How to Choose the Right Antivirus Software: A Comprehensive Guide
In today’s digital age, where our lives are intricately intertwined with technology, safeguarding our digital assets has become paramount. With the proliferation of cyber threats, antivirus software stands as a crucial line of defense against malware, viruses, ransomware, and other malicious entities lurking online. However, the abundance of antivirus options can be overwhelming, making it…

View On WordPress
#A#Advanced Behavioral Analysis Software#Advanced Threat Detection#Antivirus#Antivirus Software#Automated Security Incident Response#Cloud Security Solutions#Cloud-Based Endpoint Security Platform#Comprehensive Data Protection Suite#Continuous Vulnerability Assessment#Cyber Defense#Cybersecurity#Cybersecurity Awareness Training#Data Encryption Software#Data Protection#Defense#Encryption#Endpoint Protection Suite#Endpoint Security#Firewall#Firewall Protection#Identity Theft#Identity Theft Prevention#Integrated Firewall Protection Mechanism#Internet Security Software#Malware#Malware Detection#Malware Removal Tool#Mobile Device Management#Multi-Layered Malware Defense System
0 notes
Text
Cloud-Based VoIP Phone Systems – The Backbone For Small Businesses
Several reasons have contributed to the popularity of VoIP phone systems for small officers. One top reason is that it gives users access to a whole plethora of features and tools that can be used for business purposes. These modern-day office phone systems come with features like auto-attendant, music on hold, voicemail to email, and so on. With all these features, these phone systems have become a popular alternative to traditional landline phones and, at the same time, serve the employees in several other ways.

Cloud-based VoIP office phone systems have also gained massive popularity; as a matter of fact, they have a number of benefits that we will discuss in this post.
Cloud-Based Voip
The first benefit is that, as a business owner, you will not have to install any special hardware or equipment. It will use your Internet to store your information, calls, messages, and contacts in the cloud telephone systems. It is the latest technology in terms of business communications, and it appeals the most to businesses that don't have the budget to hire an IT team.

Other Major Benefits
This System Is Scalable
Compared to traditional VoIP phone systems for small offices, this system is scalable per your business. To add new lines, you will not have to put in any hard work at all, and you will also not have to change phone systems as your company grows.
Easy Configuration and Management
Compared to other office phone systems, it is incredibly easy to configure and manage this system. You can change your office hours, your greeting, you can add a department line, or even start an office in another state or location. Everything can be done in just a few minutes with the help of the Internet and also no specialised training would be required for the same.

Easy To Install and Use
There is no major equipment needed to run this system, and this makes it very easy to install and use. It is the most straightforward phone system for small offices that can be configured very quickly, and with cloud-hosted small business systems, your business will become fast.
#phone systems for small office#office phone systems#telephone systems#Telephone systems for small business#small office phone system#communication solutions#voip phone system#business phone systems Australia#video conference system#online collaboration tools#voip technology installations#cloud-hosted small business systems#Cloud-Based Voip#cyber security software#Voip office phone system#Voip phone systems#digital handsets voip system#VoIP office phone systems solutions#Voip Phone System data#Flexible Business VoIP Phone Service
1 note
·
View note
Text

#Cybersecurity is critical for any business that wants to maintain reliability with its data storage.#With changing data regulations#a growing number of attacks on data infrastructures#and the increased popularity of cloud-based storage#both the Cyber and Cloud Security market have surged considerably.#Join the rapidly growing CISO executive network: https://www.execweb.com/
0 notes
Text
#IT Services#IT consulting services#cyber security management services#managed detection and response mdr services#attack surface reduction#governance risk and compliance services#cmmc compliance#cloud computing#it infrastructure consulting services#Support Managed services#cloud based solutions#data analytics and ai#data analytics platform#Software development services#power generation industry#microsoft gold partner
0 notes
Text
Introduction to Armchair Activism
Current feelings about the state of radblr.
Fundamentals
"Yes, Everyone on the Internet Is a Loser." Luke Smith. Sep 3, 2022. YouTube.
An activist movement can be a place to build community with like-minded people, but action is its foremost purpose, not community. To allow yourself and other activists to remain effective, you are obliged to abandon your personal dislikes of other individual activists. Disagreements are worth discussion, but interpersonal toxicity is not.
Connect with in-person community and do not unhealthily over-prioritize online community. Over-prioritization of online community is self-harm.
Luke is a loser, but his channel is teeming with entry-level digital literacy information and advice pertaining to healthy use of technology for us cyborgs.
"Surveillance Self-Defense: Tips, Tools and How-Tos For Safer Online Communication." Electronic Frontier Foundation.
Hackblossom, outdated, is discontinued. The EFF project Surveillance Self-Defense is up-to-date, comprehensive, and follows personal educational principles of simplicity and concision.
To learn more about general (not focused solely on personal action) cybersecurity, visit Cybersecurity by Codecademy and Cyber Security Tutorial by W3Schools. Both contain further segueways into other important digital literacies.
Direct recommendation: Install and set up the linux distribution Tails on a cheap flash drive.
Direct recommendation: Develop your own home network security schema.
Direct recommendation: Always enable 2FA security for Tumblr, disable active / inactive status sharing, and learn to queue reblogs and posts to protect against others' interpretations of your time zone.
Direct recommendation: It's both possible and relatively simple to host your own instance of a search engine using SearXNG.
Zero-Knowledge Architecture.
As a remote activist (even if also a hybrid activist), none of your action should be taken on, using, or interfacing with non-zero-knowledge-architecture services. Tumblr is, of course, a risk in and of itself, but you should not be using services provided by companies such as Google, Microsoft, or any others based in or with servers hosted in 13-eyes agreement nations.
Search for services (email, word processor, cloud storage) which emphasize zero-knowledge architecture. Businesses whose services are structured as such cannot hand over your data and information, as they cannot access it in the first place. If they cannot access the majority of your metadata, either - all the better.
Communications for Armchair Activism
"Technical Writing." Google.
Contained within the linked page at Google Developers, the self-paced, online, pre-class material for courses Technical Writing One, Technical Writing Two, and Tech Writing for Accessibility teach activists to communicate technical concepts in plain English.
"Plain Language." U.S. General Services Administration.
Plain language is strictly defined by U.S. government agencies, which are required to communicate in it for simplicity and quick, thorough comprehension of information.
"Explore Business Law." Study.com.
Extensive courses are offered to quickly uptake principles of business law such as antitrust law, contract law, financial legislation, copyright law, etc. Legal literacy is often the difference between unethical action of a business and its inaction. Legal literacy is also often the difference between consideration and investment in your policy idea and lack thereof.
"Business Communication." Study.com.
Now that you're able to communicate your prioritized information, you may also initiate writing with bells and whistles. While other activists care most about the information itself, business communication allows you to communicate your ideas and needs to those who you must convince worthiness of investment to and win over.
Logic.
Learn it through and through. Start with fallacies if you're better at language and work your way backwards to discrete mathematics; start with discrete mathematics if you're better at maths and work your way forwards to fallacies, critical literacy, and media literacy. State that which you intend to state. Recognize empiricism and rationalism for what they are. Congratulations: you are both a mathematician and a law student.
Economic Literacy for Armchair Activism
"Microeconomics." Khan Academy.
"Macroeconomics." Khan Academy.
The globe operates on profitability. Women's unpaid labor is a massive slice of the profitability pie. While it's possible to enact change without understanding all that drives the events around you, it's impossible to direct or meaningfully manipulate the events around you beyond your scope of comprehension.
Understand economics or be a sheep to every movement you're active in and to every storm that rolls your way.
#masterpost#armchair activism#remote activism#hybrid activism#cybersecurity#literacy#digital literacy#women in tech#radical feminist community#mine
71 notes
·
View notes
Text
One of the biggest hacks of the year may have started to unfold. Late on Friday, embattled events business Live Nation, which owns Ticketmaster, confirmed it suffered a data breach after criminal hackers claimed to be selling half a billion customer records online. Banking firm Santander also confirmed it had suffered a data breach impacting millions of customers and staff after its data was advertised by the same group of hackers.
While the specific circumstances of the breaches—including exactly what information was stolen and how it was accessed—remain unclear, the incidents may be linked to attacks against company accounts with cloud hosting provider Snowflake. The US-based cloud firm has thousands of customers, including Adobe, Canva, and Mastercard, which can store and analyze vast amounts of data in its systems.
Security experts say that as more details become clear about hackers' attempts to access and take data from Snowflake’s systems, it is possible that other companies will reveal they had data stolen. At present, though, the developing situation is messy and complicated.
“Snowflake recently observed and is investigating an increase in cyber threat activity targeting some of our customers’ accounts,” wrote Brad Jones, Snowflake’s chief information security officer in a blog post acknowledging the cybersecurity incident on Friday. Snowflake has found a “limited number” of customer accounts that have been targeted by hackers who obtained their login credentials to the company’s systems, Jones wrote. Snowflake also found one former staff member’s “demo” account that had been accessed.
However, Snowflake doesn’t “believe” it was the source of any leaked customer credentials, the post says. “We have no evidence suggesting this activity was caused by any vulnerability, misconfiguration, or breach of Snowflake’s product,” Jones wrote in the blog post.
While the number of Snowflake accounts accessed and what data may have been taken have not been released, government officials are warning about the impact of the attack. Australia’s Cyber Security Center issued a “high” alert on Saturday, saying it is “aware of successful compromises of several companies utilizing Snowflake environments” and companies using Snowflake should reset their account credentials, turn on multifactor authentication, and review user activity.
“It looks like Snowflake has had some rather egregiously bad security compromise,” security researcher Troy Hunt, who runs data breach notification website Have I Been Pwned, tells WIRED. “It being a provider to many other different parties, it has sort of bubbled up to different data breaches in different locations.”
Details of the data breaches started to emerge on May 27. A newly registered account on cybercrime forum Exploit posted an advertisement where they claimed to be selling 1.3 TB of Ticketmaster data, including more than 560 million people’s information. The hacker claimed to have names, addresses, email addresses, phone numbers, some credit card details, ticket sales, order details, and more. They asked for $500,000 for the database.
One day later, the established hacking group ShinyHunters—which first emerged in 2020 with a data-stealing rampage, before selling 70 million AT&T records in 2021—posted the exact same Ticketmaster ad on rival marketplace BreachForums. At the time, Ticketmaster and its parent company Live Nation had not confirmed any data theft and it was unclear if either post selling the data was legitimate.
On May 30, ShinyHunters also claimed to be selling 30 million customer details and staff information from Santander, putting a $2 million price tag on the information. Both posts on BreachForums have drawn attention to the illegal marketplace, which was recently revived by ShinyHunters after the FBI took the website down on May 15. The posts may, at least in part, be efforts to restore the disrupted forum’s damaged reputation with criminals.
The two hacks were linked to Snowflake’s systems by Israeli security firm Hudson Rock, which, in a now-removed blog post, posted conversations its researchers had with the alleged hacker who claimed to have accessed Snowflake’s systems and exfiltrated data. The hacker claimed they had tried to sell the data back to Snowflake for $20 million. (Hudson Rock did not respond to WIRED’s questions about why it has removed its research).
The Hudson Rock post claimed that a Snowflake employee may have been infected by an infostealer that collected the details the hacker needed to log in to its systems. Charles Carmakal, the chief technology officer at Google-owned security firm Mandiant, told BleepingComputer that its investigations, which have been taking place in recent weeks, indicate information-stealing malware may have been used to get Snowflake account credentials.
A Ticketmaster spokesperson told TechCrunch that its stolen database was hosted on Snowflake after the company acknowledged a data breach in a filing to the Securities and Exchange Commission on Friday evening. In the middle of May, before its data was advertised online, Santander first said it had seen unauthorized access to one of its databases “hosted by a third-party provider,” however it has refused to name the third party.
Snowflake’s CISO, Jones, acknowledged the security incident on Friday, saying that if a “threat actor obtains customer credentials, they may be able to access the account.” The company says it became aware of the suspicious activity on May 23 but has since found out it had been happening since mid-April. Jones’ post says Snowflake has notified all of its customers and “encouraged” them to review account settings and ensure they have implemented multi-factor authentication. In an additional security bulletin, Snowflake says it has seen “malicious traffic” from a client calling itself “rapeflake” and also connections from another client called “DBeaver_DBeaverUltimate.” A company spokesperson tells WIRED they have “nothing else to add” beyond the information included in company posts.
Cloud security company Mitiga says its investigations have seen a threat actor targeting organizations using Snowflake databases and using an attack tool called “rapeflake” in the process. Roei Sherman, field CTO at Mitiga, tells WIRED one possible scenario is that a threat actor managed to get information about Snowflake’s systems and then stole information about its clients, possibly using automated tools and brute-forcing their way into accounts.
Sherman says little is known about what data was stolen at the moment or the “rapeflake” tool, but that the attack could have wider ramifications going forward. There are already early signs other companies may be impacted.
Sherman says some of Mitiga’s customers have reached out to it for help, while Mandiant told BleepingComputer it had been assisting Snowflake customers in recent weeks. Cybersecurity researcher Kevin Beaumont shared online that he knows of six companies that have been impacted. And Australian events company Ticketek has also revealed customer names and email addresses stored in a “cloud-based platform, hosted by a reputable, global third-party supplier” have been accessed, although a spokesperson refused to confirm if this was related to Snowflake at all.
“We haven’t seen the entire blast radius yet,” Sherman says. “Snowflake has thousands of clients—they offer self-registration—and some of their clients are huge companies. We expect to learn about additional companies compromised.”
18 notes
·
View notes
Text
Defending Against Distributed Denial of Service (DDoS) Attacks: Mitigation Techniques and Strategies
DDoS attacks are a serious threat to organizations of all sizes, and their impact can be significant and costly. Read more...
Distributed Denial of Service (DDoS) is a type of cyber attack that aims to overload and overwhelm a website, network, or server with a massive amount of traffic. In a DDoS attack, the attacker typically uses a network of compromised computers (known as a botnet) to flood the target with traffic, rendering it inaccessible to legitimate users. DDoS attacks can be extremely disruptive and costly,…
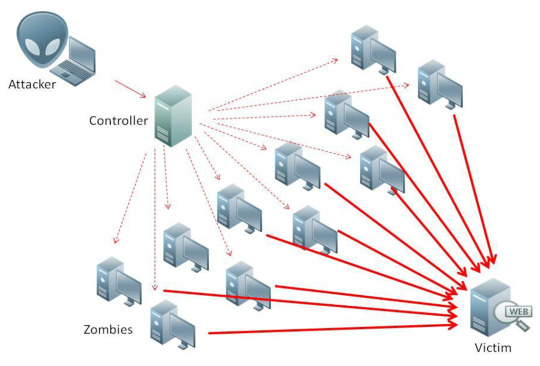
View On WordPress
#attack detection#black hole routing#cloud-based protection#cyber attacks#cyber security#DDoS attacks#load balancing#mitigation techniques#network security#Network segmentation#rate limiting#traffic filtering
6 notes
·
View notes
Text
Same Day Taj Mahal Tour by Car By Taj Mirror Company

Taj Mirror Company's Same Day Taj Mahal Tour by Car is an amazing opportunity to visit one of the world's most iconic monuments in a single day. Same Day Taj Mahal Tour by Car This tour is great for those who have limited time but want to see the Taj Mahal.
The excursion begins in the early morning with a comfortable pickup from your hotel or a predetermined place in Delhi. A skilled and courteous driver will accompany you in a well-maintained, air-conditioned vehicle, assuring a smooth and enjoyable travel to Agra, which is roughly 3-4 hours away.
When you arrive in Agra, you will be greeted by your professional tour guide, who will lead you on a fascinating tour of the Taj Mahal's history and architecture. This UNESCO World Heritage site, created by Emperor Shah Jahan in memory of his beloved wife Mumtaz Mahal, is a Mughal architectural masterpiece featuring magnificent white marble inlaid with precious stones.
After visiting the Taj Mahal, the group continues to the Agra Fort, another UNESCO World Heritage site. For years, the Mughal rulers' principal residence was this towering red sandstone fort. Your guide will explain the fort's history and strategic importance.
A delicious lunch at a respected local restaurant follows, where you may sample traditional Indian cuisine. The journey next continues to the Tomb of Itimad-ud-Daulah, sometimes known as the "Baby Taj," another stunning specimen of Mughal construction.
After a day full of historical treasures and cultural encounters, the tour closes with a relaxing journey back to Delhi. You will be dropped off at your hotel or another predetermined place, bringing an end to a great excursion.
Taj Mirror Company's Same Day Taj Mahal Tour by Car is a well-organized, hassle-free method to witness the timeless grandeur of the Taj Mahal and other Agra attractions. It provides an ideal combination of history, culture, and comfort, making it a must-see for any visitor to India.
ALSO READ-
CrowdStrike is a renowned cybersecurity firm that specializes in endpoint protection, threat intelligence, and cyberattack response services. CrowdStrike, founded in 2011 by George Kurtz, Dmitri Alperovitch, and Gregg Marston, has quickly established itself as a powerful force in the cybersecurity market. The corporation is based in Sunnyvale, California.
CrowdStrike's core product, the Falcon platform, uses AI and ML to detect and respond to threats in real time. The technology gives extensive visibility into endpoint activity, enabling enterprises to quickly detect and remediate any security breaches. Falcon's cloud-native architecture provides scalability and ease of deployment, making it a popular choice for businesses of all sizes.
CrowdStrike's role in detecting high-profile intrusions, such as the 2016 Democratic National Committee (DNC) hack, is one of its most notable accomplishments. The company's competence in threat intelligence and incident response has made it a reliable partner for both government agencies and private-sector businesses.
CrowdStrike's business strategy is subscription-based, with several service tiers to meet different corporate demands. This concept has been successful, as the company's revenue has grown rapidly and its customer base has expanded abroad. CrowdStrike went public in 2019, reinforcing its market position.
The company's commitment to innovation is demonstrated by continual updates to the Falcon platform and the incorporation of new technologies to battle increasing cyber threats. CrowdStrike's focus on proactive threat hunting, along with its comprehensive threat intelligence capabilities, enables enterprises to stay ahead of adversaries.
To summarize, CrowdStrike has evolved as a cybersecurity leader thanks to its cutting-edge technologies, strategic threat intelligence, and effective incident response. Its Falcon platform continues to set industry standards, equipping enterprises with the capabilities they need to defend against complex cyber threats.
2 notes
·
View notes
Text
Why enterprises are going hybrid and returning to colo! - CyberTalk
New Post has been published on https://thedigitalinsider.com/why-enterprises-are-going-hybrid-and-returning-to-colo-cybertalk/
Why enterprises are going hybrid and returning to colo! - CyberTalk


By Ervin Suarez, Security Engineer for Cable and Colocation Accounts, Check Point Software Technologies.
I’ve been closely observing a fascinating shift in the IT landscape and wanted to share some insights with all of you, especially given how these changes could impact our industry.
Lately, there’s been a noticeable shift among enterprises back towards colocation (colo) services, while they’ve simultaneously embraced hybrid cloud models. This trend is intriguing and speaks volumes about the evolving needs and strategies of businesses when it comes to managing IT infrastructure.
Why the shift, you might ask?
Cost efficiency: The reality is, while cloud services offer unmatched scalability, they can also escalate costs for specific workloads or data-intensive operations. Colocation offers a more predictable expense model, which is especially appealing for operations with stable demand.
Enhanced control and security: With colocation, businesses gain direct control over their physical servers, a non-negotiable for industries under tight regulatory scrutiny. This control translates into superior compliance and security, aligned with stringent industry standards.
Optimized performance: By strategically choosing colo sites, enterprises can drastically reduce latency for critical applications, ensuring high-performance outputs that cloud environments can sometimes struggle to match.
Flexibility and scalability: The hybrid model shines by offering the best of both worlds – colo for critical, stable workloads and cloud services for scalable, flexible needs. This balance is crucial for businesses that aim to maintain agility without compromising on reliability.
Robust business continuity: Distributing resources between colo and cloud environments enhances disaster recovery strategies, leveraging colo’s inherent infrastructure resilience and reliability.
Compliance with data sovereignty: In an era where data privacy reigns supreme, colocation facilities offer a strategic advantage by allowing businesses to physically host data within required jurisdictions, meeting stringent regulatory demands head-on.
What does this mean for us?
The resurgence in colocation interest, alongside a robust adoption of hybrid cloud strategies, indicates a balanced, pragmatic approach to digital infrastructure management. Businesses are seeking to optimize costs without sacrificing control, performance, or compliance.
We’re also seeing increasing collaborations between cloud and colo providers, simplifying the transition to hybrid models for enterprises. This partnership ecosystem paves the way for innovative solutions, making hybrid strategies more accessible and effective.
Innovations in networking and connectivity continue to blur the lines between colo and cloud, enabling more seamless management of distributed IT resources.
As we navigate these changes, it’s clear that flexibility, strategic planning, and an eye for optimization are key to leveraging the best of both colo and cloud worlds. The move towards hybrid infrastructures isn’t just a trend; it’s a strategic realignment of IT resources to better meet the demands of modern business operations.
This shift is supported by several trends and developments in the industry:
1. Resurgence of colocation: Colocation is becoming crucial again as companies become increasingly dependent on robust IT infrastructure to manage the growing volume of data. Traditional colocation provides reliable and secure options for IT infrastructure, which is critical given the rising importance of data privacy and security. Colocation solutions offer businesses a way to protect their data, ensure high availability, and achieve resilience while saving on capital expenditure and operational costs. This is because colocation allows businesses to leverage existing, well-maintained infrastructures which would otherwise require significant upfront investment (Datacenters).
2. Hybrid cloud flexibility: Hybrid cloud models are being recognized for their ability to provide agility and flexibility in the technology stack. This model allows enterprises to not only meet their current technological needs but also prepare for future demands. The hybrid cloud’s capacity to integrate edge computing with cloud architectures enables more businesses to adopt this technology. It effectively lowers latency, reduces bandwidth requirements, and enhances resiliency against network outages. This adoption is visible across various sectors, including telecommunications, retail, manufacturing, and energy, indicating a broad-based validation of the hybrid cloud’s value (The Enterprisers Project).
3. Multi-cloud and vendor-neutral environments: Enterprises are also moving towards a more vendor-neutral approach in their cloud and colocation strategies. This shift is partly due to the need to avoid vendor lock-in, which can limit flexibility and control. The hybrid and multi-cloud architectures, comprised of combinations of public clouds, private clouds, and colocation data centers, allow enterprises to tailor their IT infrastructure to meet specific needs while ensuring that they can manage and integrate various cloud services effectively (PacketFabric).
In summary, the trends towards colocation and hybrid cloud are driven by a need for cost efficiency, control, security, flexibility, and strategic deployment of IT resources. These models not only help with optimizing current operations, but also assist with scaling future technologies and infrastructure needs. Enterprises are increasingly aware of these benefits and are adjusting their IT strategies to leverage colocation and hybrid cloud solutions as part of their broader digital transformation initiatives.
I’m keen to hear your thoughts and experiences on this shift. How do you see the hybrid model shaping the future of IT infrastructure in your field?
Managed firewall as a service – How secure is your data center?
As we navigate through the evolving landscape of IT infrastructure, with a noticeable shift towards colocation services and hybrid cloud models, I’m thrilled to share a bit about how Check Point Software is leading the way in enhancing security within these environments.
We’ve recently launched an innovative offering, Firewall as a Service (FWaaS), specifically designed to bolster the security posture of businesses leveraging colocation facilities.
Why Check Point’s FWaaS?
In the world of colocation, where businesses seek the perfect balance between control, cost, and flexibility, Check Point’s Managed Firewall as a Service stands out as a beacon of security excellence.
We understand the complexities of managing IT infrastructure across colo and cloud environments. That’s why we’ve introduced a solution that simplifies data center workflow orchestration and scales security on-demand, akin to spinning up servers in the cloud.
Our Managed FWaaS is not just a product, but a comprehensive security ecosystem. It’s designed to integrate seamlessly with your existing security infrastructure, protecting both private and public network services from a plethora of threats that can undermine your business.
With a 98.8% catch rate, our service ensures unparalleled protection against cyber security threats, providing peace of mind in an era where security breaches are all too common.
What sets Check Point apart?
Ease of integration: Customers within a colocation facility can effortlessly connect to Check Point’s infrastructure, gaining access to a managed security cluster that’s fully maintained by our team of experts.
Comprehensive security: Our service covers all bases, from Firewall, VPN, IPS, application control, content awareness, URL filtering, anti-bot, anti-virus, anti-spam, threat emulation, to threat extraction. We manage and monitor everything, alerting you to high and critical events, ensuring your infrastructure remains secure against evolving threats.
Fully managed solution: Let our MSS experts take the wheel. We handle everything from initial setup, weekly operational changes, to yearly upgrades, allowing you to focus on core business functions without the hassle of managing security infrastructure.
Cyber insurance partnership: Recognizing the importance of comprehensive protection, we’ve partnered with Cysurance to offer cyber insurance, providing an extra layer of security and assurance for businesses in need.
Empower your security with Check Point’s FWaaS
Check Point’s Managed Firewall as a Service leverages our deep expertise to maintain your security assets, ensuring your business operates smoothly and securely, without the operational overhead. This allows organizations to scale up their security measures on-demand, mirroring the flexibility of public clouds but with the added benefit of Check Point’s industry-leading threat prevention and management.
In an era where businesses are increasingly leveraging colocation for its cost efficiency, flexibility, and enhanced control, Check Point provides a security solution that aligns perfectly with these needs. Our FWaaS offering ensures that businesses can enjoy the benefits of colocation and hybrid cloud models, with the confidence that their security is in the hands of the experts.
I’m excited about the possibilities this brings to our industry and am eager to discuss how we can support your business’s security needs in this changing landscape. Let’s embrace this shift together, with Check Point ensuring that our journey is secure.
#Accounts#applications#approach#as a service#assets#awareness#bases#Best Of#blur#bot#Business#business continuity#Check Point#Check Point Software#Cloud#cloud services#cloud solutions#clouds#cluster#Colocation#Companies#compliance#comprehensive#computing#connectivity#content#cyber#cyber insurance#cyber security#cybersecurity
0 notes
Note
I used to love Jared very very much, i had a Sam fanart blog, i defended him so hard, because i have always believed he is a good guy. Then that thing with the tattoo happened, and i'm not going to lie, it hurt. The thought that maybe he looks down at people like me was too much.
Do you understand my predicament? Jared did something that made me think he might be racist, but i can't and won't asume that he is, because i don't know him. But the damage is done, and I just can't look at him the same anymore.
And who did that damage, who ruined my fandom experience? Not Jared, but the assholes who blew up the internet talking shit about him.
I can't love him like before, because if he turns out to be a racist, my heart would be crushed.
So the best course of accion was to distance myself from that parasocial relationship.
Point is, that's the thing with celebrities, sometimes we give them too much power over our hearts, and they don't even know that we exist!
We should just look at them as regular people.
You are hating on Jared due to an assumption without doing due research. The symbol he tattoed is a texan symbol, you can find deeper research on it on this blog, just look through the tags or use keywords and find out where the symbol orginated and what it actually means. It's also used on license plates or something similar (sorry, can't remember but I'm sure someone will mention in the comments) in Texas, so does that make all those people racist too?
As for racism, you have so many cases that evidence the very contrary, Jared is warm, welcoming and supportive, he is inclusive and you see thay even with his spin off, just look at the amazing cast he's put together. So what exactly is your assumption based on?
I do get being afraid of being dissapointed, that's human but it's also important to not let other people's conclusion cloud your own moral compass, intuition and perceptions and to be careful when it comes to perception biases. Jared doesn't deserve to be labeled as a racist, he's done nothing to earn such a label and he never will. He's never harmed, targetted or devalued anyone of a different race so please consider all the secure truths you do know about him before embracing such a dark lie. You have personal account from people, from different backgrounds, religions and ethnicities that have met him, experienced him and have shared incredibly special things about how he has impacted them. That's real proof of his impact.
At the end of the day, what a person tattoos on their body is an intimate choice, we shouldn't get to judge and nothing Jared has ever said or done supports the theory that he has the inclinations you mentioned in your post. Rather, he most likely wanted a symbol of Texas and picked that one without looking too deeply into it. Either way, he doesn't owe anyone explanations about what he tattooes on his own body, which is solely his property, and he is harming absolutely no one. He simply made an uninspired choice and vilifying him for it is going way too far. Also, the same people that are calling him a racist send death threats on the daily, engage in cyber bullying, stalking and other similar behaviors what does that make them? Not to mention the biases they have towards people from different backgrounds or countries...
That being said, I think you are very wise to distance yourself if you no longer feel comfortable about something. Follow your inner compass, just please don't vilify people without truly doing deep research on them.
54 notes
·
View notes
Text
Different Kinds of Office Phone Systems for Small Businesses Explained
Businesses rely heavily on communication, and for this communication, business phone systems are the best solution. Different business phone systems for small offices are available in the markets, and it is essential that before the selection process, a company owner goes through all of them to determine the best one based on the needs eventually.

Types Of Business Phone Systems Explained
Experts say that comparing these office phone systems begins with understanding the three principles, namely - KSU, PBX and VoIP.
Ksus
KSUs stand for key service units that are uncomplicated multi-line on-premise office phone systems used by smaller and medium size organisations. They have been a very reliable solution for decades now, and it is easy for any business to use them based on their needs.
Pbxs
The term PBX denotes private branch exchange, and they are telephone systems with a PBX server residing in the office. It can incorporate digital and Internet protocol phones as well, which allows users to talk to each other inside the private telephone network.

Voip
These are cloud-based private branch exchanges that deliver communication over the Internet using VoIP or Voice Over Internet Protocol technology. The cloud PBX provider is known by the name of PBX host, and he has a server or software that helps them offer services to different businesses from under one roof.
Advantages of On-Premise Phone Systems
The first benefit of on-premise phone systems for small businesses is that they are inexpensive and can be acquired within a budget.
Then they are also very durable and long lasting, and without any need for backup, they can run for years and years.

It is also very easy to identify with them what line is used.
They come with the ability to connect phones to actual phone outlets through existing phone wiring.
Advantages of Hosted Voip or a Cloud-Based Pbx
This is an advanced multi-channel technology that remains unchallenged
It is straightforward to use at home and even in remote locations.
It is an ideal tool for collaboration and customer management.
This technology runs office phone systems at much lower initial costs.
#Telephone systems for small business#small office phone system#phone systems for small office#small office phone systems#voip phone system#phone systems#telephone systems#business phone systems Australia#digital signage solutions#On-Premise Phone Systems#cloud-based private branch exchanges#PBX phone#voip phone handset#video conferencing solutions#online collaboration tools#jabra pro 920#phone headsets#cyber security software#video conferencing#video conference system#Starleaf Video Conferencing#jabra evolve 75
1 note
·
View note
Text
ERP Trends 2024: What Engineering and Manufacturing Industries Need to Know
As we navigate through 2024, the landscape of Enterprise Resource Planning (ERP) systems continues to evolve, presenting both opportunities and challenges for engineering and manufacturing industries. Companies in this sector, especially those in key industrial regions like Maharashtra, Mumbai, Pune, and Gujarat, must stay abreast of the latest ERP trends to maintain competitive advantage and operational efficiency. In this blog, we’ll delve into the significant ERP trends of 2024 and their implications for the engineering and manufacturing sectors.

1. Increased Adoption of Cloud-Based ERP Solutions
One of the most significant trends in ERP software for engineering companies in Maharashtra and across India is the shift towards cloud-based solutions. Cloud ERP offers several advantages over traditional on-premise systems, including lower upfront costs, greater scalability, and enhanced accessibility.
Benefits of Cloud-Based ERP:
Cost Efficiency: Eliminates the need for expensive hardware and reduces IT maintenance costs.
Scalability: Easily adjusts to the growing needs of a manufacturing company in Gujarat or an engineering firm in Mumbai.
Accessibility: Provides access to real-time data from anywhere, facilitating better decision-making.
Leading ERP software companies in Pune are increasingly offering cloud-based solutions tailored to the needs of local engineering and manufacturing businesses. These solutions support remote work and ensure business continuity in an increasingly digital world.
2. Integration of AI and Machine Learning
Artificial Intelligence (AI) and Machine Learning (ML) are revolutionizing ERP systems by providing intelligent insights and automating routine tasks. For ERP software for engineering companies in Mumbai, integrating AI can enhance predictive maintenance, optimize supply chain management, and improve production planning.
AI and ML Applications in ERP:
Predictive Analytics: Helps foresee equipment failures and reduce downtime.
Supply Chain Optimization: Enhances demand forecasting and inventory management.
Process Automation: Automates repetitive tasks, freeing up human resources for more strategic roles.
ERP solution providers in Pune are at the forefront of integrating AI and ML into their systems, enabling companies to leverage advanced analytics and improve overall operational efficiency.
3. Emphasis on Cybersecurity
With the increasing digitization of manufacturing processes, cybersecurity has become a critical concern. ERP systems, being the backbone of business operations, are prime targets for cyber-attacks. Engineering and manufacturing companies in regions like Gujarat and Maharashtra need robust cybersecurity measures to protect their sensitive data.
Key Cybersecurity Features:
Data Encryption: Protects data during transmission and storage.
Multi-Factor Authentication: Enhances user authentication processes.
Regular Security Audits: Ensures continuous monitoring and improvement of security protocols.
ERP software for engineering companies in Maharashtra must incorporate these advanced security features to safeguard against data breaches and cyber threats.
4. Enhanced User Experience (UX)
User experience has become a critical factor in ERP adoption and utilization. Modern ERP systems are focusing on intuitive interfaces and user-friendly designs to ensure that all employees, regardless of their technical expertise, can effectively use the system.
UX Improvements:
Intuitive Dashboards: Provide real-time insights and easy navigation.
Mobile Accessibility: Ensures that users can access ERP data on-the-go.
Customization Options: Allow users to tailor the system to their specific needs.
ERP software companies in Pune are prioritizing user experience in their solutions, making it easier for engineering and manufacturing firms to train their staff and increase productivity.
5. Internet of Things (IoT) Integration
The integration of IoT with ERP systems is another trend transforming the manufacturing industry. IoT devices collect vast amounts of data from production lines, equipment, and other operational areas, which can be analyzed by the ERP system to optimize performance.
IoT Benefits in ERP:
Real-Time Monitoring: Provides immediate insights into production processes.
Predictive Maintenance: Schedules maintenance activities based on equipment condition rather than time intervals.
Enhanced Quality Control: Monitors product quality throughout the manufacturing process.
For ERP for manufacturing companies in Gujarat, IoT integration offers a significant advantage by improving efficiency and reducing operational costs.
6. Sustainability and Green Manufacturing
Sustainability is becoming a critical focus for manufacturing companies worldwide. ERP systems are evolving to support green manufacturing practices by tracking and optimizing resource usage, reducing waste, and ensuring compliance with environmental regulations.
Sustainable ERP Features:
Resource Management: Tracks energy and material usage to minimize waste.
Regulatory Compliance: Ensures adherence to environmental laws and standards.
Sustainability Reporting: Provides detailed reports on sustainability metrics.
Engineering and manufacturing companies in regions like Mumbai and Maharashtra can benefit from ERP solutions that incorporate sustainability features, helping them achieve their environmental goals and enhance their corporate reputation.
7. Modular and Flexible ERP Solutions
In response to the diverse needs of engineering and manufacturing firms, ERP solution providers in Pune are developing more modular and flexible ERP systems. These systems allow companies to select and implement only the modules they need, which can be easily scaled and customized as their business grows.
Advantages of Modular ERP:
Cost-Effective: Pay only for the features you need.
Scalability: Easily add new modules as your business requirements evolve.
Customization: Tailor the system to fit specific operational needs.
This trend is particularly beneficial for small to medium-sized enterprises (SMEs) in the engineering and manufacturing sectors, enabling them to adopt ERP systems without the burden of high costs or complexity.
8. Focus on Customer-Centric Manufacturing
ERP systems are increasingly supporting customer-centric manufacturing practices, where production processes are aligned with customer needs and preferences. This approach enhances customer satisfaction and drives business growth.
Customer-Centric ERP Features:
Custom Order Management: Handles unique customer requirements and specifications.
Enhanced CRM Integration: Integrates with customer relationship management (CRM) systems for a holistic view of customer interactions.
Real-Time Order Tracking: Provides customers with real-time updates on their orders.
Manufacturing companies in Gujarat and engineering firms in Maharashtra are leveraging these customer-centric ERP features to improve their service levels and build stronger customer relationships.
9. Advanced Analytics and Business Intelligence (BI)
Advanced analytics and BI are becoming integral components of modern ERP systems. These tools provide deep insights into business operations, helping companies make data-driven decisions and improve performance.
Key BI Features:
Data Visualization: Converts complex data into easy-to-understand charts and graphs.
Dashboards: Offer a real-time overview of key performance indicators (KPIs).
Predictive Analytics: Forecasts future trends based on historical data.
ERP software companies in Pune are incorporating advanced analytics and BI capabilities into their systems, empowering engineering and manufacturing firms to gain a competitive edge through better insights and informed decision-making.
10. Globalization and Localization Support
As engineering and manufacturing companies expand their operations globally, ERP systems must support multiple languages, currencies, and regulatory requirements. Globalization and localization features are essential for companies operating in diverse markets.
Globalization Features:
Multi-Language Support: Accommodates users from different regions.
Multi-Currency Handling: Manages transactions in various currencies.
Compliance with Local Regulations: Ensures adherence to regional laws and standards.
ERP solution providers in Pune and other industrial hubs are enhancing their systems to support global operations, enabling companies to seamlessly manage their international business processes.
Conclusion
The ERP landscape for engineering and manufacturing industries is rapidly evolving, driven by advancements in technology and changing business needs. Companies in Maharashtra, Mumbai, Pune, and Gujarat must stay informed about these trends to leverage the full potential of ERP systems. By adopting cloud-based solutions, integrating AI and IoT, prioritizing cybersecurity, and focusing on sustainability, businesses can achieve greater efficiency, competitiveness, and growth in 2024 and beyond.
For engineering and manufacturing firms looking for the best ERP software for engineering companies in Maharashtra or ERP for manufacturing companies in Gujarat, it is crucial to partner with leading ERP solution providers in Pune who understand the unique challenges and opportunities in this sector. Embracing these trends will not only enhance operational efficiency but also drive innovation and sustainability in the engineering and manufacturing industries.
By staying ahead of these ERP trends, companies can position themselves for success in an increasingly digital and interconnected world. Whether you are an engineering firm in Mumbai or a manufacturing company in Gujarat, the right ERP system can transform your operations and pave the way for a prosperous future.
#ERP software in Vadodara#Manufacturing ERP software in Gujarat#ERP software companies in Vadodara#ERP software providers in Vadodara#ERP for manufacturing company in Gujarat#ERP software#ERP system#cloud ERP#ERP solutions#software development#engineering ERP#management software#engineering services#engineering industry
4 notes
·
View notes