#Secure Business Data Backup
Explore tagged Tumblr posts
Text
Safeguard Your Data with Esconet’s Advanced Backup Systems
Looking for reliable and scalable data backup solutions? Esconet Technologies Ltd., based in New Delhi, delivers robust and customized enterprise data protection services, securing business-critical information across on-premise, cloud, and hybrid environments.
With features like deduplication, ransomware-resilient storage, high-speed WAN backups, and application-aware protection, Esconet ensures rapid recovery and business continuity.
From legacy LTO backups to cloud-integrated systems, Esconet’s expert team supports you with seamless implementation and 24x7 support. Their solutions are compatible with leading platforms including Dell, HPE, and Veeam.
Learn more about how Esconet can protect your business data: Esconet Data Backup Page
#Data Backup India#Enterprise Data Protection#Ransomware Backup Solutions#Hybrid Cloud Backup Services#LTO Tape Backup#Esconet Technologies Ltd.#New Delhi IT Solutions#Instant Restore Backup#Secure Business Data Backup#Application-Aware Backup India
0 notes
Text
Sigzen Technologies: Transforming Challenges into Opportunities with Robust Backup and Disaster Recovery Solutions
In today’s fast-paced digital world, where data plays a crucial role in business operations, having a reliable Backup Solution and Disaster Recovery plan is paramount. Sigzen Technologies emerges as a leader in this space, offering cutting-edge solutions that not only safeguard critical data but also transform challenges into opportunities for businesses. Automated Backup An automated backup…

View On WordPress
#Business Continuity Strategies#Cloud Backup Excellence#Data Protection Standards#Data Security Leaders#Sigzen Tech Solutions
2 notes
·
View notes
Text
Discover the key features and benefits of eShare.ai’s cloud storage solution. From seamless file sharing and real-time collaboration to top-tier data encryption and unlimited storage, eShare.ai empowers individuals and businesses to organize, protect, and access their data anytime, anywhere. Go paperless, boost productivity, and simplify your workflow with a platform designed for modern digital needs.
#eShare.ai#cloud storage#file sharing#digital organization#online collaboration#secure storage#paperless office#cloud backup#unlimited storage#business productivity#file sync#SaaS platform#data access anywhere#digital workspace
0 notes
Text
Is Your Data Storage Strategy AI-Ready?
New Post has been published on https://thedigitalinsider.com/is-your-data-storage-strategy-ai-ready/
Is Your Data Storage Strategy AI-Ready?


The adoption of AI has caused an increased need for proper data governance, and companies are now under pressure to ensure data maturity. Globally, many companies are either using or exploring AI, with over 82% actively leveraging or considering AI for business operations. Yet, according to Gartner only 14% of cyber leaders can balance maximizing the efficient use of their data and securing their data to hit business objectives.
As more businesses rush to utilize AI, they need to ensure they are operating at peak data maturity with a proper framework to handle the increasing amount of critical data they are managing. By leveraging a data maturity model framework, organizations can identify the most effective ways to optimize data usage, helping pinpoint gaps in security and foster greater data efficiency. As part of this framework, organizations also need a mature data management strategy.
One of the most overlooked parts of a mature data management strategy is having the proper storage requirements to backup and store critical data. Businesses face many threats when it comes to their data security, and proper storage to handle AI workloads may be the only way to prevent AI-generated data from being lost or tampered with due to ransomware or another disaster. Your business may be AI-capable, but is your storage infrastructure AI-ready?
Why Storage Has to Be Involved in the AI Conversation
There are several reasons why proper storage is essential for data created and consumed by AI— businesses need to ensure data remains easily accessible, is secure against evolving threats, can be recovered in the case of a disaster, and must be optimized for AI workloads.
Accessibility is important because developers must be able to quickly and efficiently find and leverage data to train other AI algorithms. Most of the time this type of data is considered “mission critical” and can be the most valuable to business operations. Having this type of data readily available is key to ensuring streamlined processes when it matters most.
This data also needs to have the highest level of security while it is being stored. Given that 96% of ransomware attacks now target backup data, storage needs to be ransomware-proof and able to withstand any downtime or outage an organization may face. Backups are primary targets for attackers because they render companies unable to restore their data, making it more likely that they will pay the ransom to retrieve critical data. In the meantime, businesses could be left defenseless and face extended periods of IT outages if their “mission-critical” data is not accessible. This could cause both reputational and monetary loss that would be devastating for shareholders, customers, and employees alike.
Cybersecurity attacks are not the only reason storage may be lost or manipulated. Production data, or the data used in a business’s daily operations, should always be treated as though it was destroyed or corrupted. Therefore, a golden recovery copy, or a clean, reliable, and isolated copy of critical data is mandatory. Accidental deletion, overwriting data, or any other kind of mistake caused by human error can compromise your data. Software and hardware failures such as corruption or viruses can also put your data at risk, especially if your software and hardware do not have the most recent updates. Lastly, environmental factors such as power outages, floods, and extreme weather are all good reasons to ensure your backup data can be recovered.
What’s more, AI tools can produce an excessive amount of data at an exponential rate, and traditional storage architectures may not be able to keep up with the amount of data needed to be stored. Therefore, storage for AI must be equipped to handle massive workloads efficiently. Using scalable and secure data storage, such as tiered storage solutions, will present optimal capabilities so data is being monitored and saved.
The Best Storage of AI Data (Without Breaking the Bank)
Tiered backup storage ensures that vital data is quickly accessible and is one of the most cost-effective solutions. It allows for data retention, permitting data to be accessed and reused at any time. Tiered storage and backups organize data based on its importance and frequency of access. High-priority data goes on fast, expensive storage like SSDs, while less critical data is stored on cheaper, slower media like HDDs or cloud storage. Specifically, AI data should be stored on tier 0 or tier 1 given the above requirements. Tier 0 is high-speed storage for mission-critical data with NVMe media types and all-flash storage arrays. Tier 1 is high-performance storage for frequently accessed data with SSDs and hybrid Flash storage media types.
Taking it a step further, backing up the data housed in tiered storage as often as possible will allow for quick access in the face of a disaster, such as human error or malicious alteration. Ensuring copies of backup data stored in multiple locations, with several types of encryptions, and on various media types is the only way to be sure backups are secure.
When choosing a ransomware-proof backup and storage vendor, it is important to ensure you are selecting immutable storage that can withstand any kind of disaster that could put your data at risk. It’s important to note that not all immutable storage delivers on this agreement. If ‘immutable’ data can be overwritten by a backup or storage admin, a vendor, or an attacker, then it is NOT a truly immutable storage solution. Understanding the core concept of true immutability will help separate secure backup systems from empty vendor claims.
These five requirements help define a backup storage environment that delivers immutability:
S3 Object Storage: A fully documented, open standard with native immutability that enables independent penetration testing
Zero Time to Immutability: Backup data must be immutable the moment it is written
Zero Access to Destructive Actions: No administrator—internal or external—should be able to modify, delete, or reset immutable data.
Segmentation of Backup Software and Storage: Backup software and backup storage must be physically isolated to prevent compromised credentials from being used to alter or destroy data, and to provide resilience against other disasters.
Hardware Form Factor: A dedicated appliance isolates immutable storage from virtualized attack surfaces and should remove all risks during setup, updates, and maintenance.
By meeting these requirements, organizations can assure immutability and thereby ensure that whatever happens—ransomware, insider threats, or credential breaches—backup data remains protected and recoverable.
As AI becomes a consistent tool for businesses, they need to adopt and identify better data management and infrastructure to ensure data maturity. The answer to this may lie in tiered storage and backups as the best way to secure the excessive amounts of data created and trained by AI and allow for the ability to quickly access and secure this critical and expansive data.
#Accessibility#admin#adoption#agreement#ai#AI data governance#ai tools#Algorithms#Arrays#attackers#backup#backups#bank#Business#Cloud#cloud storage#Companies#compromise#credential#credentials#cyber#cybersecurity#data#Data Governance#Data Management#data security#data storage#data usage#delete#developers
0 notes
Text
Learn effective Salesforce backup strategies to protect your business data and ensure seamless recovery in case of data loss.
#Salesforce backup#data recovery guide#Salesforce strategies#secure business data#Salesforce data protection
0 notes
Text
Apple's encryption capitulation

I'm on a 20+ city book tour for my new novel PICKS AND SHOVELS. Catch me in NYC on TOMORROW (26 Feb) with JOHN HODGMAN and at PENN STATE THURSDAY (Feb 27). More tour dates here. Mail-order signed copies from LA's Diesel Books.

The UK government has just ordered Apple to secretly compromise its security for every iOS user in the world. Instead, Apple announced it will disable a vital security feature for every UK user. This is a terrible outcome, but it just might be the best one, given the circumstances:
https://www.bbc.com/news/articles/cgj54eq4vejo
So let's talk about those circumstances. In 2016, Theresa May's Conservative government passed a law called the "Investigative Powers Act," better known as the "Snooper's Charter":
https://www.snooperscharter.co.uk/
This was a hugely controversial law for many reasons, but most prominent was that it allowed British spy agencies to order tech companies to secretly modify their software to facilitate surveillance. This is alarming in several ways. First, it's hard enough to implement an encryption system without making subtle errors that adversaries can exploit.
Tiny mistakes in encryption systems are leveraged by criminals, foreign spies, griefers, and other bad actors to steal money, lock up our businesses and governments with ransomware, take our data, our intimate images, our health records and worse. The world is already awash in cyberweapons that terrible governments and corporations use to target their adversaries, such as the NSO Group malware that the Saudis used to hack Whatsapp, which let them lure Jamal Khashoggi to his death. The stakes couldn't be higher:
https://pluralistic.net/2025/02/04/citizen-lab/#nso-group
Encryption protects everything from the software updates for pacemakers and anti-lock braking to population-scale financial transactions and patient records. Deliberately introducing bugs into these systems to allow spies and cops to "break" encryption when they need to is impossible, which doesn't stop governments from demanding it. Notoriously, when former Australian PM Malcolm Turnbull was told that the laws of mathematics decreed that there is no way to make encryption that only stops bad guys but lets in good guys, he replied "The laws of mathematics are very commendable but the only law that applies in Australia is the law of Australia":
https://www.eff.org/deeplinks/2017/07/australian-pm-calls-end-end-encryption-ban-says-laws-mathematics-dont-apply-down
The risks don't stop with bad actors leveraging new bugs introduced when the "lawful interception" back-doors are inserted. The keys that open these back-doors inevitably circulate widely within spy and police agencies, and eventually – inevitably – they leak. This is called the "keys under doormats" problem: if the police order tech companies to hide the keys to access billions of peoples' data under their doormats, eventually, bad guys will find them there:
https://academic.oup.com/cybersecurity/article/1/1/69/2367066
Again, this isn't a theoretical risk. In 1994, Bill Clinton signed a US law called CALEA that required FBI back-doors for data switches. Most network switches in use today have CALEA back-doors and they have been widely exploited by various bad guys. Most recently, the Chinese military used CALEA backdoors to hack Verizon, AT&T and Lumen:
https://pluralistic.net/2024/10/07/foreseeable-outcomes/#calea
This is the backdrop against which the Snooper's Charter was passed. Parliament stuck its fingers in its ears, covered its eyes, and voted for the damned thing, swearing that it would never result in any of the eminently foreseeable harms they'd been warned of.
Which brings us to today. Two weeks ago, the Washington Post's Joseph Menn broke the story that Apple had received a secret order from the British government, demanding that they install a back-door in the encryption system that protects cloud backups of iOS devices:
https://www.washingtonpost.com/technology/2025/02/07/apple-encryption-backdoor-uk/
Virtually every iOS device in the world regularly backs itself up to Apple's cloud backup service. This is very useful: if your phone or tablet is lost, stolen or damaged, you can recover your backup to a new device in a matter of minutes and get on with your day. It's also very lucrative for Apple, which charges every iOS user a few dollars every month for backup services. The dollar amount here is small, but that sum is multiplied by the very large number of Apple devices, and it rolls in every single month.
Since 2022, Apple has offered its users a feature called "Advanced Data Protection" that employs "end-to-end" encryption (E2EE) for these backups. End-to-end encryption keeps data encrypted between the sender and the receiver, so that the service provider can't see what they're saying to each other. In the case of iCloud backups, this means that while an Apple customer can decrypt their backup data when they access it in the cloud, Apple itself cannot. All Apple can see is that there is an impenetrable blob of user data on one of its servers.
2022 was very late for Apple to have added E2EE to its cloud backups. After all, in 2014, Apple customers suffered a massive iCloud breach when hackers broke into the iCloud backups of hundreds of celebrities, leaking nude photos and other private data, in a breach colloquially called "Celebgate" or "The Fappening":
https://en.wikipedia.org/wiki/2014_celebrity_nude_photo_leak
Apple almost rolled out E2EE for iCloud in 2018, but scrapped the plans after Donald Trump's FBI leaned on them:
https://www.reuters.com/article/world/exclusive-apple-dropped-plan-for-encrypting-backups-after-fbi-complained-sour-idUSKBN1ZK1CO/
Better late than never. For three years, Apple customers' backups have been encrypted, at rest, on Apple's servers, their contents fully opaque to everyone except the devices' owners. Enter His Majesty's Government, clutching the Snooper's Charter. As the eminent cryptographer Matthew Green writes, a secret order to compromise the cloud backups of British users is necessarily a secret order to compromise all users' encrypted backups:
https://blog.cryptographyengineering.com/2025/02/23/three-questions-about-apple-encryption-and-the-u-k/
There's no way to roll out a compromised system in the UK that differs from non-British backups without the legion of reverse-engineers and security analysts noticing that something new is happening in Britain and correctly inferring that Apple has been served with a secret "Technical Capability Notice" under the Snooper's Charter:
Even if you imagine that Apple is only being asked only to target users in the U.K., the company would either need to build this capability globally, or it would need to deploy a new version or “zone”1 for U.K. users that would work differently from the version for, say, U.S. users. From a technical perspective, this would be tantamount to admitting that the U.K.’s version is somehow operationally distinct from the U.S. version. That would invite reverse-engineers to ask very pointed questions and the secret would almost certainly be out.
For Apple, the only winning move was not to play. Rather than breaking the security for its iCloud backups worldwide, it simply promised to turn off all security for backups in the UK. If they go through with it, every British iOS user – doctors, lawyers, small and large business, and individuals – will be exposed to incalculable risk from spies and criminals, both organized and petty.
For Green, this is Apple making the best of an impossible conundrum. Apple does have a long and proud history of standing up to governmental demands to compromise its users. Most notably, the FBI ordered Apple to push an encryption-removing update to its phones in 2016, to help it gain access to a device recovered from the bodies of the San Bernardino shooters:
https://www.eff.org/deeplinks/2016/02/eff-support-apple-encryption-battle
But it's worth zooming out here for a moment and considering all the things that led up to Apple facing this demand. By design, Apple's iOS platform blocks users from installing software unless Apple approves it and lists it in the App Store. Apple uses legal protections (such as Section 1201 of the US Digital Millennium Copyright Act and Article 6 of the EUCD, which the UK adopted in 2003 through the Copyright and Related Rights Regulations) to make it a jailable offense to reverse-engineer and bypass these blocks. They also devote substantial technical effort to preventing third parties from reverse-engineering its software and hardware locks. Installing software forbidden by Apple on your own iPhone is thus both illegal and very, very hard.
This means that if Apple removes an app from its App Store, its customers can no longer get that app. When Apple launched this system, they were warned – by the same cohort of experts who warned the UK government about the risks of the Snooper's Charter – that it would turn into an attractive nuisance. If a corporation has the power to compromise billions of users' devices, governments will inevitably order that corporation to do so.
Which is exactly what happened. Apple has already removed all working privacy tools for its Chinese users, purging the Chinese App Store of secure VPN apps, compromising its Chinese cloud backups, and downgrading its Airdrop file-transfer software to help the Chinese state crack down on protesters:
https://pluralistic.net/2022/11/11/foreseeable-consequences/#airdropped
These are the absolutely foreseeable – and foreseen – outcomes of Apple arrogating total remote control over its customers' devices to itself. If we're going to fault Theresa May's Conservatives for refusing to heed the warnings of the risks introduced by the Snooper's Charter, we should be every bit as critical of Apple for chasing profits at the expense of billions of its customers in the face of warnings that its "curated computing" model would inevitably give rise to the Snooper's Charter and laws like it.
As Pavel Chekov famously wrote: "a phaser on the bridge in act one will always go off by act three." Apple set itself up with the power to override its customers' decisions about the devices it sells them, and then that power was abused in a hundred ways, large and small:
https://pluralistic.net/2023/09/22/vin-locking/#thought-differently
Of course, there are plenty of third-party apps in the App Store that allow you to make an end-to-end encrypted backup to non-Apple cloud servers, and Apple's onerous App Store payment policies mean that they get to cream off 30% of every dollar you spend with its rivals:
https://www.reddit.com/r/privacy/comments/1iv072y/endtoend_encrypted_alternative_to_icloud_drive/
It's entirely possible to find an end-to-end encrypted backup provider that has no presence in the UK and can tell the UK government to fuck off with its ridiculous back-door demands. For example, Signal has repeatedly promised to pull its personnel and assets out of the UK before it would compromise its encryption:
https://pluralistic.net/2023/03/05/theyre-still-trying-to-ban-cryptography/
But even if the company that provides your backup is impervious to pressure from HMG, Apple isn't. Apple has the absolute, unchallenged power to decide which apps are in its App Store. Apple has a long history of nuking privacy-preserving and privacy-enhancing apps from its App Store in response to complaints, even petty ones from rival companies like Meta:
https://www.theverge.com/2022/9/29/23378541/the-og-app-instagram-clone-pulled-from-app-store
If they're going to cave into Zuck's demand to facilitate spying on Instagram users, do we really think they'll resist Kier Starmer's demands to remove Signal – and any other app that stands up to the Snooper's Charter – from the App Store?
It goes without saying that the "bad guys" the UK government claims it wants to target will be able to communicate in secret no matter what Apple does here. They can just use an Android phone and sideload a secure messaging app, or register an iPhone in Ireland or any other country and bring it to the UK. The only people who will be harmed by the combination of the British government's reckless disregard for security, and Apple's designs that trade the security of its users for the security of its shareholders are millions of law-abiding Britons, whose most sensitive data will be up for grabs by anyone who hacks their accounts.

If you'd like an essay-formatted version of this post to read or share, here's a link to it on pluralistic.net, my surveillance-free, ad-free, tracker-free blog:
https://pluralistic.net/2025/02/25/sneak-and-peek/#pavel-chekov

Image: Mitch Barrie (modified) https://commons.wikimedia.org/wiki/File:Daytona_Skeleton_AR-15_completed_rifle_%2817551907724%29.jpg
CC BY-SA 2.0 https://creativecommons.org/licenses/by-sa/2.0/deed.en
--
Kambanji https://www.flickr.com/photos/kambanji/4135216486/
CC BY 2.0 https://creativecommons.org/licenses/by/2.0/
--
Rawpixel https://www.rawpixel.com/image/12438797/png-white-background
#pluralistic#apple#encryption#crypto wars#crypto means cryptography#icloud#lawful access#uk#ukpoli#snoopers charter#matthew green#lawful interception#Investigatory Powers Act#sneak and peek orders#checkovs law#privacy
163 notes
·
View notes
Text
The Making of a Villian - Chapter 1
The WayneTech board meeting was scheduled for 9:00 a.m.
By 9:03, their encrypted systems were silently bleeding data into a private offshore server. No alarms. No alerts. Just a quiet, surgical extraction—clean, undetectable, and irreversible.
You watched from a dusty rooftop across the street, sipping coffee like any civilian on a break. Except your hands weren’t shaking, and your eyes never left the mirrored windows reflecting a city that forgot you.
It wasn’t about the files. Not really. You’d already read them—twice—before deleting the backups. What mattered was what came next: one carefully altered blueprint. A subtle change in the emergency lockdown protocols, buried deep in the code. Harmless… until the moment someone needed them most.
You didn’t need chaos. Not yet.
You needed doubt.
Down below, Bruce Wayne’s car pulled into the underground garage. Right on schedule. You watched as security greeted him with smiles and clipped nods.
They didn’t know.
No one ever did—until it was too late.
You slipped the burner phone back into your pocket and turned away from the skyline. One step. Then another. Quiet boots on concrete. No capes. No flashy suits. Just a face they’d stopped looking at long ago.
But you were done being invisible.
Your game had just begun.
It hadn’t always been like this. You remembered your first week training with them. You’d shown up early—excited, eager to learn. Tim had offered a nod. Dick had smiled. Barbara barely looked up from her console.
You thought they were just busy. That maybe, in time, you’d earn your place. That if you just proved yourself…
And you did. Over and over again.
Yet somehow, you were always the footnote. The cautionary tale. “Don’t be like them,” Bruce had once said to Damian during a sparring match. You’d laughed it off then. Told yourself he meant your form. Not you.
You knew better now.
You remembered a moment not long ago: standing in the Batcave, trying to offer insight into an unfolding hostage situation. You had mapped out a possible escape route—one they didn’t see. You weren’t loud. You didn’t shout over anyone. You just slid the schematic across the table. Bruce didn’t even glance at it. Tim talked over you. And when the building collapsed—when things went wrong—no one asked why.
Just a quiet, disappointed look. A cold shoulder. Another mark against your record.
You weren’t angry anymore. Not really.
Just focused.
You stepped onto the street and vanished into the crowd. No one looked twice.
Perfect.
They wanted a ghost. They’ll get one.
But not the kind they can exorcise. Not a whisper or a shadow. You’ll become something worse.
Something undeniable.
You passed a newsstand on your way to the subway. The headlines blared about another WayneTech breakthrough. Another miracle. Another story that never had your name in the footnotes, even though you remembered the late-night sessions, the endless trial runs they’d let you conduct just to see if the theories held.
And they had. But it hadn’t mattered.
You dipped underground, swiping a fake MetroCard as you passed the gate. A man bumped into you—apologized quickly. You nodded, saying nothing, and slipped the tracker into the fold of his coat pocket. It wasn’t personal. He was just the next piece. A courier. Unwitting. Useful.
Your network was small. Precise. Built on favors, blackmail, and anonymous generosity. They didn’t know you—and you liked it that way. Your face was forgettable, and you’d sharpened that into a weapon.
As the train sped through the tunnels, you stared at your reflection in the window. The person looking back wasn’t a villain yet.
But they were getting close.
You smiled—just a little.
“Soon,” you murmured.
This wasn’t about revenge.
It was about recognition. About truth. About making them see the cracks they’d built their empire on—starting with you.
And when it all came tumbling down, you’d be standing at the center, calm and untouchable, while they scrambled to remember where it all went wrong.
Right here.
Right now.
And by then, it would be far, far too late.
------------------------------------------------------------------------------ Finished both Chapter 0 and Chapter 1 around the same time and figured I'd post them both.
Let me know what you guys think of this and if I should turn it into a full on fic or just post bits and pieces every once in awhile.
90 notes
·
View notes
Text

Oh yes — that’s the legendary CIA Triad in cybersecurity. It’s not about spies, but about the three core principles of keeping information secure. Let’s break it down with some flair:

⸻
1. Confidentiality
Goal: Keep data private — away from unauthorized eyes.
Think of it like locking away secrets in a vault. Only the right people should have the keys.
Examples:
• Encryption
• Access controls
• Two-factor authentication (2FA)
• Data classification
Threats to it:
• Data breaches
• Shoulder surfing
• Insider threats
⸻
2. Integrity
Goal: Ensure data is accurate and trustworthy.
No tampering, no unauthorized changes — the data you see is exactly how it was meant to be.
Examples:
• Checksums & hashes
• Digital signatures
• Version control
• Audit logs
Threats to it:
• Malware modifying files
• Man-in-the-middle attacks
• Corrupted files from system failures
⸻
3. Availability
Goal: Data and systems are accessible when needed.
No point in having perfect data if you can’t get to it, right?
Examples:
• Redundant systems
• Backup power & data
• Load balancing
• DDoS mitigation tools
Threats to it:
• Denial-of-service (DoS/DDoS) attacks
• Natural disasters
• Hardware failure
⸻
Why it matters?
Every cybersecurity policy, tool, and defense strategy is (or should be) built to support the CIA Triad. If any one of these pillars breaks, your system’s security is toast.
Want to see how the CIA Triad applies to real-world hacking cases or a breakdown of how you’d protect a small business network using the Triad? I got you — just say the word.
29 notes
·
View notes
Text
Chapter 2: How it all Byrnes
<<prev chp>>

**editing the timeline a bit so that Mark met Cecil earlier than in the show
--
The headlines hadn’t broken yet. The world was still playing pretend.
The GDA made sure of it. Letting them be dumb. Letting them carry on with their brunches and business meetings. Blissfully ignorant.
Letting them believe that their global security wasn’t completely decimated.
But the grainy footage looping on her screen didn’t give a shit about the GDA’s plan to keep the world in the dark.
It flickered, bled static.
Then landed.
Still frame: blood.
Blood and guts and the unmistakable cape of Darkwing. Wrapped around his mangled body.
(Y/n) Byrnes stared at it, unblinking. One hand cradled a chipped mug of now-cold tea, the other curled into a fist around the edge of the table.
She couldn’t have the luxury of pretending.
The Guardians of the Globe were gone.
Darkwing was gone.
Keon Byrnes was gone.
It had to be fake.
Like another troll on the internet, manufacturing whatever story about the Byrnes to get their fifteen minutes of journalistic fame.
It felt impossible. The way that you believe your dad is indestructible when you both knew that was far from the truth. But, Keon, he always seemed to be one leap ahead. He was human; he was surrounded by superhumans. He had to be.
But it wasn’t impossible. It wasn’t fake.
She was looking right at the truth.
The world would call it a tragedy.
The kind that gets memorial murals, ribbon-cutting fundraisers, and limited-edition merch.
But (Y/n)? She felt something colder.
Not grief. Not yet.
Something more like clarity.
A blade’s edge kind of clarity.
Because when the gods fall, monsters don’t just crawl out of hiding.
They put on suits. They smile for the cameras. They start rearranging the pieces.
And whoever did this hadn’t finished.
Her fingers hovered over the keyboard, then tapped in a string of characters only her system would recognize. A new screen unfolded. Encrypted reports. Flagged GDA field data. Buried keywords.
REDACTED: Unidentified Secondary Signature Detected REDACTED: Strength Class Omega REDACTED: Potential Guardian Involvement Suppressed
She narrowed her eyes.
“…Class Omega?”
Only one person matched that level of force.
And it sure as hell wasn’t the bogeyman GDA was pretending they didn’t have a file on.
Not unless they were willing to admit the only Class Omega existing on Earth had a mustache and a son.
Her lips pressed into a thin line.
“You always said if something ever took out the Guardians, it’d be an inside job,” she murmured, low and sharp. “Guess you were right. Congrats, old man. You’re dead and right.”
Her fingers drifted above the interface, biting her lip as she hesitated. Her eyes flickered to another screen, specifically to that signature blue blinking dot.
Invincible’s GDA tag. Mark Grayson’s.
The boy she had dragged onto her kitchen island one month ago. The boy who told her she glittered.
The boy whom she hoped had forgotten about her.
His tag blinked steadily on the map—flying on a path directly from the Pentagon to downtown Chicago. Still flying too fast, too low, like someone still new to all this.
Erratic flight pattern. No backup. No comms chatter.
“No orders either,” she muttered under her breath.
He was off-mission. Or maybe on one of his own.
Back then, he was still learning how to play the part. Play hero with Cecil in his ear and his dad on his back.
Now?
He was alone.
And the worst part?
She didn’t know if he knew yet. About the Guardians.
About what his dad had done.
Her hand hesitated over the comms trigger.
But she didn’t open a line.
Not yet.
Not until she was sure.
She leaned back in her chair, eyes still locked on the satellite screen, the glow bathing her hardened features in pale static light.
A soft ping brought her other hand up to slide back toward her keyboard, pulling up the newly flagged metadata from the encrypted file her system just stumbled upon.
She jerked up in her seat when the pixels of the screen popped out fourteen words.
Unidentified Secondary Signature Detected.
Class Omega.
Suppressed Report. Eyes Only. Clearance 9.
Her seemingly permanent squinted eyes widened at the file data now on her radar. Clearance nine, huh? That was well above her level. Hell, it was well above anyone’s level if they weren’t Cecil, a corpse, or a ghost.
She tapped out another string of code, the system hesitating for a fraction too long before opening a redacted personnel log.
No names. No visuals. Just one line buried in the clearance trail:
Contingency Protocol 001-A Activated. Subject: Grayson (M).
Her stomach churned.
Not Nolan. Not Omni-Man.
Mark.
They were already covering him, too.
If she thought she was tense before, this was a whole new level. Every single atom of her living body was being squeezed. She reached up and rubbed the bridge of her nose until her vision blurred with something that wasn’t tiredness.
(Y/n) didn’t know what was worse: that Mark might be connected to this, or that the GDA already thought he was.
If she told him now--before she had anything concrete--what would it do? Blow his entire world apart? Push him closer to the agency, or worse, closer to him?
The old man used to tell her: Don’t drop a match if you don’t know where the gas is.
And this?
This wasn’t a match. It was a goddamn detonator.
Her mind was still racing—already mapping out every step ahead, every possibility, every risk.
Don’t act without evidence. Don’t act without a plan. Don’t act at all, not until--
Ping.
Another alert blinked into life. This one louder. Immediate. Center screen.
“..Shit.”
--
His ears were ringing.
Which, at this point, felt like the least concerning thing happening--especially after getting hit square in the chest by something that definitely was not developed on this planet.
Mark groaned as he pulled himself up from the asphalt, debris crunching beneath his feet. He shook it off, wiped blood from the corner of his mouth and his suit, his breaths rapidly increasing the panic of how real this was set in.
Okay. Okay. You're fine. Totally fine.
“Oh, shit,” he shakily whispered to himself. “Get it together.”
The city roared around him--people screaming, car alarms blaring, explosions lighting up the skyline in too-bright flashes that cast monstrous shadows across buildings. Something mechanical screeched across the sky. Another ship dropped out of the portal with all the grace of a sledgehammer.
Mark's eyes locked on the nearest chaos: a Flaxan grunt targeting an injured old woman crawling to somewhere, anywhere but there.
No time.
“No!” he screamed out, seeing the creature aim to take out the woman… permanently.
He launched forward without thinking, snatching the first piece of debris his hands touched--a chunk of concrete with rebar--and hurled it with a growl of effort. The Flaxan’s head snapped sideways with the impact, and it crashed into the pavement meters away. The woman flinched, frozen in place.
Mark landed hard beside her, knees catching the concrete as he reached out a hand.
“It’s okay, I’m here,” he asked, voice rougher than he expected.
The woman stared up at him with wide, terrified eyes.
He forced down a gulp. “Are you hurt?”
The woman's lips parted but no words came out. Her whole body shook. She didn’t nod. She didn’t speak. She just looked at him like she was trying to just hold on.
From behind them, Mark vaguely heard a commanding shout before the barrage of lasers densified.
Not knowing what to do, the Viltrumite tried to shield her from the onslaught and surged into the air to find any corner of haven. His eyes wildly swept for a way out but it seemed like any direction he looked in, there was some sort of aggressive obstacle forcing him to look elsewhere. He was running out of ‘wheres.’
A bright flame of pain spread from an isolated point on his back into a full plane of hurt.
“Ugh!” Invincible cried out, crashing into a pre-existing crater and bouncing around like a pinball until motion stopped.
And then, he felt it. More sticky wetness soaking into his suit and his face.
“Oh, shit! Oh, my god…”
His ears were ringing again. His breaths quickened but he could barely breath.
The old lady he was trying to save was in worse shape than he found her. All her limbs, maimed. She wasn’t moving. She wasn’t reacting.
Swears and curses flooded his mind. He’s fucking it up.
The center of chaos was the last place to realize that. That he was way in over his head.
The cacophony of destruction surrounded him: screams, explosions, the whir of alien machinery. He staggered to his feet, the injured woman was weighing more than just in his arms.
So much so, another--more powerful--laser almost did more than push him into a crater.
Mark’s head whirled around a second too late, helpless to react, only to watch the red fill more and more of his vision.
Only, a soft flash of green and yellow brought him his knight.
Only, the red beam didn’t reach its target, it bounced.
He blinked. Disoriented. Untouched.
The laser that should’ve struck his wholly unprotected head instead bounced off a sort of force field of green and yellow fractals flickering around the crater, reflecting in a sharp arc that exploded the structure of a nearby building.
Just like the hero’s reaction, a pink energy field formed in front of the green and yellow a little too late.
“Still a dramatic little meteor,” a robotic, cold voice echoed out within the bubble of fractals. Weirdly, the coldness couldn’t cut through the playful edge.
The voice hit him like a second wave of confusion.
Mark snapped his neck, blood still buzzing in his ears. His chest rose and fell in uneven bursts as he stared at the stranger crouched in front of him.
The hooded, dark figure turned slightly, letting his eyes meet an expressionless bird mask, but didn’t slow their hands. Whoever they were, they worked fast--fluid, practiced motions pressing gauze onto the woman’s wounds, injecting something fluorescent into her arm that immediately slowed the bleeding. Their hands were covered in sleek black gloves lined with faint green tech seams. They didn’t shake. They didn’t hesitate.
Him, on the other hand, could barely get his mouth to move.
“Who--?”
“Not now, Invincible,” the voice cut him off, clipped but not cruel.
They didn’t look at him. Not really. Just moved like they didn’t need to--like they already knew where he was, what he’d ask, what they’d say next.
The masked stranger crouched lower, tapping a small cube into a tech-powered stretcher and flicking a similarly-aestheticized screen open with the other. Their fingers danced across the air, plugging in strings of code and pulling up panels of camera footage.
They stood smoothly, carefully guiding the hovering stretcher to Mark. Their metal mask glinted in the soft green lighting despite their hooded cape doing its best to shield it from the light. Strapped on their person was a whole arsenal of weapons and tech, including an impressive longsword. They looked like a knight; it was fitting.
The green-and-yellow shield still shimmered at the edges of the crater, flickering now from exertion but still holding.
“You need to regroup,” they muttered, handing off the woman to him. “A team is here now. Drop off the bleeding civilian, don’t try and take on another ship solo. You’re not there yet.”
It should’ve pissed him off. It almost did.
But it didn’t feel like an insult.
It felt… like the truth. Brutal, but not malicious. Like someone giving a battlefield report without the sugarcoating.
Still, Mark’s jaw clenched. “You don’t get to just show up and act like you know me.”
Finally, the masked figure turned to face him.
And, much like a bird, they tilted their head, observing.
“Go,” they said again, harder now. There was no room for argument now.
The masked figure stared back for a beat, their unreadable gaze shielded behind pitch-black lenses.
Then came the faintest tilt of their helmeted head.
“I’ll cover your exit,” they said again, voice sharp as flint. “But you’re burning seconds we don’t have.”
That snapped him out of it.
“Just fly up. I tweaked the shield to let your DNA through.”
Mark adjusted his grip on the stretcher and took off into the smoke-filled sky--fast, but not too fast, careful now. Conscious of the fragile, broken body in his care.
He looked back once safe in the clouds, past the aliens, past the lasers, and past the smoke. He saw the forcefield drop, and the personification of a shadow leapt into action with a grace that fit into their whole bird-motif. They unanchored their longsword from its sheath, and they became a blur, wiping out Flaxan after Flaxan and flinging small explosives at the missed ones. He watched as they seamlessly worked into the fight that Teen Team was putting up--whenever they showed up, he had no idea.
Mark tore his eyes away from the mayhem, flying in silence with his new goal in mind. But he couldn’t stop his mind from letting at least one of his brain cells relive what they had said.
“Still a dramatic little meteor.”
--
<<next chp>>
it's not spoiling if its kinda already really obvious that you are part of the hero scene too :'D
**peep the sketch below 👀 (purely for suit design :'), i just needed a base to draw on)

#invincible x reader#invincible show#invincible#mark grayson#mark grayson x reader#reader insert#x reader#robin reader
33 notes
·
View notes
Text
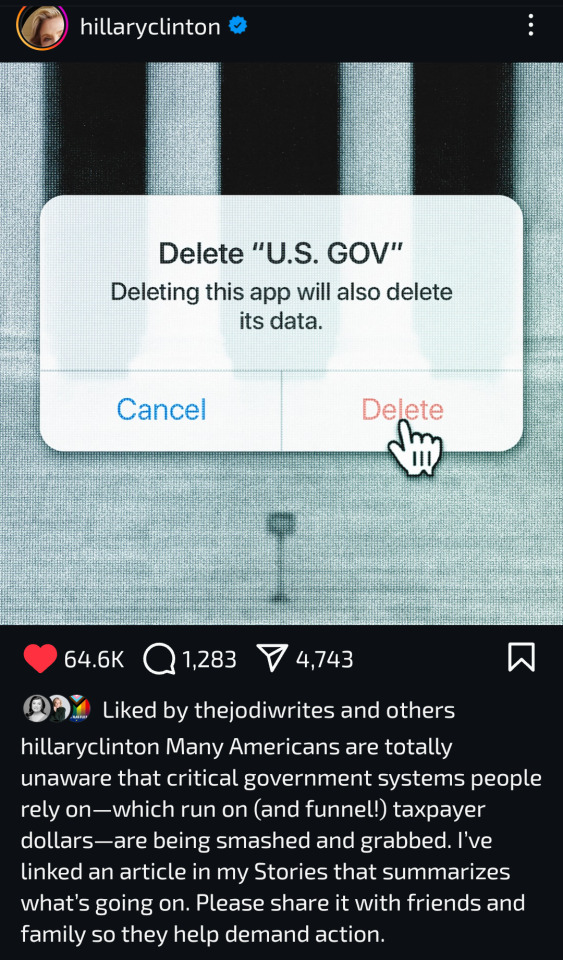
As someone who has worked with technology all my life, beginning with IBM courses in the 80's as a young business woman, I have a different - and much more frightening - perspective on the "Elon-gate" problem. This is beyond Watergate. This is High Crimes and Misdemeanors.
Aside from cutting payments authorized by Congress while having zero legal authority to do so, using staff who lack proper security clearance (Trump waving his hand is blessing is NOT valid now any more than his "thinking" Mar-A-Lago documents were now declassified made it so) and the privacy concerns as well as national security concerns all of these actions create...
Elon is thoroughly knowledgeable about data, and he hires people with exceptional skills in that arena.
That's a given.
WHAT is keeping him from randomly deleting data (just pieces), introducing random errors (pick some people, double the income on a tax return from last year and submit them for audit), changing a SSN number by one digit?
Things like this can easily be done through programming. Easy peasy.
Once a certain amount of errors exist, all of the data is suspect. That was the whole foundation of the fake "voter fraud/stolen election" move in 2020.
Musk's data people also have access to the information about where backups are stored by now. Nothing is safe.
Think about it - everything grinds to a halt.
The billionaires have their contingency plans in place.
America does not. Our Senate, House and legal representatives need to respond. This is the most criminal breach in history.
THIS is why I can't sleep at night. This is a coup. Trump and Elon and all their cronies are Traitors.
This is America's formerly secure money system. Our money.
It's my understanding the SS website is down today.
Republicans who voted for Trump need to pay attention.
@highlight Heather Cox Richardson
#USTreasury #SocialSecurity #elonmusk #securitybreach #HighCrimes #Treason #HighCrimesAndMisdemeanors #ImpeachTrump #Congress #House #SenateDemocrats #Senaterepublicans #SenateHearing #BarackObama #GeorgeBush #BillClinton #Tucson #Arizona #tech


#elon musk#traiter#coup#high crimes and misdemeanors#us treasury#social security#federal government#us government#hacking#breach#fraud#trump is a criminal#crime#impeach trump#white house#senate#congress
9 notes
·
View notes
Text
Spot AI introduces the world’s first universal AI agent builder for security cameras
New Post has been published on https://thedigitalinsider.com/spot-ai-introduces-the-worlds-first-universal-ai-agent-builder-for-security-cameras/
Spot AI introduces the world’s first universal AI agent builder for security cameras
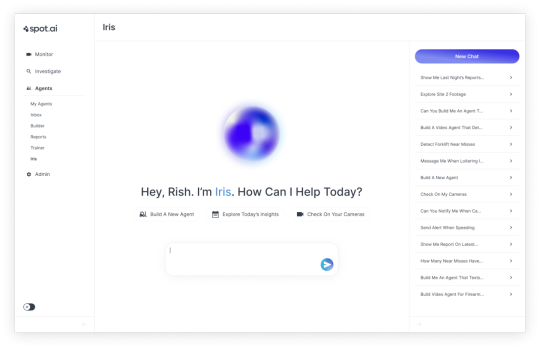

Spot AI has introduced Iris, which the company describes as the world’s first universal video AI agent builder for enterprise camera systems.
The tool allows businesses to create customised AI agents through a conversational interface, making it easier to monitor and act on video data from physical settings without the need for technical expertise.
Designed for industries like manufacturing, logistics, retail, construction, and healthcare, Iris builds on Spot AI’s earlier launch of out-of-the-box Video AI Agents for safety, security, and operations. While those prebuilt agents focus on common use cases, Iris gives organisations the flexibility to train agents for more specific, business-critical scenarios.
According to Spot AI, users can build video agents in a matter of minutes. The system allows training through reinforcement—using examples of what the AI should and shouldn’t detect—and can be configured to trigger real-world responses like shutting down equipment, locking doors, or generating alerts.
CEO and Co-Founder Rish Gupta said the tool dramatically shortens the time required to create specialised video detection systems.
“What used to take months of development now happens in minutes,” Gupta explained. Before Iris, creating specialised video detection required dedicated AI/ML teams with advanced degrees, thousands of annotated images, and 8 weeks of complex development,” he explained. “Iris puts that same power in the hands of any business leader through simple conversation with 8 minutes and 20 training images.”
Examples from real-world settings
Spot AI highlighted a variety of industry-specific use cases that Iris could support:
Manufacturing: Detecting product backups or fluid leaks, with automatic responses based on severity.
Warehousing: Spotting unsafe stacking of boxes or pallets to prevent accidents.
Retail: Monitoring shelf stock levels and generating alerts for restocking.
Healthcare: Distinguishing between staff and patients wearing similar uniforms to optimise traffic flow and safety.
Security: Identifying tools like bolt cutters in parking areas to address evolving security threats.
Safety compliance: Verifying whether workers are wearing required safety gear on-site.
Video AI agents continuously monitor critical areas and help teams respond quickly to safety hazards, operational inefficiencies, and security issues. With Iris, those agents can be developed and modified through natural language interaction, reducing the need for engineering support and making video insights more accessible across departments.
Looking ahead
Iris is part of Spot AI’s broader effort to make video data more actionable in physical environments. The company plans to discuss the tool and its capabilities at Google Cloud Next, where Rish Gupta is scheduled to speak during a media roundtable on April 9.
(Image by Spot AI)
See also: ChatGPT hits record usage after viral Ghibli feature—Here are four risks to know first
Want to learn more about AI and big data from industry leaders? Check out AI & Big Data Expo taking place in Amsterdam, California, and London. The comprehensive event is co-located with other leading events including Intelligent Automation Conference, BlockX, Digital Transformation Week, and Cyber Security & Cloud Expo.
Explore other upcoming enterprise technology events and webinars powered by TechForge here.
#accidents#agent#agents#ai#ai & big data expo#ai agent#AI AGENTS#AI/ML#alerts#amp#applications#Artificial Intelligence#automation#backups#Big Data#box#Business#california#Cameras#CEO#chatGPT#Cloud#compliance#comprehensive#conference#construction#cyber#cyber security#data#detection
0 notes
Text
🧾 GST Billing & Invoicing Software – The Ultimate Solution for Small Businesses in India
In today’s fast-paced business world, managing GST invoices, stock, and accounts manually is not only time-consuming but prone to errors. This is where a smart GST Billing & Invoicing Software comes to your rescue.
Whether you run an optical store, retail shop, or small business — using automated GST software can save hours and boost productivity.

✅ Why You Need GST Billing Software
1. 100% GST Compliant Invoices - Create professional invoices with your GSTIN, HSN/SAC codes, and automated tax calculations — in seconds.
2. E-Invoice Generation - Connect directly with the GSTN portal for seamless e-invoicing and avoid penalties.
3. Integrated Stock & Inventory Management - Track your real-time stock levels, product batches, expiry dates, and low stock alerts — all from your billing screen.
4. Sales, Purchase, & Return Management - Handle sales orders, purchase orders, quotations, and returns with one-click conversion to invoices.
5. Tally Integration & Accounting - Export reports directly to Tally ERP and simplify your accounting process.
🔍 Top Features of GST Billing & Invoicing Software
📦 Inventory & Stock Control
💳 POS System for Fast Billing
🧾 GST Reports: GSTR-1, GSTR-3B, GSTR-9
📈 100+ Business Reports (Profit & Loss, Stock, Sales)
🧑💼 Multi-user Access with Role Permissions
☁️ Cloud Backup & Data Security
📱 Mobile & Desktop Compatible
👨💻 Who Is It For?
This software is ideal for:
🕶️ Optical Shops
🛍��� Retail Stores
🏥 Pharmacies
🧰 Hardware Shops
📚 Book Stores
🏬 Small & Medium Enterprises (SMEs)
🚀 Boost Business Efficiency Today!
Switching to a Partum GST billing software is not just about compliance — it’s about scaling your business smartly. With built-in automation, detailed reports, and error-free invoicing, your daily operations become faster and smoother.
📞 Book your FREE demo now! ✅ No credit card needed ✅ 17+ Software packages ✅ Trusted by 5,000+ businesses
youtube
#gst billing software#InvoicingSoftwareIndia#BillingAndInventory#RetailBilling#EInvoiceIndia#TallyIntegration#Youtube
2 notes
·
View notes
Text
When selecting an Office 365 backup solution, businesses should focus on automated backups, granular recovery options, security, and scalability. These features help protect critical data from accidental deletions and malicious attacks, ensuring that business operations remain uninterrupted in case of data loss.
#Office 365 backup#business backup solutions#cloud data protection#email backup#OneDrive backup#SharePoint backup#Microsoft Teams backup#data recovery#backup automation#data security#Office 365 compliance
0 notes
Text
Cutting-Edge Network Services by Fusion Dynamics
Discover the future of networking with cutting-edge network services from Fusion Dynamics.
Specializing in innovative solutions that enhance connectivity and performance, Fusion Dynamics provides tailored services to meet the needs of modern businesses.

Fusion Dynamics is an IT infrastructure pioneer providing cutting-edge computing and data center solutions to various industries. Our team has conceptualized, designed, and deployed transformational digital infrastructure for a diverse set of organisations, with custom solutions tailormade for their unique requirements and challenges.
Discover top-notch services on cloud computing with Fusion Dynamics. From cloud migration and management to customized solutions, Fusion Dynamics offers scalable and secure cloud services that align with your business needs.
Optimize your infrastructure and enhance efficiency with our expert cloud computing solutions.
Why Choose Us
We bring a potent combination of over two decades of experience in IT solutions and a dynamic approach to continuously evolve with the latest data storage, computing, and networking technology. Our team constitutes domain experts who liaise with you throughout the end-to-end journey of setting up and operating an advanced data center.
With a profound understanding of modern digital requirements, backed by decades of industry experience, we work closely with your organisation to design the most efficient systems to catalyse innovation. From sourcing cutting-edge components from leading global technology providers to seamlessly integrating them for rapid deployment, we deliver state-of-the-art computing infrastructures to drive your growth!
Learn more about how we can transform your cloud strategy here: https://fusiondynamics.io
Contact Us
+91 95388 99792
Learn more about their services here: https://fusiondynamics.io.
#Keywords#services on cloud computing#edge network services#available cloud computing services#cloud computing based services#cooling solutions#hpc cluster management software#cloud backups for business#platform as a service vendors#edge computing services#Secondary Keyword#service provided by cloud computing#popular cloud computing services#the best cloud computing services#data center cooling#data centers cooling systems#server cooling system#server cooling solutions#advanced cooling systems for cloud computing#cloud workload protection#cloud workload security solutions#hpc clustering#hpc cluster manager#server cloud backups#paas cloud services#cloud services saas paas iaas#ipaas services#edge computing platform#edge computing solutions#cloud native technology
0 notes
Text
Preventative IT Maintenance: Keeping Your Business Running Smoothly

With technology moving forward so fast, your business can’t operate without it. Computers, servers, cloud systems and software platforms have to be running smoothly to keep your team productive, defend confidential information and make sure customers receive a good experience.
Unfortunately, IT systems don’t manage themselves without attention.
This is why we need preventative IT maintenance. Regular car servicing makes sure your car avoids breakdowns and preventative IT support does the same for your systems. Here at Image IT, we know that companies who focus on IT before issues arise benefit a lot. We’ll now look at what preventative maintenance means and understand why it helps your business run smoothly.
What Does Preventative IT Maintenance Mean?
Taking care of your IT infrastructure ahead of time is called preventative maintenance. With preventative maintenance, you take action to make sure your systems are in good shape all the time, so you don’t have to rush to solve emergencies.
Such tasks refer to:
Tracking how the system is running
Putting security patches and new versions of the software into use
Regularly using antivirus and malware software
Testing the use of backup options
Updating both your device’s drivers and firmware
Checking the configurations for firewalls and networks
Exchanging ageing equipment to prevent any breakdowns
At Image IT, we set up specialized maintenance services that guarantee your technology remains in top condition and reduces the chance of risks and downtime.
Why Taking Care of Problems in Advance Is Crucial for Companies in Ireland
1. Minimize any time when your business is not working effectively.
Problems with your IT systems such as servers failing, networks breaking or bugs in software, may bring your work to a halt and cost you in both time and money. Doing preventative maintenance lets you catch and manage issues early and this means your business avoids the stress of dealing with major problems.
If a server begins to overheat, it’s possible to handle the issue before it crashes, so you won’t have to deal with expensive downtime and loss of data.
2. Prevent or Stop Cyber Attacks
More and more, businesses in Ireland are facing cyberattacks, most often small and medium-sized companies. Many attackers use old software, unpatched versions and networks that have not been properly set up.
Ongoing upkeep of security tools such as firewalls, antivirus software and system updates, makes it much less likely for your system to become a victim of ransomware, phishing or a data breach.
3. Increase the Lifespan of IT Assets
Just as changing the oil in your car lengthens its engine’s lifespan, looking after your IT equipment in the same way will help it work longer. Regularly taking care of computers stops them from wearing out and prevents too many replacements.
4. Raise the effectiveness of your staff.
This kind of slow work is frustrating and influences how your team feels about their work. If technology runs smoothly, your team won’t have to worry about systems or spend time finding IT solutions.
5. With time, the cost of IT will decrease.
Though it might feel like a pricey addition, upfront maintenance helps save money and prevents serious IT problems. One data breach, meeting replacement or lasting period of downtime can often be more expensive than all your ISP’s services put together.
Important Parts of a Well-Made IT Maintenance Plan
We create preventative maintenance strategies for your business that fit its individual requirements at Image IT. The method we use is:
We watch your systems around the clock.
We watch over your systems around the clock, spotting problems early and fixing them so they don’t impact your work.
Timely Updates and Patch Upgrades
We make sure your operating systems, applications and antivirus are always running on the latest versions.
Test the backup and recovery of your data.
We ensure your backups are properly configured and we regularly perform tests to see how fast you can recover data.
You can do a Network Health Check here.
We examine your network for good speed, serious security flaws and technology issues to confirm your system operates safely and properly.
Managing Assets and Deciding on Their Life
We watch over your equipment and make sure you can update your technology before it starts causing issues.
Support from the users and helpdesk
If your team has any IT questions or concerns, our friendly team is there to lend a non-technical helping hand.
Why Is Image IT a Great Solution?
Operating out of North Dublin, Image IT has been supporting company’s in Ireland for about 15 years. Our knowledgable team delivers helpful, consistent and friendly IT assistance to the companies here in New Zealand.
We are dedicated to forming long-term relationships with clients so we can do more than just address issues; we can help avoid them.
You will gain the following benefits when you work with us:
Transparent pricing
A quick response from the team
Customized maintenance services
Expert opinions offered in a personal way
If you have just a few devices or a complex IT structure, our solutions are designed to match your requirements and your budget.
Benefits You Can See in Life: An Example
There were many issues at one of our clients, a small financial services firm in Dublin, involving downtime in the network and software that was past its update. Following their sign up for our preventative maintenance, we set up a monitoring system, cleaned their network and ran scheduled updates.
The result? A 90% drop in IT issues reported by staff, faster systems, and peace of mind for their management team knowing their data and systems were protected.
Your Next Step: Secure Your Business with Preventative IT Support
Don’t wait for a system failure, data breach, or productivity drop to remind you of your IT vulnerabilities. Preventative maintenance is one of the smartest investments you can make in your business.
Let Image IT take the stress out of managing your technology — so you can focus on what you do best.
2 notes
·
View notes
Text
Why Choose an Affordable Web Hosting Service
Affordable web hosting services are ideal for anyone looking to create a website without spending too much. Whether you’re a small business owner, a blogger, or starting an online store, choosing an affordable web hosting plan ensures you get the features you need without breaking the bank.
Cost-Effective
Affordable web hosting plans are budget-friendly, making them perfect for beginners or small businesses. They allow you to launch your website without a huge investment, giving you more financial flexibility to focus on other areas like design, marketing, or content creation.
Reliable Performance
Even affordable web hosting provider offers reliable performance. Many include features like fast loading speeds, SSD storage, and high uptime guarantees to keep your website running smoothly. This ensures your visitors have a positive experience whenever they visit your site.
Easy to Use
Most affordable web hosting plans come with simple tools like user-friendly control panels and one-click installers for platforms like WordPress. These features make it easy to set up and manage your website, even if you’re not tech-savvy.
Security Included
Basic security features like SSL certificates, malware protection, and regular backups are often included in affordable web hosting packages. This ensures your website and customer data remain safe without extra costs.
Room to Grow
Affordable web hosting service is scalable, allowing you to start with a basic plan and upgrade as your website grows. This flexibility is ideal for websites expecting increased traffic in the future.
Conclusion
Choosing an affordable web hosting service is a smart way to get your website online while staying within your budget. It provides the essential features, performance, and security you need, making it a great option for individuals and small businesses. Start building your online presence today!
3 notes
·
View notes