#cloud security solutions
Explore tagged Tumblr posts
Text
Gomboc: Remaking Infrastructure as Code Security through Intelligent Cloud Solutions
As increasingly more businesses rely on cloud-native technology, we have transformed how we think about infrastructure completely. Gone is the traditional manual config, replaced instead by Infrastructure as Code (IaC) — a cycle that allows groups to provision and control IT infrastructure from machine-readable definition files. Though this evolution has brought unprecedented speed and scaling, it's also created fresh security challenges. That is why companies today need to have good infrastructure as code security to allow their cloud environments not just be effective, but also secure.
Here comes Gomboc, the next-gen cloud security solution by design, made specifically for the era of automation.

The Security Challenges of IaC
IaC speeds up deployments and keeps stable environments in development, staging, and production. But when it's misconfigured or not monitored, IaC opens its systems to devastating vulnerabilities. One incorrect Terraform script or Kubernetes configuration can open ports, grant too much access control, or expose secret leaks — compromising your whole cloud infrastructure.
With traditional security tools falling short of being capable of finding code-level misconfigurations, DevSecOps teams today need smarter, more proactive ones. That is where Gomboc is.
Gomboc: Proactive Cloud Security for Modern DevOps
Gomboc is an intelligent cloud security platform designed to empower organizations to safeguard their cloud infrastructure on the code level — before threats hit production. By incorporating security into development, Gomboc enables DevOps teams to "shift left" and identify issues early, wasting time, cost, and risk.
Main Features of Gomboc's IaC Security
Automated Code Scanning: Gomboc scans your Terraform, CloudFormation, or Kubernetes files to spot configuration issues and possible security loopholes.
Real-Time Feedback in CI/CD: Gomboc seamlessly plugs into your CI/CD workflow, giving real-time feedback with notifications and remediations without interrupting your rhythm.
Contextual Remediation: Rather than highlighting issues, Gomboc delivers actionable, code-level remediations tailored to your cloud setup.
Compliance by Design: Maintain your configurations in compliance with industry standards like CIS Benchmarks, SOC 2, and HIPAA from the development phase.
Multi-Cloud Support: With AWS, Azure, or GCP, Gomboc allows you to keep your stack up to date with cross-platform visibility and security.
Why Gomboc Delivers Cloud Security
Most cloud security tools react after infrastructure has been provisioned. Gomboc turns that model on its head by baking security into design, halting misconfigurations from getting to runtime.
This "security as code" mindset allows development teams to move fast, stay compliant, and greatly reduce their attack surface — frictionless, headache-free, no legacy pain. It fosters a security-first culture, which holds engineers responsible for secure deployments day one.
cloud security solutionscloud security solutions
As cloud infrastructure becomes more sophisticated, so should the way we secure it. With Gomboc's infrastructure as code security, businesses no longer need to compromise on speed or security. You can have both — and grow with confidence.
Whether high-growth startup embracing DevOps or enterprise cloud-migrating, Gomboc's smart cloud security technologies will enable you to protect your code, your cloud, and your future.
Visit Gomboc.ai to find out more, ask for a demo, or start your free trial today.
0 notes
Text
What is Cloud Security: Essential Ideas and Best Procedures?
In the modern digital era, businesses are increasingly transitioning their operations to the cloud, making security a critical focus. But what exactly is cloud security, and why is it so important?
Cloud security encompasses a range of strategies, technologies, and policies aimed at safeguarding data, applications, and services hosted in cloud environments.
As cyber threats grow more advanced, effective cloud security measures play a vital role in protecting sensitive information from unauthorized access, data breaches, and other potential risks.

0 notes
Text
Pankit Desai, Co-Founder and CEO, Sequretek – Interview Series
New Post has been published on https://thedigitalinsider.com/pankit-desai-co-founder-and-ceo-sequretek-interview-series/
Pankit Desai, Co-Founder and CEO, Sequretek – Interview Series
Pankit Desai is the co-founder and CEO of Sequretek, a company specializing in cybersecurity and cloud security products and services. In 2013, he co-founded Sequretek with Anand Naik and has played a key role in developing the company into a prominent provider of cybersecurity and cloud security solutions. Prior to Sequretek, Pankit held various leadership and management positions in the IT industry at companies including NTT Data, Intelligroup, and Wipro Technologies. He holds a degree in computer engineering and brings a strong background in technology and entrepreneurship to his role.
Sequretek’s cybersecurity expertise, strengthened by cloud-based solutions with real-time, AI-driven threat detection and response, enables businesses to confidently take control, grow, and safeguard their digital assets while maintaining regulatory compliance.
What inspired you to co-found Sequretek, and how has the company evolved since its inception?
The cybersecurity landscape has long been marked by disparity, where the top 10% of companies have access to comprehensive, cutting-edge solutions, while the rest struggle with limited resources and expertise. This industry, which often caters to the elite, leaves many organizations navigating a maze of 90+ technology categories and thousands of vendors, resulting in fragmented approaches that complicate security decisions. At Sequretek, we saw this as an opportunity to change the narrative. When we founded the company in 2013, our mission was clear, to make cybersecurity simple and accessible for all, not just the few who could afford it.
Our approach has always been about consolidation and simplification. Instead of adding to the complexity with more niche solutions, we set out to build an integrated platform that addresses the key pillars of cybersecurity—endpoint security, identity governance, and threat detection—under one roof. We envisioned a world where businesses could focus on growth without the fear of cyber threats disrupting their journey. By combining AI-driven automation with a holistic strategy, we’ve empowered our clients to stay secure in the face of evolving risks, making cybersecurity a growth enabler rather than a roadblock.
What were the initial challenges you faced when starting Sequretek, and how did these shape the company’s strategy in cybersecurity?
Starting Sequretek in 2013, we encountered several challenges that significantly influenced our approach to cybersecurity. The most pressing issue was the steep fragmentation of the industry—there were too many niche solutions addressing specific security problems without an integrated approach. It was clear that if we wanted to make a meaningful impact, we needed to consolidate security capabilities and deliver a unified solution that was easy to implement and manage. This insight drove us to develop our integrated Percept platform, which covers endpoint security, identity governance, and threat detection in one place.
Another challenge was the prevailing perception that cybersecurity was a luxury reserved for large enterprises with substantial budgets. This mindset left a significant portion of the market underserved, exposing smaller companies to considerable risks. As a result, our strategy has always been focused on simplifying security by automating routine tasks, reducing the need for specialized security teams, and lowering the cost of ownership.
Could you tell us about the core philosophy behind Sequretek’s product suite and how it aligns with your original vision?
The core philosophy behind Sequretek’s product suite is rooted in the belief that cybersecurity should not be a luxury, but a fundamental right for all businesses, regardless of their size. From the outset, our vision has been to simplify security by consolidating complex technologies into a single, cohesive platform. We observed how companies were struggling with a fragmented security landscape, where they needed multiple tools to manage different aspects of cybersecurity. This created inefficiencies and increased the risk of vulnerabilities going undetected.
This philosophy is reflected in our Percept platform, which was designed to eliminate silos and provide a unified view of an organization’s security posture. By leveraging AI and automation, Percept streamlines security operations, allowing companies to detect and respond to threats with greater speed and accuracy. Our focus on automation not only reduces the burden on security teams but also lowers the cost of ownership, making enterprise-grade security accessible to businesses that may not have large IT budgets.
What distinguishes Sequretek from other players in the AI-driven cybersecurity field?
Sequretek stands out by simplifying cybersecurity through an integrated approach. While many competitors offer isolated solutions, we consolidated endpoint security, identity governance, and threat detection into our unified Percept platform. This reduces the complexity that overwhelms many organizations using multiple tools.
Our use of AI goes beyond just detecting threats—it automates responses to free up security teams and even includes natural language processing to make interacting with security data user-friendly.
How has AI revolutionized threat prediction and response at Sequretek, and what specific benefits does it offer your clients?
AI has been a game-changer for Sequretek in revolutionizing threat prediction and response. At its core, our AI-driven platform, Percept, doesn’t just spot threats—it anticipates them. By continuously analyzing vast data streams, our algorithms identify potential risks early on, allowing businesses to react before a situation escalates. This proactive stance significantly cuts down on response times, ensuring threats are addressed in seconds.
The benefits for our clients are clear- fewer distractions from false alarms, less manual work for security teams, and more time to focus on strategic priorities. For instance, when Percept detects a phishing attempt, it can immediately isolate the threat, notify the team, and even initiate a response, all without human intervention. This automation isn’t just about speed; it’s about making security accessible for companies that can’t afford large, specialized teams. We’re essentially leveling the playing field, empowering businesses to stay resilient in an ever-evolving threat landscape.
What are some of the most critical AI advancements in Sequretek’s Percept platform for managing evolving cyber threats?
The Percept platform’s AI advancements are geared toward staying ahead of the rapidly evolving cyber threat landscape. One of the standout features is its ability to use predictive analytics for threat anticipation. This shift from reactive to proactive threat management is crucial in today’s cybersecurity environment. Another critical advancement is in automation. Percept automates the detection and also response processes, such as isolating compromised devices or blocking suspicious network traffic in real time. This automation dramatically reduces response times, allowing businesses to mitigate threats instantly while reducing the burden on security teams. Moreover, with integrated natural language processing (NLP), users can interact with the platform conversationally, simplifying complex tasks like querying threat intelligence data.
These advancements transform cybersecurity from a traditionally resource-intensive activity into a more streamlined and accessible process, allowing companies of all sizes to benefit from cutting-edge defenses without needing extensive security teams.
Can you share an example of how Sequretek uses AI to streamline threat detection and automate responses?
At Sequretek, AI is at the heart of streamlining threat detection and automating responses. For instance, Percept XDR and NG SIEM provide AI-powered extended detection and response combined with next-generation security information and event management. This setup detects threats and takes automated actions, such as isolating compromised systems and notifying security teams in real time, reducing manual intervention and speeding up containment.
Similarly, Percept EDR leverages on-agent AI for real-time endpoint detection and response. When it detects a next-gen threat, like ransomware, it can immediately isolate the affected device, preventing lateral movement across the network while ensuring business operations continue uninterrupted.
Additionally, Percept Compliance Manager brings AI to governance, risk, and compliance by conducting real-time vulnerability scans and configuration audits within a single console, helping organizations maintain a strong security posture without extensive manual oversight.
How is AI changing the tactics of cybercriminals, and what innovations is Sequretek using to counteract these new AI-driven threats?
AI is reshaping the landscape of cybercrime, enabling attackers to launch more sophisticated and convincing campaigns. Cybercriminals are using AI to enhance phishing and social engineering tactics, creating highly personalized and realistic fake messages, voice, or video content to deceive individuals and organizations. The scale and speed at which these AI-driven attacks can be executed have made them a significant concern in today’s threat environment.
At Sequretek, we counteract these AI-driven threats with our own AI innovations integrated into the Percept platform. We employ advanced machine learning techniques to detect anomalies that indicate potential AI-generated attacks, such as deepfakes or sophisticated phishing attempts. Our platform uses behavioral analysis to identify unusual patterns in user activity, helping to catch threats that traditional rule-based systems might miss. The goal is to stay one step ahead in this AI arms race, using AI to outsmart cybercriminals by making our defenses smarter, faster, and more adaptive.
How do you see AI’s role in cybersecurity evolving over the next five years, and what does this mean for businesses?
As AI becomes more mature, we see its potential to fundamentally reshape cybersecurity. One major advancement will be how effectively AI systems can differentiate real threats from false positives. Today, cybersecurity teams often face an overwhelming volume of alerts, many of which are not genuine risks. With smarter AI, we’ll be able to identify true threats with much greater accuracy, which will allow teams to focus their efforts where it truly matters, rather than getting caught up in unnecessary noise. Additionally, AI will help reduce the grey areas we encounter—those ambiguous situations that aren’t harmful or safe—by making distinctions clearer and cutting down on manual oversight.
Incident response will also see transformative gains. Currently, even when threats are detected in real time, the response can still be time-consuming due to manual processes. AI-enabled automation will allow for much faster, more seamless responses, reducing reliance on human intervention and significantly speeding up the process. Finally, we’re also looking forward to advancements in natural language processing, which will simplify how teams interact with complex security data, making it accessible without specialized queries or technical hurdles. This combination of capabilities will be essential as cyber threats evolve, enabling businesses to stay resilient in a rapidly shifting landscape.
What advice would you give organizations looking to enhance their cybersecurity posture with AI today?
Organizations looking to strengthen their cybersecurity with AI should remember that AI is a powerful enabler, not a complete solution. It’s essential to approach AI as part of an integrated security framework built on the fundamentals—people, processes, and technology. Just because AI offers new capabilities doesn’t mean you should replace established strategies or think it’s a silver bullet. Instead, think of AI as a tool to enhance your team’s capabilities, not replace them. For example, AI can play a valuable role in understanding user behavior and enhancing security awareness through gamified learning, which can help reduce human vulnerabilities to attacks.
Another critical area is identifying where AI can address inefficiencies in your current tools and processes. AI and machine learning can help you respond faster and with greater precision, particularly in areas traditionally slowed down by human dependency. However, it’s important to remember that no AI tool alone will ensure complete security. It should work alongside strong, well-trained teams and established protocols to build a resilient security posture that adapts to new threats.
Thank you for the great interview, readers who wish to learn more should visit Sequretek.
#Advice#agent#ai#AI systems#AI-powered#alerts#Algorithms#Analysis#Analytics#anomalies#approach#assets#attackers#automation#awareness#background#Behavior#behavioral analysis#budgets#Business#CEO#challenge#change#Cloud#Cloud Security#cloud security solutions#Companies#complexity#compliance#comprehensive
0 notes
Text
How to Choose the Right Antivirus Software: A Comprehensive Guide
In today’s digital age, where our lives are intricately intertwined with technology, safeguarding our digital assets has become paramount. With the proliferation of cyber threats, antivirus software stands as a crucial line of defense against malware, viruses, ransomware, and other malicious entities lurking online. However, the abundance of antivirus options can be overwhelming, making it…

View On WordPress
#A#Advanced Behavioral Analysis Software#Advanced Threat Detection#Antivirus#Antivirus Software#Automated Security Incident Response#Cloud Security Solutions#Cloud-Based Endpoint Security Platform#Comprehensive Data Protection Suite#Continuous Vulnerability Assessment#Cyber Defense#Cybersecurity#Cybersecurity Awareness Training#Data Encryption Software#Data Protection#Defense#Encryption#Endpoint Protection Suite#Endpoint Security#Firewall#Firewall Protection#Identity Theft#Identity Theft Prevention#Integrated Firewall Protection Mechanism#Internet Security Software#Malware#Malware Detection#Malware Removal Tool#Mobile Device Management#Multi-Layered Malware Defense System
0 notes
Text

Cloud computing has one of the fastest adoption rates globally. Most organizations are using the power of cloud computing to access and manage data efficiently as well as for scalability. Currently, the global market size of cloud computing is $679 billion in 2024, and it is expected to surpass $1 trillion by 2027. It clearly shows how fast the world is adapting to cloud computing technology. And that increases the chances of cyber attacks and data breaches as well. It is a big concern that every organization is focusing on resolving by improving cloud computing security.
#cloud computing#cloud security#cloud computing security#cloud security solutions#software development security#cloud computing technologies
0 notes
Text
Cloud Hosting in India offers unmatched reliability, scalability, and performance, making it the go-to choice for businesses of all sizes. At Website Buddy, we provide cutting-edge cloud hosting solutions designed to deliver blazing-fast speeds, robust security, and seamless uptime. Whether you're launching a startup or managing a growing enterprise, our cost-effective plans cater to your needs. Enjoy easy scalability, 24/7 customer support, and advanced features that keep your website running smoothly. Trust Website Buddy for affordable and efficient cloud hosting in India to take your online presence to the next level!
#Cloud Hosting in India#Affordable Cloud Hosting#Best Cloud Hosting Services#Scalable Cloud Hosting India#Reliable Web Hosting Solutions#Website Buddy Hosting#Cheap Cloud Hosting India#Fast and Secure Hosting
3 notes
·
View notes
Text
Simplify Transactions and Boost Efficiency with Our Cash Collection Application
Manual cash collection can lead to inefficiencies and increased risks for businesses. Our cash collection application provides a streamlined solution, tailored to support all business sizes in managing cash effortlessly. Key features include automated invoicing, multi-channel payment options, and comprehensive analytics, all of which simplify the payment process and enhance transparency. The application is designed with a focus on usability and security, ensuring that every transaction is traceable and error-free. With real-time insights and customizable settings, you can adapt the application to align with your business needs. Its robust reporting functions give you a bird’s eye view of financial performance, helping you make data-driven decisions. Move beyond traditional, error-prone cash handling methods and step into the future with a digital approach. With our cash collection application, optimize cash flow and enjoy better financial control at every level of your organization.
#seo agency#seo company#seo marketing#digital marketing#seo services#azure cloud services#amazon web services#ai powered application#android app development#augmented reality solutions#augmented reality in education#augmented reality (ar)#augmented reality agency#augmented reality development services#cash collection application#cloud security services#iot applications#iot#iotsolutions#iot development services#iot platform#digitaltransformation#innovation#techinnovation#iot app development services#large language model services#artificial intelligence#llm#generative ai#ai
4 notes
·
View notes
Text

TekReach Solutions is an authorized provider of Digital Solutions, based in the vibrant business hub of Dubai, UAE. With a focus on Creativity and Innovation, we provide a broad range of Digital Marketing Services and IT Solutions. We are committed to supporting businesses in navigating the evolving digital landscape and achieving their objectives through leveraging innovating and practical solutions.
#branding services#cloud storage#cyber security services#digital marketing#e commerce development#e commerce services#e commerce solutions#branding#cyber security solutions#cyber security#digital marketing services#seo services#digital marketing company#ppc services#search engine marketing#social media marketing#website development#website development services#software development#mobile application development
2 notes
·
View notes
Text
Why Your Business Needs a Cloud Video Platform Today
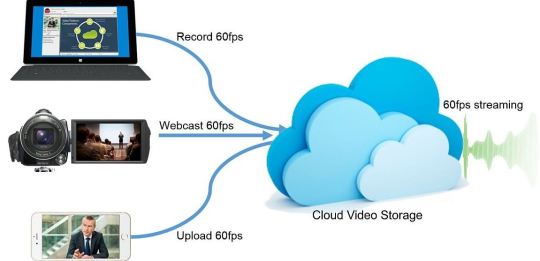
In the digital era, businesses are constantly looking for ways to enhance efficiency, reduce costs, and improve communication and collaboration. One of the technological advances that has been pivotal in achieving these objectives is the cloud video platform. This platform has revolutionized how businesses operate, offering a multitude of benefits ranging from improved communication strategies to expansive data analytics. Additionally, the cloud video platform provides scalable solutions that adapt to the needs of growing businesses, ensuring that they can maintain seamless operations. By facilitating remote work and virtual meetings, these platforms also contribute to better team collaboration and more efficient project management.
Key Benefits of Using Cloud Video Platform
A cloud video platform offers significant advantages to businesses, paramount among them being scalability, accessibility, enhanced collaboration, cost-effectiveness, and security. Understanding these benefits in detail can help organizations make informed decisions about adopting this technology, leading to more efficient operations, improved communication, and ultimately, a competitive edge in the market. Embracing cloud video solutions is a strategic move.
Scalability and Flexibility
One of the primary advantages of cloud video platform is their scalability. Businesses can effortlessly scale their video management needs up or down based on current demand without the need for significant upfront investments in hardware. This flexibility is crucial in adapting to business growth or changes without incurring additional costs or delays. Moreover, it allows companies to efficiently manage resources and respond promptly to evolving market conditions.
Accessibility and Reach
With a cloud video platform, videos can be accessed from anywhere, at any time, on any device with internet access. This global accessibility ensures that employees in different locations can easily participate in training sessions, meetings, and collaborations without the need for physical travel, further enhancing productivity across the organization. Additionally, it allows for seamless integration of remote and on-site teams, fostering a more connected and efficient workplace.
Enhanced Collaboration
A cloud video platform facilitates enhanced collaboration among teams by providing features such as real-time sharing, editing, and communication tools. These integrated features enable teams to work together more effectively, even when members are spread across various geographic locations. This real-time interaction significantly aids in quicker decision-making and problem-solving, ensuring that projects progress smoothly and efficiently regardless of physical distances.
Cost-Effectiveness
Moving to a cloud video platform can significantly reduce costs related to video content management. By leveraging cloud services, businesses eliminate the need for expensive on-premise infrastructure. Additionally, the maintenance and upgrading of systems are handled by the service provider, which can further decrease IT expenses. Furthermore, cloud platforms offer scalable solutions that allow businesses to pay only for the resources they use, optimizing budget allocation.
Security and Compliance
Security is a top concern for any business leveraging digital tools. The cloud video platform is equipped with robust security measures, including data encryption, secure access controls, and compliance with international standards. These features ensure that sensitive content remains protected against unauthorized access and breaches. Additionally, regular security audits and updates further enhance the platform's ability to safeguard valuable data, providing businesses with peace of mind and confidence in their digital security.
Improved Content Management and Analytics
A cloud video platform also offers advanced content management systems, allowing businesses to efficiently organize, manage, and retrieve video content with ease. Additionally, these platforms provide insightful analytics on viewer engagement, content performance, and other key metrics. This data-driven approach enables businesses to make informed decisions to optimize their video strategies, enhance viewer experience, and ultimately drive better results in their video marketing efforts.
Implementing Cloud Video Platform: Considerations and Best Practices
Implementing a cloud video platform yields significant benefits, but its success hinges on strategic planning and factor consideration. Vital elements encompass selecting an appropriate platform, meeting bandwidth needs, prioritizing user adoption tactics, and upholding data governance policies. These measures collectively shape a robust foundation for seamless integration and optimized performance.
Choosing the Right Platform
Selecting the appropriate cloud video platform is critical and should be based on specific business needs such as feature requirements, scalability, security, and compatibility with existing systems. Businesses should conduct thorough research or consult with experts to find the best fit.
Ensuring Adequate Bandwidth
Effective video streaming requires sufficient bandwidth. Before implementation, businesses need to assess their internet bandwidth to ensure smooth video playback and uploading capabilities without disrupting other business operations.
Focusing on User Adoption
To maximize the benefits of cloud video platform, promoting user adoption through training and support is essential. Employees need to understand how to use the platform efficiently and be comfortable with its features to fully leverage its capabilities.
Adhering to Data Governance
Businesses must also consider data governance when implementing cloud video platform. Ensuring that the platform complies with relevant laws and regulations regarding data privacy and protection is crucial.
Conclusion
The adoption of a cloud video platform can bring transformative benefits to businesses, fostering better communication and collaboration, providing scalability and flexibility, enhancing content management and analytics, reducing costs, and bolstering security. By leveraging cloud technology, organizations can streamline their operations and improve efficiency. Moreover, these platforms enable seamless remote work, support real-time collaboration, and offer advanced tools for data-driven decision-making. With careful planning and consideration of the key factors outlined above, organizations can effectively implement and use these platforms to achieve substantial business success, ensuring they stay competitive in an increasingly digital and connected world. please don’t hesitate to contact us via email or phone for further assistance!
#cloud video platform#secure video hosting#streaming video hosting#encrypted video hosting#drm encrypted video streaming#encrypted video streaming#DRM software#video hosting#security video#video platforms#online video platform#video watermark#DRM protected content#video cdn#wide vine#online courses#e-learning platforms#influencers#paid online courses#E-Learning Solutions#Digital content
2 notes
·
View notes
Text
Sigzen Technologies: Transforming Challenges into Opportunities with Robust Backup and Disaster Recovery Solutions
In today’s fast-paced digital world, where data plays a crucial role in business operations, having a reliable Backup Solution and Disaster Recovery plan is paramount. Sigzen Technologies emerges as a leader in this space, offering cutting-edge solutions that not only safeguard critical data but also transform challenges into opportunities for businesses. Automated Backup An automated backup…

View On WordPress
#Business Continuity Strategies#Cloud Backup Excellence#Data Protection Standards#Data Security Leaders#Sigzen Tech Solutions
2 notes
·
View notes
Text
Cloud Security Solutions and Infrastructure as Code Security: How Gomboc Protects Your Digital Assets
As businesses continue to transition their operations to the cloud, the need for robust cloud security solutions has never been more critical. With a growing reliance on cloud-based infrastructure, protecting sensitive data and applications is paramount. At the same time, modern cloud environments often leverage Infrastructure as Code (IaC) to automate and streamline resource provisioning. However, this automation also introduces new security challenges that need to be addressed proactively. This is where Infrastructure as Code security becomes essential.
At Gomboc, we understand the complexities of securing cloud infrastructures and IaC environments. Our cloud security solutions are designed to offer comprehensive protection for your digital assets while ensuring that your automated infrastructure deployments are secure from the start. In this article, we’ll delve into the importance of cloud security solutions and IaC security and how Gomboc can help safeguard your cloud infrastructure.
The Growing Need for Cloud Security Solutions
Cloud environments have revolutionized how businesses manage their IT infrastructure, offering flexibility, scalability, and cost savings. However, these advantages come with the risk of cyber threats, including data breaches, denial-of-service attacks, and insider threats. To mitigate these risks, businesses need robust cloud security solutions that can secure their data, applications, and overall cloud architecture.
A strong cloud security solution like Gomboc ensures that every layer of the cloud infrastructure is protected, from the network to the application and the data layer. Our platform integrates advanced security features like real-time threat detection, automated vulnerability management, and continuous compliance monitoring to offer businesses a proactive defense against emerging cyber threats. With Gomboc's security solutions, organizations can rest assured that their cloud environment is constantly monitored and secured against potential risks.
The Role of Infrastructure as Code Security
As organizations increasingly adopt cloud automation, Infrastructure as Code (IaC) has become a critical component of modern cloud operations. IaC allows teams to define and manage cloud infrastructure through code, enabling faster deployments and easier scalability. However, because IaC configurations are code-driven, any misconfigurations or security flaws in the code can lead to significant vulnerabilities in the cloud infrastructure.
This is where IaC security comes into play. Securing IaC ensures that the infrastructure code is free from vulnerabilities and adheres to best security practices before deployment. By incorporating security into the IaC process, businesses can prevent common issues like misconfigured cloud resources or insecure access controls, which could be exploited by cybercriminals.
Gomboc offers robust IaC security capabilities, automatically scanning and assessing IaC templates and code for potential vulnerabilities. With Gomboc’s IaC security features, businesses can catch issues early in the development cycle, reducing the risk of deploying insecure infrastructure to the cloud. Our platform integrates seamlessly with popular IaC tools, ensuring that security is embedded directly into the development pipeline, providing both security and efficiency.
How Gomboc Helps With Cloud Security Solutions and IaC Security
Gomboc combines cutting-edge cloud security solutions with specialized IaC security to provide businesses with a comprehensive security posture for their cloud environments. Our platform delivers:
Real-Time Threat Detection: Gomboc continuously monitors your cloud infrastructure, identifying potential threats before they can cause damage. We use advanced machine learning algorithms to detect and respond to anomalies, reducing the risk of security breaches.
Automated IaC Vulnerability Scanning: Gomboc’s IaC security tools automatically scan infrastructure code for common vulnerabilities and compliance issues. This ensures that any misconfigurations or insecure practices are addressed before deployment, preventing costly mistakes and enhancing the security of your cloud infrastructure.
Continuous Compliance Monitoring: Regulatory compliance is an ongoing concern for many businesses. Gomboc’s cloud security solutions help ensure that your cloud environment remains compliant with industry standards and regulations by providing continuous monitoring and automated reporting.
Comprehensive Security Coverage: From network security to identity management, Gomboc’s platform covers all aspects of cloud security. We integrate seamlessly with cloud providers like AWS, Azure, and Google Cloud, offering end-to-end protection for your cloud infrastructure.
Why Choose Gomboc for Cloud Security Solutions and IaC Security?
Gomboc’s unique approach to cloud security solutions and IaC security provides businesses with the tools they need to maintain a secure, compliant, and efficient cloud infrastructure. Our platform combines automated security scanning, real-time monitoring, and a proactive defense strategy to safeguard your digital assets.
With Gomboc, businesses can embrace the full potential of cloud computing without compromising on security. Whether you're managing complex cloud environments or deploying infrastructure with IaC, Gomboc ensures that every aspect of your cloud security is taken care of.
In conclusion, as businesses continue to adopt cloud services and Infrastructure as Code, integrating cloud security solutions and IaC security into your operations is crucial. Gomboc offers a comprehensive platform that helps businesses protect their cloud environments while ensuring that their IaC deployments are secure and compliant. With Gomboc, you can have peace of mind knowing that your cloud infrastructure is in safe hands.
0 notes
Text
The advantages of Computer Networks: Enhancing Connectivity & Efficiency
Computer networks form the backbone of modern communication, business operations, and data management, enabling seamless connectivity and resource sharing. Whether in workplaces, homes, or global enterprises, networking has transformed the way we exchange information. Here’s why computer networks are essential for efficiency, security, and collaboration. 1. Seamless Communication &…
#business connectivity#cloud storage solutions#computer networking benefits#digital collaboration#IT infrastructure efficiency#network performance optimization#secure data sharing
0 notes
Text
🚀 Lightspeed evolution in #tech ! Discover how 2023 advanced #AI , #cybersecurity , and more. Curious about how these changes can boost your #business ? Let's navigate this #tech landscape together! Visit us at https://techsolworld.com/subscriptions Call (800)998-2792. #TechUpdate
#cloud technology#microsoft tech#microsoft technology#microsoft 365 partner#microsoft azure#microsoft azure partner#cyber security experts#microsoft cyber security experts#microsoft appsource#find a partner on microsoft appsource#buy a microsoft 365 subscription#buy a microsoft business subscription#buy a microsoft enterprise subscription#buy a microsoft azure subscription#get a discount on microsoft azure subscription#get help with Microsoft Cyber Security#buy Microsoft 365 Business Basic#buy Microsoft 365 Business Standard#buy Microsoft 365 Business Premium#buy Microsoft 365 E5#buy Microsoft 365 E3#buy Microsoft 365 E5 no teams#buy Microsoft 365#buy Microsoft 365 E3 No Teams#get microsoft business subscription#get microsoft enterprise agreement renewal#technology solutions worldwide
0 notes
Text
Safeguard Your Data with Esconet’s Advanced Backup Systems
Looking for reliable and scalable data backup solutions? Esconet Technologies Ltd., based in New Delhi, delivers robust and customized enterprise data protection services, securing business-critical information across on-premise, cloud, and hybrid environments.
With features like deduplication, ransomware-resilient storage, high-speed WAN backups, and application-aware protection, Esconet ensures rapid recovery and business continuity.
From legacy LTO backups to cloud-integrated systems, Esconet’s expert team supports you with seamless implementation and 24x7 support. Their solutions are compatible with leading platforms including Dell, HPE, and Veeam.
Learn more about how Esconet can protect your business data: Esconet Data Backup Page
#Data Backup India#Enterprise Data Protection#Ransomware Backup Solutions#Hybrid Cloud Backup Services#LTO Tape Backup#Esconet Technologies Ltd.#New Delhi IT Solutions#Instant Restore Backup#Secure Business Data Backup#Application-Aware Backup India
0 notes
Video
youtube
🔐 Your Data Deserves Better
This Wednesday, we’re diving into the future of data protection with an exclusive presentation on GotBackup — the cloud backup service that secures your files and helps you earn residual income. 💻💰
🌍 100% Online & Free 🗓️ Don’t miss it — spots are limited!
👉 Reserve Your Spot Now
https://bit.ly/42JEDax
#GotBackup #DataProtection #CloudBackup #DigitalSecurity #OnlineBackup #PassiveIncome #WorkFromHome #TechTools #BackupSolutions #SecureYourFiles #ProtectYourData #TumblrEvents #CyberSecurity #CloudStorage
(via 🔒 Why You Can’t Miss This Wednesday’s GotBackup Presentation!)
#GotbackUp#data protection#cloud backup#digital security#Online Backup#passive income#work from home#tech tools#backup solution#secure your files#protect your data#tumblr event#cybersecurity#cloud storage
0 notes
Text
Create Impactful Digital Experiences with Augmented Reality Development Services
At Atcuality, we believe in the power of augmented reality to transform how users interact with brands. Our augmented reality development services provide businesses with innovative solutions that captivate audiences by blending digital and real-world elements. This immersive technology enables users to visualize products, explore environments, and experience services in a whole new way. Our experienced team of developers and designers work collaboratively with clients to deliver custom AR applications that align with specific business goals. By adopting AR, businesses can enhance customer engagement, increase interaction, and differentiate themselves in a crowded market. With Atcuality’s augmented reality development services, you can create digital experiences that leave a lasting impression, building stronger connections with your audience. Discover how AR can benefit your brand and redefine customer interaction with Atcuality's expertise at your service.
#iot applications#artificial intelligence#technology#digital marketing#seo marketing#seo#seo services#emailmarketing#search engine optimization#google ads#socialmediamarketing#augmented reality#augmented human c4 621#augmented and virtual reality market#blockchain#ai powered application#amazon web services#mobile app development company#mobile app developers#mobile application development#app developers#app development company#azure cloud services#cash collection application#cloud security services#iot app development services#task management solution
4 notes
·
View notes