#infrastructure as code security
Explore tagged Tumblr posts
Text
Gomboc: Remaking Infrastructure as Code Security through Intelligent Cloud Solutions
As increasingly more businesses rely on cloud-native technology, we have transformed how we think about infrastructure completely. Gone is the traditional manual config, replaced instead by Infrastructure as Code (IaC) — a cycle that allows groups to provision and control IT infrastructure from machine-readable definition files. Though this evolution has brought unprecedented speed and scaling, it's also created fresh security challenges. That is why companies today need to have good infrastructure as code security to allow their cloud environments not just be effective, but also secure.
Here comes Gomboc, the next-gen cloud security solution by design, made specifically for the era of automation.

The Security Challenges of IaC
IaC speeds up deployments and keeps stable environments in development, staging, and production. But when it's misconfigured or not monitored, IaC opens its systems to devastating vulnerabilities. One incorrect Terraform script or Kubernetes configuration can open ports, grant too much access control, or expose secret leaks — compromising your whole cloud infrastructure.
With traditional security tools falling short of being capable of finding code-level misconfigurations, DevSecOps teams today need smarter, more proactive ones. That is where Gomboc is.
Gomboc: Proactive Cloud Security for Modern DevOps
Gomboc is an intelligent cloud security platform designed to empower organizations to safeguard their cloud infrastructure on the code level — before threats hit production. By incorporating security into development, Gomboc enables DevOps teams to "shift left" and identify issues early, wasting time, cost, and risk.
Main Features of Gomboc's IaC Security
Automated Code Scanning: Gomboc scans your Terraform, CloudFormation, or Kubernetes files to spot configuration issues and possible security loopholes.
Real-Time Feedback in CI/CD: Gomboc seamlessly plugs into your CI/CD workflow, giving real-time feedback with notifications and remediations without interrupting your rhythm.
Contextual Remediation: Rather than highlighting issues, Gomboc delivers actionable, code-level remediations tailored to your cloud setup.
Compliance by Design: Maintain your configurations in compliance with industry standards like CIS Benchmarks, SOC 2, and HIPAA from the development phase.
Multi-Cloud Support: With AWS, Azure, or GCP, Gomboc allows you to keep your stack up to date with cross-platform visibility and security.
Why Gomboc Delivers Cloud Security
Most cloud security tools react after infrastructure has been provisioned. Gomboc turns that model on its head by baking security into design, halting misconfigurations from getting to runtime.
This "security as code" mindset allows development teams to move fast, stay compliant, and greatly reduce their attack surface — frictionless, headache-free, no legacy pain. It fosters a security-first culture, which holds engineers responsible for secure deployments day one.
cloud security solutionscloud security solutions
As cloud infrastructure becomes more sophisticated, so should the way we secure it. With Gomboc's infrastructure as code security, businesses no longer need to compromise on speed or security. You can have both — and grow with confidence.
Whether high-growth startup embracing DevOps or enterprise cloud-migrating, Gomboc's smart cloud security technologies will enable you to protect your code, your cloud, and your future.
Visit Gomboc.ai to find out more, ask for a demo, or start your free trial today.
0 notes
Video
youtube
Terraform on Azure - Create Bastion Service and Host | Infrastructure as...
#youtube#Learn how to deploy secure Azure Bastion Host and Bastion Service using Terraform (Infrastructure as Code)! In this step-by-step tutorial we
0 notes
Text
The Future of Cloud App Development: Unlocking Business Value
Cloud computing is rapidly transforming businesses. Many industry reports reveal that as business mobile applications grow, over 70% of digital workspaces face challenges with storage capacity and performance. The ideal solution to these issues is cloud app development, which provides unmatched scalability and flexibility.
Cloud app development simplifies data collection, enabling businesses to gather insights faster and more efficiently. It also enhances data security and streamlines management, making compliance and administration less burdensome. Cloud-powered development solutions empower businesses to create high-performance, productivity-focused applications that drive customer satisfaction and boost revenue.
Furthermore, cloud software solutions support low-code development, a time- and cost-efficient approach that minimizes extensive coding. This allows businesses to launch applications faster, optimizing resource usage and accelerating innovation cycles.
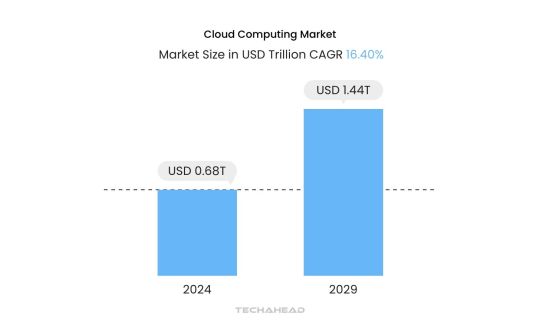
The cloud computing market is projected to grow substantially, with an estimated size of USD 0.68 trillion in 2024, anticipated to reach USD 1.44 trillion by 2029 at a CAGR of 16.40% (source: Mordor Intelligence). This robust growth highlights the rising demand for cloud solutions across industries. However, this rapid expansion in cloud applications prompts critical questions for businesses, especially around best practices in cloud app development.
In this guide, we’ll explore how to approach cloud app development effectively, the diverse cloud-based application solutions available, and how they drive value. You’ll gain insights into creating cloud applications that enhance operational efficiency, scalability, and customer engagement.
Let’s begin by examining the essentials that pave the way for efficient and future-ready cloud app development.
What is Cloud App Development?
Cloud app development refers to creating applications within a cloud environment, bypassing the need for local servers. Unlike native applications, cloud-based apps rely extensively on cloud app development services, including data storage and processing, making them accessible through web browsers and other online platforms.
As enterprise development grows more reliant on cloud capabilities, they have leveraged its computational power to build groundbreaking solutions, transforming what’s possible in technology. Cloud services now empower companies to create a vast range of cloud applications that operate seamlessly on the web, often known as web apps.
These cloud apps are reshaping various business functions, taking over essential tasks like email, word processing, file storage, data collection, and even financial accounting. Through cloud app development, organizations are equipped with efficiency, streamline operations, and scale solutions like never before.
Types of Cloud App Development
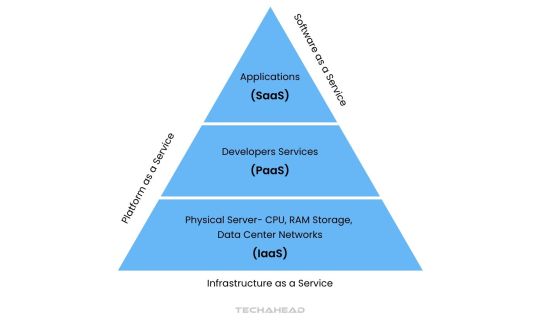
Software-as-a-Service (SaaS)
SaaS applications are hosted and maintained entirely by a cloud provider, making them accessible via the internet through web browsers. These applications relieve businesses from handling updates, server management, and software installations, as all maintenance is centrally managed by the provider. Users can seamlessly access features, integrate productivity tools, and share data across teams, which enhances operational efficiency.
Solutions like Google Workspace, Salesforce, and Slack exemplify SaaS by providing essential tools for collaboration, sales, and project management within a single, easily accessible platform.
Platform-as-a-Service (PaaS)
PaaS offers a managed environment for application development, which includes tools for building, testing, and deploying software while the cloud provider oversees infrastructure. By managing hardware and backend services, PaaS enables development teams to focus solely on cloud app development without the burden of configuring servers or databases. This platform accelerates time-to-market and streamlines scaling since the underlying resources are automatically adjusted as demand increases.
Examples like Microsoft Azure App Services and Google App Engine give developers robust frameworks and APIs, helping them build complex applications with minimal operational overhead.
Infrastructure-as-a-Service (IaaS)
IaaS delivers essential computing infrastructure such as virtual servers, storage, and networking resources. Unlike traditional on-premises infrastructure, IaaS allows businesses to pay for only the resources they use, which is ideal for scaling and managing large workloads flexibly. This model offers extensive control over the infrastructure, enabling IT teams to customize their environments and manage systems as needed.
Leading providers like AWS, Azure, and Google Cloud Platform provide services that allow companies to extend, scale, and secure their infrastructure easily, aligning with cloud app development needs for flexibility and resilience.
Function-as-a-Service (FaaS)
FaaS is part of serverless computing, allowing developers to deploy discrete code functions triggered by specific events, like user actions or system updates. With FaaS, there’s no need to manage or scale servers manually; the cloud provider handles it automatically based on demand. This model is ideal for applications requiring quick responses to high volumes of concurrent events, as it enhances cost efficiency and operational simplicity.
Popular FaaS services include AWS Lambda and Google Cloud Functions, which cater to cloud app development that prioritizes lightweight, highly scalable, and event-driven functionality.
Container-as-a-Service (CaaS)
CaaS leverages containers—lightweight, portable units of software that package application code along with its dependencies—for more efficient deployment and scaling across different environments. This model is highly beneficial for businesses adopting microservices architectures, as containers improve consistency in app deployment from development to production. CaaS platforms utilize orchestration tools, like Kubernetes, to automate the deployment, scaling, and management of containerized applications across multiple cloud or on-premises environments.
CaaS aligns with cloud app development demands for agility, allowing applications to scale seamlessly across hybrid or multi-cloud setups without compatibility issues.
Features of Every Cloud App Development Should Have
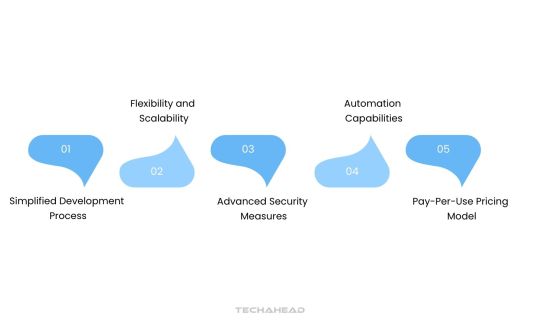
Simplified Development Process
An effective cloud app development platform should prioritize speed and simplicity. It should streamline architectural decisions, reducing complexity in creating and deploying applications across diverse technical environments. This simplicity allows hired developers to address challenges faster, minimizing errors and accelerating deployment. An efficient platform optimizes the overall development workflow, making it seamless to launch applications that meet high standards across various infrastructures.
Flexibility and Scalability
In cloud app development, flexibility is paramount. A robust platform should allow users to easily scale resources—adding or removing computing power, storage, and networking assets as demands fluctuate. Through automated scaling, these platforms adapt to dynamic workloads, preventing bottlenecks while ensuring optimal performance. During peak demand, a well-configured platform should instantly increase resources, and when demand lessens, it should scale down, maximizing cost-efficiency and resource allocation.
Advanced Security Measures
Security in cloud app development is a core feature, as cloud platforms employ top-tier security experts dedicated to threat management. These platforms adhere to stringent security protocols, often exceeding the protection provided by in-house teams. With compliance measures integrated, organizations can meet industry and governmental regulations effortlessly. Notably, 91% of companies report improved regulatory compliance post-cloud migration, emphasizing the cloud’s ability to safeguard data and ensure confidentiality.
You can also learn about the pillars of AI security and how it is protecting future technology.
Automation Capabilities
Automated processes are vital for managing complex, repetitive tasks in cloud app development. Advanced platforms support continuous integration and resource orchestration, which reduce operational burdens. Automation tools manage workload scaling, ensuring resources are available when needed without manual intervention. This allows IT teams to support growing demands efficiently while concentrating on strategic initiatives, enhancing overall operational efficiency.
Pay-Per-Use Pricing Model
A pay-per-use model enhances cost control within cloud app development, as users only pay for what they consume. This approach eliminates unnecessary expenses, allowing businesses to scale resources economically. Cloud providers track and report usage metrics, helping users monitor and optimize expenses. Some providers also offer a base level of free storage or computing power, making cloud resources even more accessible for startups and small businesses.
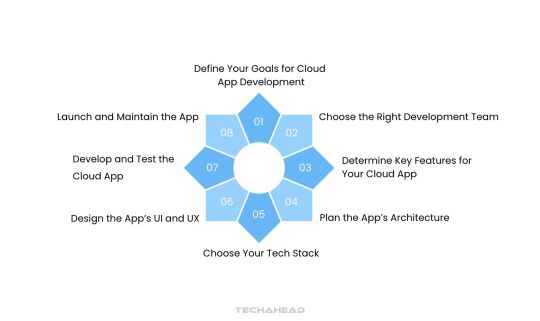
Steps to Take While Developing a Cloud App
Creating a cloud app can involve web or mobile solutions, with the required technologies varying by solution type. Despite technical differences, the fundamental process in cloud app development follows similar phases to build a robust, user-centered application.
Step 1: Define Your Goals for Cloud App Development
Establishing clear objectives is crucial before development begins. Align all stakeholders on the project’s vision and goals during the discovery phase, helping the team understand the core business needs.
Reasons to consider cloud app development include:
Workflow automation: Streamlining repetitive tasks saves time and resources
Centralized data storage: Access and manage data easily within a single, organized environment.
Enhanced team collaboration: Improve internal communication and ensure seamless data exchanges.
Advanced reporting and analytics: Gain valuable insights to drive data-based decisions.
The discovery phase also allows developers to identify project scope, complexities, potential challenges, and costs. If a swift market entry is critical, a Minimum Viable Product (MVP) may be the best first step.
Step 2: Choose the Right Development Team
Cloud app development requires specialized skills, so selecting the right development team is essential. You can opt for freelancers, in-house talent, or outsource to a software development company.
Choosing a reliable cloud app development partner ensures ongoing support as the app evolves. Here are some questions to assess potential developers:
Can you share similar cloud app projects you have handled?
What platforms and technologies are you skilled in?
How do you prioritize security and scalability in development?
How do you approach cost management for cloud resources?
Can you ensure effective collaboration throughout the project?
A reliable development partner can adapt the app as technology advances and business needs grow.
Step 3: Determine Key Features for Your Cloud App
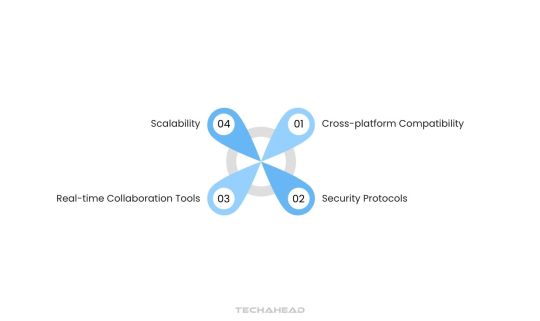
Identify core features that create a user-friendly experience in cloud applications. Essential features include:
Cross-platform compatibility: Allow users to access the app on their preferred devices.
Security protocols: Implement logins and access controls to protect user data.
Real-time collaboration tools: Enable users to work together through features like chat, live comments, and shared documents.
Scalability: Ensure the app can handle increasing users or workload.
Incorporating these features enhances user satisfaction and engagement, setting your app up for success.
Step 4: Plan the App’s Architecture
Your app’s architecture is the backbone of cloud app development, influencing scalability, security, and cost efficiency. Choose an architecture that aligns with your project’s requirements.
Key options include:
Monolithic architecture: A single, interconnected application; easy to develop but challenging to scale.
Microservices architecture: Divides the app into independent services; highly scalable but may face performance trade-offs.
Serverless architecture: Uses event-triggered functions in a serverless environment, ideal for low-maintenance, scalable solutions.
Hybrid architecture: Combines on-premises and cloud resources for high flexibility but may involve integration complexities.
Select an architecture that best aligns with your cloud app development goals. You can also look into this guide on Serverless Vs. Microservices architecture.
Step 5: Choose Your Tech Stack
The technology stack determines how quickly, securely, and effectively the app functions. Different projects require different combinations of programming languages (e.g., Java, Python, Node.js), databases (e.g., MongoDB, Firebase), frameworks (e.g., React, Angular), and containers (e.g., Docker, Kubernetes).
For instance, a Python-based stack offers scalability and maintenance ease, while Ruby on Rails works well for prototyping and collaboration. Choose the right tech stack that aligns with your app’s performance and integration needs.
Step 6: Design the App’s User Interface (UI) and User Experience (UX)
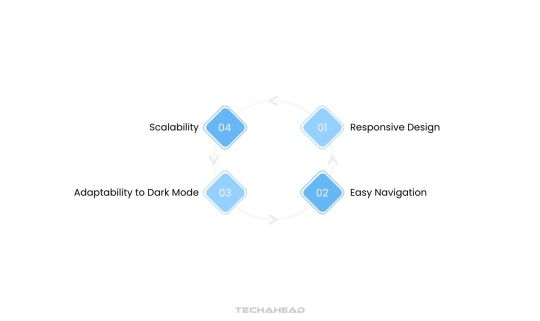
Effective UI/UX design is vital in cloud app development to create intuitive and visually appealing apps. Consider these elements:
Responsive design: Ensure seamless functionality across platforms and screen sizes.
Easy navigation: Users should quickly find what they need with minimal guidance.
Adaptability to dark mode: Offer both light and dark modes to reduce eye strain.
Scalability: Design a UI that accommodates future growth and additional features.
A responsive, intuitive, and adaptable UI makes the app user-friendly and future-proof. You can learn more about the Mobile UI designs as well.
Step 7: Develop and Test the Cloud App
Cloud app development typically uses Agile or DevOps methodologies, depending on project needs and team preferences.
Agile development emphasizes short, iterative development cycles, with regular testing and feedback after each sprint. Agile promotes flexibility, allowing the team to adapt to evolving requirements.
DevOps fosters collaboration across development and operations, with a focus on Continuous Integration/Continuous Delivery (CI/CD) and automation for efficient testing and deployment.
Both approaches streamline development, but the choice depends on team readiness and project goals.
Step 8: Launch and Maintain the App
Successful cloud app development doesn’t end with deployment. Continuous maintenance keeps your app relevant, responsive, and secure. Essential areas include:
Security updates: Regular patches to safeguard user data.
Performance optimization: Keep the app fast and responsive as usage grows.
Scalability adjustments: Ensure the app scales efficiently as demand fluctuates.
Technology updates: Adapt the stack to new versions or libraries.
Ongoing maintenance ensures a secure, scalable, and high-performing cloud app that keeps pace with technological advancements and user expectations.
Benefits of Cloud App Development
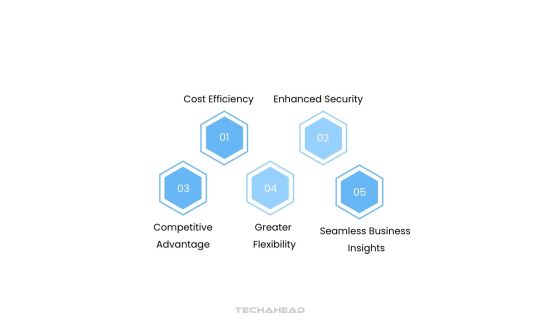
Cost Efficiency
Cloud app development significantly reduces costs by eliminating the need for on-premise infrastructure. With cloud-based applications, businesses only pay for the services they use, making it approximately 40% more affordable for small companies. This pay-as-you-go model means businesses can adjust monthly expenses based on usage, resulting in ongoing cost control.
Unlike traditional hardware, which requires significant upfront investment, cloud solutions offer flexible pricing that can scale with business growth. Additionally, many providers offer cost-saving options, like discounts on long-term contracts for larger enterprises.
You can learn more about the cost of app development.
Enhanced Security
Data security remains a huge priority when it comes to cloud app development. While integrating them, they tend to provide robust protection that safeguards sensitive information. Top cloud-based service providers employ advanced encryption techniques. It all helps in making it harder to get data accessibility for unauthorized users.
Even if there’s an intrusion attempt, encryption ensures data remains protected. Cloud hosting also includes 24/7 monitoring by specialized security teams, often surpassing the reliability of in-house systems. Research shows that 94% of businesses have reported enhanced data security after moving to cloud-based applications, demonstrating its effectiveness in managing data integrity and safety.
Competitive Advantage
Leveraging cloud app development gives companies a significant competitive edge. Cloud services handle infrastructure management, freeing up IT teams to focus on innovation and growth-centric initiatives. With a faster deployment cycle and access to the latest cloud technologies, cloud-enabled companies stay ahead in a rapidly evolving market.
Studies indicate that 77% of organizations find cloud technology helps maintain a competitive advantage. Cloud providers regularly update their offerings, allowing businesses to utilize state-of-the-art tools without needing continual hardware upgrades.
Greater Flexibility
Cloud app development introduces flexibility that in-house servers can’t match, especially in scaling resources. Teams no longer need to worry about storage or bandwidth limitations since cloud infrastructure can easily expand based on demand. This adaptability enables businesses to swiftly respond to changing market needs and to adjust resources during peak times. By outsourcing app development to cloud providers, in-house teams can focus on creating impactful solutions that directly support business objectives, fostering a more agile methodology, and resilient organization.
You can learn more about Offshore Vs. Onshore.
Seamless Business Insights
Current data-driven environment, the insights derived from cloud app development are invaluable. Cloud storage solutions offer powerful analytics tools that allow businesses to process and analyze data effortlessly. With these tools, businesses can gain actionable insights, create detailed reports, and use real-time data to enhance decision-making.
Conclusion
Cloud computing is transformative, future-ready technology that drives business scalability, efficiency, and sustainable growth. Leveraging cloud app development, companies startups or even established enterprises can significantly enhance performance, streamline operations, and cut down on overhead expenses.
Investing in cloud app development services is a strategic step for any business aiming to launch a resilient, next-gen mobile application. Given the technical expertise required for implementing cloud infrastructure in mobile applications, it’s advisable to engage skilled app developers with experience in startup solutions.
Source URL: https://www.techaheadcorp.com/blog/cloud-app-development-reaching-the-value-infection-point/
0 notes
Text
Building Your Serverless Sandbox: A Detailed Guide to Multi-Environment Deployments (or How I Learned to Stop Worrying and Love the Cloud)
Introduction Welcome, intrepid serverless adventurers! In the wild world of cloud computing, creating a robust, multi-environment deployment pipeline is crucial for maintaining code quality and ensuring smooth transitions from development to production.Here is part 1 and part 2 of this series. Feel free to read them before continuing on. This guide will walk you through the process of setting…
#automation#aws#AWS S3#CI/CD#Cloud Architecture#cloud computing#cloud security#continuous deployment#DevOps#GitLab#GitLab CI#IAM#Infrastructure as Code#multi-environment deployment#OIDC#pipeline optimization#sandbox#serverless#software development#Terraform
0 notes
Text
In cloud computing, the demand for speed, scalability, and reliability significantly influences IT infrastructure development strategies. As cloud ecosystems grow more complex and integral to operations, the potential security risks and points of failure increase. One pivotal innovation that aligns with these needs is Infrastructure as Code (IaC).
0 notes
Text
Driving Innovation: A Case Study on DevOps Implementation in BFSI Domain
Banking, Financial Services, and Insurance (BFSI), technology plays a pivotal role in driving innovation, efficiency, and customer satisfaction. However, for one BFSI company, the journey toward digital excellence was fraught with challenges in its software development and maintenance processes. With a diverse portfolio of applications and a significant portion outsourced to external vendors, the company grappled with inefficiencies that threatened its operational agility and competitiveness. Identified within this portfolio were 15 core applications deemed critical to the company’s operations, highlighting the urgency for transformative action.
Aspirations for the Future:
Looking ahead, the company envisioned a future state characterized by the establishment of a matured DevSecOps environment. This encompassed several key objectives:
Near-zero Touch Pipeline: Automating product development processes for infrastructure provisioning, application builds, deployments, and configuration changes.
Matured Source-code Management: Implementing robust source-code management processes, complete with review gates, to uphold quality standards.
Defined and Repeatable Release Process: Instituting a standardized release process fortified with quality and security gates to minimize deployment failures and bug leakage.
Modernization: Embracing the latest technological advancements to drive innovation and efficiency.
Common Processes Among Vendors: Establishing standardized processes to enhance understanding and control over the software development lifecycle (SDLC) across different vendors.
Challenges Along the Way:
The path to realizing this vision was beset with challenges, including:
Lack of Source Code Management
Absence of Documentation
Lack of Common Processes
Missing CI/CD and Automated Testing
No Branching and Merging Strategy
Inconsistent Sprint Execution
These challenges collectively hindered the company’s ability to achieve optimal software development, maintenance, and deployment processes. They underscored the critical need for foundational practices such as source code management, documentation, and standardized processes to be addressed comprehensively.
Proposed Solutions:
To overcome these obstacles and pave the way for transformation, the company proposed a phased implementation approach:
Stage 1: Implement Basic DevOps: Commencing with the implementation of fundamental DevOps practices, including source code management and CI/CD processes, for a select group of applications.
Stage 2: Modernization: Progressing towards a more advanced stage involving microservices architecture, test automation, security enhancements, and comprehensive monitoring.
To Expand Your Awareness: https://devopsenabler.com/contact-us
Injecting Security into the SDLC:
Recognizing the paramount importance of security, dedicated measures were introduced to fortify the software development lifecycle. These encompassed:
Security by Design
Secure Coding Practices
Static and Dynamic Application Security Testing (SAST/DAST)
Software Component Analysis
Security Operations
Realizing the Outcomes:
The proposed solution yielded promising outcomes aligned closely with the company’s future aspirations. Leveraging Microsoft Azure’s DevOps capabilities, the company witnessed:
Establishment of common processes and enhanced visibility across different vendors.
Implementation of Azure DevOps for organized version control, sprint planning, and streamlined workflows.
Automation of builds, deployments, and infrastructure provisioning through Azure Pipelines and Automation.
Improved code quality, security, and release management processes.
Transition to microservices architecture and comprehensive monitoring using Azure services.
The BFSI company embarked on a transformative journey towards establishing a matured DevSecOps environment. This journey, marked by challenges and triumphs, underscores the critical importance of innovation and adaptability in today’s rapidly evolving technological landscape. As the company continues to evolve and innovate, the adoption of DevSecOps principles will serve as a cornerstone in driving efficiency, security, and ultimately, the delivery of superior customer experiences in the dynamic realm of BFSI.
Contact Information:
Phone: 080-28473200 / +91 8880 38 18 58
Email: [email protected]
Address: DevOps Enabler & Co, 2nd Floor, F86 Building, ITI Limited, Doorvaninagar, Bangalore 560016.
#BFSI#DevSecOps#software development#maintenance#technology stack#source code management#CI/CD#automated testing#DevOps#microservices#security#Azure DevOps#infrastructure as code#ARM templates#code quality#release management#Kubernetes#testing automation#monitoring#security incident response#project management#agile methodology#software engineering
0 notes
Text
Exciting Mock interview with DevOps/AWS engineer #devops #cloud #aws #devopsengineer #cloudengineer
Interviewer: Welcome to this exciting mock interview for the role of a DevOps/AWS Engineer! Today, we have an enthusiastic candidate eager to showcase their skills. Let’s begin! Candidate: Thank you! I’m thrilled to be here. Interviewer: Great to have you. Let’s start with a classic question: What attracted you to the field of DevOps and working with AWS? Candidate: DevOps combines my passion…

View On WordPress
#Automation#AWS#CI/CD#cloud engineering#cloud technology#collaboration#communication#continuous integration#cost optimization#cross-functional teams#DevOps#disaster recovery#high availability#IaC#incident management#infrastructure as code#mock interview#performance optimization#scalability#security#tech trends
0 notes
Text
Transform Your Business with Natural Group's Cloud Solutions

Discover how Natural Group's Cloud Solutions can empower your business with enhanced scalability, flexibility, and efficiency. Our expert team leverages the power of cloud technology to deliver tailored solutions that drive growth and innovation. Unlock the full potential of your business with our comprehensive cloud services.
#cloud#cloud solutions#Infrastructure as a Code#Cloud Integration Services#Cloud Migration#Custom Cloud Optimization#Cloud Application Development Services#DevOps Services#Machine Learning & AI#Security Service
0 notes
Text
The so-called Department of Government Efficiency (DOGE) is starting to put together a team to migrate the Social Security Administration’s (SSA) computer systems entirely off one of its oldest programming languages in a matter of months, potentially putting the integrity of the system—and the benefits on which tens of millions of Americans rely—at risk.
The project is being organized by Elon Musk lieutenant Steve Davis, multiple sources who were not given permission to talk to the media tell WIRED, and aims to migrate all SSA systems off COBOL, one of the first common business-oriented programming languages, and onto a more modern replacement like Java within a scheduled tight timeframe of a few months.
Under any circumstances, a migration of this size and scale would be a massive undertaking, experts tell WIRED, but the expedited deadline runs the risk of obstructing payments to the more than 65 million people in the US currently receiving Social Security benefits.
“Of course, one of the big risks is not underpayment or overpayment per se; [it’s also] not paying someone at all and not knowing about it. The invisible errors and omissions,” an SSA technologist tells WIRED.
The Social Security Administration did not immediately reply to WIRED’s request for comment.
SSA has been under increasing scrutiny from president Donald Trump’s administration. In February, Musk took aim at SSA, falsely claiming that the agency was rife with fraud. Specifically, Musk pointed to data he allegedly pulled from the system that showed 150-year-olds in the US were receiving benefits, something that isn’t actually happening. Over the last few weeks, following significant cuts to the agency by DOGE, SSA has suffered frequent website crashes and long wait times over the phone, The Washington Post reported this week.
This proposed migration isn’t the first time SSA has tried to move away from COBOL: In 2017, SSA announced a plan to receive hundreds of millions in funding to replace its core systems. The agency predicted that it would take around five years to modernize these systems. Because of the coronavirus pandemic in 2020, the agency pivoted away from this work to focus on more public-facing projects.
Like many legacy government IT systems, SSA systems contain code written in COBOL, a programming language created in part in the 1950s by computing pioneer Grace Hopper. The Defense Department essentially pressured private industry to use COBOL soon after its creation, spurring widespread adoption and making it one of the most widely used languages for mainframes, or computer systems that process and store large amounts of data quickly, by the 1970s. (At least one DOD-related website praising Hopper's accomplishments is no longer active, likely following the Trump administration’s DEI purge of military acknowledgements.)
As recently as 2016, SSA’s infrastructure contained more than 60 million lines of code written in COBOL, with millions more written in other legacy coding languages, the agency’s Office of the Inspector General found. In fact, SSA’s core programmatic systems and architecture haven’t been “substantially” updated since the 1980s when the agency developed its own database system called MADAM, or the Master Data Access Method, which was written in COBOL and Assembler, according to SSA’s 2017 modernization plan.
SSA’s core “logic” is also written largely in COBOL. This is the code that issues social security numbers, manages payments, and even calculates the total amount beneficiaries should receive for different services, a former senior SSA technologist who worked in the office of the chief information officer says. Even minor changes could result in cascading failures across programs.
“If you weren't worried about a whole bunch of people not getting benefits or getting the wrong benefits, or getting the wrong entitlements, or having to wait ages, then sure go ahead,” says Dan Hon, principal of Very Little Gravitas, a technology strategy consultancy that helps government modernize services, about completing such a migration in a short timeframe.
It’s unclear when exactly the code migration would start. A recent document circulated amongst SSA staff laying out the agency’s priorities through May does not mention it, instead naming other priorities like terminating “non-essential contracts” and adopting artificial intelligence to “augment” administrative and technical writing.
Earlier this month, WIRED reported that at least 10 DOGE operatives were currently working within SSA, including a number of young and inexperienced engineers like Luke Farritor and Ethan Shaotran. At the time, sources told WIRED that the DOGE operatives would focus on how people identify themselves to access their benefits online.
Sources within SSA expect the project to begin in earnest once DOGE identifies and marks remaining beneficiaries as deceased and connecting disparate agency databases. In a Thursday morning court filing, an affidavit from SSA acting administrator Leland Dudek said that at least two DOGE operatives are currently working on a project formally called the “Are You Alive Project,” targeting what these operatives believe to be improper payments and fraud within the agency’s system by calling individual beneficiaries. The agency is currently battling for sweeping access to SSA’s systems in court to finish this work. (Again, 150-year-olds are not collecting social security benefits. That specific age was likely a quirk of COBOL. It doesn’t include a date type, so dates are often coded to a specific reference point—May 20, 1875, the date of an international standards-setting conference held in Paris, known as the Convention du Mètre.)
In order to migrate all COBOL code into a more modern language within a few months, DOGE would likely need to employ some form of generative artificial intelligence to help translate the millions of lines of code, sources tell WIRED. “DOGE thinks if they can say they got rid of all the COBOL in months, then their way is the right way, and we all just suck for not breaking shit,” says the SSA technologist.
DOGE would also need to develop tests to ensure the new system’s outputs match the previous one. It would be difficult to resolve all of the possible edge cases over the course of several years, let alone months, adds the SSA technologist.
“This is an environment that is held together with bail wire and duct tape,” the former senior SSA technologist working in the office of the chief information officer tells WIRED. “The leaders need to understand that they’re dealing with a house of cards or Jenga. If they start pulling pieces out, which they’ve already stated they’re doing, things can break.”
260 notes
·
View notes
Text
Humans are weird: Prank Gone Wrong
( Please come see me on my new patreon and support me for early access to stories and personal story requests :D https://www.patreon.com/NiqhtLord Every bit helps)
“Filnar Go F%$@ Yourself!” was possibly the most disruptive software virus the universe had ever seen.
The program was designed to download itself to a computer, copy the functions of existing software before deleting said software and imitating it, then running its original programming all the while avoiding the various attempts to locate and remove it by security software.
What was strange about such a highly advanced virus was that it did not steal government secrets, nor siphon funds from banking institutions, it ignore critical infrastructure processes, and even bypassed trade markets that if altered could cause chaos on an unprecedented scale. The only thing the software seemed focused on was in locating any information regarding the “Hen’va” species, and deleting it.
First signs of the virus outbreak were recorded on the planet Yul’o IV, but once the virus began to migrate at an increasing rate and latched on to several subroutines for traveling merchant ships things rapidly spiraled out of control. Within a week the virus had infected every core world and consumed all information regarding the Hen’va. It still thankfully had not resulted in any deaths, but the sudden loss of information was beginning to cause other problems.
Hen’va citizens suddenly found that they were not listed as galactic citizens and were detained by security forces on numerous worlds. Trade routes became disrupted as Hen’va systems were now listed as uninhabited and barren leading to merchants seeking to trade elsewhere. Birth records and hospital information for millions of patients were wiped clean as they now pertained to individuals who did not exist.
Numerous software updates and purges were commenced in attempting to remove the virus. Even the galactic council’s cyber security bureau was mobilized for the effort, but if even a single strand of the virus’s code survived it was enough to rebuild itself and become even craftier with hiding itself while carrying out its programming. This was made worse by the high level of integration the various cyber systems of the galaxy had made it so the chance of systems being re-infected was always high.
After ten years every digital record of the Hen’va was erased from the wider universe. All attempts to upload copies were likewise deleted almost immediately leaving only physical records to remain untouched.
To combat this, the Hen’va for all official purposes adopted a new name; then “Ven’dari”. In the Hen’va tongue in means “The Forgotten”, which is rather ironic as the Hen’va have had to abandon everything about their previous culture to continue their existence. The virus had become a defacto component of every computer system in the galaxy and continued to erase all information related to the Hen’va. Even the translator units refused identify the Hen’va tongue and so the Ven’dari needed to create a brand new language.
It wasn’t until another fifty years had passed before the original creator of the virus stepped forward and admitted to their crime. A one “Penelope Wick”.
At the time of the programs creation Ms. Wick was a student studying on Yul’o IV to be a software designer. While attending the institution Ms. Wick stated that a fellow student, a Hen’va named “Filnar”, would hound her daily. He would denounce her presence within the school and repeatedly declared that “what are the scrapings of humans compared to the glory of the Hen’va?”
The virus was her creation as a way of getting back at the student for his constant spite. Ms. Wick was well aware of the dangers it could pose if released into the wild and so had emplaced the limitation that the virus would only infect computers on site with the campus. The schools network was setup that students could only work on their projects within the confines of the institution to ensure they did not cheat and have others make them instead. What she had not counted on was this rule only applied to students and not teachers. So when a teacher brought home several student projects to review and then sharing those infected files with their personal computer, the virus then gained free access to the wider planets networks.
When the Ven’dari learned of this there were several hundred calls for Ms. Wick to be held accountable for her actions, and nearly twice as many made to take her head by less patient individuals who had seen their entire culture erased. Much to their dismay Ms. Wick died shortly after her confession from a long term disease that had ravaged her body for several years.
Much to her delight, she had achieved her goals of removing the source of her mockery.
#humans are insane#humans are weird#humans are space oddities#humans are space orcs#story#scifi#writing#original writing#niqhtlord01#funny#prank#prank gone wrong#virus
370 notes
·
View notes
Video
youtube
Terraform on AWS - Design a 3 Tier AWS VPC with NAT Gateways | Infrastru...
#youtube#Learn how to design a secure scalable 3-Tier AWS VPC using Terraform and Infrastructure as Code (IaC)! In this hands-on tutorial we’ll walk
0 notes
Text
The Rise of DeFi: Revolutionizing the Financial Landscape

Decentralized Finance (DeFi) has emerged as one of the most transformative sectors within the cryptocurrency industry. By leveraging blockchain technology, DeFi aims to recreate and improve upon traditional financial systems, offering a more inclusive, transparent, and efficient financial ecosystem. This article explores the fundamental aspects of DeFi, its key components, benefits, challenges, and notable projects, including a brief mention of Sexy Meme Coin.
What is DeFi?
DeFi stands for Decentralized Finance, a movement that utilizes blockchain technology to build an open and permissionless financial system. Unlike traditional financial systems that rely on centralized intermediaries like banks and brokerages, DeFi operates on decentralized networks, allowing users to interact directly with financial services. This decentralization is achieved through smart contracts, which are self-executing contracts with the terms of the agreement directly written into code.
Key Components of DeFi
Decentralized Exchanges (DEXs): DEXs allow users to trade cryptocurrencies directly with one another without the need for a central authority. Platforms like Uniswap, SushiSwap, and PancakeSwap have gained popularity for their ability to provide liquidity and facilitate peer-to-peer trading.
Lending and Borrowing Platforms: DeFi lending platforms like Aave, Compound, and MakerDAO enable users to lend their assets to earn interest or borrow assets by providing collateral. These platforms use smart contracts to automate the lending process, ensuring transparency and efficiency.
Stablecoins: Stablecoins are cryptocurrencies pegged to stable assets like fiat currencies to reduce volatility. They are crucial for DeFi as they provide a stable medium of exchange and store of value. Popular stablecoins include Tether (USDT), USD Coin (USDC), and Dai (DAI).
Yield Farming and Liquidity Mining: Yield farming involves providing liquidity to DeFi protocols in exchange for rewards, often in the form of additional tokens. Liquidity mining is a similar concept where users earn rewards for providing liquidity to specific pools. These practices incentivize participation and enhance liquidity within the DeFi ecosystem.
Insurance Protocols: DeFi insurance protocols like Nexus Mutual and Cover Protocol offer coverage against risks such as smart contract failures and hacks. These platforms aim to provide users with security and peace of mind when engaging with DeFi services.
Benefits of DeFi
Financial Inclusion: DeFi opens up access to financial services for individuals who are unbanked or underbanked, particularly in regions with limited access to traditional banking infrastructure. Anyone with an internet connection can participate in DeFi, democratizing access to financial services.
Transparency and Trust: DeFi operates on public blockchains, providing transparency for all transactions. This transparency reduces the need for trust in intermediaries and allows users to verify and audit transactions independently.
Efficiency and Speed: DeFi eliminates the need for intermediaries, reducing costs and increasing the speed of transactions. Smart contracts automate processes that would typically require manual intervention, enhancing efficiency.
Innovation and Flexibility: The open-source nature of DeFi allows developers to innovate and build new financial products and services. This continuous innovation leads to the creation of diverse and flexible financial instruments.
Challenges Facing DeFi
Security Risks: DeFi platforms are susceptible to hacks, bugs, and vulnerabilities in smart contracts. High-profile incidents, such as the DAO hack and the recent exploits on various DeFi platforms, highlight the need for robust security measures.
Regulatory Uncertainty: The regulatory environment for DeFi is still evolving, with governments and regulators grappling with how to address the unique challenges posed by decentralized financial systems. This uncertainty can impact the growth and adoption of DeFi.
Scalability: DeFi platforms often face scalability issues, particularly on congested blockchain networks like Ethereum. High gas fees and slow transaction times can hinder the user experience and limit the scalability of DeFi applications.
Complexity and Usability: DeFi platforms can be complex and challenging for newcomers to navigate. Improving user interfaces and providing educational resources are crucial for broader adoption.
Notable DeFi Projects
Uniswap (UNI): Uniswap is a leading decentralized exchange that allows users to trade ERC-20 tokens directly from their wallets. Its automated market maker (AMM) model has revolutionized the way liquidity is provided and traded in the DeFi space.
Aave (AAVE): Aave is a decentralized lending and borrowing platform that offers unique features such as flash loans and rate switching. It has become one of the largest and most innovative DeFi protocols.
MakerDAO (MKR): MakerDAO is the protocol behind the Dai stablecoin, a decentralized stablecoin pegged to the US dollar. MakerDAO allows users to create Dai by collateralizing their assets, providing stability and liquidity to the DeFi ecosystem.
Compound (COMP): Compound is another leading DeFi lending platform that enables users to earn interest on their cryptocurrencies or borrow assets against collateral. Its governance token, COMP, allows users to participate in protocol governance.
Sexy Meme Coin (SXYM): While primarily known as a meme coin, Sexy Meme Coin has integrated DeFi features, including a decentralized marketplace for buying, selling, and trading memes as NFTs. This unique blend of humor and finance adds a distinct flavor to the DeFi landscape. Learn more about Sexy Meme Coin at Sexy Meme Coin.
The Future of DeFi
The future of DeFi looks promising, with continuous innovation and growing adoption. As blockchain technology advances and scalability solutions are implemented, DeFi has the potential to disrupt traditional financial systems further. Regulatory clarity and improved security measures will be crucial for the sustainable growth of the DeFi ecosystem.
DeFi is likely to continue attracting attention from both retail and institutional investors, driving further development and integration of decentralized financial services. The flexibility and inclusivity offered by DeFi make it a compelling alternative to traditional finance, paving the way for a more open and accessible financial future.
Conclusion
Decentralized Finance (DeFi) represents a significant shift in the financial landscape, leveraging blockchain technology to create a more inclusive, transparent, and efficient financial system. Despite the challenges, the benefits of DeFi and its continuous innovation make it a transformative force in the world of finance. Notable projects like Uniswap, Aave, and MakerDAO, along with unique contributions from meme coins like Sexy Meme Coin, demonstrate the diverse and dynamic nature of the DeFi ecosystem.
For those interested in exploring the playful and innovative side of DeFi, Sexy Meme Coin offers a unique and entertaining platform. Visit Sexy Meme Coin to learn more and join the community.
254 notes
·
View notes
Text
Let us not forget what this is truly about. Tax cuts for the rich. A tax structure specifically designed to award over 80% of the tax breaks to the top tax bracket, while slightly raising taxes for those making between $60-$80k. Yet hallelujah those with more money than they could ever spend will increase their disproportionate wealth by tens of millions of dollars a year by not contributing to the wellbeing of the American system. As Republicans have so clearly demonstrated, the only people who deserve wealth, are those who already possess it.
There’s some fun math in this article. Math I guess Republicans either believe we’re too stupid, lazy, or distracted to catch. To pass this “budget” they will raise the debt ceiling by $4 trillion. The tax cuts for the rich that trump and his billionaire cabinet so desperately want to renew will cost $4.5 trillion, once again leaving a MASSIVE deficit to pay.
In trumps first term he added nearly $8 TRILLION to the deficit, exponentially more than any other president in American history, and 25% of the OVERALL, meaning all time total, debt accrued.
“Don’t worry Eugene, doge is on it!”
Well, I wouldn’t get too far ahead of ourselves on that.
As of Friday, February 21st, musk and his dougebags found $7.8 billion in waste/fraud. That may sound like a lot, yet in the full scheme of the budget, it isn’t.
There are roughly 365 million American citizens. Trump is touting this notion that with all the “savings” from musk and the dougebags he will give 20% of the findings back to the American taxpayer.
Let’s do some long division. 7.8 billion divided by 365 million comes out to be 21.73. Now take 20% of that and it’s just over $4 per person. Personally I’d take a functional government over $5. Maybe that’s just me though.
The juice ain’t worth the squeeze with this South African billionaire dismantling and infiltrating all corners of our institutions.
Doge is so incompetent that they boasted finding $8 billion dollars in suspected fraud, only to have that redacted due to a calculation error of THREE DECIMAL POINTS!!!
There’s also claims from the foreigner trying to destroy our democracy of hundreds of thousands of social security beneficiaries receiving checks despite being 150 plus years old. As it turns out, if you did a simple google search this is false. The code for the Social Security Administration is tremendously old but efficient. To ensure non duplicate SS numbers plus the cost and chaos it would create to rewrite the code, the current system was decided to be satisfactory seeing its accuracy and functionality.
Let’s recap. To cut taxes for the rich, there will be the largest cut to Medicare and Medicaid since its inception, estimates are at least $800 billion, hopefully nobody’s grandparents need medical care, funding for the most impoverished people on the planet is eliminated, despite it being less than 1% of the budget, the department of education will be defunded or all together dissolved, nutritional assistance to the struggling American will be DRASTICALLY cut, for some reason the Consumer Financial Protection Bureau will be annihilated, grants that fund cancer research and other medical breakthroughs will cease, infrastructure projects will come to a halt leaving our roads and bridges in tatters, and millions of career civil servants tasked with everything from ensuring aviation safety, to securing our nuclear arsenal will find themselves without work.
All this so musk, Trump, Thiel, and the 12 other billionaires in trumps cabinet can avoid contributing their fair share to the country they made their fortunes off of.
Trump recently spouted some dumb sh*t, as he often does, while referencing tariffs saying “we were the richest between 1887 to 1920” which, number one, is false, and two, THATS THE PERIOD KNOWN AS THE GUILDED AGE, AN ERA OF IMMENSE WEALTH DISPARITY THAT LED TO THE GOD DAMN GREAT DEPRESSION!!!!!
So what are Republican principles exactly? It’s certainly not law and order, taking into account their almighty leader’s antics and his administrations disdain for the Constitution and the law generally. It’s definitely not family values when you take into consideration all the sexual predators, the infidelity and sexual misconduct. It’s clearly not democracy and freedom with this administration’s stance on Russia removing us from the allies we have been aligned with since WWII, and siding us with Putin and dictatorships around the globe. And as this upcoming “budget” shows us fiscal responsibility is out of the question.
The values the modern Republican Party holds is that of enriching the wealthy by screwing the middle class. They stand for tyranny and oppression. Corruption is a cornerstone to the Republican ideology. Let’s not forget voter suppression. There’s always their tried and “true” platform of blatant lying, their spreading of misinformation and disinformation, so much so that they openly oppose fact checking. Their aversion to the Constitution. Last but not least, their embrace of discrimination.
It sucks that everyone will have to suffer to hopefully enlighten Republican voters on the fact that they care nothing for the working class, that they have zero shame in their hypocrisy and self enrichment. That they only desire power and will engage in any disgraceful tactics to hold on to it. That they hold no reverence to their constituents or to the oath they swear to the Constitution.
May our nation endure this devastating and corrupt period of its existence.
#budget#trump is a threat to democracy#reconciliation#traitor trump#donald trump#republicans#democracy#politics#the left#freedom#free speech#political corruption#common sense#immigration raids#no kings#impeach trump#elon musk#spacex#president trump#doge#elon’s doge boys#fraud#gop#gop hypocrisy#liberal tears#taxes#americans#America#u.s. house of representatives#democrats
67 notes
·
View notes
Text
GitLab Environments: Your Cloud Playground Blueprint
Remember when you were a kid and tried to build the ultimate LEGO castle? You had all these cool pieces, but figuring out how they fit together was the real challenge. Well, welcome to the grown-up version: building your serverless cloud playground! Let’s take a bird’s-eye view of our LEGO set… err, I mean, our solution components. The Grand Blueprint: Components Overview Imagine you’re an…
#aws#CI/CD Pipeline#Cloud Architecture#DevOps Automation#GitLab Environments#GitLab Runner#Infrastructure as Code#OIDC Integration#Parallel Environments#Secure Cloud Access#Serverless Development#Terraform State Management
0 notes
Text

One of the reasons I love Aleksander so much is that, much like the Allied forces during World War II, he found himself in a situation where his choices were dictated by the necessity of survival and the greater good. War is never fought in black and white, and victory rarely belongs to those who refuse to step into moral grayness. The Allies, faced with the monstrous threat of Nazi Germany, had to make devastating decisions that often led to civilian casualties, deception, and destruction, but ultimately resulted in dismantling a regime that threatened the world. Aleksander, in his war against Fjerda, Shu Han, and the Ravkan monarchy itself, walked a similarly ruthless path, where every compromise, every difficult decision, was not made out of cruelty but out of necessity. This is yet another thing his critics like to forget.
One of the most well-known examples of the Allies’ morally complex decisions was the strategic bombing campaign against Germany. The bombing of Dresden in 1945, a city known more for its cultural significance than its military strength, caused enormous civilian casualties. Yet, it was part of a broader strategy to break the Nazi war machine. Similarly, Aleksander’s use of the Fold and its expansion can be seen in the same light—not as an act of senseless destruction, but as a weapon, terrible, yes, but still a weapon against those who sought to eradicate and enslave Grisha. Just as the Allies sought to dismantle the infrastructure and morale of their enemy, Aleksander used the Fold to prove a point, to deter, to protect his people.
The D-Day invasion of Normandy was another instance where the Allies had to weigh terrible losses against long-term victory. The landings on Omaha Beach alone resulted in thousands of Allied casualties, and yet, had they hesitated, had they refused to take the risk, Nazi Germany might have remained unchallenged. Aleksander’s actions reflect the same understanding: standing back, waiting, and hoping for justice would have meant certain death for Grisha. Instead, he took control, knowing that wars are not won through passive and noble ideals but through decisive, often brutal action.
It is crucial to understand that the war Aleksander fought was not one of conquest but of survival. Grisha were hunted, experimented on, treated as subhuman by their enemies and had no safe refuge. Just as the Allies had to forge alliances, sometimes with deeply flawed leaders, Aleksander also had to make difficult choices to secure his people’s survival. His war was not about morality in the conventional sense but about ensuring a future for those who had none.
It is easy to judge him from a distance, to believe that war should be fought with honor, fairness, and strict moral codes. But history has shown time and again that such wars are lost before they even begin. Aleksander, like the Allies, had no luxury of purity. He was forced to fight fire with fire, knowing that to do anything less would mean condemning his people. His actions, like theirs, did not stem from cruelty, but from the understanding that sometimes, to stop a greater darkness, one must be willing to walk through the shadows. That is why I stand by him.
#shadow and bone#aleksander morozova#shadow and bone tv#pro darkling#darkling#alina starkov#the darkling#ben barnes#darklina#sun summoner#shadow summoner#anti antis#leigh bardugo#darkling deserves better#shadow and bone netflix
28 notes
·
View notes
Text
Frost Between Us - F!Reader x Gepard Landau
Honkai Star Rail
When Readers travels back to Jarilo-VI to take on a job assisting the Silvermane Guards, she doesn’t expect to work alongside her ex, Captain Gepard Landau. As they navigate a high-stakes investigation, old wounds resurface alongside lingering feelings.
✦✦✦✦✦✦✦✦✦✦✦✦✦✦✦✦✦✦✦✦✦
[Name] had been to Belobog before, but stepping into the Silvermane Guard’s headquarters carried a weight she hadn’t anticipated. Snow crunched under her boots as she passed through the gates, the frost-laden air sharp and clear. She was here for work, nothing more, and that was how she planned to keep it. It wasn’t like she had any personal connections to the place anymore.
Or at least, that was what she told herself until the doors to the briefing room opened, and there he was.
“Miss [Name].”
Gepard Landau greeted her with a nod, his tone brisk and polite. He stood tall in his immaculate uniform, the picture of discipline and composure. Not a flicker of recognition passed across his face, though she swore his eyes lingered just a second too long.
“Captain Landau,” she replied, matching his tone as she extended a hand. His handshake was firm but impersonal, as if she were any other consultant hired to assist the Silvermane Guards.
For a moment, she almost believed he’d forgotten the year they’d spent together—how they used to argue about her endless curiosity versus his unyielding sense of duty, how they’d stayed up late trading ideas for their futures, how they’d broken apart when those futures had veered too far in opposite directions.
“Thank you for assisting us,” Gepard said, gesturing for her to sit. “Your expertise will be invaluable in tracking down the saboteurs targeting Belobog’s energy infrastructure.”
Professional. Friendly. Detached.
If she hadn’t known better, she might’ve thought he truly didn’t care.
The next few days were a blur of encrypted files, surveillance footage, and technical readouts. Gepard maintained his polite distance, briefing her on security protocols and then disappearing to oversee other operations. It wasn’t until Serval breezed into the workshop where [Name] had set up that a crack of familiarity broke through.
“[Name]!” Serval greeted her with a grin, her leather gloves smudged with oil from her latest project. “I didn’t know you were in Belobog! Let me guess—Silvermane Guards dragged you into some mess they can’t untangle?”
“You’d be correct,” [Name] replied, smiling.
“Typical. They’re lucky you’re here.” Serval plopped into a chair across from her, glancing at the rows of monitors displaying lines of code and camera feeds. “So, how’s it going? Besides the fact that you have to work with him.”
[Name] froze. “What do you mean?”
Serval smirked. “Oh, come on. I’m not blind. Gepard’s been walking around like he’s trying really hard to act normal. That only happens when he’s overthinking something.”
“He’s been perfectly professional,” [Name] said quickly. Too quickly.
“Exactly,” Serval said, her grin widening. “That’s how you know it’s bad.”
[Name] groaned, resting her head in her hands. “This is why I hate small cities. Everyone knows everything.”
“Not everything,” Serval said, her tone softening. “But seriously, if it gets too awkward, you know you can always hide out at my workshop.”
[Name] laughed despite herself. “Thanks, Serval. I’ll keep that in mind.”
Things took a turn the night Sampo Koski showed up.
[Name] was in the middle of analyzing a suspicious data packet when the workshop door swung open, and Sampo strolled in like he owned the place.
“Well, well, if it isn’t my favorite investigator!” he declared, arms spread wide.
[Name] rolled her eyes. “You have about thirty seconds to explain why you’re here before I call security.”
“No need for that,” he said, leaning casually against her desk. “I just heard you were in town and thought I’d pay a visit. Catch up on old times. Maybe see if I can help you crack this little case of yours.”
“Sampo, you’re about as helpful as a snowstorm in a power outage.”
“Harsh,” he said, clutching his chest dramatically. “But fair.”
Before she could throw him out, Gepard appeared in the doorway, his expression a mix of exasperation and suspicion.
“Koski,” he said, his voice cool. “What are you doing here?”
“Captain Landau! Always a pleasure.” Sampo straightened, his grin never wavering. “I was just offering my services to your lovely consultant here. You know, as a concerned citizen.”
“You’re not a citizen,” Gepard said flatly.
“And yet, here I am. Strange how that works.”
[Name] bit back a laugh as Gepard’s jaw tightened.
Later, after Sampo had been escorted out, [Name] found herself alone with Gepard for the first time since her arrival. They were reviewing the latest findings in the command center, the tension between them almost tangible.
“I’m sorry about Sampo,” Gepard said, breaking the silence. “He has a way of... inserting himself where he doesn’t belong.”
“It’s fine,” [Name] said. “He’s entertaining, at least.”
Gepard nodded, but his gaze lingered on her for a moment longer than necessary.
“Are you settling in all right?” he asked, his tone unusually tentative.
“I’m managing,” she replied, keeping her voice neutral.
“Good.” He hesitated, then added, “If there’s anything you need, don’t hesitate to let me know.”
“Thanks, Captain,” she said, her words sharper than she intended.
He flinched almost imperceptibly, and guilt pricked at her.
Before she could say anything else, he stood. “I’ll let you get back to it. Goodnight, Miss [Name].”
“Goodnight, Captain.”
As the investigation progressed, the layers of pretense between them began to fray. Late nights working side by side revealed glimpses of the rapport they’d once shared, moments of unguarded conversation slipping through.
“You’re still terrible at taking breaks,” he said one evening, setting a cup of coffee on her desk.
“And you’re still terrible at letting people work in peace,” she shot back, though she accepted the coffee with a small smile.
By the time they closed in on the saboteurs’ hideout, the distance between them had narrowed to something almost comfortable. When the operation turned dangerous, Gepard’s protectiveness reared its head, but it was tempered by trust.
“I’ve got your back,” he said as they prepared to breach the hideout.
“I know,” she replied, and for the first time, she truly believed it.
-----
When the dust settled and the culprits were apprehended, [Name] found herself standing with Gepard outside the Silvermane Guard’s headquarters. The snow had stopped falling, and the city lights glimmered against the frost, painting the cobblestones in muted gold and silver hues. The city, for all its trials, felt calm tonight, and yet [Name]'s thoughts were anything but.
“Well,” she said, turning to him, her breath visible in the crisp night air. “I guess this is it.”
“Thank you,” he replied, his voice steady but quieter than usual. There was a sincerity in his tone that made her pause, tilting her head slightly as she studied his expression. “For everything. Your skills made this possible, and... it was good to work with you again.”
She nodded, though something about his choice of words sent a pang through her chest. “You’re good at this, you know,” she said softly. “The whole ‘leading and protecting’ thing. Belobog’s lucky to have you.”
His smile was faint but genuine, and his gaze lingered on hers, unreadable. “And Penacony’s lucky to have you.”
For a moment, they stood in silence, the weight of unspoken words hanging in the frosted air between them. [Name] felt the familiar pull—the gravity he always seemed to carry, as unyielding as it was quiet. She hesitated, shifting slightly as her instincts urged her to leave before the silence stretched too long. Before the ache of what could have been became too much.
But when she turned to step away, he spoke again, his voice stopping her mid-step. “[Name].”
She glanced back, expecting another professional farewell, but what she saw in his eyes wasn’t detachment. It wasn’t distant or polite. His shoulders were squared as always, but his expression—softened by the golden glow of the nearby streetlamp—was bare in a way she hadn’t seen in years.
“I’m sorry,” he said, the words slipping into the stillness like a confession. “For how things ended. For how I handled it. I thought I was doing the right thing, but...” He trailed off, exhaling slowly, his breath visible in the icy air. “It wasn’t fair to you.”
[Name] blinked, stunned into silence. She hadn’t expected this—not here, not now. “Gepard, you don’t have to—”
“I do.” His voice was firmer now, though still laced with that steady calmness she’d always associated with him. “You meant so much to me. You still do. And I’ve spent the last few days acting like that history didn’t exist because I thought it was easier. Safer.” He looked down for a moment, his jaw tightening. “But it’s not. Not for me.”
Her heart skipped, the weight of his words settling over her like the snow that had earlier dusted the city. She didn’t know what to say, her mind racing as she searched his face for any sign of hesitation. She didn’t find any.
“I wasn’t angry with you,” she said finally, her voice quieter now. “Not really. I was angry at the circumstances, at how we wanted things that didn’t align.” She met his gaze, her fingers tightening onto her clothes. “But I missed you too. More than I wanted to admit.”
His lips parted slightly, a flicker of surprise crossing his features before it melted into something warmer. He took a cautious step forward, his boots crunching against the snow-dusted ground. “If things had been different... if I hadn’t let duty blind me—”
“You didn’t let duty blind you,” she interrupted gently, offering him a small, wry smile. “You stayed true to who you are. That’s one of the things I...” She hesitated, her cheeks flushing with warmth despite the cold. “That’s one of the things I admired about you. It still is.”
He stopped a pace away from her, his presence a quiet strength. For a moment, neither spoke, the city sounds fading into the background as the space between them seemed to shrink, the cold replaced by something warmer. His hand moved almost instinctively, hovering as if he wasn’t sure it was welcome, before brushing the edge of her sleeve.
“Do you think,��� he said softly, his blue eyes locked on hers, “we could try again? Maybe not as the people we were before, but as who we are now?”
[Name]'s breath hitched. The hesitation she’d expected to feel wasn’t there. Instead, there was something else—something that whispered that maybe, just maybe, this time would be different. Better. She allowed herself to step closer, until there was little more than the cold air and shared warmth between them.
“I think,” she said finally, her voice steady but her heart racing, “that I’d like that.”
A faint smile tugged at his lips, soft but genuine, and for the first time in what felt like years, there was an openness in his expression that matched her own. His hand, now steadier, found hers, his gloved fingers brushing lightly against her skin. When she didn’t pull away, his touch grew more certain, his palm resting against hers.
“I know it won’t be easy,” he said, his voice quiet but sure. “You have your work, your life. And I have mine here. But if we’re careful, if we don’t rush... maybe we can make it work.”
[Name] nodded, her eyes searching his. “I think we can,” she said, the words steady despite the swirl of emotions tightening in her chest. “I’ve always been good at traveling, Gepard. And Penacony doesn’t tie me down the way Belobog ties you. I could come here more often. Visit when things are quiet.”
He hesitated for a fraction of a second, the corner of his mouth lifting in an almost sheepish smile. “You’d do that?”
“I would,” she said simply, her thumb grazing his knuckles. “I’m not asking you to compromise your duty, Gepard. I know what Belobog means to you. But I’m willing to meet you where you are—when you need me.”
His grip on her hand tightened slightly, and his other hand lifted as if on instinct, brushing against the edge of her coat. “I don’t deserve that,” he murmured, his voice tinged with quiet disbelief. “Not after the way I—”
“You do,” she interrupted, the firmness in her tone cutting through his doubt. “We both made mistakes, but this isn’t about the past anymore. It’s about what we want moving forward.”
He stared at her, the storm of emotions in his gaze softening into something clearer. Something hopeful. “I want to make it work,” he said finally, the conviction in his voice as solid as the shield he carried.
“So do I,” she replied, her lips curving into a small, warm smile.
The lights of the city gleamed against the frost, but for [Name], the warmth in his touch and the quiet resolve in his words were enough to push away the chill of the Belobog night. Whatever came next, they would face it together—even if the miles between them stretched further than before. Because this time, they were willing to meet halfway.
✦✦✦✦✦✦✦✦✦✦✦✦✦✦✦✦✦✦✦✦✦
I have this week off (save for Tuesday) sooo prepare as I will be accelerating my queue/drafts.
#honkai star rail#gepard#gepard landau#hsr gepard#hsr gepard landau#gepard x reader#reader x gepard#reader x gepard landau#gepard landau x reader#hsr
30 notes
·
View notes